Security Now 1029 transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show
0:00:00 - Leo Laporte
It's time for security now. Steve Gibson is here. We're going to talk about an Apple research paper that explores whether these new large reasoning models are really doing any thinking. I'll give you a hint they're not. Goodbye to Bill Atkinson. And then what is the Linux Foundation's response to the WordPress kerfuffle? All that and more coming up next on security now. Podcasts you love from people you trust. This is twit. This is security now, with steve gibson, episode 1029, recorded tuesday j, june 10th 2025. The illusion of thinking it's time for security now. The show where we cover your security, privacy and everything else. Frankly, we're going to do AI today with this guy right here. He's the king of the hill as far as security comes. Frankly, as far as geekiness goes, mr Steve Gibson, hello Steve, hello Leo Great Gibson, hello Steve, hello, leo Great to be with you again.
Nothing is more geeky than the clock with the milliseconds behind me now Show everybody.
0:01:12 - Steve Gibson
Let's just take 50 minutes to discuss this Open up.
0:01:17 - Leo Laporte
No, we already did it on MacBreakWeekly.
0:01:18 - Steve Gibson
Show us how it's a clapper. We need to see the clapper.
0:01:20 - Leo Laporte
It's a clapper, it's all this stuff. It's really I think it's very cool.
0:01:24 - Steve Gibson
This is the new clock, so that people because people want a clock behind me for some reason. Yeah, it came yesterday, right? Yeah, what's coming?
0:01:35 - Leo Laporte
tomorrow.
0:01:35 - Steve Gibson
You'll see. Okay, we've got a great episode. There's a something happened with Meta and also Yandex which needs to get some attention, mostly because it's really interesting. We get to do a deep dive. It bears on a lot, as we'll see. Bears on a lot, as we'll see, and that's how we're going to largely start today's podcast. We're going to finish it by looking at some research that Apple's guys did and I don't think this is sour grapes, because you know they kind of missed the AI train this. They did some tests using something other than math, which they argue is not a really good way to measure a reasoning model's ability to reason, because if it's just really good at matching patterns, it could score better than people can, because we're not that good. Anyway, so lots of fun stuff to talk about. We are going to start by, as your programs have Leo remembering somebody.
I've got that for the first page of the show notes, because he was amazing. We're going to talk about this meta-native apps and JavaScript colluding behind their users' backs. The EU has, believe it or not, rolled out their own DNS service, which the good news is it works much better in the EU than it does here in the States. They didn't create it for some guy in Southern California with a benchmark, which is a good thing, because, oh, not good over here. Also, Ukraine DDoSed Russia's railway DNS and we're going to pause on that briefly to say so. The Linux Foundation has created an alternative WordPress package manager, because apparently there's some politics over at WordPress land that created some schisms. Oh, and a court has told OpenAI that they must not delete anyone's chats Anyone's, not just selective people. We're going to dig into that. Also, there is a very bad well depending upon who uses Erlang OTP's SSH library. If you do, hopefully you already know about this 10.0 CVSS.
There's been some questions raised about whether Russia is able to intercept telegram messages. Seems like maybe, which would be a surprise. Messages. Seems like maybe, which would be a surprise. Spain's ISPs blocked Google sites. Whoops, Reddit is suing Anthropic. Twitter's new encrypted DMs are apparently as lame as the old ones were. Also, it seems that the logingov site doesn't have backups.
0:04:41 - Leo Laporte
What could possibly go wrong?
0:04:43 - Steve Gibson
Wow. And then we're going to look at an interesting way that Apple came up with to generate some really good metrics about to what degree this next generation, like the 03 and CLAW 3.7, so-called large not large language models, but large reasoning models are actually reasoning, and whether they're just better at language than reasoning. So I think maybe this time, Leo, for podcast number 1029, we've actually got some interesting stuff to talk about Finally after a thousand podcasts.
0:05:22 - Leo Laporte
We're getting the hang of it. I think, Actually, this Apple paper was a research paper. It's very scientific and deep and I'm really thrilled that you want to dissect it because I need some help. We got charts.
We got charts, charts coming up, charts coming up. Of course, we count on Steve every week, aren't you glad you're here? This is why we're here. Thank you, steve. We'll get right to the meat of it in just a bit, but first a word from our wonderful sponsor. We really appreciate the people who sponsor the show. They make it all happen along with you, club Twit members. Our sponsor for this segment is Hox Hunt, not Fox Hunt, hox H-O-X, hox Hunt.
Look, if you're in your company, you're the security leader. Wow, you have a lot of respect. You get paid to promote and protect your company against cyber attacks. These days, though, that is a tough job. More cyber attacks than ever.
You've got phishing emails and what's worse is now they're using AI. So you can't just say if it looks ungrammatical, throw it out. They all look very real, which means your legacy one-size-fits-all training awareness programs don't really stand a chance. They send at most four generic trainings a year. Most employees go oh, this again and ignore them and learn nothing. This again and ignore them and learn nothing. When somebody actually clicks on one of these fake emails, they're forced into embarrassing training programs. That really honestly, if you've ever done it, you know they feel like punishment. You're being punished and no one learns if they're being punished. That's why more and more organizations are trying Hoxhunt.
Hoxhunt is so cool. I had a great conversation with them. Basically, they've gamified this training right. It goes well beyond security awareness. It actually changes how people behave and it does it by doing something humans really dig, rewarding good clicks and coaching away the bad. If you see it at work, you can actually see it at the website.
Hoxhuntcom security. Now you'll really get this. When an employee suspects an email might be a scam, they click a button. Hawkshunt will tell them right away. Hey, nice job, you found it, providing a dopamine rush that gets your people not to be more suspicious but more kind of paying attention and and motivated to click and learn and, of course, protect your company, which is what you really need as an admin. You'll love it because hawks hunt makes it easy to automatically deliver phishing simulations across not just email but slack uh teams. You can use ai to mimic the latest real world attacks so you can really compose some humdingers. Simulations are personalized to each employee hi, this is your mom based on department, location and more.
This is so brilliant. You know you get these micro trainings, not this big long oh, you got to watch a slideshow for an hour but micro-trainings which will really solidify and drive lasting, safe behaviors. This is the way it ought to be. You could trigger great gamified security awareness training that awards employees with stars and badges. That sounds silly, but it's true. We all want stars. We do Boost completion, boosting completion rates, ensuring compliance. There's a huge library of customizable training packages you can choose from, but you can also generate your own with ai hawks hunt.
This is so good. It has everything you need to run effective security training in one platform. Every company company needs this. You can measurably measurably reduce your human cyber risk at scale. But you don't have to take our word for it. Over 3,000 user reviews on G2 make Hoxhunt the top-rated security training platform for the enterprise Easiest to use, best results. It also is recognized as a customer's choice by Gartner. Thousands of companies use it. Some of the biggest you know Qualcomm, aes, nokia. They use it to train millions of employees all over the globe. Visit hoxhuntcom slash security now, right now, to learn why modern, secure companies are making the switch to Hoxhunt, and there's a great demo there. You'll see why it's fun. And you know what, if learning is fun, people learn Hawkshuntcom slash security now. We thank them so much for supporting security now. This is actually every advertiser in security now is a company that I really think you ought to check out. This is one of them Hawkshuntcom slash security now. Thank you, hawkshunt Steve, let's talk.
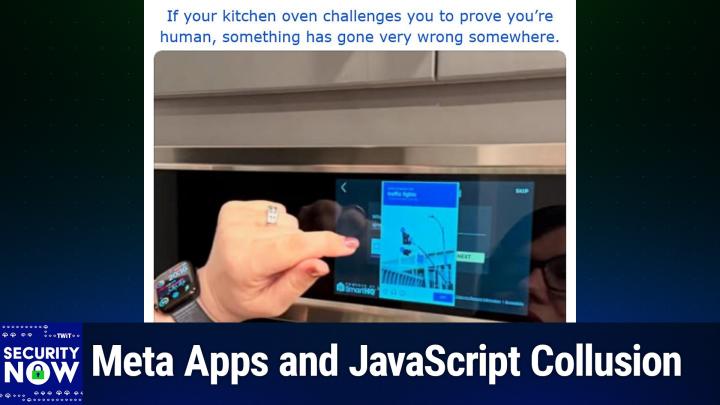
0:10:06 - Steve Gibson
We got a picture of the week we do, and I gave this one the caption. If your kitchen oven challenges you to prove you're human, something has gone very wrong somewhere no, not a captcha, wait a minute.
0:10:22 - Leo Laporte
We gotta look at this one a captcha. Wait a minute. We got to look at this one A captcha on an oven.
0:10:25 - Steve Gibson
What, the what, as Leo would say, oh no.
0:10:30 - Leo Laporte
And you can see this lady.
0:10:31 - Steve Gibson
You can see the reflection of her face, with her wearing glasses, in the screen of the oven. Somehow she is being asked. The captcha that is there on her oven screen is saying click all the bucks buttons that contain traffic lights.
0:10:50 - Leo Laporte
You can see the word traffic lights. Yeah, this is a smart things. This is must be a samsung oven.
0:10:54 - Steve Gibson
That's crazy, it is not so smart, but they build they what's not smart is they build browsers into their appliances.
0:11:03 - Leo Laporte
Oh, that's just dumb. And, by the way, I have a close friend who has a samsung refrigerator. She can't use the browser because it's out of date. It's, and that happens so quickly. Oh, but this is even worse oh yeah.
0:11:17 - Steve Gibson
So, gee, all I want to do is warm up the pie, and I've let's see where are the traffic lights and does it what? Oh my god, anyway, if your kitchen oven challenges you to prove you're human.
0:11:32 - Leo Laporte
Well, they, they, uh you got the wrong more technology than it should have.
0:11:36 - Steve Gibson
Yeah, so I wanted to take a moment to note with sadness. The internet has really responded to the passing of Bill Atkinson, who died last Thursday, june 5th, after losing his battle with pancreatic cancer. And, as you noted, that's also, of course. We know what took Steve Jobs 14 years ago, back in 2011. Steve was only 56 at the time. Still, bill went too soon. He was 71, born in 1951. I got a kick out of what he wrote in the third person of himself for the about page of his website. He modestly said aside from being a nature photographer, he meaning himself is also well-known in the world of software design. Years ago, as a member of the original Macintosh team at Apple, he helped design much of the initial Macintosh user interface and wrote the original QuickDraw, macpaint and HyperCard software. And, as I said, talk about modest. So Bill received his undergrad degree from UC San Diego, which is where he also met the now also famous Apple alumnus, jeff Raskin.
0:13:08 - Leo Laporte
Who also died of pancreatic cancer and isn't that kind of bizarre, Leo. Yeah.
0:13:13 - Steve Gibson
Like were they all drinking the same strange potion that Jobs came up with, or what? How could all three of these guys, I don't know, just seems bizarre. What are?
0:13:22 - Leo Laporte
the chances.
0:13:23 - Steve Gibson
But on the other hand, that we tend to see patterns, what, even when they don't exist anyway? Jeff was employee number 51. Um bill atkins was. I'm sorry, jeff was uh.
0:13:35 - Leo Laporte
Jeff raskin was apple employee 31 right so and and he and he met jeff was 51, so yes, yeah and he met.
0:13:43 - Steve Gibson
he met jeff at u, uc San Diego, where he was one of his professors. Then later, bill Atkinson to visit Apple, where of course, steve Jobs got his hooks into him and persuaded him to forget about school. You don't need one of those degrees. Who needs that? Join the company and change the world, and of course, jobs can be very persuasive when he wants to be. So. Atkinson became employee 51. And, of course, at Apple, bill became the principal designer and developer of the GUI for Apple's Lisa and later became one of the first 30 members of the original Apple Mac dev team, where he also principally designed the Mac's UI. He is the author of MacPaint, which at the time I'm sure you remember this, leo our jaws dropped. I mean, macpaint was an astonishing piece of work. No one could believe it and it was built upon the foundation of the QuickDraw toolbox which Bill had first written for the Lisa.
0:15:09 - Leo Laporte
In 1978, just to put it in perspective. I mean, this was a long time ago.
0:15:15 - Steve Gibson
And then ported that to the Mac. And need I note that QuickDraw was 100% pure Motorola 68000 assembly language, because that's the only way you could get these machines, I mean in order to create a reasonably priced consumer PC. Then you basically had a processor and some fancy was hardware in order to map some memory onto the screen, but there was no gpu.
0:15:48 - Leo Laporte
That you know that it was all bit banging, as we called it, in order to to draw all this and in order to, uh, you know, bill studied with raskin at the uc san diego, right, of course, ucsd pascal came from. And, uh, and and bill really wanted pascal on the Macintosh and everybody said no, you can't put UCSD Pascal on the Macintosh. Bill went home.
0:16:13 - Steve Gibson
Six days I'm trying to get six fingers on the screen.
0:16:17 - Leo Laporte
And wrote it and made it work on the Macintosh. So I wrote 68,000 code on my original Mac. But I also remember very well Macintosh programmers workshop and being able to write in Pascal.
0:16:29 - Steve Gibson
Well, and that's what impressed Steve and forever changed Jobs' opinion of Atkinson, and the key to this was that Pascal was based on a pseudo machine, a P machine. This was that Pascal was based on a pseudo machine, a P machine, and so this was the brilliant thing that Bill Atkinson realized. All he had to do was to implement the UCSD Pascal's P code, the pseudo machine, in Motorola 68000 code, and then all of the rest the compiler, the editor that was part of UCSD Pascal, all of that and all the apps and everything would start running. So it was like the perfect thing to do in under a week in order to say, okay, we got UCSD Pascal now, so brilliant, and a. It was a very nice Pascal.
I didn't mess with it on the, the Mac, but I did on the Apple too, cause Apple, too, also had UCSD Pascal. Maybe it was using a soft card, I don't quite remember now, um, but I remember that I wrote a. I wrote a, something that solved some sort of puzzles. I think it was just a, the one of the pig jumping puzzles at the time and I I did it recursively.
0:17:52 - Leo Laporte
I think, now that you say that, that the port was for the Apple too, not the Mac, right when I don't know, oh, maybe I think it was, I have to go back and look. May have been. Yeah, that would certainly make sense. Yeah, it makes kind of makes more sense. Yeah this is, what was interesting is the interface for the macintosh, and this is inside mac. The volume is all in pascal, so if you wanted to write to the apple rom, you could.
0:18:18 - Steve Gibson
Oh, that's right. So pascal would have existed. It would have been well in place by that. So I think he did for the apple too and that makes sense too, because mac paintaint was a hybrid of Pascal and assembly language.
0:18:30 - Leo Laporte
Some of those low-level quick draws obviously got to be at assembly, right? Yeah, pretty impressive.
0:18:35 - Steve Gibson
Anyway, and of course Bill also then famously designed and implemented HyperCard, which gave non-programmers access to programming and database design non-programmers access to programming and database design. And in fact, years later Bill Atkinson received it was in 1994, the EFF Pioneer Award for his contributions in the field of personal computing. You interviewed him on a long triangulation.
0:19:01 - Leo Laporte
We did four with him.
0:19:02 - Steve Gibson
One of them was a five-hour interview yeah, Yep, and you chopped it up into two pieces. So I wanted to let our listeners know that you guys did a great job with Bill Atkinson Anybody who wants to listen to him and look at him being interviewed by you. It was great.
0:19:21 - Leo Laporte
I felt very fortunate to be able to spend so much time with somebody that I admired so much well and all of his photo card stuff that you talked about for years was incredible.
Yeah, here's, if you go to my uh blog, um leofm. John jammer b slanina took a bunch of pictures of bill and I took a few of them of him on our set and you notice, by the way, he brought the sidekick, he brought the Macintosh, he brought a lot of stuff and I think it was Alex Gumpel who had a unopened copy of HyperCard that Bill signed for us. Just incredible. I have a link there to all of the interviews that we did uh with bill over a period of time. The first one was, um in 2016 at the brick house, and the last one was in 2018 in the east side studio and, yeah, that was the one. We spent five hours together. I just uh, I I'm really, for some reason, this, really this one really hit me um well, he was a good guy and really was.
0:20:27 - Steve Gibson
He was also, you know, 74. Let's not be believing at age 74.
0:20:33 - Leo Laporte
I'm certainly not planning, we're both getting close and that that's maybe another reason.
0:20:37 - Steve Gibson
But also it hit me, I think, because, uh, this is a generation yes, steve jobs, jeff raskin, bill atkinson we're a generation of people who changed computing forever and we owe them so much you know, yeah, there was someone we were laurie and I were looking at or talking about the other day, who I don't know they're 10 and like they will never know a world that didn't have the internet. Yeah, that probably probably won't be, won't be aware of it. Really. That didn't have ai, assistant stuff. I mean they're they're growing up in an entirely different environment than we did.
0:21:17 - Leo Laporte
I mean, it's just there's no comparison I guess that's why I feel it's incumbent on us to remind them of their elders, the people who made it all possible. And then we just seem old.
0:21:30 - Steve Gibson
Oh you.
0:21:31 - Leo Laporte
Yeah, we're back in the day, oh well.
0:21:38 - Steve Gibson
Oh well, anyone might be at all unsure about just how badly the likes of Meta are determined to surreptitiously track their users' movements around the internet for the purpose of secretly profiling them. The news I have to share about a recent super sneaky tracking discovery, something we've never talked about before, will disabuse anyone of any doubts along those lines. To quickly lay out what it does and how it works, the write-up of this begins with a quick overview. The guys who found this wrote begins with a quick overview. The guys who found this wrote we disclose a novel tracking method by Meta and Yandex, potentially affecting billions of Android users and I'll just save the record not only Android. This is cross-platform, but it's being done on Android. We found that native Android apps, including Facebook and Instagram, and several Yandex apps, including Maps and Browser, get this silently listen on fixed local ports for tracking purposes. Okay, now I'll just interrupt to note that that's actually kind of diabolically brilliant. Although I'm not endorsing it, it's not completely new.
For example, my own native Windows squirrel client and the other squirrel clients that people created running in the user's machine, opens and listens on port 25519. Of course, I chose that port because that's the crypto that I used For connections from a Squirrel script running on login pages. The Squirrel login JavaScript on a website's login page would send the Squirrel client app, which is running on the user's machine, a unique token by opening a TCP connection to the local host IP where the resident Squirrel client app was listening. The Squirrel client app would then connect to the remote site at the URL provided by the website, which contained a unique token. It would identify its user. That is, the Squirrel client app would identify its user and use the unique token to perform a secure public key authentication. Upon authentication success, the remote site would return a URL which the squirrel client would then forward to the waiting web browser, which would then jump the user to the logged on page at the site. Thus, essentially presto, without doing anything, the user would be logged in with complete security that could not be hacked, spoofed or intercepted. So that's how I used this feature, which is controversial at best, to allow script running in the browser to connect to something listening on the local host IP. You know 127.0.0.1. So the idea of allowing a website's JavaScript to talk to a local native app is not entirely new. But of course, what Squirrel was doing was above board and fully documented as part of the protocol. That is decidedly not the case with Meta and Yandex, who were doing this purely for tracking. And oh, is this powerful for tracking because it bypasses everything. During the development of Squirrel, there was some worry about this handy facility disappearing, since Microsoft was aware of the potential for the abuse of this and for a while they tried to shut down browser access to the local host IP from within the web browser. But there it turns out there are many other legitimate use cases for this too. So much so that too many things broke when Microsoft tried to do this and they were forced to backpedal and leave the facility in place on Windows, and it's obviously there on Android. So the guys who discovered Meta and Yandex's abuse explained.
These native Android apps receive browsers, metadata, cookies and commands from the MetaPixel, which is what they call it. It's actually a JavaScript MetaPixel and Yandex Metrica scripts embedded on 5.8 million websites. These JavaScripts load on users' mobile browsers and silently connect with native apps running on the same device through local host sockets. Since native apps have access to device identifiers like the Android advertising ID, or directly handle actual user identities, as in the case of meta apps, this method effectively allows these organizations to link mobile browsing sessions and web cookies to real-world user identities, de-anonymizing users visiting sites, embedding their scripts. This web-to-app ID sharing method bypasses all this. Is them writing. This bypasses all typical privacy protections, such as clearing cookies, incognito mode and all of android's permission controls. Yes, it also opens the door for potentially malicious apps eavesdropping on users web activity, because nothing prevents other apps from also saying, oh, let's monitor all of these meta pixel JavaScripts which are going to be trying to connect to local host. So what we have here is an interesting and extremelyinvasive hack. The concept is that this is not leveraging some bug that can be found, fixed and eliminated.
As I noted, microsoft previously tried and failed to eliminate this capability. I think it was when they were heading toward IE11, as I recall. I think that was the IE that was going to be saying eh, no more of this local host business. They had to back away. Maybe it was 10. I don't know.
Anyway, so that everyone's clear about this, the problem Microsoft had with cutting off their browser from all access to the local machine is that it has always been possible to do this and, as we've often seen, anytime something is possible, it will eventually be done and once applications have become dependent upon some available mechanism, it's extremely difficult to take it back. For example, many web developers run local web servers on their machines and they test their web code locally on web browsers running on the same machines. It's entirely practical and easier than needing to set up some second external web server somewhere and talk to it. Another example is that web browsers have become so powerful that a local application might be written to be headless without its own desktop UI and presence on its own. Instead, it will just launch the system's web browser to perform all communication with the user. The user experiences it as a website, but they're actually communicating with an application running on their own local machine. This is done by running a web server on the local machine which the browser communicates with. So Meta and Yandex are both abusing this deliberate and formally supported ability of web browsers not only to connect to far away, remote servers out on the internet, but also to little local servers set up and running inside any application on the same machine, and there's no obvious way any user can know this is going on, let alone prevent it from happening.
Since this problem is not going away, let's take a closer look at what these researchers found. They wrote. While there are subtle differences in the way Meta and Yandex bridge web and mobile contexts and identifiers, both of them essentially misuse this is again this is them writing this essentially misuse the unvetted access to local host sockets. The Android OS allows any installed app with the internet permission which will be all Android apps except maybe calculator to open a listening socket on the loopback interface 127.0.0.1. Browsers running on the same device also access this interface without user consent or platform mediation. This allows JavaScript embedded on web pages to communicate with native Android apps and share identifiers and browsing habits, bridging ephemeral web identifiers to long-lived mobile app IDs using standard web APIs. The meta Facebook pixel JavaScript when loaded in an Android mobile party underscore FBP cookie using WebRTC to UDP ports 12580 through 12585 to any app on the device that's listening on those ports. They said we found meta-owned Android apps Facebook and Instagram available in the Google Play Store, listening on this port range.
So here's the step-by-step of this in detail. First, in their normal course of use, the user opens their native Facebook or Instagram app on their device. You know, on any Android device, android smartphone the app is eventually switched away from, is sent to the background and creates a background service to listen for incoming traffic on a TCP port 12387 or 12388, and a UDP port, the first unoccupied port in the range from 12580 through 12585. Users must be logged in with their credentials on the apps, so the app the user identified to the app, facebook or Instagram. The user then opens their web browser and visits any one of 5.8 million websites which integrate the Metapixel JavaScript. Websites may ask for consent, depending upon the website and the visitor's location and local requirements, for them to do so.
The Metapixel script sends the underscore FBP cookie to the native Instagram or Facebook app using the WebRTC protocol. The Metapixel script simultaneously sends the underscore FBP value, so the same cookie it's sending to the local app. It sends it to wwwfacebookcom slash, tr and gee, do you think that maybe TR might be short for track? The URL's query tail contains other parameters such as the page's URL, website and browser metadata and even the event type, like page view, add to cart, donate, purchase, whatever. The Facebook or Instagram app which has received that underscore FBP cookie from the Metapixel JavaScript running on the browser then transmits that to graphfacebookcom slash graphql, along with other persistent user identifiers, which links the user's FBP cookie ID with their Facebook or Instagram account, thus bypassing all other privacy controls which the industry has created through the past, most recent 10 years or so. The researchers explain according to Meta's cookies policy, the underscore FBP cookie quote identifies browsers for the purpose of providing advertising and site analytic services and has a lifespan of 90 days, unquote.
The cookie is present on approximately 25% of the top million websites and, as we saw, 5.8 million overall, making it the third most common first party cookie of the Web, according to Web Web Almanac 2024. They said a first party cookie implies that it cannot be used to track users across websites, as it is set under the website's domain. That means the same user has different underscore FBP cookies on different websites. Right, it's the way it's supposed to be. Now, however, the method we disclose, they write, allows the linking of the different underscore FBP cookies to the same user, which bypasses existing protections and runs counter to user expectations.
Okay, so, just to be clear, this entire surreptitious surveillance system was specifically designed to explicitly and deliberately bypass not only all user expressible anti-tracking wishes, but also to circumvent all of the work the browser vendors have invested in to limit and control cross-site tracking. This neatly circumvents all of the explicit first-party domain-tied cookie isolation and stove piping that our web browsers have recently added specifically to prevent the abuse. So evil it is really evil, leo, and there is no other purpose. It's doing nothing other than this. There is no other reason and the only way to really remove.
0:38:07 - Leo Laporte
It is to remove Facebook and Yandex apps from your phone.
0:38:11 - Steve Gibson
Yeah, it is to remove Facebook and Yandex apps from your phone. Yeah, it is, and this behavior is entirely indefensible.
0:38:17 - Leo Laporte
I just deleted Facebook from everything, everything.
0:38:20 - Steve Gibson
Unbelievable. So that's what Meta has been up to. How does the Russian service, yandex, compare? The researchers write since 2017, the Yandex Metrica script initiates HTTP requests with long and opaque parameters to local host through specific TCP ports 29009, 29010, 3102, 30-103. Our investigation revealed that Yandex-owned applications such as Yandex Maps, navigator, search and Browser actively listen on these ports. Furthermore, our analysis indicates that the get this one, leo, oh boy, the domain yandexmetricacom, the domain yandexmetricacom Y-A-N-D-E-X-M-E-T-R-I-C-Acom, is resolving to the loopback address. I put it into NS Lookup because I couldn't believe it yesterday, and, sure enough, it came up 127.0.0.1. What it resolves? To localhost yes, in order to be extra sneaky, and I'll explain that in a second.
And the Yandex metric script transmits data via HTTPS to local ports 29010 and 3103. This design choice, they wrote, obfuscates the data exfiltration process, thereby complicating conventional detection mechanisms. Resolving to the local host IP 127.0.0.1, since script code analyzers would likely look for the string local host or the IP 127.0.0.1. But Yandex embeds a public appearing domain name to further obscure what's actually going on. And their use of HTTPS means that any communications is also obscured and is less easy to intercept, monitor and analyze. And then Yandex gets even trickier. The researchers explain Yandex apps contact a Yandex domain startup seconds parameter which they wrote we believe is used to delay the initiation of the service On one of our test devices. First, delay seconds roughly corresponded to the number of seconds it took for the Yandex app to begin listening on local ports, which was around three days. The only possible reason for this is to avoid detection and to prevent any researchers from easily discovering this deliberately concealed behavior. It's really despicable. They write after at least Facebook wouldn't do anything.
0:42:07 - Leo Laporte
The Russians would do. Right. Facebook wouldn't do anything.
0:42:11 - Steve Gibson
The Russians would do Right, embedding and bridging the Android advertising ID among other identifiers accessible from Java APIs like Google's advertising ID and UUIDs, potentially Yandex-specific as opposed to Meta's pixel case. All of this information is aggregated and uploaded together to the Yandex Met identifiers, then transferring them back to the browser context through local host sockets. Okay, in other words, meta has their native Facebook or Instagram app doing the communicating with the Meta mothership, whereas the various Yandex apps run native servers that the Yandex JavaScripts communicate with in order to, specifically to obtain whatever device-specific information Yandex may wish. That information is then returned to the browser from the little local Yandex servers, which the Yandex JavaScript then forwards to Yandex. The researchers point out an additional problem under their heading additional risk, browsing history leak and Leo, I note that we're at 40 minutes in, so let's take a pause and then we're going to look at the additional problems that doing this creates.
0:44:19 - Leo Laporte
And there are several, so now we should mention that they've they've stopped doing this, right?
0:44:24 - Steve Gibson
this is the day this report was published, they went oopsie that's admitting it. The day it came out it suddenly stopped. Oh, we don't do that what are you talking? About? What are you talking about?
0:44:41 - Leo Laporte
oh, m g, I know is it? Is it now? If I use the facebook app on a computer, is it doing the same thing or like?
0:44:52 - Steve Gibson
the website. Well, uh, it would be interesting to see if you ran the facebook app on windows. Oh, it would do the same thing you you could do a a net stat right and get the application names that are opening and listening on the local host and see whether it's whether whether facebook and instagram apps are listening on local host. I don't know if that is I. I'm not running any of that right.
0:45:21 - Leo Laporte
Yeah, for good reason, holy cow, it is a spy on on anyone's machine willfully bypassing every indication that you, as a user, have made that you want privacy yes, and willfully bypassing all of the browsers, well-meaning attempts to allow this to happen, but we're going to keep you from tracking with it now at facebook's. Can I block these ports?
0:45:50 - Steve Gibson
um, we're going to be talking about that. Okay, that's coming after our break after our break.
0:45:55 - Leo Laporte
Obviously, I have many questions, all of which will be answered soon. Oh my goodness, yeah, it's just evil. This is why we listen. What a great, what a great show. Our sponsor for this segment of Security. Now another great product. Love these guys. Threat Locker. Threat Locker is zero trust, done easy and right and affordably. I don't even need to do the ad. I just should tell you that. That's all you need to know, right? I'll give you some extra information about it you know.
Ransomware you know if you listen to the show is just killing the business world everywhere, not just business schools, infrastructure, local city governments phishing emails, infected downloads, malicious websites, rdp exploits. Look, you don't want to be the next victim. You need ThreatLocker's zero trust platform. How does it work? Really simple. It takes a proactive and these are the three words you care about deny by default approach. Deny by default approach that blocks every unauthorized action Unless it's explicitly authorized. It does not happen. That protects you from both known and unknown threats Threats nobody ever heard of, right Because they can't do anything unless they're explicitly authorized. It does not happen. That protects you from both known and unknown threats threats nobody ever heard of, right because they can't do anything unless they're explicitly authorized. That's why global enterprises like jet blue, trust, threat locker, port of vancouver, infrastructure trusts, threat locker. Threat locker shields you and them from zero day exploits and supply chain attacks, while providing complete audit trails for compliance. Threatlocker's innovative ring fencing technology isolates critical applications from weaponization, stops ransomware, limits lateral movement within your network and the good news is it works in every industry. It supports PCs and Macs. Your network can be protected in its entirety. You get great support 24-7 from US-based support folks and in a way it's a side effect, but it's a great one. Threatlocker enables comprehensive visibility and control.
Mark Tolson, he's the IT director for the city of Champaign Illinois, another very important mission critical IT operation. He says and this is a direct quote threat locker provides that extra key to block anomalies that nothing else can do. If bad actors got in and tried to execute something. I take comfort in knowing threat locker will stop that. Stop worrying about cyber threats. Get unprecedented protection quickly, easily and cost-effectively with ThreatLocker. We've talked about zero trust on the show before. It's a really great technique. This is the best way, simplest, easiest way to implement it. Visit ThreatLockercom slash twit. You get a free 30-day trial and you'll learn more about how ThreatLocker can help mitigate unknown threats and ensure compliance. Dot com slash Twitter. Yes, windows and Mac All right. So I want to hear more.
0:49:03 - Steve Gibson
Let's let's go. Yeah, so they said under their heading. Additional risk browsing history leak, they wrote. Using HTTP requests for web to native ID sharing, which is what these guys are doing, may expose users' browsing history to third parties. A malicious third-party Android application that also listens on the aforementioned ports can intercept HTTP requests sent by the Yandex Metrica script and Meta's communication channel by monitoring the origin HTTP header, which is the website domain. Thus, any app on the platform is able to use this to. Basically, the user's web browser has now been turned into a leaking sieve which is broadcasting everywhere the user goes that has either a Yandex or a meta JavaScript cookie and anybody is able to listen for it.
They said we developed a proof of concept app to demonstrate the feasibility of this browsing history harvesting by any malicious third-party app. We found that browsers such as Chrome, firefox and Edge are susceptible to this form of browsing history leakage in both default and private browsing modes. You can't hide from this. The Brave browser was unaffected by this issue due to their block list and the blocking of requests to the local host, and DuckDuckGo was only minimally affected due to missing domains in their block list. I didn't understand what they meant by that, but it's interesting that Brave does have local host blocked. While the possibility for other apps to listen to these ports exist, we have not observed any other app not owned by Meta or Yandex listening to these ports. Due to Yandex using HTTP requests for its local host communications, any app listening on the required ports can monitor the website.
A user visited with these tracking capabilities, as demonstrated by the video above, and they had a video on their site showing it. They said we first open our proof of concept app, which listens to the ports used by Yandex, and send it to the background. Next, we visit five websites across different browsers. Afterwards, we can see the URLs of these five sites listed in the app. In other words, once this local system abuse is present, there's nothing to prevent other apps from establishing their own competing services, little servers and hooking into this illicit extra browser communications to obtain, for their own purposes, the same internet-wide tracking and monitoring that the Meta and Yandex apps are deliberately employing. Finally, summarizing things they wrote, this novel tracking method exploits unrestricted access to local host sockets on the Android platforms, including most Android browsers.
As we show, these trackers perform this practice without user awareness, as current privacy controls, sandboxing approaches, mobile platform and browser permissions approaches, mobile platform and browser permissions, web consent models, incognito modes, resetting mobile advertising IDs or clearing cookies are all insufficient to control and mitigate it. We note that local host communications may be used for legitimate purposes, such as web development. However, the research community has raised concerns about local host sockets becoming a potential vector for data leakage and persistent tracking. To the best of our knowledge, however, no evidence of real-world abuse for persistent user tracking across platforms has been reported until our disclosure. Our responsible disclosure to major Android browser vendors led to several patches attempting to mitigate this issue, some already deployed, others currently in development. We thank all participating vendors Chrome, mozilla, duckduckgo and Brave for their active collaboration and constructive engagement throughout the process. Other Chromium-based browsers should follow upstream code changes to patch their own products.
However, beyond these short-term fixes, fully addressing the issue will require a broader set of measures, as they are not covering the fundamental limitations of platforms, sandboxing methods and policies. These include user-facing controls to alert users about local host access, stronger platform policies accompanying by consent and strict enforcement actions to proactively prevent misuse and enhance security around Android's inter-process communication mechanisms, particularly those relying on local host connections. So I'll add that, while these guys are only focused upon, as I said earlier, mobile platforms, this is not a mobile-only problem. As I said, mobile platforms, this is not a mobile only problem. As I said, my implementation and others of this legitimate intra platform communication for squirrels use works cross platform everywhere, on both mobile and desktop. So we know that there are currently no controls for this. So we know that there are currently no controls for this.
My own feeling is that no browsers should allow this by default. It's just too dangerous to permit, out of the box, to block and notify their user when any website they visit attempts to open a backdoor channel to something running, perhaps surreptitiously, on their own local machine. Any legitimate use of this, such as for web development, would then expect and permit this, and a browser might offer some configuration. There might be like, for example, three settings block and don't notify or request permission, or always allow. And, as another option since, for example, firefox certainly appears to have no upper limit on the number of fine-grained configuration settings that it's able to manage a user might permit this local host network communication only over certain ports, such as the standard web ports 80 and 443, to permit local web server access while blocking all other high ports that apps might use.
And, technology aside, this makes one sort of shakes one's head, leo, and I know your head's been shaking for the last half hour.
No kidding, you know, yandex is Russian, so they're not friends of the West and they're certainly not on any friendship trajectory toward the West.
But Meta is a huge and, we would wish, responsible US corporation that would like to have and deserve the trust of its users, of its users. But the design and installation of these covert backdoors in their apps, which can only have the purpose of communicating with matching user tracking web scripts spread across 5.8 million internet sites, really deserves the attention, I think, of US authorities. And, as you noted, meta knows this was wrong because this horrifying behavior was immediately shut down. The same day after the publication of this research, they got caught bypassing all user choice and anti-tracking browser enforcement and immediately turned it off. They're able to do this since those JavaScripts are all being sourced by their own content delivery network, so it was only a matter of changing the code being sent out from the mothership. But their apps will still be opening and listening for any local web browser connections. Who's to say where, when and how they might attempt to resume this behavior in the future.
Who would know they might attempt to resume this behavior in the future. Who would know? Yeah, I'm sure they'll try something else. These guys are smart Boy, and this just demonstrates how determined they are.
0:58:41 - Leo Laporte
They insist on profiling their their own users. Well, if there's any question in anybody's mind, uh, about whether facebook was evil, there should not be any question.
Evil is maybe a strong term, uh not your friend amoral yeah, uh, I mean, I'm sure in their minds it's justified because they need that tracking to sell ads and that's their revenue model. Uh, I think it's really good that you've exposed them and these guys have exposed them and, um, and everybody should know this, should somebody? So a couple of things. One, one point somebody made is uh, I, paul did, paul holder, your friend and ours, uh, because, uh, as soon as everybody knew this, we could have reverse, abused them and flooded them with fake sites and ids, which is true as soon as it becomes public, it's easy to fake. Another person, uh, pointed out out of sync also very smart that uh, it would be nice if, if, you'd get a pop-up when the browser is accessing a local host, because, yep, that's that's definitely that's questionable behavior. There's times when you do that. I do it, but you should.
You know you're doing it if it's happening and you haven't done it on purpose exactly that's not good.
0:59:49 - Steve Gibson
Or? Or I would say if, if the user puts local host into the url address, then the they're deliberately going to a localhost server. If script tries to access localhost, oh and boy in that tricky setting up yandexmetricacom to resolve to 127.0.0.1, oh so who is what what.
1:00:17 - Leo Laporte
What uh domain register would allow that. I guess you just changed the dns to point exactly it's just the dns pointing there yeah wow, unbelievable.
1:00:30 - Steve Gibson
Yeah, I mean there there is no excuse for this. They got caught, and I mean their own guilt is demonstrated by the fact that they immediately turned it off it's like oops, bad idea guys, wow what a story. Thank you for that yeah, let's take another break since we're now at an hour, and then we're going to look at the uh dns servers, the new service that's been set up in the eu by the eu. I think that's fascinating.
Yeah, um boy, that's really interesting just don't use them from the us just as long as you trust them, it's okay it's good. Actually, there's been some question yeah, why would they? Oh, it's a service yes, and no one makes anyone you know use their d, so I think it's above board. Anyway, we'll get to that in a second.
1:01:22 - Leo Laporte
Our show today, brought to you by US Cloud. You know the name. I've been talking about it for some time now, I admit. When I first heard of them, I said, are you a cloud company? They said no, we're the number one Microsoft unified support replacement. We can't help you in the cloud. I'll explain how in a minute. But their business is to replace Microsoft expensive Microsoft support with better, less expensive, faster support with US cloud. They're the global leader in third-party Microsoft support for enterprises. They support 50 of the 5-0 of the Fortune 500. And one of the five zero of the fortune 500.
And one of the reasons yes, switching to us cloud can save you a lot 30 to 50 percent over your microsoft unified and premiere support. That's big savings. But it can't just be less expensive, it has to be as good. Oh, how about this? It's better. Certainly. It's faster, twice as fast on average time to resolution versus Microsoft. Okay, that's good.
And now US Cloud's excited to tell you about a new offering that will save you money, and this is the cloud right here Azure Cost Optimization. So let's talk here, All right, when was the last time you evaluated your Azure usage? You've been thinking about it, but if it's been a while. You've undoubtedly got some Azure sprawl, a little spend creep going on. The good news is saving on Azure is easier than you think with US Cloud. Us Cloud offers an eight-week Azure engagement powered by VBox, that in eight weeks two months will identify key opportunities to reduce costs across your entire Azure environment. With expert guidance. You'll get access to US Cloud's senior engineers. That's the other way. Us Cloud's better. These guys are the best an average of over 16 years with Microsoft products. At the end of the eight weeks in this engagement, you'll get an interactive dashboard which will identify where you have rebuild or downscale opportunities or unused resources, which means you can take those, reallocate them and take those precious IT dollars. Put them toward needed resources. May I suggest you keep the savings going and invest that Azure savings in US Cloud's Microsoft support. That's what a few US Cloud customers have done. Eliminate your unified spend and the savings just continue on.
On sam, the technical operations manager at bead gaming, b-e-d-e gaming gave us cloud five stars. He gave us this review and I'm quoting we found some things that have been running for three years which no one was checking. Three years these vms were I don't know 10 grand a month. Not a massive chunk in the grand scheme of how much we spent on azure, but you know, once you get to 40 know 10 grand a month Not a massive chunk in the grand scheme of how much we spent on Azure, but you know, once you get to $40,000 or $50,000 a month, it really starts to add up. It's simple Stop overpaying for Azure. Identify and eliminate Azure creep and boost your performance, and you can do it all in eight weeks with US Cloud. Visit uscloudcom right now. Book a call. Find out how much your team can save. That's uscloudcom. Book a call today. Get faster and better. Much better Microsoft support for a lot less uscloudcom.
1:04:33 - Steve Gibson
We thank them for supporting security. Now, okay, steve, let's go. Okay, so last week you can go, leo, to joindns4.eu. Funny that it's in English. Last week, the European Union launched its own multi-flavor DNS service. They call it a safe space Join the European safe digital space. So there are flavors for government, for telcos and for home users. The service is designed to provide secure and privacy-focused DNS resolvers for the EU bloc as an alternative to US and other foreign services.
1:05:17 - Leo Laporte
So they want their own. Yeah, they want their US and other foreign services, so they want their own. Yeah, they want their own, okay.
1:05:21 - Steve Gibson
The project was first announced back in October 2022. October 2022. Sorry, the year 2022. And was built under the supervision of the EU Cyber Security Agency, enisa, enisa. It's currently managed by a consortium led by the Czech Republic security firm, whalebone W-H-A-L-E-B-O-N-E, and members include cybersecurity companies, certs academic institutions from 10 EU countries. Sounds good. I confirmed the Whalebone ownership, since I immediately dropped the various DNS resolver IPs into GRC's DNS benchmark and the benchmarks ownership tab showed they were all within a network owned by Whalebone SRO, sro.
Now, naturally, these EU resolvers include built-in DNS filters for malicious and malware linked domains, that is, filtering them out that prevent users from connecting to known bad sites. The lists are managed from a central location by EU threat intel analysts, and none of this costs anything for EU users or anybody for that matter, nor companies or any governments that might decide to adopt the service. The pitch to governments and telcos is that having the EU offer a trusted DNS service can eliminate the costs and overhead associated with running their own DNS infrastructure and, to the degree that independent DNS services required security personnel to manage and filter the directory you know, like upkeep and all that that can now be offloaded to the dedicated DNS4EU team. The variations that are offered for DNS, which are targeted to home users, give people a choice of different profiles. Malicious domains can be removed. Adult content you know malicious domains can be removed. Adult content ad filtering interestingly.
1:07:41 - Leo Laporte
So this is like NextDNS or OpenDNS or 4444. Exactly Like Cloudflare, exactly.
1:07:48 - Steve Gibson
So on their page for home users they say choose the resolver that fits your needs. So at 86.54.11.1, that's the protective resolution that removes questionable and malware domains. If you use .11.12, you get protective plus child protection, so it removes adult content. Or if you use 11.13, you get protective plus ad blocking. 11.11 gives you all of that protective, child protection and ad blocking. Or if you go to 11.100, that is to say 86.54.11.100, you get unfiltered DNS all of the domains that are available on the
net. Now, while it would be nice to have government-backed free DNS web content filtering, I have a DNS benchmark and so I immediately dropped those IPs in, wondering how those five resolver IPs list on the benchmark and I was not impressed included a clip from the benchmark showing the performance, where the word atrocious comes to mind. But stop, because people in the EU have since confirmed they work great over there and of course that's what you'd expect. Right For me in Southern California their average response time ranged from 163 to 173 milliseconds, which is very slow. For example, compare that to Cloudflare's DNS that the same benchmark had come in at 20 milliseconds. But again, I want to make sure everybody understands they didn't do this for me in southern california the european union yeah, is not suggesting that someone located in southern california should be using their dns at all.
1:10:10 - Leo Laporte
Uh is it typically the case that if it's geographically closer it's it's faster?
1:10:15 - Steve Gibson
yes, because the packets have to travel all that distance um so it's at the speed of light, steve, I mean uh, yeah, but it it turns out it's got to go across the ocean under the cable, you know?
1:10:28 - Leo Laporte
does it go through other servers too on the way, or is it?
1:10:31 - Steve Gibson
yeah, um, the it is bouncing well. I am connecting directly to that server that the reason that Cloudflare is so fast anywhere is that they're a CDN. You use a Cloudflare IP. What is it? 1.1.1.1. Well, you're not. Actually, that's a pseudo IP. You're actually being routed to some very local Cloudflare DNS server that is physically close to you. Even though I use that and people in the EU use that IP, they're getting a Cloudflare server near them.
1:11:12 - Leo Laporte
So it makes sense that Whalebone would be slow from Southern California.
1:11:16 - Steve Gibson
And again I want to make sure everybody understands I posted to GRC's DNS dev news group where we've all been testing this evolving next generation DNS benchmark code, and I asked anybody who's located in the EU to give the same set of DNS IPs a run. Because of the time zone difference I didn't hear back by the time I posted today's show notes. Since then I have, and they that for anybody in the eu if they're getting great performance they're getting the same 20 millisecond ish performance from those yeah.
Yes, so, and that's why that's why, frankly, GRC's benchmark is so valuable, is you?
1:12:06 - Leo Laporte
know I don't get the same thing as when somebody else runs it.
1:12:09 - Steve Gibson
It matters where you're running it from and which is to say it. You know and that's the DNS server you want to choose for that location. So the DNS services are available under all protocols IPv4, ipv6, dns over UDP, and so those you know IPv4 and V6 over UDP, but also DOH and DOT, where you get privacy-enforcing, secure DNS over TCP with TLS. So the benchmark showed them in green, which also indicates that they support DNSSEC security, so that the records that are available they will support signed, cryptographically signed DNS records to prevent anyone from spoofing or altering those records. So anyone in the EU wishing to explore this further should jump their browser over to joindnsnumeral4.eu, where you'll find all the information is it?
1:13:21 - Leo Laporte
it's free, right? How does yeah? It's free and see I, I understand if you're in the eu, you might want to use this. Uh, if, if our government decided to make a dns server, I don't think I'd use it.
1:13:33 - Steve Gibson
No, I just don't think I want to use the Doge DNS server while we're on the topic of DNS, I noted that Ukraine's military intelligence agency claims that it took down the DNS service of the Russian railways using a six gigabit two hundred two point five million packet per second DDoS attack. The reporting was in Ukrainian news and it was in Ukrainian, and I didn't bother to dig any further. It's unclear to me what that accomplished.
1:14:12 - Leo Laporte
You know it was fun, we could do it. Yeah, as we know, trains do not run on time now.
1:14:17 - Steve Gibson
Yeah, any attack on DNS would need to be sustained until the local DNS caches expired. At that point things would begin to collapse. But it wasn't clear what would collapse. Would the trains no longer run at all? Would the scheduling and the ticket sales fail? I don't know Now. That said, using a large number of inexpensive, stealthfully inserted autonomous drones to remotely take out many extremely expensive Russian cruise missile launching warplanes Now that's something to write home about.
1:14:57 - Leo Laporte
And a six gigabit attack is not that big. Those are like okay, wow Okay.
1:15:04 - Steve Gibson
I guess it wasn't a very, and it's probably some server in a closet somewhere that it started to smoke.
1:15:11 - Leo Laporte
But okay, who cares, it's the Russian railway, it smokes a lot. Anyway, it's the Russian railway. Yes, right, it probably smokes a lot. Anyway, it's the Russian Railway, yes right.
1:15:21 - Steve Gibson
The Linux Foundation has launched what they call the FAIR F-A-I-R WordPress Package Manager. Given the astonishing number of websites that use the WordPress core as their content management system, their CMS, I always want to keep our listeners abreast of any important WordPress-related news. So when the Linux Foundation announces the launch of their replacement for WordPressorg's own package manager, that makes the news cut. I haven't cupped up the date on the politics surrounding WordPress and automatic, but the reporting that I saw said quote the new system is a decentralized alternative to the WordPressorg plugin and theme ecosystem, developed with help from veteran WordPress developers who were pushed out from the main WordPress project last year during a power grab by Automatic and Matt Mullenweg. Oh ow, so there, yeah. So what I do know is that this replacement looks pretty sweet. It's called the FairPM page, so it's githubcom slash FairPM, they explain.
The Fair Package Manager is an open source initiative backed by the Linux Foundation is an open source initiative backed by the Linux Foundation. Our goal is to rethink how software is distributed and managed in the world of open web publishing. We focus on decentralization, transparency and giving users more control. Our community brings together developers, infrastructure providers and open web contributors and advocates, who all share the same mission to move away from centralized systems and empower site owners and hosting providers with greater independence. Fair is governed through open working groups and consensus-driven processes, ensuring that its development reflects the needs of the broader community. Whether you're a contributor, a host or an end user, fair invites participation at every level, from writing code and documentation to community organization and governance. As a community-led project, we aim to build public digital infrastructure that's both resilient and FAIR. Public digital infrastructure that's both resilient and FAIR.
The FAIR Package Manager is a decentralized alternative to the central WordPressorg plugin and theme ecosystem, designed to return control to WordPress hosts and developers. It operates as a drop-in WordPress plugin and seamlessly replaces existing centralized services with a federated open source infrastructure. And then they finished with. There are two core pillars to the FAIR system. First, api replacement it replaces communication with WordPressorg APIs, such as update checks and event feeds, using local or FAIR-governed alternatives. Some features, like browser version checks, are handled entirely within the plugin using embedded logic, and they said, for example, browsers list. And then, second, decentralized package management FAIR introduces a new package distribution model for themes and plugins. It supports opt-in packages that use the FAIR protocol and enables hosts to configure their own mirrors for plugin theme data using Asp or their own domains, while stable plugins currently use mirrors of wordpressorg, future versions will fully support fair native packages. So anyway, this seems like a useful addition to the internet's number one web authoring and delivery system.
1:19:37 - Leo Laporte
Yeah, kind of a rebuke to Matt Mullenweg, yeah, yeah.
1:19:42 - Steve Gibson
Especially when it was created by people who were pushed out, who were old WordPress hands Right, so they said okay, fine.
1:19:52 - Leo Laporte
We'll do our own. However you feel about Matt, it does seem appropriate. Wordpress should not be dependent entirely on wordpressorg for its libraries.
1:20:01 - Steve Gibson
I think yeah it's just too important. It's gotten I mean it's too big a success. Essentially, okay. I was reminded of my recent discovery and reporting of the privacy preserving. I mean explicitly and deliberately privacy preserving and unfiltered conversational AI which we talked about a couple of weeks ago Veniceai, to save all chat GPT logs, including deleted chats with the subhead. Openai defends privacy of hundreds of millions of chat GPT users, yikes, and when ours says all chat GPT logs, they mean all of every user's chat GPT logs, not just those of selected users, not just users that some court order might say you know, like under subpoena, you must save. So this is everyone's chat GPT interactions period.
1:21:19 - Leo Laporte
Even if you explicitly say delete this interaction, which is, yes, big problem here?
1:21:24 - Steve Gibson
they are not legally able they are not currently legally allowed to actually delete people's chats, so it seems clearly better for chat gpt to never have any logs to save in the first place, which is one of the features of that Veniceai service. To understand what's going on here, I think the details are worth sharing. So here's what ours reported. They said OpenAI is now fighting a court order to preserve all chat GPT user logs, including deleted chats and sensitive chats logged through its AI business offering. After news organizations suing over copyright claims accused the AI company of destroying evidence, openai explained in a court filing demanding oral arguments in a bid to block the controversial order quote. Before OpenAI had an opportunity to respond to those unfounded accusations, the court ordered OpenAI to quote, preserve and segregate all output log data that would otherwise be deleted on an ongoing I'm sorry, on a going forward basis until further order of the court. In essence, the output log data that OpenAI has been destroying unquote. In the filing, openai alleged that the court rushed the order based only on a hunch raised by the New York Times and other news plaintiffs, and now, without any just cause, openai argued the order quote continues to prevent OpenAI from respecting its users' privacy decisions unquote. That risk extended to users of ChatGPT Free, plus and Pro, as well as users of OpenAI's application programming interface.
Openai said the court order came after news organizations expressed concern that people using chat GPT to skirt paywalls might be more likely to delete all their searches to cover their tracks. What Okay, I mean even that seems kind of far-fetched to me. Do people even know that this, what they're getting from chat GPT, was skirted to paywall? Open AI said that Evidence to support that claim news plaintiffs argued was missing from the record because so far Open AI had only shared samples of chat logs that users had agreed that the company could retain. Okay, they're being responsible right Respecting their users' privacy concerns. Sharing the news plaintiff's concerns.
The judge Ona Wang ultimately agreed that OpenAI likely would never stop deleting that alleged evidence absent a court order granting news plaintiffs request to force the preservation of all chats. Openai argued that the May 13 order was premature and should be vacated until quote at a minimum news organizations can establish a substantial need for OpenAI to preserve all chat logs. They warned that the privacy of hundreds of millions of chat GPT users globally is at risk every day that the sweeping, unprecedented order continues to be enforced, openai, argued. Quote as a result, openai is forced to jettison its commitment to allow users to control when and how their chat GPT conversation data is used and whether it is retained. Meanwhile, there's no evidence beyond speculation yet supporting claims that OpenAI had intentionally deleted data. Openai alleged and supposedly there is not a single piece of evidence supporting claims that copyright infringing chat GPT users are more likely to delete their chats. And to me that seems reasonable.
OpenAI argued OpenAI did not destroy any data and certainly did not delete any data in response to litigation events. The order appears to have incorrectly assumed the contrary. At a conference in January, wang, the judge raised a hypothetical in line with her thinking on the subsequent order. She asked OpenAI's legal team to consider a chat GPT user who found some way to get around the paywall and was getting the New York Times content somehow as the output as the output. If the user then hears about this case and says, oh whoa, you know, I'm going to ask them to delete all of my searches and not retain any of my searches going forward, the judge asked wouldn't that be directly the problem that the order would address? Openai does not plan to give up this fight, alleging that the news plaintiffs have fallen silent on claims of intentional evidence destruction, and the order should be deemed unlawful. For OpenAI. Risks of breaching its own privacy agreements could not only damage relationships with users, but could also risk putting the company in breach of contracts and global privacy regulations. Further, the order imposes significant burdens on OpenAI, supposedly forcing the chat GPT maker to dedicate months of engineering hours at substantial costs to comply, openai claimed. It follows, then, that OpenAI's potential for harm far outweighs news plaintiffs' speculative need for such data. Openai argued. While OpenAI appreciates the court's efforts to manage discovery in this complex set of cases, it has no choice but to protect the interests of its users by objecting to the preservation order and requesting its immediate vacature. Openai said.
Millions of people use ChatGPT daily for a range of purposes, openai noted, ranging from the mundane to profoundly personal. People may choose to delete chat logs that contain their private thoughts, openai said, as well as sensitive information like higher as their, logs may contain their company's most confidential data, including trade secrets and privileged business information. In personal use cases, openai goes to great lengths to protect its users' data and privacy. Openai argued it does this partly by honoring its privacy policies and contractual commitments to users. And the article goes on. But everyone has the idea. So anyway, it's a mess. Anyway, it's a mess.
The bottom line is that for the time being, and since this began, no one's chat GPT logs have actually been deleted. Since May 13th, they've been forced by court order to retain everyone's everything, and I don't mean to make more of this than it is. I'm not suggesting that we should be terrified. I have no doubt that ChatGPT will treat them these logs with as much respect as possible. But deleted needs to be put in air quotes. It doesn't actually mean now that it's truly gone. Doesn't actually mean now that it's truly gone. So, for what it's worth, if you are someone who cares about maintaining as much absolute privacy as possible, you'll want to look at something such as this Veniceai, whose entire architecture is designed in TNO mode so that they never have any logs to either keep or delete. I should mention, though, that I have compared after I talked about Veniceai, I did some side-by-side comparison against OpenAI's O3 model, which blows Veniceai away. Yeah, o3 blows pretty much everyone away.
1:30:37 - Leo Laporte
It's pretty amazing, it's just astonishing yeah.
1:30:41 - Steve Gibson
Yeah, so it's not like they are at parody, but unfortunately, chat GPT, being the big guy in town, has become a target of the advertisers I mean of of the content producers and they're saying hey, you know, our content's being slurped up and users are getting it for free by asking chat gpt what happened today what model?
1:31:05 - Leo Laporte
oh, it's all using open source models.
1:31:07 - Steve Gibson
Venice's like llama and yeah, and, and actually it's distributed open source and they're not using the chat gpt api they're using. They can't obviously right. Yeah, exactly, yeah, yeah, because they are completely unsensory actually somebody can, which is apple.
1:31:24 - Leo Laporte
Apple claims that they don't send any information to chat gpt when you use it on an iphone, so presumably you could use chat gpt maybe not its strongest models, but you could use it so what?
1:31:38 - Steve Gibson
because I mean especially what we heard at the wwdc yesterday. They're all like they're engaging chat gpt all over the place yeah, but it doesn't what it's.
1:31:50 - Leo Laporte
It'll send the prompt it has to, but it won't send any personal information. So they've made a deal, obviously, of some sort with chat, gpt, with open ai, uh, to do that yeah you, uh, you mean it won't identify who you are right to, so so it's anonymizing, except your prompt. It can't right. But so if you send it your tax returns, you're out of luck. But uh, if you said it just a simple prompt, it doesn't know who it is.
1:32:20 - Steve Gibson
Got it Okay. Erlang I don't know anybody who uses Erlang, but when you get a CVSS of 10.0. Oh, that's not good. The four people who do use it really need to pay attention.
1:32:39 - Leo Laporte
It's actually widely used because it was written by Erickson for a mobile phone, so there are a lot of embedded and interesting uses of Erlang. In that case, cvs 10 is a big deal, yeah.
1:32:51 - Steve Gibson
And it's on an SSH server, so it's an authentication bypass. It got a 10.0. That's the official CVSS. The description says Erlang slash OTP is a set of libraries for the Erlang programming language prior to versions 27.3.3, 26.2.5.11, and 25.3.2.20. Those versions are safe. Prior to those, an SSH server may allow an attacker and we know that when they say may, that means we gave it a 10.0. Read between the lines, it's not much of a may probably actually should say all an ssh server already did allow an attacker.
It did it, yes the attacker already has what they want to perform unauthenticated remote code execution. They have in parens RCE by exploiting a flaw in SSH protocol message handling, a malicious actor could and we know they mean did gain unauthorized access to affected systems and execute arbitrary commands without valid credentials. Systems and execute arbitrary commands without valid credentials. A temporary workaround involves pulling the plug, involves disabling the SSH server or to prevent access via firewall rules, meaning don't let anybody use your SSH server. Anyway, you know, even though no one talks about using Erlang, as I wrote in the show notes, apparently it's out there and, leo, you've confirmed that yeah erickson mobile phones.
Is erickson still make mobile phones?
1:34:45 - Leo Laporte
no, but they made erlang so there you go. I made erlang okay, you know it's otp implies it's the one-time uh password. Oh no, that's actually the name of erlang. Is erlang Okay? So it's not a library, it's Erlang Okay, wow Anyway 10.0, kiddies, so unplug it if you got it, holy cow.
1:35:09 - Steve Gibson
Yikes, yes, can Russia intercept telegram messages? There's a report that appears to allege that Russia now has some means for intercepting telegram messages. My most pressing question is whether this applies to two-party one-to-one messages. Here's what the reporting says the Russian human rights NGO known as First Department warned on Friday just this past Friday that Russia's Federal Security Service, the infamous FSB, has learned to intercept messages sent by Russians to bots or feedback accounts associated with certain Ukrainian telegram channels, potentially exposing anyone communicating with such outlets to treason charges. Russia's principal domestic intelligence agency, again FSB, has gained access to correspondence made with Ukrainian telegram channels, including Crimean Wind and Vision Vishnun.
According to First Department, which said that the FSB's hacking of Ukrainian telegram channels had come about during a 2022 investigation into the Ukrainian intelligence agency's gathering information that threatens the security of the Russian Federation, unquote via messengers and social networks, including Telegram. The case is being handled by the FSB's investigative department, though no suspects or defendants have been named in the case. According to First Department, when the FSB identifies individual Russian citizens who have communicated with or transmitted funds to certain Ukrainian telegram channels, it contacts the FSB office in their region, which then typically opens a criminal case for treason against the implicated person. First Department said quote we know that by the time the defendants in cases of state treason are detained, the FSB is already in possession of their correspondence, and the fact that neither defendants nor a lawyer are named in the main case allows the FSB to hide how exactly it goes about gaining access to that correspondence. First departments stress that their findings highlighted the various security risks inherent in using telegram for confidential communication, especially in cases where the contents of such private messages could result in criminal charges.
Dimitri Zerbeck, the head of First Division, said that materials from telegram have already been used as evidence, in quote a significant number of cases unquote, adding that in most cases they have been accessed due to compromised devices. However, there are also cases in which no credible technical explanations consistent with known access methods can be identified. So this guy does sound like he sounds like he knows what he's talking about. He said this could indicate either the use of undisclosed cyber espionage tools or telegrams cooperation with the Russian authorities, obvious signs of which we see in a number of other areas. So you know, we've been watching Pavel Durov's previously adamant stance soften somewhat over time, particularly after he was arrested and convicted in France last summer, particularly after he was arrested and convicted in France last summer. He's allowed Telegram. You know, I'm sorry. Has he allowed Telegram to be compromised? You know it's certainly not a messaging system that can be trusted, and remember that an audit of its homegrown crypto technology did raise additional concerns several months ago. So that's not what I would recommend anybody use, leo.
1:39:49 - Leo Laporte
What I would recommend everybody use is our next sponsor. What do you know? And if you knew what our next sponsor was, you would recommend it, because our next sponsor is the thinks canary, yay yay, monitoring is what you got to do oh, I love this.
It's a honeypot you can easily configure. Here's my this is my thinks, canary uh, and, as you can see, it's not big, it's the size of a I don't know external usb drive. Uh, it's got a ethernet port on it. Power, power connection, that's it. You plug it in, you put it on your network, you register it with a console and then let me fire up the console, because this is uh-oh.
Somebody's been scanning my ports it looks like quite frequently as well. Wonder who that could be. Let's just check in on this alert. Oh, it's coming from inside the house. It's actually the I've got a fring or thing, I guess it's called running on my computer which is called left that's why it's saying left and thing is doing port scanning from time to time of all the devices on our network. So this is an example of I turned on port scanning just so you could see it. I turned on the port scan. Look, which is actually a good thing to have on. You see there's 13 pages of this. But these are just the alerts from this thing scanning it. Now it says you have more alerts than normal. You'd like to mass acknowledge them? Yes, because I know this is not a threat. I know exactly who this is.
I could turn it off and there there's the Thinks Canary hardware, which I've got right here, currently a Windows server, but there's also Canary tokens. These are files you can create with the Thinks Canary that you can put anywhere you want. I've got four tokens. One is on the Google Drive, so you can this is the interesting thing, it's not just your local hard drive. If you want to say, hey, is somebody snooping around my Google Drive, you could put tokens there. You could put tokens almost anywhere. What can a token be? Well, of course, documents, but it also can look like. You could have it be a DNS host name that alerts if somebody queries it, like Yandexmetricacom. You could have it be a credit card that alerts you when somebody uses it, an AWS API key that alerts you when somebody uses that, and on and on.
Look at this a WireGuard client config that will alert you if somebody connects to your WireGuard. You know enough to know this is bogus. This is just a fake file. The bad guys don't know. And that's the beauty of the things to canary.
You can have all the perimeter defenses in the world, but once somebody gets into your network, how do you know they're in there? Well, the Thinks Canary is a honeypot. It doesn't look vulnerable, it looks valuable. It's a honeypot. They can't resist Once somebody gets in to your network. Maybe it's a bad guy who's penetrated your defenses, maybe it's a malicious insider. They can't resist brute forcing that fake internal SSH server. But you'll then get the alert, an alert that says you have a problem, and you'll know exactly what the problem is.
No false alerts, just the alerts that matter. You can have them set by email, text, slack, webhooks. It supports, it supports API, syslogs, pretty much any way. You want to get alerted, you will get alerted. So that's the thing. You choose a profile register with a hosted console for monitoring and notifications and then you sit back and you wait. Attackers who breached your network or malicious insiders any adversaries cannot help but make themselves known because they're going to open those files, they're going to access that credit card, they're going to try to hit that fake SSH server. I think this is such a brilliant idea.
A big bank might have hundreds spread all around a casino back end. You know, at every possible spot A small business like ours might just have a handful. Let's say you needed five things to Canary's. Okay, you go to canarytoolstwit, canarytoolstwit. Five of them cost $7,500 a year. You're going to get five of them. You're going to get your own hosted console, upgrades, support, maintenance, everything. It's all in there for a year.
Oh, I can save you a little bit If you use the code TWIT in the how did you hear about us? Box. You're going to get 10% off the price, and not just for that first year, for as long as you own your Canaries, so that savings will really add up. If you're even the slightest bit reluctant, maybe I can throw one more thing in. They have a very generous return policy. You can always return your Thinks Canary with their two-month money-back guarantee for a full refund 60 days. I should mention that we've been doing these ads for eight years and all the time we've done these ads, the folks at Think thinks say that refund guarantee has never been claimed, because once you get one of these you go oh, I love it, I need more.
Visit canarytools, slash twit. Don't forget the offer code twit in the how did you hear about us box to save 10 off for life. This is such a great idea the. It's a honeypot that's easy to deploy and very effective. By the way, these guys know their stuff. It's super secure too. Canarytools slash twit. We thank them so much for their support over all these years. They're big fans of yours, steve. That's why they.
1:45:18 - Steve Gibson
That's why I can't believe.
1:45:20 - Leo Laporte
Eight years yeah, isn't that great. Uh, haroon and his team are fantastic. We saw them at RSAC, at the RSA conference, and they're just really smart guys who have created something that is super, super valuable. Isn't it fun to see. I saw all those port scans. The first time I saw that, I went and then I realized wait a minute, it's all coming from Fing. So I turned off that monitor. So that's really cool.
1:45:47 - Steve Gibson
On, we go with the show, okay. So I had to double check the date on this news when I read that Spanish ISPs had accidentally blocked Google domains while attempting to crack down on illegal soccer live streams. The double check was required, of course, because this is not the first time this has happened, nor the first time we've noted what a lame and harebrained approach it is to force specific ISPs to locally filter large chunks of the internet for only their own subscribers. Right, I mean, everybody else can see what they want. Maybe someday we'll learn, but I don't know. I'm not holding my breath. I did note that Reddit has sued Anthropic for scraping and using Reddit comments to train its clawed AI chatbot, and I guess this is just going to be a thing, leo, for a while. You know we just talked about OpenAI in trouble with the New York Times and other plaintiffs, and now Anthropic Reddit's upset, and we know there are sites that specifically say oh no, don't worry, ai is not allowed in. So I would just say obey those robotstext files, folks, behave yourselves.
A recent analysis of Twitter's new encrypted XChat messaging appears to leave as much to be desired as you might imagine. Researcher who looked into it wrote when Twitter launched encrypted DMs a couple of years ago. He wrote it was the worst kind of end-to-end encrypted technically end-to-end encrypted, but in a way that made it relatively easy for Twitter to inject new encryption keys and get everyone's messages anyway. It was also lacking a whole bunch of features such as sending pictures, so the entire thing was largely a waste of time, he wrote. But a couple of days ago Elon announced the arrival of XChat, a new encrypted messaging platform. Quote built on Rust. It actually isn't. It's written in C.
Oh, with Bitcoin-style encryption.
1:48:16 - Leo Laporte
What.
1:48:17 - Steve Gibson
Whole new architecture. Unquote what's that mean.
And so the guy says maybe they got it right this time. And then a little bit later he says the TLDR is no Use Signal. Yeah, he said, twitter can probably obtain your private keys and admit that they can man in the middle you and have full access to your metadata. So anyway, the analysis goes deeper and to me it looked kind of interesting. It might make for some additional attention and a deeper dive for the podcast. So I may return to that next week. We'll see. In the meantime, I would follow this investigator's recommendation and not assume that what elon has brought us in this new x chat is actually secure, because they apparently were in a hurry.
Uh, didn't actually write it in rust and that's you know that's hysterical that he would even claim that I know, because I guess woo rust makes it better to be good.
1:49:20 - Leo Laporte
Rocks rust makes it better and what is? What does it even mean to say bitcoin style encryption? I don't know. Is it bitcoin? Bitcoin's not encrypted, by the way exactly. It's a public ledger that everyone can look at so I guess what they're admitting is oh yeah, we, there's no encryption but I think it just like throw in some more buzzwords maybe the messages, all the dms, are put on the blockchain for everyone.
1:49:46 - Steve Gibson
You would think he would have been Dogecoin, but I guess not oh geez Louise. Yeah, meanwhile, thundermail, the worst named service ever. Please will have email servers located in the European Union for increased privacy. Yeah, okay, fine, whatever, but could you please change the damn name? How about lightning mail? Do you like that better? That's better than thunder mail, it is. I mean, thunder mail just sounds so bad, I don't know what it?
1:50:18 - Leo Laporte
is in other happy news from thunderbird. That's why right, I mean I get it.
1:50:23 - Steve Gibson
I yes. And on thunderbird, that seems I don't know why you can't change the bird to male and have it still be good, there's something about a message and thunder that just don't go together.
1:50:37 - Leo Laporte
I don't know yeah.
1:50:39 - Steve Gibson
In other happy news, the GAO, the US Government Accountability Office, has a report out which incidentally noted in passing that the logingov site service has no policy to verify that its backups are working. So a cyber attack, a mistake or any other it issue could completely crash the US government's entire login and identity system for I don't know days, weeks or even months until it's restored. This is how I get into my Social Security account. Yeah, well, you better log in and hope you stay logged in because, uh, apparently it could go away. Yeah, and lord knows, I mean you know oh, also global entry.
1:51:35 - Leo Laporte
My global entry accounts there, uh, my irs account. Actually they use id me. They. That really makes me nervous. They use a third party.
1:51:44 - Steve Gibson
Yeah, system, yeah maybe it's better to send it somewhere else maybe I would imagine id me it probably actually has backups. Okay, so let's take talk about the illusion of thinking and apple's work on this. We have one more break, but we'll get to that uh, halfway through this it's a quick break, so yeah, okay, yeah uh, a couple of days ago, I added an AI group to GRC's long-running, text-only NNTP news groups.
In my inaugural post to that group I wrote I've learned not to haphazardly create groups that do not have enduring value, since it's more difficult to remove groups than to create them, and endless group proliferation is not ideal. Clear that artificial intelligence is in the process of rapidly changing the world and I cannot imagine any more important and worthwhile new group to create. Then, just this past Sunday, upon discovering this just-released research from Apple, thanks to feedback from one of our listeners, urs Rao, I posted the following into this new our brand new AI news group. There, I said, the illusion of thinking is how the title of their well-assembled paper begins. The entire title is the illusion of thinking understanding the strengths and limitations of reasoning models via the lens of problem complexity. And so I wrote in this posting to GRC's news group is this just sour grapes engendered by Apple finding themselves behind the rest of the industry in AI deployment? I don't think so. This looks like an exploration that adds to our understanding of what we have today, and it's not suggesting that what we have today is not useful, nor that Apple might not wish they had some of their own. What it's doing is exploring the limits of what we are now calling artificial intelligence and suggesting what many of us have intuited, which is that, while a massive problem space can be solved with powerful pattern matching, when there are not patterns to be matched, today's systems are revealed to not be exhibiting anything like true problem understanding. In other words, leo, your earliest take on this, which was that AI was little more than fancy spell correction, carried an essential kernel of truth onto which Apple has just placed a very fine point. I think everyone should listen carefully to what Apple's research paper abstract explains. Abstract explains.
They wrote recent generations of frontier language models have introduced large reasoning models, lrms, that generate detailed thinking processes before providing answers and, leo, you and I were just talking about 03. And yes, it is astonishing, they said. While these models demonstrate improved performance on reasoning benchmarks, their fundamental capabilities, scaling properties and limitations remain insufficiently understood. And, as I said a week or two ago, researchers are going to be studying what we have, and it's not something that happens overnight, but we're going to begin to get answers that tell us more about what it is we have. This is one such set of answers they wrote.
Current evaluations primarily focus on established mathematical and coding benchmarks, emphasizing final answer accuracy. However, this evaluation paradigm often suffers from data contamination and does not provide insights into the reasoning traces, structure and quality. In this work, we systematically investigate these gaps with the help of controllable puzzle environments that allow precise manipulation of compositional complexity while maintaining consistent logical structures. This setup enables the analysis of not only final answers but also the internal reasoning traces, offering insights into how LRMs think, and they have that in air quotes. Through extensive experimentation across diverse puzzles, we show that frontier LRMs face a complete accuracy, collapse beyond certain complexities. There's a cliff. Moreover, they exhibit a counterintuitive scaling limit. Their reasoning effort increases, increases with problem complexity up to a point, then declines, despite having an adequate token budget Meaning we're letting you have, we're letting you think about this as much as you want. Keep going, but they don't. They wrote.
By comparing LRMs with their standard LLM counterparts under equivalent inference compute, we identify three performance regimes First, low complexity tasks, where standard models surprisingly outperform LRMs perform LRMs. Second, medium complexity tasks, where additional thinking in LRMs demonstrates advantage. And then three, high complexity tasks, where both models experience complete collapse. We found that LRMs have limitations in exact computation. They fail to use explicit algorithms and reason inconsistently across puzzles. We also investigate the reasoning traces in more depth, studying the patterns of explored solutions and analyzing the model's computational behavior, shedding light on their strengths, limitations and ultimately raising crucial questions about their true reasoning capabilities.
Okay now, as I've cautioned before, anything and everything that's believed to be known about AI definitely needs to carry a date stamp and also, probably a best used by expiration date, showing us some interesting and probably previously underappreciated features of today's LRMs large reasoning models. It's worth reminding ourselves that if Apple had written the same paper a year ago, before the appearance of LRMs, and only challenging LLMs, the results would have been similar, though significantly less impressive for the AI side. The question, then, is whether, and if so, to what degree, even larger reasoning models in the future will be able to eclipse the performance of today's large reasoning models. In other words, since what we all want to know today is what's going to happen with AI in the future, to what degree is Apple's research able to speak to any fundamental underlying limitations that might limit any future AI? That is, will this current language, linguistic, neural network-based approach hit a wall? To answer that question, we need to see what Apple's research discovered. Here's how Apple's researchers set up the question. They wrote large language models.
Llms have recently evolved to include specialized variants explicitly designed for reasoning tasks, large reasoning models such as OpenAI's O1 and O3, deepseq R1, claude 3.7, sonnet Thinking and Gemini Thinking. These models are new artifacts characterized by their thinking mechanisms such as Long Chain of Thought, cot with self-reflection, and have demonstrated promising results across various reasoning benchmarks. Their emergence suggests a potential paradigm shift in how LLM systems approach complex reasoning and problem-solving tasks, with some researchers proposing them as significant steps toward more general artificial intelligence capabilities. Despite these claims and performance advancements, the fundamental benefits and limitations of LRMs remain insufficiently understood, and you know also, they're very new right. So OK, critical questions still persist. Are these models capable of generalizable reasoning or are they leveraging different forms of pattern matching? How does their performance scale with increasing problem complexity? How do they compare to their non-thinking standard LLM counterparts when provided with the same inference token compute? Llm counterparts when provided with the same inference token compute? Most importantly, what are the inherent limitations of current reasoning approaches and what improvements might be necessary to advance toward more robust reasoning capabilities? We believe they wrote.
The lack of systemic analysis investigating these questions is due to limitations in current evaluation paradigms.
Existing evaluations predominantly focus on established mathematical encoding benchmarks which, while valuable, often suffer from data contamination issues and do not allow for controlled experimental conditions across different settings and complexities. Moreover, these evaluations do not provide insights into the structure and quality of reasoning traces. To understand the reasoning behavior of these models more rigorously, we need environments that enable controlled experimentation. In this study, we probe the reasoning mechanisms of frontier LRMs through the lens of problem complexity. Rather than standard benchmarks, meaning math problems, we adopt controllable puzzle environments that let us vary complexity systematically by adjusting puzzle elements while preserving the core logic, and inspect both solutions and internal reasoning. Then we see, to my delight, the paper's diagram of one of the puzzle tests Apple's researchers chose, which is the famous Towers of Hanoi. This is a classic puzzle with very simple rules, which is what makes it such a great puzzle. I received a beautiful wooden version one Christmas when, as a child, my annoying aunt, who was always trying to stump me, thought okay, now for those who are not familiar, I love it.
2:04:46 - Leo Laporte
I had the one when I was a kid too, and that's how I learned recursion. I think it's why I was able to grok recursion right away.
2:04:53 - Steve Gibson
Yep.
2:04:53 - Leo Laporte
Isn't that fascinating.
2:04:55 - Steve Gibson
For those who are not familiar, the puzzle consists of three pegs in a line, with one of the pegs having a stack of disks of decreasing diameter, with the largest disk on the bottom and going to the smallest disc on top. The challenge is to move all of the discs from the starting peg to the peg at the other end of the three, by moving only one disc at a time from any peg to any other peg, while never placing a larger disc over a smaller disc. It's a truly lovely puzzle, because that's the rules. The rules are simple, but the solution requires patience, repetition and grasping a deeper solution concept. That's what makes this such a perfect puzzle to test reasoning. Okay now, I should note that the puzzle is also a joy to solve by computer using traditional coding methods, and that the most elegant coding solution employs recursion, since this puzzle itself is deeply recursive. For anyone who has an age-appropriate child or nephew, amazon has a large selection, like pages, of beautifully rendered wooden and colorful versions of this famous puzzle. Now, what's so clever about Apple's choice of this puzzle is that its complexity can be uniformly scaled simply by changing the number of disks. So first imagine that we just have one disk. We can simply move it to its destination peg. If we have two disks, the smaller disk must first be placed on the middle peg so that the bottom larger disk can be placed on its destination peg at the other end of the puzzle. Then the smaller disk can join the larger disc on the end peg and the two-disc puzzle is solved.
Switching to three discs requires a bit more work. So visualize three pegs and three discs. The smallest disc temporarily goes onto the third destination peg. The middle disk goes to the middle peg. Now the smallest disk can go on top of the middle disk on the middle peg. This frees up the third peg to receive the largest bottom disk which is now all alone on the original peg. So you move that over to the third peg. The middle size disk is then moved to I'm sorry. The smallest size disk is then moved to the first peg, which uncovers the middle size disk which is on the middle peg, which can now be placed onto the third destination peg, and the smallest disc can then join the others to complete the stack and solve the three-disc puzzle. It is quite satisfying to do this.
And note that the two-versus-three-disc puzzle may hopefully teach the astute puzzler which peg should first receive the smallest disc, based upon whether the disc count is even or odd, and that would be confirmed by solving the four-disc puzzle. By solving the four-disc puzzle Now. I should mention that if anyone who is listening is planning to make a gift of one of these, please encourage its recipient to start out this way. Rather than just jumping into a very frustrating deep end using all of the eight or ten discs that these puzzles provide, solving the puzzle with very few disks will provide the encouragement and stamina that will eventually be needed to tackle and solve this very gratifying full puzzle, Then make them write it in Python.
2:09:24 - Leo Laporte
and now you got something.
2:09:28 - Steve Gibson
And again, that little trick about noticing which pen to start out with will definitely save the day, and you need it you keep it's recursive, so you need it each time we start.
Yeah, the next thing, yeah so I think that apple's choice of the towers of hanoi is brilliant by reason of the puzzles, lovely, lovely scalability of difficulty. In all, they used four different, somewhat similar sequential combinatorial puzzles Towers of Hanoi, checker, jumping on a linear strip of squares, something that they call block world, and also river crossing. So here's what Apple explained. They said these puzzles first, offer fine grained control over complexity. Second, avoid contamination common in established benchmarks. Third, require only the explicitly provided rules emphasizing algorithmic reasoning. And fourth, support rigorous simulator-based evaluation enabling precise solution checks and detailed failure analysis. Just very clever that they did this. They said our empirical investigation reveals several key findings about current large reasoning models, lrms. First, despite their sophisticated self-reflection mechanisms learned through reinforcement learning, these models fail to develop generalizable problem-solving capabilities for planning tasks. Huh yeah, and look at these charts here in the middle of page 19, leo.
2:11:20 - Leo Laporte
Yeah.
2:11:20 - Steve Gibson
With performance collapsing to zero beyond a certain complexity threshold.
Hmm, zero beyond a certain complexity threshold. Second, our comparison between LRMs and standard LLMs under equivalent inference compute reveals three distinct reasoning regimes and that's what I talked about before. They said for simpler, low compositional problems, standard LLMs demonstrate greater efficiency and accuracy. As problem, you know like there's this overthink problem. As problem complexity moderately increases, thinking models gain an advantage. So that's what we're now seeing right In what O 03 is doing. We're seeing this improved advantage.
However, when problems reach high complexity with longer compositional depth, both model types experience complete performance collapse and we see that in the chart that I've got on page 19 on the left. They said notably near this collapse point, lrms begin reducing their reasoning effort measured by inference time tokens as problem complexity increases, despite operating well below generation limits, as shown in the middle diagram. They said this suggests a fundamental inference time scaling limitation in LRMs reasoning capabilities relative to problem complexity. And they said finally, our analysis of intermediate reasoning traces or thoughts reveals complexity dependent patterns. In simpler problems, reasoning models often identify correct solutions early but inefficiently, continue exploring incorrect alternatives an overthinking phenomenon. At moderate complexity, correct solutions emerge only after extensive exploration of incorrect paths, and that's fair. And beyond a certain complexity threshold, models completely fail to find correct solutions. In other words. In other words, they're not really reasoning. This indicates LRMs raising questions about the nature of reasoning in these systems, with important implications for their design and deployment. They then list their key contributions from this research, which we're going to go into after our final break.
2:14:27 - Leo Laporte
All right, you got me thinking, uh, and I just ordered a towers of hanoi because I remember this was such fondness from my childhood. It's just pleasant and gratifying yeah, and once you understand it, uh, it's pretty straightforward, but it's fun yeah, but for a five-year-old or an eight-year-old I?
you know I hadn't really thought about this, but I think the fact that that was on our coffee table when I was a little kid and I did figure out how to solve it probably prepared me well for understanding. Recursion, because you repeat the same algorithm over and over exactly, and planning, because you have to start on the right peg to make it most efficient.
2:15:07 - Steve Gibson
There's a few things and you're able to give yourself simpler versions of it in order to kind of get the hang of it right, because you're just repeating it.
2:15:15 - Leo Laporte
Yeah, uh, there's really nothing to say except, uh, if you enjoy this show and you want to support what steve does here, best way to do that join the club. Club Twitter. Look, I'm a little round thing. Is this a tribute to Apple? I don't know. The club.
What if I press that the club is our way of kind of adding, enhancing our revenue, because if we started it during COVID four years ago, because ad revenue was declining and we didn't want to stop doing what we do, we wanted to do more of it. So we said well, you know, and this was always my thought I always wanted this to be a listener-supported network. When we first started 20 years ago, the tools weren't there to make that easy, and even though we tried, we never made quite enough money to grow and so we ended up doing ads. But I think now the tools are there. We use Memberful, which is a Patreon company, for our club membership. That's made it very easy for you to join the club. Well, and I think the testament is that is that we have I don't know what the last number is, but at least 12,000 people in the club. That's fantastic. We really appreciate it. Now we did recently raise the cost. Those of you who are already in the club continue to pay the price you paid when you joined, but for new members, 10 bucks a month. I think that's very fair.
What do you get? Well, you get ad-free versions of all the shows, because I always hate it when they, when they charge you and then still show you ads. That always. That always bugged me. So, of course, because we're charging you, you're supporting us. You don't need to hear the ads. You wouldn't even hear this plug for the club.
You also get access to the club, to it discord, which is the members home on on the internet. Now, you don't need to join the club to get the I mean the discord to get the benefits of the club. Lots of people don't, but I should tell you that the discord is where all these special shows, like yesterday's wwdc keynote, uh, the google io keynote, uh, the microsoft build keynote and future keynotes these will all happen inside the club, so that's an important reason to join. Also, our special shows, like friday I'll be doing photo time with chris marquardt, uh, at 1 pm. Micah's crafting corner is june 18th uh, that's always fun. I'm gonna do some vibe coding. When microsoft does by microsoft. Oh, micah, does some like. I'm gonna call micah microsoft from now on. And we also, uh, do other things. We've got Stacy's book club in here, the AI user group, on the first Friday of every month. We will have a Stacy's book club soon. We haven't scheduled the date yet. That's all. But all of this happens inside the club Twit Discord, so that's another benefit. You also get the special, wonderful feeling that you're supporting the work we do here at Twit, because about 25% of our operating revenue comes from you, our viewers and listeners.
Without that, we would have to cut back, frankly, we'd have to let people go. We'd have to cut back on shows. I don't want to do that. In fact, I'd like to grow, which is why I'd like you to join the club. If you would twittv slash club twit, you will have my eternal gratitude and I will see you in the discord. Twittv slash club twit. Uh, the one millionth sign up gets a free doll according to pretty fly for the cis guy. You want that? We can make it for you. It's cute, dude. Twittv slash club twit. And thanks in advance. Back to you, mr Gibson.
2:18:53 - Steve Gibson
Okay. So they say their key contributions are from the research. Yes, we questioned the current evaluation paradigm of LRMs on established math benchmarks and design a controlled experimental testbed by leveraging algorithmic puzzle environments that enable controllable experimentation. With respect to problem complexity, we show that state-of-the-art LRMs O3, mini, deepseq R1, clawd 3.7 Sonnet Thinking still fail to develop generalizable problem-solving capabilities, with accuracy ultimately collapsing to zero beyond certain complexities across different environments. We find that there exists a scaling limit in the LRM's reasoning effort with respect to problem complexity, evidenced by the counterintuitive decreasing trend in the thinking tokens after a complexity point. We question the current evaluation paradigm based on final accuracy and extend our evaluation to intermediate solutions of thinking traces with the help of deterministic puzzle simulators. Our analysis reveals that, as problem complexity increases, correct solutions systematically emerge at later positions in thinking compared to incorrect ones, providing quantitative insights into the self-correction mechanisms within LRMs. And finally, we uncover surprising limitations in LRMs' ability to perform exact computation, including their failure to benefit from explicit algorithms.
We'll get to this. But at one point they told it how to do the towers, and still could I like? They gave instructions here's how you solve this, and then anyway, and their inconsistent reasoning across puzzle types. Okay. So for those thinking uh, uh or listening to this without the advantage of the performance charts in the show, notes that the claude 3.7 thinking versus non-thinking model performance on the Towers of Hanoi puzzle was interesting. We talked about. Everyone understands the Tower of Hanoi now. Both the earlier large language model and the later large reasoning models performed perfectly and the later large reasoning models performed perfectly, returning success 100% of the time when only one or two disks were used and we saw how simple those were. Both models still did very well after a third disk was added but interestingly the fancier thinking model underperformed the simpler LLM by about 4%. That's wild.
Yeah, but when that first peg was stacked with four disks, the deeper thinking model's performance was restored, whereas the simpler Clawed 3.7 LLM collapsed to only finding the solution 35% of the time, whereas the thinking model held at 100. As the discount then increases above 4, both models' performance continues to drop. Performance continues to drop, but the LRM holds a huge lead over the LLM. Until they get to eight disks, the LLM is never able to solve that one, whereas the thinking model finds the eight-disk solution about one out of every 10 tries about 10%. But 10 disks is beyond the reach of either. The full research paper has lots of interesting detail about the various models' performance on the four puzzle types. I noted, however, that the nature of the other three puzzles seemed to be pretty much beyond the grasp of any of this so-called AI, much beyond the grasp of any of this so-called AI. One of their more interesting findings was the appearance of what they term the three complexity regimes. Paraphrasing from the paper they wrote under how does complexity affect reasoning, they said.
Motivated by the observations to systematically investigate the impact of problem complexity on reasoning behavior, we conducted experiments comparing thinking and non-thinking model pairs across our controlled puzzle environments. Our analysis focused on matching pairs of LLMs with identical model backbones, specifically Claude 3.7, sonnetnet, with and Without Thinking, and Deep Seek, r1 versus V3. For each puzzle, we vary the complexity by manipulating problem size n, where n represents the discount, the checker count, the block count or the crossing elements. Results from these experiments demonstrate that, unlike observations from math and that's probably one of the most significant things here is that we keep seeing oh, these do better than a math PhD, and it's like okay, how about frogs jumping over each other? Oh well, no, it can't do frogs. So they said there exists three regimes in the behavior of these models with respect to complexity. In the first regime, where problem complexity is low, we observed that non-thinking models are capable of obtaining performance comparable to or even better than thinking models with more token, obtaining performance comparable to or even better than thinking models with more token-efficient inference, meaning it's cheaper to do them. In the second regime, with medium complexity, the advantage of reasoning models capable of generating long chain of thought begin to manifest and the performance gap between the model pairs increases. The most interesting regime is the third regime, where problem complexity is higher and the performance of both models have collapsed to zero. Results show that while thinking models delay this collapse, they ultimately encounter the same fundamental limitations as their non-thinking counterparts.
I think it's important to address their decision to use puzzles as an evaluation mechanism versus math problems. They gave this a lot of thought and they wrote on the math and puzzle environments question. They wrote the following they said currently it is not clear whether the performance enhancements observed in recent reinforcement learning RL-based thinking models all of the LRMs we've been talking about are attributable to increased exposure to established mathematical benchmark data, to the significantly greater inference compute allocated to thinking tokens or to reasoning capabilities developed by RL-based training. That is, the reinforcement learning training. Recent studies have explored this question with established math benchmarks. By comparing the upper bound capabilities of reinforcement learning based thinking models with their non-thinking LLMs can eventually reach performance comparable to thinking models on benchmarks like MATH500 and AIM24. We also conducted our comparative analysis of frontier LRMs like CLAW3.7, sonnet with and without thinking, and DeepSeq R1 versus V3. Our results confirm that on the MATH500 dataset, the performance of thinking models is comparable to their non-thinking counterparts when provided with the same inference token budget.
However, we observed that this performance gap widens on the AIM-24 benchmark and widens further on AIM-25. This widening gap presents an interpretive challenge. It could be attributed to either increasing complexity requiring more sophisticated reasoning processes, thus revealing genuine advantages of the thinking models for more complex problems, or reduced data contamination in the newer benchmarks, particularly AIM-25. Interestingly, human performance on AIM-25 was actually higher than on AIM-24, suggesting that AIM-25 might be less complex. Yet models perform worse on AIM-25 than AIM-24, potentially suggesting that data contamination during the training of frontier LRMs is occurring. That is, there's more contamination in the older models because there's been more time for the contamination to happen as compared to the newer training benchmarks or testing benchmarks.
Given these non-justified observations and the fact that mathematical benchmarks do not allow for controlled manipulation or problem complexity, we turned to puzzle environments that enable more precise and systematic experimentation. Okay, so we have the very real problem of data contamination that makes judging what these AI models are actually doing, meaning that the models may have previously encountered the problems during their training and simply memorized the answer. So they're not actually reasoning, they're not thinking or solving new problems, they're pattern matching at a very high level and just regurgitating. But even puzzles like the Towers of Hanoi and River Crossing exist on the internet and are also presumably in the training data. The researchers talk about this.
Under the heading Open Questions Puzzling Behavior of Reasoning Models. They write we present surprising results concerning the limitations of reasoning models in executing exact problem-solving steps, as well as demonstrating different behaviors of the models based on the number of moves. Again, this is what I was talking about in the Tower of Hanoi environment. Even when we provide the algorithm to be used in the prompt so that the model only needs to execute the prescribed steps, performance does not improve and the observed collapse still occurs at roughly the same point. This is noteworthy because finding and devising a solution should require substantially more computation for search and verification than merely executing a given algorithm. This further highlights the limitations of reasoning models in verification and in following logical steps to solve a problem, suggesting that further research is needed to understand the symbolic manipulation capabilities of such models. Moreover, we observe very different behavior from the Claude 3.7 Sonnet thinking model In the Tower of Hanoi environment.
The model's first error in the proposed solution often occurs much later, around move 100, for when you have 10 disks, compared to the river crossing environment, where the model can only produce a valid solution until move 4. Note that this model also achieves near-perfect accuracy when solving the Tower of Hanoi with 5 disks, which requires 31 moves, while it fails to solve the river crossing puzzle with just n equals 3, which has a solution in only 11 moves. This likely suggests that examples of river crossing with n greater than 2 are scarce on the web, meaning LRMs may not have frequently encountered or memorized such instances during training. In other words, it is very, very difficult to test these models, where you need clean models that have not absorbed contaminating information that allows them to appear to be creating new thought, as opposed to just finding something from the past from the past. So this work by Apple's researchers is full of terrific insights that I want to commend to anyone who's interested in obtaining a more thorough understanding of where things probably stand at this point in time. I've got a link right under the title at the beginning of this in the show notes.
So here's what the researchers conclude. They said in this paper we systematically examine frontier large reasoning models through the lens of problem complexity, using controllable puzzle environments. Our findings reveal fundamental limitations in current models. Despite sophisticated self-reflection mechanisms, these models fail to develop generalizable reasoning capabilities beyond certain complexity thresholds. So I'm going to repeat that, since I think that's the essence of this entire paper. Our findings reveal that, despite sophisticated self-reflection mechanisms, these models failed to develop generalizable reasoning capabilities beyond certain complexity thresholds. So the models are doing much better at doing what their simpler LLM brethren have been doing, but the difference is fundamentally quantitative, not qualitative. Apple continues.
We identified three distinct reasoning regimes. Standard LLMs outperform LRMs at low complexity. Lrms excel at moderate complexity and both collapse at higher complexity. Particularly concerning is the counterintuitive reduction in reasoning effort as problems approach critical complexity, suggesting an inherent compute scaling limit in LRMs. Our detailed analysis of reasoning traces further expose complexity-dependent reasoning patterns, from inefficient overthinking on simpler problems to complete failure on complex ones. These insights challenge prevailing assumptions about LRM capabilities and suggest that current approaches may be encountering fundamental barriers to generalizable reasoning.
Finally, we presented some surprising results on LRMs that lead to several open questions for future work. Most notably, we observed their limitations in performing exact computation. For example, when we provided the solution algorithm for the Tower of Hanoi to the models, their performance on this puzzle did not improve. They gave them the answer and it didn't help. Moreover, investigating the first failure move of the models revealed surprising behaviors. For instance, they could perform up to 100 correct moves in the Tower of Hanoi, but fail to provide more than five correct moves in the river crossing puzzle. We believe our results can pave the way for further future investigations into the reasoning capabilities of these systems. And then, finally, under limitations they just said, we acknowledge that our work has limitations.
While our puzzle environments enable controlled experimentation with fine-grained control over problem complexity, they represent a narrow slice of reasoning tasks and may not capture the diversity of real-world or knowledge-intensive reasoning problems. You know they're algorithmic, not knowledge-based. It is notable that most of our experiments rely on black box API access to the closed frontier LRMs, limiting our ability to analyze internal states or architectural components. Furthermore, the use of deterministic puzzle simulators assumes that reasoning can be perfectly validated step by step. However, in less structured domains, such precise validation may not be feasible, limiting the transferability of this analysis to other, more generalizable reasoning. So, in other words, the only thing this is is what it is. It may or may not be more widely applicable and it may not even have any meaning or utility beyond the scope of these problems. There's not a great deal of real world, need you know, for stacking disks on poles, after all, but for what it's worth, it does track with the intuition many of us have about where the true capabilities of today's AI falls.
You know, using terms like comprehend or understand, or even reason, really don't seem to apply. They're used by AI fanboys, you know. Maybe they're just a lazy shorthand, but I don't feel that they're helpful. In fact, I think they're anti-helpful. So what I think we need is some new anti-anthropomorphic terminology to accompany this new technology. There's zero question that scale-driven computation has changed the world forever. Everyone is asking ChatGPT and other consumer AI more and more questions every day, and that's only going to accelerate as the benefits of this become more widely known. Ai does not need to become AGI or self-aware to be useful, and, frankly, I would strongly prefer that it did not. To that end, I doubt that we have anything to worry about anytime soon, and perhaps not even for the foreseeable future. Thus the title of today's podcast, the Illusion of Thinking, because I believe that the fairest conclusion is that's all we have today. It's useful, but it's not thought.
2:38:53 - Leo Laporte
Yeah, and I don't think it. Uh, you know anthony nielsen's asking a legit question is if they, how much they coach the lrm, you you can say to it, for instance, use code. And it might well have been able to do better had they said use code. There's things you can say like think harder that actually make a difference, but it doesn't change your main point, which is no, they're not thinking. Maybe they can do better. But even if they did better wouldn't necessarily mean they're thinking by any means.
2:39:28 - Steve Gibson
And I think, in the same way that we were initially astonished when these things started to talk and appeared to understand us it's like holy tomos. It is astonishing yeah, and so I think now what we're underappreciating is the amount of knowledge that is captured by these and that when we ask them to think more, think longer, think harder, more of that captured, what appears to be understanding, but isn't actually we get that out. We squeeze the sponge harder and we get more out of it.
2:40:13 - Leo Laporte
And that's, of course, what these companies are doing, as fast as they can, because everybody's competing to come out with the smartest solution. We should also note that this paper was written with the older models from Claude.
2:40:24 - Steve Gibson
They have 4.0 out now. Right, and as I said also, this is all a moving target. Yeah, I mean, it's Absolutely, and that's really the point. Though, leo, does it matter how, which model, how far into the future this goes?
2:40:40 - Leo Laporte
Probably not.
2:40:40 - Steve Gibson
Fundamentally, they're not thinking. Exactly, and they don't, I don't think they're going to. I think they're just going to be able to squeeze the sponge harder and get more of the juice out, but at some point they're not creating new juice.
2:40:58 - Leo Laporte
Right, that's exciting times. We'll see. I don't know myself Great, it was a great paper. I'm glad you explained it. I appreciate it. As always, I look to you Every week I say, oh, I can't wait till Tuesday.
2:41:14 - Steve Gibson
I wonder what Steve's going to say about this.
2:41:16 - Leo Laporte
And again, if anyone has a youngster around. Look at how gorgeous those puzzles are. Aren't they beautiful? Oh, they're fantastic, yeah yeah, there is a story just breaking that you might be interested in. This is from the Register Security researchers have managed to access the live feeds of 40,000 internet-connected cameras worldwide. These are not cameras intentionally made public. These are cameras improperly secured, and they did it with a browser, so just be. The US had 14,000 feeds total, allowing the access to the insides of data centers, healthcare facilities, factories and more. Wow, I imagine we'll be talking about that next week.
This is why you got to see every episode Security. Now we do it Tuesdays right after MacBreak. Weekly 1 30, pacific 4, 30, eastern 2030, utc. You can watch live. If you remember the club you got behind the velvet rope access in the club twit discord, but there's also for everybody, youtube, twitch, tiktok, xcom, facebook, linkedin and kick. So there are plenty of places. Uh, you can watch. Most people don't watch live, uh. 99 of the audience watches after the fact because it's a podcast, so we make copies available, uh, of both audio and video on our website at twitchtv. Slash sn steve has actually some unique versions of the show. He's the only guy who hasa 16 kilobit audio version which, if you don't know, is about a quarter of the demand for that.
But he's also got a 64 kilobit audio version, which sounds perfectly fine. That's good quality, but it is one half what we do, because for technical reasons we need to do 128. He also has the transcripts. No one has those except steve, carefully crafted by Elaine Ferris. So that's nice. Not AI, but a real court reporter.
2:43:13 - Steve Gibson
She's going to a family member's graduation, by the way at the end of the week, so this week's transcript will be a little delayed. Of course, you won't know that until you're reading it and you will have come to the end of the transcript.
2:43:25 - Leo Laporte
So this is why I'm reading it.
2:43:27 - Steve Gibson
At least now you know why.
2:43:28 - Leo Laporte
to the end of the transcript, so this is why I'm reading it. At least now you know why that and the show notes and a lot more available at Steve's website, grccom. When you get there you might want to go to grccom slash email because you can sign up so that Steve will not, out of hand, reject your emails. You'll whitelist your email address and you can even check boxes there. They're unchecked by default because steve's a good guy, but you can, if you wish, subscribe to his newsletter, his weekly show notes newsletter you'll get usually the day before the show comes out. Uh, and also, uh, he does a very rare mailing when something new comes out which I know you want to know about, like his, his DNS benchmark coming out soon.
2:44:09 - Steve Gibson
I'll have something to say about that soon, yeah.
2:44:12 - Leo Laporte
No hurry, I'm not rushing you, I just mentioned it, just saying, while you're there, you might also want to pick up Spinrite. This is the way Steve makes a living. It's his bread and butter. It's the world's best mass storage, maintenance, recovery and performance enhancing utility, suitable for both spinning drives and ssds. Current version is 6.1, just got updated.
Uh, you can find out more and buy a copy, which you should, at grccom. There's also a youtube channel with a video from this show. Uh, great way to share clips if you. You know, here's something you say god, I have to tell the boss about this, or my, my aunt or my friend, whatever Good way to do it. Everybody has access to YouTube. You can clip it out on YouTube and send it to them. Also, of course, you can subscribe because it is a podcast and your favorite podcast client and get it automatically. If you do that, leave us a five-star review so that everybody knows how great this show is. And if you're in the club, or even if you're not in the club, you might want to subscribe to our free newsletter. We have one, too, comes out every week twitter tv slash newsletter. It's free and it will keep you up to date on what's coming up on this show and all the other shows that we do steve. Have a great week.
2:45:22 - Steve Gibson
We'll see you next time we'll see you on the 17th Yay.