Security Now Episode 897 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte / Steve Gibson (00:00:00):
It's time for security. Now. Steve Gibson is here. It's another event Filled Patch Tuesday retrospective. We'll talk about a new automated attack framework. The script kits are gonna just love a replacement for true cryp for Linux, that gives you plausible deniability. And then he'll take a look at the NSA's proposal for memory safe languages. This is what everyone should pay attention to. Next on Security Now podcasts you love from people you trust. This is twi.
(00:00:39):
This is Security Now with Steve Gibson. Episode 897, recorded Tuesday, November 15th, 2022. Memory Safe Languages. Security now is brought to you by BitWarden. Get the password manager that offers a robust and cost effective solution that could drastically increase your chances of staying safe online. Get started with a free trial of a team's or enterprise plan, or get started for free across all devices as an individual user@bitwarden.com/twit. And by ExpressVPN, make sure your online activity and data are protected with the best VPN money can buy. Visit expressvpn.com/securitynow, right now and get three extra months free when you buy a one year package. And by Grammarly. The right tone can move any project forward. When you get it just right with Grammarly. Go to grammarly.com/tone to download and learn more about grammar leaf premiums, advanced tone suggestions. It's time for security. Now, the show, we talk about your security and privacy online with our guy right here, this cat, Mr. Steven Gibson of the We will protect you whether you want it or not.
(00:02:01):
Hi, Steve. Happy. Tuesday. We, we survived election day and we are now on to other things. Well, we got tonight's announcement from mar. Oh, that's right. It's huge. That's a huge, it's, we'll be at six 6:00 PM Pacific time, 9:00 PM Eastern. For those who are interested. I'm certainly a spectator, so we'll be watching. Yeah. I will be glued with my popcorn and we'll see what happens. That's a lot of fun. Yeah. also fun is today's topic. I I, with, this is another one of these weeks where there was no like, major cyber research that was, I always liked to, you know, to track cyber research things. Nothing really happened except a bunch of news, except that the NSA published a, a real interesting sort of an appeal to everyone to seriously consider switching to the use of memory safe languages. Yes. Yes.
(00:03:03):
Yes. Thus, thus, the title of today's episode of Security Now 897 for November 15th. Memory Safe Languages. We're going to do a little retrospective on the event filled more eventful than Microsoft would've wished. Patch Tuesday we're gonna look at a newly published, horrifying automated host attack framework, which script kits are sure to be jumping on. We've got a welcome new feature that's been introduced into GitHub. Also some three critical vulnerabilities in the it, it's only sixth in the world, but that gives it 1.9 million instances, the light speed web server. Oh, we've also got something I think is gonna be of interest to our Linux users, the spiritual successor to True Crypt and Vera Crypt for Linux. Oh, and then we're gonna do a little segment, two and a half minutes, we're gonna play of Australia's announcement of their intention to proactively attack the attackers, which that doesn't, I don't know how you, I don't know how you could do that legally.
(00:04:21):
Yikes. It's like, okay. And boy, she's not, she's pissed off. We've also got a controversial new feature that was added to iOS 16.1 0.1. Also, I just have to touch on a couple more decentralized finance catastrophes, believe it or not, Leo, other than the collapse of ftx last week or week, weekend before last. We've also got some miscellaneous and listener feedback. And then we're gonna, and we're gonna wrap up by taking a look at this national Security Agency promotion of the use of memory safe languages. So I think another great podcast for our listeners. Oh. And because of last Tuesday's election, they put up a chart on the screen at one point where I just said, okay, stop everything. Hold on. This is just so wrong. And I, we probably talked about this last year, but again, I just can't resist because this is just, it just makes my blood boil.
(00:05:25):
It's like, who's in charge? I, you know, I'm looking at, I'm trying to figure out what you don't like about it. We'll find out in just a little bit. Oh, I see. Yes, I do see it's green. Green is like way bigger than orange. Yes, you're right. I see. We'll show you in a second. Okay. <laugh>. Now that I, now that I look at it, yes. Oh, interesting. Huh. It's a perspective thing you just wouldn't understand, Steve. It's all about TV production. I have a lack of perspective <laugh>. That's right. Our show today, that's been said before. So our show today is brought to you by the password manager I use and love and been recommending for some time now. Bitwarden, I'm a big fan. Now, you probably know if you listen to this show that you gotta have a password manager. In fact, if you listen to this show and you're not using a password manager, you're not listening to the show, obviously, stop listening.
(00:06:22):
Pay attention, <laugh>. So really this is not necessarily for you. This might be for a friend or family member that you're helping secure. It might be, well, it might be if you're unhappy with your current password manager. I love BitWarden. You know, I've always, for a long time I've said that encryption is not reliable if it's not open source. If you don't know what they're doing, how, how are you gonna know if they're doing it right? I kind of feel the same way about a password manager. Bitwarden is the only open source. There's 0.1. Very important cross platform works everywhere. Windows, Mac, Linux, everywhere, iOS, Android, password Manager that can be used at home. You can have a personal edition at work. They've got business versions on the go and is trusted by millions. This is a really great solution.
(00:07:18):
With BitWarden. You can securely store and not just credentials, but anything you want to keep safe across personal and business worlds. They're always improving this. They just rolled out a few new features. If you're, you've heard me talk about BitWarden and sing its praises. These are some new things. Password protected, encrypted export. So most password managers have ways to export your vault. So you can go to another password manager, right? Or back it up, right? But, but there's a little flaw. Most of 'em export it in plain text. Hey, that's great for using if you just don't want any security, I guess. So now they've added encrypted exports. So this is for backup, obviously, so this is great. Or to share it with somebody or whatever. But that's a fantastic idea. They have this thing a mobile username generator, right? Every password manager has a password generator.
(00:08:10):
This will also generate a unique username, which is really cool. And it uses a number of different email providers, including mine. Fast Mail three of the five aliases that BitWarden supports mobile username generators really fantastic because then you, the bad guy would have to not only know your password, you'd have to know what your, the special username you're using. You can do Duck, duck Go email aliases support for that service has been integrated, bringing the a number of support alias services now up to five. That's fantastic. So you can do it on mobile, by the way. That's, that's the new thing. You can do it on your mobile device duct. Go Mac os browser integration. Bit Waner partnered with Duck Duco. We love them. Even though Steve hates the name. We, we love the service to create an integration with the Duck Duco browser for Mac.
(00:09:06):
We've talked about this before. So that's really cool. It's integrated into the browser. It's not an extension. This is a much more secure way to do it. Stay tuned for when they'll launch. This feature, I mean, bit Warden definitely has extensions for all the major browsers. I use it on Firefox. But I love the idea that having it built into the browser as part of the entire browser service, I think that's a great idea. Bit warden's great for individual users, free forever for individual users cuz it's open source. But they also have a number of business versions that I think are fantastic and include some features every business needs like BitWarden Send. So you're gonna be doing your taxes in the next few months, right? How often does an accountant send you your tax returns? Oh, we're all done through the email.
(00:09:52):
That's a terrible idea. Bitwarden send uses fully encrypted method to transmit sensitive information. It can be text, it can be files. You can generate unique and secure passwords, of course for every an site with enterprise grade security that's fully compliant. By the way, this is important too. GDPR, ccpa, hipaa, SOC two compliant. Now there are different business tiers. There's the team's organization option. That's $3 per month per user. The enterprise organization plan $5 a month per user. They'll allow you to share private data securely with coworkers across departments, the entire company. But as always with BitWarden, you wanna start with the basic free account, free forever, unlimited number of passwords on any platform and, and, and that personal database. Then you set that up and then you add the business database. So you get the best of both worlds. And for our business, by the way, that's a really important thing for us.
(00:10:50):
We want our employees to not only use the password manager at work, we want 'em to use it everywhere for everything, including their personal stuff. So that's really nice. And I have the premium account just cause I wanna support them. That's a, it's less than a buck a month. I think it's $10 a year. It's nothing. There's also a family organization plan, $3 33 cents a month and you get up to six users. So that's a really good deal too. Look, you gotta use a password manager, right? But can I recommend the one I use, the one I love, the one I think is the best bit warden, the only open source cross platform password manager that can be used at home on the go at work. It's trusted by millions of individuals, teams, and organizations worldwide. Get started with a, it's free forever for individuals, no problem.
(00:11:41):
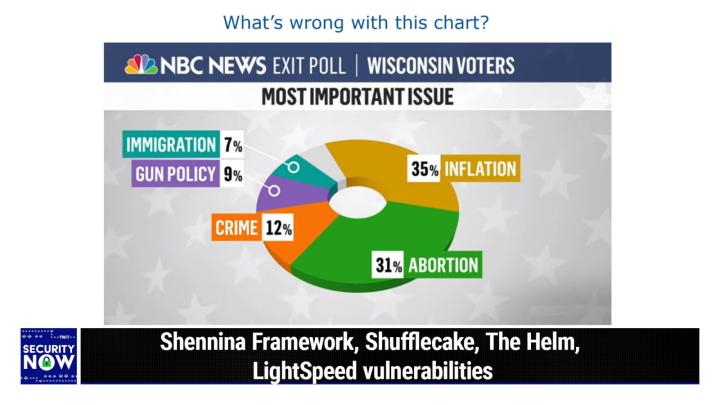
But you can also get started with a free trial of a teams or enterprise plan. Bit warden.com/twi, bit warden.com/twi. You know what, if you're at all interested, just start with a free plan. I immediately started paying 'em 10 bucks a year. Cuz I just think it's, I want to, I want to keep, get them to keep going. And it's a great enterprise solution to bit warden.com/toit. We thank 'em so much for their support of Mr. Gibson and security. Now. All right, I got a chart. So the, the whole point <laugh> of a pie chart Yes. Is to show you visually yes. The angles of the various slices of the pie. You know, I mean the, the reason aircraft instrumentation and even our cars still use dials like, you know, still have, have, have pointers. Is that, and, and a clock face, an analog clock face is so powerful is that we, it requires no interpretation, no figuring out what the numbers mean in order to get meaning from this.
(00:12:54):
And it turned, you know, like, like they, they tried to go all digital in cockpits years ago, and it turns out that was not a good idea because a pilot can instantly see the angle of needles as opposed to needing to interpret numbers. Yeah. So, so, so what happened last Tuesday during the election is that these, the, the various outlets could not resist doing this 3D thing to their pie charts <laugh>. And, and they, in order to make it more fancy 3d, they accentuated the, the, the, the third dimension creating this perspective. Well, so on today's picture of the week, it shows some, you know, a random exit poll with five different values. And the, the largest one is smaller looking than the next largest one in order, you know, in this chart, green looks like it's, you know, like way more than 90 degrees when in fact it's not.
(00:14:11):
I mean, and it, you know, compared to the orange thing. Anyway, it's just, I know I've mentioned this before, but I saw this and I thought, oh, well, you know, come on guys, just, you know, give, give us angles, which are, you know, a flat pie chart that we're looking down on from above rather than like, oh, we're gonna make this 3D and fancy. But it's pretty Steve. Yeah, <laugh>. It may be inaccurate, but it's pretty. Yeah, that's right. Yeah. Okay. Anyway, I'm done with my ramp on that <laugh>. Last Tuesday was November's, not only was it the midterm elections in the us it was November's Patch Tuesday. We had security updates being released by Adobe, Microsoft, sap, Android, VMware, Citrix and others. You know, everybody sort of piled on, probably hoping to like not be seen as, obviously if everyone does it on the same day.
(00:15:08):
In the case of Microsoft 67, security flaws were fixed. So, you know, on the high side, but not, you know, not 167. And among those were the two lingering so-called proxy, not Shell zero day vulnerabilities, which had been continuing to plague those running onsite exchange server installations. There were also another four actively exploited zero days fixed by last week's update. There was a remote code execution in the JS script nine scripting language. The, the Google tag team found and reported that to Microsoft. And now, again, zero days, right? They were, they were being exploited when they were discovered. There was a mark of the web bypass known as Zippy reads an elevation of privilege in the Windows print, spool or service. Were still discovering problems with that. Microsoft found that one being exploited and also an elevation of privilege in the windows cryptographic number generation key isolation service, which again, clever people are finding these problems and using them to elevate their privileges, typically, obviously, bad people.
(00:16:29):
So Microsoft found that being happening. However, amid all this, we did not get past this month's patch Tuesday without the induction of some new headaches for enterprise admins. Since last Tuesday, Microsoft has been investigating the cause behind many reports and no doubt, many quick rollbacks of the month's improvements to Windows which affected enterprise domain controllers, which started experiencing curb sign-in failures and other authentication problems. Well, we now, we now know since Microsoft said we're, well, we're investigating this. We know what's going on after a little bit about Curb buros, after Windows 2000 Curb, Buros replaced the creaky and never quite ready for primetime homegrown NT Land Manager protocol. And you know, we've discussed ntl m's. Many security problems through the years on this podcast. Kerberos was designed by M i t and FIR was first released. Interestingly, the year after I first published Spin Write, yes, way back in 1988 was when Curb Happened.
(00:17:51):
So it's been around for 39 years. It's a Bulletproof client server, mutual authentication protocol that works well, at least it did for Windows until last week. You know, they're gonna get it fixed. I'm sure they've acknowledged the trouble by saying this is Microsoft. After installing updates released on November 8th, 2022 or later on Windows servers with the domain controller role, you might have issues with authentication, which is to say, you know, pretty much all authentication that, that the domain controllers are using. They said, when this issue is encountered, you might receive a Windows, a Microsoft Windows Kerberos key distribution center, event ID 14 error event in the system section of event log on your domain controller with the below text. And as a consequence, here's what happens. Domain users sign in might fail. This might, this also might affect Active directory federation services authentication group managed services accounts used for services such as internet information services.
(00:19:13):
You know, their, their IIS web server might fail to authenticate remote desktop connections using domain users might fail to connect. Of course, you know, all these mights are actually wills, right? You might be able, we and we read this as you will be unable to access shared folders on workstations and file shares on servers printing that requires domain user authentication might fail or, you know, will anyway. So, you know this is the typical collapse that we on we are in with increasing frequency seeing, following the application of a monthly round of patches and improvements. Thanks to a listener, Jonathan, I'm sorry, Johan, Johann Milberg who tweeted about this. There's a Reddit thread that explains what happened. Now, the current best practice is to disable the use of the very old RC four cipher for Kerberos. But November's trouble has hit those enterprises, which did.
(00:20:26):
So this suggests that Microsoft did not test their November changes under what is now well established current best practices. I've got a link in the show notes to this Reddit thread for anyone who's interested and who would be affected by this. The, the it, it documents the fixes to this, which have worked for all of those who have implemented them. So that might be useful to some of our listeners. We tell everyone, of course, that patching as soon as possible can often be critical, and we know that it can be, but it's also true as we seem to keep seeing that doing so might also cause major systemic failures throughout an organization. So it's no wonder that those whose jobs this is to deal with this are, you know, notoriously high stressed anyway. So a bunch of problems fixed a bunch of zero days fixed a regression, which Microsoft will fix, I'm sure, and some workarounds.
(00:21:32):
So your typical patch Tuesday this next bit of news falls under the category labeled not all things that can be done should be done, and we occasionally encount those, encounter those on the podcast. Unfortunately, a new smart host attack automation framework that's a host attack automation framework was open sourced a week ago, last Tuesday on GitHub. My first thought was, please don't make attacking hosts any easier for the script kits, but it's too late. A cybersecurity engineer by the name of MA Amed explained that back in 2019, he and a fellow researcher, Cali, for for a participated in a security competition for developing offensive security tools, not defensive offensive. And as we'll see a little bit later these might be now of interest to Australia, but we'll get that, we'll get there in a minute. So Maan wrote, he said, I enjoy building security tools, and this competition was funded by H I tb.
(00:23:00):
That's hack in the box with a reward of $100,000 for the winners. He says, I thought it would be an interesting challenge to work on as a side project. I met my friend Khali. He was also interested in winning this competition. We signed up and once accepted, we started meeting regularly to build this project. Okay, so the, the Hack in the Box Cyber Week AI challenge, as it was called, had two categories, host exploitation or malware evasion. And unfortunately, they chose the Host exploitation option. So he wrote Host Exploitation sounds more relevant to our experience. The goal was to build a host exploitation framework using AI based on the concept of deep exploit. The winning team should ideally prove the accuracy of the model, the improvement of the training and execution speed, and the technical features that have been added to the framework. We started experimenting with Deep Exploit and how it works, and we decided to start a new project based on the ideas we had on how to improve that tool.
(00:24:21):
This eventually ended up having us develop something that they named Sheina, S h e n n i n a, Sheina, a host execution of, so sorry, a host exploitation framework. He said, he said, the project is four times faster than Deep exploit. We were excited about the results. Shaina comes with a deception detection capability that detects if the machine being exploited is a virtual machine or container, and then terminates post exploitation once it's detected. This feature is powered by Mesp Exploit modules. The Shaina framework has qualified for the top five projects out of 40 that is in that, in that competition, he said, we worked on developing the tool further to prepare for our final demo that will be live at H I T B Abu Dhabi 2019. Okay, so that was what, three years ago? He said, unfortunately, the rules of the competition and the judging criteria changed during the demo day, which I guess meant that they didn't do as well as they expected to.
(00:25:39):
He said, we enjoyed H I TB Cyber Week 2019. It was an amazing journey, and I enjoyed building the Shane framework. I also printed my research, presented my research on J W T hacking at the time, but jwt, or, or is is the abbreviation for Jason We tokens. And he says it was a busy week. Finally, he said, we're planning to open source the project and the experiment. There are no plans for further maintaining Shane in the near future. And that open sourcing of Shaina just came to pass this powerful shaina host exploitation framework is now up on GitHub. They do comment under the FAQ question. They an, they ask themselves, why are we solving this problem with ai? And they reply, the problem should be solved by a hash tree without using ai. However, the H I TB Cyber Week AI challenge required the project to find ways to solve it through ai.
(00:26:49):
So that's what they did. So, okay, so extracting some of the more interesting bits from the project's abstract they explain, SHEINA is an automated host exploitation framework. The mission of the project is to fully automate the scanning, vulnerability scanning and analysis and exploitation using artificial intelligence. Shaina is integrated with METAS exploit and N map for performing the attacks, as well as being integrated with an in-house command and control server for exfiltrating data from compromised machines automatically. And I'm thinking, and why post this tool publicly? Wow. Then they continue. Shane scans a set of input targets for available network services, uses its AI engine to identify recommended exploits for the attacks, then attempts to test and attack the targets if the attack succeeds. Shane proceeds with the post exploitation phase. The AI engine is initially trained against live targets to learn reliable exploits against remote services.
(00:28:12):
Shane also supports a heuristics mode for identifying recommended exploits. The documentation can be found in the docs directory within the project, and then they enumerate their features. Automated self-learning approach for finding exploits high performance using managed concurrency design, intelligent exploits, clustering post exploitation capabilities, deception detection, ransomware simulation capabilities, automated data exfiltration, vulnerability scanning mode, heuristic mode support for recommended exploits, windows, Linux, and MAC OS support for agents. Scriptable attack method with the post exploitation phase exploits suggests exploits suggestions for kernel exploits. OUTAND technique testing for exploitation checks, automated exfiltration of important data on compromised servers, reporting capabilities, coverage for 40 plus TTPs. That's of course tactic techniques and procedures within the MIR attack framework and supports multi input targets. Well, that's just great. It's bad enough <laugh>, really, I mean, do we have to be, be doing this, making this so easy for the script kits?
(00:29:45):
Well, this is the excuse they always give. It's for pen testing. You know, it's to simplify your pen testing. Ah, that's right. It's bad enough that the quite sophisticated and powerful Nmap scanner and METAS exploit exploit frameworks, both which have been developing and evolving over many years already allow sophisticated hackers to scan network regions and exploit them. But now this process has been automated with a somewhat smart front end that incorporates N MAP and Meta Exploit to create a turnkey all in one automated system that could be launched by junior hackers who would never have the ability to create such a tool themselves. So, buckle up <laugh>, you think it's meant for malicious use or, I obviously do. I just, I I I just think like, like, you know, it's one of those things that just because you can, doesn't mean you should it, this will be of vastly more interest to, to script kidds who say, oh look, we download it and I run it on my Linux box.
(00:31:05):
Yeah. And it just, it just attacks everything. And that's so's awesome <laugh>. Yeah. Yeah. But I mean, you could also see how red teams need tools or would like tools like this. Yes. So I'm sure that a red team could, could point it at their own network Right. And discover useful things. Unfortunately, it also accepts the command line star.star Oh. Which, you know, put it on the internet and let it loose. Yeah. Yes. So, and the fact that it runs on Linux means that if you compromise routers, it'll, you know, routers are all Linux based now. So just host this and start scanning and exploitating. Wow. Hmm. Yeah. So again, it, it's, it's, you know, we we're, we've seen where there's a problem with people posting proofs of concepts to GitHub now because they're immediately weaponized. Well now we've just weaponized N map and meta exploit. So you don't even have to read the manuals for them, you just press go <laugh>.
(00:32:15):
And unfortunately people will. Wow. Well, you know, the only one thing we've seen Leo over and over is the only way to drive change is to force it to happen. So the upside is, after a period of cataclysm we may end up with stronger software as a consequence, just because we didn't have a choice. Cuz you know, these AI bots are now roaming around intelligently learning how to attack Skynet. Anyone. Wow. Okay. In happier news, GitHub has just added a new private vulnerability reporting feature. It allows security researchers to, to report vulnerabilities to which they have found in, which exist in public repositories to their respective owners via a private channel for the first time. So, in other words, this new feature will allow sensitive security related reports to be filed to repo owners without having to file a publicly viewable entry in a repo's issues tracker probably should have had that along.
(00:33:34):
That's that was my first thought was, oh, you're celebrating that in 2022. Wow. Why is this a new feature today? Yeah, this should have been done long ago, but I guess maybe it wasn't in keeping with the spirit. Again, this is, you know, we need some evolution of the spirit. Right. And we're gonna get that Yeah. <Laugh> before long. Yeah. as I mentioned, there are presently 1.9 million unique instances of the light speed web server providing services on the internet. Light speed is ranked sixth most popular web server, which gives it about a 2% share of all web servers globally. So it's not, you know, not a big name, but it's there. The problem is, after some research by Palo Alto Networks, unit 42, any additions of either the free and open source version, which is known as open light speed, or the enterprise version, which is just light speed, which have not been updated in the past month, need to be patched immediately.
(00:34:45):
So I'm bringing this to our listener's attention because among them, I mean, I remember looking at light speed when I was considering servers. It's, it's a very, it is a recently written fast fleet little server, but it's got some problems. The Unit 42 research team took a close look at the source code for the, for open light speed, which of course is as you are often telling us, Leo. And you're right, a big advantage of open source, right? Is there it is. Yeah. You can, researchers if they're so inclined, can look at it and go wait a minute. That doesn't look like a, a type safe you know, cast there and so forth. Anyway, the unit 42 guys from Palo Alto Networks took a look at it and discovered three different vulnerabilities in the web server. The three vulnerabilities have been confirmed to similarly affect the non-open source enterprise version, which obviously is based on the same, you know, code base by chaining and exploiting the vulnerabilities, adversaries can compromise the web server to gain fully privileged remote code execution, meaning, you know, remote like over across the internet.
(00:36:10):
So there's the three vulnerabilities. There's a remote code execution, which is rated high severity with a CVSs of 8.8 and a privilege escalation, same high severity 8.8, and a directory traversal, which is given a medium severity of 5.8. A little over a month ago. Unit 42 responsibly disclosed their discovery of these three vulnerabilities to the server's publisher and their maintainer known as light speed technologies and even provided suggested remediation. Okay, that was on October 4th. In two weeks later on the 18th, light speed technologies released their updates. So anyone using the open version from 1.5 0.11 through 1.7 0.16 needs to immediately update to 1.7, point 16.1 and light speed versions 5.4 0.6 through 6.0 point 11 needs to immediately move to 6.0 0.12. Again, those, those were released on October 18th, not quite a month ago. So if this affects you, if you've got light speed running and you haven't, and you don't know that you've updated in the last month, do it.
(00:37:37):
There are 1.9 million of these in use. And since the fixes will be reflected in the open source version, bad guys will have no trouble seeing what was fixed and designing an exploit chain that Unit 42 warned of. Since the location of all light speed web servers are known to shown and other internet scanners, these servers will be found. So don't delay. Okay. A really cool bit of news and of interest for Linux users. Last Thursday, the guys at Kolsky Security Research, open sourced and interesting utility that I, I think will be of interest to our listeners. Here's how Kolsky explains their creation. They said, today we are are excited to release Shuffle Cake. A tool aimed at helping people whose freedom of expression is threatened by repressive authorities or dangerous criminal organizations, in particular, whistleblowers, investigative journalists and activists for human rights in a pressure in oppressive regimes.
(00:38:56):
Shuffled cake is floss, you know, free slash libre Open source software source code in C is available and released under the canoe General Public license three or Superior. They explained. Shuffled Cake is a tool for Linux that allows the creation of multiple hidden volumes on a storage device in such a way that it is very difficult even under forensic inspection to prove the existence of such volumes. Each volume is encrypted with a different secret key scrambled across the empty space of an underlying existing storage medium and indistinguishable from random noise when not decrypted, even in the presence of the Shuffle Cake software itself. Sorry, even if the presence of the Shuffle Cake software itself cannot be hidden, and hence the presence of secret volumes is suspected, the number of volumes is also hidden. This allows a user to create a hierarchy of plausible deniability where most hidden secret volumes are buried under less hidden decoy volumes, whose passwords can be surrendered under pressure.
(00:40:25):
In other words, a user can plausibly lie to a coercive adversary with a, about the existence of hidden data by providing a password that unlocks decoy data. Every volume can be managed independently as a virtual block device. In other words, you know, partitioned, formatted with any file system of choice and mounted and dismounted like a normal disc, the whole system is very fast, with only a minor slowdown in IO throughput compared to a bear L U K S encrypted disc and with negligible waste of memory and disc space. And I love this, they said, you can consider Shuffle Cake a spiritual successor of tools such as True Crypt and Vera Crypt, but vastly improved. First of all, it works natively on Linux. It supports any file system of choice and can manage up to 15 nested volumes per device making deniability of the existence of these partitions highly plausible.
(00:41:39):
So for anyone who's interested, look@shufflecake.net s h u f f l e c a k e.net and you'll find all the information there. Yeah, it looks really good for plausible deniability. I love that. Yeah, they did a, they did a beautiful job. Yeah. And Leo, I'm gonna take a sip of water while you tell us about our second sponsor. Okay. Then we're gonna talk about Australia deciding to take the gloves off. Woo. Yeah, this'll be interesting. Hmm. Hmm. Our show today brought to you by Express vpn. You know, this is, I love this because our advertisers know who listens to security now and they know your security focused. We did Bit War and a password manager. Now, let's talk about VPNs. You, I don't think I need to explain to you understand what a VPN does. It does. Well, three things primarily. One is of course, it, it protects your security by encrypting everything coming at everything coming out of your computer in an encrypted tunnel between you and the VPN server where it emerges into the public on the public internet.
(00:42:49):
It also protects your privacy by doing that. So it's security, but also privacy because your I S P and nobody along the way can see what you're doing. And that's important too. And of course, finally it gives you geographic mobility. You can appear on the internet pretty much anywhere you want with Express VPN because they have servers all over the world. You get your choice. If you just, and what's nice about Express vpn and they have a nice app, it's just a big button. You turn it on. Windows, Mac, Linux, iOS, Android, you can even put on some routers. They have their own router. Now they started selling. That is an Express VPN router. You turn it on, it's gonna automatically choose the best server for you in terms of speed. But let's say you wanna go to England, so you can watch UK Netflix, well, then you click up another button that says, you know, I want to be in London, then start it.
(00:43:41):
And now you're in London. You know what a VPN does. One thing I want to point out, you know, probably most of you are sophisticated enough to create your own vpn. I know Steve does. That doesn't give you the geographic mobility. And you know, it, it, it, honestly, it, it's somewhat limited because if you vpn, let's say back to your house where you're, you're running the server, your ISP sees the stuff emerging from your house. So it also limits the privacy thing. It's really only good for the first part, the security. If you're an open wifi access point, something like that, express VPN gives you all three because you're using a third party provider. Now, the big caveat, you've gotta trust the third party provider because they have access to all the stuff your internet service provider would have otherwise, cuz you're going through them.
(00:44:28):
That's where it becomes decrypted. And this, this is why I use Express vpn and we recommend Express vpn. Think of the extra mile to make sure there is no information about you on the Express VPN servers. And they, by the way, they get this audited regularly, so by an independent third party. So, and you can see those audit reports@expressvpn.com slash security. Now they use, if there was a good article on bleeping computer about six months ago, you could see that they use a a, a special version of Debian that refreshes itself every reboot. So it wipes the drive reinstall starts from scratch, and they do that every day. Plus, when you're on the server, they have a special server technology, they call it Trusted Server that loads into ram is sandboxed in memory. And then as soon as you leave the server, it goes away.
(00:45:16):
No traces left behind. We know this not only because of the audits, which say all of these things are true. We also know it because there are countries like Turkey where they don't, they don't serve warrants. They don't subpoena information. They just show up at the door and they take the server. And this has happened in many countries. It happened in Turkey not so long ago. What did they find on that Express VPN server? Nothing. No information about customers, nothing. It's Proof Express VPN protects your privacy. And with ISPs selling your data to data brokers, your information about your location on your phone being sold going to the irs, going to the Department of Homeland Security, we just learned that they, they buy big tranches of data from these data brokers. I think it's nice to know those Snoops cannot snoop mask your digital footprints.
(00:46:17):
I protect myself and you should too. With Express N when you connected to Express vpn, your IP address is hidden right now. This is important. Also, express VPN is not free. I wouldn't actually recommend a free VPN because it costs money to have servers all over the world. It costs money to have sufficient bandwidth for those servers to be fast enough. So you don't feel like you're, you're, you're going through Mud Express. VPN is fast enough that you can watch HD video. You can watch those Doctor Who episodes in full HD and in 4k and they, there's no slowdown. But also, and this is a little bit more subtle, they also rotate their IP addresses. One of the things that does happen with many VPNs, the IP addresses become associated with that vpn because that becomes your IP address when you exit the VPN server.
(00:47:03):
And that's how BBC I Player and others block VPNs is they know that's a VPN IP address. Express VPN assiduously rotates and moves and buys new blocks of IP addresses so that they never become identified as, oh yeah, he's on Express vpn. That's even more privacy for you. Put it on your phone, your computer on your router, turn it on with one button, you're protected. Turn it off anytime you want or leave it on. It's so fast you never notice. In fact, I've often left it on my accident forgetting that I had it on. I did a whole show on with the iPad with Express VPN turn on and after the show I went, oh, <laugh>. This whole time I've had Express VPN turn. Make sure your online activity and data's protected the best VPN money can buy. And it's not expensive, by the way.
(00:47:52):
Yes, you're paying for it, but it's less than seven bucks a month. When you use our special link, you get three months free with a one year package, less than seven bucks a month. That's your best deal. Express vpn.com/security. Now, another reason I love them, they spell express E X P R E S S, no vows dropped ex p r ESS vpn.com/security. Now check it out. If you've been looking for a VPN provider you can trust again and again. It's been express VPN ExpressVPN.com/security. Now we thank him so much for supporting Steve's efforts. I have your video ready, Steve. So good. Earlier I mentioned that Australia might have an interest in, in offensive as opposed to purely defensive cyber weaponry. As we previously noted here, Australia's been recently having, you know, more than their share of problems with cyber attacks. They've had a slew of them and they're apparently getting a bit tired of them.
(00:48:57):
So the straw that may have broken the camel's back is the most recent ransomware attack on an Australian private insurance provider named Medibank. Medibank said that attackers broke into their network, stole internal files, including sensitive personal and healthcare date details on 9.7 million. Australian then encrypted their files and demanded a ransom when a MetaBank refused to pay the ransom. Were gang going by the name of blog xx, although believed to be a spinoff of ral, began leaking some of me banks's patient records to intimidate Medibank and create public pressure to pay the ransom. One of the group's first leaks was a file named abortions. Not surprisingly, the blog XX actions have galvanized the Australian government and Australia is now vowed to go on the offensive. The group's activities have been met with outrage and significant political attention from the highest levels of the Australian government. Okay, so Claire O'Neill is an Australian minister for home affairs and she's the Minister of Cybersecurity. She was interviewed last week by ABC Insider and posted her two and a half minute discussion to Twitter. So here's what Claire had to, to say.
TV (00:50:28):
Mark Drefus and I announced with the Deputy Prime Minister yesterday that we're setting up a permanent standing operation, a partnership of new policing between the Australian Signals Directorate, which are the slab guns of the Australian Public Service and the Australian Federal Police. This is an entirely new model of operating for these two organizations. What they will do is scour the world, hunt down the criminal syndicates and gangs who are targeting Australia in cyber attacks and disrupt their efforts. This is Australia standing up and punching back. We are not gonna sit back while our citizens are treated like this way mm-hmm. <Affirmative> and allow there to be no consequences for that. Okay. Just to be clear though, this task force has been in place for a while though, hasn't it? No, that's incorrect. Okay. So this is a new operation, a permanent standing force of 100 of the best most capable cyber experts in this country that will be undertaking this task for the, for the first time offensively attacking these people, David.
(00:51:29):
So this is not a model of policing where we wait for a crime to be committed and then try to understand who it is and do something to the people who are responsible. We are offensively going to find these people, hunt them down and debilitate them before they can attack our country. What's your expectation here, what they'll be able to achieve? Because, you know, we know whether it's in this new standing operation or in, you know, the previous task forces. They've been trying for a while to go after these hackers the Americans have for years. They did manage to arrest a few of them about a year ago. What's your expectation about what they'll realistically be able to achieve? Yeah. Well, I think there's a perception in the community that it's, it's hard to do anything about cyber attacks and that's actually wrong.
(00:52:12):
There's an enormous amount that we can do. I think we need to shift away from the sense that the only good outcome here is someone behind bars because that can be hard when we've got people who are essentially being harbored by foreign governments and allowed to continue this type of activity. But what we can do is, is two really important things. The first thing is hunt these people down and disrupt their operations. It weakens these groups If governments like ours collaborate with the FBI and other police forces and intelligence agencies around the world. But the second important thing that we need to do is stand up and say that Australia is not gonna be a soft target for this sort of thing. And if people come after our citizens, we are gonna go after them
Leo Laporte / Steve Gibson (00:52:54):
<Laugh>. I don't think that's legal, right? I mean, you can't pro I you can't pursue people before they commit the crime for one thing. I know. I mean, this is like what <laugh> Very Australian. Very Australian. Yeah. Well, so her statement was released the same day that the Australian Federal Police issued a statement formally identifying the MetaBank hackers as being located in Russia, which, you know, comes as a surprise to no one Australian Federal police Commissioner Reese Kershaw said in his statement, he said, we believe we know which individuals are responsible but will not be naming them. What I will say is it will be holding talks with Russian law enforcement about these individuals. And, you know, despite an explosion in ransomware attacks, as we noted last week, more than 1.2 billion in payments made in 2021 alone, the cases where law enforcement agencies fought back and hacked the hackers have been rare.
(00:54:00):
There have been a few success stories such as the doj, you know, the US Department of Justice managing to recover the Colonial pipeline payments that was made to the dark side group. And both US Cybercom and the FBI hacked res servers following the CAA based attacks in both cases, dark side and res operations were shut down following these proactive potentially, I guess, offensive operations. And these effective responses did appear to give attackers at least a bit of pause. Yet the problem obviously persisted and persists. So it's gonna be very interesting to see what might come from Australia's new, you know, we're not gonna take this lying down anymore stance. But you know, exactly as you said, Leo, until now, the bad guys have had the advantage that they don't care about breaking cyber intrusion laws. Whereas global governments have been hampered by their need to play by the rules and act within the law.
(00:55:01):
So, you know, what does Australia exactly mean when they say they're gonna be going after the bad guys and disrupt them? You know, are they gonna break cyber intrusion laws to get that done? I, I guess we'll see. Hmm. Wow. She may have misunderstood exactly what they were gonna be doing. <Laugh>. Well, I don't know cuz I mean, he, you know, he sort of pushed back and she pushed back on him. Yeah. Wow. So anyway they, they did celebrate MetaBank decision to not capitulate to the demands of its attackers. And separately O'Neill suggested that the government might look into a law which formally bans payments made to ransomware and data extortion attackers altogether with the hope that this would strangle the financial incentive behind those attacks. Yeah. Like, you know, you're not gonna get any money out of anyone you attack in Australia, so go to attack <laugh> other people.
(00:56:03):
Again, I, I mean, I understand the outrage <laugh> oh. Yeah. You know, it's infuriating, but I know, but you can't be a, you can't be a vigilante. Yeah, you can't. No. So apple iOS, what observers are saying, looks like Apple capitulating to the demands to demands from China. The latest iOS 16.1 0.1, and also in the next beta of 16.2 have added a new timeout to the airdrop sharing feature, which limits the, the share with everyone option to 10 minutes. The reason Chinese influence is suspected is that for the time being, at least this only affects iPhones purchased in China, this new restriction is tied to the hardware. On the other hand, it's also worth noting that many people outside of China have celebrated the addition of this restriction as an extremely useful security improvement since inadvertently leaving everyone sharing on, you know, enabled could represent a significant security risk.
(00:57:22):
And interestingly, this is not the first time Apple has customized some acts, some aspects of their iPhone offerings for China. In, in researching this a bit, I learned, believe it or not, that the Taiwanese flag emoji is not available on iPhones sold in China. Talk about Petty anyway. Apple also uses the hardware tide method to limit the volume level of its devices within the EU as is required by the laws there. So in the case of this 10 minute ti, this 10 minute time limit, the motivation appears to be due to the fact that Chinese protestors had been using the feature to spread posters in opposition to Xing Ping and the Chinese government. And for those who think that this is a useful feature, Bloomberg reported that Apple does have plans to make this new airdrop option available globally next year, though presumably optional as opposed to mandatory where it is now in China.
(00:58:34):
So, you know, again, you know, we've seen that these global companies, whether it's Apple or Google or whomever, you know, if they wanna operate within, you know, other countries that have different regulations, they need to alter their behavior if they wanna stay there. Okay, a couple of decentralized finance notes that I just, I couldn't help with because these are just, again, I'm, it must be that by now our listeners understand where not to put their money. The Defi platform, Pando said it was the target of a hack Saturday, actually Saturday before last, when a threat actor attempted to steal more than $70 million worth of cryptocurrency from the platform's wallets. PDO said that it managed to hold onto 50 million of the attempted stolen funds, but the attacker successfully stole more than 21.8 million of its funds. They said that the hacker used an Oracle attack against one of its protocols, and that they're still hoping to negotiate with the attacker to return some of the stolen funds to which apparently the proper responses.
(00:59:56):
Well, you could hope I I wondered whether that had happened since now that's been 10 days so far, it doesn't appear the case. I found Pand do's Twitter thread where they had announced the hack of their system. Then over the course of several days, they followed the stolen funds as they were anonymously moved from one currency or exchange to another. You know, this is just a mess. Imagine watching nearly 22 million of your dollars moving around and being able to do nothing about it, such as the world we're in today. Also, the Defi platform, DFX Finance suffered a crypto heist reporting the loss of 4.185 million worth of cryptocurrency assets following an attack on its platform. Last week the company said the incident was identified as a, here's a new one, a re attack, which sounds like another of those increasingly common. Oh shoot, we, we failed to consider that possibility when we were designing our platform.
(01:01:12):
You know, there went more than $4 million. So anyways, I said, I'm sure everyone who follows the podcast by now knows that no one should rely upon what over and over again, appear to be half baked, poorly conceived, decentralized finance systems. And it clearly doesn't matter how well intended the creators and the operators of these systems are. And remember the famous Willie Sutton quote, you know, where he explained that the reason he robbed banks was because that's where the money was. For many people, money is the great motivator. That's the singular thing that's driving the ransomware attacks today. They could care less about anyone's data that's of no interest to them. They want money. And these defi systems are apparently sloshing around in way more money that they are responsible enough to manage. So yeah, don't put yours there. A little bit of miscellaneous. It turns out that a product which was a past sponsor of twit and of this Security Now podcast, the helm was unable to survive changes resulting from Covid 19.
(01:02:27):
They recently announced that they would be unable to continue operating past the end of the year. So they provided their users with 60 days notice, so November and December, and have already stopped accepting new subscriptions. They explained that in 2019 they had relocated their, their production operations from Mexico to China in order to improve their scalability and began to work on a version two system. But then Covid hit and their scheduling times more than doubled. I'm bringing this up here for two reasons. First, anyone who had obtained their own domain that was hosted at Helm's Registrar, you may wish to move it to somewhere else. If you wanna hold onto it, you know, like I would suggest hover my own registrar before they also became a twit sponsor. So current users will have only until the end of this year to get their domain moved.
(01:03:30):
But the helm is, you know, fully supporting that movement and Will, will, will work with any of their current users to do so. The second reason I'm mentioning this is that on their FAQ page, in response to the question, what can I do with the helm server after you shut down, they wrote, we are working on a firmware update for Helm servers to be converted to Linux servers running Armen. We will provide documentation for this conversion along with pointers to some guides for running mail and file sharing services. If you would like to continue using your helm, we expect this firmware update to be available in early to mid-December. So I've got a link here in the show notes to to the, to the support page about this happening, about helm shutting down. So, you know, just a heads up to anyone listening that if you are a helm user, some action will need to be taken between now and the end of the year.
(01:04:36):
I would imagine you'll want to, you know, keep your eye out for this firmware update to update to your device that would make it freely use useful elsewhere. Yeah, I think they're doing the, you know, the best they can. Yeah, they were hit by supply chain shortages and so forth. I know they're, I know the guys, they're great people and they're just trying to do the best thing they can. You won't be a email server anymore because serving your own email is not something for the faint of heart. It's very difficult to do from a home network. It's even for, for us, it'd be difficult to do because of the the fact that Gmail, the big mail companies just don't want to hear from you. You, they, they'll just black hole. You like that? So yeah. But at least you'll be able to use it for something and it's, it's a cool, I still have mine. It's a cool little thing. I'll, I'll, I'll put this. What is it? Arm, arm arm. Debian, Armen. Armen Armen. Not Ambien. Armen <laugh>.
(01:05:38):
Okay. So Elon meets Twitter. There's no way for a weekly podcast to possibly follow the insanity that has befallen Twitter. You know, ever since Elon has taken the reins, but one of our listeners, ed Ross, put me onto a Twitter thread from yesterday that gave me a chuckle, which I thought our listeners would appreciate. So Elon says he announced yesterday, part of today will be turning off the microservices bloatware. He says less than 20% are actually needed for Twitter to work exclamation point. And then of course, the engineers who said, Elon, you don't understand how it works, were fired immediately. Uhhuh. Yes, exactly. And after the results of pulling those plugs resulted in a new catastrophe, deur <laugh> someone named Zach Silverberg tweeted, he said, apparently they didn't turn off two-factor authentication, but they did turn off the service. Yeah. That sends you the two-factor authentication code.
(01:06:55):
So if you log out and try to log in with an authentication code, you simply won't receive one. Well, first of all, thank you Elon. You should have turned off SMS authentication a long time ago. <Laugh>. Yes, unfortunately, the way two-factor, and you know, I went through this a couple of years ago on Twitter. The way two-factor works on Twitter, you have to turn on first, but they give you two other methods. An authenticator app like Google Authenticator or hardware key. And once you get the others set up, you can uncheck as I did the sms. So if you didn't do that, if you only had sms, I don't know what you're gonna do Now, don't log out. The other thing, ed Bott butt did a good article on what to do now because Twitter security is clearly gonna fail. He suggested, I think he's right to immediately go to your Twitter account and turn off all the third party apps you've enabled.
(01:07:48):
Most of us over the years have, you know, turned on a variety of tools, maybe even log in with Twitter and stuff. For instance, I get into Medium by logging with Twitter. So medium shows up there. Given that we don't know what the security status of Twitter's gonna be going forward, disconnect those. Very, very good point. Just disconnect all of those. So I did that turn off two factor with sms, but make sure you have two factor on cuz I, you know, and then, then others are saying maybe you wanna delete your dms. Those are not encrypted. And if you had anything in there that you thought was private, maybe you should get rid of it now. It's, it's inevitable at this point that it's gonna slowly start to crumble and and the first thing that's gonna go is security.
(01:08:35):
So you'd be wise. I mean, if you wanna stay on there, that's fine, but if you'd be wise to, you know, give it nothing that <laugh> you don't wanna, you don't wanna lose. What a mess. It's such a mess. It's sad. It's really sad. Yeah, it is. Yeah. Daniel Smith a listener, he said this could be a new SN as in, you know, security now saying, and then he quoted somebody on Twitter named Lewis Lock Lock who replied to someone else. And I do love this quote, there's nothing more permanent than a temporary solution, <laugh>. That's true. You know, that you had a fix that you forgot you did right. Ages ago to your server. That's, that's exactly right. You're right. I, I overrode DNS for my e-commerce and then when they changed their ip, whoop, I stopped being able to accept payments. It was like whoop.
(01:09:30):
Yeah. Dennis Ke financial coach, he tweeted Hi, Steve wanted to let, to let you know the sponsor link for Drta seems to send you to a 4 0 4. I'd hate for y'all to lose money. Love the show. And so I went, I mean I tried drta.com/twi and sure enough it four oh fours. So I just thought Leo mostly for your benefit, Karen Junior. Dang it. But I would note that go to, yeah, they're a sponsor. Go to TWIT TV slash sponsors and there should be a link on there to any sponsor. And if the one that we told you doesn't work, let me let me click draw.com/twit. We error 4 0 4. So I will <laugh>, whoops. Wait a minute.
(01:10:22):
No. Yep. Yeah, it says things got outta control there. Auto compliance and risk management control passed. Find this pa page control failed <laugh>. Okay, I'll go I'll be taking a walk away. Well, no, after I do the next ad, cuz I know you're getting close, I will take a walk down to continuity and alert them. Thank Dennis Dennis. Dennis, thank you for the point. I appreciate that. Yeah, and by the way, if you wanna tweet me, don't do it on Twitter <laugh> do it on twit social, our ma it on instance. There we go. Yeah. Neil Baldridge tweeted, hi Steve, just a quick thank you for passing along your recommendation for the Silver Ship series. He says, I'm, I'm just into book six and finding those stories to be a great read. I'm trying to pace myself, but without much success. It's so nice to find an extensive series that's so enjoyable.
(01:11:15):
And so I'll just take this opportunity. Note that I totally agree. The series author Scott Yuha suggests that after finishing book 13, the reader should switch over to the four book PYS series. So that's what I did. I'm nearly finished with those four books. I'm more than halfway through the fourth of that four book series. So I can attest that they are every bit as delicious as the Silver Ships series. Those four books trace the history of an entirely different earth descended colony and its characters are every bit as interesting and alive as those in the silver ships. And what's intriguing is that by this point, the reader will have grown to intimately know two very different groups of human colonists. And Scott has explained that the two threads are going to be once the reader resumes with the Silver Ships series in book 14.
(01:12:17):
You know, I've come to know this diverse set of characters so well that I cannot wait to see what he has in store for them when they meet. It promises to be quite cool. So anyway, I I'm glad that a lot of our listeners have are are have picked up and are enjoying that series. Timmo Keft tweeted Hey Steve, I just wanted to respond to the whole open SSL debacle. You mentioned not many web servers except client certs. This is not the case though. Web servers serving big sites except client certs. Because CDNs and DDoS production services like CloudFlare use a client cert to assert their identity to web servers. They proxy this feature is used to ensure that the server only responds to requests provided through CloudFlare. Cloudflare calls this feature authenticated origin polls. So thank you Timmo. That certainly makes sense as a reason for web servers to solicit and accept client certs.
(01:13:25):
I guess I still doubt that the number is huge, but I agree that it would definitely be another reason for some increased vulnerability to the recent open SSL version three flaw. And of course it would be those servers that would be accepting client certs because they were being served by CDNs and DDoS protectors that are probably worth attacking. So that's a very good point. And finally NARA men IGA Tega, sorry about your <laugh> the way I pronounced your name. He said, dear Steve, after listening to episode 2 89, whoa, sorry, episode 8 92, she's a little dyslexic is okay. Dyslexic much. Yeah, <laugh> episode 8 92. He said, I decided to replace my raspberry pie home VPN server with a Zema board, which I ordered online right away following getting started instructions from the Casa Os. I created a new user and a complex password using its web UI on port 80.
(01:14:37):
But I was quite concerned when I noticed that the credentials set are only for the Casa web application. The board came with more than 10 default users on its Debbie and Os, which still had their default passwords after the initial configuration steps. He says, I could log in over SSH using Casa os Casa Os for username and password. The roots default password is also Casa Os. There are no warnings or instructions on the Zema board and Casa os websites about how to remove default users and passwords from the board. He said, I'm very concerned that if those boards are installed as a router according to this article and he provided a link, anyone will be able to ssh to it if owners don't proactively delete all Debbie and users thank you for your podcasts, your active listener for a few years already. So I wanted to share that because that's definitely a big heads up that would be important if somebody were using the ZMA board, not as I am to run spin, right?
(01:15:55):
And to develop spin. Right? But you know, using it as a pf sense router and like an exposing SSH publicly where it's got the default Casa os casa os username and password. So thank you very much for sending that to my attention. Yeah, that's nasty. Yeah. and boy they really absolutely should make a note. You know, or like the, the setup system should, should change username and password for all of those other users and not leave them, not only change them for the log into the web UI and leave all of the other ones alone. In a quick up update about spin, right? It's all but finished. I'm getting very, very close to the first pre-release alpha of six one. I ended up rewriting a bunch of the command line parser to make drive selection extremely flexible and powerful. Then as I had planned, I implemented the final verification for spin right by ranging to take a hash of an entire drive over which spin right had been run in order to absolutely verify that not a single bit had been changed across all of spin right's, various machinations with a drive.
(01:17:22):
And I discovered to my surprise that my A H C I driver would in a very low but non-zero percentage of 16 megabyte transfers occasionally not properly read the drives data to make sure this wasn't the, like I had just written this code. So to make sure that it wasn't the brand new hashing system that was at fault for this. I tried the same thing with an IDE drive using spin rights, also new bus mastering DMA driver. And that worked perfectly. So I know that my confidence testing code is working and that the new bus mastering driver is also working perfectly, but not so yet. The new A H C I driver, this just happened on Sunday evening and, and also a little bit yesterday morning. So, you know, before I switched to working on the podcast. So I haven't had a second yet to dig into any of this.
(01:18:23):
My guess is that something is going on with my end of transfer status testing where I might be shutting down the controller before it's completely finished. Having transferred everything Ram, since it's transferring data asynchronously in the background using dma, it's definitely necessary to make sure that it's finished. The good news is, thanks to now being able to take a hash of everything, spin right reads, I'm able to test that quickly and verify any fixes that I make and changes. So anyway, I'm anxious to get back to it there as I will tonight to see what's going on. And I expect to be able to say next week that I am finished with this round of spin right development and that it's currently in alpha testing. So very, very close. Cool. And I'm very excited. Yay. And Leo? Yes. tell us who sponsor, I'm gonna wet my vocal chords and then we're gonna talk about memory safe language.
(01:19:28):
I'm, I'm very interested in this cuz as you know, I li I like garbage collection. It's just me, but I like it. So we'll talk about that in just a little bit. But first a word from Grammarly. First of all, they don't put this in their copy. I just wanna say it. Grammarly's an amazing company and there's two reasons behind the scenes I love them. One is they use Lisp, the original artificial intelligence language, not for everything, but I'm, I'm, I'm told their backend is, is Lisp two, they're in Ukraine and under the most difficult of circumstances, continue to do the best software out there. So I'm a fan, I'm a, I'm a Grammarly stand. I can give you a bunch of other reasons why I use Grammarly and you should use Grammarly. Grammarly. It's not grammar checking. It sounds like it is.
(01:20:20):
It's not spell checking, it's a whole lot. It's communication, checking when it comes to work, communication is key. I often, I always tell my kids, learn to write, learn to write. Cuz no matter what your job is, being able to write is critical because that's how you communicate. Even if you don't have a writing job, you have to write emails, reports tweets, whatever. Grammarly works everywhere. I just mentioned everywhere you're working. So every important project not only gets done on time, but gets done clearly and communicates exactly what you intended to communicate. Grammarly has a free tier and they have a premium tier. Let me tell you about the premium tier. Their advanced tone suggestions and Grammarly Premium are awesome. They can help you reframe your communication to be more productive, more positive to get everyone on the same page. I have a good friend who is a manager and sometimes their emails are a little bit sharpened to the point cuz they're busy, they're managing, but they use Grammarly.
(01:21:29):
And when Grammarly says, you know, <laugh>, you might wanna just put a little little sugar on that and tells you how they do it. And it makes a big difference. In fact, I even hear them sometimes I hear them say but mostly I hear them say, thank you Grammarly. <Laugh>. It let's you reframe negative language to be more solution focused. And cuz it's not a, you know, a person over your shoulder, your spouse or what have you telling you, you know, you might wanna nicen that up. It's easier to take, right? Cause it's just a program, but it says, Hey, you know, you could put it this way and it might be more effective. And it is, it is. Let's think about this. The bottom line of all of our communications is to communicate our ideas and to get the other person to go along, right?
(01:22:18):
Grammarly helps you get that done. It makes your ideas clearer and it makes it easier for your coworkers to say, yeah, that's a great idea. Grammarly premium's, tone suggestions will take you. It's not that you're not a good writer, I'm not saying that, but they'll take your professional writing to the next level and, and make you more effective as a leader, as a communicator, as a team member. Grammarly has a lot of other great features. It's got advanced spelling. Yes, it does have grammar. Yes, punctuation is a big one. Okay? And I'm just gonna be honest with you, I use Grammarly, but I also judge when I see a, somebody spelling your wrong or putting a comma where one does not belong or leaving out a comma where one does belong. I judge we all do, we all say, hmm, well, okay, Grammarly will keep you from making those mistakes cuz they're just often, they're just, cuz you're going fast, they're typos, whatever, you know better, but it helps you do better.
(01:23:14):
And conciseness suggestions too, which are great to ensure your writing's professional mistake, free and clear. Paul Throt, professional writer, really good writer. He uses Grammarly because it helps him be even better. Oh, and, and he likes, and I do too. The emails we get every week saying this is, you know, these are, this is what all the words you typed, how many letters, words, you know, how many, it's great. Just the stats alone, the right tone, getting it right, communicating it properly can move any project forward. Get it right with Grammarly Grammarly's the best na are great people making a product that gets better all the time. G r a m a r l y grammarly.com/tone. Oh, I like that. I like that it's a special, special url, but they know it's from our ad, so you use that please. So that Steve gets credit grammarly.com/tone.
(01:24:11):
You can download and learn more about Grammarly premiums, advanced tone suggestions. You could try Grammarly. They even have a text box on the page. You could pay something in just to see what Grammarly would do with it. I think it's fantastic. G r a m a r l y.com/tone to test out grammarly's advanced tone suggestions. It's a subtle thing that can make a huge difference in your writing. Grammarly.Com/Tone. And you know, honestly in tweets too, thank the Elon. Maybe you wanna look at this. Grammarly.Com/Tone <laugh> sometimes just a little slight shift in the tone can make a all the difference, right? All right, Steve, let's talk about memory. Okay. It is, it is the number one problem, isn't it? In the It is, absolutely. Yeah. the like 70% of the vulnerabilities are this are caused by mismanagement of memory. So what I'm gonna share verbatim is what our national security agency, the NSA published in, in an effort to improve security across the board.
(01:25:32):
So they said in at the beginning, there's a short executive summary. They said Modern society relies heavily on software based automation, implicitly trusting developers to write software that operates in the expected way and cannot be compromised for malicious purposes. While developers often perform rigorous testing to prepare the logic and software for surprising conditions. Exploitable software vulnerabilities are still frequently based on memory issues. Examples include overflowing a memory buffer and leveraging issues with how software allocates and deallocates memory. Microsoft revealed at a conference in 2019 that from 2006 through 2018, 70% of their vulnerabilities were due to memory safety issues. Google also found a similar percentage of memory safety vulnerabilities over several years. In Chrome, malicious cyber actors can exploit these vulnerabilities for remote code execution or other adverse effects, which can also often compromise a device and be the first step in large scale network Intrusions commonly used languages such as c and c plus plus provide a lot of freedom and flexibility in memory management while relying heavily on the programmer to perform the needed checks on memory references.
(01:26:59):
Simple mistakes could lead to exploitable memory-based vulnerabilities. Software analysis tools can detect many instances of memory management issues and operating environment options can also provide some protection, but inherent protections offered by memory safe software languages can prevent or mitigate most memory management issues. Okay, so that sets it up. Here's how they elaborate on this. NSA recommends using a memory safe language when possible, while the use of added protections to non-member safe languages and the use of memory safe languages do not provide absolute protection against exploitable memory issues. They do provide considerable protection. Therefore, the overarching software community across the private sector, academia and the US government have begun initiatives to drive the culture of software development towards using memory safe languages. How a software program managers memory is core to preventing many vulnerabilities and ensuring a program is robust, exploiting poor or careless memory management can allow a malicious cyber actor to perform nefarious acts such as crashing the program at will or changing the instructions of the existing program to do whatever the actor desires.
(01:28:26):
Even unex exploitable issues with memory management can result in incorrect program results. Degradation of the program's performance over time or seemingly random crashes. Memory safety is a broad category of issues related to how a program manages memory. One common issue is called a buffer overflow, where data is accessed outside the bounds of an array. Other common issues relate to memory allocation. Languages can allocate new memory locations as a program is executing, and then deallocate the memory also called releasing or freeing the memory later when the memory is no longer needed. But if this is not done carefully by the developer, new memory may be allocated again and again as the program executes. Consequently, memory is not always freed when it is no longer needed resulting in a memory leak that could cause the program to eventually run out of available memory due to logic errors.
(01:29:31):
Programs can also attempt to use memory that has already been freed or even free memory that has already been freed. Another issue can arise when languages allow the use of a variable that has not been initialized, resulting in the variable using the value that was previously set at that location in memory. Finally, another challenging issue is called a race condition. The issue can occur when a program's results depend on the order of execution of two parts of the program accessing the same data. All of these memory issues are much too common occurrences. By exploiting these areas of memory issues, malicious actors who are not bound by normal expectations of software re of software use may find that they can enter unusual inputs into the program causing memory to be accessed, written, allocated, or deallocated in unexpected ways. In some cases, a malicious actor can exploit these memory management mistakes to access sensitive information, execute unauthorized code, or cause other negative impacts.
(01:30:44):
Since it may take a lot of experimenting with unusual inputs to find one that causes an unexpected response. Actors may use a technique called fuzzing to either randomly or intelligently crash craft multitudes of input values to the program until one is found that causes the program to crash. Advances in fuzzing tools and techniques have made finding problematic inputs easier for malicious actors in recent years. Once an actor discovers that they can crash the program with a particular input, they examine the code and work to determine what especially crafted input could do. In the worst case, such an input could allow the actor to take control of the system on which the program is running. Using a memory safe language can help prevent programmers from introducing certain types of memory related issues. Memory is managed automatically as part of the computer language. It does not rely on the programmer adding code to implement memory protections.
(01:32:01):
The language institutes automatic protections using a combination of compiled time and runtime checks. These inherent language features protect the programmer from introducing memory management mistakes unintentionally. Examples of memory safe languages include C sharp go Java, ruby, rust, and swift. Even with a memory. Safe language memory management is not entirely memory safe. Most memory safe languages recognize the software sometimes needs to perform an unsafe memory management function to accomplish certain tasks. As a result, classes or functions are available that are sorry, I scrolled and lost my place, are available that are recognized as non memory safe and allow the programmer to perform a potentially unsafe memory management task. Some languages require anything memory unsafe to be explicitly annotated as such to make the programmer and any reviewers of the, of the program aware that it is unsafe. Memory safe languages can also use libraries written in non-member safe languages and thus can contain unsafe memory functionality.
(01:33:32):
Although these ways of including memory unsafe mechanisms subvert the inherent memory safety, they help to localize where memory problems could exist. Allowing for extra scrutiny on those sections of code languages vary in their degree of memory. Safety instituted through inherent protections and mitigations. Some languages provide only relatively minimal memory safety, whereas other languages are very strict and provide considerable protections by controlling how memory is allocated, accessed and managed. For ex for languages with an extreme level of inherent protection, considerable work may be needed to simply get the program to compile due to checks and protections. Memory safety can be costly in performance and flexibility. Most memory safe languages require some sort of garbage collection to reclaim memory that has been allocated but is no longer needed by the program. There's also considerable performance overhead associated with checking the bounds on every array access that could potentially be outside of an array.
(01:34:48):
Alternatively, a similar performance hit can exist in a non-member safe language due to the checks a programmer, ads to the program to performed bounds checking and other memory management protections. Additional costs of using non-member safe languages include hard to diagnose memory corruption and occasional program crashes along with the potential for exploitation of memory access vulnerabilities. It is not trivial to shift a mature software development infrastructure from one computer language to another. Skilled programmers need to be trained in a new language and there is an efficiency hit when using a new language. Programmers must endure a learning curve and work their way through any newbie mistakes. While another approach is to hire programmers skilled in a memory safe language, they too will have their own learning curve for understanding the existing code base and the domain in which the software will function.
(01:35:59):
Now here's something that we've never talked about before, but I think it's an important thing to mention Here they say several mechanisms can be used to harden non-member safe languages to make them more memory safe. Analyzing the software using static and dynamic application security testing, abbreviated S A S T for static application security testing and D A S T for dynamic application security. TE can identify memory use issues in software. Static analysis examines the source code to find potential security issues. Using SaaS allows all of the code to be examined, but it can generate a considerable number of false positives through identifying potential issues incorrectly. However, SaaS can be used throughout the development of the software, allowing issues to be identified and fixed early in the software development process. Rigorous tests have shown that even the best performing SAST tools only identify a portion of memory issues in even the simplest software programs and usually generate many false positives.
(01:37:23):
In contrast to SaaS dynamic analysis, examines the code while it is executing. DAST requires a running application. This means most issues will not be identified until late in the development cycle, making the identified problem more expensive to fix and regressively test. DAST can only identify issues with code that is on the execution path when the tool is run. So code coverage is also an issue. However, DAST has a much lower percentage of false positives than SAST issues, such as a memory leak can be identified by dast, but the underlying cause of the memory issue may be very difficult to identify in the software. Neither SAST nor DAST can make non-member safe code totally memory safe. Since all tools have their strengths and weaknesses, it's recommended that multiple sast and DAST tools be run to increase the chances that memory or other issues are identified. Working through the issues identified by the tools can take considerable work, but will result in more robust and secure code vulnerable correl vulnerability Correlation tools can intake the results from multiple tools and integrate them into a single report to simplify and help prioritize analysis.
(01:38:59):
Couple last points. Auto exploitation features. The compilation and execution environment can be used to make it more difficult for cyber actors to exploit memory management issues. Most of these added features focus on limiting where code can be executed in memory and making memory layout unpredictable, which of course we've talked about extensively before. They said as a result, this reduces a malicious actor's opportunities to use the exploitation trade craft of executing data as code and overriding a return address to direct program flow to a nefarious location. Leveraging options such as control flow guard cfg will place restrictions on where code can be executed. Similarly, address space layout randomization as l r or data execution prevention, d e p add unpredictability to where items are located in memory and prevent data from me executed as code bypassing ass LR and d p is not insurmountable to a malicious actor, but it makes developing an exploit much more difficult and lowers the odds of an exploit succeeding.
(01:40:27):
Antip exploitation features can help mitigate vulnerabilities in both memory safe and non-member safe languages. So they conclude memory issues in software comprise a large portion of the exploitable vulnerabilities in existence. NSA advises organizations to consider making a strategic shift from programming languages that provide little or no inherent memory protection such as c and c plus plus to a memory safe language when possible. Once again, some examples of memory safe languages include C sharp go Java, ruby, rust, and swift memory. Safe languages provide differing degrees of memory usage protections. So available code hardening defenses such as compiler options, tool analysis and operating system configurations should be used for their protections as well. By using memory safe languages and available code hardening defenses, many memory vulnerabilities can be prevented, mitigated, or made very difficult for cyber actors to exploit. So, okay, I just, I wanted everyone to hear and to consider that.
(01:41:48):
And for those of our listeners who may be in positions where a, a choice of implementation language can be made for applications where the program security and integrity would be important. You know, consider perhaps breaking with a status quo that's been established and choose to bite the bullet and make a switch to a more secure programming language and environment. You know, take the relatively new rust language for example, since its first release in January of 2014, rust has been adopted by companies including Amazon Discord, Dropbox, Facebook, Mozilla, Google and Microsoft. You know, and it's a, it's a systems implementation language. It does not slow things down should changing to a memory safe language not be feasible for whatever reason. At least consider looking into the idea of using those static and dynamic analysis tools against your existing code base. You know, you don't have to treat what they say as gospel, but check out everything that they flag to make sure that it's not a problem.
(01:43:02):
You may find that a chunk of those things are problems and be glad that you just ran this thing over your code to see what it thinks. You know, all of that should really pay off if are all, let me, are all garbage collected languages memory safe? In theory, they would trigger an error at runtime if you had addressed memory that didn't exist, right? That crash. Yeah, I think so. Unless you used a pointer that had not, that was still available to you, that no longer pointed to anything and pilot should catch that. And we all, we often see those used after free problems. Yeah. Right, right, right. Yeah. I mean, rust actually doesn't do garbage. Collection does something a little more complex, but it's rest is very cool. Not a great language if you don't wanna spend a lot of time learning it. But yeah, I think Rust uses usage counting the call. Yeah, reference to reference, yeah. Yes. Yeah. Count by reference sort of. It's kind of, it's really clever. It's unique I think. And and we do hear that Rust has a steep learning curve. Oh, it does. I tried <laugh>, <laugh>.
(01:44:15):
It's, if you use Java, it should be pretty straightforward. If you're already using one of those languages that has a lot of, you know, declarative stuff it should feel fairly comfortable to you. It's not as best, you know, c is showing its age. Yeah. C plus plus is a mixed blessing. Yeah. e e even its developer agrees that it sort of didn't work out the way. If your language has Malik or Calec <laugh>, that's pretty, pretty good sign. You should not be using it. <Laugh>, right? Yeah. that's, that's for sure. Very good. I think this is great. So did, did you write, this is almost like a column. Did you write this like a column? Like you should submit this to somebody? Well, the NSA submitted it to the world. Oh, it's the nsa. Ah, that explains it. Yeah, yeah, yeah. Yes.
(01:45:04):
Cause that's what it feels like. It feels like a column. Okay. Yes. Yep. I missed that. I missed that one. Yep. I just wanted to share it cause I thought we made Yes, that's good. A bunch of really good points. Yeah. People forget the NSA has a couple of missions, one of which is to secure us at home through proper practices, whether it's hardening our machines or writing safe code. So that's a big part of the part of the job as well as, you know, spying on people and stuff like that. <Laugh>. Oh yeah. Oh, that sometimes those are incompatible, right? You know, if you wanna spy on them, you don't wanna use them to use anything secure. That would, that's wrong Steve. Great stuff is always Steve Gibson is@grc.com. That's his website Now. There's a lot there. So let me point you to a couple of things.
(01:45:48):
I mean, it's just fun to browse around. But of course that's where you'll find spin, right? Which is Steve Bread and Butter, the world's best mass storage, maintenance and recovery utility. Currently 6.0, soon to be 6.1. He's, he's very close Now. You'll get a free upgrade if you buy now. Get nervous. Yeah, I'm getting nervous. Do you have a button that you push that's like release the cracking? Well, there's just, there's just like so many little details, right? I know it's like, but, but exciting. So I'm excited and, and see Steve, this is good. And you should understand this. Steve isn't one of those people who releases it, sees what the bugs are and then fixes them. Steve wants to release a perfect piece of software from version 1.0. So he's, that, that would make me nervous too. In 2004, spin right Six was released and there are no known bugs.
(01:46:40):
Haven't patched it since. That's kind of amazing. Really amazing. So that's one thing. Spin, right? Probably grc.com/spin, right? It'd probably take you there. You also should take a look at the podcast cuz he has two copies of the podcast that we don't have on our TWI site. One is the 16 Kilobit audio. It's a little scratchy, but if you have limited bandwidth, it's the smallest version. Actually it's the second smallest version cause it's the smallest version I'm sure is text only. That's the transcriptions Lane Ferris does, which are great. You might want 'em separately. You might want 'em together with the audio. So you can read along as you listen. And it's certainly a utility you can use to search for part of any of the shows, any of the 897 shows and find those, those comments right in the show. So it's really, really a great thing.
(01:47:30):
He also has 64 Kilobit audio, the full quality audio. We have that and video at our website, TWI tv slash sn. You can also find security Now on YouTube, there's a YouTube channel probably, I'm not sure, but I think it's youtube.com/security. Now, if you go to youtube.com/twi, you'll find, besides all the twi bits and the shorts and stuff, you'll find a list of all the shows and you can subscribe from there as well. Of course, the easiest thing to do, probably for most people is to find a podcast player you like and subscribe to security now. And that, that way you'll get it automatically as soon as it's available. It downloads automatically. You can listen whenever you want. If you wanna watch us do it live, get the very first, first pressing the e security. Now you can <laugh> I never really thought of it that way, but I guess so you can go watch us live at live dot twit tv every Tuesday right after Mac Break Weekly.
(01:48:27):
That time will vary somewhere around one 30 or 2:00 PM Pacific, 5:00 PM Eastern, 2200 UTC Live. TWI t We invite you to join Club Twi if you are not already a member, because that'll give you ad free versions of this show and all the shows we do just $7 a month. You also get access to the Discord, the Twit plus feed, bunch of shows we don't put out in public, like hands on Windows, hands on Mac, the Untitled Linux show the G Fis and Stacy's book Club. And more to come all the time. That Discord is so much fun as well. And by joining Club Twit for seven bucks a month, you also support our forums@twit.community. Those are open to all, not just club members, but you're, but that's the only way we have of monetizing them. Same thing with our mastermind instance, which has grown.
(01:49:13):
Let me just see, the last time I checked it has grown 15000%. I don't even know what 15000% means. That's like a weird number. A 150 times, 150 times. No, I'm sorry, 22791%. So it's, that's, we have 2,518 new users. We're up over 3000 active users now. A lot of people turning to Ma Iton to retreat from Twitter, or at least to prepare a Heidi hole. Should Twitter go go crazy? My suggestion if you want to get on, on Ma on it's finest server that suits you, but if you're a TWI fan, twi.social is is bunch of TWI fans. You have to be a TWI fan to to join it. It's invitation only. Just go there and ask for an invitation and I'm adding about a hundred new people every single day. A hundred to 200 new people every single day.
(01:50:03):
It's, it's pretty wild, but it's fun. And we thank our club Toit members cuz they're the ones who are, who are paying for this sucker <laugh>. It's it's, it's getting a little expensive actually. It's it's up to when I was 15 euros a month until about two weeks ago. Then the Elon takes over Twitter and now I'm paying 350 bucks a month. It went up a, that's a few thousand percent <laugh>. All right, Steve, have a wonderful week. I know we'll be watching the TV in a couple of hours. We will to find out what's happening. And I will see you back here next week on security. Now. Righto. Bye. The world is changing rapidly, so rapidly in fact that it's hard to keep up. That's why Mikah Sargant and I, Jason Howell talk with the people Macon and breaking the tech news on Tech News Weekly every Thursday. They know these stories better than anyone, so why not get them to talk about it in their own words? Subscribe to Tech News Weekly and you won't miss a beat every thursday@twit.tv.
... (01:51:11):
It's security now.