Security Now Episode 894 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte / Steve Gibson (00:00:00):
It's time for security. Now, Steve Gibson is here. Google has created the perfect operating system. Is it possible to be absolutely secure? We'll talk about Apple. Zero days, windows, zero days, cryptocurrency craziness. And then who's responsible for that data breach? Is it you or the technology you're using? All that. Coming up next on Security Now, podcasts you love from people you trust.
... (00:00:30):
This is Tweet.
Leo Laporte / Steve Gibson (00:00:36):
This is Security now with Steve Gibson. Episode 894, Recorded Tuesday, October 25th, 2022. Data breach responsibility. Security now is brought to you by drta. Security professionals are undergoing the tedious and arduous task of manually collecting evidence with dra. Say goodbye to the days of manual evidence collection and hello to automation. All done at drta speed. Visit drta.com/twi to get a demo and 10% off implementation. And by SecureWorks. Are you ready for inevitable cyber threats? SecureWorks to detect evolving adversaries and defends against them with a combination of security, analytics and threat intelligence directly from their own counter threat unit. Visit secureworks.com/twi to get a free trial of TAUs extended detection and response. Also known as XD r and by Barracuda. Barracuda has identified 13 types of email threats and how cyber criminals use them every day. Fishing, conversation hacking, ransomware plus 10 more tricks cyber criminals use to steal money from your company or personal information from your employees and customers.
(00:01:57):
Get your free e-book at barracuda.com/security. Now it's time for security. Now. Yay. All week long. We wait for this show where Steve Gibson is gonna explain it all to us. Hey, Steve <laugh>. Hey Leo. Great to be with you again for the final episode of OC What of September Of October. Yes. October on October month. It is October. It's spooky season. Do you wear a Halloween costume? You know, <laugh>, I think, and I don't have any memory of this, I think I must have been really scared <laugh> by You don't like it? Like when I don't like it. <laugh>. When I was like three or four or something. I just must have just had that crap scared out of me. Cause I was, I have this ketchup hat and I was gonna volunteer. I also have a mustard hat. We could you, we could, you could wear that and we'd, we'd be the, the condiment.
(00:02:56):
Condiment twins. <laugh>. That's all right. Really my goal. Forget that. <laugh>. Anyway, no, I've never been a fan of Halloween. So, uh, but I am a, a fan of thinking about our industry, which, uh, it brought the title Data Breach Responsibility, uh, to this podcast. I encountered and will get to it by the end. Uh, the news of a bracing, uh, legislation being proposed this week in Australia to really up the ante on the penalties for data breaches following a string, a very embarrassing high profile problems in Australia in the past month. And I, it was a great opportunity to, to sort of step back a little bit and think about, you know, whose responsibility are data breaches. Um, and, and what's neat is that the last several years with this podcast has given us a perfect foundation for having this discussion. So anyway, this is security now, episode 894 for the 25th of, Yes, it is October.
(00:04:09):
Uh, uh, we're gonna talk before that about, uh, some news of a new Firefox browser release. Uh, Google's welcome an interesting announcement of a secure by design, new open source operating system project, which will probably never amount to anything, but it's exactly the kind of thing we need to be like taking seriously. So I'm glad they're doing it. Um, we're also gonna look at the latest cryptocurrency craziness, uh, and that a new Windows Day, which manages to bypass, downloaded executable file security checks. Unfortunately, actually what's unfortunate is that Microsoft's not so, not so sure it's real cuz they couldn't reproduce it. Oh my God. And speaking of zero days, Apple just patched their iPhone and iPad OSS against the ninth zero day of the year, which we'll touch on. We then take a look at the forces driving the evolutionary demise of the, what was previously rampant banking malware.
(00:05:17):
And at today's critical today as in it was happened this morning, Critical VMware update. Then after sharing and addressing some interesting listener feedback, as I said, we're gonna wrap up by taking a look at this, well at the downstream effects of really upping the ante on data breach penalties and, uh, why that may not be the best thing to do. And we do have a great picture of the week, which needs some explanation. Yeah, so, Cause I, I'm not, I'm not laughing. I'm, I'm just looking, you know. Yeah. Uh, cool. A great show ahead as always. I think so. Brought to you, uh, this week as it often is by those good folks. Atta Drta is your organization. I got a question for you. Is your organization finding it difficult to achieve continuance compliance? That's the kind of the standard now, isn't it? Uh, and it's really a problem if you're not a static company, but growing and scaling.
(00:06:19):
Are you doing it manually? Is that slowing you down as G Two's highest rated cloud compliance software? Drta streamlines your SOC two, your ISO 27 0 0 1, your P C I dss gdpr, hipaa, no matter what your compliance framework and provides 24 hour continuous control monitoring with a suite of 75 plus integrations. D Strata easily integrates with your tech stack through applications like AWS and Azure and GitHub, Okta Cloud Flare. Countless security professionals from companies, including Lemonade and Notion and Bamboo HR, have shared how crucial it has been to have drta as a trusted partner in the compliance process. Their deep native integrations provide instant visibility into a security program and continuous monitoring to ensure compliance is always met. Dorada allows companies to see all their controls, to easily map them to compliance frameworks. To gain immediate insight into framework overlap. Companies could start building a solid security posture from day one with drta, achieve and maintain compliance as your business scales and expand your security assurance efforts using the draha platform.
(00:07:32):
DRA DA's automated dynamic policy templates, support companies new to compliance and help alleviate hours of manual labor. Their integrated security awareness training program and automated reminders ensure smooth employee onboarding and they are the only player in the industry to build on a private database architecture from day one. That means your data can never be accessed by anyone outside your organization. All customers receive a team of compliance experts. Strata really goes the extra mile to support you. You'll have a designated customer success manager. In fact, they even have a team of former auditors. The kind of people who are gonna be looking at this data, These, these auditors who have conducted 500 plus audits, They're available for support and counsel, not counseling, maybe a little counseling, but more support and counsel. Your success is draw's success. And they know that one of the reasons they have a co a consistent meeting cadence.
(00:08:32):
So you're never in the dark. They keep you on track. Ensure there are no surprises, no barriers, plus your pre-audit calls ensure you're set up for success. When your audits begin, you will never feel alone. You'll always know Jada's got your back. Draha, personally backed by S V C I a syndicate of ciso, angel investors from some of the world's most influential companies, cuz they knew this was something that they needed, They knew the world needed. And you do, you need this. So say goodbye to ma. Manual evidence collection for crying out loud. This is 21st century. Say hello to automated compliance by visiting drta.com/twi DRA t.com/drta. Bringing automation to compliance at drta speed. Don't forget the address, please use it so they know you saw it here. drta.com/twi. If you request a demo, you can get 10% off right now. drta.com/twi. All right, I'm ready for you to explain this post in the ground <laugh>.
(00:09:35):
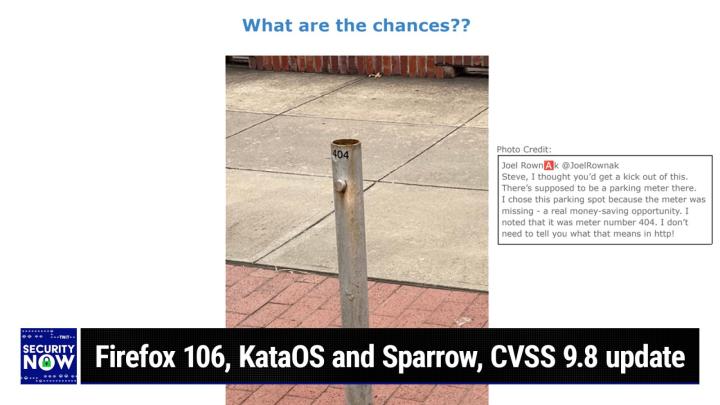
So, okay, for those who are not seeing this, we have, um, in the background is a sidewalk and then sort of a, a bricked region, uh, which abuts a street curb, a streetside curb. This was supposed to be a parking meter. Ah, and the meter is missing. Yeah. And what's so fun about this is, and this is, you know, at the height of Geekdom, is that the, the, the, the, the lower end of this parking meter's mounting poles, <laugh>, which the meter would be sitting on, uh, now I get it, is number four. Four four meter. Not profound. <laugh> meter, not profound. So Joel Roak tweeted me, That is so great. He, Joel Roak tweeted this picture. He said, Steve, I thought you'd get a kick out of this. There's supposed to be a parking meter there. I chose this parking spot because the meter was missing a real money saving opportunity.
(00:10:42):
<laugh>. Yes, I know. I noted that the meter number was 4 0 4. I don't need to tell you what that means in http. So anyway, Joel, thank you for, uh, a great, you know, listener feed feedback picture of the week. That's, that's a goodie <laugh>, that's a unique one. You're probably the first person to get this one. That's good. I think so. I like it. And, you know, probably the last <laugh>, who's, you gotta be pretty geeky. Who's gotta I star? I stared at it. I was trying to figure out what I don't, I don't get it. And then yeah, why they explained it, Of course. Yeah, that's good. Okay, so Firefox 1 0 6 is out. Last Tuesday, week ago, Firefox 1 0 6 became publicly available with a collection of new features and security improvements feature-wise. And th there are a couple of cool things here. It's now possible to edit PDFs, including writing, text, drawing, and adding signatures and setting Firefox as the default browser.
(00:11:39):
Also makes it the default PDF application for Windows. So, although that was interesting, you know, to be able to actually to, you know, modify PDFs in a browser, I guess that's good if you, you know, need to do that. Uh, also private in Firefox, private Windows can now be pinned to the Windows task bar in Windows, uh, 10 and 11 for simpler access. And they have been redesigned to increase their feeling of privacy. Now, that's what Mozilla said. I looked at it and okay at, you know, I'm not sure what the change was. They, they're very dark and very sparse looking. So I guess that's more private feeling. Uh, also swipe to navigate with two fingers on a touch pad. Uh, you know, you could swipe right or left to perform a history back or forward motion. Uh, I actually like that on my iPad.
(00:12:34):
I did that once in front of Lori. She said, Wait, what did you just do? How'd you do that? I go, Oh, well, you know, that's a, that's a geek thing. Anyway, uh, it now works for Linux users on Wayland and Wayland for those unfamiliar with the term, we'll be the successor to the original venerable, uh, X Windows system, which is, you know, how the, the, the, the standard gooey, uh, in, in Unix land, which has survived today, uh, it's being succeeded by something called Wayland. Um, also on, for, for, for this version of Firefox on Mac OS 10.15 and higher text recognition has been added to images, which allows you to extract text from selected images, you know, like a meme or a screenshot or whatever. Uh, and the extracted text is copied to the clipboard in order to share store or search without needing to manually retype what you're seeing in the picture, which is kind of a cool thing.
(00:13:38):
Uh, Firefox's web RTC capabilities also received a major upgrade with their move or Firefox's move from their use of live web. RTC went from version 86 to 1 0 3, which brought a bunch of improvements. Uh, better screen sharing for Windows and Linux Wayland users, lower CPU usage and increased frame rates during web rtc screen capture on the Mac, uh, RTP performance and reliability improvements, richer statistics and cross browser and service compatibility improvement. So, you know, just a bunch of nice upgrades to the browser, which, uh, is all of our favorites or many of our favorites. Uh, you know, so it continues to move forward. There were also a bunch of security, uh, improvements. Nothing breathtaking. I looked through them, I was like, Okay, I'll just say that there were a bunch of them <laugh> instead of enumerating them. Okay. So driven by events and evidence. I've, and I'll be doing this at the end of the podcast, also often bemoaned the increasingly sad state of affairs, which describes the insecurity of today's operating systems and software.
(00:15:00):
I've said that someday, somehow this has to change. So it was with some interest that I stumbled upon an announcement of just exactly this sort of change last week, which I wanted to share. I'm not suggesting, as I said at the top for a second, that this particular effort by three talented software engineers at Google will ever amount to anything more than a learning experience for them and hopefully for others. But even if it never moves beyond GitHub where it is, this is the sort of shape that an eventual effort will take. Um, and I'm quite clear about one thing. No closed commercial OS is ever gonna get us there. You know, all the popular operating systems we're, we're familiar with Windows, Linux, Unix, Mac Os were designed with security and mind, but in a fundamentally ad hoc fashion. That's just the way operating systems have been designed, sort of, you know, generically until now, they were all designed to have security features, but none of them were provably secure by design operating systems.
(00:16:31):
And, you know, they're, they're all old, right? I mean, that's just the way things work. Security wasn't the issue that it has beginning to finally become today. So it's instructive, I think, to listen to the language these three developers use to describe their effort. It, it's a different way of thinking and it's the language of the future. So they said, we, they said, as we find ourselves increasingly surrounded by smart devices that collect and process information from their environment, it's more important now than ever that we have a simple solution to build verifiably secure systems for embedded hardware. If the devices around us cannot be mathematically proven to keep data secure, then the personally identifiable data they collect, such as images of people and recordings of their voices, could be accessible to malicious software. Unfortunately, system security is often treated as a software feature that can be added to existing systems or solved with an extra piece of hardware.
(00:17:54):
This generally is not good enough. Our team in Google Research has set out to solve this problem by building a provably secure platform that's optimized for embedded devices that run machine learning applications. This is an ongoing project with plenty left to do, but we're excited to share some early details and invite others to collaborate on the platform so that we can all build intelligent ambient. I love that the use of this word, this term ambient, intelligent ambient systems that have security built in by default. And actually they met, designed in by default. They, they've, they, they finished saying to begin collaborating with others. We've opened sourced several components of our secure operating system called kta, K A T A OS on GitHub, as well as partnered with Ant Micro on their Reno simulator and related frameworks as the foundation for this new operating system. We chose the S E L four.
(00:19:10):
They chose s e L four as the microkernel because it puts security front and center. It is mathematically proven secure with guaranteed confidentiality, integrity and availability. Okay, so I'll just note that SEL four is an open source verifiably secure microkernel with a heritage going back to the mid nineties. So this is exactly the right sort of foundation for a more functional OS to then be built upon. They also use an SEL four framework known as campas, I guess you'd pronounce it C A M K E S, to provide static, what they said is statically defined and analyzable system components C. The C A M K E S stands for component architecture for microkernel based embedded systems. It's a software development and runtime framework for quickly and reliably building microkernel based what they said it was a MULTIER operating systems. It follows a component based software engineering approach to software design resulting in a system that is modeled as a set of interacting software components.
(00:20:40):
They said these software components have explicit interaction interfaces and a system design that explicitly details the connections between the components. So all of that kind of feeling that, you know, this is the language of where we have to be headed, it's utterly different from the essentially ad hoc design of all of today's operating systems that we're familiar with, where random coders grafted on and are still grafting on today new pieces of stuff. And, you know, after doing so away it went ship it. And in the case of Windows, we'll find the bugs later. Uh, anyway, continuing with the Google engineer's description of their work and offering, they said KTA OS provides a variably secure platform that protects the user's privacy because it is logically impossible for applications to breach the kernels hardware security protections and the system components are verifiably secure. KTA OS is also implemented almost entirely in rust, which provides a strong starting point for software security such it eliminates entire classes of bugs such as off by one errors and buffer overflows.
(00:22:16):
The current GitHub release includes most of the kta OS core pieces, including the frameworks we use for rust, such as the SEL four cyst crate, whatever that is, which provides SEL four sys call APIs. Okay, now I know what it is. An alternate root server written in rust, they said needed for dynamic system-wide memory management and the kernel modifications to SEL four that can reclaim the memory used by the root server. And we've collaborated with Ant Micro to enable G D B debugging and simulation for our target hardware with Reno. Internally, kta OS also is able to dynamically load and run third party applications built outside of that cam, that CAM'S framework. At the moment they said the code on GitHub does not include the required components to run these applications, but we hope to publish these features in the near future to, to prove out a secure ambient system in its entirety.
(00:23:31):
We're also building a reference implementation for Cato, for Kta os called Sparrow. Okay. So Sparrow will be the reference implementation for an instance of K Os they said, which combines Kta OS with a secured hardware platform. So in addition to the logically secure operating system, Kernel Sparrow includes a logically secure root of trust built with Open Titan on a risk five architecture. However, for our initial release, we're targeting a more standard 64 bit arm platform running in simulation with Qmu. And finally they set our goal is to open source all of Sparrow, including all hardware and software designs. For now, we're just getting started with an early release of Kta OS on GitHub. So this is just the beginning and we hope you'll join us in building a future where intelligent ambient machine learning systems are always trustworthy. So I have a link in the show notes to the project, uh, actually to their announcement on, uh, open source.google blog.com.
(00:24:53):
Um, but I wanted to share this because again, this is the sort of effort we are needing to begin to gain experience with the shape of an entirely new class of software, which won't be fragile by design. We finally, I believe, have sufficiently inexpensive processing power and memory so that design compromises won't be driven and arguably needed to make in order to make this sort of next generation system viable. Right now we've spoken before about how Windows original designers, among many other wise decisions, which have since been breached, placed Windows gdi, it's graphical device interface module outside of the windows kernel up in user land where its faults would not give attackers access to the kernel. But in their quest, in, in their quest for more performance, Microsoft chose to discard security concerns and move GDI into the kernel. As we know, the result has been an apparently endless stream because they're still coming of serious vulnerabilities which were created because this extremely complex and error prone code library GDI was given full kernel privileges for the sake of performance.
(00:26:32):
So obvious and clear trade off. Now, you know, it's true that the ivory tower design of an operating system can be compromised. We've seen it, but we can hope that now given the power, the performance, the memory that we've got, that a system which has been built for the express purpose of exploring and possibly of creating truly secure code will now never need to make such a mistake. So again, but do you, do you think that though something designed from scratch like this, I mean obviously it's better to start to be secure by design. The only way to start, but what, But if you have something that, uh, I mean, okay, I'm not gonna include windows in this, but if you <laugh> existing operating system that has had years to be patched and fixed and updated and then can be hardened, I almost think I'd prefer, I'll give you an example.
(00:27:31):
There's a, a security, a secure Linux called Cubes. You're probably familiar with that. Yeah, of course. Right? And it, it, it's, it's everything sandboxed, It is the Linux kernel, but it's designed to be fully secure. I feel like I almost would trust that better because people have been banging on this open source code for two decades, three decades now. So I completely agree with you if you wanted something usable Yeah. <laugh>, well, that's for sure. Yeah, that's the problem is that, you know, this is all ivory tower pie in the sky. You know, here's how we make something that, you know, is absolutely unbreakable and then someone says, okay, uh, what kind of word processor does it have? Right? But, but even, and by the way, cubes is not very usable either, but <laugh>, but then by the way, uh, no one's perfect. Even these, you know, academics, they can, they don't have, you can't do anything with it.
(00:28:26):
Yeah. But they may have accidentally left in something. Now, that's the point I wanna make it is that when they say provably securely, they mean that, that it is testily, mathematically demonst. This is a different way of programming. It's like, it's like how I'm upset when someone says all software has errors. No, there's no reason that, So, I mean, software can be perfect. It if, if, if the hardware is correct. If the hardware doesn't have bugs, then software is just math driving the hardware. It can be perfect. Is roham a software error or a hardware error? That's hardware a hardware error, right? Absolutely. So these wouldn't necessarily be immune from Roham to RO Hammerer. Correct. Correct. So, so it it needs a hardware platform which is secure and that, and then, you know, you raise a good point and you know, and, and, and so is Specter a meltdown Specter and Meltdown.
(00:29:26):
Meltdown were edge cases where there was a way to, to bypass, um, some optimizations by, you know, by, by, by leveraging this. But you know, there's a whole class of of software problems. All the buffer overflows, all the off by ones. All of the, the use after free problems, you know, the, this whole big batch of things can be fixed. And, and so again, I'm not suggesting for a second that this will be the solution or that in any way this is practical. But, but we are not gonna get to where we need to be if we keep doing things the way we have been because we have been doing them and we've even been talking about security, yet we're not, you know, things are not getting any better. And I agree with you as, as everyone knows, I just wish Microsoft would stop changing windows, leave it alone and fix it.
(00:30:24):
Because, you know, the more they add things, you know, everything they do is gonna, it brings new bugs into the system. Yeah. It's hard to fix a moving target. Absolutely. Oh, you, you can't, It's impossible. You know, all the evidence suggests it. Anyway, I just, I I wanted to sort of introduce this because, because again, this has been kind of quietly percolating in the background, but the, but the problem has always been that when you start to do something with it, the, the architecture becomes a stumbling block. Just like it did with Windows. Windows had a client server architecture where, where, you know, and, and that's what this is. When, when, when they talk about a root server, they're talking about the, the Microkernel is a server with clean transactions to clients wh which are running with no privileges. And there's, there's nothing that the client can do to that can make the microkernel make a mistake as long as the Microkernel is written correctly.
(00:31:28):
And it is, there are ways to mathematically demonstrate there are no bugs. I mean, none, there is not a bug. And again, because it is math, it is entirely possible for software not to have any flaws. And so the only way we're gonna get where we want, where we where we could be is if we fix our hardware and we fix our software. And this is what the fixed software looks like. It, it's better, it's better to have software you don't ever change and you only fix bugs. I completely agree with you. And you could actually use that for something. You can't use this stuff for anything cuz it's brand new and it's not and it's not emulating, you know, any existing system. It probably doesn't have any IO either. Cuz IO is very difficult to prove. Oh, Leo, you don't want I correct. No, you can't, you can't trust I trust any Yeah, you can't, Side effects are the opposite.
(00:32:30):
Who knows what someone's gonna send it <laugh>. Yeah, right. No, you just have to put it in a box and go, Ooh, isn't that lovely? So I would submit that's a toy. Uh, you know, know, I mean, but that's where we're gonna start. Yeah, of course. It's a to, it is a toy does when software is provably correct. It would have to be functional, right? You would have to, you would, you would have to be able to know that there is no side effects. That what goes in comes out every time the same thing. That's what it means. That's what it means. I mean, again, that's where IO gets you in trouble. This is the notion that I, that I'm, that I've we're discussing this to convey is that it is not the case. That it is impossible to produce a perfect operating system. It is possible to produce a perfect operating system.
(00:33:17):
Now, at the moment, it's not usable, but it is perfect. I mean, it is, you, you can mathematically prove it's perfection. So there are, there are mechanisms in place now in the ivory tower for doing that. And Google is saying, Okay, uh, let's take that and see what can be done. So again, we're not gonna get there unless we do this. And yes, I know this sounds a little bit like squirrel, where seven years ago I said, Hey <laugh>, I know how to solve this problem. The difference is you're not gonna do this, right? This is not something you're planning on. Okay. No, no, no. I You got other fish fry Billy me. I am deep in the IO land, Leo. I'm like, Yeah, I am. Seriously. Yeah, you have to, You are io your whole thing is io. That's right. That's right. Okay. So, okay, get a load.
(00:34:12):
You're gonna love this one Leo, this week in cryptocurrency craziness. Cause the story revolves around an organization known as Mango Markets. And in researching this, I learned that.markets is now a top level domain. So mango markets is mango.markets, uh, period. A and let me tell you, this is a crazy place. It's self-description. It is quote, decentralized cross margin trading up to 20 x leverage with lightning speed and near zero fees, unquote. Okay? I don't know what any of that means, but I do know that's not good. Uh, the top of its homepage brags long and short, everything lightning fast near zero fees permissionless. Now, I strongly suspect that they didn't mean to be quite as permissionless as things turned out to be because a serial defi, you know, dis uh, distributed, uh, uh, finance, uh, de decentralized finance. Finance, Yeah. Defi abusing hacker by the name of Abra Abraham Eisenberg managed to take 14 million in cryptocurrency.
(00:35:45):
What a surprise. Which he, which he had retain No, no, that's the beginning. Oh. Which he had retained from a previous Defi hack and compound it into 114 million from mango markets, which you might be inclined to say would now be Mango Markets. Uh, 1400 million. 114. 114. 14, Okay. Million mango markets. Oh, yeah. Yeah, man. But wait, this is not, we're not done with this. This is gets weirder. Mango markets initial tweets immediately following the incident were, and this is at Mango Markets, they said, we are currently investigating an incident where a hacker was able to drain funds from Mango via an Oracle price manipulation. We are taking steps to have third parties freeze funds in flight. We will be disabling deposits on the front end as a precaution, and we'll keep you updated as the situation evolves. This is by do way exactly why you wanna put your money in a bank.
(00:36:56):
Exactly. No pricing if had Oracles in a bank <laugh>, uh, exactly. If you have any information, please contact Block works@protonmail.com to discuss a bounty for the return of funds. In other words, they're saying, whoever you are, Ouch. Uh, would you, how would you like a bounty and give us back our money? Cause what he did, he says, was completely legal Yes. And allowed by the, uh, algorithm. Yes. A short summary of what then transpired, raised so many questions in my mind that I dug a bit deeper here. Here's what the short summary I first encountered, red quote, Mango Markets exploiter comes forward in a series of tweets over the weekend. An individual named Abra Ham Eisenberg took credit for the attack on mango markets, following which he walked away with $114 million worth of cryptocurrency. Eisenberg came clean after he was publicly identified as the attacker last week. And after the Mango Markets community voted to allow him to keep 47 million of the exploited funds if he returned 67 million back to the platform. So it, and all the other projects that depended on it could avoid insolvency, Leo.
(00:38:44):
Wow. What has gone wrong with the world? Abraham was doxed and his identity became public knowledge. So he tweeted the following, Get a load of this. This is from at avi underscore Eisen, E I s E N. He said, I was involved with a team that operated a highly profitable trading strategy. I say so. Oh my God. I believe all of our actions were legal open market actions. Yeah. Using the, using the protocol as design. It's kind of like short selling, right? Yes, exactly. Yes. At, at, yes. He said, even if the development team did not fully anticipate all the consequences of setting parameters the way they are, unfortunately the exchange this took place on mango markets became insolvent as a result with the insurance fund. Yeah. Whoops. <laugh> with the insurance fund being insufficient to cover all liquidations, this led to other users being unable to access their funds to remedy the situation.
(00:40:03):
I helped negotiate a settlement agreement. Wow. With the insurance fund, you felt bad <laugh> with the insurance fund, with the goal of making all users whole as soon as possible, as well as recapitalizing the exchange. This is similar to how AutoD leveraging works on exchanges such as Binance and BitMax clawing back some profits from profitable traders in order to ensure, just get me out of this. What <laugh>, Thank God, what, Thank God you made too much money. We, we need some of that back. Yeah. We're clawing it back to ensure all users' funds are protected. Wow. As a result of this agreement, he finally tweeted, once the mango team finishes processing, all users will be able to access their deposits in full with no loss of funds. Unbelievable. And he keeps $47 million with everyone's blessings. Okay. This, this wasn't a security breach or a hack in the sense of finding and exploiting a flaw in some code.
(00:41:17):
This guy re I have to say, I've read his blogs, really knows his way around crypto driven, decentralized finance mango's first tweet mentions an Oracle price manipulation. So we have some sort of half cocked defi, you know, decentralized finance system that was prone to manipulation. And at this point, I've, I've been, you know, uh, what, this is the point I've been making here recently. Nothing about this entire wacky defi, N F T, whatever the hell it is. World seems mature. That first note I encountered mentioned that this negotiated agreement was made by a vote of the stakeholders. I found, Leo, that voting page, I have the link in the show notes. It's that dao.mango.markets, uh, page A and the so-called discussion is somewhat humorous. Many of the lesser stakeholders cannot imagine sanctioning this manipulation of the system if you scroll down. So, so, so that's the agreement there about what the guy's gonna be returning.
(00:42:33):
All of those amounts of different cryptocurrencies are being put back. So, uh, it, and what was interesting is that the, the, there's like people giving thumbs up and thumbs down, which are their votes on this. And the, the voting strength is not per member, but it's by the size of one's wallet. So not surprisingly, those with the most money to lose were in favor of anything that would make them whole again, as opposed to those who didn't have that much in, in the game. And were just furious at the idea that anyone was talking about, you know, I mean, they were thinking this guy is a criminal, but he wasn't. All he did was play by their rules and, you know, took him to the cleaners door to, to the tune of $114 million. So anyway, this Avrum guy has a sub stack where he has talked about how all this works and explain some of the schemes he's come up with for leveraging fluctuations in the defi world instead of defi.
(00:43:45):
It's deepy value is his stub sub stack. D e e p f i v A l u e dot sub stack.com. Uh, he currently has I think, four long blog postings, uh, in July of last year. His, his blog was deep dives into Cryptonomics. August 7th of last year was anatomy of a Yield farm. And then in January, uh, this year, how our team makes millions in crypto risk free. So I think the term Leo is jumped to the shark for what has happened, uh, in crypto land. Uh, you know, and I'm not not spending any time understanding this craziness because I think, well, the thing is, I mean, it's pretty clear they're making up the rules as they go along and there are flaws in it, and somebody takes advantage of it and oops, you have no recourse. Yep. I love it that there were, what is it, 400 million votes in favor of a refund <laugh>?
(00:44:49):
Quite a few. Quite a few. Um, that's why really, if you wanna put your risk money somewhere safe, uh, put it in a bank. Put it in a bank, they got rules, they're regulated, and it's gotta be that people think that they're gonna somehow make a lot of money. Well, that's greed. I mean, this is what the real basis of all of this is just greed. It's just greed. And, uh, you know, that's what a conman says. I can't rip you off unless you are greedy. Yep. You can't rip off an honest person. Yep. Okay, let's take a break, Leo. Right? Uh, talk about a non-G greedy sponsor. <laugh>, our sponsors are never greedy. They're, they wanna give you things. They're wonderful. <laugh>, thank you for the opening <laugh>. Our show, our show today. Let me see, wait a minute here. I gotta push all the buttons, get everything set up for this fine sponsorship opportunity brought to you by Secure Works.
(00:45:46):
Oh, you know, Secure Works. Uh, if you, if you are in business and you don't know SecureWorks, may I even make an introduction? SecureWorks is a leader. I'd say the leader in cyber security building solutions for security experts by security experts. SecureWorks offers a superior threat detection and rapid incident response all while making sure customers are never locked into a single vendor. So, uh, October, we're, we're winding it up here, but it's not just the spooky season, it's the scary season, the cyber Security awareness month, which means now is the time to raise awareness about digital security. I think, Steve, you do a great job of that and empower everyone to protect their data from cyber crime. And Secure SecureWorks has the perfect solution they call itts X D R Extended Detection and response last year, uh, in 2021, ransomware totaled 20 billion in damages, attacks occurred 11 in every 11 seconds.
(00:46:48):
It's estimated that 10 years later, the cost will $265 billion a year and strike every two seconds. This year's cyber crime will cost the world $7 trillion in three years. That figure will go to $10.5 trillion and you don't want to be the next victim. That's why you need SecureWorks. TAUs D r Tais provides superior detection, identifying more than get this 470 billion security events a day, prioritizing the true positive alerts, eliminating alert noise, and allowing organizations to focus on the real threat. In addition, Tais offers unmatched response with automated response actions automated. So they can happen like that, eliminate threats, but for the damage is ever done. You gotta be fast for that. With SecureWorks Tais managed xr, you can easily leverage SecureWorks renowned experts to investigate and response to threats on your behalf. So you can cut dwell times, decrease operational burden, and reduce cost. And because you're getting 24 7 by 365 day a year coverage, it doesn't matter if you experience a Christmas Day security event or half your team is suddenly out sick, You can trust SecureWorks is there behind you.
(00:48:12):
Many companies are facing a shortage of security talent. It's kind of a given these days. SecureWorks acts as an extension of your security team on day one, alleviating cyber security talent gaps and allowing you to customize the approach and coverage level you need. Now this is really important. What happens if you already found an intruder in your system? There is no need to worry. I want you to write down this number 1-800-BREACHED one, 800 breached. Even if you're not a Secure Works customer yet, that number will connect you with SecureWorks Emergency Incident Response Team. These people can leap into action any time of the day or night, any day of the year, and provide you with immediate, immediate assistance, both responding to and remediating a possible cyber incident or a data breach. You'd need that number 1-800-BREACHED. And of course, its Secure Works if you go there right now, secureworks.com/tweet.
(00:49:11):
You can learn more about the way today's threat environment is evolving, about the risks it can present to your organization. They've got case studies there, you can get reports from their counter threat unit. They are really good and a lot more. Visit secureworks.com/tweet, Get a free trial, TAs xd r that's dot com slash twi SecureWorks defending every corner of cyberspace. There's nothing like it. secureworks.com/twi. We thank 'em so much for supporting, uh, security Now and you support us of course, when you go to that address secureworks.com/twit. Okay, Steve, back to you. So yesterday, bleeping computer disclosed the news of a new zero day flaw being exploited in the wild on Windows machines. The flaw enables executable files downloaded over the internet by attackers to run without producing any popup warnings. Uh, and in, in this case, these were the one, the, the flaw that was found.
(00:50:25):
JavaScript files were being downloaded and used to install the Magna Bur, M A G N I b e R, Magna Bur ransomware. And it turns out that the flaw allows any executable, as I said, to bypass windows detection warnings. Now, we've talked about the mark of the web, um, it's implemented, remember, remember the mark of the web for files that that come into your computer over the internet it's implemented using a very cool and underused feature of Microsoft's Ntfs file system, which is known as alternate data streams. Alternate data streams have been a feature of Ntss f Ntfs <laugh> from the start, though they've never received much attention. A file's alternate data stream is it's name followed by a colon and then the name of the string of, of, of the stream. So it can be, it literally accessed by, literally by creating a file with the a file, the file name that already exists.
(00:51:38):
Then a colon, and then the name of a str of, of, of a stream. It's like a sort of a branch off of the root file. Um, it's just that simple. It's another dimension of file metadata aside from, you know, data created last modified, you know, uh, read only compressible and so forth. Uh, and in fact the Windows filed directory, uh, listing command D you know, just standard dirt can be given the slash r command line switch, which will cause it to add a, to its listing any alternate data streams that may exist. So for example, if you were to go into your Windows download folder, uh, and then open a command line and do d slash r since almost by default the files coming in have been downloaded over the internet, you'll see a whole bunch of stuff you've never seen before. If you add the slash r, you'll see the alternate data streams that have tagged all of those, and those alternate data streams are named zone dot identifier.
(00:52:51):
So when a file has the alternate data stream zone dot identifier, this identifies a file, uh, as having originated from this, you know, the scary internet zone and causes several things to happen. One thing that happens is that Windows Smart Screen system is invoked when anyone or anything attempts to run the file. Smart screen, you know, raises an eyebrow and looks to see what it can determine about the file. It, it examines, it is as commonly downloaded using some cloud based, uh, comparison system, uh, examines the, uh, the signature is this thing signed, uh, you know, presumably that matters and so on. So in addition, and this is where we were talking about the mark of the web earlier, Microsoft Office uses this mark of the web flag to determine if the file should be open in protected view by any office apps, which would then cause macros to be disabled as an extra measure of protection.
(00:53:58):
And that's good. Okay. So what has come to light is that there's a zero day flaw that's currently under active use. It is being used to install ransomware with bypassing windows executable file protections, which has the effect of conveniently, well conveniently for the bad guys, uh, by bypassing all of the mark of the web flagging. Uh, HP threat intelligence team reported that attackers are infecting devices with Magna ransomware using JavaScript files as I mentioned before. And here's the kicker, the Java script files seen distributed by the Magna birth threat actors are digitally signed, but the signature is broken. Will doorman, who we've referred to often, he's very active, uh, a senior vulnerability analyst at analogs discovered that the attackers signed these files with a deliberately malformed key in the signature. When any executable file is signed in this manner, even though it's been downloaded from the internet and received a proper mark of the web flag, windows does not display any security warning.
(00:55:27):
The smart screen check never occurs and the file is automatically executed. Will further tested the use of this malformed signature technique and was able to create his own proof of concept files that similarly bypass the mark of the web and smart screen warnings. Note that when an unsigned file is downloaded and opened in Windows 10 unsigned, a mark of the web security warning is properly displayed. And when a properly signed file is downloaded and opened in Windows 10, a mark of the web security warning is properly displayed. It's only when a malformed signed file is downloaded and opened that Windows 10 remain silent and just runs the file. So this appears to be a bug that was, was introduced into Windows 10 since will observed that a fully patched Windows 8.1 machine displays the mark of the web security warning as expected, even when it encounters a maliciously broken signed file.
(00:56:44):
And something changed with Windows 11 since the bug does still have an effect when executing files from an archive, but not when run run when running them directly. It appears that the bug originated from the new feature in Windows 10, that it's under check apps and files. Smart screen feature, which is Windows Security app and browser control, Reputation based protection settings, which first appeared in Windows 10 disabling the check apps and files causes windows to revert to its older behavior where mark of the web prompts are unrelated to authentic code signatures. And then you do get the, the mark of the web caution. On the other hand, you then you don't get the smart screen filter checking. So it appears to be the signature checking that's resulting in a verification bypass. And again, HP discovered this being used in the wild to sneak ransomware into Windows machines.
(00:57:50):
And finally, I would say, believe it or not, but routine listeners to this podcast will believe it will. Dormin shared <laugh> the proof of concept with Microsoft who said they were unable to reproduce the mark of the web security warning bypass even though both he and Lawrence Abrams at bleeping computer had easily done so. So we'll see how this one goes. Uh, as far as I know, no CVE assigned to this yet reported by HP and Microsoft says, Eh, well that's hysterical. Was it just some flunky, I mean some intern answering the phones that day. Uh, I don't see it. Hey, I just don't see it. That's bizarre. How is that Leo? I know he published a proof of concept, right? Yep, yep. Showed them how to do it and they say, Yeah, uh, it's not happening for us. That's worse than, Oh, it's an intended, it's intended.
(00:58:51):
That's like, I know I don't, eh, I don't see it. Yeah. Yeah. Okay, so for the record, I'll note that yesterday as part of a bundle of security updates, Apple patched and fixed it's ninth iPhone zero day vulnerability of the year. And Apple said the same thing they always say, which is that quote, it may have been actively exploited uhhuh, although no one even Apple thinks that it wasn't. Uh, and of course that's why it's a a zero day as we know. Uh, well all we know is that CVE 2022 42,827 is an out of bounds right flaw reported to Apple by an anonymous researcher and caused by software writing data outside the boundaries of the current memory buffer. So your classic memory overrun, this can result in data corruption application crashes or in the hands of an expert hacker, apparently code execution. And Apple did say that if successfully exploited in a tax, this zero day could have been used.
(00:59:58):
You know, Oh yes, they're using the past tense could have been used cuz now it's been patched by potential attackers to execute arbitrary code with ker privileges to, uh, or the, the complete list of impacted devices includes the iPhone eight and later. So it's been around for a while. iPad Pro all models, iPad, Air Third Generation and later iPad, fifth generation and later, uh, and iPad Mini fifth Generation and later Apple address the zero day vulnerability in iOS 16.1 and iPad OS 16 with improved bounce checking. So again, nine of those. Uh, so where are we? Nine of those in by the end of month 10. So they're doing pretty well, less than one a month. Okay. Uh, the evolutionary demise of banking malware. While assembling today's podcast, I ran across some interesting commentary which described various factors that have worked to reduce the prevalence actually to near zero of once dominant banking malware.
(01:01:14):
I've edited it for our audience, uh, because a lot of it was stuff that we really well know. But here's the gist of what happened. As described researchers from the security firm Mandiant have reported this week that you are S N I F, well I'll, I'll pronounce it, You are Sniff, which is also known as Go Z, which we've talked about or go Z slash if fsb, one of the oldest and last few remaining banking Trojan operations that were still active this year, has completely ditched its banking fraud related features, and now appears to operate as a basic backdoor Trojan, the type of bare bones malware typically used now in access as a service schemes that red access to compromised devices. And of course they're renting them typically to ransomware perpetrators. In other words, you know, just creating and opening doors for others to use is what this once preeminent banking Trojan has become.
(01:02:34):
According to Mandian, the change took place this summer when UR sniff developers started distributing a new UR sniff. Um, which it its version was tracked under the code name LDR four Mandiant sites. Several reasons for UR sniffs new radical redesign. At least two leaks of its earlier code base had occurred. Multiple branches of its authentic code base had had been slowly diverging and were making it harder to support their features across different botnets o boohoo. But also it was an ancient code base that had finally reached the end of the road when IE was formally removed from Windows. Mandiant said quote in June, 2022 with Internet Explorer finally being fully removed from Microsoft Windows. The RM three variant was efficiently seen as a dead malware from a technical point of view, as RM three was reliant on ie for some of its crucial network communication. And there we see at the mixed blessing of ie being a left being allowed to stay around for so long because so many enterprises were utterly dependent upon it for their internal software, which would not run without it, as we've discussed many times.
(01:04:05):
So it's a surprise that you are sniff lasted as long as it did operating as a basically on a banking Trojan model alone. It had become obvious by the mid 2010s that the banking Trojans, that the, the banking malware scene was dying at least on the desktop. Banks finally growing tired of a decade of thefts from customer accounts at last, rolled out mati multifactor authentication and transaction verification systems. Though they were not foolproof, these systems did their job and made it significantly more difficult and time consuming for banking malware operators to steal money from individually compromised accounts. Back in 2016, emote and trick bot had converted their code bases from banking Trojans to generic modular back doors. And were those two were some of the first to do so. And even though they kept their banking modules around the dry decks and Qat malware also followed suit later.
(01:05:21):
In all instances. The primary driving force behind this shift in malware economics was the rise of ransomware and enterprise network big game hunting. As it became clear to ransomware operators that they could extort obscene amounts of money from companies and government networks, they started to look for ways into those networks. And the existing old time bot networks that had been converted were their way in. This led to the birth and rise of a market for so-called AABs. We've discussed initial access brokers where smaller threat actors would exploit corporate networking and server gear, plant back doors, then sell access to these systems to ransomware games and their affiliates. Evil Corp was the first major botnet operator to realize they could use their existing banking Trojan to drop mans ransomware inside the thousands of corporate networks they had at their disposal through the dry decks botnet, and even launched internal teams to write and deploy their own internal forms of ransomware.
(01:06:45):
And recall how often I noted that it was never safe to assume that an infected router would only be used as a proxy to bounce traffic or as a DDoS agent to flood sooner or later. I said the operators who had established a foothold on these routers were gonna turn around and take a look inside the network that they had infected to see what might be a valuable there. Because the dry decks botnet operated on a closed model where it's operator, where it's operator prov was only providing limited access to their botnet to only a handful of very carefully vetted operators. The the service oriented emote and later trick bot, which were open, anyone who wanted to sign up and who had been vetted, cornered the market in malware as a service working with ransomware games and after law enforcement finally cracked down on a mote and trick bot.
(01:07:55):
Two others iced ID and QBO stepped in as ready replacements after years of having slowly been growing their own botnets in the shadows of emote and trick bot. The world of underground malware is not difficult to understand. It's simply about the minimum amount of work that can be performed to obtain the largest profit banking and carding is now difficult thanks to banks and ransomware is easy thanks to all the bazillion reasons we talk about every week. There's no good reason to run a banking botnet these days, especially one as old and complicated as you are sniff had become. It's far easier to create and manage a simple botnet spam board corporate employees until they infect themselves and then sell access to ransomware or crypto mining gangs for a cut of the prophets. What this does mean though, the takeaway for us is that the urgency to remove anything that might manage to crawl into your network has never been greater. Stats from the latest intrusion reports indicate that ransomware can be deployed within 30 to 60 minutes of an initial intrusion. This strongly suggests that the deployment of responsive intrusion detection should be front of mind for all security teams going forward. There's just, there's no substitute for watching.
(01:09:37):
Um, one last bit of news today. This morning VMware released an update to repair a critical low complexity CVSs 9.8 remote code execution vulnerability in VMware Cloud Foundation, which is their hybrid cloud platform for running enterprise apps in private and public environments. This 9.8 out of 10 flaw identified as CVE 2021 39,144 was published August a year ago in 2021. The flaw exists in the open source extreme library, which is used by Cloud Foundation. And I can't excuse VMware for not having updated this a year ago because this was a well known, uh, flaw in a stream library they're using and a year has passed. It's the update happened this morning. It carries that 9.8 rating because it can be exploited remotely by unauthenticated evil doers in low complexity attacks that don't require user interaction. In other words, it's easy to do and it's just a matter of finding a server on the public net and doing it that's as bad as it can get. And due to the severity of the issue, which has existed, as I said, for more than a year, VMware has also released security patches for other of their end of life products, which remain in use, which also remove, which we're also using this extreme library for some time. VMware's release advisory said quote, due to an unauthenticated endpoint that leverages extreme for impo deserialization in VMware Cloud Foundation, which is NSX hyphen v, a malicious actor can get remote code execution in the context of root on the appliance.
(01:11:49):
Okay, so that the trouble is a deserialization flaw. And we've discussed many times that data deserialization, which is inherently a data interpreter, is often a source of extremely subtle, yet highly exploitable bugs. The national vulnerability database that is, you know, the guys that maintain the CVS system says X Extreme is a simple library to serialize objects to XML and back again in affected versions. This vulnerability may allow a remote attacker who has sufficient rights to execute commands on the host only by manipulating the processed input stream. LEO io, as you were just saying. Yep. And speaking of flaws from last year, earlier this month, VMware informed customers who updated to vCenter Server 8.0, the latest version that they'll have to keep waiting for a patch to access a high severity privilege escalation, vulnerability disclosed nearly a year ago, last November, 2021. So I don't know what's going on with VMware, but uh, you know, these are serious vulnerabilities and they should be fixing them more quickly.
(01:13:08):
Okay. I have some closing the loop, uh, tidbits to share. Uh, Nicholas Ross, he said at SG GRC in SN 8 84, you mentioned a piece of software you used to make graphs of SN m p, that's what they're called counters for you or is for your PF SENSE router. What was that software? Okay, so first of all, Nicholas was reminding me that its S n MP Simple Network Management Protocol. That was the term I was blanking on during the, the podcast a few weeks ago when I was talking about monitoring the flow in and out of my pf sense based router. The fabulous freeware utility that I love for Windows, also for Mac, which I've talked about in the past, is called Networks, N E T W O R X. It's by a company called Soft Perfect and they're at soft perfect.com. The version I have is 5.5 0.5, which is the last of the freeware releases after a long history of this thing being freeware.
(01:14:24):
When they went to version 6.0 0.1, which is the release after 5.5 0.5, it became trial wear for $30 and then you buy it for 25 bucks. In my opinion, it's certainly worth $25. But 5.5 0.5, which is what I'm using and will continue to use because it's perfect, is available on the web. I just found it on File Hippo. Uh, and I have a link in the show notes, the download, just because you always want to do this when you're downloading from a, from a download site, not the, or, you know, the origin, the download is digitally signed by a digit cert certificate issued to Soft Perfect in 2016, signed with both s sha one and s sha 2 56, cuz they wanted it to work on both old and new versions or Windows. So double check that and you can trust it. Uh, and I did, I downloaded it, I downloaded a copy of just, just last night of 5.5 0.5 from Soft.
(01:15:31):
Perfect. And verify the certificate cuz I knew I'd be talking about it today. The reason I love this so much is that although it has many features that may be of interest, three things about it stand out for me. First, as I mentioned at the time, it will monitor any interfaces SN m p counters. So I have it watching the WAN interface on my pf sense router, which by the way, it found for me, I didn't have to dig around it. You, you're able to say, don't look at my local, uh, interfaces. I want to ma to monitor something else. And it enumerated them for me and I selected from a list and it just worked. So they really, they got that right. Um, second, it offers, and this is the key, a logarithmic scale for bandwidth monitoring and display, which is so much better than a linear scale.
(01:16:30):
And it's exactly what you want. And I have a picture of a snapshot i I made last night where you can see why a logarithmic scale is so good because that way you can see fluctuations in activity when not much is happening on your network while still seeing maximum rate connection saturating transfers without going off scale. Uh, uh, I have mine sized as you can see in the screenshot below so that the, so that the, the vertical scale, uh, snaps to decade powers of 10 scaling with the max set to one gigabyte. Since I can pull down 300 megabits over my Cox cable modem that moves the graph into the la the very last upper scale region without going off scale yet when things aren't going along very much like I, like I on this graph, I'm also seeing something around just a few KBIs down toward the beginning of the graph, yet back toward the, toward the back.
(01:17:36):
It's up just shy of a hundred megabits. Anyway, love this thing. Uh, what the red and green lines on, on the show notes show is Red is always incoming for me. That's something is downloading data into my network and I want to know what that is or like that it's happening at least. And the green is things I'm sending outwards. Uh, so anyway, just very cool. I have it, it's, it auto starts. When I boot any of my, uh, my windows desktops, it sits, uh, running on a monitor. It behaves itself. You're able to set it up so there's no extraneous windows, uh, nonsense. Anyway, just a perfect piece of software. Again, softwares, so I'm sorry, networks from soft perfect N E T W O R X and get the free one or get the paid one, whatever you want. Um, Ando David Roots <laugh>, uh, he sent me a little dialogue.
(01:18:39):
He said she Colon saying it's 3:00 AM why are you up? He, and then he me responds at sg GRC recommended a book. She, But you finished the Rick Brown ones me, it's a new series, different author, and then she assembled. It Didn't resolve to anything, but you know, probably a fuming face. Anyway, uh, I'm now on book 14 of the Silver Ships series and boy has it been an interesting ride so far. One of the most interesting topics raised across the series, and it's probably safe to say though I'm not finished yet, that it's one of the series primary explorations is the truly, and I mean this is an all sincerity cuz I don't think we're necessarily a long way away from this. The truly intriguing question of the rights of sentient digital entities. Near the start of the first book, we meet Julian, the sentient intelligence that runs a derelict Starship, the series primary human character.
(01:19:59):
Alex forms a deep bond with Julian and the books explore many aspects of digital intelligence and the rights of sentient machines. Uh, really interesting. Anyway, I I'm loving this series for what it's worth. Um, Z A c C, uh, said at sg g rrc. Can we get a link to the hockey puck shaped power and reset button you mentioned on the show? Uh, he was talking about the thing that I got from Amazon, which I love, and I have like seven of them I think now, uh, attached to motherboards and now attached to both of my ZMA boards, which is just, it's a like a little floating, uh, hockey puck with four feet where there's a big easy to press button in the top and a little harder to press reset button. And I've got them swapped since I'm most often resetting <laugh>. My, uh, uh, my hardware.
(01:21:00):
So the big easy to press button is the reset button and the little one is the power button and it's also got two lights in it, 1, 1 1, 1 for power and one for hard drive activity. So anyway, love it. Uh, it's less than seven bucks and the link is in the show notes. Connect the motherboard. Yeah, exactly. Okay. Yeah, yeah, exactly. So you, you, you could normally, those little connectors will run out to the front panel right, of a case. Recognize them. Yes. Yep. And so this allows you to instead extend it out to like, for example, I if your computer case is under your desk or or behind your desk where, you know, getting to it is not easy. This basically remotes it and it's a long cord. I only need it to be, you know, a foot, but it's like you get six feet or something.
(01:21:50):
So I have a coil. Yeah, four feet long. Yeah. Oh, okay. Yeah. So Bart said, Hi Steve. I can't remember if it was the last SN episode or the one before, but I remember you mentioning how much faster spin, right? Six one can surface test today's larger drives was just looking, was just wondering is that your own tests or the feedback from the test community? I tried looking for a spin right? Alpha beta to experiment with on my own drives and PCs, but nothing that would go past the drive detection phase, which by the way is working flawlessly with my particular setups. Have I missed something or is there no such release yet? Will we be able to get past the dragons <laugh>?
(01:22:37):
I actually forgot that you said that, Uh, on the all of the spin right test releases, if you try to, if you select the menu option after selecting a drive, you then do what spin right does to actually start running the drive up comes a red cautionary screen with the title, uh, beyond this point B Dragons. So, uh, that's what he was talking about or hear live dragons or something like that. But anyway, the numbers I've been sharing are those from the testing community. And it's great to hear that the drive detection phase worked well for Bart since that's where the past year and a half have gone. Getting to that stage requires all of the new aspects of spin, right? To be working to such a degree that actually running spin right is almost ana climatic. You know, that said, none of the testing releases have gone any further since.
(01:23:34):
That's the next step that I'm currently working on, which is also happily also the last step and actually is really going very well, uh, in those testing releases. Spin right has already estimating the total time required to run on a drive by extrapolating from the speed tests it performs during startup. And it does show you those in a scam time column in the various user interfaces. Bart, in case you missed that, um, underscore skin underscore said, Love your show question though. Why on earth is spin, right? Six one gonna be free, not even an upgrade fee, you're leaving money on the table. We wanna support you. Exclamation point. These all had exclamation points, I think I'm gonna buy it again just because of how hard you worked on it. Okay, so the short version is a promise is a promise, even if it's a promise I made nine years ago and actually more than, yeah, I think it was nine years ago in 2013.
(01:24:33):
And while that's enough, more than that, I am sure that many people have purchased spin right 6.0 based upon the promise that they'd be getting six one at no charge. And while this has indeed turned out to be a much bigger challenge than I originally expected, I'm happy to do it because along the way I discovered some very cool new tricks that I didn't suspect in the beginning, which leaves me to believe that a future spin right would be have, you know, will have a few tricks up its sleeve that are unsuspected. So there will be a spin, right version seven, 7.1, 7.2 and beyond. So I'm happy to have six one available for free. I basically wanna addict everyone to what spin right has become and then <laugh>, we'll go from there. Uh, will Moler, uh, he said last week's sn the discussion of ECB mode of encryption brought back a question I've always had.
(01:25:35):
Isn't any chaining mode of encryption brittle if any part of the encrypted text is lost? Isn't it the case that all subsequent blocks cannot be decrypted? You're absolutely right, will, but as we might say that's more of a feature than a bug. One of the things we often wanna do is detect any tampering of any kind, deliberate or inadvertent. With a files contents, huge damage could be done by, for example, adding or removing a zero from financial data. Since the integrity of the data is often just as important as its secrecy, we're often wishing to both encrypt and authenticate. And in the past we've spent some enjoyable time considering whether it's better to encrypt first than apply authentication to the encrypted result or to authenticate a file before encrypting it. And hint if you do both, if you cannot do both at once and some cipher systems can and do, then you'll want to encrypt first and then apply authentication to the result.
(01:27:04):
The reason is that upon reversing the process at the receiving end or the, you know, reading end, you never want to decrypt anything that may have been altered. It's always best to verify that the file has not first been tampered with and if so, drop it immediately. If it has been altered, uh, getting back to the point as a result of that, having brittle encryption, that will always cause the file to essentially explode downstream of the point where anything was changed could be considered a good thing. You know, it won't authenticate certainly, and boy it will not decrypt, uh, <laugh>. And lastly, Ken Dudley asked, Hello, what transcription software do you use for the podcast? It is Ken, a fabulous system known as Elaine Ferris <laugh>, who is located@eigtranscription.com. She's not as cheap as software, but boy she is a lot better. Um, and one piece of miscellaneous, uh, for the first time ever, I used Edge to assemble this document yesterday and today the reason was that Chrome, which I have always been using on my main Windows seven system, has become laggy for some reason.
(01:28:37):
And it's really become a problem using Google Docs. Even just scrolling. I thought that it might be some extension that I'm running, but I'm only running last pass. And you block origin. Uh, although I did note that you Block Origin believes it's blocked more than 5,000 things. <laugh> in Google Docs. Yeah, <laugh>. Wow. Wow. So maybe I oughta actually tried disabling uBlock origin to come to think of it. It's busy. It's very busy. Yeah, so I've been putting up with it of this problem for, uh, weeks. But yesterday the lag was really interfering with assembling this document. So of course I first switched to running Google Docs under Firefox. It was super snappy and ran like a charm. But the Verena font I like to use, I didn't even bother trying any other fonts cuz I, I didn't want to go away from ver Dana had an annoying curing problem.
(01:29:32):
The letters were not spaced uniformly at all. It was conspicuous. And it turns out I'm not the only person to have reported this. Many others online have posted, uh, similar like, like kerning problems in Google Docs and Firefox looking for solutions. Nothing. They tried, worked, nothing. I tried, worked. So I, for a while I tried to ignore it, but the wrongness of it bothered me. Finally, I thought I'll use the other chromium based browser that I have. That being Edge, well Edge worked beautifully and I wrote and produced this entire show notes document using it. So here's the thing that caused me to bring all this up under Edge and Windows 10 where I was working last evening, but not under Windows seven. The Windows Alt tab key sequence switches among recently opened browser tabs in addition to top level desktop apps. As it happens, um, for me that's a huge win.
(01:30:43):
Since during the preparation of these notes, I'm often jumping back and forth between browser tabs. Having seen this behavior under Windows 10. I'm now missing it today under Windows seven, where all I'm getting is top level application Windows as I always have, as all old Windows hands know alt tab is the Windows keyboard shortcut for changing among the desktops foreground apps. And I'm often using it to quickly jump back and forth among running apps. Typically cutting and pasting to move selected content around. But I've never seen it jump between different tabs on the same browser. It must be because Edge actually is running each browser tab in its own process space for inter tab isolation. So in a sense, the browser tabs really are individual browsers, but this was unexpected and I just wanted to make a note of it. I'll just, uh, point out you can change that in system multitasking.
(01:31:50):
You can say, no kidding, show Microsoft Edge tabs when snapping or pressing all tabs. You could do all tabs. Five most recent and three most recent or don't show tabs. Now this is Windows, Windows 11. I'm not sure what the interface is on, uh, Windows 10. I bet it's the same seven. I bet it's same. Yeah, yeah. And yeah, cuz they're separate processes by the way, Chrome. They're separate processes too. That's yeah, that's the image Cromme and mean. Well, and Firefox has done that. I mean, I don't know if you, if you've looked at task manager, but boy, if you've got a bunch of tabs open, half of it is your browser. They have to do that. I, I would guess, right? Yeah, I I think they do. Unfortunately. It'd be nice if they could like nest them and show them in the, you know, in in task manager.
(01:32:31):
But anyway, they would still be there. Anyway, I also wanted to note that Google just announced, look at all my Firefox Times <laugh>. <laugh>. There you go. Yep. And they are nested. Yeah, that's a very nice display. Yeah. Yeah. Again, this might be a Windows 11 thing. I don't know. Ah, let's, let's see. Edge, I, yeah, I only have a bunch of processes under Edge, but I think, I don't know, but I would guess these are all, yeah, these are all Firefox tab. Yeah, very cool. Yeah, so I wanted to note that Google just announced that Chrome's support for Windows seven and 8.1 will be ending early next year. I think it was in February. Uh, that's one of the dumbest things I've heard recently. Windows seven still commands 10% of Windows desktops, one of mine being among them. And Windows 8.1 has an additional 2.7%, so that's 12, 12.7% or more than one out of every eight desktops still running seven or 8.1, most of them seven by a huge margin.
(01:33:35):
And the dumbest thing about this is that it must be arbitrary and deliberate on Google's part. There's absolutely no reason why Chrome should care whether it's running on top of seven, 8.1 10 or 11. If Chrome cannot ignore the version number of the Windows operating system is running on, then they're doing it wrong. Presumably, Google's decision to abandon Chrome on pre Windows 10 machines synchronizes with the end of Microsoft's extended security update. You know, their ESU programs for Windows seven and 8.1, which is occurring on January 10th next year. I suppose that at some point I'll need to give it, uh, give up my use of Windows seven on my primary working system, but I'd rather just keep working. If I have to switch Windows versions, I'm gonna suffer a bunch of downtime, you know, getting everything set up and reinstalled and going again, which, you know, is a constant annoyance for Windows, but it's, it's our life.
(01:34:42):
And Leo? Yes sir. Thinking of our life, let's talk about one of the things that is supporting our life. <laugh> Club Twi. Oh no, our sponsor. Yes, that's right. I'll talk about Club Twin another time. Data breach. Responsibility. Security now is brought to you by Barracuda. Let's talk about Barracuda. This is, uh, I mean this is if you, uh, you know, just what we've been talking about, uh, with ransomware and threats and how did those ransomwares, uh, get in email? In an email, uh, trends survey, Barracuda asked, uh, respondents, have you ever been a victim of a spear fishing attack? A targeted fishing attack? 43% said yes, but, and this is sad, only 23% said they have dedicated spear fishing protection. We just hope, uh, our employees won't open it. That's what <laugh> that's what they said. The rest of 'em said, Just hope they don't open it.
(01:35:39):
How are you keeping your emails secure? Barracuda has identified 13 distinct types of email threats and how cyber criminals use them every day from fishing to conversation hacking to ransomware plus 10 more tricks. Cyber criminals use to steal money from your company or personal information from your employees and customers, or both. Are you protected against all 13 types? Email. Cyber crime is becoming much more sophisticated. The attacks getting harder and harder to prevent. They use social engineering, they include urgency and fear to pray on their victims. And those social engineering attacks, including spear fishing and business email comprise cost businesses an average of $130,000 per incident per incident. As demand for COVID 19 tests increased at the start of the year, Barracuda researchers saw an increase in, you guessed it, covid 19 test related phishing attacks. They went up 521% between October and January of this year.
(01:36:48):
As public interest rises in cryptocurrency, the opportunity for attacks, I think you probably can guess it becomes ripe. When the price of Bitcoin went up a couple of years ago, 400%, uh, that was October, 2020 through April, 2021, Barracuda research found impersonation attacks grew almost as fast. 192% in the same period that bad guys go where the money is. Right. In 2020, the internet Crime Complaint Center, I C three received 19,369 Business email compromise, email account compromise complaints, adjusted losses, $1.8 billion. And you know, that's just the type of the iceberg securing email at the gateway. You know, perimeter protection, that's not enough anymore. Yeah, of course it's still important to leverage gateway security to protect against traditional attacks like viruses, zero day ransomware, spam, other threats. But your gateway is defenseless against targeted attacks. Spear fishing attacks, they go right through protection at the inbox levels key, right?
(01:37:55):
Including AI and machine learning. That's what you need to detect and stop the most sophisticated threats. They're evolving fast. Your software needs to evolve at the same time. Here's what I would recommend. Get a free copy of the Barracuda Report 13 email threat types to know about right now. You'll see how the cyber criminals are getting more and more sophisticated every day, how you can build the best protection for your business data and people with Barracuda. Find out about the 13 email threat types you need to know about and how Barracuda can provide complete email protection for your teams, your customers, and your reputation. Get you free ebook right now, barracuda.com/security now. That's barracuda.com/security. Now barracuda your journey secured. Thank you Barracuda for supporting security. Now, I mean, obviously this is a match made in heaven and thank you for supporting us by going to that address so they know you saw it here. barracuda.com/security now. Now back to Steve. So, uh, over the weekend, a piece of surprising sort of over the top news from Australia got me thinking about the nature of data breach, culpability and legislative response. Everyone who's been sharing this podcast for a few years will have heard and learned enough to have a well formed and well-informed opinion about culpability, but you know, not so are legislators. So first, uh, here's the news from Australia.
(01:39:37):
On the heels of a month of high profile and embarrassing attacks in Australia, there was Optus, Telstra, MetaBank, Woolworth's, and Energy Australia. Three days ago, on Saturday, the office of Australia's Attorney General posted an aggressive intention regarding legislation that is slated for discussion and adoption this week. One question that comes to mind is whether what happens in Australia remains in Australia or will this aggressive legislation, you know, just be the first and prove to be, you know, to be the harbinger of similar actions by other governments. Anyway, so here's what the Attorney General's office published on Saturday. The, the Albanese government will next week introduce legislation to significantly increase penalties for repeated or serious privacy breaches. When Australians are asked to hand over their personal data, they have a right to expect it will be protected. Unfortunately, significant privacy breaches in recent weeks have shown existing safeguards are inadequate.
(01:40:51):
It's not enough for a penalty for a major data breach to be seen as the cost of doing business. We need better laws to regulate how companies manage the huge amount of data they collect and bigger penalties to incentivize better behavior. The privacy legislation, amendment enforcement, and other measures, Bill 2022, which is happening this week, will increase maximum penalties that can be applied under the Privacy Act of 1988 for serious or repeated privacy breaches from the current 2.22 million penalty to whichever is the greater of $50 million or three times the value of any benefit obtained through the misuse of information or 30% of a company's adjusted turnover in the relevant period, whichever is greater.
(01:42:05):
They said the bill also provide the Australian Information Commissioner with greater powers to resolve privacy breaches, strengthen the the notifiable data breaches scheme to ensure the Australian Information Commissioner has comprehensive knowledge and understanding of information compromised in a breach to assess the risk of harm to individuals and equip the Australian Information Commissioner and the Australian Communications and Media Authority with greater information sharing powers. The bill is in addition to a comprehensive review of the Privacy Act by the Attorney General's Department that will be completed this year with recommendations expected to further reform, expected for further reform. And finally, I look forward to support from across the parliament for this bill, which is an essential part of the government's agenda to ensure Australia's privacy framework is able to respond to new challenges in the digital era. The albanese government is committed to protecting Australian's personal information and to further strengthen privacy laws.
(01:43:16):
Wow. Now I can see both sides of this issue. For me, it's not as cut and dried as you know, quote, companies who hold consumer data due to valid business needs and who subsequently fail to keep such data private are so clearly to blame that they should be penalized with a crippling monetary fine. I made that up, but that's what I mean in the real world. You know, we have this notion of asking for it like, well, you know, well yeah, it's too bad that his car broke down when it did, but he hadn't taken it in for service in over 10 years, so, you know, he was kind of asking for it, right? It seems to me that the underlying cause of a data breach absolutely does matter. Culpability need not be a mystery and it ought to be a factor af after all.
(01:44:18):
It certainly is a factor in all other aspects of the metering out of what we call justice. But that means that each issue needs to be taken on a case by case basis, just as it is elsewhere in the law. In the case of data breaches, the legislature might not want to do that and may not know how to do that, but it's bad legislation if culpability isn't factored into the outcome. If a company is shown to have been running a five year old and many times Obsoleted instance of, for example, VMware in the cloud that was riddled with known and long since patched vulnerabilities where one of them was inviting the bad guys into their network to root around an exfiltrate data, then yes, any reasonable person would find their IT department management grossly negligent, incompetent and culpable. And on the subject of asking for it, which relates to breach responsibility, I would add that when such a breach occurs, thus drawing everyone's attention to the fact and nature of the breach, the leaked information which would then be public should be examined to see whether any personally damaging information was being retained in excess of the minimal needs of the business's purpose.
(01:45:53):
Because doing so should be a big no-no. But if a company was running only the latest currently patched state of the art updated software, active intrusion detection and network monitoring, holding periodic employee cyber awareness, conduct training, conducting simulated intrusion drills and randomly sending their own employees test bait phishing emails. And yet, despite all of that due to an entirely unknown zero day vulnerability in the latest Microsoft Enterprise software or VMware, which we just talked about, someone crawled into their network and exfiltrated a database containing the bare minimum of personally identifiable customer information. How can it possibly be fair to Lev a crippling fine of no less than 50 million and perhaps much more onto such an enterprise?
(01:47:06):
The world as a whole is culpable for time and time again, having chosen features over security for having chosen to make our computer systems so overly complicated that they've become unknowable to anyone using them. We're all mostly just hoping that things are gonna turn out all right. This happened of course, because it's not possible to sell actual security as a feature. Security is the absence of problems. You cannot sell an absence upfront when problems take time to be found and revealed. Way back before the release of Windows xp, when Steve Bomber was jumping up and down on stage bellowing at the top of his lungs that Windows XP was the most secure operating system that had ever been created. It wasn't possible to prove or to know then just how wrong time would prove that statement to be. I know Steve Bomber and I like Steve Bomber, he's a big huggable teddy bear, but as Bill Gates would say, he's not a technical guy.
(01:48:24):
So I imagine that Steve sincerely believed what he was selling, but it didn't matter how much he believed it wasn't true. So we've built ourselves an industry where software is intellectual property that isn't sold it's license, and where the agreement to license said software invariably incorporates a statement explaining that the licenseor is making no representations of any kind whatsoever as to the operation or fitness of purpose of the software and where the licensee agrees to hold the license or harmless for any and all consequences of any failure on the part of the software to function as they might hope. Often going so far in the case of overly zealous attorneys as to say that the software's publisher has no idea whatsoever whether the software works, what it does or what it may or may not do, sign here in such a world. While it is definitely possible for negligence to be the proximate cause of horrendously damaging data breaches, it is also entirely possible for a well meaning and perfectly well behaving company to be the blameless victim of the software industry We have collectively built until, and unless things change, I dearly hope that all future legislation keeps this in mind.
(01:50:04):
And I hope that any organization who did everything right yet was breached anyway, is able to find a good law firm which is able to make this case for them. <laugh> Bravo <laugh>. But what, what, what, what, what would your best guess be as to how many of the breaches are the company doing something stupid like leaving their S3 bucket unlocked? Almost all. Yeah. <laugh>. So there's almost all, So yeah, I admit security's hard and there's companies screwing up, but a lot of these breaches of the fault of the company getting breached. Right, Right. Yeah. It is really, really, really difficult to be perfect. Yeah. And unfortunately, we've, that's where the bar is, you know, you know, you've got to be perfect. Yeah, Yeah. Well, welcome, uh, welcome to Computers <laugh>. Right? I mean this is, this is how it's always been. You know, I I used to accept, uh, requests to be an expert witness in jury trials.
(01:51:13):
Yeah. Or even in in court trials where I was just talking to a judge. And in fact, it was the last one I did was, was a New York with a talk explaining to a judge why, uh, a, an an NEC competitor Multis Sync monitor, uh, Mul Multis Sync was NE's uh, trademark. But I was trying to explain to the judge who had a green oxygen tank sitting next to him. Um, why, why I think it was Paradise was the other, what was the competing monitor firm on whose behalf I was testifying cuz they were right that NEC was wrong to sue them over their claim that it was be the last monitor you needed because it adapted to the PS two s differing sink and you did not need a new monitor anyway. Um, it was, they, they ended up the the outcome was wrong and I decided I'm never gonna testify again. Yeah, yeah. Because it's too frustrating. Yeah. But if someone comes to me and they've done everything right and they're being sued by their government, put me on the stand. There you go. I will, I will read this column and, and we'll go from there. There you go. I will defend your right to, to not be sued for that breach. Steve Gibson. He's right here. You could find him right here every Tuesday. If you need him to testify on your behalf, you may regret that <laugh>.
(01:52:50):
He, uh, he comes here every Tuesday around one 30 Pacific, four 30 Eastern 2030 utc. We're still in daylight saving time. We will not be in two weeks. So just make a note of that. I know, uh, people in the, uh, the EU have already gone to, uh, uh, ended summertime. Uh, but w but UTC hasn't, we haven't moved ourselves yet. UTC is still, uh, the same 1830 UTC or no, 2030 utc, but it will in a couple of weeks cuz UTC never moves. But we do. And uh, cuz you know, we have to follow the sun as it were. You could. The reason I mention this is so you can watch us live at, uh, live doit tv. There's live audio and there's also live video. Uh, you could take your pick uh, chat with us live if you're watching live at IRC TV Club.
(01:53:37):
Trip members can of course chat in our fabulous discord, which always is a lot of fun. And it's not just the, uh, the shows that we're talking about. We talk about all kinds of stuff in here. Clump twit, uh, basically is $7 a month for ad free versions of this show. And every other show we do plus access to the Discord, we do talk about coding, by the way, in the, the Discord. Steve, you can stop by if you want, but there's also crypto and defi and fitness, tech and hacking and ham radio and hardware and lenux and music and on and on and on. It's really more than just a chat room. It is our clubhouse. We also have, uh, shows that appear only for the club, like our hands on, uh, Macintosh show, Like a Sergeant does that Hands on Windows. Uh, Paul Thra does that.
(01:54:25):
The entitled Linux show with Jonathan Bennett Stacy's book Club coming up this Thursday. All of that just for club members. Uh, and the Trip plus feed, which includes stuff before and after the shows, a lot of times some of the best conversations are before the show gets started or afterwards. Uh, all of that is $7 a month. And it is really important right now because as we head into, uh, difficult economic times, winter is coming and, uh, we notice that most of our advertisers have decided to say, Yeah, let's, uh, we're just gonna wait and see what happens next year. Uh, we can't tell pg and e that we can't tell the <laugh> Electric Company that the, the internet service providers or anything like that. We gotta pay 'em. So your contributions to the club helps a lot. I cannot stress that enough. Go to twit tv slash club to find out more.
(01:55:12):
You can also, by the way, uh, subscribe for a year. There's no discount. We just make it easier if you don't like to pay every month. Uh, and I'm pretty sure we'll be here a year from now if you all join. And if Steve doesn't quit early, uh, we'll also, no, he's going to 9 99 he said. So, uh, we also, uh, have, uh, corporate memberships and, uh, it's really nice when a company joins. We just got another corporate membership last week, which was great. Thank you. Uh, on demand versions of the shows also available from Steve for free. They have the ads baked in at security or uh, grc.com, grc.com. And, uh, he has other things that you might want, including those great transcripts from Lane Ferris. He's got 16 Kilobit audio as well as 64 Kilobit audio. He also has spin, right, the world's best mass storage, maintenance and recovery utility.
(01:56:03):
You can get the version 6.0 right now and guaranteed upgrade to 6.1 the minute it's available. Uh, grc.com. He's on the Twitter at sg grc. You can leave messages for him in his dms. They're wide open. G uh, at sg g grc. Uh, you can also get a copy of the show at our website, twit tv slash sn. That's the free ad supported version. Uh, YouTube also has a even more ad supported version <laugh>. Uh, and uh, there's also of course, uh, the best way probably to get it, subscribe in your favorite podcast player. Our feeds only do the last 10 shows cuz it's a feed. It's not intended to have every show. All 800. What is 800? Uh, what do you got? 894 94. Holy cow. Uh, but you can go to the website at all the old shows, uh, there all the way up to episode one. Uh, and, and make sure you do cuz you want the complete set, right? Yes, Steve, enjoy your silver ships. Ev you're up to number 15. 14 four. Oh, so you only have six more volumes. Actually,
(01:57:10):
It turns out
(01:57:10):
That there, I found another six after, after the 24. So it's a, it's an even 30. I thought Rick Brown was prolific. Wow. Okay. It's, uh, it's good. <laugh>. We're gonna keep this guy up late. <laugh>. Sorry, honey, had to read the book. We'll see you next time on security now. Bye Steve. Thanks. Bye.
Mikah Sargent (01:57:32):
Is that an iPhone in your hand? Wait a second. Is that an Apple watch on your wrist? And do I, do I see an iPad sitting there on the table? Oh my goodness. You are the perfect person to be watching iOS today. The show where Rosemary Orchard and I, Mike a sergeant, talk all things iOS, tvOS, watch os Home Pod os it's all the OSS that Apple has on offer and we show you how to make the most of those gadgets. Just head to twitch.tv/ios. Check it out.
... (01:58:07):
Security now.