Security Now Episode 882 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for security. Now, Steve Gibson is here. We will talk about TLS and Villa. Really interesting testing framework for TLS libraries works really well. Google is delaying who, who could have predicted it once again, the removal of third party cookies from Chrome and proof positive that turning off macros in Microsoft office really works. Plus a look at RO hammer. It's back again. <Laugh> the attack that just never quits. It's all coming up next on security. Now podcasts you love from people you trust. This is is TWI. This is security. Now with Steve Gibson episode 882 recorded Tuesday, August 2nd, 2022 RO Hammer's Nine Lives. Security now is brought to you by Tanium. Tanium unites operations and security teams with a single platform that identifies where all your it data is patches. Every device you own in seconds and implements critical security controls all from a single pain of glass.
Leo Laporte / Steve Gibson (00:01:12):
Are you ready to protect your organization from cyber threats? Learn more at tanium.com/twit. And by ITProTV. Are you looking to break into the world of it? Get the introduction you need with ITProTV. Visit itpro.tv/securitynow for an additional 30% off all consumer subscriptions for the lifetime of your active subscription. When you use the code S and 30 at checkout and by Grammarly, get through those emails and your work quicker by keeping it concise, confident, and effective with Grammarly. Go to grammarly.com/security now to sign up for a free account. And when you're ready to upgrade to Grammarly premium, you'll get 20% off. It's time for security. Now the show we cover your security privacy online with this guy right here, all that and all that jazz. Mr. Steve Gibson. Hello, Steve. Yo Leo. Great to be with you where episode 8 82.
Leo Laporte / Steve Gibson (00:02:18):
The next, the next one of note will be in six weeks. I'll be 8 88. So, you know, just cuz that's a fun number. But that'll, you know, here, we're in August already, already in August. Okay. So this is not the actual name of the exploit. The name of the exploit didn't really move me much. It was called half double, but what it is half double is a single Hey Eddie. Yeah, exactly. But it is brilliant. And so I just thought it would be too fun to not to share it with our listeners. So today's title is RO Hammer's nine lives. Oh man, because yes, yes, it isn't God yet. And these guys have figured out a way to still flip bits in DRAM and exploit it. In fact I don't mention this until the very end, but on a brand new completely up to date Chromebook, an unprivileged user can obtain root that kernel access in 45 minutes.
Leo Laporte / Steve Gibson (00:03:26):
Oh, on a Chromebook, on a Chromebook. So of course this has all of the cloud. People terrified because they're all sharing hardware, assuming that you've got protection against a random virtual server in the cloud, obtaining root on its host and this makes it possible. Anyway, we're gonna have fun talking about that. But we're gonna first note, an urgent vulnerability created by an add-on to Atlassian's confluence, corporate work group server. Next week's use Nick security conference will be presenting not only the subject of the show, this new RO hammer attack, but also something very cool called TLS anvil, which is used for testing TLS libraries. And 13 of them were tested. We'll talk about what it found and it's like, it's not nothing. Google has decided again, although I'm I'm on their side on this, well I'm at least I'm on, on their side, on the initiative, they've decided to, again, delay their removal of third party cookies from Chrome and for, you know, presumably good reasons.
Leo Laporte / Steve Gibson (00:04:43):
We'll talk about that. And it turns out that attackers were already switching away from using office macros before Microsoft actually did it. We'll talk about the backstory there. We also have a bunch of listener feedback, some thoughts about computer science theory and bit lengths that I thought our listeners would also find interesting some interesting miscellaneous, and then we're gonna look at the return of RO hammerer, which we never really seemed to get rid of. Thanks to some really just awesome, brilliant and clever research. And of course I would argue that this is one of our better pictures of the week <laugh> we we've had people are howling over this. Some that are really fun. I gave it the title. It didn't come with a title, but I like the title. And anyway, it's a great one. So thinking other overall great podcast, it'll a lot of fun listeners we'll get to the picture of the week in moments, but first a word from Tanium.
Leo Laporte / Steve Gibson (00:05:51):
One, one of those names you probably have heard many times kind of the, an upstart in the security business. That's really transforming how people think about security at Tanium. You know, position is that the, the current approach, the general approach to cybersecurity is kind of fundamentally flawed. It management and security point tools offer a small piece of the solution needed to protect your environment. And many of them promise they can stop all breaches and well, we just know they can't plus, and this is maybe even a bigger but more subtle problem. It's hard to make proper decisions about security when you don't have up to date data and trying to defend your, your critical assets from cyber attack, with tools that don't talk to each other is just, well, that's just a bad idea, no way for it teams to navigate today's complex, fast moving attack surface.
Leo Laporte / Steve Gibson (00:06:47):
So Tanium has a different approach. Their idea is at convergence of tools, endpoints it operations and security that can give you up to date data. So you know exactly what's going on and give you solutions that can solve problems. Fast solutions for government entities, education, financial services, retail, healthcare trust Tanium for every workflow that relies on endpoint data, which is, you know, pretty much everybody right with at Tanium, all in one, you can do asset discovery and inventory, which means you can, you know, track down every it asset you own instantaneously. You can do risk in compliance management, fine and fix vulnerabilities of scale and seconds. I mean, imagine patching everything, everything you've got in seconds, threat hunting, hunting for sophisticated adversaries. In real times, you get client management, which automates operations from discovery to management. You get sensitive data and monitoring which indexes and monitors sensitive data globally in seconds.
Leo Laporte / Steve Gibson (00:07:50):
Tanium is here to really protect your organization where other endpoint management security providers have failed one platform. That's key single pane of glass tame identifies where all your data is across your entire estate patches. Every device you own in seconds implements critical security controls, and it can do it all, you know, right there with a single pan of glass, ask Kevin Bush, he's vice president of it at ring power Corp. Here's the quote. Kevin says, quote, Tanium brings visibility to one screen for our whole team. And if you don't have that kind of visibility, you're not gonna be able to sleep at night. Kevin sounds like that's an oddly specific <laugh> sounds like he knows with real time data comes real time impact. If you're ready to unite operations and security teams with a single source of truth and confidently protect your organization from cyber threats.
Leo Laporte / Steve Gibson (00:08:43):
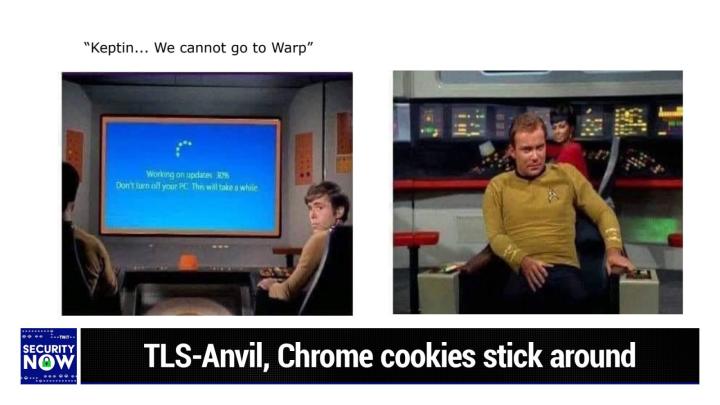
Well, maybe it's the time you met Tanium. You could find out more, go to Tanium T a N I U m.com/twit. You know, those silos are not good for you, you know it. So do something about it. Tanium.Com/Twi. We thank of so much for supporting security now and remind you that you support Steve's work too. When you use that address that way they know you saw it or heard it here, tanium.com/twit. All right. Picture of the week time Steve <laugh>. Okay. So this is two, two captures from star Trek, the original series. And, and I, I titled this kept in, we cannot go to warp. <Laugh>. So the, the first one is from Kirk's vantage point, looking out across Sulu on the left and Checkov on the right and to the view screen at the front of the bridge. <Laugh> where, where we see the, the little RO what I called a roller coaster dots and blue screen, the, the, the little spinner saying, working on updates 30% and, you know, and, and so, and so, and, and we see checkoff sort of like turning his head back to look at Kirk, presumably saying, captain, we cannot go to warp.
Leo Laporte / Steve Gibson (00:10:16):
And the second frame, it is a very unhappy looking James Tiberius, Kirk kind of like growling <laugh> because, you know, he wants to go to warp and no, his, his ship will not let him and I will note, we'll be talking about this later in miscellaneous, but URA back there ever present on the bridge through all of the original series on all six movies as well. So anyway, yes, <laugh> James is not happy that <laugh>, he's having to wait for his, his, his Starship to update and Lord help us. If <laugh> windows is embedded into future starships, please don't let let that happen. I, you know, everybody has always wanted me to write like a windows operating system, Leo, I would, I know, come on if it, it, well, I mean, I'm not going to, I've said no many times, but there's like, imagine if Steve wrote windows, well, I'm not gonna do that, but okay.
Leo Laporte / Steve Gibson (00:11:24):
If anyone tried to stick it into a Starship, okay. I would write that operating system. <Laugh> I'm just saying if that's, if that's what it takes, not to have updates ever then fine. I'll I'll step up. Okay. So the Australian software company Atlassian offers something called confluence, which is a web-based corporate Wiki written quite a while ago, 18 years ago, back in 2004 in Java. It's one we used actually and have for years. Oh yeah. Cool. Yeah, it's one of Atlassian's more popular products. It's packaged as a standalone turnkey. That includes a built in Tomcat web server and the da the database is H SQL DB, H S Q L DB, which is also a Java based database. So it makes sense that that's what it would choose. Although other databases can be used with confluence it's modern collaborative software it's used to help teams collaborate and share knowledge in, in a corporate setting it's used, for example, to capture project requirements, assign tasks to specific users and manage one or more calendars.
Leo Laporte / Steve Gibson (00:12:46):
It's typically used on premise in all over the place in both in corporate enterprise and, and government environments. So, and now I'm waiting for the other shoe to drop. Is there a <laugh>? That was the good news. Yeah. We're talking about it today because it appears to have recently come to the attention of ever prolific attackers, who based on the troubles it's been happening, happening having <laugh> recently it's come to their attention because it's been, you know, vulnerabilities have been surfacing. And unfortunately, as with any product that was first written 18 years ago, before today's hyper attack aware climate existed, some of its coding practices from back then appear to be being turned into vulnerabilities. Now, although confluence has recently suffered, as I said, from a series of troubles, it popped up again just last week, due to a very serious problem with the installation of believe it or not default hard coded credentials.
Leo Laporte / Steve Gibson (00:14:00):
As we know, anytime you hear that a problem has been created by the discovery of defar the default hard coded credentials, you know, meaning a username and password with privileges, no one should have by default being part of an installation, it's difficult to chalk that up to anything other than some previous very bad decision. In this instance, the trouble arises from the installation of an app called questions for confluence. So it's not the core confluence server itself. It's an add-on app. It's often installed on confluence server and data center on premises instances because it allows employees to ask questions and receive answers from a company's various internal departments. The installation of this questions for confluence app creates a user named <laugh>. The user's name is disabled system user with the username disabled system user, and the email of don't delete this user email.com. So, you know, fake, fake email placeholder, but disabled system user as the name of the account and the name of the user.
Leo Laporte / Steve Gibson (00:15:27):
And unfortunately, contrary to the name given to the account. It's not at all disabled, although it is indeed a system user Atlassian released a patch that disables this built in hard coded account 13 days ago on July 20th. However, confluence server admins did not have much time to install Atlassian fix because through no fault of Atlassian, the system account username and credentials for this account were posted the next day to Twitter course by Uhhuh, by someone using the handle annoyed researcher. Oh, okay. I don't know the backstory for that, but it's uncool right? To do that under any circumstances. I don't care how annoyed somebody is. That's just not the way it's done. You, you, in fact, I would argue, you cannot call yourself a researcher, no matter how annoyed you may be. If you're, you know, posting credentials for a just released flaw that no one will have had time yeah.
Leo Laporte / Steve Gibson (00:16:37):
To fix, you have to do responsible disclosure. That's just, everybody has to do that. Yeah. So as things go these days, it didn't take the bad guys long to put annoyed researchers information to nefarious use the cybersecurity firms, both of them, gray noise and rapid seven, both reported seeing immediate and continuing exploitation of this, I guess it's, I guess we'll call it a vulnerability, although it's hard to chalk up, you know, hard coded credentials. No, I guess they, it is a vulnerability. It's not like they broadcasted it, but still shouldn't be done. It's the kind of thing you do by policy rather than by mistake. I guess that's the problem I'm having. Anyway, within days of the release of the patch, it was being used in a tax CS, a has stepped up and urged confluence server owners to check to see if the vulnerable app has been installed on their servers.
Leo Laporte / Steve Gibson (00:17:35):
And if so, to install Atlassian's past patches and Atlassian noted that disabling the app due to the nature of the problem, does it fix the issue cuz it's the app's installation that created the problem by, by creating this instantiation of this, this non-disabled <laugh> disabled user. So confluence server owners must either install the security fixes or manually disabled that hard coded disabled system user account, which was created by this questions for confluence app. So anyway, because this thing, I mean, I, I I've been seeing confluence problems pass by and they just haven't risen to the level of bringing them to our listeners' attention. But this one really seemed like it was important enough that, you know, you just want to make sure that if, if you are using this thing that you, you ha you've responded to Atlassian's security fix and, or you know, killed or disabled that user.
Leo Laporte / Steve Gibson (00:18:44):
And in fact, Kevin Beaumont, the true security researcher who tweets as Gossi the dog, he said, I would recommend confluence be placed behind a VPN or reverse proxy. And he says, for example, as your app proxy, he says, requiring authentication. He said, it's simply two historically vulnerable to leave online. You're a sitting duck was his tweet. And you know, it's difficult to argue with Kevin's logic. Everyone knows that I think this should be standard practice now for all publicly exposed services, the rule would be don't publicly expose anything that doesn't utterly and absolutely by definition need to be publicly exposed. So what does web obviously need to be publicly exposed by definition? So does email and probably DNS, although I even managed to not have my DNS publicly exposed, I use, I use level threes, big iron DNS servers as masters and, and, or I'm sorry, as slaves to my master.
Leo Laporte / Steve Gibson (00:20:15):
So, so the, the, the DNS, the, the only DNS that, that my system allows is zone transfers from my two designated name servers for grc.com, which are level three monster DNS servers. And who knows. They're probably, you know, virtualized and distributed and, you know, not, not even actual single machines anymore, but anyway, the, so I guess the, the, the, the point is it is possible to absolutely protect all of an enterprise's stuff by, by putting them behind. And this is what Kevin is talking about. An additional layer of authentication, you know, put them behind a VPN, put them behind some, some additional boundary that requires authentication and only then are you able to get to it or, or use an overlay network and, you know, and, and stick them on an overlay network so that, that people have to authenticate to that in order to get there, but just don't let, just don't have them as a public IP and port that Showdan is gonna index so that the bad guys can jump on whatever it is.
Leo Laporte / Steve Gibson (00:21:40):
The instant a problem is found. I mean, that's the model today. So the only sane response to, to today's reality is no matter what it is, no matter how secure you think it is, give it additional protection, that's that it has to be the way we roll. And I've been following my own advice from, like, before we started talking about this during next weeks, 31st use Nick's security conference being held Wednesday through Friday the 10th through the 12th in Boston, Massachusetts, a team of security researchers will be unveiling what they call TLS anvil. And I guess the point of the name is to use this TLS anvil to forge fully secure and compliant, TLS connection libraries, because that's what it's designed to test in the description of their forthcoming talk, which as I said, they'll be giving at the end of next week, they explain, they said, although the newest versions of TLS are considered secure, flawed implementations may undermine the promised security properties, such implementation flaws result from the TLS specifications, complexity with exponentially many possible parameter combinations, combinatorial testing, which they abbreviate CT throughout their work is a technique to tame this complexity, but it is hard to apply to TLS due to semantic dependencies between the parameters and thus leaves the developers with a major challenge referred to as the test Oracle problem, which is determining if the observed behavior of software is correct for a given test input in this work they write, we present TLS anvil, a test suite based on combinatorial testing that could be efficiently and cement and systematic that I'm sorry, that can efficiently and systematically test parameter value combinations and overcome the Oracle problem by dynamically extracting an implementation specific input parameter model that we constrained based on TLS specific parameter value interactions, our re our approach thus carefully restricts the available input space, which in turn allows us to reliably solve the Oracle problem for any combination of values generated by the combinatorial testing algorithm.
Leo Laporte / Steve Gibson (00:24:39):
And finally, they say we evaluated TLS anvil against 13, well known TLS implementations, including open SSL, boring SSL, and NSS, you know, Netscapes security suite. This is, you know, for the original one, our evaluation revealed two new exploits in matrix SSL, five issues directly influencing the cryptographic operations of a session, which they refer to as handshakes at the handshake level, as well as 15 interoperability issues, 116 problems related to incorrect alert handling, and 100 other issues across all tested libraries. So needless to say, this was worth doing. And it is just so cool that, that we have a, have a world where academics are able to tackle something, this complex, all of this mumbo jumbo about combinatorial testing and input parameter modeling, and, or, you know, testing Oracles. That the point is, you know, you, we could reduce all that to testing. TLS is hard.
Leo Laporte / Steve Gibson (00:26:06):
We did it anyway. Their paper is really interesting. I've got the link to it in the show notes for anybody who is interested, excuse me, the 13 libraries that they tested were bear SSL, boring SSL Boan GNU, TLS Lee Brate, SSL matrix, SSL embed, TLS NSS, open SSL, rust TLS S to N TLS light, hyphen N G N Wolf SSL. As it happens through the years, we've talked about most, if not all of these, they're all familiar to me, I'm sure they are to our listeners. Those who have been with us the longest at least, and recall, for example, that S two N is Amazon's from scratch open source implementation of TLS. They wrote it because of AWS. They needed, you know, a TLS for their own cloud services, but they observed that open SSL, as we've often observed, had grown in size to half a million lines of code 70,000, 70,000 of which were tied to SSL to, you know, TLS processing, but they could be replaced.
Leo Laporte / Steve Gibson (00:27:40):
And they did replace them with about 6,000 lines of code, which Amazon observed is far easier to audit and to actually have some sense of knowing what it's, what the code is actually doing. You know, how could you do that with half a million, whether they're all tangled up with each other. So anyway, this chart, which you had on the screen earlier, Leo, thank you yeah, in their paper, gives us a cross reference to those 13 TLS proposed libraries with the number of, of different type of exploits, found problems with the handshake crypto problems affecting client and server interoperability. The generation of alerts, which is to say in the, in the protocol, when either end does something illegal, the other end is supposed to send an alert and, and, and disconnect. It's like, you're bad and I'm hanging up on you. And, and then other problems their, their paper was 18 pages.
Leo Laporte / Steve Gibson (00:28:45):
I'm not gonna go into it, you know, in great detail, but they definitely found problems of varying degrees in every one of the 13 TLS libraries. And looking over the chart, it appears the best libraries were boring. SSL. Boan NSS open SSL, and Amazon's S to N oh, as well as TLS light, you know, but, and you know, these guys now really understand the state of play with the industry's TLS support. They, they wound up having, you know, like creating the tool, running the libraries against it, and then having to sit back and ask themselves, okay it's not exactly what we expected. We didn't know what we were gonna get. You know, how do we think, how, how do we decide to think about this? And they, they ended up defining two degrees of success for this test. They wrote a strictly succeeded test means that a library behaved exactly as expected.
Leo Laporte / Steve Gibson (00:29:56):
If multiple test cases are performed during the execution of a test template, the system under test must have behaved correctly across every one of them. But then they also created a, a softer, gentler that definition. They said a conceptually succeeded test means that an implementation did not precisely fulfill the RFC requirements or did not do so in all test cases, but effectively behaved correctly. And I'll explain what, what happened in a minute, cuz they, they, when they had this thing, they then to be responsible, they needed to talk to the implementers. And it it's actually the case that the implementers convinced them that it was necessary not to be strict. So they said, okay let's just be conceptual then that's that's good. Right? So they, they said, for example, this usually applies to tests where a fatal alert was expected, but the library either only closed the connection, but did not send an alert first or the alert description did not match the RFC specification.
Leo Laporte / Steve Gibson (00:31:26):
So, so we should understand that, that these guys implemented TLS anvil strictly from the RFCs, that was their starting point was, you know, what does the spec say the library must do in each and every case and the act of testing that, I mean, we, we don't know what internal tests TLS developers may have, but if we presume that they've been using their tests and how could you not, then this, this TLS anvil's results suggest that in at least some cases, those internal tests were wanting. So they then give some examples of what they found. They said, we count all tests as past that either succeeded strictly or conceptually. And now we know what that means and include the percentage of past tests. We further list the ratio of conceptually to, to strictly succeeded tests as an additional metric to compare how close an implementation is to the RFC for our tests, rust TLS, for example, passed many tests.
Leo Laporte / Steve Gibson (00:32:53):
But most of them only succeeded conceptually as Russ often did not send any alerts. And again, it's like, you're supposed to send an alert to tell the other end, why it was, why it just misbehaved. But you know, Russ just said, you know, F off and disconnected, which it's nothing, it gets the message across <laugh>. And Bowan in contrast often fulfilled the expectations they wrote of our tests. And at the same time was very accurate with alert descriptions. Good. Yeah, they, yeah, they said, we generally found that most libraries pass a high ratio of the test templates with NSS boring SSL, TLS, light NG, and open SSL passing around 97%, which I think is very good of their applied server tests among the client tests. So, okay. So of course, server test, meaning that you're using the library to accept connections, client tests, meaning you're using the library to, to generate new TLS connections to a remote server.
Leo Laporte / Steve Gibson (00:34:11):
So they said among the client tests, bear SSL, boring SSL, and Boan have the highest ratio of past tests with 97.3 96.8 and 96.2 respectively. They said, we expand upon the results of libraries with significantly worse ratios listing, how many test templates of an, of a, of an RFC past and how many were executed for each library. We grouped the results of test templates based on similar error cases and identified a total of 239 issues. We further categorized these findings based on their impact and determined that three immediately led to exploits in Wolf SSL and matrix SSL. In other words, you know, exploitable problems in those libraries, they're, they're gone now so long as you've updated recently, cuz these guys were doing all of this work, you know, before they went public and gave everybody plenty of time to, to, to fix. They said, additionally, we found five issues affecting the cryptography of a handshake as an example, the clients of matrix SSL and Amazon's S two N and Wolf SSL are willing to negotiate parameters.
Leo Laporte / Steve Gibson (00:35:43):
They did not offer, which is interesting and you know, not good. And they said while none of the parameters negotiated are sufficiently weakening the security to pose an immediate threat. Now parameter negotiation is a basic security property of every cryptographic protocol to prevent current and potential future attacks. So again, another nice thing that these guys checked, which, which the, these, which the authors of matrix SSL S two N meaning Amazon and Wolf SSL missed. So now they know, and presumably they have fixed that. They said we identified 15 issues affecting the interoperability to an extent where a peer that operates within the boundaries of the RFC may not be able to complete a handshake. They said note that this may also include intentional deviations by the developers. If they break the implementations correctness in regards to the specification, they said 100 issues account for various likely, but uncritical cases were a library deviated from the RFC beyond alert codes and where interoperability should not be affected.
Leo Laporte / Steve Gibson (00:37:06):
Examples of these findings are a bug in open SSL, which allowed multiple TLS 1.3, hello, retry messages, which can keep the client in a handshake loop. Okay. Again, like technically a violation of the RFC, but eh, not nothing to worry about, but still what's interesting about these is if that isn't what the developers intended, then getting them to look at why that happened. Could reveal some other side effect of this. So always good to at least be sure, you know, why you deviated from the intended behavior. They said, finally we grouped 116 cases where a library did not send an alert or sent a different alert than requested by the RFC. These are minor deviations from the standard. However, in the past information gained from the type of alert sent by an implementation has been used to Mount side channel attacks. They say to avoid such deviations, great care must be taken when designing the alert handling of an implementation.
Leo Laporte / Steve Gibson (00:38:25):
We hence chose to include these findings in our report to the developers and meaning that they then after creating this produced a comprehensive report to each of the 13 developers of these packages and what they had to say about responsible disclosure and feedback, I thought was very interesting. They said we responsibly disclosed all of our findings to the respective developers during the disclosure process. Multiple developers stated that they intentionally violate RFC requirements in specific cases. As an example, in TLS, 1.2 peers are not allowed to resume a session that has been terminated by a fatal alert. However, when multiple sessions take place in parallel, this requirement is difficult to implement. Okay. So what I, what I loved about that was that that the ivory tower developers of the RFC said, you know, if, if a, if a, if a peer terminates with a fatal alert, then you're not allowed to resume a session, but the guys who implemented this or attempted to said okay, what do we do about multiple parallel sessions?
Leo Laporte / Steve Gibson (00:39:53):
You didn't say you didn't tell us what to do. So these guys went one way that the TLS anvil guys took issue with. They said multiple developers also stated that they intentionally send different alerts or no alerts at all. Intentionally one reason was to minimize the risk of creating an alert Oracle for attacks. And, and these guys themselves mentioned that in the past, the alerts that were sent had been used, had been leveraged inside channels. However, now they say we do however stress that the specified alert handling of current TLS RFCs does not result in a known exploitable Oracle, but is considered to be secure. So they're saying, eh, it's not a good excuse. They said our original test suite contained 18 additional test templates, which we removed from the test suite after discussions with different library developers, their reasoning convinced us that in these cases, our interpretation of the RFC was too strict and that their library behavior was indeed valid.
Leo Laporte / Steve Gibson (00:41:16):
Very cool. So they said our presented evaluation does not contain these additional test templates anymore. There were some cases where the developers argued that it is unreasonable to follow the specification. For example, in some tests, a server that supports both TLS 1.3 and TLS 1.2 would need different alert handling for the same effective test. The situation becomes even more tricky when the server has not decided which protocol version to speak yet. Right? So again, two different protocol versions require different alerts to be responded to, to, to, to respond differently with alerts, depending upon the problem. Yet at this stage in the handshake, the version that's being negotiation that that's being negotiated, hasn't been determined and it could be either of them. So again, you know, like it's, you know, I, I love the fact that these guys were so insanely rigorous that these, I mean, they're edge cases clearly, but I mean, they're like an edge cases, edge case, you know, yet they came out as a consequence of this.
Leo Laporte / Steve Gibson (00:42:39):
So they said, for example, a server that receives a malformed or illegal client, hello message would first need to evaluate the supported version of the client to decide which to decide upon the correct alert, handling rules correctly, handling these nuances. They said C can be complex. And it is arguable. Whether the strict RFC conformance across all supported versions is worth the added complexity. And they finished the security bugs we reported. And most of our other reports have been acknowledged by the developers and will be considered for future releases. You know, none were, were, you know, run around screaming immediately patch, or they would've been done already since most failed test templates only failed for single or very few libraries. We conclude that the developers in general share our understanding of the RFCs. So just so cool. You know, and, and I guess another way to read this would be ivory tower.
Leo Laporte / Steve Gibson (00:43:53):
Rfcs meet real world implementations. There are some places where it just doesn't make sufficient sense to go to all the trouble that absolute slavish adherence to the RFCs would require. Anyway, all this beautiful work is on GitHub. The site is TLS hyphen anvil.com, which allow, which offers Dockers to allow the use of these tests by anyone. And I'm just, I salute this. This is precisely the sort of work that we need, and as much of it as we can get so Bravo to these guys, very, very cool work, and it now exists. So it can, if, you know, if there's a 1.4, then the suites, the, the test suites can be augmented to incorporate that, you know, this ends up being a, a benchmark reference against which TLS suites can be tested. And I just that's so cool. And Leo, yes. What isn't is my throat?
Leo Laporte / Steve Gibson (00:45:04):
It is overheated <laugh> well, take a break, relax. We don't wanna wear you out. But I do wanna tell everybody about ITProTV and especially want to tell people about ITProTV, if they're looking to get into it, I know a lot of you are, and ITProTV is a great way to get the knowledge. You need to get the certifications. You need to get that first job. And of course, if you're already in it, it's a great way to add to your skills, get new certs. Re-Certify it, pro TV makes it engaging and fun. Their hosts, they call 'em entertainers are of course, first and foremost experts in the field, but their enthusiasm and passion for what they're doing really communicates and makes it fun to watch. And you can do it on your own and schedule they're 20 to 30 minute long segments.
Leo Laporte / Steve Gibson (00:45:59):
And, and, and you can binge 'em if you want. There's 5,800 hours of it training, always up to date because they've got seven studios running all day, Monday through Friday, updating this, getting the latest versions as the test changes, the software changes as new certs come out, you can watch it anywhere you want on a desktop, of course, in a browser, apple TV, there's an ITProTV app Roku, or you can watch it on your tablet, your mobile device too. I mean, it really makes it easy to learn and fun. And with their virtual labs and their practice tests ITProTV makes sure you'll be, you'll be ready with the hands on knowledge you need. And you'll kind of be prepared for the test cuz you've taken 'em already. And I think that really helps one reviewer said quote, best website to study it and cybersecurity related courses.
Leo Laporte / Steve Gibson (00:46:50):
I like the part where they make a few courses free for a weekend. They do that every month. And it's great. In fact, for August, they're gonna do I think one that everybody interested in it should go and look at getting started in it. It's free the weekend of August 13th and 14th. That's a couple of weeks from now. They're gonna have two free live webinars, August 4th which is this Thursday, Don Ette will do how to get into it. And this is a Q and a with one of their founders. So that's a really great opportunity to ask your question. So if you can't be there live Thursday, August 4th, 2:00 PM. Eastern, if you can't, of course you'll be on demand, but, but if you wanna ask those questions, be there live August 4th, 2:00 PM Eastern and then all things, cyber security. That's with Ben Fike on Thursday, August 18th, also 2:00 PM Eastern new it training episodes of course are added to their library every day.
Leo Laporte / Steve Gibson (00:47:46):
In fact, today you can step into the booming cloud world with ITProTV's AWS cloud practitioner training, AWS cloud practitioner. It's of course that gives you everything. You need to get that cert and then get on your way to a career in the cloud. And if I think for a lot of people already in it, this is an area you'd like to get into what a great way to do it. So register right now go.it. Pro.Tv/Aws-Cloud-Practitioner. Did you get that? Go.It. Pro.Tv/Ws-Cloud-Practitioner. And of course, if you've got a business and you've got an it team, ITProTV has a great business plan for you too. A great way to get your team up is skilled up ups, skilled. I guess they called it and ready to face any challenge. Again, it pro.tv/security. Now, if you wanna sign up, you can get an additional 30% off all consumer subscriptions for the lifetime of your active subscription.
Leo Laporte / Steve Gibson (00:48:52):
Just use the code SN 30. That's nice if you do cuz then they know you saw it here and that helps us a lot. So it pro.tv/security. Now all one word and the code is SN three zero an additional 30% off. As long as you stay active, you pay 30% less. That's a great deal. Itprotv build or expand your it career and enjoy the journey. Itprotv slash security now, and now we go back to you, Steve and more great security stuff. So Google well last Wednesday they keep putting this off don't they, they just keep, they keep putting it off. And, and, and I, I guess I'm sympathetic because I recognize we all should recognize how difficult change is. If there's one of the, you know, the overriding themes of, of the podcasts lessons, it would be change is hard and nobody wants it.
Leo Laporte / Steve Gibson (00:49:58):
Just, just, you know, say I P V six, and you can rest your case anyway, their VP of the privacy sandbox initiative Anthony Chavez said last Wednesday, the most consistent feedback we've received is the need for more time, right? It's not Google. No, no, no, no. They're ready to pull the plug. Oh yeah. Uhhuh that's right. The more time to evaluate and test the new privacy sandbox technologies before deprecating third party cookies in Chrome, this feedback he wrote aligns with our commitment to the CMA. We'll get to that in a second to, to ensure that the privacy sandbox provides effective privacy preserving technologies, and the industry has sufficient time to adopt these new solutions now. Okay. I would argue that the industry will not adopt anything until you pull the plug on the old solutions. And you've said, Hey, we told you we are gonna pull the plug.
Leo Laporte / Steve Gibson (00:51:09):
We gave you plenty of time. We're sorry that cookies are gone and you can't track anybody anymore. Here's the API that, you know, we created to let you do that. So, you know, start doing it again. No, it's like, okay. The, the lesser we keep seeing is you have to make, make people change. Okay. So anyway, let's, let's back up a bit Google, once again, delayed its plan to terminate Chrome's support for third party cookies is what this amounts to they first failed their, this privacy sandbox initiative back in 2019. When my mustache was a little less gray with the announcement that its implementation would begin this year in 2022, meaning that this would be the only way to, to do what do we call it interest based advertising or something. I'm sure there's a term. Anyway, last year, after being scrutinized by the UK's competition and markets authority, that's that CMA that Anthony referred to and the S DOJ, our department of justice, Google announced their intention to delay their third party cookie phase out until the middle of next year.
Leo Laporte / Steve Gibson (00:52:30):
So 2013. And now last Wednesday, what Anthony is announcing is another delay saying that now it won't be, I saw August of 20, 24 somewhere, but, you know, basically they won't end, they're promising not to end support for third party cookies before the second half of 2024. And again, my feeling is just do it just, you know, have the system in place, have it well tested, have it working and then end the way it used to be and make people switch. And you know, <laugh> in two years, are we still gonna be here in two years? I think we are Leo. Yeah. so we'll get to see what happens. In the second half of 2024, we'll be right here under its current timeline, Google will expand the availability of its privacy sandbox trial to what they said was millions of users globally. Meaning that Chrome will begin to get this technology.
Leo Laporte / Steve Gibson (00:53:36):
And they're saying by early next month, so early September millions of users using Chrome will have this. What we've talked about before the topics API will be live, then they plan to gradually roll out the test to more and more users throughout the rest of 2022 and 2023. They hope to officially launch the privacy sandbox APIs by the third quarter of 2023, meaning. Okay. about a year from now, Anthony said, quote, this deliberate approach to transitioning from third party cookies ensures that the world can continue to thrive the world. Relying. You mean the advertisers without relying on cross site tracking identifiers or covert techniques like fingerprinting. Okay. So, you know, on the podcast we've talked, we, you know about, and we've been, if you'll pardon, the choice of words we've been tracking, Google's proposed tracking technologies closely. Their first attempt at replacing third party cookies was their awkwardly named federated learning of cohorts, you know, flock, which as Leo, you grabbed the fact that that was about birds, which, you know, all of the code names in that generation were birds focused, right?
Leo Laporte / Steve Gibson (00:55:12):
Yeah. Then when that failed to take off largely because no one understood how it worked and it was way too opaque. Google announced their new approach called topics, which is largely the same, but is far more understandable and inherently transparent in the way it works. And as the name suggests, and we did a podcast on this, so we've completely covered this topics more transparently you know, it works more transparently and makes it obvious how and what interests it is sharing with websites that users visit. It's got about 300 different topics. And when a user visits, a website that requests the information Chrome will offer from a pool three different topics in a random sequence that it knows the, in that the users is interested in. So it's sufficiently cloudy, you know, fuzzy that you can't track a user by seeing what topics their browser is offering from one site to the next the site's publisher, then that is the site's server that receives these three randomly selected from a larger pool that the user has shown their interest in by, by virtue of where they've gone to the sites they've visited in the past, that that server can then choose to share that information with their advertisers, which they certainly would.
Leo Laporte / Steve Gibson (00:57:00):
Okay. And, you know, being a technology hound, I understand and love these initiatives from Google. They make sense to me, but the big question in my mind will be whether any of this can actually replace all other side channel tracking. You know, as we've observed, if you turn off cookies, bad guys will just, or gray guys <laugh> will just use some other means of tracking like fingerprints. All of the, you know, the stuff that, that the panoptic click site shows is leaking from our browsers. I think that the only way wherever going to be free of tracking all together is through legislation, which makes it flatly and permanently illegal will of course, will first need a privacy protecting replacement, which Google's topics does offer. But once that's in place, we're gonna need governmental regulation probably led by the EU since they seem to have a pension for that to completely outlaw any and all other forms of anonymous internet, user identification, aside from the San, the use of the sanctioned API, which will hopefully become an industrywide standard.
Leo Laporte / Steve Gibson (00:58:23):
And, you know, I think has the chance to, so again, I, I it's, it's gonna ha everybody, every step of the way, this is gonna require people being forced to change. It's so far, it's already been slow and painful. I don't see any reason for that to be any different. You know, Google's got this thing in place. They've gotta stop moving the goal posts or no one's ever gonna believe that they're gonna be serious. So hopefully, you know, latter half of 20, 24 will finally see Chrome remove third party cookies, completely, you know, all together from, you know, from the chromium core. And by that time topics will have been around long enough so that if somebody says, you know, says, wait a minute how do, how are we supposed to track people? It's like, well, you're supposed to use topics and it's been around for a couple years.
Leo Laporte / Steve Gibson (00:59:19):
So it's, you know, your fault. If you're not, it's gonna be a race, cuz that's about, you know, episode 990 or about, it'll be a race between weather. Wait, we, we have our, oh yeah. The, the, I was, I was just gonna say we have our birthday on August 19th, but that's not cor that doesn't correspond with episode 9 99. Cause that Isly it not into 52. Right? <Laugh> thank goodness. But yeah, it's gonna be a race between whether Google clobbers third party cookies or you Cloer security now, which will happen first. No one knows. Yeah. You, you can back out Steve. It's not a permanent, you know, <laugh>, I'm glad to hear you saying that. No one wants you to stop. Okay. Well, all right. We'll see how it goes. <Laugh> you have to hang well, no, I'm not making any, no, don't make, don't say anything.
Leo Laporte / Steve Gibson (01:00:11):
Just William. I'm gonna get there. No, say anything. See what happens when the time comes. Okay. So proof point release the results of their email based malware attack analysis in their report. They observed that their analysis of campaign threats, meaning, you know, malware campaigns, which include threats manually analyzed and contextualized by proof points, threat researchers. They found that the use of macro enabled attachments by threat actors had decreased approximately 66%, meaning it's dropped to one third of what it was before between October, 2021 and last month, June, 2022. And remember that Microsoft previously announced it would begin to block XL four and VBA macros by default for office users in October of 2021 for XL four, which coincides exactly with the beginning of the observed drop works in their use. It works. Yes. And also in February of this year for VBA. And as we know, there was some confusion last month by Microsoft saying, oh we're not sure.
Leo Laporte / Steve Gibson (01:01:41):
Okay, now we are again, but now it's gonna just be a documentation change. The, the, the disabling has ultimately remained in place. Thank goodness. So not surprisingly threat actors across the landscape have responded by shifting away from macro based threats, even before it had like the boom had been lowered because they knew that, you know, the way they'd been doing it was gonna end based on proof points, campaign data, since October 21 threat actors have pivoted from using macro enabled documents attached directly to, to messages, to deliver malware and have increasingly been using container files, such as ISOs and RA attachments and windows shortcut, you know, dot L K link files. So what's going on is that Microsoft blocks VBA macros based on the so-called. And I, I love this, the mark of the web, you know, whoa <laugh> which tags files based upon their source.
Leo Laporte / Steve Gibson (01:02:54):
The mark of the web identifies whether a file originated from the internet zone within their computer and the mark of the web. I just love saying that tags, the file that's downloaded, but it cannot tag files contained within other files, right? So the mark of the web can be bypassed by using a container file format, an it security company out flank <laugh> that's, that's a great name, has detailed multiple options for red teamers to bypass as it, the acronym of course is M OT w mark of the web mechanisms. And of course these techniques can be used by threat actors as well. Threat actors could use container file formats such as, as I mentioned, ISO RA zip I and I M G image files to sneak macro enabled documents into a user's machine, bypassing that flagging the container gets flagged. But of course it's contents do not. So the file system will not identify the document as coming from the web. And some of these new defenses will be bypassed. And you know, it occurs to me, Microsoft. Hello, Microsoft <laugh> are you listening?
Leo Laporte / Steve Gibson (01:04:20):
Why not mark the contents of containers? You know, you're marking the file, mark the contents. Maybe they can't cuz the, the cont the, the mark of the web is, is, is an, an NTFS property. And so you probably can't reach in, but if you watched the container being de containerized, then you know, you could get smarter Microsoft. So maybe you need to get smarter. Anyway, the cat and the mouse race continues having Microsoft finally hampering, thank goodness. The auto running of these macros by default was a huge leap forward. I'm still somewhat amazed by the amount of pushback that Microsoft received. You know, people wanna have the power without being willing to take responsibility for what having it means. So, so Microsoft finally, after decades did the right thing by simply taking that power away while providing them with ample safe workarounds.
Leo Laporte / Steve Gibson (01:05:27):
And again, I, I, I would argue Google is gonna have to do the same thing. They're gonna end up pulling the plug on third party cookies and people are gonna scream. And the good news is they will have had years to adapt their technology. So pull the plug anyway, Google, okay. Lewis who hangs out in the spin ride.dev news group. He wrote sometime between last week and this week, he said, I was surprised to hear this week that spin writes 6.1 is still using 16 bit addressing, limiting it to 64 K. And then he said I forgot the word used. And he means segments 64 K segments. He says, is this actually helpful in 2022? And wouldn't it be simpler for the code to use 32 bit addresses rather than swap between 64 K blocks. And he said, and he finished haven't.
Leo Laporte / Steve Gibson (01:06:27):
We been at 32 bits for almost 40 years. Okay. So Louis's question raises an interesting point about practical computing and computer science that I wanted to take a moment to address. So let's for a minute delve into some theoretical aspects of computer science, which not everyone may have stopped to consider. Okay. First of all, let's understand that whatever they are being used for the number of binary bits collected together, determines the number of possible states that the collection of bits can have. We might be using a collection of bits to represent a value. In which case the number of bits determines the number of possible discrete values that can be represented by that collection, or the collection of bits might be a cryptographic key. In which case the number of bits in the collection determines how many wrong keys that one, right key is hiding among, or the collection of bits might be a pointer to one object in a linear array of other objects.
Leo Laporte / Steve Gibson (01:07:52):
In that case, the number of bits in the collection determines how many discrete objects that collection of bits is able to refer to so far, it would appear that the more bits, the merrier after all what's wrong with being able to represent more values than you might need to, or what's wrong with being able to refer to more objects than you could have. In all cases, logic would suggest that there will be some minimum number of bits required to do the job, but that having unused bits would not be a problem. There are at least two problems with having unneeded and unused bits. One is power consumption, all other things being equal, and they pretty much are 32 bits consumes four times the power of eight bits. And those 32 bits consume equal amounts of power, whether they are zeros or ones, because they still need to be checked and moved around.
Leo Laporte / Steve Gibson (01:09:03):
And speaking of moving them around, whatever the bit size is that is the size of the collection. All of those bits need to be moved. They probably need to be loaded and stored from, and two main memory. But as we know, memory bandwidth has become one of the limiting and crippling factors in modern computing. Since main memory has been unable to keep up with our data, hungry processors, all manner of multi-level caching has been deployed in an attempt to decouple the slow, main memory from our super fast, super hungry CPUs. So if a CPU is using 32 bits to refer to a small collection of objects that could be referred to by only eight bits, then 24 bits out of the 32 bits of precious memory, bandwidth are being completely wasted. The CPU is only obtaining 25% of the systems possible memory bandwidth. If as in this example, 32 bits are being used where eight bits would've been sufficient.
Leo Laporte / Steve Gibson (01:10:19):
The other consequence of unused bits is the size of the program's code and data. If the code is using 32 bits where eight would've been sufficient, the resulting code will be much larger as by as much as four times. That means it takes as much as four times more space takes four times longer to load and runs as much as one quarter of the speed, since there's just so much more code bulk for the CPU to slog through. So this all tells us that the theoretical optimal number of bits to use would be just as many bits as are required, but no more. In fact, there were back in the early days of digital computer design, variable bit length computers, early serial memories, such as paper tape and magnetic tape drum and delay line did not inherently bring along any natural boundaries. So they worked well with the idea of variable bit length computing.
Leo Laporte / Steve Gibson (01:11:31):
And remember the back in the forties and fifties, this was all being invented. No one knew back then what answer would be best with what the answer would be? So who knew perhaps variable length computing was, would turn out to be the best, but when core memory was, it turned out to be far more convenient to stack the planes of core memory grids and to read out a fixed number of bits in parallel, one from each plane of memory. So it became natural for computers to load and store data in the same bit lengths as the core memory could produce and consume per cycle. And that approach of grouping data bits into bites and into words, having fixed links has stuck with us ever since. So what does this have to do with spin? Right? Spin right. Was born when the IBM PC was using the 80, 88 X 86 chip, it had 16 bit registers and 20 bits of addressing the 16 bit registers could represent 64 K different values.
Leo Laporte / Steve Gibson (01:12:54):
And 20 bits of addressing could refer to one megabyte of Ram. But back then one megabyte was so much memory <laugh> that it wasn't even standard. It was quite common for the first PCs to have 2 56 K or five, 12 K of Ram, because programs back then were small, efficient, and really didn't do very much the PC's bios Ms. Dos and all of the dos clones were, and still are today 16 bit code, and they would only run 16 bit programs yet. An incredible amount of work was accomplished by word star word, perfect vis calc Lotus 1, 2, 3, Dase, three Fox pro and many other 16 bit programs including spin right today, spin right is a 16 bit program because it's still running on the 16 bit dos operating system. And even today, I'm not unhappy about that because most of what spin right, is doing fits nicely into 16 bits.
Leo Laporte / Steve Gibson (01:14:08):
And again, as we've just seen more bits is not always better, but even back then many of those other programs were bursting at their seams within the constraints imposed by 16 bit code spin Wright. Wasn't one of them, but the PC's memory was first expanded. And then it was extended using elaborate page swapping schemes to allow data hungry tools like Lotus 1 23 to operate upon much larger data sets. And toward the end of all, that dos extenders were created to host true 32 bit programs on poor 16 bit dos doing this was an act of sheer desperation. It was the definition of clues because dos could still only run under the CPU's real mode and protected mode was required to go beyond 16 bits to true 32 bits. So the CPU was being dynamically, switched back and forth on the fly between real mode and protected mode.
Leo Laporte / Steve Gibson (01:15:23):
It was a mess, but spin right is not pure 16 bit code. It's true that it's running in real mode alongside the 16 bit bios and 16 bit dos, but spin writes 6.1, not six oh, but six one takes advantage of what must have been an inadvertent bug in the way, the very first 82 86 chips operated in which that bug has appeared in every chip since because Intel must have been worried about breaking backward compatibility. If they were to fix this bug, the bug arises from the fact that the limitations inherent in the 80, 80 eights and 80, 80 sixes real mode, which is the only mode they had can be simulated by protected mode. So the 82 86 chips and all of the chips, which have followed, don't actually have real mode, they have what amounts to a clamped down protected mode with full access to the system's IO hardware.
Leo Laporte / Steve Gibson (01:16:46):
So there are no restrictions there there're basically simulating real mode and there was always a subtle bug in that simulation. Since I've talked about this before in greater detail, I won't go into it again, but suffice to say that spin right, uses this bug to obtain 32 bit access to any machines. First four gigabytes of Ram from within 16 bit real mode code, it's kind of the best of both worlds spin right itself, remains small with most of it remaining pure 16 bit code, but when, and as necessary, it's able to directly address any memory that's accessible with 32 bits, which is for gig doing this was necessary in order to obtain the absolute, maximum possible performance from a HCI connected drives. And boy, will it be necessary for N V E under spin, right? Seven by, because it's able to read very large 32 K sector, 16 megabyte blocks in a, at a, with a single command all at once.
Leo Laporte / Steve Gibson (01:18:06):
And boy we've seen what that means, but in real mode, the program counter, which points to instructions is still 16 bits long. So code must be executed within 64 K bite blocks. And one of those is what spin right has outgrown thus now needing a second code segment block to contain its growth once spin right, six one is finished and published. I plan to immediately begin the work of recoding 16 bit spin right into true pure 32 bit code, cuz it is moving to a 32 bit operating system in order to be able to boot over U E F I so. Oh, interesting. Is it still, yeah. Is it still free to, or no because no dos will ever be 32 bit. Okay. So it's not free dos. I found a little embedded 32 bit protected mode, realtime operating system which is like a, a perfect host for this.
Leo Laporte / Steve Gibson (01:19:12):
And it, it will be able to dual boot bios or U E F I and that will just, you know, that basically takes all the limits off of what spin right. Will be able to do, you know, for example, in the future, running on all of a user's drives or a systems drives at once rather than one at a time. Oh, nice. So yeah. Yeah. That's a great, it'll be, it's gonna be very cool. So anyway, I just sort of wanted to, to, you know, just sort of touch on the reality that, you know, you know, when I hear people especially talking about 64 bits, I just think, oh really, come on. I mean, again, we're, we're, there, there really are real world problems associated with having to sh to shuffle all those bits back and forth if you don't need them. So okay.
Leo Laporte / Steve Gibson (01:20:06):
Some feedback from our wonderful listeners. Oh, and Leo you've forwarded this email to me this morning. Yes. And you saw it too apparently. Yes. Yeah, I did. Jonathan Le Shu. I, I hope I'm pronouncing your name correctly. Jonathan L E I T S C H U H. He tweeted Y two tweets yesterday. And as I said, followed up with a piece of email to the twit gang. Anyway, I just wanted to share it. He's with the open source summit. And he said, he said at SG GRC and at Leo LA port, I've been listening to at security now for years this year, I'm speaking at black hat event. Wow. And DEFCON. Oh wow. And besides LV exclamation point, he said, I learned so much from your show. I wouldn't be where I am today without it. Thank you so much for the amazing education you've provided.
Leo Laporte / Steve Gibson (01:21:07):
And then in the next tweet, he continued it's from your stories of great hackers, like T Ormond D and Dan Kaminski, and many others that I learned, the norms of vulnerability disclosure. I learned the importance of building software that is secure by default. That's nice. So Jonathan, thank you for the tweets and congratulations on, on being at black hat DEFCON as a speaker. Speaking of Dan Kaminski, I, I forgot to tell you this, but Dan's mom, Trudy was on the cruise with us. Ah, and sh you remember, you told quite a story about Dan's mom. She was quite famous defending her son. She told more stories like that on the cruise, including when he was 11, he'd been writing for computer magazines and the computer publisher, not knowing he was 11 said, I've got a big project for you. <Laugh> and his mom who was very protected, Trudy was amazing.
Leo Laporte / Steve Gibson (01:22:04):
It was really nice to meet her on this cruise. She was very protective. She said, you know, he's 11 <laugh>. And Dan was really mad at her saying, well, I could do it. <Laugh> but yeah, she was a, she was great. And she had not heard your tribute to Dan. Of course, Dan is as, as we know, passed away last year. And it's at the age of 42, it was very tragic. So her friend who brought her on the cruise is gonna play that tribute to Dan for her. Oh, good, good. But she was, I think really glad she came on the cruise. She'd been pretty depressed. And she came on and she got so much you know, adulation and and got so much out of telling her stories about Dan to the, to the group that I just thought I'd pass that along to you.
Leo Laporte / Steve Gibson (01:22:50):
It was kind of, it was kinda cool. Neat. Yeah. Thanks for joining us. And an example of what you get with with when you don't expect it on one of these cruises besides Kobe stuff. Yeah, yeah, exactly. <Laugh> oh yeah. I said what, what you didn't expect? No, yeah, I did. I kind of expected the COVID you're right. Did not expect Trudy. That's one of the fun things about meeting our audience. As you know, you've learned this, our audience is very diverse and sometimes very interesting. One of the guys on there was army human intelligence. I see. I said, what do you do for the army? He says human. I said, oh, what's that? He says, well, I do interrogations. I was at Abu grave. And I went, oh, and we had a very, we had some very interesting conversations, really fascinating stuff.
Leo Laporte / Steve Gibson (01:23:34):
Very cool. So just some super smart, talented, interesting people. So as you know, it's always fun to go on these yeah. Meetups and trips and so forth because, oh, and Laura and I had a ball when we were out out that's right. Traveling around, you know, meeting everybody. Oh, people love you. Yeah, of course. So Alex Naja Nehouse ne yeah. We know, we know Alex. Well, yeah, we know him. Well, a great friend of the show the very first sponsor that this podcast is had exactly right. Thank you, Alex. He said, he said, I especially enjoyed your, and Leo's Merth at the astonishing at the astonishing flaws in the MV seven 20 in episode 8 81. He says, I worked in China in the mid nineties. This doesn't surprise me. It's a cultural thing. A fundamental business drive to maximize profit by cheapening the product <laugh> to which I say, well, God help us.
Leo Laporte / Steve Gibson (01:24:35):
That's <laugh> mark OJ. He said, hi, Steve longtime listener here, love your show. Just wanted to drop an information that there is an open source version of tail scale that is called head scale. That's kind of clever head versus tail. Seems good. Alternative to the paid version available here, and a link to it at GitHub. So head scale, is it? And I just wanted to pass that on because there is a community supported tail scale, but they're, they're pushing people to, to subscribe. And I would, I would also head toward the free one. Someone tweeting as a Henning said, dear Steve, just listen to GRC. Okay. He said a GRC 8 81. He means SN close enough, 8 81. Yeah. Yeah. And your criticism of the way Microsoft implemented the protection against brute force password guesses, he's said Peren allow 10 failed logins then Ben and ban any logins for 10 minutes, then allow 10 failed logins again.
Leo Laporte / Steve Gibson (01:25:43):
And so on. You asked why Microsoft did not block the logins indefinitely. And frankly, once he said it, I was like, duh, of course he says, and this is my answer because I designed a login system for our university's web applications that works the same way. If we, we would block accounts, then it would be easy for anyone of our aspiring computer science students to produce a small script that locks out all of our users, of course, Uhhuh, oh, in one night. So just by attempting failed logins, that's right. You could lock everybody out, completely prone to abuse. See you and I, but this is a problem. All security has we, we didn't, we didn't think evil enough. We did not think evil. Yeah. Yeah. You're right. Yep. So, wow. Anyway, thank you very much. And, and to the other, a number of our listeners said Steve, you know what the problem with that is? It's like yeah, I do now. I mean, yeah, thank you. <Laugh> now many of our S X K C D following listeners sent me the following graphic. I've got it in the show notes. And it's, it's cute. And it's, and so this is just classic XK, C D it, the, the, the little picture is titled energy tip increase the security of your home power supply by installing an air gap. <Laugh> yeah. Now I get it <laugh>.
Leo Laporte / Steve Gibson (01:27:25):
And so it shows the cord coming in from the right to a flood lamp, which is aimed at, and maybe like about a foot away from a solar panel that then has a cord coming from it to a little box, presumably, an inverter that, that turns the DC back of the AC and off it goes. And of course I loved the concept. It's funny, but the engineer in me immediately is appalled by the inefficiencies. You have inefficiency converting the electricity to light. You have the inefficiency of the light escaping in all sorts of directions. I mean, we can see the light bulb shining here from the side, so that's bad. Then we have the inefficiency that's inherent in solar to DC conversion and the inefficiency of a DC to AC inverter. So, yes, I know I'm being far too pedantic, but I would not have my home air gapped for that reason.
Leo Laporte / Steve Gibson (01:28:29):
I don't think he's serious. I think it's serious. No, no, no, no, just it's a, it's a wonderful cartoon. So thank you again. X, K, C, D. You've provided us with many moments. Richard, somebody who's, who's got his name as Richard C with five syringes and the word flu in his Twitter name. He, he liked our mention last week, and this is another bit of Merth from us, Leo about this crazy Microsoft printer, weird cloning copy creation. And I didn't include it in here, but he mentioned he had a long tweet that went with this picture showing brother MFC J 9 85 DW printer, and then another identical one pers copy one. And notice that it's the second one that has been set to default. Yes. He solved it and yes, he, he, he noted that exactly. This happened for reasons.
Leo Laporte / Steve Gibson (01:29:28):
He was never able to figure out now he knows the, the real one stopped working, the copy worked and he said, okay, fine. He fixed it the way most people do. I'll just use that one. <Laugh> it's like, oh, okay. Wow. Oh, that's Klugy. Yeah. Someone tweeting as hve wear said at SG GRC, a little pushback on your windows, OS being creaky and brittle, he says, take a look at elevens settings controls no longer are they a thin veneer over ancient code? They are beautiful. E they are a beautiful evolution of the venerable property sheet control top to bottom credit to Ms. Where credit is due. Okay. So after reading this tweet and wanting to include it in the podcast for the sake of balance, I would like to be balanced. I, I thought I might have missed something. So I fired up a virtual box VM, where I keep an instance of windows 11, because you know, it's not actually good for anything.
Leo Laporte / Steve Gibson (01:30:36):
And I went over to these settings controls after waiting for it to update itself, somewhat endlessly, much like Kirk on the bridge. I was unable to go to warp drive or warp speed. So anyway it looks, first of all, exactly like windows 10, perhaps I missed what hve wear was referring to. But I beautiful. What are you talking about? It's beautiful. It's beautiful. Just like windows 10, just like windows 10. So, so I poked around and actually it was your, your discussion with Paul from last week, Leo, that led me to the control panel for sound. It looks exactly like what we had, perhaps as far back as windows 3.1. <Laugh> at nothing. It is in fact, the old control panel. You nailed it. Yes, it is. It is the pro old property sheet control. Yeah. Yeah. Or go to internet options.
Leo Laporte / Steve Gibson (01:31:34):
Dialogue. It's the same. Yeah. As we've had forever. Yeah. Or the device manager, the same as we've had, and I could go on and on. So, you know, he says no longer, are they a thin veneer over ancient code? Well, I think that's precisely what those ancient dialogues are. Look at these, this is his story. I know. I mean, nothing has changed. This looks like, say XP. They are ancient code. Yeah. And I think that's great because those are the parts of windows that still work. Right. Most reli. In fact, when you wanna change user settings, you don't want the thin veneer crap. No, the Microsoft is no given us the, you want the old school. Yeah. You don't want something that looks like a webpage. You don't want this. No, <laugh> no, you don't. You don't. You want the old school. In fact, many people have learned with the command is to open those old user property settings, you know?
Leo Laporte / Steve Gibson (01:32:35):
Yeah. So anyway, I did, I didn't mean to dish on H but I just, you know, I thought, okay, wait, am I missing something here? Is that did maybe 11 did change everything? And I just haven't dug in deep enough, but no, it's still windows three, one with, you know, I mean, it doesn't have the same borders and the same, you know, colors. It's got rounded corners now come on. And for what it's worth again, I'm happy that they're leaving the stuff alone. That works. Yeah. Because for that reason it works. Okay. I noted URA on the bridge behind behind Kirk at the top of our show notes. And I just wanted to make a mention of her passing this past weekend, Michelle Nichols at age 89 passed. And of course she was O Herra through the, all of the original three short years and all six feature length films and the bridge would not have been the same without her.
Leo Laporte / Steve Gibson (01:33:46):
Mm-Hmm <affirmative> we have previously lost Spock Leonard bones, McCoy, Scotty, and nurse chapel Kirk and checkoff and Sulu are still with us and will keep our fingers crossed that they, that they keep going for a long time. So, you know, what an incredible legacy there was, there was a, a book, I guess I read two of them. It was called the enigma cube and that enigma something there, there were two of them. Anyway, there was a, there was a funny little bit there where, where some, I'm trying to remember how it was about, about time travel. And somebody saw a really, really very gifted physicist was confessing to some friends, like in the far future that he really liked this really cheesy science fiction series that, you know, was, he felt was really beneath him. And it only had three seasons and it was called star Trek.
Leo Laporte / Steve Gibson (01:34:51):
And he was sure that nothing was ever gonna come of it, but, you know, he liked it anyway. And of course the joke was that yeah, you know, it isn't like it's still spawning new series, even that even today in, in 2023. So and also Leo, I wanted to mention I think we talked about it on the air last week two series the dropout on Hulu and we crashed on apple TV. I really enjoyed them. And for those who don't know the story of Theranos, a very young female Stanford university, undergrad who basically wanted to achieve Steve jobs, style, success, and, and apparently who believed that all she needed was to want it badly enough decided that being able to perform hundreds of blood screening tests, given a single pin prick drop of blood from a user's finger would change the world.
Leo Laporte / Steve Gibson (01:36:01):
And of course in that she was correct. You know, that certainly would've changed the world, but she was wrong in her belief that all she needed to do was wanting it badly enough. And, you know, she had, believe it or not, no education or training in the science that would be needed to realize her dream none at all. There was never any reason to believe that it was possible. And there was a lot of reason to think that it wasn't, but those pesky details didn't give her any pause. Now being a bit of a biohacker myself and being somewhat enthralled by this presentation. I was interested in, in a couple things, I, I wanted to know how accurate this series was. And I was interested enough in the blood testing technology that this Elizabeth Holmes and her Theranos were attempting to commercialize that I followed up by watching, you know, as much as of the various YouTube clips from the time and subsequently as I could, that is, you know, the real, the real stuff, cuz everything's on YouTube now.
Leo Laporte / Steve Gibson (01:37:13):
And I even did some research in the us patent and trademark office to get some sense, as I said, for how accurate its portrayal of these events and characters was, well, it was based on the podcast. So, you know, it's accurate because it, the dropout was based on a podcast, right. As was we crashed by the way they were both came from podcasts <laugh> oddly enough. So for anyone else who may be interested or curious, given the available public record, everything yeah. Portrayed in the dropout was astonishingly accurate. It was well researched, right? Yeah. Oh my God. Right down to the lighting used to shine off the cornea of Elizabeth Palm's eyes. Yes. I noticed that. Yes. <laugh> in a series of memorable closeups. Yes. I even found a multi page document, which dissected the Edison mobile lab machine that they were never able what they were never able to get to work.
Leo Laporte / Steve Gibson (01:38:18):
What was clear was that even if it had worked, it would never have been able to achieve what they were promising. Yeah. That the in, in, in the series that we saw in the dropout, the original science, the scientists who, who were working on the original concept ended up, you know, leaving the company through various reasons and their work was discarded and basically a robot glue dispenser was, was used to, to replace this thing. And it was downhill from there. Yeah. But for anyone who's interested, if you haven't seen it, I, I really enjoyed it. I, I recommend it. And, and, and we crashed, I thought was equally good. You know, both our and I, and you and I, Leo were talking about this before the show. I think you and I particularly, and other people in the industry would be drawn to this because we've seen this over and over and over.
Leo Laporte / Steve Gibson (01:39:26):
Right. I mean, the, you know, it, it is the Steve jobs personality type that is able to bring apple back to life from the dead. I mean, remember how close it was to being gone and it, and to create the, you know, these things, I mean, you know, sketchy as Elon has become, when you see those rockets come back to earth and land it's like they work, oh God, they work it's astonishing. And you know, it takes people who have this kind of personality. I thought that we, we crashed was mostly at a, a, a demonstration of that personality. Oh, I agree. Yeah. To me it was less. Yeah. Yeah. And well, cast boy. Oh, is he good? That guy, Jared letter, he was a so good. Yeah. Oh, just fabulous. Very believable. Yeah. Yeah. Yeah. I think this is both are indictments of that Silicon valley culture where you can raise a lot of money based essentially on hype and you know yes.
Leo Laporte / Steve Gibson (01:40:29):
And, and charisma. Yeah. And, you know, and the, and the venture capitalist certainly know that for everyone that succeeds big 20 die horribly. Right. And, you know, and, and burn up a lot of cash and, you know, BMW leases are, you know, are, are, you know, ended and blah, blah, blah. You know, I mean, massive amounts of money gets burned through. Oh, yes. What was not clear to me about we crashed is the timeline. I think they, they didn't succeed in, in showing us that this was a 10 year span. Right. Because you know, it was crammed into eight episodes. Right. So somehow I missed the, the sense of, of that time that went by, which I think would've, you know, was sort of missing from that. I don't know how you do it. I mean, they, they, they, they kept flashing years up on the screen, you know, the, the date, but it didn't, but they didn't convey the, the, the time that was taken.
Leo Laporte / Steve Gibson (01:41:27):
But anyway I, I recommend both without without hesitation, if you're interested in this idea of, you know, fundraising personalities, it's not the way I operate. I, when I was creating the light pen, I built one and got it to work. And then I built like 12 and I sold them and I took the money from those and built a hundred and sold them and took the money from those. And, you know, yeah. Bootstrapping the old, the old fashioned world, very old school. Yeah. Which is the way jobs in Wosniak started in the beginning with that apple one. Right. I mean, right. You know, they, they got the bite shop to agree, to buy some, and they, who knows, they probably got a down payment from him. And then they did used that in order, in order to bill was a famous phone call, Steve jobs make to get the parts on credit, which no one would've given this, you know, hippie kid <laugh>, but somehow he was a good talker.
Leo Laporte / Steve Gibson (01:42:24):
He really, he, in some ways is the prototype for both Adam Newman and Elizabeth Holmes. Right. Well, he was, he was clearly Holmes's inspiration. She talked about it. She went to the black turtleneck. Yes. Yeah, yeah. Good TV too. And that's, I think the other side of that, it's both entertaining shows. Yeah. Yeah. Really good. And really well produced. And I will close before we talk about our, our show topic with an observation that win amp has released is about to release. Well, it it's released a, a release candidate after four years in development. And I don't recall what caused me to mention win amp last. But when I did, I remember at like adding something like win amp really <laugh> and I was immediately scolded by a number of our listeners who said, Hey, I'm, I'm still using it. It's the best media player ever created by man.
Leo Laporte / Steve Gibson (01:43:26):
Yep. And, you know, I can certainly respect that since I've created a few things that others regard as the best ever and they've been around for quite a while. So I just wanted to give our Intrepid die, hard, win amp fans. The news that after four years of development, the first new release candidate of win amp has been released. Lawrence Abrams over at bleeping computer was where I learned of this. And basically they've spent all of this time moving the code from visual studio 2008, which by the way, is what I'm still using. Cuz it works great to visual studio 2019. They now have it under 2019. So future movement will be easier. He wrote win amp sees development after version 5.6, six, six, Ooh, that's the wrong word? That's that's the wrong place to stop was, was released in 2013. And he says, that was until October, 2018 when win amp 5.8 was leaked online and the developers decided to publish it themselves on the win amp.com website.
Leo Laporte / Steve Gibson (01:44:41):
And I think it was that leakage online. That must have been the reason I mentioned it previously. Cause that seems about like 2018 about the right timeframe. And he said since then a developers have promised an updated version with cloud streaming support and more modern features. Oh it looks just wonderfully funky still. They Lawrence has a screenshot of it and it's oh, it's, it's so retro that it just warmed my heart. Leo. Anyway, finally in November, 2021, he said the win amp.com website received a facelift with a new logo and a beta signup form to be notified with new versions were released last week, win amp 5.9 RC one build 9, 9, 9 was released marking it as the first version released in four years, that has the first release candidate after the revitalized of the revitalized media player while the win amp release candidate does not contain too many changes.
Leo Laporte / Steve Gibson (01:45:39):
The main goal of this release was to upgrade the code base from visual studio 2008 to 2019. Now though this has been completed, the team can add new features and capabilities to the media player. So anyway it's win amp is not dead. It's been, hasn't been moving a lot lately <laugh> but there's still life. There's still life left in it. Not dead yet. Looks like there will be. It's just a flesh wound. Just a Les wound. That's right. No, I think it's really cool. And it's, it's a great product. It has been for years. Yeah. Yeah. All right. RO Hammer's nine lives coming up, but first a word from our sponsor. I have a soft spot in my heart for this company for a couple of reasons. One they're in Ukraine and they, and they're still cranking out the best software Grammarly.
Leo Laporte / Steve Gibson (01:46:31):
I'm talking about just doing a great job. The, the tool that everybody who writes, whether it's emails or papers or novels should have. The other reason I love it is it's one of the best examples of what you can do in lisp. I mean, I think there's other languages involved now in the front end and so forth, but, but the fundamental AI was has always been done in lisp. I love Grammarly and I'm happy to use it. I'm a happy longtime Grammarly customer. So is Lisa. We all, you know, communication is the most important thing I tell. I tell my kids this, you know, you, you, whether you're a scientist or a salesman whatever you're doing, it's all about ultimately it's about communication and being able to write clearly to express your ideas clearly is, is so important for your success for your future.
Leo Laporte / Steve Gibson (01:47:23):
But it's also important for how you think, because it's really important part. I I'm sure you agree with Steve on this important part of the thinking process is putting it. You say putting pen to paper, although these days it's putting pixels to screen, but it's the same idea, putting it down makes a big difference. Grammarly is there to make your writing fast, simple, and most importantly clear. It's an all in one writing tool. It's not a spell checker. It's not a grammar checker despite the name it's, it's really there to help you create clear, concise communication and do it faster and easier than ever. And I, that could be anything from emails to boardroom presentations to contracts. It helps you find the right words to communicate efficiently. Lisa uses it because, and, and this is a really perfect use for it. It also analyzes tone.
Leo Laporte / Steve Gibson (01:48:18):
Okay. So she writes a lot of emails and she's a very busy person. She's a, she's a CEO and like a lot of very busy CEOs. Sometimes her tones can seem a little Brus cuz she's just writing the answer clearly. And Grammarly's great to say, well, that's, you know, that's nice. Maybe would you maybe like to soften it a little bit or gives it some her ideas to make it more friendly? And she really appreciates that. And because it's a computer program, not a human like me leaning over her shoulders saying, well, what do you mean there? It's easier to take those suggestions and incorporate them. It's a desktop app. You can actually try it right there on the website if you want. But it's a, you can use it as a plugin, as a desktop app. It works wherever you do anything that you're entering text in Grammarly can be there to help you.
Leo Laporte / Steve Gibson (01:49:04):
Whether you're trying to nail a, a perfect cold pitch. In fact, for email Grammarly's tone detector is absolutely free, which will help you make the right impression. Not too much, not too little, just a little bit of, you know, tone. You've got ideas in your head. Putting those ideas into words can always be a little complicated, especially as you're writing really fast. Sometimes things get a little tangled with Grammarly premium. You can clear up that confusion with clarity focused sentence, rewrites Grammarly. It's kind of amazing because it's AI under kind of understands what you're trying to say and says, you know, if you said it this way, it might be a little clearer. It untangles those thoughts, which helps you understand better. What you're trying to say too. Grammarly premium's tone transforms also can help you convey confidence establish a tone, a mood. I just think Grammarly is an amazing tool.
Leo Laporte / Steve Gibson (01:50:02):
I want you to try it. You can try it right now for a free account. Go to grammarly.com/security. Now G R a M M a R L y.com/security. Now I, you know, I wanna support 'em cause I think they're making a great product and they're doing it under a lot of duress in Ukraine. So when you're ready to upgrade a Gramly premium, you get 20% off just cuz you're listening to security. Now, 20% off, get to the point faster, write better, accomplish more with Grammarly, a really great tool. Absolutely. At least try it on the webpage than maybe install the free version. Eventually you're gonna want premium. It's really worth it. And 20% off when you go to grammarly.com/security now G a M a R L y.com/security. Now great product from really talented coders. Yeah, they're right. And li okay. I just, you know, I like to see that <laugh> actually, it makes total sense that they would it's AI list, right?
Leo Laporte / Steve Gibson (01:51:03):
It's what you, it's the right language for that. I completely agree. Yeah. Grammarly thats less security. Now go ahead. You're you're talking about the, about the importance of language and one of those sort of conversations you have in college, you know, like along with the meaning of life, right. Is okay. We, we think in the language that we speak, you know, that's the way we manage our own thoughts and the way we, we process reality. Mm-Hmm <affirmative> so that means that the thoughts we have need to be expressible in the language we speak. So to what degree does our choice of language constrain? What we're able to think. Yes. And as that'll, you know, that'll keep you up late at night. It's like, wait a minute. You mean, I can't think of anything I want, no, you can only think what you're able to express in your language.
Leo Laporte / Steve Gibson (01:52:04):
One of the things that great, no Chomsky who is very, is very important for a computer science, but he, he is was a philosopher of language. Gosh, he's 90 now I'm seeing yeah. <Laugh> wow. But great philosopher of language. And that was one of the things he was always intrigued by is how much of the language you use, how much of what you think is informed by your choice of language? I think it's, it's a fascinating, yeah, fascinating. So yeah. Yeah. Okay. yes. RO hammer is back alive in kicking. Not only is win amp, not dead <laugh> but neither is RO hammerer. Well, there you go. And it really shouldn't surprise. It really shouldn't surprise any of, of us by now the, the principle we've seen and learned over and over in context after context is that mitigating and I've, you know, quotes, mitigating a security flaw is not the same as fixing it and security flaws turn out to be stubborn.
Leo Laporte / Steve Gibson (01:53:07):
Things. All we need, you know, to do is, is to look at the continuing saga being brought to us by specter and meltdown, you know, where the discovery of fundamentally exploitable flaws arriving from the advanced performance optimizations, which have been deeply built into modern CPUs, which can be used to leak secrets across process isolation boundaries. And, and we see an example of a family of flaws that similarly refused to die. And as we know, another completely unrelated yet still fundamental flaw was discovered years ago. And we talked about it at the time in the operation of today's dynamic, random access memory security researchers discovered that modern memories. This is DRAM memories. You know, main memories of our systems had become so hyper dense with every possible margin engineered out that adjacent rows of bits, which were of course supposed to be completely independent of one another were in fact often able to interfere with each other and being the super clever engineers that they are.
Leo Laporte / Steve Gibson (01:54:34):
These researchers figured out how to turn the resulting spontaneous bit flips that could be induced to occur into active and effective security exploits. I mean, I just, you know, the, I, the idea of leveraging a, a hardware anomaly like that into a security exploit, I mean, that's just, just genius. Of course the DRAM manufacturing industry responded, but not by reducing the storage density of Ram back down to where there would be sufficient noise immunity to prevent adjacent row interference. Oh no. It responded with a wait for it. Mitigation of the problem by making the memory system still more complex by selectively refreshing the endangered rose of DRAM, which surround the rose, which might be causing interference, whether that interference was deliberate or accidental, this was named target row refresh or TRR is now built in to DDR for Ram. So, you know, you're in trouble when D Ram is the subject of an apparently endless series of CVE worthy exploits.
Leo Laporte / Steve Gibson (01:56:07):
There was the original RO hammer. Then we had D rammer, which was the double RO hammerer, then Ram bleed. Then spoiler, then trespass with TRR. So two trespass, and then the last year's blacksmith, it's been a never ending parade. And now having not yet used up its nine lives, we have the less glamorously named half double attack. The name of this latest attack comes get this from a crochet stitch, which is taller than a single, but shorter than a double <laugh>. I know the point is the actual fundamental problem of DRAM activity, noise immunity being too low was never addressed in case after case, since the cost of treating the underlying disease was too high. It would've meant backing off on DRAM storage density instead of treating the disease one symptom after the next has been treated so today, even the most recently engineered DRAM has remained diseased with some fancy patchwork added in an attempt to shore up its fundamental problem.
Leo Laporte / Steve Gibson (01:57:36):
I name today's podcast RO Hammer's name lives because this problem, as I've said, refuses to die. These amazing researchers are back having almost not surprisingly worked around the most recent iteration of RO hammer mitigations their paper, which will be delivered during the same used Nick's security conference next week, where D where the TLS anvil will be shown is titled half double hammering from the next row. Over the abstract of their paper explains. They said row hammer is a vulnerability in modern DRAM where repeated accesses to one row. The aggressor give off electrical disturbance whose cumulative effect flips the bits of an adjacent row of the victim. Consequently Roe hammer defenses presuppose the adjacency of aggressor victim pairs, including those in low power DDR four and DDR four most notably TRR that's the target row refresh in this paper, we present half double, an escalation of row hammer to rose beyond immediate neighbors using half double.
Leo Laporte / Steve Gibson (01:59:07):
We induce errors in a victim by combining many accesses to a distance two row with just a few to a distance one row. Our experiments show that the cumulative effect of these leads to a sufficient electrical disturbance in the victim row inducing bit flips. We demonstrate the practical relevance of half double in a proof of concept attack on a fully up to date system. We use side channels, a new technique. They invented called blind hammering a new spraying technique and a new specter attack in our end to end half double attack on recent Chromebooks with error, correction, code ECC and TRR protected, lower power DDR, four memory. The attack takes less than 45 minutes on average. And as I mentioned, they root. So what these guys have figured out is sheer brilliance. They came up with a way of turning the target row, refresh RO hammer mitigation, which is now present in all of the latest DDR four drams against itself.
Leo Laporte / Steve Gibson (02:00:43):
They've figured out how to use TRR to induce the problem that it's designed to prevent <laugh>. Here's how they described what they accomplished. They said RO hammer is a widespread DRAM issue caused by the unintended coupling between its constituent rows by repeatedly accessing one row. The aggressor an attacker can corrupt data in adjacent rows the victims by accelerating their charge leakage as a powerful means of bypassing hardware and software memory protection, RO hammerer has been used as the basis for many different attacks. Previously RO hammerer was understood to operate at a distance of one row. An aggressor could only flip bits in its two immediate neighbors. One on each side, this makes intuitive sense as a coupling phenomenon, the RO hammer effect should be the strongest at closest proximity. Indeed. This assumption underpins many counter measures which have been proposed against RO hammer, especially the ones that rely on detecting aggressors and refreshing the charge in their intended victims.
Leo Laporte / Steve Gibson (02:02:12):
In fact, target RO refresh TRR, a productionized counter measure, widely deployed as part of low power DDR four or standard DDR, four chips falls into this detect and refresh category. In this paper, we present half double, a new escalation of RO hammer where we show its effect to extend beyond just the immediate neighbors. Using half double. We are able to flip bits in the victim by combining many accesses to a far aggressor at a distance of two, with just a few to a near aggressor at a distance of one, both aggressor distances are necessary accessing just the far aggressor does not flip bits in the rows in the row. That's two away, whereas accessing just the near aggressor devolves into a classic attack that's easily and is mitigated based on our experiments, got a load of this. The near aggressor appears to act as a bridge transporting the RO hammer effect of the aggressor onto the victim.
Leo Laporte / Steve Gibson (02:03:42):
Concerningly tr R actually facilitates half double through its mitigative refreshes, turning their recipient row into the near aggressor. That co conspires with the far one that necessitates the refresh in the first place. It's just, it's just brilliant in effect. They wrote the cure becomes the disease while they said, while the discovery and evaluation of half double is the main contribution of this work. We also demonstrate its practical relevance in a proof of concept exploit. However, and boy did, they have to work to do this current systems limit the attackers control, introducing four challenges, all which they had to overcome. First, the adversary needs to allocate memory contiguous in a DRA bank. However, without access to physical addresses and huge pages, we have to introduce a novel approach combining buddy allocator information with a DRAM timing side channel to reliably detect contiguous memory. Second challenge ECC protected memory can make bit flips unobservable depending on the victim data, which the attacker does not control.
Leo Laporte / Steve Gibson (02:05:18):
The adversary cannot template the memory like in previous RO hammer attacks since hammering requires knowledge of the cell data as the state of the art does not solve this problem. We introduce a invented and introduced a novel technique called blind hammering to induce bit flips despite the error correction ECC mechanism of LP DDR four third challenge to overcome reduced address based sizes on recent arm based systems break the page table spraying mechanism from previous attacks. Therefore we had to develop a new spraying technique that is still unmitigated and forth challenge without temp planting. We need an Oracle telling whether RO hammer in, in induced an exploitable bit flip without crashing the exploit for this. We in invent and introduce a novel approach using a spec based Oracle for explore for exploitable bit flips.
Leo Laporte / Steve Gibson (02:06:28):
And here it is, they said, we combine all of these techniques into an end to end successful proof of concept. The half double attack, which escalates an unprivileged attacker to arbitrary system memory reads and right access. In other words, full kernel privileges. The half double attack runs within 45 minutes on a fully updated Chromebook with TRR protected, low power DDR for memory. And they finish we summer to summarize, we make the following contributions. First, we discover a new RO hammer effect, half double and evaluate a set of devices and modules for susceptibility. We perform a thorough root cause analysis to empirically proof that TRR is responsible for the half double effect. We analyze the stop gap mitigations present in today's systems and show that with a new exploit using half double, we can bypass them and build an end to end. And our end to end half double attack runs on up to date, Chromebooks and combines the half double effect with exploitable techniques, side channels and a specter attack.
Leo Laporte / Steve Gibson (02:08:08):
So the moral of our story is responding to fundamental exploitable design flaws with mere mitigations only delays the inevitable. I expect that DDR five DRAM will learn the lessons of the half double attack to render, to render it too less effective by further complicating our DRAM. Maybe that will be the end of it. Or maybe DRAM and RO hammerer will turn out to have still more life left in it. Do you maybe would you say maybe that you should eradicate not mitigate? I don't know if that makes sense. <Laugh> it rhymes? Hey Leo, great marketing term. You could raise some money with that eradicate don't mitigate, mitigate, eradicate. That's right. I'm good at writing ad copy. That's that's my only skill that would do it. So anyway, RO hammer still with us and boy so clever to be able to use the previous hardware mitigation in order to facilitate the next generation attack.
Leo Laporte / Steve Gibson (02:09:30):
<Laugh> Gumby says Leo, leave the sloganeering to the pros. Okay. I will. <Laugh> Steve Gibson. You did it again as you do every Tuesday on security. Now thank you so much for being here. This is of course the one and only show you have to listen to every week, just to keep up with in the fast paced world of bad guys. Steve is@grc.com. That's the Gibson research corporation. There you'll find his bread and butter. His life's work, the mass storage, the UBA, mass storage, maintenance recovery utility in the world's spin, right? 6.0 currently somebody in the discord was saying, when is 6.1 coming out? And I told them when it's done, not one minute sooner or later. So you'll find if you subs, if you right now, if you buy 6.0, you'll get 6.1. When it comes out as a free upgrade, you can also participate in this development.
Leo Laporte / Steve Gibson (02:10:29):
It is awfully close. Now I have a feeling I feel like, but you're right. Not to say it. No, don't don't don't wanna can't Nope. Can't Nope, Nope. It's tempting. I know, but Nope. If you're at grc.com you'll note, there is also a, a place where you can get besides all the other great stuff. This podcast, Steve has 16 kilobit audio versions. That's unique to him. And he also has the transcripts written by Elaine Ferris. Those are very, very useful if you like to read along while you listen, but also if you wanna search for something, you can search the transcripts and go right to that part of the show. Also 64 kilobit audio as well. That's at grc.com. Leave feedback for Steve there at grc.com/feedback or on his Twitter. He's at SG GRC on Twitter. His DMS are open it's worth following him to keep up on the latest.
Leo Laporte / Steve Gibson (02:11:20):
We also have a copy of the show at our website, twi.tv/sn audio and video available on our site, or subscribe in your favorite podcast client. You'll get it automatically. The minute it's available, there's even a YouTube channel. If you, if you hear something and say, I gotta send this to the boss or to the it department, you could, it's easiest way to probably send a clip is to go to the YouTube channel. And then you could just snip out that little part and send a link to them. If you are a member of club TWI, of course you could add free versions of the shows. You also get the fantastic club to discord where the party goes on seven days a week. You also have the trip plus feed coming up. Some exciting events, April 18th, I'm sorry. August 18th. We've got Alex.
Leo Laporte / Steve Gibson (02:12:03):
Lindsay's ask me. Anything is AMA is at 9:00 AM Pacific on the 25th, the following week Stacy Higginbotham am Pruitt and I will do the Stacy's book club Clara and the son, if you haven't read it yet, you got a couple weeks, three weeks. Hurry up, read it. Now it's a, it's a great book. So if you wanna join the club, go to twit.tv/club TWI and thanks in advance. It's a big help to us. All. We will be back here as we always are next Tuesday, one 30 Pacific, four 30 Eastern, 2030, UTC for security now. Thanks Steve. Have a great week. We'll see you next time. See you my friend.
Rod Pyle (02:12:46):
Hey, I'm Rod Pyle editor in chief at AD Astra magazine. And each week I joined with my co-host to bring you this week in space, the latest and greatest news from the final frontier. We talk to NASA chiefs, space, scientists, engineers, educators, and artists. And sometimes we just shoot the breeze over. What's hot and what's not in space, books and TV, and we do it all for you, our fellow true believers. So whether you're an armchair adventure or waiting for your turn to grab a slot in Elon's Mars, rocket, join us on this weekend space and be part of the greatest adventure of
Rod Pyle (02:13:15):
All time
Speaker 3 (02:13:17):
Security.
Speaker 4 (02:13:18):
Now.