Security Now Episode 913 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for security Now. Steve Gibson is here lots to talk about. A DDoS attack against Mastodon. Steve's take on blocking TikTok. Does it accomplish anything? Github's new secret scanning service. Something we should all probably be running the latest WordPress plugin that's threatening more than a million sites Russia, finding Wikipedia. And Steve digs deep on the case of the chicken phone points or something. It's all coming up. Next on Security Now. Podcasts you love
... (00:00:41):
From people you trust.
... (00:00:44):
This is TWiT.
Leo Laporte (00:00:49):
This is Security Now with Steve Gibson. Episode 913 Recorded Tuesday, March 7th, 2023. A foul incident Security now is brought to you by Thanks Canary. Detect attackers on your network while avoiding irritating false alarms. Get the alerts that matter for 10% off and a 60 day money back guarantee. Go to canary.tools/twit and enter the code TWIT in the how'd you hear about us box. And by Drata. Too often security professionals undergo the tedious, arduous task of manually collecting evidence with Drata. Say goodbye to the days of manual evidence collection and hello to automation. All done at draha speed. Visit drata.com/twit to get a demo and 10% off implementation. And by Kolide, Kolide is a device trust solution that ensures that if a device isn't secure, it can't access your apps, it's zero trust for Okta. Visit kolide.com/securitynow and book a demo today. It's time for security.
Leo Laporte / Steve Gibson (00:02:00):
Now. You've been waiting all week, so why to hear from this guy right here, Steve Gibson, our secretarian whoa secretariat, our Secretary of Security. That's exactly Ariat or something not true. Every week we get together, Steve explains why the world's going to hell in a hand basket. I suspect, Steve, I may be wrong, but I suspect you will be answering some pretty important questions this week. This week's answers are many. As it turns out. How has FASSAN survived a sustained DDoS attack? Or has it? What luck have your poll and the F B I had with taking down DDoS for higher services and have they returned? What's the point of blocking TikTok and is it even possible? What happens when government backs surveillance goes rogue? And exactly what is strategic OB objective 3.3. Hmm. What, if anything, does it pretend for future software?
(00:03:08):
Should you enable GitHub's new secret scanning service and get yourself scanned? What exactly did SIS S'S secretive red team accomplish? And against whom, which messenger apps have been banned by Russia? Who's missing from that list and why? What exactly is old? That's new. Again, what happens when everyone uses the same cryptographic library for their TPM code? What's the latest word? Press plugin to threaten more than 1 million sites. And why has Russia fined Wikipedia? And once we put that collection of need to know questions to rest, we're gonna examine the surprising revelations that surface as we unearth the foulest of security of recent security incidents. Thus today's podcast, when you say foul fel incident, o w l <laugh>. Yes, indeed. People who are not watching will not maybe immediately get the pun indeed that you have made a foul incident and so foul.
(00:04:18):
I can't wait to find out what that's all about. And of course, we do have another great picture of the week. Yes. Which makes you question humanity. Once again, I saw it and I went, what <laugh> Security now is brought to you by Thanks, Canary. Hey, I wanna show you something, Steve. This is so cool. You know all about it. Very, the very, one of the very first shows we did, I think, I think it was Thanks Canary, you know, immediately, don't you? It's a that's what it's, but more importantly it's a honeypot. One of our very first shows was all about honeypots the Honey Monkeys episode. And that's exactly what the thinks canary is, but a, a heck of a lot easier than the honeypots. We were talking about the time. In fact, I remember we talked to Bill Cheswick when we did that event in Boston a couple of years ago.
(00:05:08):
And bill said, I think I wrote the first software honeypot cuz he was trying to track down a hacker. Boy, is this easier? What's a honeypot? A honeypot is something that is irresistible to bad guys. Something that they've just got investigate. It could be a document that says, you know, employee payroll information. It could be an entire server offering file shares. It could be an FTP site. There's lots of things honeypot can, can imitate. But that's the beauty of this things canary. It can do it all. The canary is a little appliance that you put on your network, actually. You probably wanna have multiple canaries on your network. They don't look vulnerable, they look valuable. You could set them up in any variety of ways very easily. You get a console and you just choose. And they do it right too.
(00:05:57):
They don't just make it look like that thing. They give it a Mac address. That's appropriate. You know, the Mac address it would have if it were really from that company. It can be a Windows file server. It could be a, a router, it could be a Linux web server. It could be lit up like a Christmas tree with services or just a few selected services. This one turns out, I've mentioned this before. This is a sonology nas. And when you hit it, when you see it, it it, it has a DSM login. Like, just like the real deal has a Mac address. Just like the real a deal. Here's the difference. When an attacker attempts to log in, I get an alert and I know somebody's inside my network. This is why we've always said security's a layered approach. You know, we've got zero trust networks, we've got per perimeter defenses, we've got inbox defenses.
(00:06:47):
But ultimately at some point there's always a chance somebody's gonna get in. And then what? That's why you need the canary cuz you need to know if somebody's wandering around your network. On average it's 91 days before a company finds out that somebody's in the network. This just takes three minutes to set up no ongoing overhead. Practically in zero false positives, you'll detect attackers the minute they start exploring long before they can dig in. It's no wonder things to Canary hardware like this VM and cloud-based canaries. Yet they got, those two are deployed and loved in all seven continents. Prowling attackers look for juicy targets, right as they browse around your network. They browse active directory, for instance, for file servers. You could put this on active directory. They explore file shares looking for documents. They tried to fault passwords against network devices. In fact, that's one of the great things.
(00:07:45):
The alert will say what the login they attempted with, with my fake sonology here. And that tells me a lot about what they already know. You know, what, what email address they use, what password they use tells me a lot. Canary can also impersonate individual files. You can create canary tokens with your canary scatter them around a network. Pdfs, XLS doc files, except they're not. They look like they are, but they're really trip wires spread around your network to alert you when a bad guy wanders around. You can order configure and deploy network canaries throughout your network. As I said, they now have cloud-based birds and VMs as well. Then you wait your things to Canary quietly. It's a quiet little servant running in the background, just like a real canary and a coal mine, right? Just sitting there. But this one doesn't sing it.
(00:08:36):
Just sit there quietly. Little green light waiting for intruders. It's constantly checking up, providing an up to the minute report if you want, on their status. Cuz you'll get the canary console. Even customers with hundreds of canaries receive just a handful of events per year. No false positives. But what what's really amazing is when you've got these canaries, when you get, when you, and we, this happened to us, when you get the alert, it's like, whoa, quick, let's track that down. You can do it. Get an alerts via email, via text, via Slack notification. They support webhooks, cis syslog, you bet. Or your canary console. But, and or all of the above. Actually all the above is fun. Cause then you get, you know, your phone goes like crazy and you go, oh my God, <laugh> in this case I think it was who was it?
(00:09:26):
Was it Megan? I think Megan had a Western Digital passport or some, some NAS device. She plugged into the network and it was running software that went out and pinged every IP address on the network. Said hello, or who are you? Tell me about yourself. Well, we got, I got an alert from this canary right here. And because it was coming from 10 dot I knew it was inside the network, we were able to quickly track it down, disconnect the device, never to connect it again. That was gr it was a good kind of trial run cuz I don't think it was malicious. But boy, it really let us know this thing works. Just ask a principal security engineer of a fortune 50 company. We got the quote Canary, he says, has helped us detect and mitigate several incidents, several that could have turned into catastrophes.
(00:10:16):
An alert filed by their clone site Token allowed us to identify and force a takedown of several doppelganger domains that were purchased by bad actors for the purpose of launching phishing attacks against our employers and our employees and customers. It went on. Then this, this is probably on the on the canary.tools/love, which has all of these great testimonials. He says, I cannot recommend this product enough. You don't know what you don't know, but Canary helps. You know what you need to know when it matters. You may have heard about the circle CI compromise recently. How did users find out? Most users found out about the incident from their thanks Canaries. You can, you could look it up. Canaries work. They prove it continually. It's real peace of mind. And you need one visit. Canary.Tools/Twit. Five canaries, 7,500 bucks a year. You want more.
(00:11:11):
Maybe big banks certainly would have hundreds. Small operation, maybe fewer, but just as a example, five canaries, 7,500 bucks a year. That gives you your own hosted console. So you can mess with the settings, change it around. It's kind of fun to play with it. You get updates, support and maintenance. And if you use a code twit, by the way, in the, how did you hear about US box? Just type t w i t. You're gonna get 10% off your canary price for life on all of them. 10% off for life. And we know you love your things Canary, but, and I always say this, they have a very generous two month full refund money back guarantee. But I have to say, I talked to 'em the other day, they said, in all years they've offered this money back guarantee. They have not done one refund.
(00:11:58):
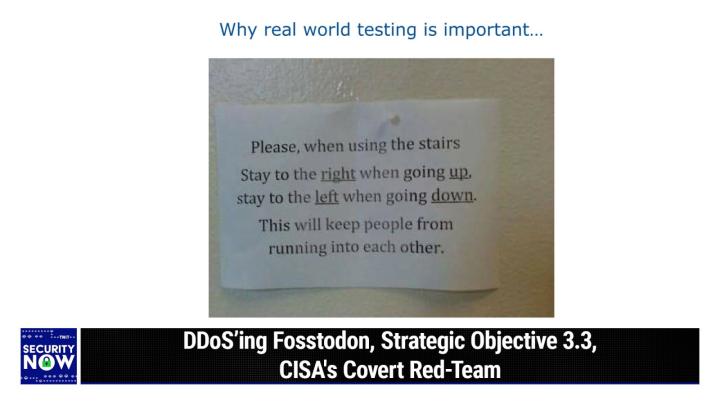
Nobody gets a canary and says, oh yeah, I don't like it. Everybody wants it. Everybody needs it. You should get some Canary Dot tool slash twit enter, enter the code twit and the how did you hear about us box that's important for Steve and Mecu. Then they know you saw it here. So please do that. Canary.Tools/Twit. And we thank 'em so much for their support of the program. Canary.Tools/Twit. Steve, I think, I bet I know you've got a picture of the week. So yes, as I said, this one will make people question humanity. Once again, <laugh>, I I li I gave this one the caption why real world testing is important. And this picture was provided courtesy of Simon Zfa a friend of the show. It's a photo of a notice that was posted. It's in some organization somewhere on the wall.
(00:12:55):
And it, it explains what you should do. It says, please, when using the stairs, stay to the right when going up, stay to the left. When going down this oh dear, will keep peop this will keep people from running into each other. No, no. <Laugh> quite the opposite. <Laugh> it's a guarantee that people <laugh>. Yeah. And, and, and you also kind of have to wonder what, like, are people having their eyes closed when they're using the stairs? And you shouldn't need this notice, obviously. Yeah. you know, you ought to see people like approaching you on the same side and, and you know, one of the two of you decides to switch sides. But of course, you know, this was just wonderfully written from like, the perspective of someone standing at the bottom looking up the stairs. Yeah. Not from the perspective of the person actually doing the walking would've been sufficient just to say, state of the right please.
(00:13:54):
State of the right. Yeah. Yeah. That's like when you're driving on a street. Yeah. Like, you know, similar to that. That's what everybody does Anyway. But no, we're gonna be more, as I said, why real world testing is important. You should test this signage after you've posted it and see what happens. And then consider changing it. Okay, so last Thursday, Chris Miller posted on Fassan. Hi all. We're still under a major DDoS attack and that's why mobile and desktop clients are not currently working. We've had to put the site behind CloudFlare temporarily until the attack stops. We're looking at other long-term solutions, but we need to get through the current moment first for now, use the web interface. Thanks for your patience. And as of yesterday, when I last looked, that attack was still ongoing. Foss Don as its name suggests, you know, f o s s t o d o n is the largest mastodon instance inhabited by open source software denizens.
(00:15:01):
And sadly, this most recent attack marks only the latest in a growing string of DDoS attacks that have hit an easily brought down unprotected Mastodon server instances over the past few months. And Leo, you were saying now that that mastodon.social is in trouble. Yeah, Garron, who created Mastodons runs mastodon.social. His was down, he, he tooted a couple of days ago. And last week during this show, in fact, I think it was, I was getting a lot of messages from people saying, is your site is twit social down? We run a master on instance. And I checked, you know, we have a thing called sidekick running that talks about traffic. And in particular, how many cues are open and how many have been processed, how many haven't, and how many have failed. And it was through the, the number of cues is through the roof, which is sometimes a sign of you know, too many people using the site.
(00:15:53):
But nothing had happened for that to make that the case. So while, I don't know, I'm gonna guess that was also a DDoS attempt there, there people were flooding us with the posts or, or wi with connection attempts. And so that connection overflowed the That's right. The inbound cue. Yeah. Psychic would've died. Yeah. So anyway, what's happened is, and here's like some anecdotal examples we just had, the pace of these attacks has increased significantly after Mastodon gained a huge amount of attention thanks to the mass exodus from Twitter, following Elon's takeover and his subsequent actions, which, you know, struck many as not being in the best interests of neither the larger Twitter community, nor their own individual best interests. So fearing the approaching end of Twitter, many jumped over to the mastodons decentralized model, which inherently prevents a repeat of essentially, you know, what Elon is doing at Twitter.
(00:16:50):
It also means a DDoS can't bring the whole thing down, right? Because well, it it can't bring, you know, individual instances down exactly. Be being, being federated. There's other places you could go there. There's a guy feta tips F E D I T I P s@mastadon.social. Yeah, that's good. Yeah. As in, yeah, as in federated tips. And he posted, or that person posted, the Mastodon social server is currently under a heavy DDoS attack and may not work properly. The 12,164 other servers on the network are unaffected. This is part of the reason why federated networks are a good idea. If one server goes down, the others work fine. The more spread out we are on small and medium sized servers, the harder it is for anyone to take down the network because there's no obvious target. He says there are also many other reasons why federation is good.
(00:17:51):
And then he provided a, a, a link to fedi tips slash why is the Fed averse hyphenated. So, you know, there's, there's not much more to say here other than a note that feta tips is certainly correct. On the one hand, the nearly weeklong DDoS attack against Fasad Don has rendered its mobile and desktop clients inoperable. But thanks to their web front end moving behind Cloudflare's front end protection, at least their web interfaces operable and their remaining on the air. As I noted recently when we were talking about the most recent DDoS connection rate attack record being broken, no standalone server on the internet can withstand today's DDoS attacks, not even for an instant. Is that cuz they're amplified? Is that, is that why they're so strong? Yes. Today's modern iot, ot, botnet based attacks are large enough to swap even medium size bandwidth providers.
(00:18:57):
That, that is to say, you know, it might even be that the traffic doesn't actually reach your server because it brings down the routers upstream of your server because these attacks are just so big. So it's not that your server is even down, it's that the, the traffic from outside on the internet can't e can't even reach it because the attack just swamps the, the, the aggregating routers before they have a chance to even get to your server. So the only recourse, I mean only if you have to be on the net, is to move behind the protective skirts of one of today's major DDoS protection services. The problem is such service is not free unless the service wishes to provide such service charitably. And that's one thing that sort of annoyed me elsewhere on Reddit, the Fosters Don admin was grousing a little bit about the need to be rescued by a commercial service such as CloudFlare.
(00:19:56):
You know, in my opinion, they should consider themselves incredibly fortunate that such a facility like CloudFlare exists. Otherwise, they would be off the net for as long as the D Dossing Creon wanted to keep them off the net. And, you know, I've had experience with that in, in my past and, and it is in fact we got an interesting graph coming up next, which gives us a sense for the scale of the problem, not, not only in attack size, which as we've said is now just, I mean, it's incredible amounts of attack where it's, it's, you know, to call it overkill is is an understatement because it, it would just, the attacks were so large that they would, they just melt the wires essentially <laugh> between the, the, the, the server being attacked in the outside world. Okay, so on the subject of DDoS attacks, the network security provider Nets Scout has noted that the efforts by Euro poll and the F B I to take down more than 50 DDoS for higher services in the middle of last December has indeed led to a measurable decline in DDoS attacks.
(00:21:13):
Now, I have got a chart in the show notes that demonstrates that visually those declines have been recorded at broadband providers across both the US and the eu. And moreover, nets scouts said that DDoS traffic has remained at lower levels for the month after those takedown efforts. This suggests that no new players have immediately appeared on the underground DDoS market to fill the void after last year's. Takedowns on the other hand, you know, four or five weeks isn't much time to wait for a new service to get us itself up and going. So to illustrate their data, NetScout provided this nice chart that we've got on the screen right now so that we were able to see for ourselves that chart leaves little doubt that the takedown effort had its intended effect where the takedown occurred. You could see a dramatic decrease in something.
(00:22:14):
So wondering exactly what that something is, you then look at the horizontal scale to learn that the charge horizontal axis is in a attack per day. So you learn that while yes, the number of attacks per day did indeed fall from their peak of around 3,500 DDoS attacks per day globally. And, and that peak was reached twice and a number of, of shorter peaks, like more than 3000 were reached another four times, still a few weeks ago a month after this takedown actually it was the 22nd of January. There were a thousand attacks in that day. And of course, it only takes one attack to ruin a particular website's day. So, you know, it's definitely good that law enforcement is on this and is taking down these DDoS for higher services since they commoditize DDoS attacks, they allow anybody to send a little Bitcoin somewhere and say, I want this site removed for X length of time.
(00:23:25):
I think, you know, you, you, you, you pay by the minute how long you want the, the site to be gone. So that's not the kind of commodity that you want around. And I'm delighted that the F B I in Europe hole are on that. But, you know, we, we still seeing individual attacks breaking records, so it's clear that there's still plenty of fire power left to which Fassan and mastodon.social can both attest you know, fassan moved to self behind CloudFlare got their website back up. Once the attack abates, they will presumably move back and depending upon the size of the grudge or whatever it is, I mean, like, you know, who knows why fosson is being attacked. The part of the problem is these attacks are so trivial to execute now that they don't really have to mean anything. It's just, you know, if you've got a, an idle botnet that can do DDoS attacks, well, you know, spin the wheel and pick your target.
(00:24:22):
It's, it's, I mean, it's sad and there's, it, it's the, the probably the biggest weakness, the biggest fundamental weakness that we have in the, the way the internet works with its autonomous routing is that, you know, the, the brilliance of it is that you can drop a packet on the network anywhere in the world and the routers will forward that packet to its destination ip. And that's also the bad news because if you've got a whole bunch of people all dropping packets all aimed at a given at the same ip, this the world, the global internet will concentrate all of those packets into that single location and create a single point of failure. And, you know, that site is no longer able to respond to good packets because the malicious ones have just flooded it. So that hasn't been fixed, and I don't see any fix for that.
(00:25:20):
It will be, it would take, you know, some, as we've talked about this before, right? Some clients that are generating DDoS attacks are able to, to spoof their source ip, they're able to just make up whatever IP they want as the packets are leaving. Well, that traffic could be blocked at the, the first time it comes to a network border because that network border knows very well what networks are inside of it. So you're saying an I S P specifically? Correct. I mean, we've always, we've said this for years that ISPs have got to be doing this. They've got to Yep. Block outbound traffic that's not originating from IP addresses inside their range. Exactly. It's called egress filtering and it's all the technology is there. It's just, it's, I can't believe they're not doing it still. I know. That's, yeah, that's kind of stunning.
(00:26:19):
I thought they were <laugh>. Yeah, maybe. Well, you know, maybe Comcast is, maybe the big ones are, but it, all it takes is one little Ukrainian i p or, or something, right? And, and, and the argument has been, well then bots would then start making up ips within the network. So you didn't know. Oh, that's true. Run where in the network it was. And, and, and, you know, the bots are also disposable, right? They're, they're all compromised routers, you know, th that exist in, in back closets and corners. So in fact, it's not like they're, they're people who need to avoid or evade law enforcement. They're just, you know, i o t devices that have long been forgotten that, that have not been patched, that have been taken over remotely, and now they're serving somebody else's ends. So we got a sort of a mess and it's, it's not being resolved quickly.
(00:27:12):
So, okay. Last Thursday, the headline in Gizmoto read, we found 28,000 apps sending their data to TikTok. Banning the app won't help. I'm just gonna share the beginning of gizmo's very long article since it contains most of the useful information. Gizmoto writes, president Joe Biden gave federal agencies 30 days to remove TikTok from government devices earlier this week. You know, and that means la that, that, that was last week until now. Most politicians, Gizmoto is saying, intent on punishing TikTok have focused solely on banning the app itself. But according to a memo reviewed by Reuters, federal agencies must also quote, prohibit, prohibit internet traffic from reaching the company that, and Gizmoto says, that's a lot more complicated than it sounds, and I'll interject here, a lot less complicated than Gizmoto thinks, but we'll get to that in a minute. Anyways, so they said, Gizmoto has learned that tens of thousands of apps, many which may already be installed on federal employees work phones, use code that sends data to TikTok some 28,251 apps.
(00:28:38):
And it's unclear which platforms those are on th there's no mention of that here. They said use TOS software development kits. Sdks, which they explain are tools which integrate apps with TikTok systems and send TikTok user data for functions like ads within TikTok, logging in and sharing videos from the app. That's according to a search conducted by gizmoto and corroborated by app figures and analytics company. But apps aren't talk's only source of data. There are TikTok trackers spread across even more websites. The type of data sharing TikTok is doing is just as common on other parts of the internet. The apps using the TikTok S D K include popular games like mobile legends, big Bang Trivia Crack and Fruit Ninja photo editors like V S C O and Kava, lesser known dating apps, weather apps, wifi utilities, and a wide variety of other apps in nearly every category, the developers for the apps listed above did not immediately respond to a request for comment.
(00:29:48):
Anyway, gizmoto article goes on, but we got the gist of this. Okay, so there's two parts to this whole mess. The first is, what are we actually trying to do here? And the second is, is it even possible? Okay. To, to first to give the whole idea of banning TikTok some perspective as well as a bit of an updated reality check about the present nature of consumer tracking on the internet overall, the nonpartisan Brookings Institute titled their commentary from the middle of just last month, TikTok Bans won't guarantee consumer safety. And so in this case, I've grabbed just the end of that long piece where they conclude and summarize a bit. Are talk's data practices different from other companies. And they say several experts have already argued that TikTok bans won't make Americans safer. One reason is that much of the information collected by TikTok is like that compiled by many companies that host consumer facing products.
(00:30:56):
The app undoubtedly has information on which videos users have watched, comments they've made about those items and their geolocation while watching the videos, as well as both users and their friends contact information. But that is true for nearly all digital platforms and e-commerce sites around the world. It is also the case that digital firms compile data on users and many buy and sell consumer data via third party vehicles. It's been estimated that leading US data brokers have up to 1500 pieces of information on the typical American, and that both domestic and foreign entities can purchase detailed profiles on nearly anyone with an online presence. Even with aggregated data, it is possible to identify specific individuals through a relatively small number of attributes. With some research estimating that 99.98% of Americans could be de anonymized from relatively small data sets. Still what sets TikTok apart are the amount and type of trackers they use.
(00:32:12):
According to a 2022 study utilizing Apple's record app activity feature, TikTok utilizes over twice the average number of potential trackers for social media platforms. Almost all of these trackers were maintained by third parties making it harder to know what TikTok is doing with the information they collect. If concerns about TikTok are around the compromising of personal information with government authorities either in China or elsewhere, there are many firms both within the US and abroad that have been accused of the same. For example, a former Twitter employee was convicted of acting as a foreign agent for Saudi Arabia, providing confidential information from that platform about dissidents to foreign officials. Consumer geolocation data are routinely bought around the world by data brokers and repackaged for sale to advertisers, governments, and businesses regarding concerns that Chinese companies operating within the US are beholden to Chinese laws. The same can be said of American companies that operate in China.
(00:33:21):
Some observers have expressed worries about Tesla vehicles being made in China for some of the same reasons and what the company may have to do to maintain good relations with Chinese officials. Furthermore, if the criterion for bans based on national security is access to user's confidential information, there's a long list of American and foreign companies that face security challenges via their Chinese operations. As examples, many digital products sold domestically are made in China, and a wide variety of smart appliances, pharmaceuticals, personal protective equipment, computer chips, and other products are assembled there. Okay, so you know what's actually developed over time globally is a rich and deeply interdependent ecosystem. And there are myriad companies collecting and selling data on everyone who's using the internet. Our illusion of true anonymity is exactly that, an illusion as third party cookies once did. Most of this operates under the radar while unseen.
(00:34:32):
It is still utterly ubiquitous. It's, it's everywhere. Okay, so that leaves the question, assuming that the government's of the world decide that they're going to blacklist TikTok, is that even possible? Well, as we know, IP addresses are readily changed, but the domains used by d n s lookups are generally hard coded into apps and trackers. That means that D DNS lookups are toss Achilles heel. I did a bit of research and I identified five domain name roots, which often also have sub domains. So some wildcard matching would be necessary. There are also two Akamai CDN domains, but taken together, those would appear to be all of the domains currently in use by TikTok. So they are tiktok.com, tiktok.org, TikTok v.com, TikTok cdn.com, musical.ly, and then the two Akamai CDN networks. Okay. So if federal agencies were to locally configure their networks local DNS to black hole, those domains and their sub domains, you know, perhaps returning 0 0 0 0 or 1 27 0 0 1, or maybe pointing them to a local server.
(00:36:05):
So you know, to have them resolved to something once local device CAS expire. You know, the DNS cas and a quick d n s dig that I did indicates that those domains are running with quite short ttl, you know, time to live expirations all traffic of any sort bound for TikTok would lose its destination IP and would be blocked at the border. It would just get dropped at the client device that would no longer be able to get the IP for any TikTok property. On the question of whether this would be a good thing to do, I have no opinion. Whereas the technology is interesting, the politics is not, you know, tensions are clearly on the rise with China, so I suppose that nationalism and protectionism are bound to rise as well. But I think more than anything, the technology lesson we take from this is that there is an incredible unseen and largely unappreciated underground of activity that very few internet users appreciate.
(00:37:12):
Out of curiosity, I went over to MSNBC's website@msnbc.com and you block origin lit up counting that single website homepage causing my browser to connect to 38 other domains. And Fox news.com connected my browser to 51 other domains, you know, 38 and 51, I'm sure that few are directly affiliated with either property and how many CDNs do they need? You know, all of that other crap is superfluous. It's, you know, who knows what. And since most people have no idea what's going on, why not load up with revenue generating trackers? I doubt that TikTok cares at all about the loss of connectivity to federal government networks and federal employees who want to continue to use TikTok on their own devices while within those networks can simply switch to their cellular provider for continued unfettered internet access. If the United States government's actual goal is to protect its citizens from the data collection of a Chinese state owned and controlled entity, then blocking all TikTok traffic at US borders is gonna be necessary.
(00:38:30):
But every time Russia or some other repressive regime does the same thing, we make fun of them. So, you know, make up your own mind. Yeah, I mean, do we want a great firewall of the us? I think some people would like that. I, I, exactly. Yeah, it just, it seems crazy and I think that, you know, this just seems like way overblown. I thought it was interesting that Brooking said that in their, in that 2022 analysis, TikTok was running more tracking things. Yeah, that's interesting. More than twice. Yeah. That yeah. Yeah, that's interesting. But on the other hand, it's, it's twice more than a whole lot <laugh>, so it's just a lot, lot more than Facebook really More than Instagram. Yeah. I I will find that hard to believe. Agree. And I have to say, these same people who are shouting about shutting down TikTok have done very little to protect our privacy with telecommunications companies, right?
(00:39:30):
Who, who lobby very hard and give them a lot of money. And they just mom on that. Right? And, and, and to your point, Leo, it was a really good one when, when you mentioned Facebook and in and Instagram, the number of trackers is one metric, but the number of tracking events is a different metric. And because of the heavy use of Facebook and Instagram, that's good point. Yeah. They're, they're getting many more event tracking events. Well, we know that because they kill your phone battery. It's the first thing you do if you want to save your phone is take Facebook and Instagram off. Yep. I don't think TikTok kills my phone battery, but I don't know, maybe it does. Let's take a break. Okay. I'm going to get ready for the next phase of this. Get ready for the next phase of your life, Steve Gibson <laugh>.
(00:40:23):
While you do that, I shall get ready to tell you about the next phase of our sponsorship. Our sponsor today, ISTA, D R A t ATA is actually the, the answer to a question a lot of companies have these days. How do we maintain compliance? That is one, you know, there's, it's security has many jobs, but one of the jobs you have is to prove that you are secure, that you are compliant to your stakeholders, to government regulators. It's, it's a big part of it these days. And I am amazed at how many companies to this day are doing evidence collection for compliance manually by hand. <Laugh> what <laugh> as a leader in cloud compliance software, G2 Crowd says a leader Joda streamlines your SOC two, your ISO 2,701, your gdpr, your P C I D S S, your hipaa, all those compliance frameworks that so many companies are you know, re required to respond.
(00:41:36):
Tora gives you 24 hour automated continuous control monitoring. You focus on your business and on scaling and being secure and all the stuff you care about. Let DRA do the evidence gathering automatically. And by the wayra, Gerda integrates with more than 75 of the applications of the clouds that you already use your entire tech stack. Aws, Azure, GitHub, Okta, CloudFlare, of course, all of them, countless security professionals from companies who had been manually collected, suddenly realized we could do it better, are using dda. Companies like Lemonade and Notion and Bamboo HR have all shared how critical it's been to Haveta as a trusted partner in the compliance process. And one of the reasons you kind of, you might be inclined to say, okay, these are the guys. DDA is backed by S V C I, what, what you say. Well, how, how does that help?
(00:42:36):
Well, it's a syndicate of ciso, angel investors. So these are, these are guys and gals on the front line, CISOs who say, you know, dra, this is the, this is the one everybody's gonna have to use. These CISOs from some of the most influential companies in the world, put their money where their mouth is. DDA allows companies to see all their controls, easily map them to compliance frameworks. So you can gain immediate insight into, you know, how you're doing, into overlap. Sometimes there's overlap. Get rid of that, save yourself some money and start building a solid security posture. Achieve and maintain compliance. Expand your security assurance efforts. Strada, automated temp dynamic policy templates, support companies new to compliance really make it a lot easier for you. So don't, don't say, oh, I don't know, are we gonna be, trust me, so many companies ahead of you have done this.
(00:43:28):
Automated Reminders insurance, smooth employee onboarding. They're the only player in the industry that has a completely private database architecture. So your data can't be accessed by anyone outside your organization. Anyone at all. Andrada is on your team. They're there to help you. So every Jada customer gets a team of compliance experts. You'll get a DES design dedicated, I'm sorry, designated customer as success manager. They have a team of former auditors, auditors who have conducted more than 500 audits themselves. They're there for your support and your council. You can ask them questions. And because Draw maintains a consistent meeting cadence, you're never kind of out in the cold. You're always on tracks, no surprises, no stoppers, you know, no barriers. They'll even do pre-audit calls with you to prepare you for when your audits begin. They're really a partner. That's what you want with Strata's Risk Management Solution.
(00:44:26):
You can manage end-to-end risk assessment and treatment workflows. You could flag risks, you could score them. You can decide whether you wanna accept them, mitigate them, transfer them, avoid them. Draw auto map's appropriate controls to those risks. Simplifying risk management, automating the process and draw's Trust Center provides real-time transparency into security and compliance postures. So that improves your, because people say, oh, they're doing it right. That improves your sales, your security reviews gives you better relationship with customers and partners. This is just a win-win all around. Say goodbye to the tedious manual evidence collection. Say hello to Automated Compliance by visiting drta drta.com/twi, D R A tata.com/twit dta, bringing automation to compliance@dtaspeeddta.com slash twit. You'll get 10% off when you request a demo and make sure you use that address so they know you heard it. Here on the Steve Gibson Show. Thank you Draha, for your support of security.
(00:45:30):
Now, back to you, Steve. So this piece piqued my interest because of the recent discussions we've been having about the UK's decision to mandate, you know, the equivalent of some sort of backdoor in otherwise secure and private communications. A report from the office of the Inspector General for the Department of Homeland Security, which was titled Secret Service and ICE, did not always adhere to statute and policies governing use of cell site simulators. And they, and they said, and it was followed, law enforcement sensitive redacted that report found that the US Secret Service and the US Immigration and Customs Enforcement, you know, ICE have not obtained court orders for multiple operations in 2020 and 2021, where they deployed cell site simulators, you know, stingrays to intercept mobile communications. The report found that one Secret Service field office had deployed stingrays on multiple occasions on behalf of a local law enforcement agency without obtaining court warrants.
(00:46:47):
The report also found that ICE did not believe court authorization was required for some of its operations. Furthermore, the report also found that neither the U S S S, what's that? The us Oh, the US Secret Service, nor the ICE were documenting operations related to supervisory approval and data deletion procedures. So, yeah we need to be careful with the technology that we make generally available, and those who have the technology need to know that their use of it will be monitored and they will be held accountable. This demonstrates obviously, the potential for abuse. Once loopholes are placed into our supposedly secure and private communications, we'd like to believe that only those holding valid court orders, you know, search warrants would have access to private communications. But experience suggests otherwise you know, we're all, everybody's only human, right? Except chat G P T, and we're not sure what it is.
(00:47:57):
Okay, strategic objective 3.3. This is a biggie. And in fact, I'll have something more to say about this Next week. I found a, a recent speech that was given, but dated March, 2023. So this month, last week, the Biden administration published its 39 page National Cybersecurity Strategy. I haven't had time to go through the entire document, but if it appears worthwhile, I'll likely cover it in additional detail next week. And in fact, I did see some, some stuff about I o T that I want to talk about too. But one section of the document in particular, it was brought to my attention by Mark Fishburn, a listener of this podcast, who knew I'd find it interesting and our listeners will know why when I share it. That section is strategic objective 3.3 labeled shift liability for insecure software and services get a load of what is now part of the United States official National Cybersecurity strategy.
(00:49:11):
It says, markets impose inadequate costs on and often reward those entities that introduced vulnerable products or services into our digital ecosystem. Too many vendors ignore best practices for software development, ship products with insecure default configurations or known vulnerabilities and integrate third party software of unvetted or unknown Providence. Software makers are able to leverage their market position to fully disclaim liability by contract, further reducing their incentive to follow secure by design principles or perform pre-release testing. Poor software security greatly increases systemic risk across the digital ecosystem and leaves American citizens bearing the ultimate cost. We must begin to shift liability onto those entities that failed to take responsible, sorry, failed to take reasonable precautions to secure their software, while recognizing that even the most advanced software security programs cannot prevent all vulnerabilities. Companies that make software must have the freedom to innovate, but they must also be held liable when they fail to live up to the duty of care.
(00:50:41):
They owe consumers, businesses, or critical infrastructure providers responsibility must be placed on the stakeholders most capable of taking action to prevent bad outcomes. Not on the end users that often bear the consequences of insecure software, nor on the open source developer of a component that's integrated into a commercial product. Doing so will drive the market to produce safer products and services while preserving innovation and the ability of startups and other small and medium sized businesses to compete against market leaders. The administration will work with Congress and the private sector to develop legislation establishing liability for software products and services. Any such legislation should prevent manufacturers and software publishers with market power from fully disclaiming liability by contract and establish higher standards of care for software and specific high risk scenarios. To begin to shape standards of care for secure software development, the administration will drive the development of an adaptable safe harbor framework to shield from liability companies that securely develop and maintain their software products and services.
(00:52:06):
This safe harbor will draw from current best practices for secure software development, such as the N I S T secure Software Development framework. It must also evolve over time, incorporating new tools for secure software development, software transparency and vulnerability discovery. And finally, to further incentivize the adoption of secure software development practices, the administration will encourage coordinated vulnerability disclosure across all technology types and sectors, promote the further development of software bills of material, and develop a process for identifying and mitigating the risk presented by unsupported software that is widely used or supports critical infrastructure in partnership with the private sector and in the open source software community. The federal government will also continue to invest in the development of secure software, including memory safe languages and software development techniques, frameworks, and testing tools. <Laugh>.
(00:53:11):
Wow. Okay. Now obviously no strategy is law, right? A strategy is only that. And major software publishers have strong arms in Washington where legislative votes are available to the highest bidder. So nothing here in this 3.3 section is actionable. And there will be a great deal of pushback against any sort of weakening of today's current blanket contractual protections, which we've often noted, you know, is like, well, yeah, you could use the software, but whatever it does, it does, and we don't really know. And if you don't like it, your, you know, all you can ever do is ask for your money back. That's your maximum recourse. What caught me off guard here was the precision of understanding about the nature of this problem. You know, that one sentence software makers are able to leverage their market position to fully disclaim liability by contract. In other words, if you don't like it, don't use it.
(00:54:22):
On the other hand, their position doesn't make not using it a practical alternative, right? You know, you, you have to use Microsoft stuff if you're in, in, in the enterprise. So anyway, they said further reducing their incentive to follow secure ByDesign principles or perform pre-release testing. So, you know, I would say the writing is not yet even on the wall, but it's obviously in some people's heads. And it just got written down in the official national cybersecurity strategy for the first time ever. So it's obvious that others have noticed the same irresponsible attitudes toward critical software security that we've been discussing here on this podcast. I mean, you know, the fiasco of Microsoft's printer problems, which they just ignored for six months, which hurt huge numbers of their customers. So wa was they'd be lying. So they'd be liable for this. Yes. Which I think is fantastic.
(00:55:26):
I mean, they're not gonna, they're not gonna think it's very fantastic, I'm sure. Oh no baby. Does it mean liable criminally or liable civilly? Like I'm sure it's civil liability. Yeah. And maybe just opens up the idea that if you were a victim of a printer hack, that you could recover losses from Microsoft. Of course, they're shrink wrap licenses and all those ULAs and all that say, oh, we're not liable, and Oh, you have to go to garbage. Well, that's just it, you know, that is their, they're disclaiming their, they're disclaiming liability by contract, which they specifically targets and says, this is not okay, good. We talked about it on TWI a little bit, and now why don't, why don't we get your take on it? Cuz that seems a big sea change. And you're right. Will Congress let that go through?
(00:56:12):
Probably not, but yeah, that's good. It's, it's good to just shake some trees a little bit, I guess. Well, and, and ask if the public would not be Yes. You know, for this. So you, it's like anybody who hears this is like, well yeah, of course. Why wouldn't they be responsible? Right, of course. And as I've been saying, it's insane what we have now where there's zero zero accountability and we've all, we've all seen those, you know, disclaimers on boxes of software and so forth that say, you know, not, not we not representing that this is fit for any purpose whatsoever. And <laugh> me merchant ability or fitness of use. Yeah, we don't, we don't know. We don't guarantee you nothing <laugh>, you know, you may drive the car off the lot and the wheels all fall off and fall so, well, you know, we thought we screwed them on tight, but I guess Henry can open, but actually that's the difference.
(00:57:03):
Cuz car manufacturers are liable. That's my point. Software manufacturers are not, this is an anomaly in the Yeah. For, for something that has become as important as software has. I agree. You know, and it's only because of history right? Back when it was just like, well, you could store your wife's recipes on your Apple two, you know, and if, if, if, well if we lost them, we're sorry. Yeah. You should have held onto the paper copy. Yeah. <laugh>. And it, it just, and it went from there, right? It never changed. Good. I love it. Yeah. This is, I hope, I hope they're, this is get this happening. This is good. This is big news. And, and again, just the fact that it's been written down and now people are gonna see it and go, huh? Yeah. Why is that? That way, you know, it's like, okay, good.
(00:57:51):
So back in December, GitHub announced the public beta of their free secret scanning alert. The, it's, it's the, the name of this is weird secret scanning alerts. I had to like, what? Anyway, public beta in December, their free secret scanning alerts across public repositories. And now by secret scanning, they mean that GitHub will proactively scan all code submitted for the inadvertent inclusion of any secrets. Like, whoops. We left the admin password in the code by mistake. It's a very cool idea. And since its initial release in beta, more than 70,000 public repositories have turned on secret scanning alerts and have uncovered thousands of leaking secrets, stuff that the authors did not intend to leave in their code. So as of one week ago, last Tuesday, a week ago today, last Tuesday, GitHub's secret scanning alert experience is generally available and free for all public repositories.
(00:59:04):
Github users could enable secret scanning alerts across all of the repositories they own to notify them of any leaked secrets across their entire repository history, including code issues, descriptions, and comments. Github secret scanning works with more than 100 service providers in the GitHub partner program. In addition to alerting users, they will notify their partners when one of their secrets is leaked with secret scanning alerts enabled regular users will now also receive alerts for secrets where it's not possible to notify a partner, for example, if self-hosted keys are exposed along with a full audit log of actions taken on the alert. So one example of this in practice is a DevOps consultant and trainer whose handle is at R A J B O S, I guess his name is Rob. Anyway, he enabled secret scanning on approximately 14,000 repositories and discovered over 1000 secrets. Rob remarked quote, my research proves the point of why everyone should have secret scanning enabled.
(01:00:18):
I've researched 14,000 public GitHub action repositories and found over 1000 secrets in them. Oh my god. Yeah. Even though I train a lot of folks on using GitHub advanced security, I found secrets in my own repositories through this. It's easy, it's easy to make that mistake. It really is. I, yeah, I have to be very careful cuz I have, and I bet you a lot of these are this I have well, some of it's gonna be code with like your Amazon secret key a p i key unit. Right? Right. But I also, I back up my dot files, my settings files my PGP stuff's in there. I back up my EMAX setup and it's very easy to, you know, you often people hard code secrets into those files and, and then you're syncing 'em to GitHub. It's easy to forget and miss it.
(01:01:12):
Yep. And, and for example, you might have put that in just for like during testing, right? Yeah. Just like, like, like, like, so you didn't have to keep entering the password every time you, you just put a little shortcut in and then when, when you go to production, you forget, forget. And it's like, whoops, there's a way to do it. You know, they're, they're really easy, not that easy, but there is a little thing you could do to have PGP encrypted keys in all those secrets and then there's kind of safe, they're still in the code, but they're safe. And I've always thought, ah, I should probably do that. And I have never done it <laugh>. So, you know, I'm counting on my own brilliance to remember not to not to upload those files. Oh boy. Good luck. So also, last Tuesday, CISA revealed the somewhat bracing results of a secret red team exercise that they carried out against the network of a large named US critical infrastructure organization with a mature cyber posture. During that exercise, they quote, obtained persistent access to the organization's network, move laterally across multiple geographically separate sites and gained access to systems adjacent to the organization's sensitive business systems. [inaudible]
(01:02:37):
Says the, that on at least 13 separate occasions, its red team triggered measurable events. It wasn't clear whether this was deliberate or unavoidable, you know, but that should have gotten it caught and didn't in every case, the organization failed to detect these actionable events. As I noted, CISA officials declined to name the organization, but they did say that although they did manage to get in, they found the organization had good cybersecurity policies in other parts of its network, such as up to date and hardened perimeter infrastructure and good password policies. Okay, so how did Sissy's Red team gain its initial entry? Fishing? Today's most difficult to corral cyber weakness people on the inside or on the inside, and it's just too easy for someone to inadvertently allow a bad guy in. And that's what happened in this instance. And, and once they got in, they stayed in, moved laterally, set up shop, moved around, explored the network, all un unseen.
(01:03:58):
Okay. So I titled this little short bit of news what's left after reading that Russia had formally, legally banned the use of all foreign messaging applications inside Russian financial institutions and state owned companies. Again, this is one of those, what they, they're only now like why would you, why would you not do it a law? I was like, are you still using Windows in Russia? What? Anyway, the law which entered into its effect this month outlaws the use of apps such as Discord, Microsoft Teams, Skype for Business, Snapchat, telegram, three, a Viper, WhatsApp, and WeChat. Now the page announcing this was in Russian and it lists those. And if you're interested, I have the link here at, at in the show notes like we have any Russian speakers but notably missing is Apple's, iMessage, and Android's messages. Hmm. Which are both end-to-end encrypted.
(01:04:59):
Hmm. You know, you can see the, the, the, the, the name of the things that I named there, they are, you know, nine specifically enumerated messaging apps. So this legislation, which specifically enumerated those nine third party Messenger apps doesn't mention the two mobile platforms Native messengers. So, you know, perhaps that's the answer to my rhetorical question, what's left? Or perhaps those are just implied. You know, the news was that all foreign messaging applications were banned. So perhaps Russia has some state owned or trusted messaging apps that no one, you know, that no one is gonna want to use or trust. I don't know. Anyway, just sort of interesting. There's like, okay, can't use these, but we don't know about iMessage or, or messages on the Android platform. As we've noted before, cis a is maintaining a list of what they call, it's the, the k v list, the known exploited vulnerabilities.
(01:06:07):
And K V has become a common abbreviation within the security industry for that growing list. In other words, these are vulnerabilities, which cis CISA has had reports of actually being used in the field. So that's like the patch first list, right? And once upon a time, it wasn't very big, but it's been growing during the last year. The size of this catalog of known exploited vulnerabilities very nearly tripled in size. It jumped from 331 entries at the start of 2022, but finished out last year with 868 individual vulnerabilities known to have been seen being actively exploited. Okay? Now here's the interesting part, although this near tripling of the list in one year would suggest that new bugs are being exploited. A look at the issuance dates of the catalogs CVEs for those shows that the vast majority of the new cisa, K E V entries are for older vulnerabilities that companies failed to patch for years, all which came under attack last year.
(01:07:30):
The oldest of those was the exploitation of a bug that was originally had a patch a available for it 21 years ago, back in 2002, which was, it came back to life and was being used for vulnerability exploitation. So, wow, as I said, you know, we, we've often talked about how amazingly difficult it is to get our, the old stuff patched. And, you know, that's another advantage of this directive. 3.3, right? If the, if software were more secure out of the gate rather than relying, I mean, like relying by policy, which is what Microsoft has become, right? They are relying by policy on updates. There's, there's not even a, it's, it's not a shock. It it, you know, it's hundreds of security vulnerabilities per month are being fixed. So, you know, and, and we hear stories, right? Of how, what is it? Windows seven or eight shipped with 10 over 10,000 known problems.
(01:08:40):
And yeah, some of them are that, you know, the, the color of this gray shading changes if you shake the computer sideways during a full moon, they're just not big problems, but obviously a lot of them are big problems. And so what's happened is it's just become, oh yeah, Jill, what, what, what day is it? Okay, ship it. We'll, we're gonna, we have weekly updates. We'll fix it later. Well, not all systems have weekly updates or monthly updates, I should have said. So it would be nice if there was a little more pressure to get it right the first time since we seemed, you know, as a, as an industry, as a, as a world, we're just not keeping things patched, even when, when fixes are available. <Laugh>, speaking of patches, remember when everyone used Intel's sample U Universal Plug and Play implementation code as their actual production code, apparently without ever actually looking at the code, and even in the face of that comment header block at the top of the code, which loudly stated that this was sample code only and should never be used for production.
(01:09:54):
And that as a result of that, the entire industry suffered as a whole from a widespread vulnerability in that sample code, which everybody had in their routers. Okay, well, history isn't, it's not really repeating, but it's certainly reminiscent this time. It's a pair of widespread vulnerabilities which have befallen multiple vendors platform trusted platform module, you know, the TPM code. It's not, as I said, not quite the same as the U P N P debacle since these vendors were at least using the TPM reference implementation library, which should have been okay. But this is another example, at least, of the danger of monocultures and why we're more healthy. If as another example, we keep browsers other than chromium alive. In this case, researchers at Cork's Lab discovered a pair of buffer overflow vulnerabilities in libraries implementing the TPM 2.0 security specification. The vulnerabilities would allow an attacker who could gain access to the TP M'S command line interface to leverage the vulnerabilities to corrupt the TP m's memory and access sensitive information handled by the tpm, such as encryption keys, which of course is exactly what all of the TP M'S fancy hardware technology is supposed to prevent.
(01:11:25):
Patches for this were released at the end of last month, end of February. And since many vendors all directly implemented the same reference library, the TPM implementations from ibm, the trusted computing group themselves, red Hat, Sui Linux, and many others are all affected. So we can look for some updates to that coming soon. Okay, two last pieces WordPress, just a quick note to all of our listeners who manage WordPress sites, more than 3 million WordPress sites, which are currently running a plugin called All in one s e o will need to be updated to resolve a set of vulnerabilities that could be used to hijack sites. This is often the case. The troubles were found and reported by the researchers at Word Fence. And again, 3 million plus WordPress sites currently vulnerable. As I've noted before when we were talking about the inherent danger of third party developed WordPress add-ins, which, you know, which appear to be having constant security problems.
(01:12:37):
And again, not cuz anybody's malicious, typically just because, you know, there are unprofessional developers who, who, who, you know, create a widget and think, Hey, I'm gonna make this available to other people anyway, adding protection from word fence if it fits your budget, would seem like a large and worthwhile ounce of prevention. So, just a reminder that those guys are there and they really are on the ball. And finally, the Russian government has fined the Wiki Media Foundation. You know, the organization behind the Wikipedia portal, 2 million. Okay, well, rubles, that's about $27,000 Oh, for failing to delete mis misinformation, Leo, about the Russian military and its invasion oops. Its special operation in Ukraine. According to Reuters, this is the third time Wikipedia has been fined by Russia since the country's invasion of Ukraine. Wikipedia said the recent fine was related to articles on its Russian language portal related to Russian invasions of Ukraine, the battle for Kyiv war crimes during the Russian invasion of Ukraine, the shilling of Marol Hospital, the bombing of the Marol Theater, and the massacre Inm Bucha.
(01:14:05):
I noted last November when the second of the, oh, I'm sorry, I noted not, not here on the podcast, but I noted that last November when the second of the three fines was levied, the same fine of 2 million rubles was set. But back then, those 2 million rubles were worth $33,000 today, 27,000. So those rules appear to be slipping against the dollar a little bit. The Wikimedia Foundation has stated that they refused to back down and remove what it said was clearly fact-based, multiply sourced, verified truth. And they've been appealing these fines in Russian court so far. They've only had one successful ruling. But no, we can hope, I mean, Leo, I wouldn't expect much from the courts to be honest with you, but I'm surprised they even like bother father. Yeah. Like, you know, I mean, who runs those courts? Let's think about that, right? Yeah. And I, you know, I would imagine if they, you know, they should not pull the content down. If Russia wants to block all of Wikipedia, fine. Let 'em then just another loss for Russia's citizens, right? Who are, you know, part of, part of this mess. Sad. It's very sad. Sad. Okay, our last break and then, oh, baby we're gonna discuss a foul incident. <Laugh>. I can't wait.
(01:15:40):
I was trying to decide where to go to dinner tonight. I'm thinking now, Popeye's, but we'll find out. We'll find out. Stay tuned. Our show today, brought to you by Collide Coli, K O L I D E. It's a device trust solution that does really the most fundamental, most important thing, and make sure unsecured devices cannot access your apps. Now think about it. If, if LastPass had this, they might be in a different situation these days, right? The, the key of course to security is to make sure that people who are running insecure devices and apps aren't accessing your devices and apps. Collide has some big news. If you're an Okta user, I know many of you are collide can get your entire fleet to 100% compliance. Collide patches, one of the major holes in a zero trust architecture, device compliance. Think about it.
(01:16:44):
Your identity provider only lets known devices log into apps, right? So far so good. But just because a device is known doesn't mean it's in a secure state. In fact, I'm gonna bet plenty of the devices in your fleet probably shouldn't be trusted and you're trusting 'em right now. Maybe they're running on out-of-date OS versions, or maybe they've got unencrypted credentials lying around. There's a whole lot of things. Their browsers aren't up to date. If a device isn't com or they're running an old version of Plex, if a device isn't compliant or isn't running the collide agent, it can't access, it won't be allowed to access the organization's SaaS, apps or other resources. The device user can't log into your company's cloud apps, not until they've fixed the problem on their end. It's that simple.
(01:17:35):
For example, a device will be blocked if an employee doesn't have an up to date browser. But here's the thing, it's not just slam the door in their face. It's gonna use end user remediation to get the user to fix the problem and drive your fleet to 100% compliance without overwhelming your IT team. That's what Collide does. Without collide, your IT teams have no way to solve these compliance issues or stop and secure devices from logging in. But with Collide, you said, and enforce compliance across your entire fleet is another great benefit of KA collide. It's fully crossed platform Max Windows, even Linux collides unique in that it makes device compliance part of the authentication process. So the user logs in with Okta collide alerts them to compliance issues and says, mm, mm mm prevents unsecured access devices from logging in. And this is security you could feel good about because Collide puts transparency and respect for your users at the center of their product.
(01:18:37):
To sum it up, collide method means fewer support tickets for you, less frustration for you and your end users, but most importantly, it means a hundred percent fleet compliance. Visit collide.com/security now learn more. Book a demo, K O L I d e.com/security. Now this is a great idea and a much needed piece in that overall security puzzle. Collide, K o l i d e.com/security. Now, Al, now I can't wait to hear all about this foul story. We are going to encounter a mystery and solve it. Ah, when I read from a Chick-fil-a, ah, data breach report, <laugh>, okay, submitted to the US state of Maine's Attorney General, which disclosed that 71,473 Chick-Fil-A account holding customers had, had their accounts breached through a credential stuffing attack. I was skeptical, and I'm at least still a bit confused, that number just seems far too huge to be the result of what amounts to opportunistic, previous breach driven guessing of account user and passwords.
(01:20:08):
And really, okay, think about it. Why would some random hacker be going out of their way to compromise the accounts and more than just a few of Chick-fil-A customers? Why not Chase Bank of America or TD Ameritrade? I mean, chick-fil-A really, you know, you know, those are the customer accounts that you choose to penetrate. You must really have a thing for chicken <laugh>. So, I don't know. I, I, I don't know. It, it doesn't make any sense to me that number, first of all seems too big. 71,473 individual Chick-fil-A customer accounts each, which would've taken effort to compromise. And what do you get for all that effort? I don't know. Apparently some Chick-fil-A redeemable loyalty reward points, okay? We've been talking about this form of attack recently, but just to reiterate, since this is where details matter, credential stuffing attacks are the reuse of username email and passwords leaked from previous online site breaches, which are then being used to blindly guests log in credentials at other unaffiliated websites.
(01:21:25):
The point is, as I've said before, all rational logic suggests that this should be an extremely low yield attack. Meaning that in order to correctly guess the logins for 71,473 individual Chick-fil-A customers, it would be necessary to wrongly guess a gazillion other times. When I initially saw that large number, my first thought was that it couldn't actually be a true credential stuffing attack. And for the record, I've never been a fan of the term credential stuffing. The industry I think could have come up with a better name like credential reuse attack, but credential stuffing it is, and as long as we all know that it's a credential reuse attack, that's fine. So for that many accounts to be successfully attacked, I'm suspicious of whether Chick-fil-A might have earlier lost control of their own customer account data and that the leaked information itself was now being used to log in and attack their customers.
(01:22:35):
This would, you know, this would convert the attack from surprisingly successful low yield against a bizarre target to unsurprisingly high yield against the only available target. You know, if it was Chick-Fil-a's data that had been breached, you know, leaked, you know, if you've somehow acquired Chick-Fil-A's customer log on data, then that's gonna be your only target. On the other hand, if we assume that this was actually a true credential stuffing attack, and putting aside for the moment the question out of a universe of equally suitable targets, why would an attacker choose Chick-Fil-A, the Chick-Fil-A's disclosure to various states Attorneys General did Really, I wouldn't even choose him for a chicken sandwich, let alone No. A credential stuffing attack. No, no. And you'll get a kick at the, at, at, at what I put down at the very end of the show notes, but, okay, we'll get there here in a minute.
(01:23:43):
The Chick-fil-a's disclosure to various states Attorneys General did state that the attack took place over a two month span. So this is Chick-fil-a's disclosure, right? So Chick-fil-A is saying the attack took place over a two month span from last December 18th through February of 12th last month. Okay? So that's 56 days during which 71,473 Chick-fil-A customer accounts were breached at an average rate of 1,276 successful account breaches per day. So the logistics of such a credential stuffing attack would be that an attacker has a massive database of prospective login credentials, which they for some reason choose to aim at Chick-fil-a's website <laugh>. I mean, first of all, who has an account with Chick-fil-a <laugh>? Well, yeah, you'd have to be quite a fan. I agree. <Laugh> and in blind account credential guessing they then pour this massive database through the website's, clearly unrestricted authentication front end at presumably some massive rate.
(01:25:09):
Perhaps the attack was distributed with the massive database spread among many attacking clients in order to increase the overall rate of credential guessing, because of course, modern websites are able to simultaneously entertain many incoming connections. But in a situation where there's no apparent oversight over failed authentication, which must have been happening with like millions of instances, monitoring or throttling of failed authentication of any kind is missing. So, you know, there's no real need to distribute the attack. Nothing prevents a single attacking machine or only a handful from each establishing their own hundreds or thousands of simultaneous login sessions with a single Chick-fil-A server. That works too. If we accept Chick-Fil-A's claim that this was truly blind credential guessing from a database of previous completely unaffiliated websites, then the per guest yield had to be quite low. <Laugh> a ver a it, you know, again, how many people are there in this leak database that also happen to be Chick-fil-A customers?
(01:26:25):
Oh, I'm looking at Chick-Fil-a's website now, cuz I'm really curious, why would you have a login? And they have something called Chick-fil-A one, which is yes. A point, you know, a customer loyalty thing, you earn points and then you get some, you know, a free waffle fry or something. Yeah. It's, you know, every, every x number of, of coffees I used to buy at Starbucks, I would get a, I would get a yes. So that's what it's stars. But again, why would you want to hack it? What are you gonna get? Somebody's Chick-fil-A points. Exactly. <laugh>. So maybe their credit card. I mean, it had to be Well, and that wasn't available. It there, there it was blinded so it, it it could not be seen. Okay. Okay. So it, so the yield per guess had to be quite low. A very low per guess yield meant that the total number of guesses had to be massive.
(01:27:15):
So this in turn means that the Chick-fil-A website servers raised no alarm of any kind while starting last December the 18th. Their incoming connection rate had to have skyrocketed as millions of attempts to log in there were now failing <laugh>. The authentication failure rate had to be astronomical <laugh>, yet nothing at their end took any notice. So that's, this is a crime of opportunity because most sites you wouldn't even be able to do that. They'd be rate limited or the, you know, they, an alarm would be raised. Maybe Chick-fil-A just didn't have any protection. Clearly they didn't. Right. Or it wouldn't have, they weren't paying attention 50, 56 days Yeah. Without them noticing. Yeah. Once Chick-fil-A somehow became aware of the attack, presumably when a sufficient number of their own customers complained of some sort of account tampering like, where did my chicken bone points go? Or whatever the hell it is. <Laugh>,
(01:28:16):
You know, they were, they were able to identify Exactly. You know, cuz that's what you want is they want the chicken bone bones, I want those chicken bone points. Mm-Hmm. <affirmative>. That's right. They were able to identify exactly which of their customers had their accounts breached in this manner. First, remember we have an exact count, right? 71,463. We're never gonna forget that in, in a way, this is Chick-fil-a's way of saying, we just never thought anybody'd want to get in <laugh> that badly. We didn't, we didn't, we didn't secure it cuz we thought, well, who, who would care if you were <laugh>? Oh my gosh. I know. Okay. Okay. So the reports, now that they've repaired any damage done to those customers, they've, you know, restored their previous chicken bone points, <laugh> made them whole again and instructed them to change their Chick-fil-A passwords. And also anywhere else that they were reusing the same password.
(01:29:14):
Okay, that's, now we know what happened. We have two takeaways from this fel incident. First, if we accept on its face that this was an unaffiliated if somewhat bizarre attack, then it could only have succeeded as it has due to the continuing presence of a widespread and stubborn reuse of user passwords across sites. Oh. But we know that happens. We really do. And we do, unfortunately. Yeah. And of course that, and remember, that's not yesterday. That's today. Right now. Yeah. This was, this was just happening. This means that more than ever, it is rapidly becoming truly imperative for the uniqueness of passwords to be enforced across all of the user's online accounts. We've learned from our own podcast audiences' reports in the wake of the last past vault debacle that updating passwords can be a slow, tedious, and laborious process. But now more than ever before, if your password manager offers a global password reuse audit as many do, maybe also a password strength audit.
(01:30:30):
It's important that you allocate some time to begin replacing any duplicated passwords and also in strengthening any existing passwords that, that do not contain sufficient state-of-the-art entropy. I'm sure that this message is largely redundant and is unnecessary for this podcast audience, but the success of this Chick-Fil-A attack informs us <laugh> that everyone listening needs to share their understanding of this and why this is important with everyone they know. Yes. Adjacent podcast adjacent listeners. Yes. Yes. Because if we're to believe Chick-fil-A, it's clear that the reuse of passwords remains widespread across the internet. And we're starting to see an evolving epidemic of this new form of surprisingly successful attack. This brings us to the second and more interesting technology question. What can websites do in the face of what appears to be an escalating and approaching epidemic of opportunistic low yield credential reuse attacks When a logger, when a whole lot logger, when a user logs into a website, their browser requests the login page, which presents a form to be filled out. Okay? Now I got to this point in preparing today's show notes when I thought that I ought to go over to Chick-fil-A's website to see whether they presented the login as a single form or multiple staged forms. And what did I find?
(01:32:19):
I have a picture of what I found in the show notes. You can go to Chick-fil-A and click log in and you'll see it too. There are a pair of standard login credentials, prompting for email address and password, but there's also a sign in with Google and a sign in with Apple. Mm-Hmm. <affirmative>. And in the spot where there was once a sign in with Facebook. Oh. The page now reads, looking for Facebook login. Isn't that interesting? Hmm. Clicking that link takes existing Chick-fil-A customers to a page that says it screams in Big red boldface Facebook login is no longer available, huh? It says, to continue using your account, you will need to set up an email and password login method. In other words, old school, please enter the email address associated with your Facebook account to get started to find your Chick-fil-A one account.
(01:33:30):
And then they prompt for your Facebook email. But they're not letting you log in with your Facebook account any longer. Though we cannot know for sure when Chick-fil-a's probably most popular login with Facebook OAuth two option was removed. Anyone doing some forensic post-incident digging would be skeptical of the coincidence given the recent attack. Unfortunately, since their login page is algorithmically generated and thus cannot be brought up with a specific, with a static url, the internet archives Wayback machine cannot be queried to see when login with Facebook was removed as an option. But given that login with Google and Login with Apple are both still present and that Chick-fil-a's replacement for login with Facebook is migrating users from Facebook login to their native login, I would, but I would bet a month's pay that. Now we know what actually happened. It was not a generic credential stuffing attack, it was specifically a Facebook credential reuse attack.
(01:34:56):
And now we why Chick-fil-A was the target. It was because they offered the popular login with Facebook option. Somebody somewhere has a boatload of in the clear Facebook login username and password credentials. And over the course of several months, they explored the intersection of that stolen Facebook credential set with the Chick-fil-A customer account database, which is pretty close to one to one. I'm betting <laugh>, I don't know, but I'm just thinking. But you, you'd have to log into face. So you'd have to have a Facebook cookie on your browser, right? No, no, no, no, no. You, no. Could you log in with Facebook and that'll do it? Exactly. Yeah. You, you click log in with Facebook, then you provide the, your Facebook credentials and you're logged into Chick-fil-A. There were 71,473 Chick-fil-A customers Wow. Whose Facebook credentials are part of the stolen Facebook data set. And as a consequence, their Chick-fil-A accounts were breached.
(01:36:18):
Now when you think about it, if you had a trove of valid Facebook login credentials, what's the most valuable thing you could do with them? Who wants to log in to those random users Facebook accounts? There's no money in that. No. What you wanna do is leverage the increasingly pervasive use of o o two account login to compromise the myriad other accounts belonging to those hapless Facebook users who have chosen to identify themselves to other website properties only through their Facebook credentials. Hmm. So you're testing it. You're not trying to get chicken points? No, no. You No, no. In fact, those, the, the, the, the stolen accounts were for sale on the dark web. People wanted chicken bone points. Oh, okay. Okay. All right. Okay. So they were actually compromising those accounts. So that was intentional. They intentional just that were worth something.
(01:37:22):
Aim a little higher kids. I just, but think about it. You, so again, if you have Facebook, if you have valid Facebook login credentials, you don't care about logging into people's Facebook accounts. No. Who cares about that? You wanna log into the other accounts, right? Those people have elsewhere on the internet where they've used Facebook to identify themselves. Now, probably a lot of these people don't use two factor either, right? Right. So all you need is the credentials. You don't. Correct. Yeah. So now as the attacker, you have a valuable and potentially widespread attack, if this is true, as seems extremely likely given all the evidence. We have a perfect example of why the use of oof two for logging in with a common credential poses a significant threat. What are we loudly telling everyone who will listen about their passwords? We're saying do not use the same username and password to log into multiple websites.
(01:38:28):
Right? Everybody knows that. But the use of oof two, which is now being actively promoted due to its extreme ease of use, is a direct contravention of that advice. It is the explicit reuse of a single set of credentials, Facebook credentials, across a great many website properties. And while there may not be much value to an attacker to use a stolen Facebook credential to log into that Facebook user's account, there might well be significant value in their ability to log in everywhere else that Facebook user use their Facebook credentials to create non-Facebook accounts. So this begs the question, how are in the clear Facebook account credentials harvested? And we quickly find an example, Bloomberg News Technology and cybersecurity article from October 7th, 2022. Okay, just last October, just two months before we're told the attack on Chick-fil-A began, has the headline, Facebook is warning 1 million users about stolen usernames and passwords.
(01:39:51):
The article says, the company found more than 400 problematic Android and iOS apps, games and photo editors tricked users into providing credentials. Okay, now just grabbing one paragraph from Bloomberg's coverage. They wrote, A typical scam would unfold, for example, after a user downloaded one of the malicious apps, the app would require a Facebook login to work beyond basic functionality, thus tricking the user into providing their username and password. Users could then, for example, upload an edited photo directly to their Facebook account. But in the process, they unknowingly compromise their account by giving the author of the app access. So what the Chick-fil-A attack probably reveals is the new use to which stolen Facebook credentials are now being put again, obtaining access to a Facebook user's account is far less profitable than being able to log into any and all of that user's non-Facebook accounts where they may have something of value.
(01:41:10):
Most users, as we know, have not the faintest clue how all of this technology we've given them to use works no idea whatsoever. And Leo as the tech guy, you know that better than anyone. Yeah. So when they're asked by a spiffy neat app they've just downloaded to provide their Facebook login credentials so that the app can link to and synchronize with their Facebook account, they don't know any better. Right? Why would they? Right? And most users would not understand that in the process, thanks to the fact that they've also been using login with Facebook everywhere they possibly can because it's so much easier to do that, that they're also giving away the access to their accounts at all of those other websites as well. We've often noted that the use of oof two is an inherent privacy compromise since that third party, Facebook, Google, apple, or whomever knows everywhere you're using them to log in and where you are at the time.
(01:42:23):
But this Chick-fil-A attack with its subsequent removal of its most popular login with Facebook option reveals a much darker side of the widespread use of this form of single sign-on solution. All of the common wisdom urges users to avoid credential reuse. But credential reuse is exactly what single sign-on promotes. And thus, this foul incident as highlighted, has highlighted a worrisome truth behind a growing trend. And I leave you with the end of the show notes picture of the week, which I found on the Chick-fil-A site, which is also a little cute <laugh>. It's, it's got, it's got four cows standing up each holding a portion a sign. The first one says eat. The second one says more m o r and the third one says chicken. So yes. Yeah. This is the famous, the cows are, the cows are encouraging you to eat more chicken and less, less burgers and more and less beef. Yes. More, yes. More chicken fingers. Which is amazing cuz chickens don't even have fingers. Well, well, sir, you have, you have done it again. You have, you have gotten to the bottom of one of the nation's most critical security issues. <Laugh> <laugh>,
(01:43:52):
The incredible Chick-fil-A breach. Be sure to dump your chicken bone points out before the next half. You now, you now ex you've now explained it to all in a way no one else. You, this is a scoop, sir. This is a scoop. You've figured it out. I, you know, just turn on two factor everywhere Facebook has it. I don't know why you wouldn't use it. And then you, no one steal your chicken bone points, okay? Yep. Okay. Or any other bone points anywhere else. Keep your bone points to yourself, Mr. Don't keep. However, don't keep your podcast points to yourself. Spend them right here. Join us every Tuesday as we do security. Now, I know you want every copy of every show. Steve has 'em. In fact, he has unique versions of those at ours website, grc.com. He's got 16 kilobit versions. I think you've got 16 kilobit of every single one, right?
(01:44:45):
16 Kilobit audio. I went back and squashed down the ones before. Oh, they sound terrible, but they're small. They're small. He also has transcripts and Elaine has written transcripts for all the shows. Yep. So that's a really nice thing. You can use it for searching, but you can also use it for list reading as you listen or just reading 'em standalone. Although why you wouldn't want to hear Steve's d tones on your podcasting devices Beyond Me. GRC dot com's, A place to get those. He also has the full 64 Kilobit audio version of us. Well, while you're there, check out Spin, right? The world's finest mass storage, maintenance, and recovery utility now at version six. But 6.1 is imminent and if you zeroing in on it home and right in there home and right in, all you have to do is buy 6.0.
(01:45:34):
You'll get 6.1 the minute it's available, grc.com, lots of other free stuff there. Browse around to your heart's content. You can even leave Steve feedback questions or comments at grc.com/feedback. You can also tweet him. His dms are open. So he takes direct messages as well at his Twitter account, which is SG G R C SG grc. We have copies of the show on our website, TWI tv slash sn. We've got 64 Kilobit audio and our unique version is video. You can watch Steve as he works at twit tv. There's also YouTube channel, which is of course also video dedicated to security now. And you can subscribe in your favorite podcast player. Get it that way the minute it's available. You can also you can also watch us do it live. You get the freshest version if you tune in right after Mac Break, weekly of a Tuesday, usually around one 30 Pacific, four 30 Eastern, 2130 utc@live.twit.tv.
(01:46:33):
Wait a minute, do we set the clocks back this weekend? This thing I think we do. It is, it is one of these weekends in March, March soon. So it will be instead of 2130 utc, it'll be 2030 UTC starting next week. I believe we, we we're, we're going going back to summertime. So anyway, you figure it out, don't miss it. If you're watching live, you could chat live. We have an IRC channel dedicated to the, the Twit network@irctwit.tv that's run by our community, our great community. We also have the Club TWIT Discord. You can join that if you're a member of Club Twit. And I encourage you to join Club Twit seven bucks a month. Get you, add free versions of this show and every other show, special shows we don't put out anywhere else. You get access to the Discord, lots of extra content, and it's just seven bucks a month, twit.tv/club twit to find out more. And we do appreciate all of the Club TWIT members who make this show and all the shows we do possible. It's really a, a huge boon to us. So thank you, Steve. Have a wonderful week. We'll see you next time under daylight saving time indeed spring. Indeed, we will. And who knows what the week will bring. We'll find out and we'll let everybody know.
(01:47:51):
Bye.
Jason Howell (01:47:53):
If you love all things Android, well, I've got a show for you to check out. It's called All About Android. And I'll give you three guesses. What we talk about. We talk about Android, the latest news, hardware, apps, we answer feedback. It's me, Jason Howell, Ron Richards, Huyen Tue Dao, and a whole cast of awesome characters talking about the operating system that we love. You can find all about Android at twit.tv/aaa