Security Now Episode 891 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for security. Now, Steve Gibson is here. Another flaw in teams. You might wanna know about this before you let somebody use your computer. We'll talk about that exchange server. Zero day, they're at it again. A brand new way to do caps thanks to CloudFlare, I think will like this one a little bit better. And then an ika I flaw that they didn't want to pay security researchers for, to fix. It's all coming up next on Security Now. Podcasts you love
... (00:00:33):
From people you trust. This is TWiT.
Leo Laporte (00:00:41):
This is security now with Steve Gibson. Episode 891, Recorded Tuesday, October 4th, 2022. Poisoning. Akamai Security now is brought to you by ZipRecruiter. There are so many podcasts out right now. It takes a team of people to bring each and every one of them together. Whether you're hiring for a podcast or for your growing business, one place makes it easy. Ziprecruiter. And now you can try it for free at ziprecruiter.com/securitynow and by ITProTV. If you're looking to break into the world of it, or if your IT team needs to level up, get the introduction you need with ITProTV. Check out an ITProTV business plan by visiting itpro.tv/securitynow today. And by Kolide, Kolide is an end point security solution that uses the most powerful untapped resource in it and users visit kolide.com/securitynow to learn more and activate a 14 day free trial today.
Leo Laporte / Steve Gibson (00:01:50):
No credit card required. It's time for security. Now, I know you've been waiting all week long. Mr. Gibson is here. He's prepared. He is ready to talk about the world of security. Steve Gibson from SG GRC fans. Is, is that you looking at the screen? Yeah. As if I can like see through the Magic Mirror. I look back at you that <laugh>. It's a, it's a, it's an affectation that, that performers often use. I'm actually not even looking at you at all, but <laugh>, our, our audio listeners are like, What are those two clowns in order to look at you? And I'd have to turn my back on our audience, and I don't want to do that. So what I do Oh, sounds good. Is I look across to the left as if, didn't you, didn't you study drama at Yale or, Yeah, that's where I learned that.
Leo Laporte / Steve Gibson (00:02:36):
Why, Ah, Eye line. Yeah, that, So it kind of looks like I'm looking at you and in fact, I'm not. But you're to the, It's complicated. It's complicated. So that's, that, that works. What's up, Steve? So we got the first podcast for October, the fourth quarter of 2022, titled Poisoning Akamai. Oh boy. And, oh, it's, it's really fun. Not only what two youngsters figured out, and the fact that this all happened without many people knowing about it earlier this year, but what the consequences of this could have been, and also what happened after they went to Akamai to explain. So really interesting. But we are gonna first examine a puzzlingly insecure implementation by Microsoft in Teams Design. And also look at Microsoft's complete rewrite of Microsoft Defender Smart Screen. And we'll talk about that also, Ross Co Naar strikes. Yes, it's hot.
Leo Laporte / Steve Gibson (00:03:46):
You know, October, So that's goody season. Yes. And Exchange Server is again, under serious attack with a new zero day, which Microsoft knows about, hasn't fixed yet. And their suggestion mitigations have been worked around. So we're hoping for an actual fix soon because it's a nasty one. Cloudflare has introduced Turn Style, which is their free and much improved capture which they're offering even to non-Cloud flare users. We gotta talk about that. Also, Google just yesterday published a Fabulously engaging six video YouTube series under the Banner Hacking Google. So I, I have to that to talk about, and that's the tweet that you saw that I set out. I was so fascinated by that I forgot to tell everybody about the podcast. Anyway I'll get around to that when, when you tell us about our sponsor here in a minute. Then we're gonna spend some time sharing and replying to some lister feedback before we examine, as I said, a breathtaking flaw that was discovered in Optimize Global content delivery, network caching system, and what became of it. Hmm. And of course, we've got a picture of the week <laugh>. That's, it's bizarre, bizarre, bizarre, weird. It's, it's that strange one.
Leo Laporte / Steve Gibson (00:05:17):
All of that still to come on this fine security Now on a Tuesday afternoon. Our show today brought to you by ZipRecruiter, and really, when I say brought to you by ZipRecruiter, I kind of mean it because ZipRecruiter is where we go to hire. As you know, a podcast is not just me and Steve sitting around shooting the breeze. We got producers, we got editors, we got engineers, we got a lot of people involved. There are currently over 2.4 million podcasts in the world. If you include security now, 2.4 million and one. And every one of them is, you know, takes a team of people to put 'em together. That's a, a lot of jobs. At least 2.4 million jobs, right? Probably three or four times that needless to say, hiring the right people for those roles is important. It's very important to us.
Leo Laporte / Steve Gibson (00:06:08):
You know, as it is funny, until I owned a company, I didn't really understand this, but your company isn't you. Your company is the people who are in the company. That's what makes the company. It's not you, it's not your product, it's the people. And so, whether, you know, you have a, an opening in for us in continuity or an opening in engineering or opening in sales, you, the person you put in there is what makes your company succeed or conversely fail. You wanna hire the best possible person for that. When we had an opening in continuity, we posted on ZipRecruiter. That's Lisa's favorite hiring place. Fact's, the only one we use found Viva within. You know I think Viva's application came in with a couple of hours, hired her in a few days. And, you know, when you've got an opening and, and everybody's working overtime to fill that job, it's really nice to have somebody come in that's competent.
Leo Laporte / Steve Gibson (00:07:00):
That's great. We love her. We've hired all of our best people through ZipRecruiter. So whether you're hiring for a podcast or for your growing business of any kind, there's only one place that makes it easy. Ziprecruiter, you can try it for free right now. Zip recruiter.com/security. Now, they do a few things that are really great. I mean, one is you're posting everywhere, right? So the most people are gonna see it more than a hundred job sites and social networks and all this stuff. But the I, the thing I love, and Lisa says this is, you know, vital is they don't call her, they don't send her an email. It goes into the zip recruiter inbox. They preformat all the resumes, so it's easy to scan them. They give you a screening question so you can eliminate people who are just not right for the job.
Leo Laporte / Steve Gibson (00:07:47):
And then they do something really magical. They go out and look at all the resumes. They have more than a million on current resumes, and they find people who have the qualifications you are looking for and tell you about them. So you can invite them to apply. And I tell you something, one of the miracle things that happens when you invite somebody to apply, they wake up, they go, they respond, they show up, they do the interview. They're very flattered. It's a great way to fill those difficult to fill jobs. Four out of five employers who post on ZipRecruiter get a quality candidate within the first day, four outta five. And I would say our experience has almost always been within a few hours. So if you, if you love what we do here at twit and you wanna support us at security now you could try ZipRecruiter for free today.
Leo Laporte / Steve Gibson (00:08:34):
All you gotta do is go to that special address so that Steve gets credit ziprecruiter.com/security. Now it's really kind of important. That's how they're judging whether their advertising's working. And obviously you don't need to go there if you're not hiring. But the next time you wanna hire, please do us a favor, go to ziprecruiter.com/s e c u r i t y n o W, Security Now, ZipRecruiter. It is the smartest way to hire. We, we love our employees that we, we got through ZipRecruiter. Steve, I didn't have to go to ZipRecruiter to find you. I had had to have a zip drive to find you <laugh>. That's exactly right. Flick of death way back in 1999 or something like that. Oh, yeah. We didn't know about pictures of the week back then. We should have probably had those on the screensavers. These are good.
Leo Laporte / Steve Gibson (00:09:25):
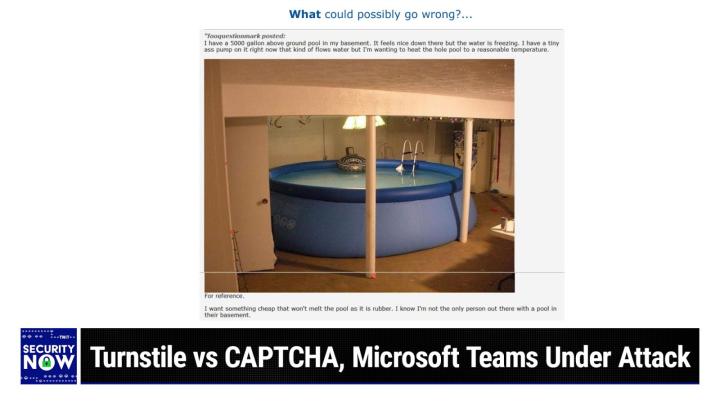
I like this. They were fun. Yeah. So this one is nothing, not really anything to do with security, but it's just so fun. So it, it falls under the broad banner, one of my favorite banners. What could, could possibly go wrong. I'd like to do it with you. Okay, We'll do it from now on <laugh>. So, so this, this posting says I have a 5,000 gallon above ground pool in my basement. It feels nice down there, but the water is freezing. I have a tiny ass pump on it right now that kind of flows water. But I'm wanting to heat the whole pool to a reasonable temperature. And then we see a picture of this mo monstrosity. So we're, look, we're looking at, you know, a basement with apparently a door open that is where the stairs leading down into the basement end and this huge pool that looks like it's about to burst.
Leo Laporte / Steve Gibson (00:10:37):
But I think that's probably the way they're supposed to look, because you're gonna have an awful lot of water pressure pushing the bottom skirt of the pool outwards. And it's being like kept from expanding endlessly by a, by a collar at the top. But boy, you know, this is 5,000 gallons of water that only has one that's like, it's trying to leave the pool as as hard as it can <laugh>. I have to go to Wolf from Alpha for this one. What is the water pressure? 5,000 gallons of water stored. And what would you say the area of that? Oh, maybe hundred square feet. Square feet. 5,000 square feet. Yeah. Maybe he'll be generous. Yeah. Anyway, so he says, he gives us the picture for marking it for reference. And he says, I want something cheap that won't melt the pool as it is rubber <laugh>, he says, And then I love this.
Leo Laporte / Steve Gibson (00:11:36):
I know I'm not the only person out there with a pool in their basement, and I'm thinking, ah, maybe you are <laugh>. Think you that pool for sure. Oh, I don't know. Anyway, this, this, according to Wolf from alpha 5,000 gallons of water stored in a hundred square foot, whatever, generates 5.06, six times 10 to the 10th square feet foot squared gallon past gallons. Don't know what any of that means. It's bad do, How about millimeters of mercury? That would be a pressure measurement. It might be kilogram meters to the fourth per second squared is another unit. <Laugh>? no, no. I'll have to convert that. I'll get back to you. Yeah. Elon Musk uses those measurements for his SpaceX program. Yeah. So yeah, I'm not a rocket scientist, I tell, Anyway just another fun one to share. I hope he found something to heat that pool without melting the rubber <laugh>.
Leo Laporte / Steve Gibson (00:12:42):
Yeah, well, we were thinking maybe a Bitcoin mining device down there, maybe helpful. Yeah. Do they have submersible Bitcoin miners? No. Oh, I know what you need. You need a sov <laugh> circulator in there. You could ve yourself maybe, maybe you could just heat the environment and of course, the water would eventually warm up to the ambient temperature. Well, for reason it's cold is it's sitting on bare dirt. Yeah, that's gonna get cold. Yeah, it looks creepy. <Laugh>. The creepiest would be just seeing him get in it. That's, that's, I hope the whole family knows how to swim. My god. Maybe needing that. Yes. Okay. So three weeks ago, they security firm Vector publish a report, which closely examined the way Microsoft Teams manages its users application authentication. The report is long and we don't need get it to get into the nitty gritty to understand what's going on.
Leo Laporte / Steve Gibson (00:13:45):
So I'm just gonna share two small pieces from their long report. In their overview, they explain, in August, 2022, the Vector project team identified a post exploitation opportunity allowing malicious actors with sufficient local or remote file system access to steal valid user credentials from Microsoft teams due to their plain text storage on disk. In other words, Microsoft teams, after you have authenticated yourself statically stores the authentication information, the tokens in the local file system there for everyone to access. So they said this plain text credential management has determined, sorry, was determined to impact all commercial and GCC desktop teams clients for Windows, Mac, and Linux. So common to all desktop platforms, the the big three, they said, While credential harvesting from memory from, you know, RAM is a common post exploitation step, we believe that lowering the bar necessary to harvest creds down to just simple read access to the file system expands opportunities for an adversary, simplifies their task, and is particularly interesting when stolen credentials offer an opportunity to retain user access unencumbered by otherwise pesky. One of my favorite words, multifactor authentication speed bumps with these tokens, attackers can assume the token holder's identity for any actions possible through the Microsoft Team's client, including using that token for accessing Microsoft Graph API functions from an attacker's system. Additionally, these tokens are equally valid with MFA enabled accounts, creating an allowance to bypass MFA checks during ongoing use. Microsoft is aware of this issue, but indicated it did not meet their bar for immediate servicing.
Leo Laporte / Steve Gibson (00:16:11):
Microsoft stores these credentials to create a seamless single sign on experience within the desktop application. However, the implementation of these security choices lowers the bar. Anyone who installs and uses the Microsoft Team's client in this state is storing the credentials needed to perform any action possible through the team's ui, even when teams is shut down. When these tokens are stolen, it enables attackers to modify SharePoint files, Outlook, mail and calendars, and teams chat files, attackers conter with legitimate communications within an organization by selectively destroying exfiltrating or engaging in targeted fishing attacks. The thing that truly frightens us, they said, is the proliferation of post MFA user tokens across an environment. It enables subsequent attacks that do not require additional special permissions or advanced malware to get away with major internal damage. With enough compromised machines, attackers can orchestrate communications was in an organization assuming full control of critical seats like a company's head of engineering, CEO or cfo.
Leo Laporte / Steve Gibson (00:17:32):
Attackers can convince users to perform tasks damaging to the organization. They say, How do you practice fish testing for this? Okay, so this is one of those head buried deeply in the sand issues which we've increasingly been encountering from Microsoft. The kindest way I think, to interpret this in Microsoft's favor is to suggest that Microsoft has now structured itself so that it's deliberately cut off from the outside. Someone who has no authority or power is running interference and responds to any offering made at the foot of the ivory tower by en enhancing the phrase. We're aware of this and it is not a security concern. And that's as far as any inquiry goes. If history is to repeat itself, especially now that this problem is well known, there will eventually be some egregious abuse of what is obviously a totally unnecessary and easily exploitable security weakness in teams.
Leo Laporte / Steve Gibson (00:18:44):
At that point, a holy, unnecessary emergency will ensue and teams will have this behavior by design changed. It's totally true that having persistent and static access to a previous successful authentication creates a standing vulnerability. Perhaps that's, you know, perhaps it's been done so that other components such as Skype and Outlook are able to share in this authentication as indeed they are. But in an alternative design, for example, they could share a common authentication service, which then relies upon encrypted authentication tokens, which would at least tie the tokens to the local machine's authentication service, perhaps its TPM and would make them much more tricky to abuse. Instead, Microsoft has chosen, for whatever reason, to simply store them in a well known location in every local machine's file system where they're accessible not only to all Microsoft components, but also to anyone else who might wish to abuse this implied trust.
Leo Laporte / Steve Gibson (00:20:00):
You remember, I mean, we talked about the same thing with Google and passwords and Chrome stored in the clear go. Google's response initially was, Well, somebody has physical access to your system, you're outta luck anyway. All bet all bets are out. And maybe that's Microsoft's response. Although remember Google did change that eventually <laugh>, right, Right. Yeah. So, okay. But Vera also had, I was gonna share two things. Vera also had another interesting piece of background to share. They gave this section the clever title Electron hyphen a security negative. It was clever of course, because we've all agreed that electrons carry a negative charge. Vector is suggesting that the electron development platform carries negative security. So here's what they explained about Microsoft Teams' use of the Electron application platform. They said Microsoft Teams is an electron based app. Electron works by creating a web application that runs through a customized browser.
Leo Laporte / Steve Gibson (00:21:05):
This is very convenient and makes development quick and easy. However, running a web browser within the context of an application requires traditional browser data like cookies, session strings and logs. This is where the root of this issue lies as Electron does not support standard browser controls like encryption and system protected file locations that are not supported by electron out of the box, but must be managed effectively to remain secure. Therefore, by default, the way Electron works incentivizes creating overly transparent applications. Since Electron obfuscates the complexities of creating the application, it is safe to assume that some developers may be unaware of the ramifications of their designs decisions. And it is common to hear application security researchers bemoan the use of this framework due to critical security oversights. So phrased another way, we might say that Microsoft team's choice to use the easy to use electron development model, which employs JavaScript, html, and CSS encourages rapid and easy application development by less experienced developers.
Leo Laporte / Steve Gibson (00:22:43):
From what Vector said, it also sounds as though electron's browser centric development environment encourages significant resistance. I'm sorry, the, the development environment encounters significant resistance when trying to do things like storing encrypted data into the file system. If that's true, then we have another case of Microsoft placing its short term needs in front of long term sec long term security and quality. So you know, hey, you know, let's use electro, we'll get, we'll get platform agnostic operation and everything will be great except, oops, there for whatever reason, they just decided as, I think exactly as you suggested, Leo, you know, they, they've said something to the equivalent of, Well, if someone's gonna access your lap, your local machine, you're in trouble anyway. So not our problem. Yeah. Until it is, and I don't think we're gonna have long to wait for this one, one in a posting last Thursday the 29th titled More Reliable Web Defense, Microsoft explained that they had scrapped an entirely rewritten their edge browsers built in smart screen library.
Leo Laporte / Steve Gibson (00:24:03):
They said starting in Microsoft Edge 1 0 3, which by the way is three versions ago, they said users can navigate the internet with more reliable web defense. Thanks to the updated Microsoft Defender Smart Screen Library that ships with Microsoft Edge on Windows, the updated smart screen library was completely rewritten to improve reliability, performance and cross-platform portability. These benefits are the foundation leading up to the security improvements that will increase our ability to protect users from emerging threats. And at the end, they noted that for enterprise customers who experience compatibility issues and need to revert to the legacy Microsoft Defender Smart Screen, we added a temporary policy called New Smart Screen Library enabled. They finished this policy will become obsolete in Microsoft Edge 1 0 8. Okay? So it's unclear why anyone would have compatibility issues unless something they were doing was tripping smart screen, false positive responses.
Leo Laporte / Steve Gibson (00:25:19):
But since we're currently at release 1 0 6 and the option to revert will only remain available in the next release 1 0 7, any enterprise having trouble with the rewrite, should address those problems quickly. Because unless Microsoft is convinced to delay the removal of that temporary policy, and we've seen that happen before, so that could happen again if enterprises say, Wait, wait, wait, we're not ready yet. You know, again, they all enterprises that have have needed this needed to disable the update should look into fixing that fast. And of course, I'm a huge proponent of wholesale rewrites of anything as we know. We haven't yet figured out how do evolved software gracefully. Part of the problem is that the various challenges software might face once released into the field, are often not fully appreciated by those who initially design and write it. So the process of watching an initial release interact with the world teaches its designers a lot. The first reaction is to patch over any shortfalls in the original design. But once those patches, patches have acquired patches, it's often the case that the best solution is to quit patching the patches and take everything that is now understood about the problem and start over. So bravo to Microsoft for deciding to, to do exactly that, to start over, will never know what precipitated that decision, but edges users will likely be the winners.
Leo Laporte / Steve Gibson (00:27:03):
Okay. I never pass up the opportunity to mention Ross, come, Nazo, <laugh> an opportunity <laugh>, because it's just too far. I love how you do it too. You like really give it and face. Yeah. Oh, and you know, I don't speak Russian, but part of this makes me wish I did because it sounds like some of it is fun. Anyway, an opportunity presented itself when Ross Cub Naor added the popular music streaming platform, SoundCloud to Russia's nationwide internet block list. And Leo, I have a link here in the story here at the bottom of page three, the show notes. It's worth clicking that link just to glaze over. As I said, I've, I've got the URL to Ross Cuban ZOS block list page. And thank goodness for the web's Western heritage, since at least the URL uses the Latin alphabet, I'm unable to make heads nor tails of anything on that block list page following the url.
Leo Laporte / Steve Gibson (00:28:09):
At least the numbers are Roman and the capture <laugh> you think I my capture, the one I got was, I don't think I could have entered it properly. Oh, okay. Well your yours is, you need to put some bicycles in there. Something That's right. Give me, gimme some stop. What do I do? You know, this is where Google Translate would be handy. All right. I'll figure it out. Anyway, I just, I just wanted to, to see that the Russian is a weird language. So, and I don't know why Ross k Naor is, you know, I guess maybe that's the English translation. Yes, Thank you. So the presumption is that the blockage was the result of SoundClouds hosting of podcasts, which we're discussing Russia's invasion of Ukraine. Of course, you can't have any of that in a repressive totalitarian regime. So no more SoundCloud, you know, add yourself to the lineup, we'll translate to the rescue.
Leo Laporte / Steve Gibson (00:29:07):
Ah, yo universal service. It says, Yeah. So now I, I can, now I can now they've unlocked it. Have I unlocked it? Let's unlock it. I wonder why specify the domain? Why do you think there's a capture on their I don't want you to use robots, right? You, yeah, I can obtain the measures taken to restrict access to sites. So what was, what was the site that they inadvertently sound soundcloud.com, I assume it's dot com soundcloud.com. Yes, It is forbidden. You are forbidden. Oh, says, no, no, no, no. You may not ever look at this secret. Well, it's gonna happen. What happens if you put noodles.com in? Is that forbidden too? I think it's, it's more has, I don't know what it has to do with Maybe you click the button and it just says forbidden. Oh, you gotta do another capture. Yeah.
Leo Laporte / Steve Gibson (00:30:00):
I think for everyone, noodles.com <laugh>. Yeah. Okay. And now I have to fill in capture 5 3 7 8, 6 3. Very secret. Okay. <laugh>, Forbidden <laugh>. Ah, well, there you go. Noodles.Com is forbidden Noodles. Not you, you cannot have any noodles in Russia. Oh, he's forbidden. Oh, <laugh> Ross come down are forbidden. Okay. So Exchange server, once again under attack, a Vietnamese group named g G TSC discovered an active in the Wild Exchange server zero day. And let me just preface all of this by the, by saying this is very bad. I mean, this is the <laugh>, the, Okay. Here's what they said at the beginning of August, 2022, while doing security monitoring and incident response services, G TSC soc, that's their Security Operations center team, discovered that a critical infrastructure was being attacked specifically to their Microsoft Exchange application. During the investigation, BTS c Blue team experts determining that the attack utilized.
Leo Laporte / Steve Gibson (00:31:23):
And, you know, this is a translation from Vietnamese, so bear with, but it's pretty good determining that the attack utilized an unpublished exchange server vulnerability, I e as zero day vulnerability immediately came up with a temporary containment plan. At the same time, red team experts started researching and debugging exchange Decom compiled code to find the vulnerability and exploit code. Thanks to experience finding the previous one day exchange exploit, the red team has a great understanding of exchanges, code flows, and processing mechanisms. Therefore, research time was reduced and the vulnerability was uncovered quickly. The vulnerability turns out to be so critical that it allows the attacker to do a remote code execution on the compromised system. G TSC submitted the vulnerability to the Zero Day initiative, you know, Zdi right away to work with Microsoft so that a patch could be prepared as soon as possible.
Leo Laporte / Steve Gibson (00:32:34):
Zdi verified and acknowledged two bugs whose CVSs scores are 8.8 and 6.3 respectively, again, the beginning of August, 2022. We are now two months downstream, right? August of September we're in October. This has not actually been fixed yet since this was reported. G TSC said that they've encountered other customers who they're also charged with monitoring whose infrastructures they're keeping an eye on, also experiencing a similar trouble. And after careful testing, they confirmed that those other systems were being attacked using the same zero day vulnerability to help the Exchange Server community temporarily stop the attack until an official patch is available from Microsoft. They published their coverage of their findings while responsibly excluding the information needed to recreate the attack. The exploits caused cause Exchange Server to download a malicious dl whose code is then injected into the always present and busy service host dot XE process in Windows.
Leo Laporte / Steve Gibson (00:33:54):
Once that's done, the DLL is started and it phones home to the machine at the IP address. 1 37 1 8 4 6 7 3. I imagine that changes from instance to instance of, you know, DLL instance of dll. A simple and effective RC four Cipher is used with a key chosen at run time to then s to then encrypt the communications back to the command and control server. The G TSC folks also explained, they said, while providing SOC service to a customer, GTS e Blue team detected exploit requests in IIS logs with the same format as the proxy shell vulnerability. And in fact, this is now I just saw this, I, I wanted to check before, just before the podcast to make sure that I'd hadn't missed any updates like Microsoft had just patched or, or, or just pushed an update. But there's still nothing from Microsoft. This is being con this is being called informally proxy, not Shell vulnerability instead of the proxy shell vulnerability, cuz it is definitely a variation on that theme.
Leo Laporte / Steve Gibson (00:35:12):
In the show notes for what it's worth, I I share an example of the, the URL that is, that is in there. And they said, checking other logs, we saw that the attacker can execute commands on the attacked system. The version number of these exchange servers showed that they were already running with the latest update. So an exploitation using the actual proxy shell vulnerability was impossible. Thus, the Blue team analysts confirmed that this was a new zero day remote code execution vulnerability under active exploitation. So I've got links in the show notes. There are indications of compromise published and available if anyone wants to make sure their exchange server instance hasn't already been made a victim, and there are mitigation steps that can be taken. Last Thursday, Microsoft publicly acknowledged the trouble with their own posting titled Customer Guidance for reported zero day vulnerabilities in Microsoft Exchange Server.
Leo Laporte / Steve Gibson (00:36:19):
I've got a link in the show notes. The trouble is the mitigation, which was first proposed by the GTS E people, appears to be what Microsoft has copied and is echoing. It recommends basically adding a pattern matching rewrite rule to the IIS web server, which hosts exchange. But in an update from GTS C just yesterday, October 3rd, they noted and they, they said, quote, after receiving information from ja whose Twitter handle is test a null, they said, We noticed that the Red Xs used in the rewrite rule could be bypassed, and they then link to a YouTube demo. So I read that to mean that Microsoft's official proposed mitigation can be bypassed. And in fact, there is an article just posted by, from bleeping computer confirming that Microsoft's mitigation of this vol, the zero day remote com remote code execution vulnerability for exchange server can be bypassed.
Leo Laporte / Steve Gibson (00:37:31):
So things are really not good. Let's hope that Microsoft gets a permanent fix for this problem published soon, and that all exchange server users jump on getting their systems updated. I don't know of anything else that we could do in the meantime, except I can take a sip of water, Leo, since my throat's a little soft. That's a good thing to do. In the meantime, <laugh> Security now is brought to you by ITProTV. And I, while you are hydrating, we'll talk about a great way to get those security certs. You need to get a job in technology or to get additional skills to keep and improve your job in technology or maybe even more importantly to train your entire IT team. You hear this show and you go, yikes. It's, it's pretty bad out there, isn't it?
Leo Laporte / Steve Gibson (00:38:26):
And I hope, I hope if you're a company with an IT department that they pay attention to security. But are they up to date? Do they have the latest search? Do they have have the latest knowledge? That's where ITProTV can come in. We talk all the time about what a great place to go IT Pro TV is for individuals looking to get into it or to, you know, upskill and so forth. But you need to upskill your team too. And ITProTV is a benefit. They will love it. It, it's great for them and it's great for you. It's a win all around. They'll love it because it pro TV hires experts in the field. People who are working in the field really know their stuff. But it's very important also have a passion for it. They're not like, Oh, here's here, we hear they are really into this stuff and their passion, their excitement communicates and gets you excited about it.
Leo Laporte / Steve Gibson (00:39:15):
That's why it pro TV's lessons are so engaging. It's why more than 80% of people who start a video on IT PRO tv actually finish it. It's why your IT team will be thrilled when you say to them, Hey, we got a learning platform. We've got some ideas of things we want you to learn. Here's IT pro tv. They're gonna love it. It pro TV has seven studios. They're open all day, Monday through Friday, 8:00 AM to 6:00 PM recording new content. So you're always getting the latest content of everything you need your team to know. Every vendor, every skill, every cert, all in one place. Microsoft IT training, Cisco training, Linux training, Apple training, of course security cloud and so much more, more than 5,800 hours, up to date hours worth of training from technical skills to compliance. There's even soft skills in there.
Leo Laporte / Steve Gibson (00:40:09):
You can do so much with your ITProTV business plan too. Their dashboard is great. It lets you track results. Of course, you need to do that for the C suite to prove that your spend is worth it, right? They give you great beautiful visual reports that will show metrics like logins, viewing time tracks completed so forth. You can manage all your seats there. Assign and unassigned team members, even subsets of teams. So you can say you, you need to take, in fact, you can even do it a single video on a course. You need to take episode 13 of securing your workstation so that you can go down the hall and help these people get their systems set up, that kind of thing. You can easily manage who's getting what kind of training. Keep an eye on their progress, monitor their assignments, monitor usage of the platform so you can prove that you're getting the ROI right?
Leo Laporte / Steve Gibson (00:40:58):
And of course it pro TV has fabulous individual plans too. It is the place to learn these skills that are so vital to any modern enterprise. Give your team the IT development platform. They need to level up their skills while enjoying the journey. That's what they're famous for. Just go right now to ITProTV slash security now and find out more. Really recommend it. If you're an individual, go there as well. It pro.tv/security. Now we think of so much for supporting Steve's work. I mean, I think a lot of of companies, I know a lot of companies require, you know, this show as as as required watching cuz that's how you keep up on what's going on. It's good to have those certs though, and those, the basic skills as well. In fact, make it easier for you to understand whatever the hell Steve's talking about.
Leo Laporte / Steve Gibson (00:41:49):
<Laugh>, I should probably go back to school too. No, we also know that a bunch of professors tell their students That's right. Don't That's right. Watch the podcast. Yeah. In fact, we have a number of companies that bought Club twi subscriptions just to give them ad free versions of these shows. So, nice. Yeah, it's really great. On we go. So last Wednesday, our friends at CloudFlare posted the formal announcement of the availability of some of the work they've been focused upon this past year. This has been some time in coming. They've been working on it and it's now available. Their posting was quote, announcing turn style, a user friendly privacy preserving alternative co to capture. So our longtime listers know that through the years we first introduced the abbreviation capture standing for completely automated public touring test to tell computers and humans apart.
Leo Laporte / Steve Gibson (00:42:46):
I think it was Carnegie Mellon, right? The first capture yeah. Right. And it, and it was kind of clever. And now Google does it and it's so clever. I'm so tired of telling Google That's a bike. That's not a bike. Oh, I know. And clearly we're training their Waymo division on how to drive and it's, it, I'm often sure that it's correct and Google says no. Terrible. Here's some, here's some boats or, you know, whatever. It's like. Yeah. So, and as you said before, by the way, ineffective Yes. If you're really a bad guy, you know how to defeat these captures easily. Well also, I'm sitting here as a normal user doing web-based research with, with an IP that hasn't changed in several years. Yeah. They know who you are. And Google is supposed to know. Yes, exactly. Yet. And, and, and so the idea is that it, it's supposed to not bother you.
Leo Laporte / Steve Gibson (00:43:49):
Right? Unless it's not sure about whether or not, and it's like, what are you doing? Am I your free image analyzer? Yes, that's exactly. It's so obvious. Sorry. Yeah. Sorry. So thank you. So we've followed the evolution and use of captures. So in keeping with our capture covering history, here's what CloudFlare has done, and it looks like to be a hundred percent good news. They said today we're announcing the open beta of turn style. An invisible alternative to capture anyone anywhere on the internet who wants to replace capture on their site will be able to call a simple API without having to be a CloudFlare customer or sending traffic through the CloudFlare Global Network. Sign up here for free and the url, it's easy. Www.Cloudflare.Com/Ip/Turn style. T u r n s t i l e. That's it. You fill out a form and in order to create a a, an identity with them and you, you make three modifications, which I'll explain a second.
Leo Laporte / Steve Gibson (00:45:04):
They said there's no point in rehashing the fact that capture provides a terrible user experience. Yes. <laugh>, It's been discussed in detail before on this blog and countless times elsewhere, the creator of the capture has even publicly lamented that he quote unwittingly created a system that was frittering away in ten second increments. Millions of hours of a most precious resource. Yes. Human brain cycles. Yes. He said, We hate it. You hate it. Everyone hates it. Today we're giving everyone a better option. And of course, this comes from our forensic CloudFlare. Yeah. They said, Turn style is our smart capture alternative. It automatically chooses from a rotating suite of non-intrusive browser challenges based on telemetry and client behavior exhibited during a session. He, they said, we talked in an earlier post about how we've used our managed challenge system to reduce our use of capture by 91%.
Leo Laporte / Steve Gibson (00:46:22):
Now anyone can take advantage of this same technology to stop using Capture on their own site. They then go on to explain that it's not only captures miserable user experience, that is the problem. They said, while having to solve a capture is a frustrating user experience, there's also a potential hidden trade off a web a website must make when using Capture. If you are a small site using Capture today, you essentially have one option, an 800 pound gorilla with 98% of the capture market share. This tool is free to use, but in fact it has a privacy cost. You have to give your data to an ad sales company according to security researchers. One of the signals that Google uses to decide if you are malicious is whether you have a Google cookie in your browser. If you have this cookie, Google will give you a higher score.
Leo Laporte / Steve Gibson (00:47:26):
Google says they don't use this information for ad targeting, but at the end of the day, Google is an ad sales company. Meanwhile, at CloudFlare, we make money when customers choose us to protect their websites and make their services run better. It's a simple direct relationship that perfectly aligns our incentives. In June, we announced an effort with Apple to use private access tokens. Visitors using operating systems that support these tokens, including the upcoming versions of Mac o s or iOS, can now prove their human without completing a capture or giving up personal data. By collaborating with third parties like device manufacturers who already have the data that would help us validate a device, we are able to abstract portions of the validation process and confirm data without actually collecting, touching, or storing that data ourselves. Rather than interrogating a device directly, we ask the device vendor to do it for us.
Leo Laporte / Steve Gibson (00:48:38):
Private access tokens are built directly into turn style. While turn style has to look at some session data like headers, user agent and browser characteristics to validate users without challenging them. Private access tokens allows us to minimize data collection by asking Apple to validate the device for us. In addition, turn style never looks for cookies like a login cookie or uses cookies to collect or store information of any kind. Cloudflare has a long track record of investing in user privacy, which we will continue with turn style. They then explain a bit more about what's under the hood saying to improve, to improve the internet for everyone. We decided to open up the technology that powers are managed challenge to everyone in beta as a standalone product called Turn Style. Rather than try to unilaterally deprecate and replace capture with a single alternative. We built a platform to test many alternatives and rotate new challenges in and out as they become more or less effective.
Leo Laporte / Steve Gibson (00:49:50):
In other words, what they're really also saying yes is that when, when the bot farms figure it out, start working it out. Right? They're just gonna change the, the, the, the rules and no users will have to have any effect. What are the odds are gonna end up having to identify bicycles after a while? Oh Lord. Let's hope not. I hope not. At Le at least we'll know that if that has to happen, it's, it had to happen. Right? It's not something that, you know, convenient for. I mean, Yeah. Yes. Again, I, I have, I have no explanation for the fact that I'm having to click on, on, on you know, parking meters in order to tell people you used to every once in a while would say, Oh yeah, yeah, you just say I'm not a robot. And then say, Of course you're not.
Leo Laporte / Steve Gibson (00:50:36):
We know that, but That'ss gone away now, right? Apparently I haven't seen that for a while. Mm-Hmm. Mm-Hmm. So they say, First we run a series of small non interactive JavaScript challenges, gathering more signals about the visitor browser environment. Those challenges include proof of work, proof of space, probing for web APIs and various other challenges for detecting browser quirks and human behavior. As a result, we can fine tune the difficulty of the challenge to the specific request. Turn style also includes machine learning models that detect common features of end visitors who were able to pass a challenge before. The computational hardness of those initial challenges may vary by visitor, but is targeted to run fast. You can take advantage of turn style and stop bothering your visitors with a capture even without being on the cloud flare network. While we make it as easy as possible to use our network, we don't want this to be a barrier to improving privacy and user experience.
Leo Laporte / Steve Gibson (00:51:50):
To switch from a capture service, all you need to do is, and they have three things. One, create a cloud flare account. Navigate to the turn style tab on the navigation bar and get a site key and secret key two, copy our JavaScript from the dashboard and paste over your old captured JavaScript three, update the server side integration by replacing the old site verify URL with ours. They said there's more detail on the process below, including options you can configure. But that's really it. We are excited about the simplicity of making a change. Yeah. Make it easy. But remember the people who are using that crappy Google capture are doing it for one reason. They're lazy as hell. And I bet you, you watch it. No, nobody, no big effect. Yeah, because that's why they're using this crappy one. They don't care. Well tho those of us who care will will do You have captures on your same?
Leo Laporte / Steve Gibson (00:52:53):
No. You see, I just <laugh>. I point Exactly. Neither do I. Nope. No. So anyway oh, I did, I also wonder for this for, for our listeners, anyone who wants to go to that sign up page, it's the shortcut of the week. So it's GRC se slash 8 91. I also wonder, get you directly to sign that it ad blockers certainly no script would kill it. I wonder, you know, if it's seen as intrusive by some ad blockers, cuz they are, you know, running some stuff in the background to see who you are. Right, Right. Although I would imagine Google is doing that too, right? Oh, Google's worse, I think is a lot of CloudFlare and points out that if you don't, if you're not logged into Google, you don't have a Google cookie on your page, they assume you're, you're up to no good <laugh>.
Leo Laporte / Steve Gibson (00:53:47):
Yeah. You can't be, you can't be a nice person. Can't be human. Yeah. You're not, you're not logged into Google. Yeah, that's right. Okay, so my last piece is really cool. I, this is the, this is what I posted to my Twitter feed that so distracted me that I forgot to post about today's podcast. Google has put together a marvelously engaging series of six 15 to 19 minute videos under the banner hacking Google. It's a world class production such as you might expect from a company with Google's resources, which of course we're all providing to them. And yes, of course these are ultimately promotional, but that doesn't dissuade me from recommending them without reservation because they are gorgeous and they will be, I think of tremendous interest to this podcast listeners. I've already, since this morning received a bunch of feedback and I've got more loves and retweets on that tweet that I normally get on my weekly announcements of the, of the podcast show notes.
Leo Laporte / Steve Gibson (00:54:57):
So I first still, this is kind of funny. I stumbled onto the second one in the series not realizing that it was number two since it was numbered 0 0 1. Of course. Ugh, They I love it. I know zero based numbering, God bless you, Google. They started numbering from zero as I've always wished we had. Yes, we have one more, one more episode. Foresight to do that doesn't allow us to squeak out. One last one when 9 99 wraps over my, my my three digits back to zero. In any event, I've only had the time so far before today's podcast to watch that second one all the way through. But based upon the one I watched, I mean, look at those graphics, Leo, they've just got stunning graphics. It's, it's really cool. It's network news, production quality, I mean just very high quality. Better than network news really.
Leo Laporte / Steve Gibson (00:55:50):
It is really better than documentary production quality I've seen. Yeah, yeah. Well they got the money, so there Yes, exactly. They got the money. There are six videos. Operation Aurora Threat Analysis Group. That's the one I saw which talks about the, the, the origin and status of Google's tag team. And we're always talking about them cuz on those podcasts cuz they're doing such great work. Nu the third one is Detection and response. The fourth one, Red team, the the fifth one, Bug Hunters. And then the last one is Project Zero. Again, I've not, I've only had a chance to watch the, the tag team one and it was really cool. So anyway, I commend our listeners to that. The videos are collected in, there's a playlist on YouTube. Yeah. Yes. Yeah. They are collected into a YouTube playlist for easy access. A I have a link to it in in today's show notes which will take you directly there also.
Leo Laporte / Steve Gibson (00:56:49):
And and it's weird too because when I tried to create my own shortcut to it, it wouldn't, the redirect wouldn't go to the playlist. Yeah. It insisted on starting at the first video. But if you google the phrase hacking Google playlist, then a few links down from the top, you'll find that's the actual playlist page, which I do have a link to in the show notes. Or if you want to use a GRC shortcut, grc.sc/hacking Google that will bounce you to the first one. And then they all link successively first one, which is episode zero zero. Because yes, actually Google should do what we do. We start all our shows now with episode zero, but that's the trailer. So ah, see and if Google had done that, they have a trailer, but if they just made their trailer episode zero, you would not have been, you know, fooled.
Leo Laporte / Steve Gibson (00:57:40):
Yes, yes. That's a very good point. There's a programming language that I really like, but there's one thing I hate about it. It's called Julia and it uses one index to raise and it's like, but they just say this is how people count. How dumb is that <laugh>? My my point. Exactly. I mean, you're having to do this ridiculous math every single time to subtract one <laugh> or add one. Yeah, well, their point is that normal people have to do the ridiculous math to do zero based arrest. Oh my God. Well, and one of the most common problems are the off by one. Exactly. Exactly. I mean, it's, I spend more time thinking, Okay, do I mean greater than or greater than equal? Equal or equal to, I always do, You know, I always cover my rear by doing greater than or equal to just in case.
Leo Laporte / Steve Gibson (00:58:34):
Yep. Yeah. It's funny too, I do the same thing when I'm ending a loop for a counter. I don't say end it when this is equal to something <affirmative>. Mm-Hmm. <Affirmative>. It's just superstitious. But I, I say when is equal or greater because you know why not, Even though it's demonstrably the case, it will hit that number <laugh>, it's skip and, and if it doesn't, then you've got bigger problems. But I do it exactly the same thing. It's never equal. It's always great. Equal seems too precise <laugh>. Yeah. You're, you're, you're, you're trusting the computer. And again, it's like, well, I, it's hard to justify, but it just, it seems better. They also have in fix arithmetic functions. And while I know everybody knows in fix it just you know, once you start using, who is this Julia thing aimed at a data scientist, It's actually a really nice language.
Leo Laporte / Steve Gibson (00:59:24):
Very, very nice. But I do have to question that choice. So they've dumbed it down in order, they dumbed it down just like Python is a little dumbed down too, because they want Right. But even pythons in order to make it, in order to make it more domain specific. Yeah. Or just more accessible. But I think just get used to zero index raise and that's then you're done with it. Wow. And you're done with Yeah, that was like Pascal go, which, which starts strings with the string length. Yeah. And then one is the first letter That's dumb two. No, Yeah. Nu terminated strings. It's the only way to go that is a win. And that there, the beauty, all of my, all of my code is not terminated. It's just, But you, because you're coding also an assembly and it just, and that's where this all comes from.
Leo Laporte / Steve Gibson (01:00:07):
Yes. And in fact, that's the problem with a, with a one based right index, you have to subtract you. I'm always thinking in terms of the offset from the pointer. Right, because your pointer points to the first thing in the array and it's zero in. Yeah. They're really going against God's will on this, I think. So. I don't, Yeah, this is God or John v Neman, one or the other. It's gonna be very unhappy. Sometimes they, they seem the same. So we had a listener James who said, Hi Steve as a 2019 Honda Accord owner, I followed your detailed explanation of the key FOB hacking saga with a vested interest. Yeah. I don't leave anything of value in the car specifically because you made it clear anyone can get in and even if they can't steal the car without the fob, they can take anything at any time.
Leo Laporte / Steve Gibson (01:01:03):
Unfortunately, last week I was their next victim. Fortunately for me, they didn't get what they were after. As I don't keep my lu nut lock keys in the car anymore since the rims are quite worthy of theft. They did rifle through everything he has in all caps and got a bag from the trunk that I liked, but I didn't even notice the 20, but I didn't even notice the $20 in the glove box under the empty lu nut lock key bag. Although the care and fob he says, although the car, Oh no, the car and FOB were confused, he says, My FOB would unlock but not lock the doors. I was able to get the car to the dealer. So he's saying the, the attack confused the fob car relationship as we would expect it to. He says, I was able to get the car to the dealer and by the time I got there, the FOB had somehow synced.
Leo Laporte / Steve Gibson (01:02:02):
So it was functioning normally. I explained the experience and my full knowledge that this is a Honda specific technical flaw that I, that I know the dealer cannot fix, but could they at least wipe and reset my system so that the currently stolen code wouldn't work anymore for this set of thieves. He said, I was told by the service department manager Bill, that the reset costs $220 and I would have to pay for it. I declined. So I thought that was an interesting bit of feedback from the field regarding an attack that we covered in some length enough for James to know exactly what was going on. John said, Hi, Steve. I've noticed that there's been a lot of discussion around fishing protection on some of the most recent episodes of Security Now and how Squirrel, Fido, et cetera, will address or resolve it.
Leo Laporte / Steve Gibson (01:02:58):
One thing you haven't mentioned recently though, is that just using a password manager, such as Last Pass or Bit Warden, et cetera, will also provide a degree of protection as the auto fill will fail as a fake URL will not match the one linked to the stored credentials. Longtime secure, now listener and thanks from Brisbane, John and I've, I've put that in here just because I wanted to amplify it. I, he's absolutely right. I have forgot to mention in our recent discussion of this that it is one of the benefits of a password manager, which takes what's in the url. Absolutely. Literally. And so if you're expecting an auto log on and you don't get it you know, it's protected you from a fishing scheme that was using a lookalike URL or something similarly confusing. Eric Sidel said, Hi, Steve. I've been listening to episode 8 89 and wanted to mention, I've also been using security now since I got my CI S S P for CPEs to maintain the cert.
Leo Laporte / Steve Gibson (01:04:07):
There's a bunch of acronyms for you. He says, I've never had any issue either. I've never had any issue either when submitting them with isc. Thanks again for a great resource for that. And I just wanted to say that as, as a consequence, am I talking about that in 8 89? Many of our listeners said, Yeah, that's what I do too. So it's clear that that works for people. Manuel said, or asked, he said, I have a question that I'm hoping you might answer. I recently installed backup software ease us, ease us to do backup, and later realized that it's Chinese software. Now I'm wondering if I just compromised my computer and my whole home network. Oh, Lord. Do you have any advice on this? I, I, Ali, hold on. Do you have any advice on this way of thinking? Should I reinstall my windows?
Leo Laporte / Steve Gibson (01:05:03):
Oh, look for a way, look for a way to reinstall the bio slash U efi. Buy a new phone, a new tv. Yeah. Throw it all out. A new, a new router. Oh, a new everything. Where should I I draw the line. Oh, he's joking. Thank God. No, I I, he said he just started listening to the podcast. So but, but this is, I mean, it's worth, it's worth discussing. Yes. Because, you know, Casper Ski is now being looked at very unfavorably because they of course are a Russian cybersecurity firm. We know Casper Ski well. There's, from everything I've seen zero evidence to, to suspect them of any bad behavior. But it's just creepy that they're Russian and you know, and we know that companies in Russia don't have necessarily full autonomy Right. Over their own actions. Yeah. And, and there's, you know, that's an easy thing to do because there are lots of other choices for any viruses that aren't from Russia.
Leo Laporte / Steve Gibson (01:06:08):
Right. I guess you could say the same for to do backup. I recommend it ease us all the time on the radio show cuz they offer good quality products. In many cases for free to do has a free version that do, does a good job. Maybe that's why it's free. And, and, and it happens. That my favorite remote access software, I've talked about it often, remote utilities. It's also from a software publisher in Russia. Yeah. And it's like, well it's, I guess being forewarned is useful, but I, I, I mean, and it is tough where we've got like this saber rattling going on increasingly between the US and China with, you know, it, with, with tensions escalating at some point, you know, and apparently like teams on both sides poking around aggressively inside of each other's networks. I got a email from somebody today saying, I will never buy an iPhone cuz they're made in China.
Leo Laporte / Steve Gibson (01:07:08):
I'm only buying Samsung cuz it's made in South Korea. And I guess, you know, I can't disagree with that. There is zero evidence that any, just because something's made in China that is somehow dangerous. I guess maybe software would be a little bit easier, but if they were exfiltrating stuff from your backup, I think <laugh>, I think even if you didn't notice, somebody would notice that. Well, and we've got motherboards all being made now in China, everything components and Yes. And there you don't really have that much of a choice. I mean, good luck finding one anything a TV or route a phone that's not made in China. You know, and we, we've also talked about the, the, the difficulty of even like visually inspecting a motherboard. Right. You know, look at all those little bitty chips. Right. What are they? No one knows what the Yeah, exactly.
Leo Laporte / Steve Gibson (01:07:56):
Right. Yeah. No, it's, it's a, I mean, it's a concern. Yeah. I mean, you can be too paranoid. I also Yeah. Don't want people to be xenophobic. You, you can't, don't, don't conflate the Chinese Communist party. No. Which is yeah, absolutely awful with the people of China and xenophobia was exactly the word that I've had on the tip of my tongue through this. Yeah. Because it's just, you know, it's not, it's not the right way to be. So Christian Sanchez said, Hi, Steve, wondering if you have any thoughts on this. Washington Post articles assertion that public wifi is safe. And he linked to it. He said, I admit, I clicked on it, expecting to laugh at thoughtless misinformation. But the discussion in the comments turned me around, Is the near ubiquity of HTTPS enough to declare public wifi safe? What about man in the middle hijacking dns, longtime listener and big fan of the show.
Leo Laporte / Steve Gibson (01:08:51):
Keep up the good works. Sincerely Christian. And I read the article and it was written by somebody who really knows what they're talking about. And they, they had the position that I do, which is, yes, there has been such a transformation since we were first talking about fire sheep back then. Mm-Hmm. <Affirmative>, where, where, you know, open access wifi was a catastrophe because that was a fire sheep remember was a plug, a Firefox plugin where you were able to, Oh, in fact, I, I'm talking on my own lines. I've got some piece of the Washington Post here that I wanted to share. So the, the Washington Post wrote, and I've, I've edited a bit to bring it up to the level of our listeners. They say, You probably don't need to worry about public wifi anymore. Here's what a creep in a coffee shop could actually learn about you.
Leo Laporte / Steve Gibson (01:09:43):
That was their headline from uncovered webcams to reused passwords. It's thought to keep track, I'm sorry. It's tough to keep track of how much risk our everyday digital activities actually pose. For example, take wifi networks in airports and coffee shops. They're part of life for anyone who travels or works remotely. They also have a reputation as cyber security risks. Do they still deserve it to see what potential hackers could see on a shared network? We invited professionals from cybersecurity company avast to compromise my home network with all, all with my consent. We logged onto the same network at the same time, just like we would at a coffee shop to see how much data a bad actor with a few free tools could learn about an unassuming wifi user. What we found or didn't find might be a relief for the coffee shop crowd. After a few minutes clicking around my finance work streaming and social media accounts, Avast team could see the site side visited, though not what I'd done there the time of day.
Leo Laporte / Steve Gibson (01:10:59):
And the specific device I used in this case, a MacBook Pro. It's not nothing, but it wouldn't do hackers much good if they were looking to rip me off. He says Chester wi wow. With Nuki, a principal research scientist at security company sofas said that it's also also relatively reckless for hackers to sit around messing with public networks, quoting him that type of data isn't only low yield, it's high risk. If I can fish your password from my chair in Moldova and have zero risk of going to jail, why would I get on an airplane? That's a good point to go to, to go to your local Starbucks. Yeah, that's a good point. Yeah. So our, our author said in the Internet's earlier days, the vast majority of web traffic was unencrypted, meaning anyone savvy enough to Eves drop on a network could see everything you type at a website.
Leo Laporte / Steve Gibson (01:12:02):
And that's where I interjected our longtime listeners will all remember fire sheep. He said by 2017, the balance had shifted with more than half of all web traffic using the encrypted HTTPS protocol. According to data pulled from Mozilla today, few legitimate sites remain unencrypted with more than 90% of websites loaded in the United States, obscured from prying eyes according to Mozilla's data. This means even if someone using a public network to even this means even if someone, I guess, oh, you yeah. Used a public network to spy on you, what they discover probably wouldn't be very valuable. Anyway, the article finishes Focus your energies on cybersecurity chores within your control, such as setting strong passwords, saying yes to software updates and learning the signs of a scam. And don't sweat the public wifi too hard if a site link or app seems sketchy, steer clear. Which of course is always great advice.
Leo Laporte / Steve Gibson (01:13:11):
So anyway, great question from a listener and thank you for the pointer to the Washington Post article. I I agree. You know somebody really concerned could use DNS over tls, right? So that even the, the places they're going, even their DNS queries would not be visible in the clear cuz DNS by default is still not yet encrypted. I don't see that changing. That would be it. That would be difficult to change, but, but we could certainly in as individuals cause our DNS to go through as secure TLS tunnel and then nothing about what we're doing would be accessible someday. I'd love your opinion on a thing called the wifi pineapple. Are you aware of this? Yeah, yeah. It's a pen. They call it a pen testing device. Although you could easily use it in a coffee shop to attack wifi users.
Leo Laporte / Steve Gibson (01:14:07):
I, Yeah, I think the, the, the, the, the, the power there would be if somebody were using a laptop where the laptop had inbound security problems. Yeah. Like, you know, file Windows file and printer sharing where it was set up to be online. Sure. Then you'd know. So it's, so, but one of the things there you can do with this is mimic a preferred network and then have that device log into you. That would be bad because most Windows users have their, their Windows firewall set up to be transparent on their local network. Right. So if it were, if if someone knew who you were and and could masquerade as your local network, then your, your machine would log into it automatically and it would ha it would have access inbound through your firewall in a way that the, there's somebody inside your computer right now.
Leo Laporte / Steve Gibson (01:15:04):
There's somebody on your network. On your network. Yeah. One of the ways that you might use this in this area anyway, probably yours as well Comcast is, is the dominant cable provider. They put in these Xfinity routers as you know, that open access points, public access points, and I would bet a a majority of people who are on the road in areas like ours make sure that their phone in their laptop, if it sees Xfinity network, will join in. So the first thing I would do if I had a wifi pineapple is proof and xfinity.com network just to see, and you just, Im immediately get connection. Yeah. And you could pass if you wanted to pass the internet through it, but <laugh>, but you'd still be on their network. So I feel like if you are really a determined attacker, there are still things you can do.
Leo Laporte / Steve Gibson (01:15:52):
Yes. Yeah. Yeah. And so the only solution to that would be to be choosing the proper vpn. Remember that you need a VPN that VPNs everything, right? Your computer does not just, for example, your web traffic, you want it to completely encapsulate your network. That would, that would protect you from everything we've just been talking about. Yeah. Because it would be linking through all of your local infrastructure connection back to a VPN server somewhere, either back to your home or to, you know, a good reputable commercial provider. You use the phrase, and I I I think it's a very apt to this for this is it's your, what's your threat model. So if you're, if you're working for the nsa, your threat model is very different than than Leo going down to the Starbucks. And so you have to know what your threat model is in an act appropriately.
Leo Laporte / Steve Gibson (01:16:44):
And so most people pro you know, this post article's probably accurate, don't have to do anything. I think that's true. Yeah. Sean Nelson, he said, Hey Steve, I've been looking for a product like this for years and I finally found it. I think it might interest you too. It's an SD card with encryption built in. Oh, this, this allows you to take pictures without, or videos without risking that the contents will be viewed or confiscated by anyone else. From what I can tell, it works by storing a master key set by the user. And I'm gonna explain in detail how it works in a second. But he said, then each time the card powers on, it creates in stores a new symmetric session key, which gets processed through the master key for safe keeping. Any new files get encrypted using that new symmetric master key. When the device is powered off, the key is removed from volatile memory and the only persistent copy of the key is encrypted with the master key.
Leo Laporte / Steve Gibson (01:17:51):
If you take a picture and power off the camera, next time it powers on, no pictures are visible. If you can take new pic Oh, it says, he says you can take new pictures, but they too are unreadable after you turn off the camera. However, when you attach the SD card to a computer and supply it with the master key, it is able to download the pictures along with each associated session key and unlock everything on the camera. I've been looking for this for my dash cam for a long time. Given the state of the world, many others might be looking for something similar. So I think this is very cool and clever. I've got the link to it at the bottom of this article. It's another example of the principle I often observe, which is that the generic and now well proven tools we already have can be combined in an endless number of ways from what Sean described.
Leo Laporte / Steve Gibson (01:18:53):
Here's how I would design this device, and it's likely what its maker Swiss bit has done during setup on a pc, a public key pair would be created and the SD card will be provided with the public key and that's all. Then whenever the SD card is powered up, an internal high entropy generator would synthesize a transient 2 56 bit symmetric key in ram. That key would be immediately encrypted under the cards configured public key and only the encrypted key would be written to non-volatile store and retained. Then during the cards, use all data flowing in and out of the SD card being read and written would pass through that AEs 2 56 bit cipher, which would be transparent to the device it's plugged into. It would look like just like a regular SD card, which was initially blank when the camera and or SD card is powered down.
Leo Laporte / Steve Gibson (01:20:05):
The RAM resident 2 56 bit symmetric key is forgotten and lost since it was encrypted under the user's public key. The only way for it to ever be decrypted would be with the use of the matching private key, which is deliberately unknown to the camera and the SD card. So it's a very slick solution for using an SD card to continuously capture photos and videos while never allowing the contents of the card to be exposed. Anyway. Very cool. Sean, thank you for sharing it with our listeners. I wouldn't be surprised or we have some, some people interested. He did mention that it's pricey. I think it was $159 for 32 gigs. Oh yeah. Wow. If if me, if memory serves, that's like, like 10 times more than the normal price. Yeah. Yeah. So plus don't ever have problem with that card because there's nothing on it.
Leo Laporte / Steve Gibson (01:21:00):
But gobbled e go <laugh>. That's true. You can't recover that data. Don't, don't lose your matching private key either. Right, Right. Yeah. Jeff said, Hey Steve, I noticed on three MA's blog that they just joined Proton Brave the Tour Project and a couple of other internet services to launch the privacy pledge initiative. And so that's at privacy hyphen pledge.com. I won't go into any detail. I just kinda wanted to give them a heads up. They've got a bunch of, you know, I guess, Okay, five privacy forward principles. The this group, which is Brave David Carol, Male Fence, Moje, Neva Open Exchange, Open Media, Proton, you know, the, the encrypted mail people three month, the tour project to Denova and you.com. So, you know, and they, their their good ideas. The internet above all should be built to serve people. This means it honors fundamental human rights is accessible to everyone.
Leo Laporte / Steve Gibson (01:22:07):
It enables the free flow of information. Businesses should operate in such a way that the needs of users are always the priority. That's the first principle. Second one, organizations should only collect the data necessary for them to sustain their service and prevent abuse. They should receive people's consent to collect such data. People should likewise be able to easily find a clear explanation of what data will be collected, what will be done with it, where it will be stored, how long it will be stored for and what they can do to have it deleted. Third principle, people's data should be securely encrypted in transit and at rest wherever possible to prevent mass surveillance and reduce the damage of hacks and data leaks. Fourth online organization should be transparent about their identity and software. They should clearly state who makes up their leadership team, where they're headquartered and what legal jurisdiction they fall under.
Leo Laporte / Steve Gibson (01:23:04):
Their software should be open source wherever practical and op, open to audits by the security community. And finally, web services should be interoperable insofar as interoperability does not require unnecessary data collection or undermined secure encryption. This prevents the creation of walled gardens and creates an open competitive space that fosters innovation. So they, they say, This is the internet that we deserve. This is the internet we are fighting for. It is within our reach. We simply need to be bold enough to seize it and maybe smoke something. You know, I mean, we all, we all wish that was the internet we had. It's not, I mean, honestly, anybody should be able to sign this because there's plenty of, you know, ways out of this. Like, you should only collect the data necessary for you to sustain your service. Okay. Yeah. It should be encrypted at rest whenever possible.
Leo Laporte / Steve Gibson (01:24:06):
Okay. <laugh>. Yeah. It it, I know. So it's sort of a happy, it's pretty nabi pamby, frankly. Yeah. It reminds me of the Hate Ashbury. Oh, I get it now. Yeah, yeah, yeah, yeah, yeah. I mean, I'm glad that that, that they said this, but honestly, Google could sign this without any, you know, hesitation. Yeah. I don't think they would be admitted. You, you're not invited. Sorry. Go. No, you, you, you go to the forum and you put your name in and they say, We'll get back to you <laugh>, they send you this images Hope that's a parachute, not a <laugh>. Yeah. Yeah. That's an odd image to put next to your request to join the privacy pledge. I'm not sure. Yeah. Jump off the cliff with us. See what's in that backpack. Yeah. Don't look down. And she's Don Edwards, my last chair here.
Leo Laporte / Steve Gibson (01:25:03):
He said, Hi Steve. Surely the EU nonsense would go away if EU sites change the analytics.google.com URL to analytics.google.eu. Oh, then, yeah, I know. That's what I thought too. Said then. Then Google could use their EU servers to do the analytics in keeping with EU rules and laws. Keep up the good work, Don. Now I didn't know when I read this whether analytics.google.eu worked. So I gave it a try. It returned to DNS lookup failure. So that doesn't appear to be an immediate option for those in the e eu. What I assumed do Don meant was that if Google wanted to respond to this concern, this might be a clean means for them to do so with, you know, nation after nation ruling against the use of Google Analytics as it stands today as being unlawful, something likely needs to change. So I thought that was a very cool suggestion.
Leo Laporte / Steve Gibson (01:26:03):
Analytics dot, google.eu. I mean, it's almost, you know, you're like supporting the EU when you make that change. Yeah. You have to actually create a server at that address first. That would be, I think they could do that in about, you know, two seconds. About two seconds. How long does it take to provision that somebody presses a button somewhere and now there's Google Analytics that.eu. It's somewhat telling that that does not exist. I know. Wouldn't that I I was surprised. Analytics requests are redirected to the US probably in every case. I would bet. Yeah. That's where, that's where they're most useful are. Yeah. That's where we we really want the information. That's right. Let us take a time out because you are gonna talk about this Akamai thing, this poisoning. It's neat. Yeah, yeah. But first a word from our sponsor, Kolide. We love collide.
Leo Laporte / Steve Gibson (01:26:57):
I love this idea. Now, if you use Slack in your business, Kolide is an endpoint security solution for companies that use Slack, that uses the most powerful untapped resource in it. Your end users see U unfortunately, up to now, old school device management tools like MDMs have really treated users as the enemy, right? They force disruptive agents onto employees', devices, agents that slow performance treat privies and afterthought because after all, we have to know exactly what you're doing. That way of doing things unfortunately turns it admins and end users into adversaries, right? And unfortunately <laugh> it, it often just makes the situation worse because end users just use their own devices. They say, Fine, fine, I'll use my computer, my phone. Now you've really got a problem.
Leo Laporte / Steve Gibson (01:27:58):
It, I understand why you wanna treat every device like Fort Knox, cuz security is hard. But I think this is a better way and I think it really works. It's called Kolide, K O L I D E. Instead of forcing changes on users, collide sends them security recommendations via Slack. It treats your users like grownups. Now probably most of you're saying, well, they're not grownups or toddlers. Well, they are grownups. And if you give the information that they need and explain what you're doing and why, say we want your assistance to protect the company, it really is great. Kolide notifies your team when devices are insecure. And then, you know, it says why this is a problem. Let's say for instance that they've been saving recovery codes in the clear in their download directory. I bet you a lot of your users do that.
Leo Laporte / Steve Gibson (01:28:48):
Kolide sees it, sends them a note saying, you know, I see you have these recovery codes for you know, our our system in your download folder in plain text. Let me explain why that's a problem. And let me show you step by step how to fix this. The users want your company to succeed. They don't want you to be hacked. That's bad for everyone. When you reach out to employees with a friendly Slack dm, when you educate them about company policies and why they are that way collide helps you build a culture in which everyone contributes. Everyone's a partner in the joint effort to keep the stuff secure because they understand what you're asking for and they understand how to do it and, and their partners, they do it. It all starts when you get collide. The first message they'll get from Kolide is, Hey, we just, we're starting to use collide.
Leo Laporte / Steve Gibson (01:29:40):
Let's walk through the steps to install it on your system. Here's why it's gonna be a great thing. And if you're an IT admin, and I know this is a new way of thinking, it might be a little challenging at first, but honestly, trust me, it works. Kolide, has lots of reasons to think. So collide gives you a dashboard as the IT professional lets you monitor the security of your entire fleet. Totally cross platform, Mac, Windows, and Linux. You can see everything you need to know, like which employees have their discs encrypted who's got their OS up to date, who hasn't done the updates, who's using a password manager, who's not. All the things you know, you are best practices. And then instead of saying, Do this cuz I said, so you're saying let's explain why you need this, why it's good for you and good for us and let's do it together.
Leo Laporte / Steve Gibson (01:30:28):
It's just great. It also collide. Makes it very easy to prove compliance which I know nowadays is really important. We talk about, almost all of our advertisers now are talking about compliance. Obviously this is something you gotta pay attention to. Auditors, customers, leadership, they will all know you're doing the right thing. Kolide users centered, cross platform endpoint security for teams that Slack, that's the elevator pitch. One line that says it all. You can meet your compliance goals by putting users first. You can, and I know you want to visit kolide.com/securitynow to find out how. Follow that link the hook you up with a goody bag. I got my laptop stickers. I got my Kolide t-shirt. You get the t-shirt just for activating a free trial. There's several models. This is one of them. I love this. This is a nice t-shirt. It's another one I took home cuz I I love it even more.
Leo Laporte / Steve Gibson (01:31:21):
<Laugh> collide. And they said, you gotta keep one here. See the Pinocchios, the Flying Pinocchios <laugh> and then their tag honest.security. I love it. Kolide kol i d e collide.com/ Don't forget this part security now got a t-shirt for you, some sticker, some other swag collide.com/security. Now this is just the right way to do it, the right idea, an idea whose time has come. But I understand there's people are going, ah, you're already using Slack, right? That means you care about your employees, you're letting 'em use Slack. Take the next step, kolide.com/securitynow. Now back to Mr. G. So last Thursday we got a glimpse into a world shaking flaw. Oh, that very few pha that very few people knew about until now. A 23 year old Italian security researching enthusiast by the name of Jacopo Ted and his friend Francesco Mariani stumbled upon a flaw in Akamai CDN that could have ruined many days for half the world's websites that rely upon Akamai. A content distribution network is at its heart, a massive global distributed cash. It keeps track of a website's content, pretty much everything, and holds the most recent current version of a website's content in a cash which is local to that remote site's visitor. In that way, since the cash is close, the site's performance remains snappy, even though it's web server might be on the other side of the planet. And on a not particularly fast connection.
Leo Laporte / Steve Gibson (01:33:16):
So first of all, imagining that this can be done at scale safely is nuts <laugh>, but that hasn't <laugh>. It's like, no, don't, don't try to do that bad idea. But that hasn't stopped the world's very successful CDNs from doing it anyway. What's absolutely obvious is that this only works if the massively distributed web asset cash maintains its coherence so that it always accurately reflects the correct contents of a remote website. If it were possible in some way to deliberately alter a CDNs distributed cash to change any of those locally cashed remote web assets. Like for example, a site's JavaScript, nothing less than Havoc would rain since such an attack would be tantamount to having the ability to directly alter a sites served content. Since this podcast is titled Poisoning Akamai, you already know that this was somehow done. But the reason this podcast is titled Poisoning Akamai is because the story told by 23 year old jacopo of their discover and the discoveries aftermath is absolutely worth sharing.
Leo Laporte / Steve Gibson (01:34:54):
So posting to medium.com, jacopo opens his story by explaining. In March, 2022, my friend Francesco Maria and I were teaming up on a private bug bounty program organized by white jar to search for bugs on a website that was using Akamai cdn. The Akamai waff, that's the web application firewall rules were bothering us while experimenting with the most common attack types. So we quickly got bored and started trying more esoteric payloads and mixing them. Finally, we ended up finding a vulnerability that really made us exclaim, Wow, we broke half the web. But let's start from the beginning. He says, at one point we were intrigued by an unusual DNS failure response received by sending twice an HTTP slash 1.1 get request to the host being tested with the connection colon content length header and containing another get request to www.example.com as its body. Okay, now, at this point I'll interject that I remember that we did an extensive podcast on exactly this subject, but I cannot recall what the sub, what the specific topic was.
Leo Laporte / Steve Gibson (01:36:29):
It involved chaining http requests or problems with http chaining or proxying? What these guys are talking about is having an HTTP style get query, not a post query where the get query contains in its body, which is normally empty for get queries. Instead another http get query falling, all of its query of his regular query headers. That's not the normal format for get queries where the specification of the object being queried for is in the get URL path. But again, I know we covered this years ago in this case, there example shows a get query containing the query headers connection colon content length, which is not normal for a get query and content length. Colon 53 also not normal. Those are what you see in post queries cuz that specifies the, the, the, the, the the after the query post contents will be there and their length.
Leo Laporte / Steve Gibson (01:37:43):
So upon seeing this odd DNS failure response, Jacobo wrote weird behaviors like this can often be overlooked while testing so many, many things. But luckily this time we decided to dig deeper. He said, I have to admit, it took me a while to figure out what was going on and I also had to reread Nathan Davidson's excellent article on hop by hop headers that I had studied in the past. And so it is for what it's worth, indeed, an excellent article, which I would recommend to anyone who's interested in digging more deeply into this topic that was not necessary for understanding what's going on here. I've got a link to the article in the show notes. He said, As explained in rfc, this is Jacopo as explained in RFC 2068, section 13.5 0.1. There are some special headers named hop by hop, which are removed from proxies before forwarding requests to the next proxy or the destination.
Leo Laporte / Steve Gibson (01:38:50):
And of course, that's what Akamai is, is it's a network of proxies, which are, are caching proxies. He said the addition of the connection header allows including more hop by hop headers in addition to the default ones specifying the content lake header as hop by hop. It happened that Akamai first proxy removed it during the request, I'm sorry, turning the request body into a second request. Akamai second proxy then resolved the two requests separately since the first proxy received two responses, but only one was expected. A desynchronization occurred and the second response was cued and subsequently sent in response to requests from other clients slash users causing an http smuggling vulnerability. That's a formal, formally named thing. He said, understanding this in detail requires a certain degree of knowledge about network architecture, web protocols and other fancy stuff. So I try to explain it more easily with a chart.
Leo Laporte / Steve Gibson (01:40:06):
And I I have the chart and the show notes and Leo, you had it on the screen there. So that sort of gives you a sense for what it is. It, what it very clearly shows is what happens. It all boils down to an ized caching server query parsing error, which results in a single query rather than being kept as a chain being split into two and forwarded to two separate destination client web servers. Then the two separate queries are answered each by their own server and returned to the cash for cashing, which is what Akamai does. But the cash was only waiting for the reply to a, a single original query that would've normally been chained. Instead it was split. So it places the unexpected reply into a queue. And that's the behavior that we talked about a few years ago where it then is available for, for handling serialized http queries and that reply will be returned to someone else.
Leo Laporte / Steve Gibson (01:41:18):
So Jacobo says however he wrote, I could not immediately understand why the DNS error was showing up and why www.example.com was not being resolved. The answer was actually quite simple, but my coworker's intuition was crucial. Mized proxy that routes requests appeared to resolve DNS only internally with an mized network. Okay, so, so that, that was sort of a subtle point that he was making the point that it was a fluke that the DNS failure occurred. It was the DNS failure that caused them to look more deeply into why the DNS failure, even though what was actually going on. It doesn't really matter that optimize only resolving local DNS queries. It's just that it was that, that fact that led that it was the first little piece of the, of the breadcrumb tr trail that they then followed that led them to the a, a serious bug in AC optimize caching architecture.
Leo Laporte / Steve Gibson (01:42:26):
He said we were using a VPN to verify that the desynchronization was an open one, meaning that it affected the responses given to IP addresses other than the ones we were attacking from. So in other words, they, they used a VPN to, to shift their IP and then generate a query from a different IP to see if it, if it was open, meaning that multiple users at different ips would also be affected. And they confirmed it was he that also believing it possible that the bug concerned all Akamai customers around the world. We changed our target from the original server they were testing at which they redacted from their notes to more popular sites. To our amazement, we noticed that it worked on them all and that sometimes smuggled responses were being server side cashed from Akamai Edge nodes for the entire geographic area closed to the ip, sending the malicious request.
Leo Laporte / Steve Gibson (01:43:36):
This allowed us to semi permanently, depending on cash times, create new arbitrary contents within almost any domain served by Akamai resulting they wrote in a huge all caps impact as a proof of concept we created for the whole Italian area. The newly cashed page, demo.paypal.com/jacobo, teddy underscore hacker one dot js containing the content of www.sky.com/robots.text Another Akamai customer because we didn't own a host on the Akamai network to use for publishing our arbitrary contents. Okay, so just to make this clear so far, they arranged to place a brand new page into optimize web cash named slash ja cobo tesi underscore hacker one dot j s associated with the root of demo.paypal.com. Thus anyone else in Italy who was also being served by ized cash for that locale, which had been poisoned, would be able to receive that cash page by asking for it from demo dot PayPal dot com's web server.
Leo Laporte / Steve Gibson (01:45:17):
So upon receiving that query, the local Akamai cash would see that it had a copy of that page in his local cash and would return it quite quickly to whomever asked. He said, once we understood the seriousness of the situation, we decided to report it ethically and responsibly, first of all, to Akamai. Unfortunately, we quickly realized that Akamai doesn't have a bug bounty program, Hall of Fame swag giveaways or anything, and they, they clipped out a piece of the email that they received on 3 25 20 22 at 2029 from Akamai written to Jacopo to tedc, and he said H and the email from Akamai says Hydro Jacob Copo. It's quite clear what's happening here. Peren, thanks again for the very detailed report. Closed Peren, we had no issues confirming your report. We're working on mitigations and making changes to our http parsing and processing logic. Unfortunately, Akamai does not have a bug bounty program at this time, and we are not able to provide a direct monetary award. But regarding some other means, a recognition of your contributions. I'll get back to you soon. Send him some stickers. Stickers are always good. <Laugh>, effing believable. Thanks for letting us know <laugh>.
Leo Laporte / Steve Gibson (01:47:01):
Okay, so Jacopo says we are white hats, but we're, but we're still not willing to work for free because this vulnerability was very critical and our skills are rare, complex, and sought after and we think they deserve to be valued. So while Akamai was patching following our report, we chose to race against the time by asking for bounties from single Akamai customers, which is so clever. He says, While this may sound strange from our point of view on technologies, those who use a framework plug in CDN whatever, assume both their benefits and their risks thanks to our work, Akamai and all their customers have been made aware of a security issue, boy and how, and have been able to fix it. So it's just fair that they pay for our service because without us, the vulnerability would still be there. We used BB Scope to extract links for all the public programs on the most popular bug bounty platforms.
Leo Laporte / Steve Gibson (01:48:17):
Next, we wrote a short bash script to filter from the list only the domains whose DNS pointed to Akamai. Okay, so in other words, they very cleverly reported this bug as it related to specific major Akamai customers whose websites were indeed still in serious danger until Akamai pushed out a fix. And what were their results? Jacopo wrote First White Jar immediately gave us 5,000 euros for their private program. They said on bug crowd, they were not competent enough to understand the vulnerability and closed both our reports for tesla.com, which was vulnerable as duplicated they said of a ticket clearly not related to ours. And for last pass.com as not applicable because they were unable to reproduce integrity regarding the Brussels Airlines program, which we showed was vulnerable. Told us that Brussel's Airlines is already aware of any request smuggle vulnerabilities in their web assets.
Leo Laporte / Steve Gibson (01:49:42):
And Jacob Copo said, Yeah, any lol he says, and closed our ticket as it duplicated on Hacker one. Some programs refused our tickets and closed as not applicable. He said Starbucks replied, The vulnerability in their opinion wasn't a major security issue. Playstation staff failed to reproduce even after we created a new page for them under the www.playstation.com domain. <Laugh> Marriott informed us that cash issues were temporarily out of scope for awards. He said, however many other programs paid us. We received $25,200 from PayPal, 14,000 8 75 from Airbnb, $4,000 from Hyatt Hotels, 750 from Valve Perens Steam 450 fromto and $100 from Goldman Sachs. A hundred dollars. I know that's a hundred dollars. Just a little stingy there. Goldman in particular, they said Airbnb handled a situation outstandingly applying custom rules on optimize web application firewall in less than 24 hours to block requests containing connection colon content length, even before optimize official fix.
Leo Laporte / Steve Gibson (01:51:19):
Paypal was also a curious case because they confirmed our report and issued a bug bounty long after optimize fix. So we don't know if they ever saw the vulnerability working or if they just trusted our proof of concept video. Akamai fixed it by applying some rules that prevent specifying the content length keyword with the connection header value. But we're not sure that there are no other bypasses or other unexpected similar ways to split the requests. Unfortunately, Microsoft and Apple acknowledged our reports after Akamai had already deployed a fix, but they thanked us anyway via private emails. So <laugh>, as we already know, I think from all of this, I'm most disappointed in Akamai. You know, their business is doing something that is so inherently dangerous where a mistake as we've just seen could have truly horrific consequences and they have no formal or informal bug Bounty established.
Leo Laporte / Steve Gibson (01:52:36):
The idea that a company of this size could just say, Gee, thanks guys, and not write them a sizeable check on the spot is unconscionable. The way these guys arranged to monetize their discovery was quite clever, ingenious, isn't it? That's so clever. Yeah, <laugh>. But that also means that they knew because they're clever, they knew full well that for an exploit with this much power and virtually universal application. I mean, Microsoft and Apple sites could be compromised. They could have asked the likes of Erodium for a million dollars and they would've received So it is the bad guys, in other words. Yes. Yeah, they would've received it anyway. I thought it was a very interesting story about something that happened earlier this year and because the guys were white hat hackers, few people, few people ever learned of it. Yeah, Akamai fixed it still hasn't given them anything, but they made more than $50,000 by going to the the the victims.
Leo Laporte / Steve Gibson (01:53:41):
Basically. The victims, Yes. Showing the victims that they had problems. This works because there was a mitigation the victims could employ, right? Had the individual, the individual customers of Oai have the so-called web application firewall, right? And so on an on a, on an on a user by user basis, they were given them a patch for their firewall. Had that not existed then it'd be really a problem. They wouldn't have been able to get any money outta anybody. None. None except just put out a medium post as they did and say, These guys cheap <laugh>, Boy <laugh>, thank you Steve Gibson shining light into the dark corners of the internet. It's pretty powerful beacon too, and thank you for doing it. You never ne know what's gonna crawl out. <Laugh>. Yeah, every Tuesday right here we do it about one 30 or 2:00 PM Pacific.
Leo Laporte / Steve Gibson (01:54:35):
That's let's see, four 30 to five Eastern. That's about 2030 UTC if you want to tune in and watch us live. That's how you get the kind of the first pressing the extreme, the extra Virgin Security. Now <laugh> the live stream is that Live twi do tv. You can chat with us at irc Do TV club members of course can chat in the Discord. The Discords always open though, and we're always chatting about all kinds of geeky topics. It's just part of our bigger club twi offering. $7 a month gets you add free versions of this show and every other show we do access to shows we do only in the club, like the Hands on Macintosh and Hands On Windows show, the Un Linux show, the Stacey's book club and so forth. Plus you get the Trip plus feed, which includes a lot of stuff that doesn't happen in the shows before and after the shows and so forth.
Leo Laporte / Steve Gibson (01:55:29):
And the triangulation episode we just did that was played for the, by the Club. Thank you club members. We really appreciate it. Seven bucks a month seems fair. There's a yearly plan. There's corporate plans to twi that TV slash club twi. And if it's just security, now that rocks your boat and you don't wanna pay for all the other shows and the other benefits. 2 99 a month gets you a free versions of security. Now you can also go to Steve's site and get a copy grc.com. He's got two unique versions of the show. He's got, of course the 64 Kilobit audio, but he's got 16 Kilobit Audio for the Bandwidth impaired and those great transcripts by Elaine Ferris, which lets you read along as you listen or search for topics and that kind of thing. All of that@grc.com. While you're there, pick up a copy of Steve's True Bread and Butter Spin, right?
Leo Laporte / Steve Gibson (01:56:16):
The World's Best Mass Storage, Maintenance and Recovery Utilities 6.0, the current version 6.1 coming any day now. And you'll get a free copy if you buy it today. Yep. By 6.0 today. Steve also has lots of, and you'll get very early access to the beta because it's gonna, because of the fact that it's a DOS app, I'll, I'll have that available to six zero owners a long time before it's all packaged in its window boot generating. Oh, okay. Form. Cool. So that's the other thing is that, I mean, I'll be working as quickly as I can, but there's just gonna be some delay. Yeah, good to know. Okay, so there'll be a, a really early access, another good reason to get it right now. Grc.Com. Lots of free stuff there. Fun stuff. You can leave Steve feedback there. Grc.Com/Feedback. You can also leave it on his Twitter account.
Leo Laporte / Steve Gibson (01:57:06):
He's at sg GRC as dms are open at SG Steve Gibson. GRC gives him Research Corporation <laugh>. That's another good place to leave feedback for Mr. Gibson. We have 64 Kilobit audio and high quality seven 20 P video available at our site, Twitter, that tv slash sn. You could download it there. You could subscribe in your favorite podcast player. There's even a YouTube channel dedicated to security Now. Plenty of ways to get it. The only thing I ask, get it every week. You don't wanna miss an episode of security. Now. Thanks for being here, Steve. Thanks for all you do. We'll see you next time. Thanks buddy. Bye. The Vault salute.
Jonathan Bennett (01:57:49):
Hey, we should talk Linux. It's the operating system that runs the internet about your game consoles, cell phones, and maybe even the machine on your desk. But you already knew all that. What you may not know is that Twit now is a show dedicated to it, The Untitled Linux Show. Whether you're a Linux Pro, a burgeoning csit men, or just curious what the big deal is, you should join us on the Club Twit Discord every Saturday afternoon for news analysis and tips to sharpen your Lenox skills. And then make sure you subscribe to the Club twit exclusive Untitled Linux Show. Wait, you're not a Club Twit member yet. We'll go to twit.tv/clubtwit and sign up. Hope to see you there.