Security Now Episode 904 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for security. Now, Steve Gibson is here and the topic of the day, really the topic of the whole show is the topic everybody has wanted Steve to comment on since the news broke late last year about the last pass reach, what happened? What does Steve think and what's he gonna do that's coming up next. Before we get to the show though, I want to do one thing. We do this every year. I want to invite you to take our twit audience survey. It's at twit.tv/survey 23. It should only take you a few minutes. It helps us understand our audience. We do this only once a year. We don't track you, we don't want to, but we do need for advertising purposes to know a little bit more about you. It also helps us decide what shows to do next. So if you want your listening experience to be a little bit better, if you want to get your voice heard, it's completely optional, but we sure appreciate it. Go to twit.tv/survey 23. I shouldn't tell you this, you have to the end of the months, but please don't wait. Do it <laugh>. If y'all do it now, then I don't have to mention this again. <Laugh> TWIT TV slash survey 23 and now security. Now
(00:01:15):
Podcasts you love
... (00:01:17):
From people you trust. This is TWiT.
Leo Laporte / Steve Gibson (00:01:25):
This is Security Now with Steve Gibson. Episode 904 recorded Tuesday, January 3rd, 2023. Leaving LastPass Security now is brought to you by Fortra. The cybersecurity landscape is full of single solution providers, making it easy for unexpected cyber threats to sneak through the cracks. That's why Fortra created a stronger, simpler strategy for protection. They're your cybersecurity ally, working to provide peace of mind for every step of your journey. Learn more at fortra.com. And by Thnks Canary. Detect attackers on your network while avoiding irritating false alarms. Get the alerts that matter for 10% off and a 60 day money back guarantee. Go to canary.tools/twit and enter the code twit in the How did you Hear About Us Box. Thanks for listening to this show. As an ad supported network, we are always looking for new partners with products and services that will benefit our qualified audience. Are you ready to grow your business?
(00:02:31):
Reach out to advertise at twit tv and launch your campaign Now. It's time once again. First show of the new year for security. Now, here he is well rested, relaxed, hasn't had a security problem in weeks. Ta So Steve Gibson. Hi, Steve. Yo Leo, great to be with you for this first podcast of 2023. Wow. Did you have a good holiday? I did. I got a lot of work done, which is, for me, that's a good holiday. And I apologize to my lovely wife who just said, you're a machine. Yeah. And I said, well, you know, I, when you love what you do, you do what you love. You kind of have to though to be a good coder. You kind of keep, it's you, you get rusty quickly, so you have to keep going. Right. That's been my experience on cnn. Farid Zakaria had a series of interviews of like, well, people we all know.
(00:03:30):
And the one that I thought was interesting was Elton John. Yeah. And and you know, we, you, you hear about these guys who are like this amazing, but when you look at the backstory, like there, when in, in his twenties and thirties, he didn't think he was gonna succeed. No. Little Reginald Peron, he was, they, the Beatles used to mock him <laugh>, but, but he knew the Beatles on the bright side. <Laugh>. Yeah. Anyway, so I, I guess my point is that, yeah, you know, I've been programming computers since I was 14 and because I love it. Yeah. And, and I have a, I have a plan that's going to keep me coding until I'm finally dry. Okay. Where did the enter key go? What, where, what is it? Has it gotten harder or easier for you as time goes by? I, I suspect that I, I guess it was, it would be a change in characteristics.
(00:04:30):
The, the, certainly the way I approach solving problems in code has matured so that things are, things are easier because I'm not painting myself into corners that when surprises occur, it's like, oh, look. In fact, I had that happen a couple weeks ago. With, cuz I rewrote spin rights logging system completely. Well, it turns out the, what I had written was pretty good. And so it allowed me, it, you know, it didn't fight back very much when I was like trying to change the way it worked. And it's like, wow, this was a pleasant experience. I didn't think I was gonna have that happen. So, you know, in, but you know, in what, when you're starting out, you, you can sort of force the computer to do what you want, as opposed to it just sort of gracefully agreeing. And, you know, those are, and that's a sort of a con a, a consequence of the way you approach code.
(00:05:23):
So, and somehow I think you get it in your mind and you're speaking a language that is second nature. And so now it's a question of just conversing. Right. And, and I think, I think in the beginning I was cuz I, I, I, I remember I was editing a series of books in my late teens called Teacher Self Basic. Oh, yeah. Bob a All Bob Albrecht was the author. And you were 19 in editing Bob Albrecht's books. Yeah. Wow. <Laugh>. anyway, but Wow. But I, I remember coding back then because I, you know, didn't have a lot of experience when when the program didn't do something, you'd go, oh, and you'd like, stick in a go-to. Right. Right. You'd like, like, oh, I need an if statement here to make it go over here a bandaid over. It's like, yeah.
(00:06:16):
It, it was just like, oh, not, not worse. And it got worse and worse and worse. Exactly. Because you, you end up just chasing yourself around stairs. Oh, wait, now it needs to be this. Yeah. Unless it's this, in which case we wanna go over here <laugh>. So yeah. Anyway. Yeah, you don't do that anymore. You know, you, because you have enough experience now you kind of know the consequences of that kind of behavior. Yeah. And, and I will tell you though, the same problems or the, the, the, the same issues always exist, which are those off by one problems. That's like something fundamental. It's universal computers. Yeah. It just, you know, do I mean greater than, or do I mean greater than or equal to? And it's like, oh. And so now, you know, I'm just, so, so I think what, what you learn is to be very careful about those.
(00:07:06):
They're, you're not gonna get rid of them because, you know, you can't. But, so, but what you can do is appreciate that there's a landmine every time you're, you know, checking to see whether, wait, do I mean to the Carrie Bid is on, or the Carrie and the Zero Flag are on. Yep. Yep. So, yep. You know? Yep. I totally understand it. Yep. That's what you're using. Okay. So let's get to the show. Here we go. Our listeners will be glad, those who have already left to know that the title at the today's podcast is Leaving Last Pass. Yikes. I have to say I left almost two years ago, more, maybe more for Bit Warden, and then about a year ago, I finally said, I'm gonna delete my last Pass vault, which as it turns out, I'm thanking, thanking goodness for I do hope they didn't back it up somewhere.
(00:08:01):
And that, that wasn't the backup that was downloaded. There's no assurance on that. You know, this past couple weeks, a single topic has dominated the security industry, and by far the majority of my Twitter feed and dms, you know, it, it had just exploded. So today, after a brief update on how my holidays went with spin, right we're gonna spend the entire podcast looking at a single topic, which is last Pass. Mm-Hmm. And, and I, I think everyone is gonna appreciate this because, you know, there's no hyperbole, there's no hyperventilation. There was plenty of that on the internet. And we'll talk about some of that, because that's part of what fueled everyone's frenzy. So we're, I'm gonna do a little bit of taking down of the take downs, but you know, so the question is what happened? What does it mean?
(00:09:01):
How, how worried should you be? What are the consequences and what's next? And of course, we have a great picture of the week, so very important subjects and we will get to those in just a second. But before we do, we have a sponsor. I would like to thank, they are very important to our forward looking <laugh> prospects here at the Network and for security Now. And I'm very pleased to welcome Fortra. Actually, I had a good conversation with these guys. They used to be, you may know the name Help Systems for 40 years for was Help Systems and known for helping organizations become more secure, more autonomous. Over the years, customers have shared its gotten harder and harder to protect their data. Oh, yeah. No kidding. Cyber threats, of course, evolving. They're becoming more powerful than ever before in an industry where really the only constant is change.
(00:10:04):
Adaptability is the best way to grow in the right direction. Help systems listen to their cu, as they always did for 40 years, listen to their customers concerns, did some problem solving, delivered with impressive results, which means they're actually a different company, almost entirely a different company today. That's why Help Systems is now rebranding. They want you to know as Fork your cybersecurity ally. Of course, help Systems was known forever as being a people First support and best in class portfolio. The best there is in the business. And that's gonna stay the same, the same exact, you know, quality you've expected for years from Help. Systems forres transform the industry by creating a stronger line of defense from a single provider. They work with the top 10. This is important. The top 10 Fortune 500 banks all use for to, to stay secure. Their infrastructure also helps support nuclear power grids.
(00:11:07):
That's, you know, this is mission critical stuff. And forres there to make sure their mission is served without cybersecurity problems. Fortraes key area of emphasis where technology meets humanity includes securing infrastructure. Very important with the power grid, right? <Laugh>, if you've got a nuclear power plant your infrastructure better be secure, I would hope. Securing data security awareness, that's really important. Operational support, your employees need to know what to watch out for, right? For does it all. They have professional security services, which means they can do or help you do pen testing security consulting services. They will help you with social engineering train, learn how to avoid it. They will help you with red teaming. You may have a red team, but a lot of companies don't. Forter can do it all, or they can support your existing Red team with red team exercises.
(00:12:09):
They offer managed fully managed security services, including managed detection and response, managed data loss prevention, and IBM security services. If you're an msp, this is a great addition to your portfolio. I might add throughout every step of your journey. And this is the thing that's made for so well known in the business. For experts are determined to help increase security maturity while decreasing the operational burden that comes with it. They're there as your trusted partner. Your team members Fork understands we're all more powerful when we work together. So they prioritize collaboration with customers throughout every step of their unique cybersecurity journeys for organizations. For knows that the road to creating a stronger, simpler future for cybersecurity begins with a daily commitment to listening to each individual concern and providing integrated scalable solutions. Check out all the critical solutions and experts at the For Family has to offer, including through the combined intel of Fortress, Agari, and Fish Lab Solutions, fortress Quarterly Threat Trends in Intelligence Report.
(00:13:16):
This valuable resource provides an analysis of the latest findings and insights into key trends shaping the threat. Landscape Fortress approach is different in pursuit of a better future for cybersecurity. They are driven by the belief that nothing is unsolvable for tre positive change makers and your relentless ally providing peace of mind through every step of your cybersecurity journey, set yourself up for success. Go to for.com to check out one of their free trials or demos today. Here is to a stronger, simpler future for cybersecurity. Who's in visit for.com to learn more. F O R T R A for.com. Welcome for to the Security Now Family, to the Twitch family. We're really glad to have you. And I think there's a lot of people out there who will be very glad to have for on their side. Check 'em out for.com Picture of the week time, Mr.
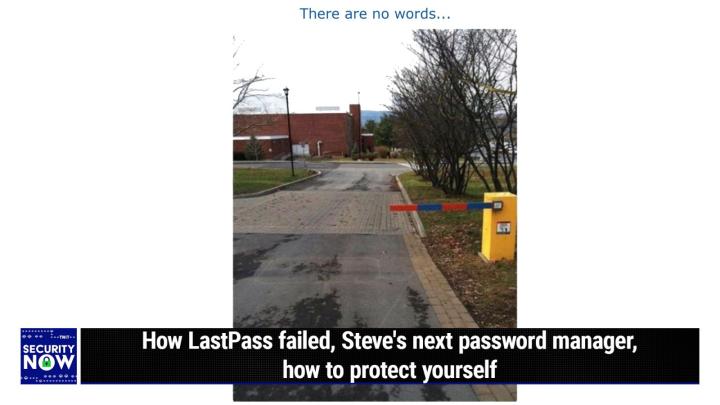
(00:14:12):
G <laugh>. So this is another one of those. I just, I looked at the picture and I gave it the caption. There are no words <laugh>. And in fact, and I immediately burst out laughing when I saw it. Yeah. I, I looked carefully at the road behind where the arm is to see if maybe somebody had photoshopped it to like, to like, exclude the arm from the picture, because how else do you explain this <laugh>? Okay, so, so for those who are not seeing the photo or don't have the show notes, we've got your, your automotive gate, you know, with an arm that comes down in order to block a car from passing. And in fact, you can see these, the, the, the sensor loops that are in the asphalt that, that have the wires going over to the little motor stand that, that moves the arm up and down.
(00:15:08):
So it all looks real. The only problem is the arm extends about like a foot into the roadway. Yeah. And it's a two, it's a two-lane road. There's a lot of room to drive around the arm, let's put it that way. Yeah. I just, you know, somebody went to a lot of trouble. This is a, a bright yellow pedestal with a blue and red striped like visible arm. You know, it's, I was gonna say, so you don't hit it, but it'd be hard to hit it because it's like not in the road, <laugh>. Oh, yeah. That's a good point. It's not even like you could hit it in, you'd really have to work at it. Yeah. Now maybe if your passenger door was open when you were driving, it's just a suggestion. It's a security suggestion, <laugh>. Oh, wow. Anyway, thank you. Whomever said this, I appreciate it.
(00:16:03):
Okay. as I said, if there was any security news that happened since our last podcast, I never had time to track it down since I was digging deep into today's topic, which exploded my Twitter feed. So next week I'll be looking back over everything that has transpired in the security world other than Last Pass since our last Oh, good podcast. Oh, good. Okay. And we'll, we'll catch up. So, you know, nothing is getting by me. We'll, we'll, you know, we'll, we'll be, you know, ne next week will be brought current from the last time we talked. Also the last time we talked, I mentioned that the eighth alpha release of Spin, right, had been put out on the prior weekend before the podcast. There has been no release since we're still on eight. And <laugh>, the testers are getting anxious. Hmm.
(00:17:00):
They're like, Hey, we we're having a lot of fun here. Well, what happened? Okay. So mostly those releases were intended to resolve a couple of mysterious behaviors that people were reporting on seriously damaged drives when they were testing spin. Right. You know, against what turns out, they have literally, our, our testers have boxes of old hard drives that they've been holding onto in anticipation of this day. So, you know, I've got pictures of them like, you know, boxes, and there's like, and they're like ta they, like, they have scoreboards of Spin. Wright has recovered these 11 and it's got problems with these four, and we're not sure about, you know, a couple others. It's sort of, it's a lot of fun. Anyway, because I, I was focused on resolving those few mysteries. It was just difficult for me conceptually to move on because there were some problems that I didn't understand.
(00:18:00):
So I wasn't fixing the growing number of non mysterious things that people were noting. You know, those were things like during intense data recovery spin right? Was not updating its onscreen clocks. They were just froze while Spin Wright was like grinding away on a hard drive, trying, trying to recover a damage sector. Or if the system hung or crashed, the permanent log of all the work that had been done up to that point would be lost because spin right's log was deliberately being kept in Ram until spin right's, graceful exit. But unfortunately, if there was not a graceful exit, you'd get no log. So anyway, thanks to all of the feedback during that first flurry of testing, I saw the spin, right? Could be much more aware of drive trouble now that it was no longer isolated from the drive by the system's bios.
(00:18:55):
So, and more es essentially, the feedback from that extensive initial testing showed me some ways in which I could improve upon my whole first take. You know, I, I want six one to be as good as it can possibly be, not only because we're gonna be living with it for a while during the work on six on spin, right? Seven, but because every way in which I can make six one better today will be inherited by spin right's future. So none of this work is, you know, is gonna get tossed. So I've reworked some significant portions of spin right over the holidays. Logs are now being incrementally written to non-volatile media so that everything that has happened so far will be saved in the event of a system hang or crash. And if the user wishes to write spin right's log back to the same drive, spin right's running on, then it will be spooled to Ram and written at the end, and they're notified that's gonna happen.
(00:19:55):
So they could, you know, change their mind if they want to. I, you know, I've also completely rewritten Spin Rights Clock Management and Completion Estimation system. It's now also providing much more feedback about the state of critically ill drives, which it turns out we have in abundance, thanks to the testers that we have pounding on spin, right? So, I'm, I'm left now with a bunch of to-do list items. Our GitLab has a lot of feedback, so I'm gonna continue planning. Well, I'm gonna continue working on this ninth alpha release that is, you know, when I release it, that's what it'll be because my goal is to basically finish it again, get everything done that I know of that can be finished so that people are not reporting things that I already know I need to do. I'm gonna do all those first and then release nine.
(00:20:46):
This Alpha release nine ought to be like, as close to beta as it can be. I'm sure there'll be a few more iterations. I suspect that these really weird drives are still gonna give spin rides some heartburn. But, you know, now's the time to <laugh> to take an ad acid. So okay, we last talked about last pass following the November 30th disclosure of the second breach. So that was, you know, in each of these breaches, the one back in August. And now that this one in November, there have been a pair of disclosures. There's the, there are immediate acknowledgement that something happened, and then about three weeks later, we get you know, a more fulsome explanation of exactly what that was that happened. And you know, I noted then that the first, that is then on, on November 30th, that the that it was, that the, the I'm, I'm sorry, after the first announcement in August, I noted that their follow up occurred exactly three weeks, 21 days later with the results of that forensic analysis.
(00:22:02):
So when we talked about this on November 30th, our listeners may remember that I noted that we might expect to receive an update on the second breach three weeks after that three weeks after Wednesday. November 30th was Wednesday, December 21st, and the follow up arrived one day after that on December 22nd. Now, the, you know, the likes and the click bait driven tech press and some security researchers postings suggested that Last pass had deliberately timed their bad news for release shortly before Christmas in some attempt to have it swept under the rug. But given the timeline we've seen last pass adhere to previously, I think that's not the case. And it, you know, it's the kind of junk that causes any careful reader to when they see that, if they understand that that isn't actually where the timing came from, to wonder whether what follows will be objective reporting of facts or a subjective smear.
(00:23:04):
Two days after Christmas, a researcher named Jeremy Gosney, who is a widely recognized expert in password cracking, wrote a lengthy and inflammatory takedown of last pass o over on his new Mastodon account. Yes. Yeah, yeah. He, he, he, he recently moved there from Twitter, and in fact, over on Twitter, he said, I won't be posting anything new here. I'm over on Maston. So while Jeremy made some excellent points that I will be touching on here in a few minutes, he, he also suffered from the piling on syndrome. You know, know, for example, he wrote quoting him last passes claim of zero knowledge he has, in quotes is a bald face lie. Nearly everything in your last pass vault is unencrypted. He says, I think most people envision their vault as a sort of encrypted database where the entire file is protected. But no, with LastPass, your vault is a plain text file and only a few select fields are encrypted.
(00:24:15):
Okay, well, you know, <laugh>, what does one say to that? There's, there's nothing about that that accurately conveys the truth or even a sense of the truth. As, as evidence of that, another well-known researcher Wladimir Palant, the creator of Adblock Plus who blogged a lot he, he blogs from his site titled Almost Secure and he had four blogs over the holidays about this incident the day before Christmas. Wladimir posted an article titled What Data Does Last Pass Encrypt? And this is important, he provided a snippet of JavaScript code that could be dropped into any web browser's developer console, which we all have to retrieve the logged on users data blob, you know, their vault directly from last pla, last passes Cloud server. And I'm gonna suggest that everybody listening to this podcast do this because there's some fun things we have in store.
(00:25:24):
In the show notes, I have this little three line snippet of code. So any current LastPass user can obtain their encrypted vault data to examine it for themselves. Open any browser. I used Chrome for this. I also tested on Edge log into LastPass, assuming you still have an account there so that you're looking at your vault page, which is what you get when you log into last pass press F 12 to open the developer tools. I think there's also some other way of getting in there, probably under the main menu. I'm sure you can go to developer tools. F 12 is what I use. And your screen, your screen will basically split into your webpage on the left and this whole bunch of stuff maybe you've never even seen before on the right, which is, you know, where all of the magic under the browser happens.
(00:26:15):
Select the console tab to move to that, to the console view in the developer tools, and you'll have a cursor. So paste the short three line JavaScript query, which is shown above in the show notes into the console, and press enter if everything worked. Your page will, the, the screen there will fill with a large XML format dump containing name value pairs. But the vault is far larger than your page. So look carefully at the bottom of the page where CHRO or Edge will be saying, show more, where you can like, ask it for another chunk, but also offering a copy button, click copy, which will move all of that query response data onto your machine's clipboard. Open a text editor, you know, I use Notepad plus plus on Windows, then paste the clipboard into the editor and save the file so you don't lose it.
(00:27:16):
Okay? Now there's a bunch of stuff there that you can peruse Passwords begin with p with a letter P, lowercase P and an equal sign, followed by a double quoted string. A E S C, BBC encoding has two parts. The first being I will be, I'll be getting into the little bit more of this in here in a minute, but I'm just wanted to g go over this part first has two parts. The first being a pseudo random initialization vector, which CBC requires. And the second half, or part of it being the encrypted string itself, the older format passwords will only have a single Sian encoded string, which is the E C B format encryption of the data since E C B. That's the electronic codebook we were actually talking about back when we were talking about Microsoft Office 365 in October. It does not use an initialization vector.
(00:28:19):
And that's the reason its use has been deprecated. So then with Notepad plus plus, since you're able to do red rejects searches there, I wrote a quick red rejects to scan my encrypted vault for any non CBC encoded or encrypted passwords, and I didn't find any. And I've got, I put the little, the little red rejects expression also in the show notes for anyone who is interested. Now, that's not conclusive, but I'm pretty sure that my vault contains very old and original passwords, which predate last passes switch to cbc and will be getting to why that's important here in a second. So anecdotally, I'm not seeing evidence of old CBC encryption that was, that, that was not autonomously upgraded for me. And again, I just, I wanted to make sure that everyone understood that they are able to easily obtain their, their encrypted last past vault blob and have a look at it for themselves.
(00:29:26):
And we got, I'll have more to say about that in a minute. So anyway, for those who are interested, will Adam Amir's blog posting is titled What Data Does Last Pass Encrypt? And it provides additional details beyond what I've just said, said, and I've linked to it in the, the, the show notes. But on the question of whether any sensitive unencrypted information is contained therein I guess the question is what is your definition of sensitive? And that will vary by user. It, it is certainly the case that, that the last pass vault does contain unencrypted information. Presumably this is for some features that they wanted to provide. It's, you know, it's not exactly clear, you know, why they're doing this. We've got, as you were saying before, le Leo a bunch of smart coders that are listening to this podcast.
(00:30:26):
You were talking about the advent of code and, and your, your work on that over the holidays. I have asked, and I am here asking for some interested hacker coders. Hmm. To write a simple utility to de obviscate all of the non-encrypted data in the last pass blob so that we can all see what it looks like. I know I could, I, you know, I developed squirrel. I could obviously do that myself. I'm gonna stay focused on spin, right? Because that's where I should be. And the hacker coders would rather I finish spin write <laugh>. Yes, they would get, get distracted by this. Anyway. Well, how is it how is it obscured? Is it as a, a, it's ju it's just base 64, and that's, that's, I've got coded. Okay. So that's pretty straightforward. So it will be a, you know, be a simple matter to, to, to, for, to write some code.
(00:31:20):
It, it could be Pearl, it could be Python, it could be whatever. It would be really cool, except for the privacy concerns, to have a website where you could dump the file in and it would give it back to you unencrypted. That way people, you know, it would just be easier for people to use, but they probably don't want to be handing their last pass fault, even though it is encrypted to, you know, some random website. So I think an, an app that you could run on your local machine that de obfuscates the, this last pass vault blob so that you can see the URLs, you can see the email addresses and the things that look like just hex junk now, well, those are not encrypted, they're just obfuscated in order to, to send them back and forth across the internet, because as we know you have to, you, you, you're unable to send any special characters a across a seven bit channel.
(00:32:11):
So, so I, I already posted this, this question and a request for such a utility over in the Security Now News group on G R C, everybody listening to it, ha listening to this podcast is able to do it. You know, shoot me a, a tweet or send a note to, to Greg at, you know, our, our support address at grc. So, so, so that I find out about it and I will post the, the outcome, the results you know, tell everybody a week from now on the podcast how they're able to de obfuscate their blob. I think you should go grab it now though, because LastPass could change this if they decide they don't want everyone grabbing it all, all on the other hand, they probably have to obsolete all their clients in order to change it. So it may be staying where it is.
(00:32:59):
Anyway, I've got mine. You should probably grab yours, and then a week from now we'll have some utilities, I'm pretty sure which will allow us to, to clarify what's there. For what it's worth, somebody who replied to Weir's Post obtained and examined their encrypted blob and was not concerned on his page where he shows their, the, the, the responses to what he wrote, this person said, thank you for this article. As a longtime last pass user, the latest news was unsettling. I dumped my data following your instructions and took a very careful look. I found that user ID passwords, account names, account numbers, and especially the notes, you know, extra, were all encrypted now, okay, this sounds like this person didn't de obfuscate the file, so they may have just been looking for email addresses and user usernames and IDs in clearex, you know, completely legible.
(00:34:04):
Ask e so they may have the wrong idea. Anyway, this person said, I did searches on specific sensitive data and literally inspected every page, and that's a lot of pages, and found no sensitive data that was in plain text. Hmm. On the other hand, all of the URLs were in hex, which to my mind is not encrypted. Okay? So they knew that. They said for, for me, this is a lower priority as my browsing history is collected by everybody these days as evidenced by instant ads for something I just started searching for. I was considering changing password managers, but do not plan to at this point. It has prompted me, however, to change my master password, which has two-factor authentication protection also, and to review my most sensitive data and ensure it is as secure as possible, strong passwords and two-factor authentication, et cetera.
(00:34:54):
Thanks again for this article. It was most useful, and again, I'm not sure this person actually understands what was lost, but we are all going to within the next week, okay, so at this point, there are about five different directions. I want to take this because we have so much ground to cover a little more than you might guess by the end of this podcast. I believe you'll have sufficient information to make an informed decision on your own if you haven't already. And if you have, you'll have more evidence for that decision. And it won't be the result of a bunch of inflammatory and exaggerated half truths. Okay, so let's examine what last pass posted. Just the meat of it on December 22nd, which is stirred up this hornet's nest. The, the, the main issue is a couple paragraphs. They said, based on our investigation to date, we've learned that an unknown threat actor accessed a cloud-based storage environment leveraging information obtained from the incident we previously disclosed in August of 2022.
(00:36:04):
While no customer data was accessed during the initial August, 2022 incident, some source coded technical information were stolen from our development environment and used to target another employee obtaining credentials and keys, which were used to access and decrypt some storage volumes within the cloud-based storage service. They said LastPass production services currently operate from on-premises data centers with cloud-based storage used for various purposes such as storing backups and regional data residency requirements. The cloud storage service accessed by the threat actor is physically separate from our production environment To date. We have determined that once the cloud storage access key and dual storage container decryption keys were obtained, the threat actor copied information from backup that contained basic customer account information and related metadata, including company names, end user names, billing addresses, email addresses, telephone numbers, and the IP addresses from which customers were accessing the LastPass service.
(00:37:20):
This is a little bit more extensive than their initial claim that just some customer information was yes, exfiltrated. And then here's the big one. The threat actor was also able to copy a backup of customer vault data from the encrypted storage container, which is stored in a proprietary binary format that contains both unencrypted data, such as website URLs, as well as fully encrypted sensitive fields such as website usernames and passwords, secure notes and form filled data, which is exactly what we all that we've been talking about. This, this vault blob. So yes, Leo, exactly as you say, this is, you know, this is what this on December 22nd is what blew the lid off of this, is that LastPass confirmed they, that unknown actors have acquired their customer's vaults. All of the vaults, some of the vaults. They're not very forthcoming in this. They're not, in fact, I think they're criminally not forthcoming to be honest.
(00:38:31):
And, you know, every single customer should have now by now received an email saying, yours was one of the vaults. Have you received such an email? Has anybody, we all, we all, well we all, we all received the, the email of this. This is generic though. Is it Mike? Yes. Is it your vault? Is it his vault? Whose vaults? All of them. So one presumes, if it was not all, they would've said some <laugh>, because that would've been, that would've been better than not saying anything. Yeah. no, you know, no coo o worth his salt is gonna say, oh yeah, they got everything, they got the whole farm. In fact, we, we, we haven't seen our, our cleaning people. You know, who knows? Yeah. Okay. So anyway, that last, when, so when they say a backup of customer vault data, it's of every bit of that data.
(00:39:21):
Yes, we yes. You can assume yes. There's no other way to read that. They would've said some, a fraction of fraction of our customers or something like that. Okay, so last pass, admitted that they're offsite cloud backup of their customers, mostly encrypted, but also some not encrypted vault data was exfiltrated and is now in the hands of malicious actors. This is the eventuality that all of this t n o, you know, trust no one client side encrypted before it leaves your computer technology was designed to address. The idea is that, as you know, the u if the user has chosen a strong and unaskable master password, the only thing the bad guys get or got was some less critical metadata, including some web browsing and IP usage history. Okay? So one thing needs to be made very clear while, and, and I've seen some misunderstanding about this already in Twitter, while changing and strengthening your last pass master password now would make or changing the iteration counts now, which we'll be getting to in a second would make any next similar loss by last future hacks.
(00:40:47):
That's right. Less problematic. But that vault data was encrypted with your old master password, correct? We don't, by the way, we don't know how old, cuz we don't know the, the date of the backups. There's so many missing pieces of information. We could at least hope they were being conscientious about backing up. But was this the main backup or just so well the ba we want the bad guys to have the latest ingredient. Gotta have the latest, like yeah, that's right. We want fresh backup. Didn't, but I, but you understand my question. You can't assume that it's your current master password. What if you had monkey 2 2 3 0 3 some years ago? That's, you don't know. Is that in the backup? What vault did they back up? Good point. I think that the lawsuits will probably clarify a lot of this information. I think that's, that's, that's where we're gonna be finding out.
(00:41:35):
Wow. So re so anyway, just to finish the vault blobs, as you said that that ha were stolen, were encrypted under the last pass master password at the time of that backup. We don't know what that was, but it was before today, right? Or whenever you obviously you just changed it af you know, after this announcement. So so, so we wanna be clear about that. Okay, so let's talk about cracking these mostly encrypted vault blobs. Way back before some clever hacker realized that they could program a G P U to run a cryptographically strong hash function very, very quickly. Passwords were protected by hashing them. Like once, you know, that was plenty since the crypto geniuses who designed these hash functions did so specifically to provide that guarantee, which was that passing a password through a hash once would produce a unique value that could not be reversed to obtain the password that was originally fed into the hash.
(00:42:47):
Okay, so no problem, right? Well, not quite right. The way to defeat this mechanism is to get a super fast hashing engine like A G P U, then run every possible password through the hash and see whether what comes out matches what came out when the user originally hashed their password. So somewhere along the way, hackers realized that doing that every time they wanted to crack a password was highly redundant. And this was around the same time that hard drive mass storage as prices were falling. So the concept of a rainbow table was born, the idea was to run all possible passwords through a common hash function that all the websites were using at the time, and do it just one last time. Run every pass every, every possible password through the hash function one last time, but this time store the result along with the password that was input.
(00:43:52):
Then when presented with a hashed password that it leaked from some website breach, you'd just do a lookup in this rainbow table. You'd look for that, the, the same hash and then that would tell you what password was used to to get that hash. And then you'd go run around to the sites that that user uses and log in. Cuz everyone was only using one password back then also. Okay? So, you know, the trouble was hash functions were designed to be both secure and efficient. Where efficient means fast, but fast is the reverse of what we want for passwords, since we wanna prevent this sort of brute force password guessing to obtain a hash, okay? Therefore, password based key derivation functions generically known as P B K D F and there is a popular one that is actually called P B K D F two.
(00:44:53):
They were created, there's a handful of popular PBK dfs that have various features and trade-offs, but most rely upon iterating some core function. They're doing something. Some number of times when I was working with squirrel, I wanted something that was G P U resistant. And so I used S script, which is a so-called memory hard function because there is, there's no way to short circuit the need to have a chunk of memory that is filled up by the password creating pointers that that that the, that the algorithm has to jump around between within this memory. The reason this is it's A G P U defeater is that GPUs have lots of computational power, but typically not lots of memory per core. So, you know, that's an example of, of a a p a pbk d f that that is different than iteratively hashing at the s h a 2 56 function.
(00:46:03):
Some, you know, a whole bunch of times in order to slow things down. But anyway, so that, so that, that's what these things are. As I said, most of them rely on iterating some core function. If performing a single password hash is too fast and it is nowadays, then you hash the hash and then hash the hash of that and then hash it again and so forth. Okay? So where I'm headed with this is that back in 2008 when Joe Siegrist founded last pass, a single hash iteration provided sufficient security in 2008, GPUs had not yet been dev developed and deployed for hashing and computers were much slower than they are today. You know, the cloud didn't exist where you could just borrow some insane you know, computational resources for a few milliseconds, but through the years all of that has changed. So last pass began iterating their P B K D F, the switch from one iteration, the original one iteration to 500 iterations, thus making it 500 times stronger.
(00:47:21):
But on the other hand, it was 500 times very weak occurred in June of 2012. Then, okay, so that was four years after last passes initial launch that only held for about eight months until February of 2013. I guess more like six months anyway no, about eight. Yeah. F February of 2013, that's when last passes default iteration count was jumped by a factor of 10, from 500 to 5,000. And then finally, five years after that, nearly five years ago in February of 2018, the last jump was made from 5,000 to a heady 100,100 that is 1 0 0 1 0 0 iterations. And you told us about this when they did it and told us to up, up it, right? Yeah. Yes. If this sounds somewhat familiar, right? It's because we talked about this change on the podcast at the time, five years ago. Okay? So this, the, the strength of the P B K D F two had that LastPass uses has moved forward.
(00:48:44):
And the last update was five years ago, bringing it to a little over 100, more than a hundred thousand iterations. Okay? So let's switch now from password hashing iterations. We'll be coming back to that in a second to the strength of the password itself. Last pass originally enforced a minimum master password length of eight characters. Again, 2008. Okay? You know, but that too needed upgrading as our systems became faster and as asking users to invent stronger passwords became more socially acceptable. Like, you know, monkey 1, 2, 3, eh, no, I don't, you know, hopefully no one's using that anymore. And remember how far we've come from the days when a user's single password that they used across all their websites, it's like, that's my password was written on a yellow post-it note stuck to their large C R T screen border. You know, that's, that were under the key, maybe under the keyboard if they, if it happened to slip their mind, you know, back then passwords were regarded as a sheer annoyance with no perceived value.
(00:49:57):
Look how things have changed. Five years ago in 2018, LastPass decided that they needed to update their minimum eight character password length and to recommend using numbers and both upper and lowercase letters. But Vladimir Palant noted something distressing about last passes master password strength policy. He wrote When Last Pass introduced their new password complexity requirements in 2018, they failed to enforce them for existing accounts. Mm-Hmm. <affirmative>, in other words, LastPass chose to leave their existing customers possibly two short eight character passwords alone. Mm. Maybe they didn't wanna ruffle feathers or perhaps they were worried about the support requirements of like, oh, you know, people calling up and saying, wait a minute, what I have to change my password? You know, and presumably anyone who has changed their last past password in the last five years will have been required to strengthen it in the process when setting up its replacement.
(00:51:10):
While it's true that LastPass has no idea about the length of their customer's passwords, since all they receive is a hashed blob, it would've been trivial for last pass to add some logic to the last pass client code to scold their users. When the client notices that the master password being submitted no longer meets contemporary complexity requirements, most users would've taken heed of such advice from their password managers. And again, these days we've all grown accustomed to such requirements. So assuming that Watir is correct, and I've read another anecdotal account from someone who today, actually it was yesterday, still has an eight character last pass master password protecting an unused account. So that's suggests this is the case. This means that an unknown number of last pass user accounts whose data was recently stolen from the last pass cloud backup may have only been protected by an eight character password.
(00:52:25):
And unfortunately it gets worse. There are also reports, and I have since I tweeted about this a couple hours ago, I have confirmation from multiple of our listeners, there are reports within the last pass watching security community that last passes P B K D F two iteration count, which was also jumped from, its too low setting of 5,000 up to 100, more than a hundred thousand in 2018 was not pushed out to all last pass users. Oh, that's very bad. And I wrote in the show notes yesterday, if this is true, it's truly horrifying because that's protecting you against brute force, right? Yes. Because taken together it means that there might be last pass vaults, which were allowed to exist for the, the past five years since those improvements were made, which are protected by both short eight character passwords and only hashed 5,000 rather than 100,100 times.
(00:53:41):
And I started that sentence saying, if this is true, now we know it is. I have a bunch of people in my Twitter feed who looked after they, after they saw the show notes, which I posted about an hour before the podcast, that that made them look in their last pass vault and their iteration count was still 5,000. So it didn't automatically reset it to a higher number. No. Now, if you were a listener to this show you'll remember that we at least had set it to 50,000. I remember you saying turn it up to 50,000. That was before the a hundred thousand 100. And, and, and that'd be better. The only, the only expense is time. That is the time it takes the hash when you enter your credentials and then your client says, yeah, okay. You know, like that, that successfully de decrypted the vault blob.
(00:54:35):
So you've entered it, you've entered it correctly. It's more important on a, on a phone for instance, which has a slower C P U than a desktop. Yes. Yes. But how much time? An hour? No, a few seconds. Oh no, no, it's a few seconds. Yeah. And that's why, you know, I'd say set it to a million. Yeah. Set it as as high as you can, right? Yeah. Because you, and the other thing too is, and we'll be talking about this in a bit because there was some controversy that, that that Jeremy raised about, you know, how bad last pass was at keeping secrets. The, the point is we're also not entering our last, our master password often unless we've decided Right? We want lots of security and so we, it should always be expired very quickly. And, and nowadays on most devices, including your phones, you can use biometrics in lie of re-entering the master password.
(00:55:23):
Yep. which I think would limit, you would bypass that pbk pbk DF two, right? I don't know what the, so no that would still do the un unlocking bit. No. so it, it, what it would do is you enter your, your master password once Yeah. Go through that length of time. Yeah. Then the result is encrypted under biometrics and stored locally. And stored locally. Okay. So then, so then you apply your so biometric to be instant and it Yes. It ends up being instant. Yeah. And that's what I do. So plus somewhat mar I would say marginally more secure. Right? Significantly, significantly secure. Yeah. Okay. Yeah, yeah, yeah. Provided that your biometric system is effective as it is on Apple. Yeah. The, the way all of these pbk DF two s are designed, the, the time required is a linear function of the iteration count.
(00:56:13):
So a million is is a flat 10 times stronger than a hundred thousand. Okay. So that's not bad. No, that's good. Yeah. Worth doing. Okay. So, all right. Okay, so now I wanna share some of my feelings about some comments recently made by the well-known password cracker Jeremy Gosney. And since everyone listening to this knows quite well who I am, I want to introduce Jeremy a bit. The relevant paragraph of his LinkedIn bio says, he says, I am also a core developer of Hash cat, a popular OpenCL based open source password recovery tool. And I'm widely regarded as one of the world's top password crackers. I was named one of the top 100 security experts in 2013. I was also one of the winners of cloud flare's Heart bleed challenge, and was one of the first to publish a working private key recovery exploit for heart bleed.
(00:57:10):
My work in research has been featured in hundreds of news articles and has even been incorporated into university classes and certification courses. I additionally served as a judge on the experts panel for the password hashing competition. So this guy is clearly a serious developer techie who is well able to understand everything that he sees going on in a password manager. And Leo, after we take our second break, we're gonna see what he thinks about this. I'm just tooting on because, you know, I don't use that other thing anymore. <Laugh> just saying as I hope Steve discusses the last past breach in today's episode, he also makes recommendations for current users. The episode will be available at twit tv slash sm later today or watch us live. And I wanna make sure people know that there's some more good stuff coming. Okay. Then we're not done yet at https slash i like typing that s slash slash thanks to you Twitter, TV and Google, frankly who made us do it. <Laugh> <laugh>.
(00:58:22):
All right, now we're gonna talk about our advertiser cuz we have a great one and you know it and I know it. They've been with us for a while. The great folks at thinks, the people who make the canary the ultimate honey pot. Here's my canary right now. It tastes like plastic, not honey, but to hackers, this is the most delicious thing they've ever seen. This is a honeypot you can implement in seconds. Put it on your network, put many on your network. Because here's the biggest problem we face right now with with breaches, is you may, you may think you have, your primitive fences are perfect, no one will ever get in. I'm not gonna have a problem with breaches. But what if they do get in? Now what's your strategy for finding out if they're in? And this is the real problem On average companies go 91 days between getting breached and finding out about the breach.
(00:59:23):
That's three months plus that a hacker can be wandering around in your network. Exfiltrating data, downloading, I don't know, password vaults, whatever he wants without you even knowing about it. So what you need is some way to put trip wires inside your network. Sure, you've got your imeter defenses. Hey, keep those up. They're very important. But these little trip wires let you know if somebody's breached. And that is really, really important. The beauty of this is these little devils just sit there quietly, silently without at, at taking any attention until somebody taps on them. And then they let you know. They give you an alert in the way you want. That tells you there's somebody inside the network. Hugely valuable. Now what does this look like to an attacker? Whatever you want. So these are fully configurable. I have this one set up as a sonology nas, it has a Sonology Mac address.
(01:00:27):
Looks just like a sonology. It has the DSM seven login, just like the real deal. It is in no way it's completely indistinguishable. In no way can they tell that this is honeypot. It looks like a nas. It could look like a Linux server, a Windows server. It could look like a Windows box. You can light it up like a Christmas tree, turn on all the services or only. This is what we do. Turn off few services strategically chosen to attract the Wiley hacker. They can't stay away from these. They don't look vulnerable, they look valuable. There's another thing you can do with your canary, which is so cool, is create canary tokens files. They're just normal files. You could put 'em on a thumb drive, bring it over to computer, copy it over. Looks just like a pdf, an Excel spreadsheet, a document, whatever.
(01:01:16):
I always name them. Fun things like employee payroll information or social security numbers. Put those, screw those around your network too. And when an attacker attempts to open them, they phone home, they immediately notify the canary. The canary immediately notifies you. You can order, configure and deploy your canaries throughout your network. By the way, there are cloud-based birds too. I'm holding the hardware bird, but you can have a cloud-based canary as well. Virtual canaries. The canary tokens make one a Windows file server, another one a router, throw in a few Linux web servers. They all host realistic services. They look and act exactly like its namesake. And then you just say all done. And you wait. They're running quietly in the background waiting for intruders. Every customer gets their own hosted management console. So you can configure things right through the console. In fact you can have it alert you through the console, but I think a lot of people maybe would prefer text messages.
(01:02:18):
You can do that. Emails. Sure. Slack. Yep. Web hooks. So that means sports, a whole bunch of stuff. You use Syslog. You still use Syslog. I more power to you. It'll do a SIS log event, but they're gonna let you know your thanks Canaries constantly report in. They give you an up to the minute report on their status. So it's always easy to see is it up, is it running, is it doing its thing? So, you know, but those alerts, when you get the alerts, the warning, warning, danger, alien approaching, those are the real deal. There are no false alerts. It's a real deal. Most companies find out they've been breached way too late. Three minutes of setup, no ongoing overhead, zero false positives. As close as you can get. And you can detect attackers long before they dig in. That's why thinks Canary Hardware, vm, and cloud-based canaries are deployed and loved all over the world.
(01:03:10):
All seven continents. Yes. If you go to, by the way, if you want to just see how much love there is, go to canary.tools/love, and you'll see the, the, the CISO of Slack. All the people who use Canaries saying these things are incredible. So lemme tell you the costs. You wanna know, right? The boss wants to know. Somebody wants to know. I'll give you an examples. You know, a small company like ours might have a handful, right? Big banks might have hundreds. Casino operations. Vni knows. Sky's the limit, right? You want 'em everywhere, anywhere. A hacker might be wandering around, but I'll give you an example. Five Canaries put 'em all around. 7,500 bucks a year. You get your own hosted console, you get upgrades, you get support, you get maintenance, you get replacements for free. You sit on it, no problem.
(01:03:57):
They'll send you another one. And if you use the code Twits, this is important in the, how did you hear About Us Box 10% off your Canary Price for Life forever. They're, they're so grateful to you and we're so grateful to you that you get 10% off forever. Now, another thing they'll reassure you. I know you're gonna love this thing. We, this is such a great tool, a must have for any security operation, but if you're not happy, you can return your canary. And they are so generous cuz they know nobody ever returns them. You got two months to do it. 60 day money back. Full refund guarantee. Okay? So write this down. Canary.Tools/Twit. The code is twit, T w I t in the hat that you hear about us box for 10% off for life. These things I, I don't know how you would operate with Adam if you don't, you have no idea what's going on right now inside your very own network. Canary.Tools/Twit, the easiest honey pot ever. Simple, easy to use, and they work, they're great. Canary.Tools/Twit.
(01:05:10):
Okay, Steve, let's continue one. Okay, so back to Jeremy Gosney. As I said, he is recognized password. Cracker Hacker hashing, guru extraordinaire, <laugh>. So here's how his posting began. He said, let me start by saying I used to support LastPass. I recommended it for years and defended it publicly in the media. So do we Google? So do we. So is Steve, of course, right? It was great. If you search, if you search Google for Jeremy Gosney plus last pass, you'll find hundreds of articles. He says, where I've defended and or pimped last pass. Yes, he said Peren, including in Consumer Reports magazine. He that I defended it even in the face of vulnerabilities and breaches because it had superior user experience and still seemed like the best option for the masses, despite its glaring flaws and has still has a somewhat special place in my heart being the password manager that actually turned me on to password managers.
(01:06:16):
Yes, yes, yes. It set the bar for what I required from a password manager and for a while it was unrivaled, but things change. Mm. And in recent years, I found myself unable to defend Last pass. I can't recall if there was a particular straw that broke the camel's back, but I do know that I stopped recommending it in 2017 and fully migrated away from it in 2019. He says, then below is an unordered list of the reasons why I lost faith in last pass. Now, I'm not gonna drag everyone through all of Jeremy's ranting because I don't think it's rational nor fair to last pass. Recall that even though Jeremy is clearly a highly skilled and qualified technologist, it was he who wrote in this rant that, you know, nearly everything in your last pass fault is unencrypted. You know, and he says that, he said, you know, last pass is claim of zero knowledge is a bald face lie.
(01:07:20):
Well, we already know that, that the, the, the, the intent, the essence of that is not the case. There is, there are things that are not encrypted. And you know, last pass has always been clear about that. It's made some people uncomfortable. But, you know, the bulk of what we have been using last past four is protecting our, our our login credentials. I do have to say it's less than ideal. And, and at least l a bit warden, our sponsor and last, and one password do encrypt that metadata as well. Right. and the only reason it's potentially problematic is cuz now somebody has a list of all the sites you have a password for, right? Correct. Yeah. Correct. And actually we'll be talking a little bit about the, the, the, the metadata consequences here in a second. So, okay. Okay. So anyway and, and you know, he talks about zero is not zero, but you know, he knows what zero knowledge means.
(01:08:21):
It, it doesn't mean, you know, nothing is there that is unin encryption. There's no such thing as perfection. Well, and and you do need some things unencrypted, right? Like the iteration count has to be unencrypted because you need it in order to perform the decryption <laugh>, right? Yeah. So, you know, so, and, and, and, and it would be interesting to know why there are these metadata things that have been left in the clear. Is it just legacy? Is it just because back then, oh, you know, once upon time didn't matter? Is it because they are, they're actively harvesting that information and selling it? I mean, we don't know. Yeah, that's a good question. Anyway. Do you know if Joe, Joe Ri wrote it that way first in the first place? I reached out to him over LinkedIn. He, I don't know if he's even still with last pass.
(01:09:10):
He, I'm gonna, he's not I'm gonna guess he hasn't been for years right. That he is enjoined not to say anything negative about the company. Yes. So I would be surprised if he said anything. Yes. And he did not. Yeah. He sold, he sold it outright. When, when the last time I talked with some people, that last pass, which is about two or three years ago, his niece was still working there and I was very pleased to meet her, but she said Uncle Joe had long left. Although last, was that when we did the Yeah, at the rsa we did the Boston? Yeah. Yeah. No, not Boston. It was RSA in San Francisco. Oh, okay. Yeah. And which they, they hosted a party which we attended in 2020 <laugh> early 2020. But anyway sh they were a little closed lipped about Joe's continued participation now, and it's my sense that he had long left, but they didn't want anybody to know.
(01:10:02):
Well, I, I I, in looking back over the timeline, there was the concern when LogMeIn bought Last Pass, and that's when it started, I think. Yes. And, and he has a couple last pass blog postings for like a couple years after that acquisition, and then there's nothing more from him. Yeah. Yeah. That's when we left. And ly la Long me has spun off Last Pass as a standalone company. So they are now independent right. Of of LogMeIn. Yeah. And as I understand it, they're owned by a, you know, a equity capital company, a hedge fund, the worst possible owner Yeah. Of anybody. Yeah. Yeah. Okay. So the biggest concern is another of those legacy issues, which last pass seems to have been reticent to address. And, and this gets back to that E ec B cbc recall it a few months back, last October in our podcast 8 93, we talked about Microsoft's decision to leave their Office 365 message encryption using the electronic code book that the e c b cipher mode. And remember that to illustrate the danger of that, we showed that classic Linux Penguin where using Cipher blockchaining, the, the good encryption, it, it encrypted the Penguin's image into a pure high entropy rectangle of noise. There was, you could see nothing there, it was just gray. Whereas the use of E C B left a very visible penguin in the image <laugh>.
(01:11:36):
Okay. Yeah. It appears that last pass was also originally using the clearly less secure E c b mode to encrypt its passwords. Then somewhere along the way they realized that this was no longer the right solution. So they began encrypting any newly saved passwords with a more secure C B C mode. But for some reason they never proactively re-encrypt the original less secure E C B passwords under C B C Now, okay, that's the, that's the information that, that is that the security experts who have looked at vaults are claiming my own analysis of my vault yesterday showed no evidence of E C B encryption. You're able to tell because of the format of the string following the P equals, whether it's C, BBC or E C b, mine were all C bbc and I'm pretty sure that I've got some old long abandoned, like my password for hamachi probably <laugh> is in is is in last I did, yeah. <Laugh>
(01:12:54):
Why removed it? And, and, and I have, and I haven't changed it, I haven't removed it, it's still there, but it was not in E C B, it was in C bbc. Mm-Hmm. <affirmative>. So my experience is that mine got updated. On the other hand, I don't know if I changed the iteration count or if they did, but we know that a lot of people did not have theirs changed. So, see this, by the way, I blame last pass at this point for not, they need to put out in this information what did they do? When did they do it? What didn't they do? Yeah. Because why are we having to guess? Right? And, and using hot tempered security experts who, you know, and JavaScript post pasted in the developer options of their website to figure this out. We shouldn't have to do this. They need to come, they've been I think less than forthright, but go ahead.
(01:13:50):
Well I, you know, I'm sure everything that gets published goes passe us through their attorneys and Well, that's what's happening obviously. It's, it's amazing that any amazing that a period came out the other end, yeah. They're doing the minimum disclosure they can legally get away with, which is disappointing. But I, I guess I understand. Okay, so if this is true, if there is, there is, it is the case that c BBC and E c b password encryption is allowed to coexist for some people they were not updated as a consequence of that A user's vault will contain a mixture of old passwords encrypted under E C B and newer ones under C B C. I can find no plausible reason for this being left as it has been. But, and also no verification so far that this is true. Probably a week from now we'll know because I'm sure that a bunch of our listeners are gonna be grabbing their, their last pass blob vault and run it through the, the, the de obfuscate that we're gonna come up with and we'll know if they've got e ECB encryption.
(01:14:58):
The, but you know, one thing that's interesting is that if all your passwords were encrypted under E C B, what this would mean is that last pass on their end looking at your encrypted passwords, even though they can't tell what they are, they can tell when they're duplicated because that's what ECP does. Oh, right. Every time the same password is encrypted under the same key, you get the same electronic code book output. But we, and we know they can do that cuz they will warn you, you've used this password before. Well, but that could be done on the client's side. Oh, okay. So your your your client, right, who has the vault decrypted it sees everything. That's the different, very important to make that distinction between they can see and what we can see. Yeah, yeah, yeah. Right. But what they could see, and maybe this was something that Joe, you know, again, in 2008, you have to pretty much forgive anything.
(01:15:57):
Absolutely. One, one pat, one hash was all anybody was using. And we soon learned, well, let's try 500. Well, 500 we could, we could do that now in a blink. So I'm convinced Joe did the best possible at the time and continue to keep it up to date as long as he was there. I I I know you were convinced of that when he showed you everything. That's why we chose it. That's why we chose it. I mean absolutely is, you know, he, he completely showed me what he was doing. I was able to see to, to duplicate and verify the algorithm, you know, it was all open. Yep. Okay. So anyway, I just wanted to mention that maybe the reason E C B was chosen once upon a time was that again, from the last, from last passes view, they could have seen where the same password be was being used on multiple sites.
(01:16:48):
They would not have been, they would not have had to rely on the client to, to tell them about that. And in fact, I don't think the duplicate password feature was there in the beginning. That was like, like a, you know, a great new feature. It's like, we're gonna help you clean up your recent passwords. Pretty recent, right? Yeah. Yeah. Okay. So that brings me to another Jeremy's points. He writes quote, last pass has terrible secrets management. Your default encryption key is always resident in memory and is never wiped. And not only that, but the entire vault is decrypted once and stored entirely in memory. Okay. And, and, and I wanna point these things out because, because people who read his rant got very upset, but some of this is nonsense and he knows it as we know. I've been saying recently that it would be nice if the last pass vault were being incrementally decrypted.
(01:17:48):
I've, so I've mentioned that every time we talked about LastPass recently, so that only the one password needed for login was decrypted from the opaque blob, which after its plain text was used could be overwritten. But according to Jeremy, that doesn't appear to be the way LastPass manages the user's vault. As for the encryption key, always being resident in memory, that's a pure requirement of any password manager that isn't, that is not constantly pestering us to reauthenticate to it. None of us wanna be constantly doing that. But if you did last pass offers the ability to auto log out after X minutes of inactivity, at which point it would presumably, and I'm sure it does wipe all decrypted content from RAM and require the user to log in again before its next use. Also remember that when you go to a new site, create a new account and last pass says, you want me to remember this for you, you click okay, you don't have to reauthenticate.
(01:18:55):
Well, that means that LastPass has added that to the vault, encrypted it using the key, which it ha, which it has to be decrypted for it to do that and sent the update back to last Pass Central. So again, it, you know, these things, this terrible secrets management is a requirement for the convenience that we're we're all getting from every password manager. So, you know, it's not terrible secrets management as Jeremy characterizes. It's, it's a necessary trade off made for convenience and every other password manager will need to be similarly terrible in order to get its job done without pestering its user to death. And we all need to appreciate that none of the password managers are pretending to protect their users from client side machine attacks. There is no protection for that ever from anyone that isn't available. We're getting the promise that remote websites cannot access our vaults and that our password manager providers and anyone who might attack them also cannot access our vaults.
(01:20:06):
And on that last point, it appears that LastPass has made a series of design policy decisions through the years for reasons only they know that may have left their users less secure than they could have been in the event of the attacks they have just suffered. Jeremy also notes that while last passes Vault key uses a e s 2 56, it's 2 56 bit key is derived from only 128 bits of entropy. If true, that's also unfortunate. Although 128 bits of pure entropy is plenty, why not take the opportunity to generate and use all 2 56 bits for the a e s key? Again, there may be an engineering reason, but overall it feels as though the original security design of last pass, which in 2008 was ample with even Jeremy jumping up and down defending it has not aged well. And that last passes caretakers have not been as excited about keeping last pass on the cutting edge as crypto enthusiasts like Jeremy or I would've been.
(01:21:31):
And that's why after having surveyed all of the available commentary and thinking about everything I've recently learned, I've decided to pull up stakes and leave last pass. Okay? There is a an alternative if you trusted them, but you would have to go through and change all your master pass, not your master, all your site passwords in just in case. I know some people are doing that, but that's could be a lot of work. Well, the problem is, and I mean, and that isn't an alternative because what we're seeing is evidence of them not caring. Yeah. I mean that, that's really what this boils down to is them not caring. And anyone who's been listening to this podcast for a while knows what not caring means. Yeah. Not caring is not neutral, not caring is the, the end of life as you know it from a security standpoint.
(01:22:28):
Because if there is an opportunity for for to, to take advantage of a mistake, that opportunity will be taken. So Jeremy noted that this most recent breach, he said was last passes seventh in the past 10 years. I didn't verify that number, but we all know that they've had their share. And while everyone knows that I'm the first person to forgive a mistake under the theory that they are often unpreventable this recent breach of their cloud pro, their cloud backup provider, which their November disclosure said they shared with their affiliate go-to makes one wonder whether some corners may have been cut in the interest of profit and only insiders know, but there really isn't any excuse for the engineering decisions they've made, which have made the consequences of their now having lost their customer vaults potentially much more serious. They could and should have pushed their legacy users to move to a longer and stronger master password.
(01:23:44):
They didn't, they could and should have had their last past clients upgrade all older E C B password encryption to c bbc. They didn't. They could and should have absolutely upgraded every user from 5,000 iterations of P B K D F two to at least 100,100 iterations. They didn't do that either. We now have confirmation of that. They could and should have kept me as a loyal and faithful LastPass user and evangelist. They didn't. Hey everybody. Leo LaPorte here. I am the founder and one of the hosts at the TWIT Podcast Network. I wanna talk to you a little bit about what we do here at twit because I think it's unique and I think for anybody who is bringing a product or a service to a tech audience, you need to know about what we do here at twit, we've built an amazing audience of engaged, intelligent, affluent listeners who listen to us and trust us when we recommend a product.
(01:24:52):
Our mission statement is twit, is to build a highly engaged community of tech enthusiasts. Well already you should be, your ears should be perking up at that because highly engaged is good for you. Tech enthusiasts, if that's who you're looking for, this is the place we do it by offering 'em the knowledge they need to understand and use technology in today's world. And I hear from our audience all the time, part of that knowledge comes from our advertisers. We are very careful. We pick advertisers with great products, great services with integrity and introduce them to our audience with authenticity and genuine enthusiasm. And that makes our host Red Ads different from anything else you can buy. We are literally bringing you to the attention of our audience and giving you a big fat endorsement. We like to create partnerships with trusted brands, brands who are in it for the long run, long-term partners that want to grow with us.
(01:25:52):
And we have so many great success stories. Tim Broom, who founded it Pro TV in 2013, started advertising with us on day one, has been with us ever since. He said, quote, we would not be where we are today without the Twit network. I think the proof is in the pudding. Advertisers like it Pro TV and Audible that have been with us for more than 10 years, they stick around because their ads work. And honestly, isn't that why you're buying advertising? You get a lot with Twit. We have a very full service attitude. We almost think of it as kind of artisanal advertising, boutique advertising. You'll get a full service continuity team, people who are on the phone with you, who are in touch with you, who support you from, with everything from copywriting to graphic design. So you are not alone in this.
(01:26:44):
We embed our ads into the shows. They're not, they're not added later. They're part of the shows. In fact, often they're such a part of our shows that our other hosts will chime in on the ads saying, yeah, I love that. Or just the other day, <laugh>, one of our hosts said, man, I really gotta buy that <laugh>. That's an additional benefit to you because you're hearing people, our audience trusts saying, yeah, that sounds great. We deliver always overdeliver on impressions. So you know, you're gonna get the impressions you expect. The ads are unique every time. We don't pre-record them and roll them in. We are genuinely doing those ads in the middle of the show. We'll give you great onboarding services, ad tech with pod sites that's free for direct clients. Gives you a lot of reporting, gives you a great idea of how well your ads are working.
(01:27:34):
You'll get courtesy commercials. You actually can take our ads and share them across social media and landing pages that really extends the reach. There are other free goodies too, including mentions in our weekly newsletter that sent to thousands of fans, engaged fans who really wanna see this stuff. We give you bonus ads and social media promotion too. So if you want to be a long-term partner, introduce your product to a savvy engaged tech audience, visit twit.tv/advertise. Check out those testimonials. Mark McCreary is the c e o of authentic. You probably know him one of the biggest original podcast advertising companies. We've been with him for 16 years. Mark said the feedback from many advertisers over 16 years across a range of product categories, everything from razors to computers, is it. If ads and podcasts are gonna work for a brand, they're gonna work on Twitch shows.
(01:28:29):
I'm very proud of what we do because it's honest, it's got integrity, it's authentic, and it really is a great introduction to our audience of your brand. Our listeners are smart, they're engaged, they're tech savvy, they're dedicated to our network. And that's one of the reasons we only work with high integrity partners that we've personally and thoroughly vetted. I have absolute approval on everybody. If you've got a great product, I want to hear from you. Elevate your brand by reaching out today@advertiseattwit.tv. Break out of the advertising norm. Grow your brand with host Red Ads on twit. Do TV visit twit tv slash advertise for more details or you can email us, advertise@twit.tv if you're ready to launch your campaign. Now, I can't wait to see your product, so give us a ring.
(01:29:22):
During my post-incident survey of security professionals, three cloud-based password managers kept being mentioned over and over. They were Dash Lane one password and Bit Warden. We all know that Bit Warden is an active sponsor of the TWIT network and a frequent advertiser on this podcast. So I was glad to see other knowledgeable researchers praising it. Here's what Jeremy Gosney wrote once he had calmed down a bit from his being jilted <laugh> from his being jilted by last pass. I think that's what happened. He he was upset. Yeah. Yeah. Clearly he said, so why do I recommend Bit Warden and one password? It's quite simple. He says, I personally know the people who architect one password. And I can attest that not only are they extremely competent and very talented, but they also actively engage with the password cracking community and have a deep, deep, he says, again, with asterisks desire to do everything in the most correct manner possible.
(01:30:30):
Do they still get some things wrong? Sure. But they strive for continuous improvement and sincerely care about security. Also, their secret key feature ensures that if anyone does obtain a copy of your vault, they simply cannot access it with a master password alone, making it uncrackable. Next he says, bit warden is 100% open source. I have not done a thorough code review, but I have taken a fairly long glance at the code and I am mostly pleased with what I've seen. I'm less thrilled about it being written in a garbage collected language, garbage collected language. And there are some trade-offs that are made there. It's crk, but overall and net, so. Right? Yeah. But overall bit warden. And all you have to do is wipe any plain text. You know, I, I did that in Squirrel as like, you know, before you release memory, you, you zero out the, the, the plain text and then you're fine anyway, he says, but overall bid warden is a solid product.
(01:31:33):
I prefer bit warden's user experience and I've considered crowdfunding a formal audit of Bit Warden, much in the way the open crypto audit project raise the funds to properly audit true crypt. The community would greatly benefit from this. Okay. Now I know from my Twitter feed that many of my Twitter followers, or at least those who are tweeting to at S SG G R C are using one password. I've not looked closely at it, but from what Jeremy says, that would appear to be a solid choice. Another password cracking enthusiast by the name of Steve Thomas ranks Dash Lane. First bit warden second, and one password third. But only because Dash lane is using his favorite PET password. Key derivation function known as Argon two. Argon two is a memory hard function designed in 2015, which is highly resistant to G P U attacks. It won the hashing challenge.
(01:32:36):
Yes. That's being the most secure. Yeah. But it's implementations, it's need to be careful about side channel leaks. Oh, interesting. Since the, the original design accesses memory in a password dependent sequence, thus from, you know, you're able to defer something about the password. Yeah. From, from from memory access patterns as a consequence. Improvements have been made in Argon two since then. But a password manager's choice of his key derivation function is incidental at most. And the strength of any good function can simply be turned up as needed over time. So it appears that all three of these are in the running. Next. I went to check out the personal plans, these three offered blessedly. I don't need a family plan or a business plan or anything other than a, just please keep all of my passwords safe, secure, and synchronized among all of my devices.
(01:33:37):
Plan. Although the value of a password manager is now well proven so that asking for some money should not be a problem. I like the idea of being able to turn people onto it so that they can take it out for a spin without needing to pay in advance for a year's commitment. In other words, a useful free tier such as Last Pass once had, but then abandoned, you know, that was part of my criteria in the beginning. Mm-Hmm. <affirmative> for last pass. That was the beginning, the end right there. I think that went away too. Yep. Mm-hmm. <Affirmative>. So that's part of my criteria for the perfect Password Manager. Unfortunately, dash lane's free plan only a now allows for the use of a single device. So you can't use it on both your desktop and even one mobile platform. Mm. That's crazy. No. Why allow any devices if you can't use at least two?
(01:34:35):
So you need to pay at their minimum plan of $33 per year in advance, which does then provide for an unlimited number of devices. One password doesn't even try to offer a free tier. If you want to use one password, you pay $36 in advance for a year to use it. Bid Warden of the three is the only one to offer an actually useful free plan, which allows for the use of any number of devices. And Leo, as you often note when you're talking about bid warden, since their free plan actually really does everything, you'll probably need their $10 per year paid plan at less than a third. The price of the others is mostly just there to support them, although you do get two factor authentication for, for that $10 per year. Oh, that's worse. And I would a yeah. Yes. And I would argue that for 10 bucks, come on.
(01:35:32):
Yeah. You know, you, you, you should usually see what my latte costs. Now, incidentally, I did ask when they started advertising, I said because we'd been burned by last pass, frankly. I said tell me about the free plan. They said, look, we're open source. It's always gonna be free because otherwise people just Fortra it. It's free, free. We have no, that's not part of our business models to make money on the free plans. So that's reassuring. They're not gonna do the pull a last pass and say, oh yeah, now you have to pay for it. Open source has a lot of benefits in this area, I think, you know. Well, and as Jeremy noted, the icing on the cake is that Bit Warden is also 100% open source. Yeah, I saw a tweet passed by some time ago that our old friend, Alex Nehouse was moving his family to bit warden and choosing to self-host a bit Warden Server.
(01:36:26):
That's another option. Cloud. Yeah. Yeah. And actually after this happened, I kind of, cuz for a long time I've said, well, I'm never gonna be able to protect it as well as professionals at let's say last pass, whoops. Or Bit Warden or one password or Dash Lane will. But then there, there's the counter argument, which is it's a single point of attack. That's where all the vaults are. So if you self-host, I put it on Dropbox, it's encrypted. They'd have to target me or stumble upon it somehow. And even then they'd only get the encrypted blob that we've talked about that is well encrypted. Yep. So I'm thinking about making mine self-hosted now. Well, you know, those are the sorts of things that, that, you know, that the use of a truly open password manager can provide. Yeah. Yes. And, you know, and while it's not of interest to everyone, I imagine that it's a sort of thing that would appeal to this podcast audience.
(01:37:17):
On December 7th bit, warden posted a blog titled New Deployment Option for Self-Hosting Bit Warden. I've got a link to that in the show notes, bottom of page 10 of the show notes for anyone who's, who's interested in taking the path that Alex took. And so, you know, that's something that is that can be done. And in my digging around over the holidays, I stumbled upon a bit Warden page, which linked to their past annual third party outside network security and application security penetration testing audits. So they're auditing themselves, having themselves audited by a number of different outside firms every year. I, I ended up not being able to find that same page later, but I found another that provides the same info and it's under bit wardens.com/help/is hyphen bit Warden hyphen audited. And so there are links there to everything. And I also noted at the bottom of that page that they're signed up with Hacker one to offer and manage bug bounties against their platform.
(01:38:27):
So the reason I originally chose Last Pass and was comfortable endorsing it was that its author opened up its internals to me so that I could understand exactly how it worked and it was solely on that basis. And for that reason that I chose it, I don't regret the decision I made back then. Last Pass has been a flawless companion for me over the years. I say that knocking on wood somewhere because, you know, my Vault has now been absconded with. But as we've observed earlier on this podcast, the world has been changing ever since. And last pass no longer fits the way it once did. And you know, it and its organization is beginning to act and feel a bit too old and creaky, which is not what anyone wants in their password manager. An example of a different, more aware and contemporary approach is bid warden's description of their management of their user's.
(01:39:30):
Master password bit Warden wrote, s h a 2 56 is used to derive the encryption key from your master password bit Warden Salts and hashes your master password with your email address locally before transmission to our servers. Once a bit, warden Server receives the hashed password, it is salted again with a cryptographically secure random value hashed again and stored in our database. The default iteration count used with pbk DF two is 100,001 iterations on the client client side. Iteration count is configurable from your account settings and then an additional 100,000 iterations when stored on our servers for a total of 201,000 iterations by default. Okay. Can I interrupt with a stupid question? What's with the hundred thousand one or the a hundred thousand 100 <laugh>? They don't like round numbers. That is roundish That is a great question. I I, okay. There's nothing, there's no technical, it's just a random, it's not like it's, is not like it's a power of two or something where it's gonna, you know, be some magic.
(01:40:48):
It's, it's bizarre. It's Prime. Oh, well, yeah. And that, that wouldn't matter either anyway. No, I <laugh> So, so, so, so, so Bid Warden is not so, is not only hashing a hundred thousand times on our system and you can turn that to anything you want. And by the way, I would go with like 350,000 that's turn it up. That's pretty much, yeah, I'm gonna turn mine up. That's pretty much where, where you want to be at this point. Okay. And then they're getting it, resulting it and then running it another a hundred thousand times on their, you know, high speed machine because they can just, you know, because, so anyway everybody knows what happened then I went to bit warden.com/twit. Thank you slash twit. By the way, this is is not a paid ad in any respect. This is No, I I this is Steve.
(01:41:37):
I, everybody who's listening to this knows Yeah. That, you know, I chose them because they're open source. They have a useful free tier and they're as good as anybody else. Yeah. Are you gonna self-host? You're certainly capable of doing that. It looks like you actually have to run a bit Warden server. You can't just have a bit Warden Fire. There is a third party server that is widely agreed to be much faster. I think it's written in Go. So you could use, you don't have to use it's open source. Somebody else has written a server that's better than Bit Warden's. Nice. And most of the people who self-host that I know use that software, I'll find it for you. But you know, I don't self host. I'm not, I'm not gonna bother. No, no. I mean, I mean, again, the reason we did this in the beginning was that we had really strong local client side encryption and we were just using the, the, the, the, the provider to hold onto our data for us.
(01:42:30):
Right. Right. Unfortunately, last pass has just demonstrated that we can no longer trust them to do that. It's, it's literally the worst thing that could happen to a pass. Well, except for not encrypting it. Right. But, but it's super well say it's good. It's as bad as you get. Yes. Well the, the, the reason we were all using the cloud is if your local encryption is solid, it doesn't matter. Right. If they lose control. Right. Unfortunately, they both lost control and their local encryption. Correct. Was not being kept was not being kept up to date. Yeah. Ugh. Okay. So I signed up for Bid Warden started the $10 plan, then I went to a menu item I had never used in my last Pass Vault export. And I exported a 77 K Byte CVS file. I opened my shiny New Bit Warden web interface and under tools at the top was a menu item import data from a dropdown menu.
(01:43:32):
There I selected the import source as being Last pass CSV provided the file name of the, of the file I'D exported from Last Pass and watched a perfect error free transfer of my entire legacy last pass data into Bid Warden, my password database, auto-filled credit cards and all my secure notes made the move without incident or complaint. I have done this as well several years ago, but I did it. The only thing I would say is immediately securely erase the C SV file cuz it's in plain text, right? No, no, no. Not the csv. No, it is an encrypted vault. It's still encrypted. Okay. But it, wait, no, no. It, it has to be un it has to be encrypted text. Yeah. Yeah. Yes, yes. In order to import it course treat that carefully. <Laugh> Yes. I I I I I was briefly confused with the XML that we grabbed from The's last passage.
(01:44:28):
No, but this have to unencrypted so it can be re-encrypt. Yeah. And in fact, I remember being very, I remember being very nervous about the fact that that file was on my system. Yes. I was like, yeah, delete it securely. The other thing when I did the import, I had some very long and weird notes in Last pass and a few of the very long note fields got munged on the import or maybe on the export. I'm not sure at what end, but you might check if you use Secure notes to make sure everything got in. I remember that I had some trouble with that. In fact, actually I think the import didn't work because Bit Warden said, well, I don't know, this is too long. I can't <laugh> I can't. And, and I was wary of that, but I had no complaint complains or, or issues at all.
(01:45:13):
Simon Zfa, who is a frequent contributor to the podcast, he said that that the Android client, I put him off a little bit. Do you? But you certainly are an Android. Oh, no, no, it's fine. Okay, look, I mean, I guess we should also say, and, and we talked about Tavis Ory saying this, that the JavaScript stuff like the plugins for the browsers, perhaps the, the mobile clients for all of these password managers, these are a little bit potentially problematic, especially if code got injected, malicious code got injected and so forth. Right. Well, again, there is no guarantee being made for any of this Right. Over on the client's side. Right. That isn't something we have any control over. If something evil gets in your machine, you know, it can be logging your keystrokes. That's a good point. If you're watching you, you type your master password, all bets are off.
(01:46:08):
Some might say Tavis did that. It's better to use the binary as opposed to the JavaScript plugin on the browser and last pass bit Warden Dash Lane and and one password all offer a standalone app. I think in some cases it's electron. So maybe that's not great <laugh>. The other thing I would say is if you are in the minority and you only use Apple products, you, apple has a very good, I think password manager that will do all the things a password manager will do. And it's all kept within the Apple ecosystem. It's, it's a little hard. You can use it on Windows and Android, but you have to have an Apple app to do that. Probably, probably should be added to the list of potential candidates for people who are mostly Apple focused. I was gonna say yes, if, if, if you were a Mac user, then that would make certainly sense to, to stay there.
(01:47:02):
And of course I'm not, I just, I'm an I I use them. It's nice, it has a very nice generator, it fills it in and it's, but I, I still, I need Bit Warden cuz I use Linux. You know, I use other stuff and and bit. I need a cross-platform one. And I, you know, as much as I love Bit Warden and they are a, a sponsor and it's what I use personally I think you'd be fine with Dash laneer one password as well. I see no reason not to, not to use those. Yes. As I, as I said at the beginning or when we were talking about this, I see lots of tweets from our listeners who are one password users very happy. Yeah. You know, e even Jeremy when he is not, you know, frothing, <laugh> thinks that one password is a good thing too.
(01:47:44):
Right. So we have one last thing to talk about, which is the remediation of any danger which may arise from any prior use of last pass. When I was deciding upon the title for today's podcast, I was tempted to title it, don't Panic with a Nod to Douglas Adams because, you know, I doubt that anyone should panic. There are some caveats though, as I noted earlier, you should definitely check your last pash iterations to assure that it had been bumped up to the 100,000 level. You know, and in my show notes here, I said, please shoot me a note if you discover that it's not a hundred thousand, a hundred thousand and a hundred and un and that happened immediately. We got a lot of 5,000 p people out there. So that's a concern. But you know, assuming that you have a hundred thousand plus iterations and that you're using a master password with good entropy, other than some incidental personal information disclosure of the sort that, you know, as, as was said, commercial entities that you work with on the internet probably already have about you, you know, and like all the advertising companies out there that are tracking us, your actual risk of having your own vault decrypted should be low.
(01:49:05):
If you were using a very high entropy password with 55 0 bits of entropy, a single G P U attempting to crack the last pass default, assuming that it is a hundred thousand plus iterations of an s h a 2 56 based pbk, D F two would require 200 years and an estimated cost of 1.5 million. Okay. Now 50 bits is a lot of entropy. Studies have shown that the average password only contains somewhere around 40 bits of entropy. Since that's 10 fewer bits. The strength is two to the power of 10 weaker. Two to the power of 10, of course is 10 24, so roughly a thousand. So a 40 bit password would be about 1000 times less strong. So that brings us down to a couple of months for A G P U to crack a single user's vault and a cost of about $1,500. And this of course reminds us why the strength and the length of our password is so crucial for avoiding brute force attacks.
(01:50:23):
Everybody remember password haystacks. It taught us the lesson of how easy it was to create long and highly brute force resistant passwords. The second factor mitigating our risk, if you'll, pardon my pun, is the presence of second factor authentication. Everyone who's listening to this podcast almost certainly has a time-based authenticator and has added the requirement for its use to their most important online accounts for iOS. I still prefer O T P off, which uses iCloud for its synchronization among my iOS clients. As I scroll through all of the accounts I have registered in O T P off, it's comforting to see that I have that additional layer of protection beyond what was contained in my last pass vault. But this leaves the theoretical risk. Now you know, that any crucial high value credentials that might have been saved in that vault, which are not protected by a second factor could be at risk since last pass was not encrypting our email addresses and website URLs.
(01:51:41):
There was definite leakage of who we are and where we go, you know, and what we do without any need to decrypt anything. This opens last, passes users to the potential for potent phishing attacks by leveraging what might be learned from an examination of the unencrypted data contained in their vault. So everyone needs to be on heightened alert, unfortunately, forever, because, you know, this data's never gonna go away for convincing looking online scams sent to your email addresses and referring to websites you use, which I assume we're all gonna be seeing once our last pass vaults have been de obfuscated by the little utility programs that hopefully our listeners are in the process of writing right now. The final takeaway is that if you are concerned that your last pass master password was not high quality, high entropy and may not have had a, a high iteration count at the time of its theft from last pass, the risk of brute forcing might be higher for you.
(01:52:54):
So it might be worthwhile for you to take the time to scan through your vault after importing it into your next password manager and manually changing the login passwords of any of your important accounts, which are not also protected by some form of strong second factor authentication. And finally, the last page of today's show notes contains a link appendix for anyone who's interested in reading the original source material that I found Ed shared above. I've got Jeremy Goss's rant link wa la Vladimir p four recent LastPass blog posts and also Steve Thomas's identity over at Twitter and at Mastodon as well as his website. So anyway it was a good run, but it was time to say goodbye and I sincerely hope that none of our listeners were caught by this breach. I, I know that some of our listeners did have 5,000 iterations.
(01:54:04):
We could hope that they had a really good brute force. And remember, you know, we're talking tens of millions of customers in this backup blob. The danger is much greater for people who are likely to be targeted than, you know, our aunts and uncles, right. Who we, we talked into using last pass and honestly, 10 years ago, I would even say if it was hard to get 'em to use last pass, don't feel obligated to move them off of it. Although you might. Yeah. Yeah. I mean it would be nice incidentally, Steve, are you gonna go through all your passwords and and change 'em because I'm gonna look at them. You took 'em all over with you and those are still in that blob. Correct. And presumably if somebody was, I'm sure you had a very long strong password and you used two factor, does two factor help in the case of brute force?
(01:54:55):
I guess it does right now. That's a really good question. It's the, the way last pass implements their, their, their so-called, you know, no password deal is that they locally encrypt the, the decrypted password, the decrypted master password, and then that gets sent to them when you then use their two-factor authentication for their password free mode that they came out with a few months ago. They verify that the, the, the, the, the second factor is correct, then they send you the encrypted password for you to decrypt locally in order to get access to your vault. So I don't, the way I read that, it doesn't get factored in to your master password used to encrypt your vault. So Wow. So the, the the, the second factor there is not a benefit. Wow. So better hope you had a good random, well it probably isn't random cause you had to memorize it, but a good long unroot forcible master password.
(01:56:16):
Yes. And given that these guys have had, potentially have had this for some time and will have it forever more ever and we know that cracking technology is only ever gonna get better. Oh boy, boy, it's not gonna get worse. This is, this is so bad. This is so bad. It probably would be prudent, honestly, to go through and change at least the password you care the most about, like your bank credit cards stores. Yeah. those are, and really, I mean, it's not that big a hassle, right? You, you, you log onto the site, you, you Yeah. You know, and, and that's easy. And then you go to the change my password and you put in the old one and you, you make up a new one. Wow. I, I do think it's, unfortunately, it's probably, I mean, who in order to rest easy, right? Right. The other thing you could try is set up your new password manager without important importing any passwords, <laugh>. And then when you go to a site, you know you've got a password, this forces you to say, I forgot and reset it. And you will gradually fix your passwords by starting fresh with a password manager. That sounds like fun, <laugh> <laugh>.
(01:57:32):
But it really, honestly, this is why this is so serious. That's kind of the best and only thing you can do. You have to, if you really wanna be safe hopefully your parents didn't listen to your advice. They didn't get last Pass <laugh>. They just got the little book at Kmart that said passwords and they wrote them all down one by one carefully. And it's got the rubber band holding it closed. Yeah. And they keep it in the left lower left drawer where no one will look. Cuz they'd probably be safer if they had, wow. I apologize. When we started doing ads for LastPass, they were a quality product. We were very proud to be associated with them. They saved us in the year 2020. I don't know if it would still be here if they hadn't bought studio naming rights.
(01:58:21):
I apologize to all of you who started using LastPass because of us. But we all got bit and there's the, there's the answer. There's the show you've been waiting for. I'm waiting for well, at, at, at every point. We were being clear that the quality of the master password is paramount. Yeah. Like, and that was the idea, right? You only have one that you need to like, be in charge of, be responsible for, make it a good one. Right. And, and, you know, password Haystacks teaches us the lesson that you can just put a bun, you know, like put 20 periods after it <laugh> and that makes it way stronger, way more impossible to brute force. And it's, you know, it's not a difficult thing to do. Well, in fact that is the advice somebody gave. If, if you are writing your passwords down and putting 'em in a little book is, that's not the password by itself.
(01:59:15):
Add a 10 digit number that you know well. Correct. Always. You don't write it down. And that will not only lengthen the password appropriately, it will also make it useless if they find the, the bad guys find the book. Wow. thank you very, very, very much Steve for doing this. I, I, I think I tooted unmasted on Dang, the one week. We don't have a security now <laugh>. And we have a story that we really wanna know what Steve thinks, but now, you know, thank you Steve. Do get the show notes for all those links, read more. Grc.Com is his website. You'll also find two unique versions of the show there. He's got a 16 Kilobit audio for people who really don't ha well, you know, have limited bandwidth and transcripts written by one of the people who has limited bandwidth.
(02:00:03):
That's why the 16 Kilobit show show audio exists. So Elaine Ferris could download it at her limited capability Ranch. She's a, she is a what are, what are they? A Collier as well as a a court reporter? Yeah, she does horseshoeing. So she is transcribing this. There will be a, I believe it's Collier. I hope you're, I'm right, Elaine, if I'm not, can you replace it with the right word? Thank you. Those transcripts are available@grc.com while you're there. Pickup spin, right? The world's best mass storage, maintenance and recovery utility. Getting better with 6.1, which will be out soon. And if you buy 6.0 now, you'll get 6.1 for free. When it comes out, you also can participate in the beta period. I'm sure there will be something like that. Yep. Yep. After the after the show, you can go there and leave comments for Steve at grc.com/feedback.
(02:00:58):
He's still on Twitter. He's gonna be the Please turn out the lights when you leave. Sg grc actually, don't worry because I think the power company will turn 'em off <laugh> sooner than later. Sg GRC on Twitter, his dms are open. You can leave comments there as well. We have the show at our website twit.tv/sn. That's where you can download shows. You can also go to the YouTube channels. There's a dedicated channel. You can find that. And all our dedicated channels at twit youtube.com/twit youtube.com/twit. Subscribing is probably the best way to get it. That way you get it automatically. If you are a Club Twit member, you can subscribe. We give you a very special feed just for you to the ad-free subscription so you don't get any ads in the show or any of our shows. Seven bucks a month gets you, that gets you the Discord, which is wonderful.
(02:01:49):
It gets you access to the TWIT plus feed with lots of shows we don't put out in public, including hands on Mac, hands on Windows, the Untitled Linux Show. Lisa and I in two weeks are gonna do a inside twit for club members, all of that available at twit tv slash club twit. And thank you in advance. You Club twit members help us keep the lights on, unlike Twitter. Yeah, we pay our rent. That's, I'm just saying <laugh>. And I presume you stock the bathrooms with toilet paper. Well, yes. Well, we were thinking about making employees bring their own, but no, no, we actually, and we have a janitorial service. It's unbelievable. It's very nice. Unbelievable nice. But in order to do all that full service organization, you need to join Club Twit. Otherwise, it's all bets are off. Thank you Steve. Great job. Really, really appreciate your frank, honest appraisal of this situation. That's what we count on. Thank you, Steve. Have a great week. See you next.
Steve Gibson (02:02:44):
Bye.
Mikah Sargent (02:02:48):
Is that an iPhone in your hand? Wait a second. Is that an Apple watch on your wrist? And do I, do I see an iPad sitting there on the table? Oh my goodness. You are the perfect person to be watching iOS today. The show where Rosemary Orchard and I, Micah Sergeant talk all things iOS, tvOS watch os, home Pod os it's all the OSS that Apple has on offer and we show you how to make the most of those gadgets. Just head to twit.tv/ios to check it out.
... (02:03:23):
Security Now.