Security Now 951 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte & Steve Gibson (00:00:00):
It's time for security. Now Steve Gibson is here. What happened when Montana tried to ban TikTok? What's eus Cyber Resilience Act and how good lucky are we to have csa? And then the way the EU is about to break browser security for everyone worldwide. Steve explains it all. Next on Security Now, podcasts you love from people you trust. This is tweet.
(00:00:36):
This is Security now with Steve Gibson, episode 951, recorded Tuesday, December 5th, 2023. Revisiting browser Trust. Security now is brought to you by Finked Canary. Detect attackers on your network while avoiding irritating false alarms. Get the alerts that matter for 10% off and a 60 day money back guarantee. Go to Canary tools slash twit and enter the Code TWIT and the how did you Hear About Us Box and by Vanta, automate compliance and streamline security reviews with the leading trust management platform. Join 6,000 fast growing companies like Chili Piper Patch, an Autodesk that use Vanta to manage risk and prove security in real time. You can try vanta free for seven days by going to vanta.com/security. Now, no cost or obligation. It's time for security. Now, the show, we cover the latest news about security, what's going on on the internet with this guy right here. Who knows All sees all tells all Mr.
(00:01:44):
Livelong and Prosper. Steve Gibson. Hi Steve. Yo Leo, welcome back from your week long retreat. We missed you last week, aunt held down the fort. Thank you for the tribute you did. That was very sweet. Well, it's funny because no major topic occurred and when I looked at the previous week's episode, that was ethernet turned 50, and I had received a notice from my phone saying, Hey, Leo's about to have an event. It was my birthday was the 29th, so yeah, yeah. And so what was funny too was that my calendar didn't have your year of birth, so I didn't know which number this was. So I went to Wikipedia and of course it knew and it said 66, so I put all the, I know. Well, no, it said 66 on Monday the day before Tuesday, right? And so I forgot to add one.
(00:02:39):
So I produced the show notes I had, the title was Leo tur 66. Woo-hoo, I wish and email out to everyone. And I quickly got a note from John saying, Steve Leo's been 66 all year, a whole year. I was like, oh crap. That's right. I need to add one. Anyway, I really appreciate, I quickly fixed everything. And anyway, we had a great show. We had one piece that the Ant was great for was one of our listeners asked about my technical suggestions for how to block his third very most technical savvy of all three kids from any access to the internet. And my answer was, forget about it. Don't try. This is a problem that requires parenting, not firewalls. And anyway, so we had a good time talking about that. I'm going to drag our listeners one final time. I hope it's final through the issue of what the EU is planning to do because two notable industry people weighed in last week.
(00:03:59):
Actually the second of these two had shared some statistics about the distribution of certificate authorities, which is sort of astonishing. So today's title is Revisiting Browser Trust. I think everyone's going to find it interesting. If not, by the time you get there, you'll be exhausted anyway. So you could just say, okay, I don't want to hear Gibson talk about this anymore, but there are a couple important new pieces of information that I think are going to be useful. But before we get to that, we're going to answer some questions. How can masked domain owners be unmasked? What new and very useful feature has WhatsApp just added? How did Iranian hackers compromise multiple US water facilities across multiple states? Recently, how did Montana successfully, oh no, I'm sorry. Did Montana successfully ban all use of TikTok statewide and has that even possible? How many Android devices are RCS equipped now?
(00:05:08):
What's the eus Cyber Resilience Act all about? And is it good or bad? Is ransomware finally beginning to lose steam? What's the deal with all these new top level DNS domains? Do they make any sense? Has CSSA been listening to this podcast or have they just been paying attention to the same things we have? What's up with France's Ban on All Foreign, literally in quotes, foreign messaging apps? And did the Prime Minister's nephew come up with an alternative? And as I said, I want to share two final insights from independent industry veterans regarding the eus. I mean, this is like all but happened at this point, signed behind doors, new legislation to forcibly require our browsers and operating systems to trust any certificate signed by their member countries. And of course, I know I have a lot of commentary at the end about how I just, well, we'll get there. And of course we have a pretty funny picture of the week, so I think that's a great podcast for our listeners. I would expect nothing less.
(00:06:30):
Wow, I think I can see the next free GRC program as a program that rips those certificates out at the roots from your browser. I mean, seriously, we're going to need that, Steve boy, just unbelievable. Anyway, let's, we'll get to the show in a second. Our show today brought to you by this, oh, I sent my canary to get refreshed. I sent it back so I can't show you. It's just about the size of an external hard drive, like one of those USB hard drives. But it is super cool because it ain't no hard drive. It is a honeypot and it is the cleverest thing ever. Look, here's the problem. You've got great security, right? You've got all the defenses up, but what do you do if, I don't know, 23 and me or Marriott or LastPass or hundreds of other companies, you've been breached and there's a person running around on your network, you can't see 'em, you don't know they're there.
(00:07:38):
They're doing infinite damage. They're in, what do you do about it? On average, companies don't find out about a breach for 91 days. That's 91 days of damage that somebody can do. So the solution is a honeypot, something inside the network that looks so juicy, so wonderful, so beautiful that the bad guy can't help but say, oh, let me get into there. That's what I really need. Everyone knows honeypots are a good idea, and you'd wonder, well, why doesn't everybody run them? Well, it's simple because with all our network problems, nobody needs one more machine to administer and worry about. And how do you know if your honeypots secure? Right? Did you do it right? If you're not Bill Cheswick, maybe not. So we know the benefits honeypots can bring, but the cost and effort of deployment has always dropped honeypots at the bottom of the list of things to do, not anymore.
(00:08:35):
Now you can get a Thinked Canary, which is designed with rock solid security. Okay? So these guys have been spending the last decade teaching private industry and governments how to crack into systems. They are the best in the business, and they designed the canary to be absolutely secure, but to look like something super valuable, you can deploy 'em in minutes. Even on complex networks, no admin problems from your point of view. You can make your canary look like anything from a Sonology Nest to a SCADA device to Linux server, windows server. You can have it all the services turned on like a Christmas tree, or you could just have a few special little lights turned on, and the triggers are simple. If someone accesses your canary tries to log in, or by the way, I didn't mention, you can also set little trip wires, lure files, PDFs, docs XLS files all over your network.
(00:09:36):
If somebody tries to open one of those, or brute forcing your, let's say fake, I dunno, SSH Server Canary will use a very simple, uncomplicated, high quality marker of trouble on your network. It sends you an email, a text, you get to choose slog. It supports webhooks. They've got an API. You get to choose how you get notified. You can get a phone call if you want, but the point is, when you get that notification, that's not a false positive. There is somebody in your network, and I mean, wouldn't you like to know? There's no point hiding your head in the sand. If somebody's in your network, you darn well better find out as quick as possible. That's what the canary does. You choose a profile for your canary. It could be a brand name router. It could be almost anything. If you want, you can further tweak the services your canary runs.
(00:10:27):
You could have a specific IAS version for instance. Or you could say, I want to use open SSH or it's very flexible. You register your canary with a hosted console for monitoring and notifications. Then you wait. If your network secure like ours has been, it's quiet because it's a canary in the coal mine, right? You don't want it to be chirping unless there's a reason the minute attackers have breached your network. Or by the way, this works with malicious insiders too. You got Larry in accounting who says, I bet you if I could download that Excel file that has all the payroll information, I could do something with that. But the minute he touches it, you get a notification, you'll be alerted. If you want to know how much love there is for the canary, go to the website, Canary Tools slash Love, and you'll see why some of the biggest names, some of the top CISOs, some of the people you will know, love these canaries on all seven continents, by the way, which tells you something. Deploy your birds, forget about 'em. They'll remain silent until they're needed. Get one alert. It's again, email, text, oh, it works with Slack. Lift that one out. Visit Canary tools slash twi.
(00:11:50):
People always say, well, what's the price? What's this going to cost? I'll give you an example. A big operation you might have hundreds. A small company like ours might have a half a dozen for five canaries you're going to get for $7,500 a year, you get five canaries, your own hosted console, all the upgrades, all the support, all the maintenance. Use the code twit in the how did you hear about Us Box for 10% off forever, for as long as you continue to subscribe, right? Thinks Canary adds incomparable value. I mean, this is the best way to do a honeypot, but if for any reason you're unhappy, you can return your Canaries. You have two months to do this. It's a 60 day money back guarantee for a full refund. That's a lot of confidence, right? They said, we know you're going to like it.
(00:12:34):
So if you don't let us know. But I have to tell you, in all the years canary's been running ads on security now. Now, but not one person has ever returned it. There's a zero return rate. It's pretty amazing. Visit Canary tools slash twit. That's how you get your Canaries Canary tools slash twit, C-A-N-A-R-Y. And don't forget to use that offer Code twit and the how did you hear about Us Box for 10% off for life. Great product. Really great product A must have. Thank you. Thanks for your support. Now let's get jiggy with our picture of the week.
(00:13:13):
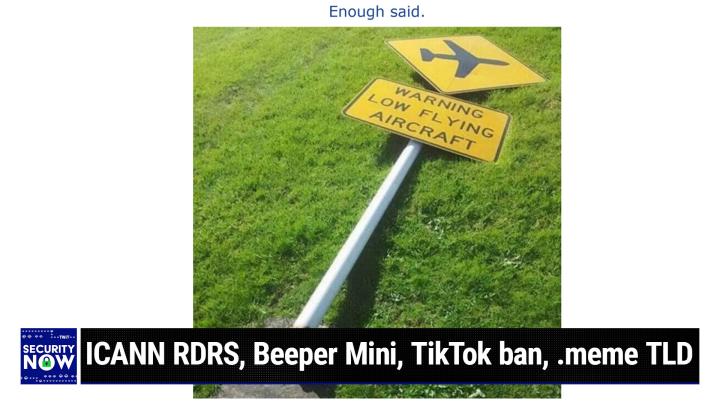
What are you laughing at? You want me to show it? I'm looking at the picture. Oh, you're waiting. Oh, okay. Let me get the camera back on me and I'm going to show the picture the week. Should I show the world at the same time? Oh, sure. It's just so good. Okay, here we go. Okay. That is funny. Well, you described this, Steve. So what Leo is laughing at, and I have to say, when I looked at it again this morning when I was selecting from among the archive, I did, I burst out laughing. It's just so perfect.
(00:13:54):
It is a sign that says, and it's a real authentic sign that in a yellow rectangle says Warning Lowlying aircraft, and it's got then a diamond above it showing a picture, sort of an iconic picture of an aircraft. Yeah, you funny. Well, this is so obviously near an airport. I mean, you see this. Yeah, I was thinking that. Where would you encounter a sign that's warning you of low flying aircraft? Small airport. Small plane airport. You definitely see, yeah. Anyway, what's so funny about this is the sign has been knocked over. So you can see it's broken off at the base and it's lying on the grass because the presumption is low flying aircraft. The low flying aircraft. Got it. Anyway, that's as low as you can go. It's on the grass. Yeah, it's just so good. That's hysterical. It makes me love humanity even more. Last week we had one where there was a sign in front of an escalator that had some yellow warning tape across it, and it said, this escalator is refusing to escalate.
(00:15:06):
I love people with a sense of humor. That's awesome. That's great. And actually, someone tweeted me and he said, okay, that's dumb. An escalator is the one piece of equipment which is still useful even when it's broken. Well, that's a good point. And a set of stairs not quite as good, but it still works. And of course, liability and all that. You couldn't do that Anyway. Okay, so one of the things that always was always chafing while I was with Network Solutions, which I'm very loyal, I started with them in the beginning. They were your registrar for grc grc.com on day one, my domain was at Network Solutions. They were the guys, they were the big kahuna. They may have been the only kahuna back in those days. But what really chafed was the idea of, and this of course came along later, the idea of my needing to pay them additional money annually even to redact the domain registration listings they themselves had created for IAS Internets who is database queries.
(00:16:23):
The original idea behind domain registration was that for it to be public, right? I mean this whole thing was this, we're all one big happy Globe worldwide network and this is all going to be wonderful. And so the people who registered domain names should be public. But it wasn't long before spammers and scammers were scraping the public domain registration, who is database for information and abusing it in every way imaginable. So it soon became prudent to have that data masked and masking services appeared. Then the domain registrars themselves began offering this extra service with many seeing the provision of this masking as of course, another revenue opportunity. So just one of the many reasons I'm so glad that I left Network Solutions and moved over to Hover who has been, if they're not still a sponsor of the TWI network, they're good and they still do free who is privacy, right?
(00:17:30):
Exactly. And I went back to make sure that that was the case. So that's the way it should be. Okay. Now in the EU with GDPR, things are somewhat different now, as we know, GDPR has had its pluses and minuses. One of the minuses we all now experience every day is the pervasive annoyance of every website being forced to waive its cookie policies in our faces and obtain our acknowledgement and consent. On the flip side, one of the pluses is that the GDPR includes a stringent data protection law that has forced domain registrars to redact information on owners from their publicly available who is databases. This information is still present on domain in the private databases of domain registrars, which they have to have that in order to maintain the domain. And it has historically been made available to some organizations, but usually on a very limited fashion, like under court order or responding to subpoenas or following intelligence sharing arrangements and agreements of some sort.
(00:18:47):
Okay, I'm bringing this all up today because last Tuesday, ICAN announced a new facility to improve the current situation for those such as in law enforcement who have a legitimate need to obtain access to otherwise redacted domain ownership information. So with a bit of editing, here's what ICAN said. They wrote the internet corporation for assigned names and numbers. That's what ICAN stands for. I-C-A-N-N has launched the registration data request service RDRS. The RDRS is a new service that introduces a more consistent and standardized format to handle requests for access to non-public registration data related to generic top level domains. gtld personal data protection laws now require many ICAN accredited registrars to redact the personal data from public records that was previously available in their WHO as databases with no one way to request or access such data. It can be difficult for interested parties to get the information they need.
(00:20:04):
The RDRS helps by providing a simple and standardized process to make these types of requests. The RDRS can be an important resource for ICAN accredited registrars and those who have a legitimate interest in non-public data like law enforcement, intellectual property professionals, consumer protection advocates, cybersecurity professionals, and government officials. The RDRS is a free global one-stop Stop, one shop ticketing system that handles non-public TLD registration data requests. The RDRS connects requestors of non-public data with the relevant ICAN accredited registrars for TLD domain names that are participating in the service. The system will streamline and standardize the process for submitting and receiving a request through a single platform. The service does not guarantee access to requested registration data. All communication and data disclosure between the registrars and Requestors takes place outside of the system by utilizing a single platform and request form. RDRS provides a consistent and standardized format for handling non-public TLD registration data requests.
(00:21:28):
This simplifies the process for Requestors by automatically identifying the correct registrar for a domain name and preventing the need to complete multiple forms with varying sets of required information managed by different registrars. The service also provides a centralized platform where requesters can conveniently access pending and past requests. They also have the ability to create new requests, develop request templates, and cancel requests when needed. Finally, registrars can benefit from using the service as it provides a mechanism to manage and track all non-public data requests in a single location. Registrars can receive automated alerts anytime a request is submitted to them. The use of a standardized request form also makes it easier for the correct information and supporting documents to be provided to evaluate a request. So to me, this seems like it has been a long time coming and it makes so much sense today. There are so many shenanigans going on with internet domain names that abusers of the system need to know that their ability to hide is being reduced and legitimate domain owners should have a reasonable expectation of privacy.
(00:22:50):
So the idea of having the who is databases not all public yet, still creating a uniform less hassle full means of obtaining that non-public data across registrars who all have their own ways of doing things. To me, the idea of standardizing this process for obtaining the information makes a lot of sense and seems like a long missing piece that's finally being provided. So props to I can for this. Yay. I think that works due to the strength of Facebook. Metas WhatsApp, as we know, is the world's number one most used, most popular messaging app. And last Thursday, WhatsApp announced a significant new feature which was missing when they announced something earlier in May known as chat lock. Okay, first, here's what they announced on May 15th under the headline chat lock, making your most intimate conversations even more private, they said, our passion is to find new ways to help keep your messages private and secure.
(00:24:13):
Today we're excited to bring to you a new feature we're calling Chat Lock, which lets you protect your most intimate conversations behind one more layer of security. Now, right off, I think that sounds like a great idea, and we'll look at why they think so. They said locking a chat takes that thread out of the inbox and puts it behind its own folder. That could only be accessed with your device, password, or biometric like a fingerprint. It also automatically hides the contents of that chat in notifications too. We think this feature will be great for people who have reason to share their phones from time to time with a family member or those moments where someone else is holding your phone at the exact moment. An extra special chat arrives. You can lock a chat by tapping the name of a one-to-one or Group and selecting the lock option.
(00:25:10):
To reveal these chats slowly pull down on your inbox and enter your phone password or biometric. Over the next few months, we're going to be adding more options for chat lock, including locking for companion devices and creating a custom password for your chats so that you can use a unique password different from the one you use for your phone. And it is that last feature that I had on my mind the whole time I was reading the foregoing. It was like, well, that's nice that you're going to move this out of the inbox and you're going to give it its own place to live, but then you're going to allow the same phone password or biometric to unlock it. That's not optimal to me. That's not, or I should say maximal. And for this, the whole point is to obtain something maximal. So what they announced last week was they said earlier this year we rolled out chat lock to help people protect their more sensitive conversations.
(00:26:15):
Today we're we're launching Secret Code, an additional way to protect those chats and make them harder to find. If someone has access to your phone or you share your phone with someone else with Secret Code, you'll now be able to set a unique password different from what you use to unlock your phone to give your locked chats an extra layer of privacy. You'll have the option to hide the Locked Chats folder from your chat list so that they can only be discovered by typing your secret code in the search bar. They've just done this whole thing exactly right. If that doesn't suit your needs, you can still choose to have them appear in your chat list. Whenever there's a new chat which you want to lock, you can now long press to lock it rather than visiting the chats settings. We're so happy our community has been loving Chat Lock and hope that Secret Code makes it even more useful to them.
(00:27:15):
Secret code starts rolling out today, and in the coming months, we'll be available globally. We're excited to keep bringing more function to Chat lock to help people protect their privacy. Let us know what you think. Anyway, as I have been saying, I think it makes total sense and I predict it will become a heavily used feature from a privacy and security standpoint. It makes sense for our devices to have multiple layers and levels of protection. We need to have more than just a device being locked or unlocked that's no longer sufficient, or at least certainly not for all possible use cases. And that's what this is. This is allowing what's apt to be extended to, and I don't think that using the same password or biometric, as I said, makes sense for an inner level of protection. Locking enhanced layers of privacy behind something makes I think the most sense. So Bravo to meta for doing this.
(00:28:20):
Okay. I said recently that one of the broad changes to the way we've always done things must somehow be the elimination of any initial default password from our devices. My first thought was to require the user to set a password themselves while preventing them from setting it to password or Monkey 1 23 by also embedding some minimal complexity requirements. But I don't think that's the right solution. I think the right answer is to have the device randomly assign a strong password when it's initially set up, and that's it. The user needs to write it down. Period. We've been talking for years about the need to be using strong passwords that we cannot recall, that needs to apply to equipment as well as websites. So here's the news that brought me back to this train of thought. Hello to this. The US government has confirmed that an Iranian hacking group named Cyber Avengers, where the A VEI know of is actually a numeral three.
(00:29:43):
Okay? We know they're 12-year-old boys now. Go ahead. Yes. Cyber Avengers, right? Okay. And actually, Leo, you're right, because a 12-year-old could do this, they've gained access to the equipment at water facilities across multiple US states, CISA, the FBI, the NSA, and other agencies say the attacks began around November 22nd. Jesus I know. And exploited PLCs, programmable logic controllers that we've spoken to many times in the past manufactured by the Israeli company, NICs, the group targeted TROs PLCs that were still using the default password. 1 1 1 1. Oh my goodness. That's absurd. And that's our water supply. I know. God, it's unfreaking believable. So last week, CSA asked us organizations to please change the default password, enable multifactor authentication, and remove the devices from the internet. Gee, what a concept US officials say the Cyber Avengers Group is affiliated with the IRGC, an Iranian Military and Intelligence Organization.
(00:31:11):
Maybe they're their kids. According to the Shadow Server Foundation, between 500 and 800 TROs PLCs are currently exposed to the internet. And lemme just say that you almost, you probably have absolutely no actual business purpose for connecting A PLC to the internet. It runs equipment in factories well, and obviously water systems, but who needs to hook it to the internet? Okay, 66 were identified in Australia, 52 in Singapore, 42 in Switzerland. So those are the top three. Australia, Singapore, Switzerland, 37 are known to be in the United States, and apparently they've all been hacked and they're all controlling our water supply. Then following up is Estonia and Spain, both with 31, and then it continues to dwindle down the list like pretty much everybody has one. Every country, unlike web servers, PLC systems, as I said, typically have no need to be exposed to the internet doing so.
(00:32:27):
If you actually had to do that, it should require jumping through some real hoops. Under no circumstances should a device be produced where both has a well-known default password all set to 1 1 1 1 in the factory, and is also exposing any interface protected by that default password to the internet. In today's world, designing and selling such systems is really nothing short of irresponsible. We've talked in the past about countries becoming proactive in scanning their own internet address space with an eye toward getting ahead of attackers and cleaning up some of these issues. This is the sort of thing that CISA in the US ought to be considering, because in cisa, I'm increasingly impressed by them. We finally have a proactively useful cybersecurity entity. Yeah, Chris Krebs was great when he ran it. He's a smart guy. Yeah, they're on the ball. Yeah. I'm not surprised. So I think Retcon five in our chat room said it's simple.
(00:33:41):
You just change it to 2, 2, 2 2 and next year, 3, 3, 3, 3. That's good. Yeah. I mean, at least it would. At least the kitties rotating the script kitties would not be able to get to you. Unbelievable. Unbelievable. Oh my God. Okay, so a while back, we covered the news that a bunch of states were enacting legislation to block the use of TikTok on government devices within their jurisdictions. Doing that was likely within their power, but the state of Montana wanted to go further and get this LEO outright ban all use of the TikTok service statewide. Okay. Now, from a purely technical standpoint, this would be somewhat tricky. Since network boundaries and state borders are not currently aligned since there's never been any need to align them, but now it appears that it might not matter about that after a recent federal ruling, which occurred just last Thursday.
(00:34:51):
NPRs coverage of this also provides some interesting background, so I want to share it. They wrote, A federal judge has blocked a law in Montana that sought to ban TikTok across the state, delivering a blow to an unprecedented attempt to completely restrict a single app within a state's borders. The ruling, which came on Thursday, means that Montana's TikTok ban, which was set to go into effect on January 1st, has now been temporarily halted US district Judge Donald Malloy said Montana's TikTok ban oversteps state power and likely violates the first amendment. Malloy wrote that though officials in Montana have defended the law as an attempt to protect consumers in the state, there is little doubt that Montana's legislature and Attorney General were more interested in targeting China's ostensible role in TikTok than with protecting Montana consumers. Montana as a state does not have authority over foreign affairs, Malloy said, but even still, he found the national security case presented against TikTok unconvincing writing that if anything, the Montana law had a pervasive undertone of anti-Chinese sentiment.
(00:36:21):
The ruling is preliminary with a final determination to be made following a trial expected sometime next year. TikTok, which has more than 150 million American users, has for years been under intense scrutiny over fears that its Beijing based parent company by dance would hand over sensitive user data to Chinese authorities, or that Beijing would use the app as a propaganda tool, even though there's no public proof that either has ever happened. Although several states and federal governments have prohibited the app from being downloaded on government devices, Montana was the first state to pass an outright ban of the app. Some critics have accused it of government overreach in May. TikTok sued the state over the law arguing that it amounts to an illegal suppression of free speech. Lawyers for TikTok argued that the national security threat raised by officials in Montana was never supported by any evidence.
(00:37:20):
Malloy government. The judge overseeing the case was skeptical of the ban. In an October hearing on the lawsuit, he pointed out that TikTok users voluntarily provide their personal data despite state officials suggesting the app was stealing the data of users. He said, state officials justified the Montana ban under a paternalistic argument. As Washington continues to debate, tiktoks future states have been acting faster, and the law in Montana was considered an important test case of whether a state level ban of an app would survive. Court challenges backing the Montana law were 18, primarily Republican led states that were eyeing similar bans of TikTok. Aside from legal hurdles to implementing such laws, cybersecurity experts have raised questions of how from a technical standpoint, such a ban would even be possible. Right? Count me in that group, those pesky technical details, which keep tripping up. The legislators who believe that they can simply have any magical technology that they demand.
(00:38:34):
And then, anyway, NPR concludes. President Trump clamped down on TikTok and attempted to outlaw the app, but his efforts were twice struck down in the courts. National security experts say TikTok is caught in the middle of escalating geopolitical tensions between the US and China. As Washington grows ever more concerned about the advancement of Chinese tech like semiconductors and the country's investments in artificial intelligence, supporters of restricting or banning TikTok in the US point to Chinese national security laws that compel private companies to turn information over to Beijing authorities. They also point to bite dance tiktoks corporate owner. It admitted in December that it had fired four employees, two of whom worked in China, who had improperly accessed data on two journalists in an attempt to identify a company employee who leaked a damaging internal report. Now, I'll just say that by no means am I defending TikTok, but let's not forget that many domestic companies, as well as many of our own US law enforcement agents, we've covered these issues in the past, have also been caught with their hands in the cookie jar.
(00:39:51):
It appears that access to personal and private data is quite tempting, so it's not just Chinese misbehavior. Oh, and finally, this is significant too. TikTok says, China based employees no longer have access to US user data under a new firewall. It is put in place with the help of Oracle, with this change dubbed project Texas, after Oracle moved its corporate headquarters to Austin, all American's data will be stored on servers owned and maintained by Oracle with additional oversight from independent auditors. So it seems clear that TikTok is obviously, well, we know that TikTok is obviously an extremely successful and valuable service. It seems to me that they're making every effort to legitimately assuage concerns of secret Chinese influence. And of course, today's social media is all about influence, but such influence is as pervasive over with Facebook and X as it is anywhere else. That's the problem. It's very selective enforcement. I mean, it's all crap.
(00:41:05):
How do you pick one out? It's all propaganda. It's all lies. And as you and I know very well, if the Chinese government wants information about US citizens, they just go to a data broker. It's cheap, right? And in fact, there's some, oh, it's Senator Ron Wy. Widens smart. He's good. Yes, he's smart. He's threatened to stop the appointment of somebody, I don't remember whom, until the NSA answers questions about whether it's been purchasing this private data about US citizens. They've been really hedging their responses to that question, which tells me, of course they are. Right? Otherwise, they just say no. And by the way, that's why Congress will never pass a law against data brokers because law enforcement and our three letter agencies are saying, you can't do that. We need that information. Yeah. Yeah. Sad. Yeah. Okay. So just a quick note. RCS is now enabled on more than 1 billion Android devices.
(00:42:16):
We recently noted Apple's announcement that they would be upgrading their non iMessage messaging of which is currently using SMS and sorry, hiccuped, which is currently using SMS and MMS to RCS. So it was noteworthy that last Thursday, Google announced that its RCS messaging system is now enabled on more than 1 billion Android devices. So it appears that Android users will be ready once Apple joins them with RCS next year. And as I said, I will be quite happy to have a better messaging experience with any members of my little otherwise iOS group who have an Android forced the whole group down to SMS. It's be really nice to have the RCS features, which looks like it's pretty much at parody largely with iMessage, so that's great. Well, and this will cross your desk later today, and I'm sure you'll want to talk about it next week, but Beeper has just announced this.
(00:43:22):
Maybe you heard us talking about it on Mac Break Weekly, this new program, beeper Mini that basically they jailbreaked an iPhone and reverse engineered the protocols to use to log into the iPhone servers. So you are able now on an Android device to use messages legally and be a blue bubble and all of that. Now, what do you mean legally there is a carve out in the DMCA, apparently, I didn't know this, Jason Snell explained it. That allows you to reverse engineer this particular kind of thing, so it wasn't illegal to reverse engineer it. Furthermore, and this is what I wonder, and I would love to hear your thoughts on it, is speculated that Apple can't stop this without breaking their own authentication servers. So they're kind of over a barrel because if they attempt somehow to prevent this login, now, I don't know that I wouldn't be surprised if Apple has some secret way of doing this. A fingerprint. Yeah, I You'd have to have a pseudo iPhone in order to connect to their servers, right? I mean, yeah, I don't know. It works. You're right. It's two bucks a month.
(00:44:39):
I'm curious. What we said is I wouldn't subscribe for a year, and it just happened this morning, beeper mini Wow. It goes on. Androids gives you full parody. It's basically using iMessage on and Android logging in with an Apple account and it's open source and they, well, at least the Python part is Oh, logging in with an Apple account. Yeah, yeah, yeah, yeah. You're using your Apple account and going through the servers. The question is, I've got to think Apple has some sort of fingerprint. How could they not know it's not an iPhone? But I don't know. We'll see. Maybe they just never needed to worry about it because they figured no one could break in. How could you do this? It's a proprietary protocol, right? And then furthermore, there's no man in the middle. It is effectively you as using this software like you would use messages on an iPhone encrypted direct.
(00:45:35):
I mean, it's very interesting, and Apple may or may not have a technical ability to feed it, but if they do, then there's the secondary question of would they, given that it would certainly raise the ire of regulators all over the place, because that is certainly in any competitive move to say, no, no, you can't have this. Especially if there's a carve out that says it's possible to reverse protocol. So if it's legal, even if Apple could block it, would they? Is the question That's a fascinating subject. You'll be talking about this, I'm sure. Yeah, so I guess their concern would be that having a non iPhone endpoint, running iMessage protocol is inherently insecure, right? So that will be, if they do break it, they will say, no, no, we're protecting your security because Android devices are inherently insecure and should not be allowed on our network in this way.
(00:46:32):
That's probably not the case, but that would be their, I guarantee you that'll be the verbiage. Oh no, we're just protecting the network, the integrity. It's the same verbiage at and t used in Carter phone when they said, no, you can't put any non at t devices on our phone network. That would break it. Boy, I remember those days. Wow, you had to rent a phone from MA be, and of course the Carter phone decision, a Supreme Court decision overturned that and changed the world. So it's as always in this business we're in interesting times. It also did lower the quality of telephones. Well, that's true. Remember those old at t sets? You could run over them with a truck. The Western Electric? Yeah. They were made like a hard rubber.
(00:47:17):
They were tough. Yeah. I think it was bake light. I think it might've been bake light in the early days for sure. Yeah. And then a steel base plate. I mean, they were really built. The 5 0 1 was the model number of that classic phone. The mic pickups were carbon. Yes. And sometimes they get clumpy, so you'd bang it. Yep. We sound like two old children. Old men. Yes. Children. Back in the day, you would bang, if it started to sound bad, you'd bang your phone and it would fix it. Dad, you're making that up. No, it's true. Break loose the carbon granules, right? Oh God. Okay. So much as I'm becoming, as we're going to hear later, increasingly annoyed with the EU over their move to commandeer, our web browser's, well-established system of trust. It appears that the eus European Council in Parliament have reached a useful agreement known as the Cyber Resilience Act.
(00:48:22):
This is a piece of legislation designed to improve the security of smart devices sold within the European Union. The new regulation, it will take three years to come into effect, but God bless 'em. This is a good thing. This new regulation applies to products ranging from baby monitors and smart watches to firewalls and routers. Under the new rules, vendors must establish processes to receive reports about vulnerabilities and must support products for at least five years. Moreover, products will be required to come with free and automatic security updates as the default option. They must ensure confidentiality using encryption, and vendors must inform authorities of any attacks. This won't be happening immediately. As I said, the requirements set by the new rules will come into effect three years after the Cyber Resilience Act is formally voted on the EU Parliament floor, given the requirements, which will likely require some redesign and new infrastructure to support them, that seems reasonable to me, at least in this regard.
(00:49:37):
The EU is finally leading in the direction we need to be heading and not backwards as they are unfortunately with browser security. But so this is really cool. This says that connected consumer devices three years from the time they sign this into law, which is imminent, will be required to auto update by default, which means all of the consumers who have heretofore not been protected and are running routers and firewalls and everything else, baby monitors with extremely obsolete firmware, we'll get five years of support including automatic updates to them. So yay, the forensics industry is getting better at tracking cryptocurrency flows and cyber insurance firms are being more forthcoming about what they're seeing. So we know more now than we have previously. For example, one of the newer Upper Echelon ransomware groups we've referred to before is known as Black Basta. This gang is believed to have netted more than $107 million in ransom payments since it first appeared and began operations early last year.
(00:51:07):
Those who watched this have believed that it was emerged from the ashes of Conti after Conti shut down since we're closing out 2023, and it emerged for the first time early last year. That's $107 million in less than two years time that $107 million represents payments made by more than 99 0 victims of the get this 329 organizations known to have been hit by the gang. Okay, so there's 365 and a quarter days in the year, yet in less than two years, 329 individual organizations were breached by this group. So on average, that's about one every other day a breach every other day. The largest payment observed was $9 million, while the average ransom payment is 1.2 million times 90. So this is according to a joint research published by the blockchain tracking company elliptic and the cyber insurance provider, Corvus Insurance. Now, unfortunately, what this shows is that there is a great deal of money to be made through cyber extortion, which is really what this all boils down to.
(00:52:46):
And the hostile governments, or in this case government, since this group is known to be operating out of Russia, harboring these criminals are more than happy to turn a blind eye. This means that a great deal of pressure will continue to be placed on the security of our networks and systems. And unfortunately, as the last few months of many very serious large weaknesses and compromises have continued to show our networks and systems are not up to the challenge. Years of laxity in the design operation configuration and administration of these systems is catching up with us. We know that thanks to the internet or well, thanks to the inherent inertia, which works against change, we're not going to fix these endemic problems all at once, but they're never going to get fixed at all if we don't apply constant effort in that direction. And I have some good news to that effect here in a minute.
(00:53:52):
I did want to mention that Google is offering a new meme top level domain for N who wants to play with meme related internet properties and to observe that it's difficult to keep up with all of the new TLDs which are appearing. And it does feel as though this aspect of the Internet's original design, which is to say the original concept of a hierarchy of DNS domains anchored by just a few major classifications, is not evolving that well. There are companies that attempt to snatch up their existing.com second level domain names in every one of the other top level domains, presumably to preserve their brand and their trademark. But that's certainly not in keeping with the spirit of creating additional DNS hierarchies for future growth. I have no interest in grc.meme and GRC zip would've caused all kinds of confusion. What is that GRCs an a entire website in a zip archive?
(00:55:06):
Yeah. Who knows? Although I think GRC meme might be kind of fun. Well, while you were telling us about Canary Do Tools, I thought, well, there's a perfect good use of a good use of one of the newer TLDs. I'm sure that canary.com was taken decades ago, so that wasn't available. I use a email domain, TLD for my email. I have a variety of domains that I use for email that are, you can't get a good.com anymore. They're gone. It's true. Yeah, it's true. Yeah. Okay. Speaking of cis, A-C-I-S-A, last Wednesday, they introduced a new series of publications called Be Still My Heart Secure by Design with its first alert titled How Software Manufacturers Can Shield Web Management Interfaces from Malicious Cyber Activity. And if I didn't know as I do that anyone who's focused on security would naturally come up with the same thoughts, I would think that they'd been listening to this podcast, get a load of what's in this first document, and it's short. So CSA writes, malicious cyber actors continue to find and exploit vulnerabilities in web management interfaces. Newsflash in response, software manufacturers continue to ask why customers did not harden their products to avoid such incidents. Like what do you mean you left the default set to 1, 1, 1, 1? That's crazy.
(00:57:04):
Who would do that? CISA says, secure by design means that software manufacturers build their products in a way that reasonably protects against malicious cyber actors successfully exploiting vulnerabilities in their products. Baking in this risk mitigation in turn, reduces the burden of cybersecurity on customers. Exploitation of vulnerabilities in web management interfaces continues to cause significant harm to organizations around the world, but can be avoided at scale. CISA urges software manufacturers to learn from ongoing malicious cyber activity against web management interfaces by reviewing the principles below. And again, they're quoting this podcast recently. Principle one, take ownership of customer security outcomes. And actually, there was only one principle that, one, take ownership of customer security outcomes. They said, this principle focuses on key areas where software manufacturers should invest in security, application hardening, application features, and default settings. When designing these areas, software manufacturers should examine the default settings of their products.
(00:58:34):
For instance, if it is a known best practice to shield the system from the public internet, do not rely on customers to do so. Oh, again, thank you. Thank you. Yes. Because we know customers aren't going to do it. They're not. Apparently they plugged it in and left it set to 1, 1, 1, 1. Exactly. God. They said rather have the product itself enforce security best practices. Yes. Examples include, and we have three bullet points disabling the product's web interface by default. Oh, yes. Thank God. This is in print and including a loosening guide that lists the risks in both technical and non-technical language. Right. Make it very simple for Johnny that come with making changes to the default configurations. Two, configuring the product so that it does not operate while in a oh look, does not operate while in a vulnerable state, such as when the product is directly exposed to the internet.
(00:59:53):
Third, warning, the administrator that changing the default behavior may introduce significant risk to the organization. Okay, now look, think about that. This is a complete reception of the way everything is done today. Yay for csa. I love this principle. Take ownership of customer security outcomes. That's exactly right. Don't let, it's your job. It's not their job. Right, which is a complete turnabout. Yes, they said, they said Additionally, software manufacturers should conduct field tests to understand how their customers deploy products in their unique environments and where their customers are deploying products in unsafe ways. This practice will help bridge the gap between developer expectations and actual customer usage of the product. Field tests will help identifying ways to build the product so customers will securely use it. And finally, furthermore, software manufacturers should consistently enforce authentication throughout their product, especially on critical interfaces such as administrator portals.
(01:01:15):
So wow. Amen to all of that. Now, as I said, none of these concepts will come as news to the listeners of this podcast, but it would be great if those manufacturers to whom CISA is addressing this alert would immediately take heed. We know it's going to take time for any such change to work their way through the entire supply chain from drawing board into final deployment. It would've been nice if we could have started that secure by design process 10 years ago, but we haven't even fully started it today. The fact that this alert has been published with what it says is a very good sign. I suspect that this may be the first step toward beginning to hold the designers of these systems accountable for their default security. Unfortunately, due to the hold harmless nature of software and equipment licensing agreements, accountability, as we've discussed before, is difficult to create.
(01:02:26):
I intentionally dislike the idea of having government criminalize insecure design. That's a slippery slope. That's not far from what the EU is planning to do with their E-I-D-A-S 2.0 web certificate overreach legislation and technology rarely make great bedfellows, but one of the ways we've seen government influence things for the better is by using its own purchasing power to create voluntary incentives with cisa. The US government finally has a highly effective and worthwhile cybersecurity agency based upon what CISA just published last Wednesday. That thing I just read, it would not be a stretch to imagine adding exactly those default network behavior requirements to any future software and equipment purchasing made by state and federal government agencies that would affect voluntary change. Overnight vendors will be required to legally attest that their equipment abides by this new set of requirements, and if it was later found not to be true, then they could be held liable for damages resulting from the functional out of spec behavior of their equipment.
(01:03:52):
And just to be clear, not for bugs in their systems, but for the deliberate design of those systems. As I've repeatedly observed, anybody can make a mistake, but vendors can and should be held responsible for their policies and design is a policy. So yay to csa. Okay, last one before we take our break and then get into our topic is, this one is really interesting and it led me down a path I didn't expect. While we're on the subject of things governments do also. Last Wednesday, France's government announced a near immediate ban, as in 10 days from last Wednesday, on the use of what they called foreign end-to-end encrypted messaging apps. That's so French, that's France, that's France for you. They've banned government officials from using foreign encrypted messaging services, including specifically Telegram, signal, and WhatsApp.
(01:05:09):
The government is notifying its ministers and their cabinet staff. What do they got that they must uninstall any such applications from their devices? By this coming Friday, December 8th, French officials have been told to use the French developed alternative messenger known as vid, O-L-V-I-D official. If it's not French, it's not good. Must be French officials cited privacy risks and the need to quote advance towards greater French technological sovereignty. May we quote. Okay, so what the heck is vid? Even though we've never talked about it here. I have to say that it looks pretty good. Good. It's both open source. Well, it is open source for both Android, iOS, Mac, oss, and Windows, and it's living over on GitHub. Oh, well, that's fine. Here's how it describes itself. Vid is a private and secure end-to-end encrypted messenger. Contrary to most other messaging applications, VID does not rely on a central directory to connect users, and there is no user directory. Vid does not require access to your contacts and can function without any personal information. The absence of directory also prevents unsolicited messages and spam because of this. From a security standpoint, vid is not yet another secure messenger. It's LA French tech.
(01:06:56):
Wow. Okay. Vid guarantees the total and definitive confidentiality of exchanges relying solely on the mutual trust of interlocutors. This implies that your privacy does not depend on the integrity of some server. This makes vid very different from other messengers that typically rely on some trusted third party, like a centralized database of users or a public blockchain. Note that this doesn't mean that AVID uses no servers. It does. It means that you do not have to trust them. Your privacy is insured by cryptographic protocols running on the client side on your device, and these protocols assume that the servers were compromised from day one. Even then your privacy is insured. Okay, so this is less loony than it might seem at first, though it does have some feeling of nationalism and protectionism with the French government labeling everything else foreign and talking about the need to increase France's technological sovereignty.
(01:08:10):
But that said, all of it is not some random homegrown messaging app designed by the prime minister's nephew. That's exactly what it sounds like, right? That you'd expect, oh no, this is safe, my nephew says. So I've not had time to look at it closely, but it looks like the real deal. And the more I look at it, the more I like it. Over on Ovid's website, which is OL v.io, they proudly note that Ovid does not require any personal data. No phone number. That's nice. No email, no name, no surname, no address, no date of birth, no nothing. That's one of the things that bugs me about signal. I don't like that. Yes. Yeah, I completely agree. Unlike your previous messenger, Ovid will never request access to your address book. So those are some compelling features. And under the headline, compatible with what you already have, they say Ovid is available for your Mac, OS and Windows computers, as well as your iPhones, iPads, Android, smartphones and tablets. No sim, no problem. No SIM card required. wifi is all you need. Since Ovid needs no phone number to work, you can use any of your devices and they'll stay in sync. Ovid even works in an emulator. Geeks will love it. So Ovid uses something known as SaaS based authentication. Of course, Leo, you'd expect them to be sassy, them being French. Yes, French.
(01:09:56):
This SAS stands for short authenticated strings. The concept of SAS was produced and formalized in a 311 page PhD thesis by, of course, a French cryptographer, Sylvain Pacini back in 2009. So here's what Pacini explained in the first two paragraphs of his PhD thesis. He said, our main motivation is to design more user-friendly security protocols. Indeed, if the use of the protocol is tedious, most users will not behave correctly, and consequently, security issues occur. As an example, you are not behaving correctly. You must go convert to the beginning stop. An example is the actual behavior of a user in front of an SSH certificate validation. While this task is of utmost importance, about 99% of SSH users accept the received certificate without checking it. Designing more user-friendly protocols may be difficult since the security should not decrease. At the same time, interestingly, insecure channels coexist with channels ensuring authentication.
(01:11:27):
In practice, these ladders may be used for a string comparison or a string copy, for example, by voice over IP spelling. The shorter the authenticated string is the less human interaction the protocol requires, and the more user-friendly the protocol is. This leads to the notion of SAS based cryptography, where SAS stands for short authenticated string. Finally, in the first part of this thesis, we analyze and propose optimal SAS based message authentication protocols. By using these protocols, we show how to construct optimal SAS based authenticated key agreements. Such a protocol enables any group of users to agree on a shared secret. Key. SaaS based cryptography requires no pres shared key, no trusted third party, and no public key infrastructure. However, it requires the user to exchange a short SaaS, for example, just five decimal digits. By using the just agreed secret key, the group can now achieve a secure communication based on symmetric cryptography.
(01:13:01):
And yes, Leo five digits. All it takes since 2009, this SaaS proposal first outlined by this guy's PhD, has received a great deal of further scrutiny within the security community and it has held up 100%. So this works by having the users at each end initially discover each other by sharing the short tokens being displayed on each other's devices. That's a little hardship because I'd have to tell you what that pre shared key is somehow over a secondary channel, right? Yes. And that's exactly the case. So for that, some form of already authenticated out of band channel is used like an audio or a video call to exchange the information that each user's device presents. And this simple process has been proven, as I said, to be cryptographically sound, but notice also this eliminates spam completely. Right? Good. It's over. Yeah. So I also really like the fact that it's got integration with a desktop.
(01:14:15):
That's something I've been missing as a cross platform, iOS and Windows user. And as you said, LEO Signal is annoying with its required tie to a phone number, signal claims that's needed to prevent spam, but with vid, there's no possibility of being spam. Yeah. People know my phone number. That does not prevent spam at all. Right. Right. And we also, as we covered, I think it was you maybe been with AMP when we talked about the breakdown of signal's cost structure, I think that was, yeah, I was here with you before you left. That telephone authentication is a huge percentage of signal's total annual outlay, because verifying those phone numbers is very expensive. So a real world out of band interaction is required to establish a channel between two participants or among the participants in a group. After that, the devices remain linked for further communication. So what pays for this? The system runs on a freemium model, all bi-directional text messaging and incoming audio. Encrypted audio is free. You get unlimited messages, unlimited attachments, secure group discussions, unsend and edit messages, remote deletion, ephemeral messages, multiple profiles, user mention, markdown, Ovid web, whatever that is, and inbound secure audio calls. The system is financially supported at a five euros per month level. Those by those who want to be able to initiate secure voice calls as well as use Ovid on multiple devices that receive all messages and keep themselves cross synchronized.
(01:16:25):
Yeah, so it's only free if you limit yourself to text messages, but for there it really is. There are also more powerful enterprise plans that have much more features. It's interesting that the French government is telling their ministers and cabinet staff that they must switch to Ovid since only text messaging is completely free. So one wonders, who's going to pay they to the French public? Congratulations. There is an enterprise classification. So presumably France government would act as an enterprise and then would make all of their individual government employees subscribers underneath that one umbrella policy. If I'm Mr. Vid, I'm going to give it to 'em free. This is the best publicity you could ask for. I know, right? I mean, yes. Yeah. Yes. Anyway, so I wanted to make sure that all of our listeners were aware that it existed. I was installing it. Right now, it may suit many people's needs.
(01:17:32):
Yes. Cross platform desktop for Mac and Windows. I'm sure it runs under wine and there's probably a way to get it running underneath. Well, if there's web, there's a web version, which there is. You just do it on the web and that's, yeah, that's straightforward. vd.io. Yeah. Yeah, I'm installing it right now. It looks good. The one negative is that they give you a backup key because it will do encrypted backups, but you can't cut and paste it. So I have to type in this very long 32 letter and number backup key, but I'm typing it in, right? Or just take a picture of it with your other phone. Oh, aren't you smart? You must be Steve Gibson. I know you. No, this is cool. You know what my name is, I should be using vid. But the problem is, as with all these messaging systems, you have to get other people to use it.
(01:18:26):
I mean, that's the problem. And I don't know anybody who uses all fit so much for that. Alright, let's take a little break, come back, we will talk some more and you're going to tell us some good deep stuff about certificates, but first word, French episode. Can I do this whole show? Lexi, would you mind Vanta? A growing business likely means growing threats and more tools, more third party vendors, data sharing. Oh, that's always risky, right? Way more risk. Vanta was founded in 2018 after several high profile data breaches, and of course since 2018, the last intervening five years online security has become kind of job one for a lot of businesses. Vanta understands firsthand how hard it is for fast growing companies to invest the time and staffing to build a solid security foundation. Vanta was inspired by a vision to restore trust in internet businesses by enabling companies to improve and prove their security.
(01:19:43):
So Vanta brings your GRC and security efforts together under one roof. Integrate information from multiple systems, reduce risks to your business and your brand all without the need for additional staffing. You like that? And because Vanta automates up to 90% of the work for your compliance for SOC two and ISO 2 7 0 0 1 and more, of course you can focus on strategy and security and not worry about maintaining compliance. G two loves Vanta year after year. Just check out some of the honest customer reviews on G two from business leaders, this one from a chief technology officer, there is no doubt about Vanta ass effect on building trust with our customers. As we look more with Vanta, we can provide more information to our current and potential customers about how committed we are to information security and Vanta is at the heart of it. Customers need this.
(01:20:39):
They need that. Reinsurance partners too, head of quality assurance and customer support says Vanta is the best in automated compliance monitoring. Join 6,000 fast growing companies like Chili, Piper, patch and Autodesk that use Vanta to manage risk and prove security in real time. You can try vanta free for seven days. Go to vanta V-A-N-T-A vanta.com/security now. Okay, I'll give you a free seven day trial. You can check it out VA nta.com/security Now, no cost, no obligation, and I think it pays, it'll really pay for you to check this out. vanta.com/security Now. We thank so much for supporting Steve and the show, Mr. Gibson. Okay, so we've been covering the news of the now impending EU E-I-D-A-S 2.0 legislation. I know mostly from the standpoint of the two open letters that those in the industry and academia have authored and co-signed, and of course by those in the industry and academia, I mean a number now totally more than 500 individuals who are truly concerned about what the EU is about to unilaterally place into law.
(01:21:57):
Four weeks ago. This podcast was titled Article 45. So I understand that we've already talked about this, but I just encountered, as I mentioned earlier, two new pieces of commentary from two well-placed technologists. So I decided to share their appraisals to create some what it would really mean to the world perspective. And there are a couple of surprises. The first person's name is Ivan Ick. I was immediately curious when I saw that Ivan had chosen to weigh in and address this issue. I know his name well, if Ivan's name doesn't immediately jump out and mean anything to you, you may know his well-known website and service SSL labs for as long as I can remember, Ivan's SS l labs. It's just SSL A B s.com has been the go-to site for checking the security at both the server and browser ends of secured connections. Ivan is also the author of two books, Bulletproof, TLS and PKI, understanding and employing SSL slash TLS and PKI to Secure Servers and Web Applications.
(01:23:09):
Its first edition was published nearly 10 years ago in 2014, and the book is now in its second print edition with added coverage of TLS 1.3. It's also available as an ebook. Ivan's second book is the open SSL cookbook, the Definitive Guide to the most useful command line features that anybody who's ever looked at open SSL knows that a command line reference would be a good thing to have. Anyway, that one's in his third edition also available for free. He and his wife Joanna, are based in London. His piece, which he wrote last Thursday, and if all of that preceding didn't give you the idea, this guy understands authentication and certificates and SSL and TLS, and he's been at this for a long time. His piece is titled European Union Presses Ahead with Article 45. So Ivan wrote, the European Union continues on its path to E-I-D-A-S 2.0, which includes the controversial Article 45 that basically tells browsers which certificate authorities to trust E-I-D-A-S, which stands for Electronic Identification and Trust Services is a framework aimed at regulating electronic transactions.
(01:24:28):
As part of this proposal, the EU wants to support embedding identities in website certificates. In essence, the goal is to bring back extended validation certificates, browsers, of course, don't want that, but the real problem is the fact that with the legal text as it is at the moment in its near final form, and I'll just mention that this is what was signed behind closed doors, the EU gets the final say in which certificate authorities are trusted. I mean, that's the crux of this and we have a lot more to say about that. But he says the global security community has been fighting against Article 45 for more than two years now. We wrote about it on a couple of occasions. As of November, 2023, the European Council and Parliament have reached a provisional agreement. The next step is for the law to be put to the vote, which is usually a formality in November ahead of the crucial vote.
(01:25:32):
The campaign intensified with browser providers, Google, Mozilla, civil society groups, EFF and other companies, and more than 500 security experts voicing their concerns. In the end, it did not help the bureaucrats drafted the text and voted behind closed doors with little acknowledgement of the protests. And therein lies the main problem. The EU doesn't understand the global technical community internet standards are developed collaboratively and organically with careful deliberation of the details. The eu, on the other hand, prefers a top-down approach that ignores the details and apparently involves no debate. They expect everyone to trust that the details will turn out all right, the text voted on, was published only after the fact. The EU might have the right to govern its territory, but when it comes to these global matters, it also has a duty to respect and compromise with the rest of the world. Above all, care must be taken to separate technology and politics as much as possible.
(01:26:50):
After all, it took the world a very long time to achieve reasonable security of global website authentication. A decade ago, we were witnessing hackers breaking into cass and government agencies issuing certificates for Google Properties. Today we have much stricter issuance and security standards, and we also have certificate transparency, which provides visibility and auditing. No one knows what's going to happen with that and the EU doesn't engage. Where are we now? The EU wants browsers to display legal identities embedded in the qualified certificates, but it also wants to control who issues them. It so happens that the same certificates are used to store the identities and authenticate websites. It's not at all clear if the EU cares about the latter part. In fact, the following statement appears in the recitals, in the provisional agreement. The obligation of recognition, interoperability, and support of quacks is not to affect the freedom of web browser providers to ensure web security domain authentication and the encryption of web traffic in the manner with which the technology they consider most appropriate.
(01:28:15):
So he writes, can browsers recognize and show legal identities from the EU approved cas, but continue to require full compliance with current technical standards in order to fully trust qualified certificates? Or can browsers require two certificates, one for TLS and the other for identities like Mozilla proposed a year ago? We'll need to wait and see. So that's what Ivan wrote, who's way been around the block and paved a bunch of the block. The second piece, which Ryan Hurst wrote a little over two weeks ago is titled E-I-D-A-S 2.0 Provisional Agreement Implications for Web Browsers and Digital Certificate Trust. And here's where some really interesting numbers come up.
(01:29:10):
It goes, what Ryan wrote goes further than anything I've seen so far to provide an assortment of interesting facts to clarify the way things are today, and to examine what the eus proposed changes would mean to the industry and to the world. He leads with a summary writing. This document contains my notes on the problematic elements of the provisional agreement on the EU E-I-D-A-S 2.0 legislation reached by EU legislators on November 8th. So six main points. Mandatory trust in EU approved certificate authorities. Browsers will be required to trust certificate authorities approved by each European member state. This could lead to scenarios where the government forces the trust of cas that put global users at risk. Two, lower standards for EU approved certificate authorities establishes a lower standard for European cas limiting the browser's ability to protect users from underperforming EU certificate authorities, third EU to override browser trust decisions.
(01:30:30):
In cases where an EU investigation does not lead to the withdrawal of a certificate's qualified status, the EU can request browsers to end precautionary measures, forcing them to trust the associated ca. And why would that be in there? I mean, that's just like asking for for a fight. Number four establishes global precedent for further undermining encryption on the web. When a liberal democracy establishes this kind of control over technology on the web, despite its consequences, it lays the groundwork for more authoritarian governments to follow suit with impunity. Next, browsers are forced to promote legal identity for authentication of websites. Browsers will be required to have a user interface to support the display of legal identity associated with a website potentially reversing previous design choices made based on user behavior and research, and I'll come back to this point later, but what gives the EU any authority over the design of third party browsers over which they have no say?
(01:31:53):
And lastly, the inconsistencies of recitals with the substantive legal text. The recitals in the legal text have ambiguities and contradictions, which will cause long-term negative consequences for the web. In other words, the recitals were put in in order to try to soften what the legal text says, but of course, the legal text is what's binding. Okay, so Ryan explains, the text says browsers must either directly or indirectly take a dependency on the EU trust list to determine if a CA is trusted for website authentication. This is a list of cass as determined by each member state to be in conformance with the legal obligations under E-I-D-A-S. He says, to put this into context, based on the currently authorized organizations on this list, we can expect to see 43 new organizations added to both the Mozilla and Chrome root stores. This is just a number though. Let's give it a little color. And Leo, there's a chart here at the bottom of conveniently numbered page 13.
(01:33:19):
He says, today, there are seven organizations in the web, PKI, that are responsible for 99% of all certificate issuance. That's astonishing. Once again, let me say that. Seven organizations, seven certificate authorities, seven certificate signers. Those seven are collectively responsible for 99. Actually, I think it's 99.36 if I recall, percent of all certificate issuance. So this chart has this big, huge blue region. Yeah. Who's internet security research group? That's almost half. And that's let's encrypt. That's encrypt. Oh, I love you. Let's encrypt. Good for you. Wow, that's great. Isn't that astonishing? Oh my gosh. Let's, encrypt has 46.52% of all currently non expired web certificates. That's really awesome. In circulation. That's what I use for my website. Yep. Love it. Well, I'm still with number two, but number two has about half of that. And that's of course DigiCert dig. Yeah, and they're very good. Yeah, they're my favorite.
(01:34:43):
They are still my they're They're expensive. They're not cheap. They're more expensive than others. That's true. Yeah, though what you get in turn is a higher level of assurance. Inherently, let's encrypt is only a domain validator. That's all it's able to do, although it is able to do that for free. And as we can see from this pie chart, that's what half of the internet is using today. Wow. 46.52%. So what astonishes me though is that, so we have DigiCert at 22.19 sec Tigo, half of that. That is half of DigiCert at 11.89. Google Trust Services is at 8.88. Surprising actually followed by GoDaddy. Yeah, that's who we use at 5.77. Microsoft Corp has 3.45 and then iden trusts commercial root ca is down at 0.63. So if you sum all of those, those are the top seven, and you could almost argue that you don't need that last 0.63.
(01:35:58):
But if you include that in order to get to 99.32%, those seven cas alone give you coverage of 99.32%, which says you're only missing a bare 0.63% in all the others. The hundreds of others, Leo only account total for 0.63%. So this should bring everyone up short. This means that the industry in the guise of the CA browser forum has been incredibly permissive about extending our global browser trust to organizations whom we really have very little actual need to trust. Yet today, we're inherently trusting the certificate, the signatures of certificates that most of us are never going to see. And of course, the great controversy is that any of them could sign the certificate for any domain they wanted to, and a browser would trust it because we trust anything that any of them sign. So that suggests to me that we're going in the wrong direction here by even the idea of adding anymore. It's like, what? No, we can survive with seven whose iden trusts don't. That's a good question. I don't know whose certificate. They're small. They're signing. Yeah. And why isn't Verisign on this list? Yeah, that's surprising. Good question. Yeah, I love it. That let's encrypt is so dominant. I mean, is that okay? People who come to our site do not look at the certificate and say, oh, it's GoDaddy not. And by the way, that saved us hundreds of dollars.
(01:38:08):
I mean, so yeah, DigiCert is the gold standard, but I don't think our users really care. And frankly, if Let's Encrypt had existed 10 years ago, the pie chart would not look like this. I agree. It's going to be 99% soon enough, and in 10 years it won't look like this. So, okay, here's what Ryan has to say about this. He writes, there are between 75 and 85 organizations in the various root programs constituting the entire web, PKI that can issue certificates for the entire web if we use the higher estimate of 85. So that's like all the rest, which includes these seven. So those other 82 have just microscopic shares, right? He says, if we use the higher estimate of 85, and the reason is an estimate is like he says between 75 85 is like those last 10. It's like they signed Monkey Moose and one, their certificate expired. I mean just like nothing Monkey Moose, I want that one. That's a good one.
(01:39:26):
And by the time this podcast is over, somebody will have registered it. So he says, if we use the higher estimate of 85, the addition of the EUS 43 member countries represents an increase of over 50% in the number of organizations that are trusted for doing what they're doing. And they don't have to abide by anybody's rules. The EU says, you must trust these. He says, Ryan says, why is all this significant? While it's true that there are numerous Cass in the web, PKI, beyond the seven mission critical ones, each additional ca represents an increased surface area for all users of the web. The long tail cas, those lesser relied upon entities are part of the web PKI, because they ostensibly meet the same objective technical and procedural standards as their more prominent counterparts. So in other words, we all trust all of those essentially unneeded cas because the way the system has evolved, it would be considered rude not to give anyone the benefit of the doubt and trust their work signing certificates until and unless they give the world reasonable cause not to.
(01:41:00):
However, it's also likely that with the ISGs let's encrypt having changed the rules, no one in their right mind today would attempt to establish a new commercial certificate authority. That would be nuts. Given today's startling distribution of signed web certificates, my feeling is that we ought to be running in the exact opposite direction. Then what the EU proposes, if I didn't trust at 0.63 was also eliminated. Presumably also with minimal impact, we could reduce CA trust to just six well-proven certificate authorities. That sure seems like the future as opposed to adding 43 new and highly politicized political trust roots. So Ryan continues writing web browsers, set these standards to participate in their programs, striving for objectivity, openness, and consistency. This approach not only keeps the web open and fosters the development of sovereign digital capabilities in various countries, but also involves a balancing act mitigating the risks associated with the expanded attack surface that each new ca introduces what the EU proposes, tips the scales of this system by lowering the bar for European cas, allowing them to meet a lower standard while at the same time putting these governments in charge of which Cas meet the bar.
(01:42:42):
I know such a terrible place to put it is we can't allow this to happen. He says, to put this in context, consider this case in 2013 where a French agency that was allowed into the web PKI was caught minting SSL certificates that impersonated major sites like Google. Putting 27 governments in a position to add more cas that are trusted by the world means they can do this at scale if they decide to do so. Oh my God. Or an attacker uses these government's ability to do so for their own benefit. That's a good point. That's a good point. If an attacker gets in and gets the root certificate, all hell breaks loose. Yep. Overnight. It's worth noting that the browsers distrusted this ca when it did this. In this new world that won't be possible.
(01:43:49):
Now consider for a moment that there are 195 sovereign nations in this world. For now, the 27 member states of the EU will be the only countries in the world with the ability to force browsers to trust arbitrary Cass like this or to add their pet features. How long Ryan asks do we think that will last if browsers become compliant with this new legislation? He linked to an article which appeared in ours Technica 10 years ago in 2013. In what I read above, I was pleased to see that this podcast had covered every one of those incidents cited, and I'll just skimm it over here because for example, there was the trust wave was discussed. And also remember this, the Netherlands based Digi Notar, Digi Notar, I do, I know you'll remember Digi Notar. So there have been several other instances in addition to this cyber defense agency that have been caught in the past.
(01:45:02):
And the good news is browsers are immediately able to blacklist the hashes of those known fraudulent certs and then yank the trust from the root. The French legislation prevents that. I mean, it's hard to believe it does. He says, okay, so, and of course, now we know that we only really need to trust six or seven cas to obtain trust coverage of 99.32% of the entire web. So next, Ryan makes the point in the eus legislation says, requires browsers to have a user interface to support the display of legal identity associated with a website. He writes, extended validation certificates once used by about nine to 10% of websites now represent only about 3.8% of all certificates on the web. And one wonders once they expire, if they'll be renewed as ev, because as we know, browsers no longer show anything special.
(01:46:15):
Web PKI. Cass originally marketed these tools for increasing conversion rates among other supposed benefits, meaning more consumer belief in the value of the site. But there was never any data supporting these claims. Over time, it became apparent that they provided little to no value and in some cases even harmed users. A notable example of the confusion arising from this paradigm is a case where a security researcher demonstrated the ability to quickly and inexpensively a legitimate company with a name conflicting, with a well-known organization without needing to reveal the identity. Okay, so for those interested, the researcher was a guy named Ian Carroll. Ian filed the necessary paperwork to incorporate a business called Stripe Inc. And he did this in a different state than where the actual stripe in was incorporated, which is perfectly legal. Legal, yeah. He then used the legal entity to apply for and receive an EV certificate to authenticate the website, stripe.ian.sh.
(01:47:40):
But of course, Ian was unable to get stripe.com because the real stripe owned that domain. But creating a stripe.com subdomain or a stripe subdomain under his own Ian SH domain was sufficient. This was because at the height of EV certificate usage, the domain's EV certificate details would be shown instead of that messy http URL. Oh my god. So what visitors to Ian's demo site saw was simply Stripe, Inc. And I'll note, oh boy. Yep. And I'll note that this followed three months after a different researcher named James Burton established a valid business entity verified identity to demonstrate how the resulting EV certificate might be used to add an air of authenticity to a scam site. So you go to the scam site, the certificate says identity verified. Oh, it must be legit. That's right. That's clever Devi. The bottom line. Yes. The bottom line was that since typical users don't actually have any idea what's going on, all of this extra specialness was abandoned, or as Ryan puts it, this incident along with several others and research based on large scale analysis of user reliance on browser trust indicators led to the de-emphasis of all these affordances in the browser ui.
(01:49:23):
The previous ui, which highlighted this information was redesigned and demoted in the visual hierarchy, setting it on a path for a likely eventual removal as a result, which is where we are today, but the legislation that is poised to become law in the EU after years of the industry warning against all of this in the strongest possible terms requires browsers, literally is enforcing the design of browsers to bring this back and for the EU to be able to add their own identity assertions to the browser's location bar display. This is horrible. It's Leo. It's unbelievable. It's breaking security. Yes, it is. Another point of security of serious concern is that the eus forthcoming legislation explicitly and deliberately limits the ability of browsers to protect users from poor performing EU certificate authorities.
(01:50:35):
They're forced to accept the certificate even if they know these guys are BSOs. Correct? Correct. It is no exaggeration to say that we depend upon our browsers to have our backs in countless way. Ryan writes this today, CAS are removed as trusted for a vast range of reasons. For example, last year, and I checked this out, it was in 2022, a Turkish certificate authority TUGRA demonstrated they lacked the most basic security practices and could not effectively respond to a security incident and were distrusted as a result, not due to having made any mistake, but because their service was clearly shown to be unconscionably insecure. When I dug into this Leo, their web portal had never changed the default admin login credentials, admin, admin of a certificate authority. But that's why this system works because the browsers and say, yeah, we're revoking that ca. Yes, Ryan writes, under this new legislation, browsers will no longer have the ability to distrust European cas that are trusted for quacks except for breaches and loss of integrity of an identified certificate, whatever that means.
(01:52:11):
Each of the CAS trusted within the web PKI represents a risk to users. This is why it is so important that browsers acting as the agents of their users are empowered to establish uniform criteria to ensure all the cas meet minimum best practices and have the ability to remove them when those minimum best practices are not met. The text reduces the cases substantially in which they may do that and he says, unfortunately it gets worse. He then cites some legislation that will take effect. And so the legislation reads, web browsers may take precautionary measures related to a certificate or set of certificates in case of substantiated concerns related to breaches of security or loss of integrity of an identified certificate. When such measures are taken, the browsers must notify their concerns in writing without undue delay along qui with a quill pen. Oh my God, yes.
(01:53:18):
Piece of parchment along with a description of the measures taken to mitigate those concerns, this notification should be made to the commission, the competent supervisory authority, the entity to whom the certificate was issued, and the qualified trust service provider that issued the certificate or set of certificates. Upon receipt of such notification, the competent supervisory authority is expected to issue an acknowledgement of receipt to the web browser in question. We have received your missive. Oh my gosh. And shall respond. Did anyone ever see, what was it? Brazil I think was the movie. It's totally Brazil. Yes. Oh my God, bureaucracy. Submit your form in triplicate B stroke 7, 9, 3 5. Wow. So anyway, the legislation contains language such as shall not be subject to any mandatory requirements other than the requirements laid down earlier and shall not take any measure contrary to their obligations set out In Article 45 referring to the browsers again, the EU is flatly asserting absolute authority over the trust that browsers will place in any certificates issued by their member states.
(01:54:48):
And the text also says that even in the cases where there are breaches of security or loss of integrity of an identified certificate, the EU can override the browsers and force them to trust the associated ca anyway. When the outcome of an investigation does not result in the withdrawal of the qualified status of the certificate or certificates, the supervisory authority shall inform the web browser accordingly and request it to put an end to the precautionary measures referred to. In other words, there is no other way to look at this Leo. Other than that, they are absolutely getting into business. They have no business getting into shocking. The more time I've spent looking into this, the worse it seems. The world has spent a great deal of time slowly and carefully evolving an equitable system of trust, and now for essentially commercial like ego reasons to force the display of website digital identity through the equivalent of their own system of EV certs.
(01:56:03):
This legislation would force all web browsers to accept root certificates from every EU member state, which would then use them to assert the identity of anything they choose. And there's nothing any browser can do about it. What I'm most wondering now is what gives the EU the right to dictate the operation of our web browsers? To me, this seems like uncharted waters. Users currently have some say over the certificates which populate their root stores if they wish to remove trust from some certificate authority. Nothing prevents them us from doing so, but the EU is stating that browsers will be required to honor these new unproven and untested certificate authorities and thus any certificates they issue without exception and without recourse. Does that mean that my instance of Firefox will be legally bound to refuse my attempt to remove those certificates? If the EU wants to create their own EU browser based upon a fork of chromium, embellish it with their own certificates and a user interface display of whatever those certificates wish to assert, then require that their own citizens use it.
(01:57:32):
The only people who would have any problem with that would be their own citizens who could then decide whether they want to keep those legislators in office. To me, that appears to be the only feasible course of action. What's completely unclear and what I haven't encountered anywhere is an explanation of the authority by which the EU imagines it's able to dictate the design of other organizations' software because that's what this comes down to. The EU tried to do this, the UK tried to do this as we know with end-to-end encryption. Every last publisher of that technology said no. And the UK blinked Edge and Chrome on Windows obtained their root stores from Windows. So the EU is telling Microsoft that they must add and unilaterally trust 43 new root certificates to their operating system's root. And what about Linux? Who's going to make Linux do this?
(01:58:38):
Good luck sneaking this past. That's never going to happen. Yeah, because the OSS stores, in fact, most of the time your OSS is the root. Firefox is the only exception. And in a weird thing that you missed last week, Leo Firefox one 20 just added a new option to include the Windows root certificates into its own root store. But that's optional, right? And that's optional. Yes. It could be turned off. And of course, and really there's the very real specter of what other doors this opens. If the EU shows the rest of the world, then it can successfully dictate the terms of trust for the independent web browsers used by its citizens. What other countries will follow with similar laws? Now everyone gets to simply require that their own countries certificates get added. This takes us in exactly the wrong direction. That's crazy. None of this is good, and it's not even as if there's some actual problem that needs to be solved here.
(01:59:50):
Leo, someone just invented this over in the eu. It's just crazy. The more I think about this, the more I like the idea of disabling firefox's, newly added trust, the certs in the underlying operating systems root store option. Then pruning all but six of firefox's current root certificates that trusts 99% of the internet certificates and likely 100% of any certificates that I would choose to trust. Well, when are we going to get the Steve Gibson prune your CA's app? Because how easy would it be to prune out all the CA's? Definitely doable. You could list them and have check boxes next to 'em. You could have your recommended six. Press a button, somebody. The good news is this is generic enough that somebody will do it by the next podcast. Yeah, Paul, if they weren't all doing advent of code right now, maybe they interesting.
(02:01:02):
Wow. Did you miss, is that the week you missed? I missed it. I mean, it's not over. It's all months. But if you don't start on day one, you're, it ramps up. So you're just going to skip it this year. Well, I'm not going to do it in real time. I'll probably get around to doing it. Honestly, I'm not really in the mood to sit down. You're altered. Yes. You have an altered state of basically I want to go out and hug a tree and that's it. That's it. So, wow. This is hair on fire bad. I'm very glad you covered it. Yeah, it's astonishing. But the funny thing, it's trivial to prune these out. It's not illegal even in the eu, right? Probably not. As we know, the problem is all the people who won't prune it, and that's who the browsers are worried about, is they're wanting to protect everybody.
(02:01:56):
Normal people won't, only the listeners of this show will know what to do. Yeah. So can the EU outlaw the use of a browser unless it complies? I mean by what authority do they dictate the operation? That's interesting of software they don't control. So if Firefox says, and I hope they do, if the Mozilla group says, no, we're not going to do it, then what? Can they ban it EU wide? No. Maybe they could. They could fine. I guess the EU Hass done some good things. I have to say, absent a US government that's willing to protect our privacy, it's good that the EU is, yep. GDPR does have some privacy centric things. They've done some dopey stuff. This cookie thing just drives me crazy. The cookie banner, oh my God, it's so meaningless. And how many billions of human hours are lost clicking that thing?
(02:02:59):
And now this, I don't know. I mean, what's worth somebody who doesn't, who's just like laissez-faire like the US government is, do whatever you want, or somebody who does some good things and some bad things, I think, I don't know. Wow. Well, thank goodness you're here because I appreciate you're covering this. Steve's website is grc.com. Of course, not governance, whatever that Relevance. Relevance and compliance. No. Gibson research corporation.com. That is where you'll get valid drive, which is a must have for anybody who's buying USB thumb drives, or I guess even USB drives. The bad guys are everywhere. And so many other wonderful things, including spin, right? The world's best mass storage, maintenance and recovery utility, which is currently version six. You didn't release it while I was gone, did you? I didn't, but I'll have an announcement next week. Okay. You'll get a free upgrade though, so don't hesitate.
(02:04:02):
If you buy it now, you get a free upgrade@grc.com. Anybody who has drives of any kind mass storage of any kind should have that can also, there's lots of other free stuff he does. It's really a wonderful site. Plus, of course, that's where he puts his versions of the podcast. Now he has the normal 64 Kilobit audio that we have as well, but he also has a 16 Kilobit audio file, which is all scratchy. Sounds like Thomas Edison, but it's lightweight and that's the reason for it, because then Elaine Ferris, who's I guess on dial up still can download it at our Horse Ranch and transcribe it. So that's the other unique version Steve has is a very nicely done transcript, not ai, a human doing it. So you can get that there. These are all free by the way, grc.com. You can leave feedback at grrc.com/feedback on X.
(02:04:55):
He's at SG grc. Let me put that up so that people can note that down so that you can DMM him there. His dms are open on x.com, and there's forums, by the way, at grc.com, which are a great place to communicate with not only Steve, but other Steve Fidos. We have on our website the audio of course, and the video of this show, TWIT tv slash ssn for Get It Security. Now, there's also a YouTube channel dedicated to it, and the best thing honestly to do is subscribe in your favorite podcast client, because that way you'll just download it automatically. Now, actually, I should say Apples and some others, if you don't listen to every episode, stop downloading it. So if you really want a collection of episodes, so you can, I mean, most people want the full set. We recommend Pocket Casts where you can say, and there's a box.
(02:05:47):
They download it and it'll download 'em automatically whether you listen or not. And then eventually you'll get around to it. I know you'll, let's see, what else? Oh, if you're not a member of Club Twit, can I beg you? Can I plead with you to join it? We need your support. Badly. Twit has, I'm looking at the stats here, produced 1000 days, five hours and 34 minutes, 47 seconds of content for you. 20,000 plus episodes, and fewer than 2% of you listeners, you nice people pay for it. Now. You pay with your attention in the ads. But wouldn't you like ad free versions? Wouldn't you like to support what we do and keep the lights on here? Because yesterday, Lisa said, oh, just so you know, we're going to lose a million dollars next year more than, and I said, we need to grow the club to survive. So if you're not yet paying seven bucks a month, that's all it is. The first number one reason because you want to keep hearing Steve and all of the stuff we do. Number two, because you get ad free versions of all the shows. You get, shows we don't put out in public. You get access to that wonderful club, Toit Discord. I think we give you a lot of value for your dollar. Go to twit tv slash club twit. We would really appreciate that.
Ad (02:07:12):
Zicam knows that when you live life to the fullest, you never want to let a cold slow you down. With Zy cam's cold shortening products, you can actually shorten colds when taken at the first sign. And with the winter chill in the air, you need the number one cold shortening brand to help shorten a cold when taken at the first sign this season, because you should never let a cold stop you from missing out on your favorite moments of the season. Click here to shop Zy icam, the number one cold shortening brand.
Leo Laporte & Steve Gibson (02:07:42):
Steve, I hope you have a lovely week. Elaine asked me since we're talking about the wonderful, the holidays. Yes. Are we off the 26th and on January 2nd? So there is a best of Jason Howell, our producer will tell me, but there is a best of for this show, and I can only imagine it would be on the 27th is Wednesday the 20th will probably have a show, and the third will have a show. But the 26th is Tuesday, which is, oh yeah, we do the show on Tuesday. When do we do this show, Steve? Yes. The 26th will absolutely be the best of, and we will have. Okay, so that means no transcript for Elaine on. She can take the week off. Righto. And we will do a show the 19th and January 2nd as well. God willing, if the lights still are on and people think I'm joking, but if we're a million dollars short, I don't have a million dollars to put into this. So maybe Steve, I can get your Bitcoin vault. Oh, nevermind.
(02:08:49):
Yes, that's right. We do the show Tuesdays right after Mac Break Weekly, which is about one 30 to 2:00 PM Pacific. Let's say 5:00 PM Eastern Time, 2100, 2200 UTC. Now, that's only if you want to watch it live. Most people don't. If you do want to watch it live, there's two ways that members of Club Tweet can watch in the Discord. We'd stream it live there, and because the Discords live streaming is so wonky, volume's all over the place, it stops. It stopped three times during the show. I mean, it's just terrible. We really need a way for you to stream it. So what we'll do is we'll on youtube.com/twit, we will turn on the live stream when the shows begin. Interstitial stuff, we won't bother, but when the shows are on, there'll be a live stream. If you want to be notified, go to youtube.com/twit. And if I think I'm told my children, tell me if you hit the bell, you'll get a notification when the show starts live stream, so you can watch it live there on YouTube.
(02:09:50):
And I think that's a much better quality. And we'll also help people who listen on or watch on TVs or listen on Amazon Echoes and things like that. Steve, my dear friend, thank you. A pleasure as always. We'll be back next week. I didn't get to any of my mailbag listener feedback because there was just so much people to talk about, and this E DDoS thing is a big deal. It matters. We got to have it on everybody's radar and see, hopefully saner heads prevail somehow. The good thing about civil disobedience digitally is nobody can bonk you on the head. So I'm a fan of That's good. I don't have any padding up there. I'm a fan of civil disobedience on the internet, and I think that's the answer to this. It's the only way, frankly. But I did install Ovid. Thank you, Steve. Have a wonderful week. We'll see you all next time. Steve buddy on security.
Rod Pyle (02:10:49):
Hey, I'm Rod Pyle, editor in Chief VAT Astor magazine. And each week I joined with my co-host to bring you this week in space, the latest and greatest news from the Final Frontier. We talked to NASA chiefs, space scientists, engineers, educators, and artists, and sometimes we just shoot the breeze over what's hot and what's not in space Books and tv, and we do it all for you, our fellow true believers. So whether you're an armchair adventurer or waiting for your turn to grab a slot in Elon's Mars Rocket, join us on this in space and be part of the greatest adventure of all time.
Ad (02:11:29):
Need a winter holiday escape? Forget your cure. In Fiji, white sand, beaches and scuba diving are calling. Your Tropical Paradise Getaway is just one nonstop Fiji Airways flight away with round trip fairs starting at $899 from LAX or SFO. Or check out great fairs to Australia, New Zealand with seamless connections via Fiji book now@fijiairways.com. From here to Happiness Flying Direct with Fiji Airways. Wells Fargo presents one of the surest ways to grow your money. A Wells Fargo CD account where you can earn a 5.0% annual percentage yield on an 11 month term with a minimum opening deposit of $5,000. Visit a Wells Fargo branch or wells fargo.com/cd rates to open a CD account and start growing your savings with Wells Fargo Bank. NA member FDIC.