Security Now Episode 915 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for Security Now. Steve Gibson is here with lots of topics on the agenda. We're gonna kick it off with four extremely serious zero day flaws in many Android devices. Find out if yours is at risk. Then we'll talk about TikTok, the move to ban, and some real scary stats and information about the d i drones from China. All of this coming up next on Security Now, podcasts you love
... (00:00:33):
From people you trust. This is TWiT.
Leo Laporte (00:00:41):
This is Security now with Steve Gibson. Episode 915, recorded Tuesday, March 21st, 2023 flying Trojan Horses. Security now is brought to you by Drata.. To often security professionals are undergoing the tedious, arduous task, manually collecting evidence. Theta say goodbye to the days of manual evidence collection and hello to automation. All done at rota speed. Visit drata.com/twit to get a demo and 10% off implementation and by ACI Learning. Tech is one industry where opportunities outpace growth, especially in cybersecurity. One third of information security jobs require a cybersecurity cert To maintain your competitive edge across audit IT and cybersecurity readiness visit go.acilearning.com/twit. And by xpressVPN. Using the internet without express VPN is like having a first aid kit, but not keeping it stocked. Protect your data and identity every time you go online with the number one rated VPN provider today. Visit expressvpn.com/security now to get three months free on a one year package. It's time for security. Now, the show we get together and talk with this guy right here, Steve Gibson all about, well, everything on his mind, including security. Hi, Steve. Yo Leo,
Steve Gibson (00:02:17):
Welcome. Great to be with you again for the Flying Trojan Horses episode.
Leo Laporte (00:02:24):
<Laugh>. We've been working with Mid Journey Stable diffusion and others to generate some flying Trojan horses having some difficulty, oddly enough, but we'll get a, yeah, we'll get a D for
Steve Gibson (00:02:33):
You. You got something that's pretty good. But I think we've got a lot of fu I know we have a lot of fun things to talk about this week on our time Limited Quest to answer today's burning questions. One of them cause us to wonder how worried should Android smartphone users be about Google's recent revelation of four serious flaws in Samsung's bass band chips. Also, what great idea should the N P M maintainers steal? What is it that nation states increasingly want to have both ways? What crazy, but perhaps inevitable change is Google Telegraphing that it might be getting ready to push on the entire world? Was it possible to cheat@chess.com? And what did checkpoint researchers discover? What's the most welcome news of the week for the United States infrastructure? And if Trojan Horses could fly, how many propellers would they need? <Laugh>, the answers to those puzzles and
Leo Laporte (00:03:43):
Rules really,
Steve Gibson (00:03:44):
Really coming up next on security.
Leo Laporte (00:03:46):
Now you're gonna answer that. Are you? That's right. Really? All right. I look forward to it. But first, a word from our sponsor Drata. <laugh>. How many propellers with Drata? Hmm, hmm, hmm. Drata is your your number one place to go if you are still suffering with the tedious time taking painstaking collection of evidence, manual collection of evidence for your, your security, and for preparing for your audits and things like that. If your organization is finding it difficult to achieve continuous compliance as it quickly grows and scales, you need to know about draha as manual evidence collecting, slowing your team down. Of course, it is. As a leader in cloud compliance software, that's what G2 says. Drata streamlines your SOC to your ISO 2700 0 1, your P C I D S S, your G D P R and other, your hipaa, other compliance frameworks.
(00:04:49):
Providing 24 hour continuous control monitoring. You focus on scaling security. Let Drata collect all the evidence you need for compliance with a suite of more than 75 integrations, Stratta easily integrates with your tech stack through applications like a W s and Azure and GitHub, and Okta and CloudFlare. Countless security professionals for companies like Lemonade, love them, notion. Use that every day. Bamboo hr, they've all shared how crucial it has been to have drta as a trusted partner in the compliance process. Drta personally backed by S V C I. Why should that matter? Well, that is a syndicate of ciso, angel investors who presumably know exactly what the pain points are in their businesses. They come from some of the world's most influential companies. And when they sawada, they said, yeah, that's it. That's what we need. Drata allows companies to see all their controls, easily map them to compliance frameworks.
(00:05:54):
So you get immediate insight into overlap. Companies start building a solid security posture. They can achieve and maintain compliance. They can expand their security assurance efforts, and they can do it all. At Drata speed. Drata's automated dynamic policy templates. Support companies new to compliance help alleviate hours of manual labor. You'll love the integrated security awareness training program. The automated reminders, those make sure employees get onboarded smoothly and efficiently. Effectively, Andrada is the only player in the industry to build on a private database architecture. So your data can never be accessed by anyone outside your organization. Andrada is a partner, a trusted partner. They will work with you. Every single Drata customer gets a team of compliance experts, including a designated customer success manager. They're there for your success, right? In addition, they've got a team of former auditors with a total of more than 500 audits.
(00:06:56):
They're there for your support and council. You can ask, Hey, you know, if you were auditing us, what would you be looking for? Draw up. Make sure that you're never left holding the bag. They've got a consistent meeting cadence. It's very thorough. They keep you on track to make sure there are no surprises, no barriers, and you'll love Rod's pre-audit calls so you can prepare for when audits are coming. With Jada's risk Management solution, you can manage end-to-end risk assessment and treatment of workflows. You can flag risks, you can score them. You can decide whether to accept, mitigate, transfer, or avoid them. Drata maps appropriate controls to risks. Simplifying risk management, automating the process. Andrada Trust Center provides real-time transparency into your security and compliance posture. And that really helps when you're going out. You're reaching out for sales or, or security reviews. You'll improve your relationship with your partners, with your customers. They'll love seeing all of this. Say goodbye to manual evidence collection. Say hello to automated compliance at drata.com/twit. Drata.com/twit. Bringing automation to compliance at Drata speed. drta.com/twit. We thank of so much for supporting Security Now, the work Steve's doing here, and you support it too, when you, you go to that address and make sure you go to the full address drata.com/twit so they know you saw it here. Thank you Drata. Now to the picture of the week
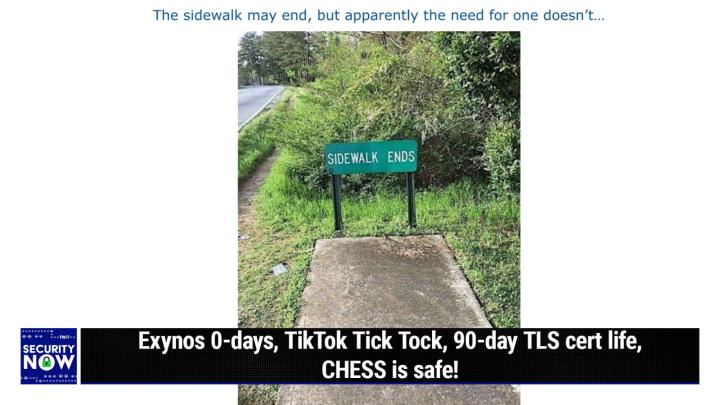
Steve Gibson (00:08:36):
<Laugh>. So, okay. You, you know those, what what this reminds me of is, is the old school railway sightings where it just, it ends in, in like, you know, it's just a stub and you've got this, this industrial strength looking barrier at the end. Typically remember it like it had two big pistons that were spring loaded, right? Right. So that if any cars like rolled, tried to roll off the end of
Leo Laporte (00:09:07):
Tracks, keep going off the end. Yeah,
Steve Gibson (00:09:08):
Exactly. Kind of give it a nice That's what this
Leo Laporte (00:09:11):
Is gentle. Yeah. Yes. Keep you from going off the end.
Steve Gibson (00:09:14):
Except for people. Right? So, so we have a, we have a sidewalk which stops and as, I guess some municipal code required in order to make it very clear, maybe it's the, like, keep skateboarders from, from hitting the bush that is after the sidewalk. There's a sign across it that says sidewalk ends. You know, very much like that other one. We had the gate that said, you know, sidewalk closed. Yeah. There, there, there, there was actually a sidewalk beyond the gate, but
Leo Laporte (00:09:46):
It was closed. But
Steve Gibson (00:09:47):
It was closed for some reason. Here,
Leo Laporte (00:09:49):
There's no sidewalk. So of course
Steve Gibson (00:09:49):
There, there was a well-trodden path around that, that closure and look, and then apparently there
Leo Laporte (00:09:55):
Is a trodden path to the left <laugh>.
Steve Gibson (00:09:58):
Yes. Well, now, and that, that's actually the point is that, so this sidewalk ends into what looks like just like a big bush. Mm-Hmm. <affirmative>. And one wonders, if they didn't feel like tackling the bush, or if the bush came after the end of the sidewalk or before. We really don't know the sequence of events here, but the need for a sidewalk does not end even though the sidewalk is That's exactly right. <Laugh>,
Leo Laporte (00:10:19):
Thank you for observing that. You know, just stop and go back.
Steve Gibson (00:10:23):
Exactly. What are you gonna do? Like, oh, Martha, we have to turn around now. So no. Instead they, the clearly many people have said, oh, look, there's a path to the left of the end of the sidewalk. We'll just continue along. That I bet
Leo Laporte (00:10:40):
Was, I bet there wasn't for a while. And then they made one.
Steve Gibson (00:10:43):
Oh and boy, this is, you know, now I don't think we're ever gonna get a sidewalk. No. Because the problem has been solved.
Leo Laporte (00:10:51):
This is a pet peeve of mine all over petal Luma, because of poor planning and, and malfeasance in the city council and so forth, there are streets with no sidewalks. I could walk to work easily, except I take my life in my hands because there's no sidewalk for half the route. And you're walking in the street. Yeah. And it just irks me. It, it, it, it's really fortunately they're starting to put a sidewalk in out here. Eventually we're gonna have a sidewalk. I don't know if we'll go all the way to my house, but I would like to walk to work. It's only a couple of miles, but I don't, it's, I don't dare, you know, put it in sidewalks. Yeah. People let people walk. Anyway, on we go. Yes.
Steve Gibson (00:11:32):
So one of the more worrisome revelations of the past week came to light last Thursday when Google's Project Zeros standard non-disclosure deadline expired 90 days after they had informed their Android hardware and software partner Samsung, of the 18 separate vulnerabilities they had discovered lurking inside Samsung's widely used even by Google's pixel phones exos modems. And here's the big news. Four of those vulnerabilities are as bad as any can get for an always connected smartphone. And in fact, those four vulnerabilities are so bad that Google has decided to make a rare exception to their standard disclosure policy. You know, which is like <laugh> fix it by now, by by 90 days or else? Well, not else in this case, for the sake of the world. They've con they are continuing to hold back details cuz it is that bad. Is
Leo Laporte (00:12:44):
This different than the SS seven broadband baseband exploit? Is this a new this is a
Steve Gibson (00:12:50):
New one. Oh, yeah, yeah, yeah. This is not an exploit against the SS seven protocol. These are a, as they call them, internet to baseband remote code execution vulnerabilities, which requires zero click, no, nothing click. I I
Leo Laporte (00:13:08):
Just need to know your phone number. That's
Steve Gibson (00:13:09):
It. That's exactly right. Horrible. Okay. They, so they said in late 2022 and early 2023, project zero reported 18 zero day vulnerabilities in EXOS modems produced by Samsung Semiconductor. The four most severe of these 18 vulnerabilities allow for internet to baseband remote code execution tests conducted by Project zero. Confirm that those four vulnerabilities allow an attacker to remotely compromise a phone at the baseband level. That is, you know, underneath the operating system, down at the, at the chip, at at, at the, the cellular modem chip level with no user interaction and require only that the attacker know the victim's phone number with limited additional research and development, we believe said Google, that skilled attackers would be able to quickly create an operational exploit to compromise affected devices silently and remotely. In other words, you now know what all of the state level actors and for example, what the NS o group in Israel are busy doing is like, what, what, what, what, what, what?
(00:14:36):
Like, you know, come on, go figure it out. So they said the 14 other related vulnerabilities were not as severe as they require either a malicious mobile network operator. In other words, they're, it's gotta be carried by the, by the cellular protocol or an attacker with local access to the device. Okay. Ask for where these chips are in use and thus, what devices would be vulnerable attack targets. First of all, none of our listeners, unless you are, you know, the king of Siam or something, probably need to worry, right? These, this, this would only be a targeted attack script. Kitties are unlikely to ever get access to this. But, you know, if you might be a target, then pay attention to these model numbers. So they, Google said Samsung semiconductors advisories provide the list of EXOS chip sets that are affected by these vulnerabilities based on information from public websites that map chip sets to devices affected products likely include mobile devices from Samsung, including those in the S 22, M 33, M 13, M 12, A 71, a 53, a 33, a 21 s, a 13, a 12, and a zero four series mobile devices from Vivo, including those in the S 60 16 S 50 S six X 70 x 60, and X 30 series.
(00:16:14):
The pixel six and pixel seven series of devices from Google and <laugh>, any devices that use the XOs auto as in automobile, T 51, 23 chip set. Now, Leo, I'm not hip enough to like these model numbers. Are these current smartphones? These, these, these series? Do you know like how, how recent these things are not clear to me. Wait, they, they said we expect Hold on patch.
Leo Laporte (00:16:46):
I was, I was over here we're painting, I was painting the ceiling. Wait a minute. Hold on. I'm back. Yeah. The s yes, I think it is the S 23 is the current Samsung phone, and I believe that has that XOs chip in it. And okay. Sam, you know, Google in its pixel phones. This is the pixel seven.
Steve Gibson (00:17:08):
Okay. So six and seven, they, they both do, Google knows that they
Leo Laporte (00:17:11):
Have Samsung chips, so, okay. They never said exos. In fact, they didn't wanna say Samsung, but then we found out Uhhuh <affirmative>. So now we know. Yeah, okay.
Steve Gibson (00:17:22):
Okay. So they, they, they said we sorry to make you run a lot,
Leo Laporte (00:17:26):
A lot of, a lot of modern smartphones have Qualcomm,
Steve Gibson (00:17:30):
But okay. Right.
Leo Laporte (00:17:31):
These don't, and the Samsungs don't. So there you
Steve Gibson (00:17:34):
Go. Of course not gonna use
Leo Laporte (00:17:36):
Qualcom. Yeah, no. They're gonna use xo. Yeah. Right.
Steve Gibson (00:17:38):
So they said goo Google said, we expect that that patch timelines will vary per manufacturer. They said, for example, affected devices, received fixes for all four of the severe internet to baseband remote code execution vulnerabilities in the March, 2023 security.
Leo Laporte (00:17:58):
Oh, we came out about a minute ago. Okay, fine.
Steve Gibson (00:18:01):
Okay. Thank you. Right. And, but, but, but this also says, you know, one of the things that we've said is if you, if you care about your, your Android smartphone security, then you really want to be with someone who is gonna be patching responsibly. And that's gonna be Google and Samsung. Yep.
Leo Laporte (00:18:21):
There it is. The March update. This is it. Yep.
Steve Gibson (00:18:24):
Yep.
Leo Laporte (00:18:24):
And they don't,
Steve Gibson (00:18:25):
They said, in the meantime, users with affected devices can protect themselves from the baseband remote code execution vulnerabilities mentioned in this post by turning off wifi calling and voiceover l t e data in their device settings. So there is a workaround again. So it's, if you only leave old school cellular connectivity on, then you're, you're safe. It is the internet and the data connectivity that, that, that is where the vulnerability comes from. And they said, as always, we encourage and users to update their devices as soon as possible to ensure that they're running the latest bills that fix both disclosed and undisclosed security vulnerabilities. See, I get,
Leo Laporte (00:19:11):
I get it now because I'm looking at the, the devices and they're all in the last couple of years, and that's because faulty and wifi calling is in the last couple of years. So this clearly in that part of it because for instance, the S 23, the newest Samsung is not on the list, which means they, they figured it out and fixed it, but but all of the stuff from the last couple of years, including the pixel six and seven are so,
Steve Gibson (00:19:36):
Yeah. Or, or maybe the 23 is not because they're using, you know, they, they, they certainly Samsung didn't know of the problem and fixed it in the 23.
Leo Laporte (00:19:46):
Right. Three, they must be using a different chip set
Steve Gibson (00:19:47):
Somehow. Yes. Or they just re-engineered it and that and the re-engineering accident didn't, didn't have the problem. Yeah. They
Leo Laporte (00:19:53):
Fixed it by accident. Yeah,
Steve Gibson (00:19:54):
Exactly. Yeah. So okay. So here's how Google has positioned their unusual decision not to fully disclose after 90 days, which isn't violation of, you know, like they're, it's been a hard and fast rule for them. So they said, under our standard disclosure policy project, zero discloses security vulnerabilities to the public, a set time after reporting them to a software or hardware vendor. In some rare cases where we have assessed attackers would benefit significantly more than defenders if a vulnerability was disclosed. We have made an exception to our policy and delayed disclosure of that vulnerability due to a very rare combination of level of access these vulnerabilities provide, and the speed with which we believe a reliable operational exploit could be crafted. We've decided to make a policy exception to delay disclosure for the four vulnerabilities that allow for internet to baseband remote code execution.
(00:21:08):
We'll continue our history of transparency by publicly dis sharing disclosure policy exceptions, and we'll add these issues to that list once they're all disclosed. In other words, they're, they're saying, we're not gonna tell you what's wrong, but we're at least gonna tell you that we're not gonna tell you. So, you know, you know this, there's something wrong even if you don't yet know what. So they said, of the remaining 14 vulnerabilities, we're disclosing four vulnerabilities that have exceeded Project Zero's standard 90 day deadline today. They said, these issues have been publicly disclosed in our issue tracker as they do not meet the high standard to be withheld from disclosure as the four bad ones do. They said the remaining 10 vulnerabilities of those 14 in this set have not yet hit their 90 day deadline. Remember, there were some that were disclosed only in 2023.
(00:22:05):
So ear, ear earlier this year, but will be publicly disclosed at that point if they remain unfixed. So, you know, the concern here is that this is these four, you know, this is a big juicy set of very, I mean, like infinitely essentially powerful exploits, which every very powerful and really bad actor in the world knows now, not only exists, but also roughly where it exists. And as always, we know that there's a huge difference between a patch being available and that patch being applied everywhere it's needed. Google's pixel devices, as we n noted, were early recipients of those patches, and presumably Samsung's devices will be too. But what about those vivo phones and the autos automobiles that incorporate those chips? Those will never be updated, of
Leo Laporte (00:23:06):
Course. Ah, nobody updates. Yeah.
Steve Gibson (00:23:09):
Right. Exactly. So, you know, as I said, random people, like most of us, almost certainly have little to fear since script kitties are never gonna get their hands on these. But this is the sort of vulnerability, which is exactly what the likes of Israel's n s o group is looking to add to their Pegasus smartphone spyware, as are other less public state level actors. So I would imagine that without exception, that, you know, the victims of the exploitation of these vulnerabilities would only those who are highly targeted and valuable mm-hmm. <Affirmative>, and of course it will turn their phone into listing devices, right? I mean, they'll, they'll suck out their, their messaging history and what they're doing and tracking, and also probably turn the microphone on in order to, you know, over you know eaves drop in real time. So anyway, you know, it's no comfort if you might be such a target, but hopefully you've got, you know, you're not using some random also ran Android device that might have this chip.
(00:24:19):
You've got, you know, a Pixel or Samsung, and it'll get fixed quickly. And as, as you know, as Google noted, there is a way that you could until your device is patched, you could make yourself secure if you were someone who should be concerned about that. So, of course, always good to keep our devices patches patched. But I, I doubt that most of us have anything, anything to worry about. And, you know, I don't <laugh> since I'm an iOS device user. So okay. I saw an interesting idea for wrapping the potentially hazardous N P M command within a protective shell. Now, N P M of course stands for the node package manager, you know, node as in O js JavaScript. It's the command line interface to the most popular JavaScript code repository. The idea for this protective wrapper comes from a company named Socket who says of themselves, they, they said, secure your supply chain, ship with confidence socket fights vulnerabilities, and provides visibility defense in depth and proactive supply chain protection for JavaScript and Python dependencies.
(00:25:39):
Now, they call their latest innovation safe N P M, and I'm gonna share a bit of their sales pitch, not because I necessarily think that our listeners should go get it, but because it nicely describes the open source package distribution risks that we've been covering now for quite a while. So, socket explains, they said Socket is proud to introduce an exciting new tool, safe N P M that protects developers whenever they use N P M install, which is, you know, the, the, the, the, the command that you issue at the command prompt to install some new package in, in into your system. They said, sockets safe, N P M C L I, you know, command Line interface Tool transparently wraps the N P M command and protects developers from malware, typo squats, install scripts, protest, wear telemetry, and more. 11 issues. And all today, when you run p m installed, it's difficult to know which transitive packages will get installed, whether those packages will execute, install scripts, or if those packages have been compromised by malware.
(00:26:58):
The average N P M package has 79 transitive dependencies. That means installing a single package with N P M install will, on average install 80 80 total packages. They say it's hard, if not impossible, for developer to audit, let alone even understand the full list of packages that will be installed. Most of us just cross our fingers and hope for the best worryingly. Any of these 80 packages can declare an install script, third party shell code that N P M will automatically execute during installation. While there are legitimate use cases for install scripts, it's also a favorite feature of malware authors. 94% of malicious packages used at least one install script. Developers also face the ever-present risk of typo squatting attacks, where an attacker publishes a package with a name similar to a more popular package. It's way too easy for a busy developer to make a typo when running N P m install and install the wrong package.
(00:28:18):
Sometimes, however, typos can have disastrous consequences, such as in the case of running N P M install Web with two Bs three instead of NPM install w e B three. Anyway, then they show an example of something quite malicious, hiding inside that double B version of the Web three package. Just, you know, a typo, W E B B three, somebody stuck it there hoping that somebody would type it by mistake and people did occasionally. So so they show that. Then they go on to explain, they said, this type of malware is all too common. Socket has helped to remove over 200 packages for security reasons, malware, ransomware, spam, et cetera, in the past 30 days alone. They said, to help you get a sense of the scale of the problem, we freely share samples of recently removed N P M packages with the public with the public for non-commercial research purposes.
(00:29:25):
In conversations with developers, we kept hearing the same request. Developers want a way to securely and confidently run N P M install without the fear of malware or rogue scripts infecting their systems. Our most popular product socket for GitHub already proactively scans GitHub pull requests for software supply chain risks, including typo squats, install scripts, and more than 70 customizable issues. But until the day, we have not had a good way to protect the developer's local machine from bad packages. That's why we're super excited to share this initial release of Safe NPM with you today. Socket is proud to introduce a new feature, safe npm blah, blah, blah, that, you know, and basically they then repeat what they said. When a developer attempts to install a malicious or risky package, socket pauses the installation and informs the developer about the risk, if any are detected. The developer is given the option to stop the installation and protect their machine before the package is executed or even written to disk.
(00:30:40):
Alternatively, the developer is also free to proceed and accept the risks. Okay, now, the reason I'm bringing all this up and wanted to cover, first of all, we've, every single one of those problems with N P M we've talked about on the podcast, you know, scripts being run and, and so forth. So I'm bringing this up not to take anything away from these guys. But they want $10 per month per user for this, which, you know, if you are only occasionally doing this, this seems excessive to me. But more than that, all of this sounds like something that the maintainers of N P M, that package itself and you know, and all other similar package managers ought to have already built into their basic command line offerings. You know, I have no way to directly influence that happening, but it may be that bit Warden now supports the superior Argon two P B K D F, thanks to our talking about it here, followed by some of our listeners suggesting it and implementing it and pushing it across the finish line.
(00:31:57):
So, if any of our listeners are able to plan a bug in the ears of the guise who are responsible for evolving N P M and the other major package managers, I think it's clear that it's well past time for the industry's various package managers to get proactive about protecting their users from all of this nonsense that's going on in the major repositories that they are, after all pulling their packages from, there's no sign of this abuse calming down. It's not like it's a passing fad. All of the indications continue to be that it is still ramping up since the package manager that goes out and retrieves the package on behalf of its user and then follows all of the dependency linkages and make sure that everything else that's necessary is there that function. You know, that, that, that exact function needs to evolve beyond being what it originally was a few years ago before this all began to happen with the repositories, you know, a simple no responsibility being taken, trivial command line retrieval and installation tool, it needs to shoulder those package managers now need to shoulder a lot more responsibility.
(00:33:20):
So anyway, when I saw this announcement from Socket, I thought, you know, nice that they go, these guys are doing that. You can get that right now from them. And depending upon, you know, your level of risk tolerance you may choose to do that. But what we really need is for this to be made universal and the package managers need to step up and start taking responsibility <laugh>. Okay? So things are getting interesting as an increasing number of governments are looking at their newly strengthened privacy laws and realizing that the behavior of the big tech giants is in contravention of those statutes. We've already been covering some of these events as they've been happening, but here are a few interesting pieces that we haven't talked about before. Last year, south Korea's privacy watchdog known as P I P C, the Personal Information Protection Commission imposed a pair of stiff fines on Google and meta for breaking the country's privacy laws by not obtaining oh boy, lawful consent from users and tracking their online activity for advertising purposes.
(00:34:47):
The P I P C imposed a 69,000,000,001 that's still pretty significant. 52 million fine on Google, and a 31 billion or 31,000,000,001, which is 23 million fine on meta. And, you know, both of those giants could have trivially paid the fines, but that would've set a dangerous precedent, and they would also likely have been required to stop doing what they had been fined over, which both companies appear to be certain is required for their businesses to thrive. So rather than pay up, both Google and Meta have instead elected to counter sue the P I P C in their recently filed lawsuits. Both companies argue that it's the website operators who should be responsible for obtaining individual user consent, not their platforms, which they contend only receive and aggregate this data, which is being collected by visitors to the websites. Okay, so there's one piece. Meanwhile, over in the Never Dull European Union, nearly three years ago, back in July of 2020, the CJ eeu, which is the CJ stands for Court of Justice for the eu, ruled that a transfer of data to US providers violate the rules on international data transfers, which are spelled out in the G D P R.
(00:36:26):
So the C J E U consequently annul the existing transfer deal privacy shield. This followed their previous annulment of the Safe Harbor Agreement back in 2015. So while all of this sent shockwaves to the tech industry, US providers and EU data exporters, they said they just largely ignored the case meta's Facebook like Microsoft, Google and Amazon has relied on the so-called standard contract clauses and supplementary measures to continue data transfers and calm its European business partners. So back in August, the Consumer Protection Agency, N O Y B filed 101 complaints against specific individual websites, which were still using Google Analytics and Facebook tracking tools, despite clear court rules making that use unlawful. I mean, it's, it's unlawful to do that and everyone's continuing to do it. So this N O Y B Consumer Protection Group said, okay, let's start turning up the heat here. And now we're talking about this because last Thursday, Austria's Data Protection Authority, which is the d sb, has ruled that Facebook's use of its tracking pixel directly violates the G D P R a guy named Max Shrems, the chairman of this N O Y B EU said Facebook has pretended that its commercial customers can continue to use its technology despite two court of justice judgements saying the opposite.
(00:38:13):
Now, the first regulator told a customer that the use of Facebook tracking technology is illegal. Oh, and I suppose it's not surprisingly that also the use of login with Facebook is also illegal since, as we've noted, it's essentially a tracking technology. The use of Google Analytics falls under the same regulation and has already been ruled unlawful. The concern is that if any of these tools are used, data are inevitably transferred to the US where the EU claims to be worrying that the data is at risk of intelligence surveillance. They, they, they quote, you know, FSA and blanket NSA rights to look at any that they want to. So, as I was thinking about this, what strikes me as more than a little ironic is that these governments who don't want their citizens webpages to contain tracking pixels or to use US-based services that might send data outside of their union, nor for their citizens to be using apps with ties to potentially hostile governments, are the same governments who are increasingly up in arms over their inability to intercept their own citizens end-to-end encrypted communications, not only when they might deem it necessary through a wiretap style search warrant, but also in the form of continuous background surveillance, monitoring of all textual and written communications for anything that, I mean, visual and written communications for anything that they might deem to be illegal or suspicious.
(00:40:02):
And of course, tracking their locations is part of that deal since it doesn't do any good to know what's going on if you're unable to go grab the perpetrators. So it's apparently okay for the governments to spy on and track their own citizens, but no one else should be able to. They're all about the rights of their own citizens, except when it's they who are violating them. And that's why I named this little piece of news. It's only a, it's only okay when we do it. So we got some more news to talk about, but Leo, I think we should take our second break. You
Leo Laporte (00:40:36):
Bet. Mm-Hmm. <affirmative>. Yeah, max Shrems actually has the laws named after him because he's such a active advocate of this kind of privacy they call it shrems.
Steve Gibson (00:40:49):
And, you know, I, it's gonna be up to legislators to figure out like what
Leo Laporte (00:40:55):
Happens. Yeah. Shrems was chiefly responsible for making sure data for a citizen of a country is stored in that country, not some other third party country. I think that's a fairly reasonable. Yep.
Steve Gibson (00:41:07):
And I think that's probably what's gonna happen is, is, is, you know, meta and Google are not gonna pull up stakes. They're only gonna move. They're just gonna move there. They're
Leo Laporte (00:41:13):
Stuff over there, network operations center over there. It's no big deal. Right? Right. Yeah. Right. Our show today brought to you as is our studio <laugh> by the great folks at ACI Learning. You may say, who are they? Well, you know them because ACI learning is part of it, pro or vice versa, I guess. They've, they've merged together enhance what IT Pro can do. And I know a lot of you who listen to Security now are happy it pro customers and users and have been over the years for the last decade. Our partners at IT Pro have brought you highly engaging, but also extremely informative IT training, which you've been using. I know many of you to level up your career or to level up your organization's IT team. Well, now that IT pro is part of ACI learning, you are seeing an expanded reach additional production capabilities and a variety of ways to learn, not just on demand or remote learning, but even in person learning as well with their ACI learnings hubs.
(00:42:19):
So that's very cool. So whether you're at the beginning of your career or you're looking to move up in your area, perhaps you're looking to move laterally in it, cuz there's really a lot of different things you can do in it. ACI learning is here to support your growth not only in it, but in cybersecurity and audit readiness too. One of the most widely recognized certs, some, something many people get before their first IT gig is the CompTIA A plus CERT compt courses with IT pro from ACI learning make it easy to go from daydreaming about a career, a fulfilling high paid job in a in an industry you love to actually launching it. Earning certificates opens doors to most entry level. It positions, it supplies potential promotions for those already in the field. It's not just the cert, not just the, the the, the, the, you know, certification that says, yeah, you've got that knowledge.
(00:43:11):
It's, it's the fact that you did it. That you went, you studied, you took the test. You, you, you, you did what you needed to do to get that cert that shows a future employer or your current employer that you, you've got what it takes. You know, this is, I I want this person working for us. Tech is one area, by the way, where the opportunity grows so much faster than than the the people available to fill it. There's more than a million open cyber security jobs right now. In fact, a recently LinkedIn study predicted that IT jobs would be the single most in demand category in 2023. And getting those searches really a big part of it. But a third of information security jobs require a cybersecurity certification. 23% of all IT jobs require a cybersecurity certification. You got those certs make a big difference in your desirability, right?
(00:44:07):
Organizations are starving for cybersecurity talent and that gap is just getting bigger and bigger all the time. The average salary for a cybersecurity specialist, 116,000 a year. A c i learning, by the way, that's the average. That means half are getting more right? A c i learning's information security analyst and cybersecurity specialist programs are a great way to get certified and get that job. The Global Cybersecurity Workforce Gap last year went up 26% over the year before. And I bet you when we get the numbers for 2023, it's gonna be even more. This, there's such demand for people with these skills and you can have them. ACI Learning offers, multiple cybersecurity training programs that can prepare you to enter or advance within this exciting industry. The most popular cybersecurity certs at ACI Learning includes C I S S P C council's Certified Ethical Hacker certified Network Defender, cybersecurity Audit School.
(00:45:09):
This is really kind of a newish category that's exploding is audit and cybersecurity frameworks. Knowing how to use those frameworks is huge, right? That's a big skill. Where and how you learn matters to aci Learning offers, fully customizable training no matter what kind of learner you are. In person on demand remote, you could take your learning beyond the classroom with ACI Learning IT Pro Audit Pro including Enterprise Solutions webinars, the Skeptical Auditor Podcast practice labs, learning hubs, where you can go in person and and and work side by side with your peers and instructors and their partnership program too, which is great for organizations. Let me also say congratulations cuz they have another podcast that Don p does. The it Pro Tech NATO podcast just had their 300th episode. Nice going Don. Really, I love these guys. We've known 'em forever. We've watched them grow and now I'm so pleased to see this merger with ACI learning cuz it really enhances all the things they can offer.
(00:46:14):
Tech is the industry where opportunity outpaces growth, especially in cybersecurity. And if you're listening to this show, you are already there. You just need that piece of paper. Now, one third of information security jobs require that cyber security certification. You need it, right? Maintain your competitive edge across Audit IT cybersecurity readiness with ACI learning, visit the website, go dot aci learning.com/twit. Go dot aci learning.com/twit. There is a special offer code. Yes, there is TWIT 30, TWIT three zero 30% off a standard or premium individual membership at it Pro. Again, the website, please use this too so they know you saw it here. Go dot aci learning.com/twit. In fact, do us a solid, tell 'em when you talk to 'em, I heard about you on security now it's really gonna help go ACI learning.com/twit. And we thank them so much for sponsoring the studio. And and, and for going forward. This is gonna be a great year for learners at ACI Learning. Go dot aci learning.com/twit. Now back to Mr. G.
Steve Gibson (00:47:33):
So while we're talking about nervous governments, I'll just note that a New Zealand well, that New Zealand, not a New Zealand, the New Zealand put a ban on the use of TikTok by their lawmakers and other parliament workers. This ban goes into effect actually at the end of next week as March ends. And the Scottish government hasn't quite gotten there yet, but officials were strongly advised to remove the TikTok app from all their government devices. Meanwhile, the Australian government has published a lengthy 113 page report it received from academics as part of its own TikTok investigation. The document describes, talk's deep ties to the Chinese Communist Party. Mean basically, it wasn't clear there was any news there, but they just wanted their own in order to to, to support their own plans. You know, it's viewed as preparation for a government-wide ban that may arrive shortly.
(00:48:41):
It's expected in the next couple weeks. And of course, over here in the states, the F B I and the US Justice Department have launched an official investigation into bite dance you know, talk's parent for using the TikTok application to spy on American journalists. And, and, you know, this is that old news that some rogue employees were, and it turns out in apparently indeed misusing TikTok to spy on one of Forbes reporters in an attempt to identify that reporter's sources and the by dance said that they fired the individuals who surveilled the journalists. So, you know, more of this drumbeat. And Leo, I know that you and your two co-hosts on Sunday talked about TikTok. I wasn't able to listen to that, but you said you were going to is there anything else that has happened?
Leo Laporte (00:49:35):
Well, I mean, so I mean, yeah it's a, it's imminent that they're gonna ban it, I think.
Steve Gibson (00:49:44):
So so you think in this country, in the us so Yeah, but not so not just governments, but everybody.
Leo Laporte (00:49:50):
Yeah. so apparently TikTok says that the Biden administration a couple of weeks ago told them, sell it or we're banning you. Whether they'll be able to sell it is a question because the Chinese government has to approve it. And as it seems unlikely that they will, they've said in the past, back when Trump tried this, yeah, we're not gonna sell it. Cuz there's technologies that we don't want anybody outside China to have AI technologies in which case that's gonna put the Biden administration up against the wall. And they're, you know, they, I guess they'll have to ban it. They haven't announced publicly. It was TikTok that said, so TikTok has the CEO of TikTok is testifying in front of Congress, right? Tomorrow, Thursday. I think it's tomorrow. Yeah. Yeah. Right. And apparently they've paid a bunch of influencers to come into Washington <laugh> to, to, to tell Congress don't ban TikTok. I mean, I kind of have the, a sympathy for that, but my son got his career start on TikTok. It was a huge launching pad for him.
Steve Gibson (00:50:51):
Well, and can you imagine, I mean, this would be unprecedented where an app that is this popular, literally, I mean, it would go dark,
Leo Laporte (00:50:59):
Right? That's my biggest concern is it's just a bad precedent for the American government to ban an app. You know, there'll be retaliation. American apps will be banned all in, you know, there are already many of them banned in China, but elsewhere, perhaps. And I just think it sets a bad precedent. Well, I understand the security concerns and I don't think any government person should have TikTok on their phone. No, they probably shouldn't have smart phones at all.
Steve Gibson (00:51:25):
You know, and, and every time we talk about Russia doing one of these bands, we roll our eyes, it's like, oh boy. You know? Yeah. Represser of regime.
Leo Laporte (00:51:32):
Well, you know, it's welcome here,
Steve Gibson (00:51:33):
Here we
Leo Laporte (00:51:33):
Come. Yeah, yeah. So I just, I just don't know. I don't, I don't absent solid proof that China right, is doing something with TikTok. Right. I understand the reason you might want to be feared and certainly I think it's well within the rights of governments and agencies and the Defense Department and so forth to ban TikTok on those government phones. That's fine. Yeah. But there's so many people, millions of people, creators all over the United States who make their living through TikTok. So I I have some concerns over that, you know? Wow. Yeah. Wow. I, I don't know what the answer is cause I understand the security concerns. I really do. Yeah. Yeah.
Steve Gibson (00:52:16):
Okay. So once upon a time when I was just a we lad, oh, you could purchase this a
Leo Laporte (00:52:23):
Hundred years, years ago. Yes,
Steve Gibson (00:52:24):
I know it's you, it's been a while. I had hair. You could purchase a certificate that would last longer than an all day sucker <laugh> ac actually it would last for a full five years. You know, those were the days. In fact, those certificates lasted so long that many companies would completely forget all about them until they were surprised when connections to their web servers suddenly began to fail. Yes. So then it would be a mad scramble to remember, ha how do we create a certificate signing request again? I don't remember. And you know, the guy who did that last time, well he hasn't been with us for a few years, so we need to, you know, refigure out the magic incantations that are required. So it was often a lot of excitement about every five years, give or take. Well, as we chronicled on this podcast since the days when I was a wela at the beginning of this podcast, over the years, certificates have largely done their job, but we've also had a lot of fun here.
(00:53:38):
And, you know, here on the podcast, examining the myriad ways they have fallen short through no fault of their own. One big topic for us was the whole mess of certificate revocation. That was a lot of fun. At one point, our longtime listeners will recall, I created and then immediately revoked my own certificate to demonstrate just how totally broken the Chrome browser's certificate revocation system was. It didn't e actually have one Chrome happily honored my revoked certificate that other properly functioning browsers knew better and they blocked it. This then forced Google to manually add an exception from my deliberately revoked certificate to Chrome's shortlist of known bad certificates. Even though Chromes still remain blissfully unaware of all other revoked certificates in the whole world, due to the fact that it's revocation system, as I said, never actually worked. After they did that, when I created another revoked certificate to demonstrate that they had special cased my first certificate by manually adding it to that short list, well they decided to just ignore me since I was <laugh> annoying them.
(00:54:59):
And I had proven my point. But almost inevitably, certificate expiration durations have been creeping downward. They first dropped from their original, you know, set it and forget it, duration of five years down to three years, then they dropped to two years. And now we're all at just one year plus one month. And while this is admittedly, you know, five times the work as it was when certificates lasted five years, cuz now they only last about one year, the people responsible for keeping certificates from expiring now tend to always have that in the back of their minds. I know, for example, the GRCs cert will reach its end of life at the end of July this year. So that's not far off. It's not like it's five years from now. So, oh yeah. You know, will I even still be <laugh> worrying about this then? So the story behind how this indu the industry certificate life was cut in half from two years to just one year is relevant because a more extreme version of it might be in our not too distant future.
(00:56:15):
Recall that three years ago, back in 2020, it was Apple who made the unilateral decision to stop supporting any certificate whose date of issuance was more than a year and a month earlier than its date of expiration. So for whatever reason, 365 plus 33 is 398 days. And 398 is the maximum distance you can have from not valid, not valid before to not valid after dates, which is what the, the, the certificates contain. So since Apple's decree would cause any and all iOS and MAC OS devices to reject any then non-compliant websites, the rest of the certificate issuing industry had no choice other than to drop their certificate lifetimes to what Apple was now gonna require. But now there's some scuttlebutt that Google with their ability to also unilaterally control what most of the web does through the operation of their Chrome browser, that they may be considering doing something similar.
(00:57:43):
But Google is talking about reducing certificate lifetime to just 90 days. Oh boy, <laugh>, that's a problem. So initially playing NICE Google says that it plans to make a proposal of this to the ca browser forum, right? C a b, the CA browser forum, which we've spoken of often back in the day when all this was happening more regularly. The, the this CAB forum is an informal group of browser vendors and certificate authorities who meet regularly to discuss, you know, industry-wide initiatives and like keeping everything on the same track. What, what, what, what cert, what field certificates should have and so forth. Okay? Now no one expects administrators of every server on the planet to be manually generating and freshly installing t l s certificates every three months. So the point like, I mean the explicit point of Google's recently telegraphed move is to move the entire industry to enforced certificate automation.
(00:58:58):
Acme A C M E is the automated certificate management environment as we know it debuted with the free certificate provider. Let's encrypt. But I know for example, that my chosen certificate provider DigiCert now also supports ACME Automation and there's a nice ACME client for Windows, which we'll be able to automate the process for my non Unix servers. So it'll be a matter of maintaining an account in my case and, and a balance with digit cert, or some means for them to pull money as needed. Then my various servers will be able to serve their own 90 days certificates and notify me only when there's some problem in Google's document proposing this certificate lifetime shortening. And you know, it's a polite proposal, right? Cuz I mean the, the, the presumption is this is gonna happen. Google said the following in support of the move to automate certificate issuance, they wrote the automatic certificate management environment, acme, which is R F C 85 55, seamlessly allows for server authentication, certificate request issuance, installation, and ongoing renewal across many web server implementations with an extensive set of well-documented client options spanning multiple languages and platforms.
(01:00:32):
Unlike proprietary implementations used to achieve automation goals, Acme is open and benefits from continued innovation and enhancements from a robust set of ecosystem participants. Although ACME is not the first method of automating certificate issuance and management. And then they, they, they cite C M P E S, T C M C and S C E P, which all predated it. They said it has quickly become the most widely used. Today over 50% of the certificates issued by, you know, globally for the web public key infrastructure rely on ACME 50%. Furthermore, they said approximately 95% of the certificates issued by the web P k I today are issued by a CA owner who has some form of existing ACME implementation available for customers. In other words, you don't ha you won't have, no one's gonna have to ch change cas. All of the cas 95% of them already support acme.
(01:01:41):
So all you have to do is ask for certs that way instead of doing it through the web interface. They said a recent survey performed by the Chrome Root program indicated that most of these ca owners report increasing customer demand for ACME services with not a single respondent expressing decreased demand. And this means that before long Acme support will become a standard feature of any server that needs to support TLS connections as most do and will. And in an interesting bit of coming full circle, the reason i I tied this back into certificate revocation is that with Google reducing certificate lifetimes to just 90 days, the fact that their premium flagship web browser does not and never has properly supported certificate revocation becomes much less of an issue since a ST stolen certificate would on average only be useful for half that period of time, about six weeks before its short, life came to an end. And just to be clear, there is no timetable for any of this, but it does appear to be a thing and it would likely behoove anyone who is now in the process of set setting up any new server environment to plan to implement ACME Automation sooner rather than later maybe from the get go. Yeah. I certainly would if in, in my case, because the change does make sense and the writing does appear to be on the wall. It's,
Leo Laporte (01:03:26):
Yeah, I don't mind if it's automated. I mean, right now we're going through this hassle. We've got a three years paid certificate, but every year we have to update it. Yep. And we just went through that with a bunch of servers. If we can implement Acme everywhere, I mean, I use Let's Encrypt and that's three months and it's automatic and it's fine. Yep. So I guess if we, we can implement Acme everywhere it's, hmm. I mean there are definitely gonna be people who know how to get a new certificate with a CSR and all that who don't know how to set up a script like Acme.
Steve Gibson (01:04:00):
Yeah, I I'm sure this is gonna cause some pain. Yeah. And and Google's point is, I mean, the, they recognize that, that they're pushing the world. They're, they're taking the position that, that, you know, from what we've observe observed on the podcast, security changes move very slowly. If we can get Acme in place such that certs only have a 90 day life, then we will be similarly be able to roll any other changes in certificates, like more use of elliptic curve certs, or we decide we want to change to post quantum certificates that make it even much easier. Yeah. Oh my God. It'll be automatic, right? Essentially. Right. So, so I, again, you know, we always see that these sorts of changes are, are difficult to force down everyone's throat, but at some point it makes sense to do that. And, you know, yeah, Google is gonna be the bad guy this time. Yeah. The bad cop. Leo, yes. You'll be glad to know that chess is safe.
Leo Laporte (01:05:09):
<Laugh>. I actually know a little bit about this, but I'd like to hear what you, what your story is.
Steve Gibson (01:05:14):
Yeah. So in their blog posting title, checkmate checkpoint research exposes security vulnerabilities on chess.com. They describe how they discovered, reported, and helped fix vulnerabilities in the popular chess.com platform. Now, for those who don't know, chess.com is the world leading platform for online chess games with over 100 million members and more than 17 million games played per day. I I thought that ratio was interesting. A hundred million members. Yeah. 17 million games per day. Yeah. So it functions as an internet chess server, a news website, and a social networking platform with a strong focus on community building, community-based forums and blogs which allow players to connect with each other, socialize, share thoughts and experiences, and learn from each other about playing chess. Chess.Com also conducts global championships, which consists of prize money to the tune of a million dollars for the winner and the coveted chess.com global champion title.
(01:06:26):
So Checkpoint decided to take a close look into the functioning of chess.com cuz there had been some allegations of cheating in the past. What did they find? They found a number of ways that the communications with the site could be manipulated to cheat. They discovered that it was possible to win by decreasing the opponent's time and winning the game over time without the opponent noticing what had happened. They also discovered that it was possible to extract successful chess moves to solve online puzzle challenges and win puzzle ratings. To do this, they intercepted the communications between the client side, you know, the player and the server, the chess.com website. What they discovered was that the server was accidentally sending the correct solution to the puzzle. Oh, I could use that <laugh> to the client side. Okay. <laugh>. And that allowed a cheating client to abuse and cheat on puzzle championships.
(01:07:38):
Hmm. In which the winner gets prize money by simply submitting the correct moves that the server was inadvertently providing. And also it was possible to modify in that case also the elapsed time it took to consider the solution. And finally, they discovered that in communication between two friends on the platform after approving the friend's request to connect an attacker or somebody, you know taking an attacker role is able to intercept the request with a proxy tool and succeed in both manipulating game timing, which allows a quick win and in solving a puzzle, which raises his score and the value on the platform. So the good news is, today, thanks to checkpoint's work, the game of chess as played@checks.com is safer and fairer than ever before.
Leo Laporte (01:08:33):
I like the ir because in fact, most chess.com cheating and most online cheating in chess has nothing to do with a hack. Right? It just has to do with me having my stock fish chess game running at the same time on my phone as I'm on chess.com and entering the moves in. And that unfortunately is not a hack that's a little harder to fight. Actually, it's fascinating to see how they fight it because it in
Steve Gibson (01:09:00):
There is deep learning at chess com.
Leo Laporte (01:09:01):
Yeah. Well, the way, so the way you do it is chess computers calculate the current balance of the game in cent pawns a hundredth of a pawn, right? And among two human players, the lead change is much more variable. In Setons, you know, might be a hundred or 200 Setons, and then up and down and up and down. Ah, but when a machine plays, it's a fairly linear gain, gain of cent pawns. You don't have the same variations. And so it is a little easier to spot a machine player because it doesn't make the same mistakes that humans do, humans blunder. And and so if a machine never blunders, and then there's other ways to tell, they play lines that are kind of more machine-like although that's getting harder and harder because as they get better and better, they look more and more like humans, but really they play too well. That's the, that's the easiest way to spot 'em. <Laugh> <laugh>. Right? And if you, for instance, it's been a big scandal super grand Master named Han Neiman has been accused of cheating because his rating went up, you know, went up normally fairly steadily and suddenly soared in a very unusual way. And furthermore, his, his results in games where he's over the board and there are measures taken to prevent cheating. His results are not nearly as good <laugh>.
Steve Gibson (01:10:33):
So, and, and, and he was actually playing against Magnus, wasn't he?
Leo Laporte (01:10:36):
Magnus lost a game to him, which is very rare. Magnus is easily the best player in the world lost a game to him, and then, and then you, you can't accuse somebody of cheating. That's not allowed. So he intimated
Steve Gibson (01:10:51):
And not very sportsmanlike. Yeah.
Leo Laporte (01:10:53):
So he intimated there was something not kosher, and that got the investigation going. And then in the second game with him, he resigned after one move to kind of further indicate his displeasure. There's been investigations since. There's no conclusive evidence that cheated. Wow. But there are, there's a lot of circumstantial evidence.
Steve Gibson (01:11:13):
And it's also really interesting that, that when he's in an environment where he cannot receive any help, right. He's not playing as well.
Leo Laporte (01:11:20):
So, so the, the single thing that they did was they delayed the broadcast. So normally streamed live, and so a a accomplice at home could be watching the game live, and somehow we don't know how transmit the moves
Steve Gibson (01:11:34):
Communicating back to
Leo Laporte (01:11:35):
His, but if they delayed the broadcast by 15 minutes, suddenly his, his results aren't as good. So it's a little suspicious. It's unknown really, frankly. Yeah. And now Magnus has stopped playing in the world championship. He's said, nah, I don't wanna play anymore. So it's So just computers When when computers got that good. We thought that's it for chess. Yeah. And it's turned out, no, it's been, there's been some issues, but p people, humans still like playing. They even like playing against machines as good as they are. Wow. Yeah.
Steve Gibson (01:12:07):
Okay. So in very welcome news, CISA has announced that they have started scanning the internet exposed networks of the US' critical infrastructure for vulnerabilities and warning those who are responsible. Yay. As we know, we've been covering other countries welcome announcements of their intentions and results from doing the same. And in some instances, their scans have turned up many important things that did need fixing. So it's very welcome news that now in the US CSA has begun doing the same thing here. SSA's announcement last week is titled CSA Establishes Ransomware Vulnerability Warning Pilot Program. And it too has already borne fruit. They said, recognizing the persistent threat posed by ransomware attacks to organizations of all sizes, the cybersecurity and infrastructure security agency announces today the establishment of the ransomware vulnerability warning Pilot <laugh>, the R V W P as authorized by the cyber incident reporting for Critical Infrastructure Act.
(01:13:25):
Boy, they love their acronyms. The C I R C I A of 2022 through the RV W P C I S A will determine vulnerabilities commonly associated with known ransomware exploitation and warren critical infrastructure entities with those vulnerabilities enabling mitigation before a ransomware incident occurs. Perfect. They said the R V W P will identify organizations with internet accessible vulnerabilities commonly associated with known ransomware actors by using existing services, data sources, technologies and authorities, including our free cyber hygiene vulnerability scanning service. What organizations interested in enrolling can email vulnerability csa.dhs.gov. And they finished CSA recently initiated the RV WP by notifying 93 organizations identified as running instances of Microsoft Exchange service with a vulnerability called Proxy, not Shell, which has been widely exploited by ransomware actors. This initial round of notifications demonstrated the effectiveness of this model in enabling timely risk reduction as we further scale the R V W P to additional vulnerabilities and organizations.
(01:15:02):
So that's all really good news. And of course, this begins as just, oh, we're just sticking our toe in the water to notify people of ransomware. Cuz of course, who could object to that? We can foresee that this is gonna become much broader as it proves itself over time. And I just think this is gonna have to become the way things go. Note that the cyber hygiene vulnerability scanning service they refer to is not open to the private sector unless the organization qualifies as a critical infrastructure provider in a, in an faq, SISs a answers the question, who can receive services by replying federal, state, local, tribal, and territorial governments, as well as public and private sector critical infrastructure organizations. And of course, as the guy I who created and launched GRCs Shields Up service 24 years ago, back in October of 1999, and that was by the way, 106,477,630 network scans ago, I've seen firsthand how important and effective this sort of proactive scanning can be.
(01:16:23):
And even more recently, Leo following our podcast number 3 89, which was January 30th, 2013, I quickly added that Universal plug and play, you know, u p and P scanner to Shields up. And since then it has informed 55,301 visitors that they have for some reason, universal plug and play publicly exposed. Yeah. So I think it's very clear that this sort of proactive scanning is where we have to go. It's just gonna be so important. And it, and, you know, you could, it's probably the local governments that, or, or you know, the, the, the, the regional national governments that need to do the scanning because their packets need to be above reproach, right? You just don't want anybody scanning organizations because they may be looking for vulnerabilities to exploit as opposed to vulnerabilities to notify the the responsible parties. So again, this is a change that has been coming for a while and you know, yay,
Leo Laporte (01:17:34):
Yay, yay, yay.
Steve Gibson (01:17:36):
Okay, we're gonna talk about flying Trojan Horses <laugh> after
Leo Laporte (01:17:41):
You,
Steve Gibson (01:17:42):
After you tell our listeners why
Leo Laporte (01:17:45):
We're here. Expressvpn. Yeah, that's right. And we're still working on our mid journey prompts. We're trying to get some flying Trojan horses for some reason the AI just refuses to let Trojan horses fly. They just, they're ground bound. I don't know why that is. Our show today brought you by Express VPN. N if you're not ground bound, if you get round, round, round, get around, you want ExpressVPN. Using the internet without express VPN is like not having your emergency kit Stockton ready ever go over to the first aid kit. And there's nothing in it I have that's no fun. Most of the time, you know, everything's fine, but when something goes wrong, and it always does, you're gonna wish you had that first day getting stocked up. You're gonna wish you had a vpn. We're gonna go on a trip soon, right?
(01:18:35):
We're gonna be on a cruise ship. We're gonna be on a cruise ship wifi every time we connect to that wifi at a hotel, at a cruise ship, at an airport, at a cafe. You're on the same network with a bunch of other people of dubious <laugh> origins. You know, and when they're on the same network as you, there's all sorts of things they can do. Your data is valuable, your laptop is valuable. Hackers can make a lot of money selling personal information about you on the dark web. You ever see a wifi pineapple at work? It's terrifying. But if you've got a VPN going, they can't even see that you're there. They just see a encrypted stream of nothing flying through the air without ever, ever being able to track it back to its origin. In fact, it doesn't take much technical knowledge to be a bad guy on a cruise ship or a hotel or an airport.
(01:19:26):
All you need is this, you know, a $60 wifi pineapple and then he smart 12 year old could do it. Not to mention your internet service provider, of course, that's your I S P at home, but it's also your carrier on your mobile. And when you're an out and about, it's whoever's providing the internet to you, that person can see everything you're doing and can, can capture it and sell it on to a data brokers and it's perfectly legal. Again, a VPN will protect you there. It creates a secure encrypted tunnel between your device and the internet so that no one can steal your data, no one can spy on you. And it's using strong encryptions, so you know, there's no way it can be hacked. The other advantage is the IP address you use when you do emerge on the public internet belongs to the VPN provider, not you.
(01:20:16):
But this does raise an interesting point. You are dependent on the security, the privacy of the VPN n provider. That's why I only use and only recommend Express vpn. They go kind of belt and suspenders on not tracking you. It's in their privacy policy. And that's, by the way, been independently vetted continuously is by third parties. I think it's Price Waterhouse Coopers does that. And they say, Nope. The privacy policy is exactly as they say. And this trusted server technology works exactly as advertised. That's the interesting part. So Express VPN servers all run a custom version of Debbie in the Linux operating system that wipes the entire drive and reinstalls every single time it's rebooted, which is every single day. So that's one. Even if they were writing to the hard drive, it would be erased every day. But better than that, when you spin up the server, and by the way, this is one of the beauty parts of Express vpn.
(01:21:11):
You put it on your phone, on your router, works on many routers. They also sell routers with Express VPN built in on your computer. You're, and you turn on Express VPN n with that big button, you say, turn on my protection. It spins up their trusted server, something they wrote and created using open source VPN technology. But they've wrapped it in something very interesting. It runs only in RAM and it is sandbox. It cannot write to the hard drive. So you're sitting in this, you know, virtual server that's isolated from everything else, cannot write to the hard drive. And the minute you close the vpn, it goes away. It's gone with no trace left of you. So that's the kind of thing you want. You also want a VPN provider who rotates their IP addresses. So it's not obviously a VPN provider. You want a VPN provider with servers all over the world.
(01:22:03):
So you can go to the fastest one, the nearest one when you need speed. And if you want to go to a different geographic location when we're traveling, I want to come, I wanna watch my F1 races on P n, I'll use Express VPN n to surf back to the US and be able to watch it. That's the kind of thing a great VPN can do. And only express VPN does a 100% privately securely and at a very affordable price. Now you're gonna say, I know there are free VPN providers. You bet browsers can provide 'em, operating systems can provide 'em, but I would submit <laugh>, if you are not paying, you are the product, not the customer. Pay and express VPN's very reasonable. Use our deal less than seven bucks a month for the best VPN service. Fast private, secure ExpressVPN.
(01:22:54):
That's what I use. That's what I'll be taking with me on our trip. Secure your online data today, visit expressvpn.com/securitynow EX P r ESS vpn. Don't ask me to spell vpn expressvpn.com/securitynow make sure you use that slash security now so they know that you saw it here. You'll get an extra three months free when you buy a one year package that brings it down to below seven bucks. A very, very good deal. I just renew every year cuz it's just, you know, it's really, you know, you won't always need it, but it's like your first aid kit. It's really nice to know it's there as you travel around. Express vpn.com/security now. We thank 'em so much for supporting the show and we thank you for supporting the show by going to that address so that you know, they know where you saw this lovely commercial <laugh>. Now back to Steve and flying Honey Monkeys.
Steve Gibson (01:23:52):
So yes okay, this sort of reality check time, but I think everyone's gonna find this interesting. A a large and significant group of fully bipartisan, not just token bipartisan senators have all co-signed a letter to SSA's director Jen Easterly, the letter requests that SSA examine the very popular drones made by D J I for evidence of China, that China might be covertly acquiring valuable information from them. Okay, in a minute we're gonna walk through a complete interesting and revealing, well conducted technical forensic analysis of DJ's drone controller software to learn exactly what's going on. Well, let's first set the stage because this just happened by looking at this letter, which reveals the politics, which are driving the concern. And for those who don't follow politics, you know, the names of the senators won't mean much, but for those who do, these are all senators, many of them senior that you'll have heard of this.
(01:25:04):
So this letter was signed by Mark Warner, Marsha Blackburn, Richard Blumenthal, John Thune, Jean SA Shaheen, Rick Scott, Kirsten Sinema, Todd Young, JD Vance, Ted Budd, Dan Sullivan, dead Fisher, Mike Braun, Cynthia Loomis, Tommy Tuberville, and Jerry Moran. So though series players here on the Senate, so here's what the senators are asking of SSA's director, they said, dear director Easterly, we write today regarding the cybersecurity risks posed by the widespread use of drones manufactured by Shez d i, innovation Technology Company Limited D j I to operators of critical infrastructure and state and local law enforcement in the United States. In short, we believe that given the company's identified connections to the Chinese Communist Party, the use of its drones in such sensitive contexts may present an unacceptable security vulnerability. We ask that the cybersecurity and infrastructure security agency cisa evaluate this concern and make the results of its valuation available to the public through the National Cyber Awareness System.
(01:26:23):
China's efforts to modernize the capabilities of the People's Liberation Army, including through their ministry civil fusion, I'm sorry, their military civil fusion strategy, which systematically blurs the lines between P L A and civilian science and technology research and development efforts are well documented. In October, 2022, the Department of Defense identified D J I as a Chinese military company operating in the US under section 1260 H of the William M Mac Thornberry National Defense Authorization Act for fiscal year 2021. Identification of this relationship between d i and the P L A suggests a range of risks to US operators of the technology, including that sensitive information or data could wind up in p l a hands indeed Huawei, another entity identified under Section 1268 has been credibly accused by the Department of Justice of misappropriating intellectual property and trade secret information from US companies. Yet despite these risks, the use of d i drones remains widespread throughout the us Here we go again.
(01:27:44):
Uhhuh <affirmative>. In 2021, it was reported that D j I controlled almost 99 0% of the consumer market in North America and over 70% of the industrial market. Yes, it's the only kind I buy <laugh>. I know, it's they're the best <laugh>. Right? Right. And in and Leo, you're doing your part to increase those percentages, <laugh>? Yes, I am. Every time I sink a drone <laugh>. And in 2019 it was reported that 73% of public safety operations are flown by the company's aircraft. As a result, the C C P may have access to a variety of proprietary information. Ooh. For, for in, for example, they don't have my information. For Right. Your yours is drowned. Yeah. For example, a 2017 Department of Homeland Security Assessment warned that Chinese companies had used grape production information gathered by a d i drone, purchased by a California wine producer to inform their own land purchasing decisions.
(01:28:58):
Even worse, ooh, worse than that, the widespread use of d i drones to inspect critical infrastructure allows the C C P to develop a richly detailed, regularly updated picture of our nation's pipelines, railways, power generation facilities and waterways, which I guess they can't get from their spice satellites, you know, orbiting overhead or their balloons. Anyway, they said this sensitive information on the layout, operation and maintenance of US critical infrastructure could better enable targeting efforts in the event of conflict. We appreciate that CSA has addressed the, this risk in the past, most notably in a 2019 industry alert stating the federal government's strong concerns with Chinese drones and warning entities to be cautious in purchasing them. However, over the past four years, more information regarding the scope of the problem has become available. And that's what we'll be talking about, including the official identification of D J I as a Chinese military company by the Department of Defense.
(01:30:10):
We therefore ask that SISs a revisit its analysis of the security risks posed by the use of d i manufactured drones and release the results of that analysis publicly through the National Cyber Awareness System. What do we know about? DJ's observed behavior three years ago. The security firm Grim went to a great deal of trouble reverse engineering DJ's software. Here's what they found, they said, given the recent controversy over D J I drones, a defense and public safety technology vendor sought to investigate the privacy implications of d i drones with the Android dj, I go four application to conduct their analysis. The vendor partnered with inactive and that's a group we've referred to before, a credible security firm who performed an in-depth dynamic and static analysis of the application. Their analysis discovered four main causes of concern within the D J I go four application.
(01:31:22):
Most notably, the application contains a self update feature that bypasses the Google Play Store. The application contains the ability to download and install arbitrary applications with user approval via the Weibo S D k. During this process, the Weibo s SDK also collects the user's private information and transmits it to Webo prior diversion 4.3 0.36. The application contained the mob sdk, which collects the user's information and transmits it to Mob Tech, a Chinese analytics company. And finally, the application restarts itself when closed via the Android swipe closed gesture. Thus, users may be tricked into thinking the application is closed, but it could be running in the background while sending telemetry requests to provide an independent review of the findings. The vendor then asked Grim these guys to validate syn actives findings. This blog describes they wrote Grimm's setup and Workflow for validating the syn active research using the techniques described in the following sections to perform static and dynamic analysis.
(01:32:45):
On the d i go four Android application, grim was able to verify and confirm the findings from syn active's report. The code associated with this blog post can be found in our GitHub repository. Okay. Okay, so let's follow along because it's much more interesting than just being asked to accept the conclusions without knowing where they came from. It's also interesting to learn how such an investigation is conducted. So they wrote, Grimm's researchers used two different setups. An arm-based Android six marshmallow, that's API 23 emulator and another with two physical devices, A rooted Nexus six and an Unrooted Motorola Moto 3g. The Android emulator is a part of Android Virtual Devices manager, a subsystem of Android studio that can be controlled through A D b, which is the Android debug bridge. Additionally, Android Studio is able to redirect all traffic to an H T T P proxy.
(01:33:52):
We redirected traffic through Burp Suite under which requests can be captured and intercepted. Frida. A dynamic instrumentation tool was also used on the emulator by directing, by directing, by directly pushing and running Frida server on the device. We chose a p i 23 due to the added certificate authority, certif certificate protections, which were introduced in Android 24. So the point was that their, their TLS proxying was easier under a A P I 23. The Nexus six P running Android n and A a p I 23 also was connected to a desktop through U S B and controlled through a d B. Both devices were connected to the same wireless network. The setup for analysis on this phone was similar to the emulator except for the proxy and certificate. The proxy was done with IP tables to redirect all traffic on ports 4 43 and 80 to Burp.
(01:34:53):
Originally we attempted to connect via U S B ethernet adapter, but we found that the behavior of the app was different from the more normal wifi setup. We used Frida to bypass S S L pinning on the Nexus six p. Additional testing was conducted with a similar setup using a Motorola Moto 3G running Android L and the O OSP Zap proxy. Okay, so that setup gives them a testing platform, the ability to view, extract, and debug the Android code through the Android debug bridge. And they have an effective shim, which allows them to transparently monitor all communications in the clear without encryption so they can see everything that's going on. They said the d i Go four Android application was heavily obfuscated utilizing both static and dynamic obfuscation techniques to thwart analysis. An active provided grim with a detailed writeup and scripts to de obfuscate the code and help analyze the application.
(01:36:00):
The first protection the application uses is a custom version of B A N G C L E Banky. This tool encrypts java bite code dot dex files, which can then be decrypted and loaded dynamically during runtime. To understand and defeat this technique, we can draw parallels to the well-known binary obfuscation technique packing, where the code contained within an executable is also decrypted and loaded during runtime. The two main methods of de obfuscating packed binaries are to statically analyze the packing routines and extract the data or dump the memory of the executable after the data has been decrypted. In the context of Android applications, we can do the same. There's been previous research on static analysis of Banky. Howevers was unable to apply the previous techniques to the D J I go four application as it is using a custom version of Banky rather grim utilized syn actives Frida scripts to search through the memory of the Android application at runtime and dump the decrypted dot decks Java bite code files with the dumped Java bike code files.
(01:37:18):
Grim was able to use Java decom compilers such as GA DX and Pro Cion to decompile the bike code and apti and obtain near accurate Java source code on which we can perform. They wrote static analysis in addition to protecting the Android Java bike code. The Java source code also features various static obs obfuscation techniques, most notably string obfuscation. Most of the strings used in the Java source code are obfuscated. However, this protection is rather simple to decipher as described bys inactive and then they turned out they were just base 64 encoded after being xor scrambled with a hard coded key. And they said additionally, the d i go four application uses obfuscated string getter classes. These classes define an accessor function, which takes an index to the desired string. These obfuscated strings can be easily recovered by decompiling, the relevant class, adding a main function that dumps the strings, recompiling the code and executing it.
(01:38:29):
And I'll just note that there's nothing at all nefarious about using string indexes. I did exactly the same thing in my design of squirrel. It's a very clean way of adding language independence to an application Throughout your code. You refer to UI display strings only by index and then a language pack provides the phrase dictionary, which the indexes point to. Anyway, they said, with the ability to decompile the Java code and decode strings within the Java code, as well as intercept and analyze the application's network requests, we were able to fully reverse engineer the application's execution.
(01:39:15):
Synap Synap sys report describes the d i Go Force custom update mechanism. This update service does not use the Google Play Store and thus is not subject to the review process as such. There is no guarantee that the application that is downloaded for one user matches that of another user. If G'S U update server is malicious or compromised by an attacker, it could use this mechanism to target individual users with malicious application updates. And this behavior is a violation of Google's developer program policies, which states an app distributed via Google Play may not modify, replace, or update itself using any method other than Google Play's update mechanism. Likewise, an app may not download executable code. For example, decks Jar or dot s. So files from a source other than Google Play using, they said using dynamic analysis grim researchers were able to intercept traffic pertaining to the update of the d i go four application Upon application startup or when using the check for updates option within the application, A request was sent to service hyphen ad H o c as it, you know, ad hoc.d.com, which responds with a URL to an updated application pk.
(01:40:54):
This APK file is downloaded directly from D servers via A U R L and they provide it. It's there, there's a d cdn.com and then a bunch of hicks. This update option completely bypasses the Google Play store giving D servers the ability to fully control the A P K downloaded, whether with malicious intent or not. When the server's response is received, the application prompts the user with the update notification. Once the user clicks on the update notification, they're asked to install the update. This update process does require the user to give the d j I go for application, the install unknown apps permission to help investigate the issue further grim, modify the server's response. Anyway, I I I go on in, you know, additional detail as do they following all of this. And you know, this all comes down to the app, yes, is able to pull updates from anywhere it wants to outside of the Google Play Store.
(01:42:08):
There are some SDKs, which, which do obtain significant personal information, which it's easy to argue they don't need. For example, at one point the app grabs the I M E I, the I C C I D, the MAC address, the Android id, the device name, and so forth, encrypts it using an R s a public key embedded in this Webo S D K and sends it. They, they basically fully reverse engineered this application. And, and yes, if you wanted to be worried, then here's an example. The, the, what what isn't said, of course, is that, you know what other apps are doing the same thing. They, they, they, they wrap this up finally under impact. And they said, given these findings, it's useful to consider the best and worst case scenarios for how these features are used. While they could just be slightly odd implementations for acceptable behavior, they could also be used in a much more nefarious way again, okay?
(01:43:23):
In the best case scenario, these features are only used to install legitimate versions of applications that may be of interest to the user, such as suggesting additional D J I or Webo applications. In this case, the much more common technique is to display the additional application in the Google Play Store app by linking to it from within the application. Then if the user chooses to, they can install the application directly from the Google Play Store. Similarly, the self updating components may only be used to provide users with the most up-to-date version of the application. However, this could also be more easily accomplished through the Google Play Store. In the worst case, these features can be used to target specific users with malicious updates or applications that could be used to exploit the user's phone. Given the amount of user's information retrieved from the device, d i or Webo could easily be able to identify specific targets of interest.
(01:44:31):
The next step in exploiting these targets would be to suggest a new application via the Weibo SDK or update the, the d i application with a customized version built specifically to exploit their device. Once their device has been exploited, it could be used to gather additional information from the phone, track the user via the phone's, various sensors, or be used as a springboard to attack other devices on the phone's wifi network. This targeting system would allow an attacker to be much stealth with their exploitation rather than much noisier technique such as exploiting all devices, visiting a website, regardless of whether DJ I or Webo utilize their application's functionality to target users, they have created an effective targeting system. As such, attackers who know of this functionality may attempt to compromise DJs and Weibo servers to exploit this functionality themselves. Given this risk, it's much safer to rely on Google to provide application validation and distribution security.
(01:45:47):
And okay, I got a chuckle out of that line. Since the overtly policy violating behavior, these guys have reverse engineered, demonstrated and observed for themselves. Oh, and I, I skipped over where they actually changed the U R L that was being queried and demonstrated the successful installation of an an arbitrary A P K. So it can indeed, there you go. You can do it <laugh>, improve the concept, anything. Exactly. Yeah. So anyway, what what, what I got a chuckle out of was that, you know, that this policy violin behavior was downloaded initially through the Google Play Store. Oh, so lot of good that did. Right? Right. I mean, as, as we know, there's, what is it? I don't know how I have it in my show notes a little bit later. How many millions of apps are on Google play? So the grim guys conclude saying this, they say this blog post, Grimm's efforts to validate syn active's privacy assessment of the D J I go four Android application and determine the impact of their findings.
(01:47:00):
After dumping the encrypted classes and setting up an emulated and physical test environment, grim performs static and dynamic analysis in order to reverse the application and validate synap syns findings. The d i go four application contains several suspicious features as well as a number of anti analysis techniques. Hmm. Not found in other applications. Hmm. Using the same SDKs Overall, these features are worrisome and may allow d i or Weibo to access the user's private information or target them for further exploitation. Okay? What wasn't directly addressed here was the application platform. This was not the analysis of some controlling code buried in a lawnmower. It's the code controlling what happens to video imaging being captured by the world's most popular aerial drones, which are in use not only by US citizens, but by US law enforcement and military on military bases in the US and elsewhere.
(01:48:15):
Is there any reason whatsoever to think anything nefarious is going on? No. Is there any solid evidence of misuse of this technology perhaps beyond suspicions about some data leakage from grape harvesting? Apparently not. Are the US senators wrong to be concerned? No. We now have inable proof that we have unwittingly invited hundreds of thousands of camera equipped flying Trojan horses into our midst, including into areas where there is danger of some of our nation's most private and sensitive operations being sent to a country with whom we appear to be becoming increasingly adversarial. So this brings us back, once again, this time armed with a beautifully clear example to the utter insanity of the situation we are currently in. None of this makes any objective rational sense. If we are doing anything more than merely paying lip service to security, we've walked into it with our wise, with our eyes wide open.
(01:49:41):
Why? Probably mostly because it was the path of least resistance, which was while everyone was happily getting along and minding their own business. This concrete and clear example begs the question, but what if? But this d i drone instance is just one among millions of similar potential true points of vulnerability. Okay? For example, the Windows operating system that most of the world is sitting in front of is composed of a kernel and Rio libraries for which Microsoft is the author and has the source code. But in order for it to do anything useful at all, the system also contains countless proprietary third party device drivers, the scores, the source code for which Microsoft has never seen. What do those drivers in detail do? No one other than their authors has any idea. Could any or more of them have undisclosed nefarious Trojan like functionality? Of course they could.
(01:50:55):
Why not? And if they don't today, any future update to them could just like any app in Google's play store for the sake of convenience and increasing number of these are included with the base operating system image, but the system also has the capability of going out to fetch additional drivers when needed and their updates. And all of these many chunks of unknown and unvetted code operate at ring zero with full unrestricted kernel privileges. My point is the actual security model of the world's most pervasive operating system is utterly broken. It's a complete joke. It's smoke and mirrors. We don't want that to be true. It's quite uncomfortable for it to be true, but pretending that it isn't true doesn't change the reality. It's the Wizard of Oz. We're supposed to keep our eyes on the impressive display of security in front of us. Steve Balmer jumping around on stage while we dare not consider and look behind the flimsy curtain where reality lurks, what's the solution?
(01:52:10):
Well, if ever hostilities across the world escalate into a true fight, we're screwed. The first thing you should do probably is turn off your router <laugh> and preserve the operation of your own internal network. That's a good point. <Laugh>. The only, the only solution I can see is for everyone to soberly appreciate the true consequences of what would happen. Now in today's deeply interconnected world, if superpower hostilities ever to boil over, we all need to just get along and for all of the embedded Trojan code that everybody has probably installed over time in everybody else's worlds to remain untried and unused looping back to the d i go for app, that app is just one from among the, and here it is the 2.65 million apps, which are currently listed and available for download through Google Play Store. The economics of what Google has built does not allow for any authoritative representation of app security to be made.
(01:53:36):
Google depends upon some of its own engineering and the engineering of many other security companies to analyze apps and catch misbehavior. But we are constantly learning of hundreds of thousands, if not millions of downloads of apps by users which are later found to contain malicious functions. The only long-term solution, if we're really willing to foot the cost of true security is for all proprietary closed solutions to be eliminated and for everything to be open source created by a broad community of cross-checking developers. Until, and unless that happens, all we can do is hope for the best.
Leo Laporte (01:54:30):
Wow. Steve, you've finally come around. I am a big proponent of open and that's one of the many reasons why yeah, Richard Stallman calls proprietary software malware because you never can know exactly what it's doing or who's it, who it's phoning.
Steve Gibson (01:54:47):
No. And, and as as I've said, the idea that voting machines are, you know, are, are,
Leo Laporte (01:54:53):
That's nuts.
Steve Gibson (01:54:54):
Closed source doin like dominion. Let, let just it ought to be open source. Open source. You still make, still make money by selling the hardware. Oh yeah. The touch screens and the machines and all that stuff. You just can't keep what it does to yourself. That that is nuts. Totally agree. And, you know, and so we've evolved a proprietary software ecosystem around powerful companies that want to leverage the fact that their stuff is secret. Mm-Hmm. <affirmative>. And we are now looking, we're we're, we're in danger of howing of having what we have sown being reaped against us. And again, the the the think about all of the random stuff we install with device drivers running in Ring and no one has ever seen what's inside them. Yep. We have no idea. Yep.
Leo Laporte (01:55:51):
Really good point. I I couldn't agree more,
Steve Gibson (01:55:57):
And I don't know how we get there from here, but at least having, taking a sober look at where here is Yeah. Is important. And yes, you know, flying Trojans <laugh> from a Chinese military owned company, that's a little, that's a little nerve-wracking. And, and, okay, so the government is gonna have to use domestic drones that aren't gonna be as good and gonna are gonna cost three times as much. But if that's the, if that's what you want, then that's what you're gonna have to pay
Leo Laporte (01:56:26):
For. And if we go to war, throw your smartphones out and get, go get those Nokia <laugh> candy bar phones. Yeah. You know, we, we were talking about this earlier on Mac Break Weekly Russia's government says no s phone the foot of you. Because smartphones are inherently spy devices. I mean, just in every respect.
Steve Gibson (01:56:51):
Yep. They are, they are all, they're connected computers and nobody, and they're not open. They're
Leo Laporte (01:56:57):
Closed. Yeah. Nobody knows what they're doing. Yep. Exactly. Yeah. Very good. Thank you Steve. You'd done, you'd done it again my friend. We do security now on Tuesdays, and I know a lot of people wait till Tuesday to <laugh> and say, you know, I'm sorry, I can't take any calls between two and 5:00 PM Pacific, I'm busy. That would be roughly 4:00 PM 4:35 PM Eastern. 2130 UTC is the nominal start time. Actually 2030 now because we are in summertime. All you have to do if you wanna watch it live and get the freshest version is go to live TWIT tv. There's live audio and video there. People who listen live, like to chat with others listening live. They could do that in our irc IRC dot TWI tv open to all. There's also a Discord for our fabulous Club TWIT members.
(01:57:55):
They get ad free versions of the shows, they get special shows, they get the Discord, lots of privileges and just seven bucks a month. We'd like to encourage you all to join. We are now at 1% of the audience, which is good. <Laugh>, I'd like to see five 10, who knows, you know, that would make us a self-sustaining enterprise, and I like that. Just go to twit.tv/club twit if you want to be in the Discord and listen to those shows without ads after the fact on demand versions of the shows are available@stevesitegrc.com. He's got 16 Kilobit audio, he's got transcripts, he's got 64 Kilobit audio. And, and the first two are unique. No, only he has those. We have 64 Kilobit audio and video. That's our unique format at twit tv slash sn. By the way, when you go to Steve Site, check out spin, right?
(01:58:48):
The world's best mass storage, maintenance and recovery utility 6.0. Still the current version. Don't worry if you, you know, if you, Patrick Norton sent me an email, I don't know if you got his email. He said, I got an email from probably from support. He said, I you know about something I bought in 2004. And I said, yeah, that's spin, right? <Laugh>, <laugh>, are you upgrading every 6.0 old holder or is there a cutoff date? Every one of 'em. Yep. Well, that's probably what you, it was an email saying, standby. Here comes 6.1 19 years. Yeah, <laugh>, very few people can write a program that that bug free and, and works for 19 years. This is about, I think the only guy who can do it grc.com. You can also check on all the free stuff like Shields up and oh, he's got a ton of stuff there.
(01:59:38):
The in control software to keep Windows eleven@baygrc.com. Leave him feedback at grc.com/feedback. Or on Twitter, he's at sg grc on Twitter and his dms are open. You can let's see. I, I mentioned that you could download it at twi.tv/sn, but I didn't mention there is a YouTube channel. This is a good way to share. You could send people clips. Youtube makes that easy. There's a dedicated Security Now channel. And of course, you know, the easiest thing to do if you want to collect all, what is it, 500, 915 subscribe That way you'll just get 'em automatically and just look for it in your favorite podcast player and you'll get it automatically the minute it's available. And you can go to the webpage if you want to download, download the other ones. There are, I think a few scripts people have written.
(02:00:30):
I don't know how up to date they are. That would, you know, suck them all down. But it's a good pro, you know, get a, get an intern to do it. Get, get, get all 915. Ask Chat G P T. Wait a minute, we're already in the nine hundreds. Yeah. I wonder if chat g p t they could, they could write a little Python script. Oh yeah, yeah. I bet it could write me a Python script to download all 915 episodes of security now from TWIT TV slash sn. I bet you it could somebody try that? We have only, I'm sorry to say 84 more episodes. So start collecting them now. Make 'em last. Make them that all day. Sucker <laugh>. You could listen to it again and again and again. You can say, wow, things were really rough in 2007. Yes, they were <laugh>. We will see you all next Tuesday. I will see you then Steve. Have a great week. Yep. Great. Thanks buddy.
Rod Pyle (02:01:28):
Hey, I'm Rod Pyle, editor-in-Chief of Ad Astra magazine, and each week I' joined with my co-host to bring you This Week in Space, the latest and greatest news from the Final Frontier. We talked to NASA chiefs, space scientists, engineers, educators and artists, and sometimes we just shoot the breeze over what's hot and what's not in space, books and tv. And we do it all for you, our fellow true believers. So whether you're an armchair adventurer or waiting for your turn to grab a slot in Elon's Mars Rocket, join us on This Week in Space and be part of the greatest adventure of all time
... (02:02:00):
Security Now.