Security Now Episode 869 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for Security Now. Steve Gibson is here with an acronym soup, including do D's new D I B VDP program. We're gonna talk about open SSF and then a simple way to tell the world you don't wanna be tracked. And this time it really works. You can stay tuned. I hope for this one. It's all coming up next on Security Now, podcasts you love from people you trust. This is TWiT. This is Security Now with Steve Gibson episode 869 recorded Tuesday May 3rd, 2022 global privacy control. Security now is brought to you by PlexTrac the proactive security management platform that helps you focus on winning the right security battles with PlexTrac. You'll streamline the full workflow from reporting to remediation. Visit plextrac.com/twit and claim your free months and by bit warden. Get the password manager that offers a robust cost effective solution that could drastically increase your chances of staying safe.
Leo Laporte (00:01:11):
Online. Get started with a free trial of a teams or enterprise plan or get started for free across all devices as an individual user at bitwarden.com/twit. And by ITProTV, give your team an engaging it development platform to level up their skills. Volume discounts. Start at five seats, go to itpro.tv/securitynow, and make sure to mention SN 30 to your ITProTV account executive to get 30% off or more on a, a business plan. It's time for Security Now the show every Tuesday, that answers the vital question. What the heck? And here's the man with the answers to all your questions, Steve Gibson what could possibly go wrong is actually the that's could possibly, yeah, that's a, that's really, that's the question you really, really do answer Steve from grc.com. Hello, Steve. I have sort of a blast from the past some good news.
Leo Laporte / Steve Gibson (00:02:14):
This is security now episode 869 for this is our first episode of May, 2022 titled global private, and the subtitle is hope Springs, eternal. I'm hopeful. That's my nature. I've always been hopeful. I, I refuse not to be hopeful. Why not have hope? Anyway, this is rather than a ton of little time topics, it, the way it turned out that we have a, a, a number of bigger topics, we're gonna examine the success of the abbreviation overloaded DDS, D I B V DP pilot program. Boy, the government loves their initials. We're gonna introduce the relatively new open SSF, the open source security foundation with the introduction of their first project, which is they called a package, a project. We're gonna look at some hopeful new privacy legislation recently passed in Connecticut's house, which if signed into law would allow it to join four other existing privacy, progressive states among which California and Colorado number that now they called.
Leo Laporte / Steve Gibson (00:03:39):
They're be considered the three CS, Connecticut, California, and Colorado. And we're gonna talk about that. We're also gonna look, I got a kick out of this. I don't, someone must have tweeted this to me Moxie, Marlon spike, who of course famous for being the, the lead designer of a signal messaging platform. He developed his own port knocking solution to a decade ago, and I just, I loved, he asked himself at the end of, of his page on GitHub about this. Like, why do you even need this? And I know that everyone will get a kick out out of his answer. We've also got a bunch of listener feedback, and then we're gonna talk about what global privacy control is and why this time might be different. So I think another great podcast for our listen. Excellent. Very excited.
Leo Laporte / Steve Gibson (00:04:39):
Before we get a, into this let me take a little time out for our first sponsor of the show PlexTrac. We talk about 'em all the time, the purple teaming platform it's a proactive cybersecurity management platform, if you want big words, but what it really does is it helps your security teams get their job done with a minimum of, you know, must fuss bureaucracy. They could focus on finding the flaws and remediating them without focusing a lot on writing reports and all that stuff. If you're ready to gain the benefits of a purple team, but have no clue how to get started, maybe you want to secure your security posture, but you're having a hard time optimizing it efficiency and facilitating collaboration within your teams. This is a great solution for you. And if you are on the front line, if you are where the rubber hits the road, if you're one of those security team members, you're gonna really want PlexTrac because it takes the busy work out of your job and puts the fun back in PlexTrac is a powerful, yet simple cybersecurity platform that centralizes all the security assessments, all the pen test reports, all the audit findings, all the vulnerability tracking, and then makes it really easy to write reports, to work, to collaborate, to get them remediated.
Leo Laporte / Steve Gibson (00:06:02):
It really transforms your risk management life cycle because your security teams will generate better reports faster with less aggravation. They can aggregate and visualize analytics and they can collaborate on remediation in real time, all through the PlexTrac, the PlexTrac platform addresses pain points across the spectrum of security team workflows and roles for, and I'll tell you about some of the modules. There is a number of 'em, but the reports module is really the thing that you'll use probably most often to report your security findings. You could put code samples in and embed. 'em Very easily screenshots videos. You can import findings from all the tools you use, all the scanning tools. You can export to custom templates with a click of a button. We use existing templates. Once you've got a template, it makes the reporting much, much easier, not spending a lot of time typing.
Leo Laporte / Steve Gibson (00:06:51):
You're spending more time testing. There's a runbooks module. You'll love cuz it facilitates all your tabletop exercises and red team engagements. You're breaching attack simulations, your purple teaming activities. It'll improve communication and collaboration, PlexTrac upgrades, your program's capabilities by making the most of every team member and tool. And again, taking out the busy work. So they really can focus on the stuff that really matters. There's also an analytics module. You'll really appreciate this cuz it helps you visualize your security posture so you can quickly assess and prioritize, which creates a more effective workflow. You can map risks to frameworks like Mir attack to create a risk register. Enterprise security teams love PlexTrac to streamline their pen tests, security assessments, incident response reports, and much more keeping red and blue teams focused on getting the real security work done with PlexTrac you'll gain precious time back in your team's day and you'll improve your morale or your employee's morale PlexTrac enterprise customer Jacobs engineering gave us a great quote.
Leo Laporte / Steve Gibson (00:07:56):
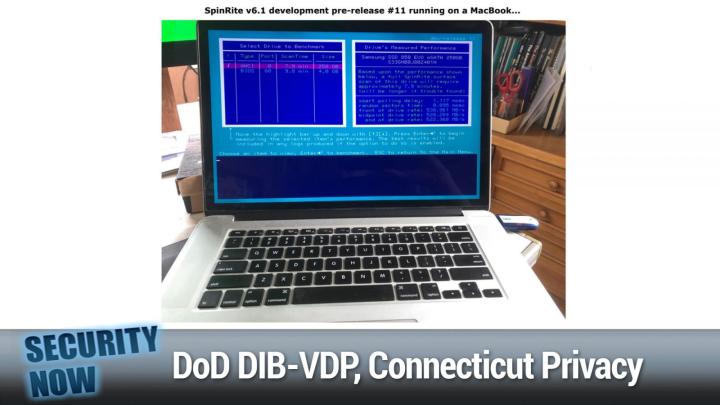
Deploying PlexTrac, allowed our teams to cut the reporting cycle by 65%. Wow. Book the demo today and see how much time PlexTrac can save your team. Try it free for one month. See how it can improve the effectiveness and efficiency of your security team. Simply go to plextrac.com/twit claim. Your free month P X, T R a C PlexTrac.com/t w I T. Thank you. Plextrac for supporting the good work. Steve does here on security now and you support us by going to that address. So they know you saw it here. Plextrac.com/Security Now I didn't even ask Steve, do we have a picture of the week <laugh> we do as a matter of fact? Well, good. It'll be a bit of a surprise. All right. One of our listeners posted this in the pin right development group, but I just got a kick out of it.
Leo Laporte / Steve Gibson (00:08:54):
That's really good news. It's spin right. Running on a MacBook. Wow. <laugh> wow. Look at this. Holy cow. Yeah. and the, the other cool thing is I remember a long time ago guessing that I thought that the spin right would be so fast that it could do. I think I, I had said half a terabyte per hour was my estimate of its speed. As we can see from the screen here, the, and he's just run the benchmark where we're benchmarking the front, the middle and the end of the drive. And we, we can see that this 250 gig drive in the MacBook would take 7.9 minutes to, for spin ride to scan. So that's, you know, four times that is about 30. So, so that would mean 30 minutes to do a terabyte. In other words, we're doing two terabytes per hour rather than half a terabyte per hour.
Leo Laporte / Steve Gibson (00:10:02):
So it really becomes, you know, far more feasible to, to run spin right on these really don't, today's really massive drives. How are you running on the MacBook? Do you have to boot into the free Doss or you do need to have boot camp? So it uses bootcamp. Ah, okay. So not the modern MacBook, unfortunately, exactly. Not the most recent MacBook that did remove bootcamp. And, and you, you can see in the picture, he's got a thumb drive plugged into the USB there in the back right of the keyboard. And so he, he intercepted the boot and booted Frida. So, so Intel only, and you do need bootcamp. So certainly on all of the older MacBooks it'll run like run perfectly. So anyway, just very cool little picture caught me by surprise. I said, Hey cool. Cuz I've actually run it on my MacBook years ago when I diddled the keyboard, the reason it wouldn't ever run before was that spin right.
Leo Laporte / Steve Gibson (00:10:59):
Once spin right. Starts going. It directly pulls the keyboard hardware. Well, PCs have keyboard hardware, max don't they have a USB keyboard, which interfaces and sort of emulates the bios, but spin right. Wasn't it was like pushing past the emulation. So you couldn't run even though everything else worked about it. It just wouldn't, you know, the, the keyboard died after you started up spin. Right. So I've made sure that won't happen in the future and it's wow. It's gonna be so much faster. Okay. <laugh> the DODs D B V DP pilot. M O us E yeah. <Laugh> yeah. So the program of the D O D you know, that's, our us department of defense was named the D I B V D DP pilot program. And despite suffering from program name abbreviation overload, it just successfully finished its year long pilot test. This is the D I B stands for defense industrial base.
Leo Laporte / Steve Gibson (00:12:10):
V DP is vulner disclosure program. Thus D I B V D P. It was a 12 month voluntary event established collaborative, collaboratively by DC threes. And I oh, that's the no D D oh, DC threes defense. No, that's DCS a anyway. <Laugh> it's here. So, oh, defense cyber crime center is the DC three. Oh my God. So established collaboratively by DC three S that's the defense cyber crime center, D O D in does fence industrial base collaborative information sharing environment. And I kid you not that's the D C I S E so. Oh, and the D O D vulnerability disclosure program, thus the D O D V DP, and the defense counter intelligence and security agency, the DSA <laugh> right that year long bug bounty program scrutinized a fraction. And this is key because we're gonna see what a fraction. It was a fraction of the USS massive defense industrial base.
Leo Laporte / Steve Gibson (00:13:34):
Yesterday on Monday, the efforts organizers announced that more than 400 valid vulnerabilities had been uncovered. So during the 12 month pilot program, nearly 300 vulnerability security researchers, hacker one, that's where they, they were sourced, cuz you had to be vetted. And we, we talked about this a year ago, like that this was gonna start and you had to be vetted. You just couldn't come watering in and attack the us government and, and hope to get away with it. So hacker one was, was the coordinator. Those nearly 300 vulnerability filed 1015 reports during their examination of the networks of individual participating defense contractors to the D O D as a result of their scrutiny. Those 401 vulnerability were deemed actionable and required remediation. The pilot effort was running coordination with the, oh my God, the defense cyber crime center. That's the DC three and the defense counterintelligence and security agency that the DSA, the program began with 14 companies and 141 public facing assets.
Leo Laporte / Steve Gibson (00:15:06):
That is to say those were the targets. The 14 companies with 141 public facing assets were initially offered to these hacker one hackers. Then over the course of the year, that effort was expanded to include 41 entities and 348 systems. Now the point of this is this is minuscule. What, what should give the program managers pause is that 401 actionable vulnerabilities were found in those 348 systems belonging to 41 entities yet somewhere between 100,000 and 300,000 companies contract directly with the Pentagon and its components. So like I said, you know, literally so more, more than one actionable vulnerability found per system on average and about 10 per entity that contributed and participated voluntarily in the program. And we have a minimum and I'm not sure why the number quota was so large. I mean, you know, to say between a hundred thousand and 300,000 is like, okay, well <laugh> how, how could it be a three to one, you know, give or take, but anyway, that's the us government for you.
Leo Laporte / Steve Gibson (00:16:47):
So this legitimizes, the long running worry, which yeah. About the latent digital vulnerabilities of the firms that make up the department of defense's supply chain, which has, as we know, been rocked by a number of major breaches over the years. For example, one of the most notorious incidents incidents, which I referred to sort of in passing last week occurred back in 2009 when suspected Chinese hackers broke into one of the contractors working on the F 35 joint strike fighter, which as we know is the most expensive weapons platform ever in us history and Madoff with it, design data. Oops. So Melissa vice, the interim director of the do O D vulnerability disclosure program said, so she was directing this effort, said the pilot bug bounty, which concluded at the end of April intended to identify whether similar critical and high severity vulnerabilities existed on small to medium cleared and non cleared D I B that's defense industrial base.
Leo Laporte / Steve Gibson (00:18:05):
So that's collectively how these companies, these contractors are known company assets with potential risks for critical infrastructure and the us supply chain. That was Melissa saying that. So armed with this data, an analysis of the D I B vulnerability report management network, which is yet another abbreviation will now take place in order to document the pilot program's lessons learned and inform the way forward for a fully funded program, Alex Rice, the co-founder and CTO of hacker. One who, as I said, was the organizing. He, you know, or one provided the hackers. He said, quote, with CSA now mandating vulnerability disclosure for government agencies and federal contractors. The D I B V D P takes the practice a leap forward by demonstrating the efficacy of V vulnerability disclosure programs in the real world. So the fiscal 2022 defense policy bill required the D O D to assess the feasibility of allowing a threat hunting program on the defense industrial base to read out foreign hackers and study the possibility of establishing a threat information sharing program for, you know, what has become a sprawling D O D enterprise.
Leo Laporte / Steve Gibson (00:19:43):
Yeah. If you got 300, 300,000, well, a hundred thousand or 300,000, you're not really sure, you know, subcontractors that's sprawling earlier this year, the do D CIO, John Sherman said the Pentagon was getting rolling on both of those examinations, which as a, as I said, the fiscal 2022 defense policy bill required that they do this. So they did now we've seen, and the bureaucracy has witnessed the clear, the clear feasibility of these programs. And when you stop to think about it, this approach makes so much sense, no sane and talented white hat hacker is gonna poke at government network and systems at the risk of triggering a law enforcement action against them. Right. You know, we've seen exactly that happen in the past. So that must be done within the bounds of a sanctioned bug hunting program. And similarly, no sane and talented white hat hacker, no matter how patriotic is gonna invest their valuable time, doing such poking for free when they could be potentially earning a bounty from poking at some private enterprises networks and systems that pays a bounty.
Leo Laporte / Steve Gibson (00:21:08):
So the government needs to pay and no private enterprise has as much money lying around as the government or a government. So paying is not a problem. So it really ought to be that fully sanctioned government bug bounty programs would to allow hackers to earn Boies, which are competitive with those in the private sector, become a permanent reality in the future successes, such as we're we've, we're seeing here, you know, this and, and, and what, what we saw during this D O D D I B VDP <laugh> though they really do need a sexier name for it move us, you know, another step in that direction. So this was all good. And, you know, a lot of people said, wait a minute, you know, 10 vulnerabilities, which needed action per contractor on average. And we have how many hundreds of thousands of contractors. So, yeah.
Leo Laporte / Steve Gibson (00:22:10):
Okay. we've never talked about the relatively recently formed open SSF, hard to pronounce or say open SSF STAs for open source security foundation. It's a Linux foundation project created in 2020 by a very large group of sign, significant tech and financial firms with the charter to help steer guide and share open source security tools, which unfortunately are lacking. Its membership is divided into two classes, premier and general members with the premier members in an alphabetical order being one password, AWS Atlassian, Cisco city coin base, Dell Erickson, fidelity, GitHub, Google WowWay Intel, IBM JRO JP Morgan, MEA, Microsoft Morgan Stanley, Oracle red hat sync, Sonatype VMware. And we pro and there are about three times as many general members, which I won't enumerate, but you know, many are equally notable. Like, you know, there's Bloomberg, Comcast, Goldman Sachs Mongo DB, Spotify, Susi, tenable, Tencent Carnegie, Mellon, and Mir.
Leo Laporte / Steve Gibson (00:23:41):
So, you know, again, this is a, a heavyweight group. I also saw in some reporting that Samsung was a member, but they weren't listed on the group's official page. So@Openssf.Org, by the way so that page open ssf.org says opensource software is pervasive data centers, consumer devices and applications securing open source supply chains requires a combination of automated tooling, best practices, education, and collaboration. And so they defy, they divide the effort that they're organizing into three components. There's working groups where they say collaborate on the planning, design and delivery of security, tooling, and best practices that secure, critical open source projects. Then they have town halls stay informed about the latest happenings in open source security gauge with experts in our community and training take free courses on secure coding practices as part of our software development fundamentals, professional certificate. So all of that is nothing but good.
Leo Laporte / Steve Gibson (00:25:01):
You know, we've, again, it feels like it's coming along a little late game, but wow. You know, better, better than never. Okay. So that's the open SSF we're talking about this previously undiscussed group today, because last Thursday, they announced the first results, which were a success with some caveats that I'll discuss of their project known as the package analysis project. I've got a link in that show notes for anyone who's interested but they to introduce it, they, they explain package analysis, scanning open source packages for malicious behavior. And so they said today, we're pleased to announce the initial prototype version of the package analysis project, an open SSF project, addressing the challenge of identifying malicious packages in popular, open source repositories. And you know, <laugh> talking about something we've been talking about out a lot recently open source repositories. They said in just one month of analysis, the project identified more than 200 malicious packages uploaded to PI PI and N PM.
Leo Laporte / Steve Gibson (00:26:24):
Okay. So, you know, think about that for a minute. Thanks to this prime 200 previously present, but unknown malicious Python and JavaScript packages were found in a minute, I'll share some of the details about what they found, but their announcement continues saying the package analysis project seeks to understand the behavior and capabilities of packages available on open source repositories. What files do they access? What addresses do they connect to and what commands do they run? The project also tracks changes in how packages behave over time to identify when previously safe software begins acting suspiciously. This effort is meant to improve the security of open source software by detecting malicious behavior, informing consumers, selecting packages, and providing researchers with data about the ecosystem though, the project has been in development for a while. It has only recently become useful following extensive modifications based on initial experiences.
Leo Laporte / Steve Gibson (00:27:42):
Okay. So what they they've built is a big heuristic engine, which is capable of performing static code analysis. You know, currently of packages residing in Python and JavaScript repositories, and as is the case with heuristics, which we could think of as, you know, complex rules of, of thumb tweaking and adjusting of weighting factors is typically necessary. But if the signals they're able to obtain from their static code analysis are strong enough, robust determinations should be possible. So they continue the vast majority of the malicious packages we detected are dependency, confusion and typo, squatting attacks. The packages were found, the packages we found, they said usually contain a simple script that runs during and install and calls home with a few details about the host. These packages, they congest are most likely the work of security researchers looking for bug Bies since most are not exfiltrating meaningful data, except the name of the machine or a username.
Leo Laporte / Steve Gibson (00:28:58):
And they make no attempt to disguise their behavior. Still. Any one of these packages could have done far more to hurt the unfortunate victims who installed them. So package analysis provides a counter measure to these kinds of attacks. They said there are lots of opportunities for involvement with this project. So they're also soliciting from, you know, the community and our listeners are part of that community. They said, and we welcome anyone interested in contributing to the future goals of the four of them detecting differences in package behavior over time, automating the processing of the package analysis results, storing the packages themselves as they're processed for long-term analysis and improving the reliability of the pipeline. They, they then finished checkout our GitHub project and milestones for more opportunities and feel free to get involved on the open SSF slack. This project is one of the efforts of the open SSF securing critical projects working group. You can also explore O other open SSF projects like S SL S a I didn't dig into what that was and SIG store, which expand beyond the security of packaging is themselves to address package integrity across the supply chain.
Leo Laporte / Steve Gibson (00:30:27):
So this is very welcome news. As we know for the past several weeks, especially I've been lamenting the inherent lack of security of the systems that have been built to make sharing code libraries virtually effortless. The trouble has been that polluting these code repositories is also effortless. And recently we've seen this process even being automated with bots to further thwart code identification and its take down. I mentioned some specific examples from among the more than 200 malicious packages discovered during the first month of the system's use. The first two attacks listed in their case study, published on GitHub were against discord clients and their users. They explained that discord attacks are focused on attacking discord accounts or clients. They said a stolen accounts can be resold used for fraud like cryptocurrency scams or used to gain insider knowledge or secrets. The first one that was over on PI PI is discord CMD and in their analysis results, they said this Python PA package will attack the desktop client for discord on windows.
Leo Laporte / Steve Gibson (00:31:48):
It was found by spotting the unusual requests to raw dot GitHub, user content.com, discord API, and IP info.io. They said, first it downloaded a back door from GitHub and installed it into the discord electron client. Next it looked through various local databases for the user's discord token. It grabbed the data associated with the token from the discord API and xFi it back to a discord server controlled by the attacker. And what's so cool of course, is that they found this with automated scanning heuristics. The second discord malware was over on NPM and was titled color SSS, and their analysis result. They said similar to discord CMD above this NPM package attempts to steal a windows users discord account token, and was discovered by identifying calls to the discord, a API, this package first searches through local browser databases for a token queries, the discord server to discover details about the token and ex filtrates.
Leo Laporte / Steve Gibson (00:33:11):
These detail ex filtrates the details to a discord server controlled by the attacker. They also, during this this first month of scanning discovered a couple of remote shells, they explain for those who don't know, a remote shell is used by an attacker to provide access to a command shell running on a target machine over the network. They're usually reverse shells that connect to an attacker control machine. So we have O over on NPM, this one was was Roku hyphen web hyphen core slash Ajax. And they, they explained during install this NPM package, exfil trades details of the machine that's running off and then opens a reverse shell, allowing the remote execution of commands. This package was discovered from its requests to an attacker controlled address. Another one in Python over on Pipi is CRE three. And the analysis says package opens a simple reverse shell.
Leo Laporte / Steve Gibson (00:34:23):
When a specific module is imported from the library, allowing remote command execution, it uses a simple OB technique to make it harder for a reader to notice this package was discovered from the request to the attacker control address. And lastly, over on NPM, this one was random hyphen voucher code hyphen generator. And they said when the library is imported, it queries a server running on their, on their Heroku cloud platform. The server response includes a command and a flag indicating whether or not the command should be run in the response we observed, the command stopped a process managed by PM two. However, they said the same response can be changed to run any command. The attacker wish to execute, including open a, a reverse shell. The library then uses voucher code generator to provide the advertised functionality. So, you know, you get your voucher code generator, but you also you'll get a reverse shell that you probably didn't count on.
Leo Laporte / Steve Gibson (00:35:37):
They said this package was discovered from the, the unusual request to the Heroku server, their case studies page finishes by TA by talking about dependency, confusion on Ty typo, squatting, you know, where they just, you know, we've been talking about that recently where, you know, I remember that dependency confusion. They did note that packages, Ty typically used a high version number. So PA so the package managers that don't know better see that a high version number is available higher than the one they have and say, oh, I, I better go get that. And of course when they do, they get themselves honed. So not good as we've covered previously. Oh, and I was just gonna talk about exactly that, that, that the, the use of high version numbers in order to trick package managers in, into obtaining it Google, who is an active participant in this effort added a bit of additional background in the they're on, in their own blog posting.
Leo Laporte / Steve Gibson (00:36:40):
They explained, they said, despite open source software's essential role in all software built today, it's far too easy for bad actors to circulate malicious packages that attack the systems and users run that software, unlike mobile app stores that can scan for and reject malicious contributions. And, you know, this is Google speaking. We know how tough even that is for them package repositories. They write, have limited resources to review the thousands of daily updates that must maintain, oh, and must maintain an open model where anyone can freely contribute. You know, thus one of the big problems as a result, malicious packages like UA, hyphen parser, hyphen JS, which we actually had spoken of previously and node hyphen IPC are regularly uploaded to popular repositories despite their best efforts with sometimes devastating consequences for users, Google, they write a member of the open source security foundation is proud to support the open SSFs package analysis project, which is a welcome up forward, helping secure the open source packages.
Leo Laporte / Steve Gibson (00:38:02):
We all depend upon the package analysis program, performs dynamic analysis of all packages uploaded to popular, open source repositories, and catalogs the results in a big query table by detecting malicious activities at alerting consumers to suspicious behavior before they select packages. This program contributes to a more secure software supply chain and greater trust in open source software. The program also gives insight into the types of malicious packages that are most common at any given time, which can guide decisions about how to better protect the ecosystem. Okay, so this is all for the good, the bad news is that this, again puts us back into, I think, a pretty clear cat and mouse game because the project is inherently open. The bad guys could learn what the system is keying on and simply arranged to avoid it. How many times in those descriptions I just shared, did we hear quote, this package was discovered from the request to the attacker controlled address, right?
Leo Laporte / Steve Gibson (00:39:19):
Or another of those several of those descriptions said these dependency confusion attacks were discovered through the domains. They use such as burp collaborator.net pipe, dream.com, interact.sh you know, which are commonly used for reporting such a tax. So the bad news is once the bad guys learn that these simple factors, which did not previously interfere with their nefarious aims have become problematic for them to use. They'll simply stop being such, you know, stop using such obvious targets by arranging to use non-obvious, you know, addresses such as by proxying their connections through any of the gazillion compromised consumer routers on the internet. We've already discussed, you know, such readily available. Proxying being used to hide back to command and control servers in this case. It wasn't necessary to do that before now. It is so it'll happen. We already saw something similar with the adoption of package submission bots, which we were just talking about the other day being used to create unique per Haage submission accounts, this prevented casual linkage to other malware, which had also been submitted by the same, you know, mal doer.
Leo Laporte / Steve Gibson (00:40:50):
The underlying problem is that at the moment, and as you know, Google referred to saying it was crucial and necessary, anyone is able to offer packages for submission. You know, if there's no reputation system in place. And the problem with reputation based filtering is that, yes, it can be discriminatory, preventing valid, unknown publishers. Who've not yet established a reputation from contributing their efforts. So we still have some problems to solve. Nevertheless, it is wonderful that the internet, I'm sorry, the inherent value and power of open source software and its need for some form of security oversight is being formally recognized. And that we now have an open SSF, an open source security foundation, which will focus and work towards introducing improvements in this valuable ecosystem. And again, if at anybody is looking for something to contribute to something, you know, some way to apply their skills, I think this is great because you know, the, the gotcha here in the whole OSS movement is that security is as big a problem there as it is for the closed source world.
Leo Laporte / Steve Gibson (00:42:16):
And Leo, I'm getting a little horse here. So before we talk about Connecticut's recent legislation, I'm gonna take a sip of water. Well, no need to get horse. We will be glad to take over here. Thank you, Steve. Our show today brought to you as a, I mentioned earlier by bit warden, very big fan, as you know of bit warden. I switched over to bit warden a couple of years ago because I was looking for a password manager that was open source. So it could you know, it could easily be verified doing what it said. It did. It also meant that I could use it for free forever. I could host my own vault if I wanted to things like that. I really like it bit. Warden's the only open source cross platform, password manager that could be used at home and at work or on the go and is trusted by millions with bit warden.
Leo Laporte / Steve Gibson (00:43:14):
You can secure early store credentials across your personal and business worlds. It all begins with the creation of your vault, the personal vault. And then when you join an organization they invite you to participate in their vault. Now you have two vaults and by the way, bit warden makes it very easy to go back and forth between your personal stuff and the business stuff. And they're always isolated from one another, which is great. Pit warden just added a something called. I love this a username generator, and they've always had a password generator. It's one of the great benefits of pit warden and any password manager but the username generator it's built into the web vault, the desktop app, the browser extensions it'll be coming soon to their mobile app has been highly requested by the community. I think they're the first to do this.
Leo Laporte / Steve Gibson (00:43:59):
The username generator makes it easy to create a random username. So now you have your password and a random username and even extra level of security and privacy on your logins. It also means that having a different username for every website really makes it much harder to do the credential stuffing. You know, the cross site credential stuffing, that's been such a big problem. It's difficult or impossible for hackers to cross reference lists of leak data and find useful information about an individual. The generator will, if you want create a plus addressed email. So if, if you're using Gmail or any provider that supports that feature, you can add the random username to your regular email with a plus it'll still work. There's also a catchall address that you can use or a simple random word plus addressing provides extra options for mailbox management, of course and may reveal any services that have sold email addresses to third parties.
Leo Laporte / Steve Gibson (00:45:04):
Always nice to know. That's one of the reasons I do use a unique username for every single site I sign up for other options include a generated email address at a specific domain for a catchall email account. So for instance, I control my own domain. I can have unlimited email addresses at that address before the ad sign. So I can use the, and do use the bit warden to generate unique. I just love this. It could also be a simple, random word and number to be used as a non email user name. It's very flexible. I think this is just a really great idea. One more reason. I love bit warden and for your business, it's a must fully customizable adapts to your business needs. They have bit warden send. They're always adding new features, which is one of the things I love about bit warden is of in very active development.
Leo Laporte / Steve Gibson (00:45:49):
So bit warden send is a only encrypted method to transmit sensitive information, text or files. This is a very handy way to send files that are of critical privacy importance, but you still can use the public email system, which I think is great. Of course with bit warden, you can always generate not just usernames, but passwords unique and every site, enterprise grade security, that's GDPR, CCPA, HIPAA, and SOC two compliant. And of course, with an end to end encrypted vault, it mitigates Phish as well. Bit war knows when you're using the browser plugin. If you're on the wrong site, it can, it won't fill in the password. If you wanna do the business thing, the teams is three per month per user, which lets you shared private data securely with coworkers or a whole department or an entire organization. The enterprise plan bit warden's enterprise organization plan is just $5 per month per user.
Leo Laporte / Steve Gibson (00:46:47):
Of course, as an individual, you can use that basic free account forever unlimited number of passwords. You can always upgraded their premium account for less than a dollar a month. I think I paid $10 a year for that and it's worth it. I do it just to support them. There's a family plan too, for $3 and 33 cents a month. You can have up to six users with all the premium features. So that's a nice way to give everybody in the family access to the pit warden account. We are fans of course, as you know, on security now of password managers. That's no question bit warden is the one I recommend as the only open source cross platform password manager that could be used for home on the go at work and is trusted by millions of individuals, teams and organizations worldwide get started with a free trial of the teams or enterprise plan or simply get started for free across all devices forever as an individual user.
Leo Laporte / Steve Gibson (00:47:39):
And we have their promise. They gave it to me <laugh> that they wouldn't, that will be free forever. Don't worry about it. They're not gonna suddenly say, oh, we're not gonna do this free thing anymore. Free forever as an individual userat bitwarden.com/twit. I, I shifted more than a year ago now and no looking back. It's fantastic bit warden.com/twi. I'm telling everybody about it, including you. Thank you bit warden for supporting security now. All right. Steve hydration. Depletion. Yes. Yes <laugh> thank you. So Connecticut, the, you know, a state in the us I've who are not in the us, mm-hmm, <affirmative>, it's difficult to spell, but what you get the trick it's okay. The us federal government is not moving forward on consumer privacy protection. So several states have taken matters into their own hands. The state of Connecticut's attorney general advanced a bill last Thursday that would offer residents a useful set of baseline privacy, right?
Leo Laporte / Steve Gibson (00:48:50):
If signed into law by Connecticut's governor Ned Lamont, Connecticut would join four other states which have already enacted similar legislation. Those four are California, Colorado, Virginia, and Utah Connecticut's bill, which is their SB six, which is named act concerning personal data privacy and online monitoring. If signed and the governor's spokespeople are not committing, but are not saying no. And it's expected to go. It's expected to pass. It would take effect July 1st of next year, 2023. So not immediately even when signed and it closely resembles the privacy laws, which have already been passed in Colorado, Virginia, and Utah, in that it allows residents of those states to opt out of sales, targeted a and profiling. And after two years by 2025, the law requires companies to acknowledge optout preference signals for targeted a advertising and sales. Now websites and companies would be required to proactively obtain consent to process sensitive data and need to offer Connecticut residents ways to revoke that consent.
Leo Laporte / Steve Gibson (00:50:21):
And the law provides that organizations will have no more than 15 days to stop processing data. As soon as consent is revoked, parental consent is needed for any website to collect personal data from children under the age of 13, but businesses are banned from collecting personal data and using targeted advertising on children between the ages of 13 and 16, the bill forces companies to honor browser privacy signals like the global privacy control, thus the title of this podcast. And we'll be talking about that here in a minute. So the consumers can opt out of data sales at all companies in single step. And as we know, global privacy control, oh yeah. <Laugh> I have in my notes, global privacy control is today's main topic. So we'll be discussing it in detail shortly. So ki Lamont the senior council at the future of privacy forum added that Connecticut's bill goes beyond existing state privacy laws by quote directly limiting the use of facial recognition technology establishing default protections for adolescent data and strengthening consumer choice, including through requiring recognition of many global opt out signals.
Leo Laporte / Steve Gibson (00:51:49):
Nevertheless, he says a federal privacy law remains necessary to ensure that all Americans are guaranteed strong baseline protections for the processing of their personal information. Now, the law also joins California and Colorado in adding sunset clauses to the so-called right to cure. In other words, PLA placing an end to that, right, which has been regarded and treated as a get out of jail free card. This right to cure describes a process where companies are given a set amount of time to fix violations. The a four enforcement action can be taken or lawsuits can be filed. In other words, it basically allows 'em to bypass the law. Its presence has been a hotly debated topic in many state assemblies across the country. It's been the reason why several previous privacy bills have failed to pass consumer reports, which worked with Connecticut lawmakers on their bill called the right to cure provisions in most privacy laws.
Leo Laporte / Steve Gibson (00:52:56):
They're the ones who coined the term. It get out of jail free card for companies violating consumer privacy. However, Connecticut gets right to cure provision sunsets on December 31st, 2024 Colorado's provision sunsets the next day on January 1st, 2025. But our, and I say our Leo cuz you and I are both in CA California. California's sunsets the first of next year, January 1st, 2023, which puts teeth in this for California. Once these sunset, the states will be able to take enforcement action against organizations that violate the law, California, Colorado, and Connecticut are therefore being referred to as the three CS because they all have useful sunset provisions a lawyer David Straus, who serves as chair for the hush Blackwell law firm's privacy and cybersecurity group said, he said through joint enforcement, the three CS of state privacy law will be in a unique position to dictate the future of us privacy because of, as we know when for state laws, any business doing, doing business in that state, which to say, you know, all businesses need to abide by the laws within that state.
Leo Laporte / Steve Gibson (00:54:33):
So he said through joint enforcement, the three CS of state PR of state privacy law will be in a unique position to dictate the future of us privacy, assuming that continuing abstinence or sorry, continuing at absence of any overriding federal law, but this will not be the case with Virginia and Utah where right to cure will endure. So Connecticut's SB six also establishes a privacy working group to analyze a number of issues and provide a report by September 1st of this year. And without federal support, it's all a bit of a sticky Wicke. Several states have spent years attempting to pass their own privacy laws due to the lack of any movement on privacy legislation at the federal level calls for a federal privacy law have ramped up since the European unions infamous GDPR, their general data protection regulation became enforceable in 2018, which has served as a model for similar laws in Japan, Brazil, South Korea, and elsewhere, but New York, Texas, Washington, and dozens of other states have FA have faced so far insurmountable pushback, but attempting to move their own privacy legislation forward due to backlash from businesses that complain the bills will create a significant amount of extra work for effectively any business with a website oh, Boohoo, right?
Leo Laporte / Steve Gibson (00:56:10):
You have to pay attention to a signal, you know, an opt out signal from the browser and then behave accordingly. Gee, anyway, the three CS, California, Colorado, Connecticut won't care and won't need to any web-based business with a customer in California, Colorado, or, and presumably Connecticut, once its legislation passes will need to get their digital act together soon in the case of California, as I said, by the end of this year or face legal check challenges. And as we'll see the best news is that the adoption of the new GL global privacy control browser signal means that we're not all going to be needing to keep clicking something like I want my privacy at every website we visit unlike that horrible cookie mess that we're facing.
Leo Laporte / Steve Gibson (00:57:06):
Okay. Now I ran across this and I loved it. This is Moxy. You know, we all know Moxy, Marlon spike. We've spoken of him often. He's most famous for his hand in the development of signal, which provides a secure technology for true end to end encryption of instant messages. We did a podcast on it years ago, if anyone is interested in how signal works, of course, WhatsApp is based on signal, unlike telegram signal employs standard proven and understood cryptographic primitives. You can look at it and go, yeah, this is secure. You know, there's no Hocus Pocus, mumbo jumbo there. It's just very clever. And, and, and that's where that, that ratchet concept was introduced in order to allow secure messaging, even in an asynchronous message passing environment. Well, it turns out that 10 years ago Moxi took us his own stab at his own design and implementation of port knocking for anyone who's interested.
Leo Laporte / Steve Gibson (00:58:18):
It's on GitHub. I've got the link in the show notes and I won't go into it in depth. It's just a no another way to solve the problem, but what I loved and the reason I'm mentioning it today is that Moxy ended his page with a section titled, why is this even necessary? Which I wanted to share because it'll sound quite familiar. In answer to that question, Moxy wrote you are running network services with security vulnerabilities in them, period <laugh> and then he said, again, you are running network services with security vulnerabilities in them. He said, if you're running a server, this is universally true. Most software is complex. It changes rapidly and innovation tends to make it more complex. It is going to be forever hopelessly insecure, even projects like open SSH that were designed from the ground up with security in mind where every single line of code is written with security as a top priority, where countless people audit the changes that are made every day, even projects like this have suffered from remotely exploitable vulnerabilities.
Leo Laporte / Steve Gibson (00:59:52):
If this is true, what hope do the network services that are written with different priorities? Have he said, the name of the game is to isolate compartmentalize and expose running services as little as possible. He says, that's where knock knock comes in. That's hit the name of his solution. Given that your network services are insecure, you want to expose as few of them to the world as possible. He's finished saying I offer knock, knock as a possible solution to minimize exposure. So from the, from the mouth of Moxi there it is, you know, it's, as I said, it should sound familiar to anybody. Who's tired of listening to me say the same thing on this podcast. All, all of the evidence that we have that we, that we cover every week proves this point over and over and over exactly as Moxi stated. So it's a reason why, you know, I'm big fan when you have fixed IPS on your endpoints, absolutely use firewall, you know, IP based firewall filters so that nobody anywhere else has, has any access to the ports, which you have opened between two fixed locations.
Leo Laporte / Steve Gibson (01:01:22):
And even if they're mostly fixed, you know, as I've said, you know, if you've got a cable modem that that IP is not changing often, like nearly never. So even there it's feasible to do IP based point to point filtering. And if you need to connect to clients that are gonna have a floating IP, some, you know, some form of port knocking, some form of out of band or kind of quasi in band authentication in order to then give that IP and port temporary access just, it makes all the sense in the world. And there are, you know, widely available tools for making it happen. You just have to decide to, okay, some feedback from our listeners D sta wrote from at DTA, he said, how can a cryptocurrency wallet in a browser be a very bad idea while last pass and other browser based password managers are a very good idea.
Leo Laporte / Steve Gibson (01:02:31):
<Laugh> and you know, that's a really good question. I had to think about a bit about how to explain why I still feel that both of those apparently opposing evaluations can both be true at the same time. I think it boils down to necessity and practicality. It is not necessary to use a browser as a cryptocurrency wallet. It would be far safer to perform a wallet's operations in a more secure container in any other more secure container. And it would be, and is practical to do so. Most people do. I also agree that a bra browser is not as secure as I would wish it were for the storage of all of my most precious static passwords in any password manager, but it's pretty much necessary to integrate a password manager into our browser. And it would be less practical not to have that integration.
Leo Laporte / Steve Gibson (01:03:43):
If a password manager were not integrated, we would need to manually look up every site. We were visiting, then display, copy, and paste our username and password for that site into the browser and passes through the clipboard, which has been a problem in, in, in what mal malware that, that monitors the contents of our clipboards. We would also be at an increased risk from lookalike phishing domains. Since we might be fooled by pay poll.com. Whereas an integrated password manager would not be, this podcast has well established that browsers are today's number one, attack targets. They are the attack surface, which we all present to the internet as we move about. They're not perfectly secure. They're not as secure as we could wish they were yet. We are not see reports of browser native password databases, north third party, password manager, extensions being hacked. So it must be that unlike the mistake we discussed last week that was made in the browser based cryptocurrency wall, add on those who are authoring and maintaining both browser native and third party password managers are really taking their jobs and responsibilities.
Leo Laporte / Steve Gibson (01:05:11):
Seriously. They may not be sleeping well at night. And I know if I was responsible for this, I wouldn't be, but that's so that we can a Neville he's retweeted. Hi, Steve, regarding spin right. 6.1, I use a raspberry pie four as a NAS will 6.1 be able to run on hi. No, <laugh>, I I've replied to a spin. Wright is lovingly written in native X, 86 assembly language. So it is, and has always been intimately tied to the Intel X 86 processors. So there's no way that version six one at least of spin, right. Will run on anything other than a system with an Intel processor. The only way to run spin right on a mass storage device from a non-Intel platform will be to temporarily move the device to any Intel PC. And of course the good news is that spin right. Six one is so fast now that a great deal of testing and maintenance can be accomplished in a very, in very little time, but, you know, never say never, I don't know perfectly what the future of spin ride is, but for their foreseeable future, at least, you know, even seven and seven point X and everything that I know of in the future, it's still gonna be Intel based.
Leo Laporte / Steve Gibson (01:06:41):
Someone whose handle is at F I Z C H FIS. <Laugh> he said he tweeted a few weeks ago. You mentioned a piece of networking equipment that you use for segmenting your network for the life of me. I cannot find at that episode of security now, nor do I remember what the device was. Can you shed some light on this for me? And yes, I recall pointing up over my shoulder at the little SG 1100 firewall router by net gate, which runs PF sense and could do everything you might ever or want a little router to do since it has separate physical land wan and auxiliary interfaces. It's perfect for creating an isolated I O T network whose devices can only see each other on the same sub land. They could see the internet, but not across each other's network. And if anyone if you just Google net gate SG, hyphen 1100, it'll take you right there.
Leo Laporte / Steve Gibson (01:07:54):
And, you know, I literally, it's what I'm using on my network right now. Yep. There it is. Neat little Gimo and it's just, it's a turnkey PF sense firewall and PF sense will do anything. Ben Hutton tweeted at S at SG GRC. He says I'm a little behind, but in SN 8 56, you mentioned that you wouldn't want to be able to translate two factor authentication generation data back into the original QR codes. He said, but some apps allow for export and import. Could you explain how this is different please? Okay. So a two-factor authenticator receives a QR code from a website to establish a two-factor identity for a user. The site will generate and store a random secret key, which is associates with a user's account. It will then display that random key in the form of a QR code. The use of a QR code allows that key to be easily transmitted optically to an authenticator app on the user's smartphone using its camera.
Leo Laporte / Steve Gibson (01:09:14):
If we didn't have QR codes or something similar, the site would need to have the user. It would have to display like the private key in hex or something, and have the user manually enter that key on the smartphones touch screen, which will be a nightmare. So using a QR code for this is a huge convenience. And at that moment, by the way, when the QR code is being displayed by the website is when I press control P to capture and print that page for my own offline QR code authentication archive. The reason I would rather use an authentication app that does not allow for private key export is that anyone who might be able to arrange to obtain brief unlocked access to my phone might export my collection of authenticator, private keys, thus defeating all of the multifactor security I've come to lie upon the only valid reason to ever need to export an authenticator.
Leo Laporte / Steve Gibson (01:10:23):
Private key repository would be to move them to another authenticator app for instance. But since I keep all of those keys printed on paper, I never need to export anything. I, I only need to reimport my private key archive, which is in the form of a she, of printed papers each containing one QR code. Bruce Schneider's famous advice regarding passwords applies here many years ago, Bruce said, do not memorize your passwords, write them down. They should be so complex that you cannot possibly remember them all. And we're very good at managing bits of paper. Bruce said a note that printing these QR codes has the inherent advantage of moving the archive offline. It's true that someone with physical access who knew where this little Shea of papers was stored, could obtain all my authenticator QR codes, but that's not the threat model we're attempting to protect against.
Leo Laporte / Steve Gibson (01:11:31):
And if it were safety deposit boxes or a safe or any sort of physical lockbox is a long established means for protecting that kind of real world asset. The threat model we're attempting to thwart is online. So moving their backup offline provides for added protection. And one last point is that I understand that it's not as high tech to print QR codes on paper, but it's our technologies that office that often bite us in the butt sometimes, especially where security matters. A bit of judiciously placed, low tech is the more secure solution, even if it's less glamorous. Okay. So after our final sponsor we're gonna talk about the new hope in town, global privacy control. Mm let's. Do it in just a second, but first allude from our sponsor is usual. I'm gonna take a little break here. Our show today brought to you by ITProTV.
Leo Laporte / Steve Gibson (01:12:41):
You know, I'm a big fan of it. Pro TV. We've been them with them since this, they started out, I think, you know Tim and Don went to an event I did at NA in which we were talking about, you know, what TWiT does. And they said, boy, they were already it trainers. They said, boy, that'd be a good way to do it. Training an ITProTV was born and they're doing great seven studios in their Gainesville, Florida headquarters running Monday through Friday, all day recording new content. And the reason they do that is you always have to keep the content up if you're doing it training because everything changes new versions of the software, new tests for the certs. You, you just, you just gotta be always updating an ITProTV always is if you have an it team, I always talk about ITProTV for individuals.
Leo Laporte / Steve Gibson (01:13:31):
But if you have an it team, you should consider ITProTV to keep their skills up, to keep their certs up to date. They have a great business offer. And I think just as important when you use ITProTV, and you give that to your it team for training, they appreciate it. Cuz it's engaging. It's informative. It's easy to digest all 20 to 30 minute chunk each course divided up so they can do a bit at a time. And by the way, people love it. Pro TVs, videos, 80% of the people who start a video at it, pro TV go all the way to the end, finish it. It's you know, it that's a good sign, right? It means they get engaged immediately. They're learning. They go. Yeah. And you want that? You want your team to go. Yeah. I love this courses are entertaining and binge-worthy which keeps your team not only interested, but vested in learning ITProTV will get you the training and search for your team, all of the training and they need in one place, every vendor, every skill you need for your it training, including Microsoft, it training Cisco Linux, apple security cloud and on and on and on even the compliance and soft skills.
Leo Laporte / Steve Gibson (01:14:45):
So it is a one stop shop for all the training more than 5,800 hours of on demand training and their dashboard for the business plan is great. You can track your team's results, manage seats, assign and unassigned team members. You can even do subsets of teams, whole teams customizing the assignments for them. You can monitor their progress. You can get reporting on usage of the platform to make sure that your investment is, is paying off things like logins, viewing time tracks completed monthly usage reports. Assignments can be full courses or even individual episodes within courses. And because every course at it, pro TV has a transcript. It's really easy to find the part of the course you wanna focus on and say, Hey gang, you really need to learn this <laugh> you need to learn this subject. You'll get immediate insight into your team's viewing patterns and progress over any period of time.
Leo Laporte / Steve Gibson (01:15:38):
And the reports are visual. So you can show 'em to the the the bean counters people write the checks and say, see, see, look, <laugh> see it's working, it's working. So for individuals, as well as for businesses, the best place to get your it training ITProTV, give your team the it development platform. They need to level up their skills and enjoy the journey too, cuz it should be fun, right? It pro TV for teams from two to 1000 volume discounts start at five seats. The website, is it pro.tv security now. And when you're there, when you talk to your account executive, don't forget to say SN 30, SN 30. So you'll get an additional 30% off on the business plan. So you may get volume discounts as well. This is in addition to that SN three zero, visit ITProTV slash security now, and by the way, individual users use that code too.
Leo Laporte / Steve Gibson (01:16:39):
Get 30% off as long as you're active forever it pro.tv/Security Now offer code SN 30. We thank them so much for making security now possible. And now speaking of the possible, or maybe the, the impossible global privacy control, <laugh> it Steves. Okay. <Laugh> so what is global privacy control? Believe it or not. It is what was clearly the right solution and what I was vocally arguing for as being obviously the right solution when its predecessor known as do not track was first proposed 13 years ago, back in 2009. Yes. During this podcast Lee we've been around for a while. We are finally gonna get it. It will have legally enforceable teeth and I could not be more pleased. I got a kick out of this. This is what Wikipedia has to say about do not track and it's useful cuz it also reminds us of a few things that happened.
Leo Laporte / Steve Gibson (01:17:49):
Wikipedia says, do not track D N T is a no long is a no longer official HTTP header field designed to allow internet users to opt out of tracking by websites, which includes the collection of data regarding a user's act to across multiple distinct contexts and the retention use or sharing of data derived from that activity outside the context in which it occurred. The do not track header was originally proposed in 2009 by researchers, Christopher, a Sego, Sid sta and Dan Kaminski Mozilla Firefox became the first browser to implement the feature while internet Explorer, apples, safari, opera, and Google Chrome all later added support efforts to standardize do not track by the w three C in the tracking preference expression working group react reached only the candidate recommendation stage and ended in September, 2018 due to insufficient deployment and support D N T they write is not widely adopted by the in street with companies citing the lack of legal mandates for its use as well as unclear standards and guidelines for how websites are to interpret the header.
Leo Laporte / Steve Gibson (01:19:23):
Thus critics purport that it is not guaranteed that enabling D NT will actually have any effect at all. The w three C disbanded its D T working group in January, 2019, citing insufficient support and adoption apple discontinued support for D T the following month citing browser fingerprinting concerns Uhhuh as of November, 2021, Mozilla FA Fox continues to support D N T in Firefox. The feature is turned on by default in private browsing mode and optional in regular mode. In 2020, a coalition of us based internet companies announced the global privacy control header that spiritually succeeds the do not track header. The creator's hope that this new header will meet the definition of user enabled global privacy controls defined by the California consumer privacy act, the CCPA and European general data protection regulation. The GDPR in this case, the new header would be automatically strengthened by existing laws and companies would be required to honor it.
Leo Laporte / Steve Gibson (01:20:50):
Okay, so that was D N T what we will be getting is GPC. If I go to the global privacy control.org website, so it's global privacy control, G L O B E a L P R I V a C Y C O NT, R O l.org website with Chrome. The top of the page looks like, and I have a picture of it in the show notes, there's a red dot and it says, GPC signal not detected. And it then, and since this is the global private org site, it says, please download a browser or extension that supports it. But if I go to the same site with Firefox, after enabling, Firefox's already present and built in global privacy control settings, I'm greeted with a different banner at the top, I get a green dot and the words GPC signal detected. So from a technology standpoint, GPC has 100% of the elegance simplicity that made D NT, such an obviously correct solution.
Leo Laporte / Steve Gibson (01:22:11):
The specifications abstract reads. This is the abstract for GPC. It reads this document, defines a signal transmitted over HTTP and through the Dom that's one additional feature that we'll talk about in a second, that conveys a person's request to websites and services to not sell or share their personal information. With third parties. This standard is intended to work with existing and upcoming legal frameworks that render such requests enforceable. The specifications introduction explains they say building websites today often requires relying on services provided by businesses other than the one which a person chooses to interact with this result is a natural consequence of the increasing complexity of web technology and of the division of labor between different services. While this architecture can be used in the service of better web experiences, it can also be abused to violate privacy, which like perfectly contextualize rises. This, this issue, several legal frameworks exist and more are on the way within which people have the right to request that their privacy be protected, including requests that their data not be sold or shared between the businesses, with which they intend to interact requiring that people manually express their rights for each.
Leo Laporte / Steve Gibson (01:23:50):
And every site they visit is however impractical. Okay. Then they ha they, they, they cite a chunk of the CA the California consumer a protection act, which reads this is from the, the CCPA, given the ease and frequency by which personal information is collected and sold. When a consumer visits a website, consumers should have a similarly easy ability to request to opt out globally. This regulation that is this, the California consumer protection act now enforce. And in law in California and the get out free jail card is, is sun setting and ending at the end of this year, says this regulation offers consumers a global choice to opt out of the sale of personal information, as opposed to going website by website to make individual requests with each business, each time they use a new browser or a new device. So in other words, thank goodness.
Leo Laporte / Steve Gibson (01:25:04):
We're not gonna need to be going, you know, doing something like clicking on, yes, I'll accept your cookies, the equivalent of wherever we go. And then back to the the specification for for GPC, they said this specification addresses the issue by providing a way to signal through an H ATP header or the Dom a person's assertion of their applicable rights to prevent selling data about them to third parties or sharing data with them. This signal is equivalent for example, to the global privacy control in the C EPA regulations. And I'll get to that in a second. So, as I said, the specification could not be more clear or easy to implement. I have a, a sample header in the show notes, whereas D do not track was D N T colon space. One to enable it. This one is S E C probably short for security, S E C hyphen, then GC colon space one, that's it, your brown, when it makes a, a, a query to any asset, you know, it's gonna have a, it's gonna say, get as the verb or maybe post, and then the URL, then there'll be a host colon header that tells the site which host it wants.
Leo Laporte / Steve Gibson (01:26:39):
So like, you know, example.com and then SES C hyphen GPC, colon space. One to say, I am requesting of you the site associated with this query from my browser, that you Abey, you abide by these regulations. So it defines and standardizes this new HTTP header, S E C E hyphen GPC, which when affirmatively set has the value of one meaning true. Okay. Now for a minute, recall the mess that ensued when Microsoft decided to have internet Explorer, 10 default to transmitting that D N T colon one header Wikipedia reminds us of this. They wrote with I E 10 when using the express settings upon installation, a do not track option was enabled by default for I E 10 and win eight Microsoft faced criticism for its decision to enable, do not track by default from advertising companies who say that use of the do not track hitter should be a choice made by the user and must not be automatically enabled.
Leo Laporte / Steve Gibson (01:28:03):
The companies also said the, that this decision would violate the digital advertising alliances agreement with the us government to honor a do not track system, because the coalition said it would only honor such a system if it were not enabled by default, by web browsers, a Microsoft spokesperson Def its decision. However, stating that users would prefer a web browser that automatically respected their privacy on September 7th, 2012, Roy fielding an author of the do not track standard committed APA to the source code of the Apache HTTP server, which would make the server explicitly ignore any use of the do not track header by users of, of internet Explorer. 10 fielding wrote that Microsoft's decision deliberately violates. They do not track specification because it does not protect anyone's privacy, unless the recipients believe it was set by a real human being with a real preference for privacy over personalization.
Leo Laporte / Steve Gibson (01:29:20):
The due do not track specification did not explicitly mandate that the use of do not track actually be a choice until after the feature was implemented in internet Explorer, 10, according to fielding, Microsoft knew its do not track signals would be ignored and that its goal was to affect the, give the illusion of privacy while still catering to their own interests on October 9th, 2012. So he patched it on September 11th on, on October 9th, 2012, just well, you know, a little over one month later Fielding's patch was commented out, restoring the previous correct behavior for Apache because nobody agreed with him on April 3rd, 2015, Microsoft announced that starting with windows 10, it would comply with a specification and no longer automatically enabled do not track as part of the operating systems express default settings. But the company will quote, provide customers with clear information on how to turn on this feature in the browser setting, should they wish to?
Leo Laporte / Steve Gibson (01:30:31):
Okay. So to prevent any of this, the formal specification for the new S E C hyphen GPC header, clearly states, they said a user agent must not generate a S E C GPC header field. If the person's global privacy control preference is not enabled or defaulted to, but they allow it to be defaulted to a user agent must generate an S E C GPC header field with a field value. That is exactly the numeric character. One. If the users global privacy control preferences is set, a user agent must not generate more than one S E GPC in a given request and must not use a S E C GPC field in a, an HTTP trailer. They're rare, hardly anyone uses them. We've talked about them once before a server processing, an HTTP request that contains an S E C GC header must ignore it and process the request as if the header had not been specified, unless the field value is exactly the character.
Leo Laporte / Steve Gibson (01:31:51):
One, if there are multiple S E C GPC headers, and at least one has a field value of one, then the server must treat the request as if there were only one S E C GPC header with a Val field value of one. And as if there were, and as if there were none, otherwise HTTP intermediaries must not remove an S E C GPC header set to one, but they may remove S E C GPC headers that contain other values. Additionally, an HTTP intermediary that has reasons to believe that the person originating a given HTTP request has a do not sell or share preference, may insert S E C GPC header set to one. So the specification also defines, as I noted a new top level JavaScript, global value global privacy control, which allows any script running in the browser to determine whether the query, which loaded that script sent the S E C GPC one header to the server.
Leo Laporte / Steve Gibson (01:33:09):
<Laugh> and, and the sample script that they had, they have some JavaScript. They have, if an if statement with Peren and then they start with, you know, an exclamation point bang for negating. So, so if not navigator.global privacy control, and then in curly braces, they have the comment wonderful. We can sell this person's data. Meaning global privacy control was not set in this browser or for this query. Since the only thing that differentiates this from the earlier D N T effort is the promise of legal enforcement under the European union's GDPR. And at least in California and soon Colorado and Connecticut. I was curious to look at that at a bit more closely, Wikipedia closes out their discussion by noting GPC is a valid do not sell my personal information signal. According to the California consumer privacy act, which stipulates that websites are legally required to respect a signal sent by users who want to opt out of having their personal data sold in July of 2021, the California attorney general clarified through an FAQ that under law, the global privacy control signal must be honored.
Leo Laporte / Steve Gibson (01:34:44):
Now as a California resident, this made me curious to read the actual California legislation. So I found it, but don't worry. I'm not gonna drag everyone through it. I'll just note that I am completely satisfied with what the legalese says. I'm not an attorney, but it was written in very clear and concise English, which to my untrained eye leaves, zero wiggle room. This time they're not screwing around for any, for anyone who's curious to see for themselves. I have a link to the, to the 28 page PDF where on page 17, and this is just an excerpt from the entire legislation. So this is a small chunk of it. That's why it's only 28 pages, but on its page 17, paragraph 9, 9, 9 3 1 5 is titled requests to opt out. And anyone who's interested can, can follow that. So it appears that we are about to get what we wanted and hoped for more than a decade ago.
Leo Laporte / Steve Gibson (01:35:55):
If you are a Firefox user, bring up your browsers, detailed configuration settings by entering about colon config in the URL field. As we've talked about many times, then enter privacy.global as the search term to reduce those gazillion items that will come up to just two, then double click on each to flip them from false to true, which will also make them bold. Then head over to HTTPS colon slash slash global privacy control.org. And at the top of at page, you'll see that your Firefox browser is now and hopefully forever transmitting your legally enforceable assertion that you do not give your permission, that you are yep. That you are affirmatively revoking permission and choosing to opt out of any site that you visits legal, right, to share your information with any other entity, for any purpose whatsoever. And they will honor it. And as well as individuals, we don't need to enforce that right?
Leo Laporte / Steve Gibson (01:37:14):
Since once California's right to cure provision sunsets. At the end of this year, it seems clear that the biggest violators of consumers asserted legal rights to privacy will be taken to task by California's attorney general, who has clearly stated their intention to do exactly that. Now, although Chrome is becoming increasingly conspicuous for not directly supporting the transmission of this GPC signal, plenty of Chrome compatible add-ons and other browsers already do a bean brave disconnect, duck dot go, opt me out. And privacy Badger. Now being a perennial minimalist, it would be nice if you block origin were to add the GPC header for us. Since I already have you block origin installed every way, including in Chrome, but gore hill has, was asked about six months ago, whether or not he would consider doing so. And he declined on the basis that it was just another D NT fiasco that doesn't appear to be true.
Leo Laporte / Steve Gibson (01:38:31):
So there's some hope that in the future he might reconsider, although he is extremely curmudgeonly. So perhaps highly unlikely, perhaps, perhaps not <laugh>. Yeah, for me, I'm, I'm liking the new add-on opt me out where the you of out is instead a w making it me as in Kas. Meow. So it's spelled O P T M E O w T opt me out opt Meow. The reason, yeah, the reason I like the way the re the reason is I like the way it looks, and it was developed by some guys who had been deep into the global privacy control effort. Their names are listed as contributors to the spec. They're at the, the, we, the Wesleyan university's privacy tech lab. Wesleyan's a private college in Middletown, Connecticut, probably not coincidentally where this legislation is a, a on the verge of making them the third sea of, you know, with California and Colorado preceding opt me out is free and open source and hosted on GitHub.
Leo Laporte / Steve Gibson (01:39:48):
That's about two and a half Meg. So it's a relatively small download and their page. Github has a bunch of other privacy related projects for anyone who's interested it's available from the Chrome web store and supports all of the many chromium based browsers. So Chrome, brave edge opera, and Vivaldi, the brave browser began testing default inclusion of the GPC header last October. So it's probably well in place by now. And you, you just, if you're a brave user, just go to global privacy control, I expect you're already gonna see a green light shining back at you without needing to add anything else. So by all means, by all means, check to make, to see whether your browser may already support it like Firefox did. And I didn't know it, and didn't have it turned on now. I do. And it, it is. So if your browser doesn't have it, this little opt me out, looks like a, a slick way to add it.
Leo Laporte / Steve Gibson (01:40:46):
I've got a picture of its settings page here at the bottom of the show notes, it just got three buttons enable, which sends do not sell signals to every visited domain. Or you can be selective if you like you, you can, you can give it a domain list which sends do not sell signals according to the custom domain list, which you can provide, or you can disable does not send any do not sell signals. So, huh. It took us a long time to get here, Leo, but this is certainly encouraging. Yeah. And boy, this would just be great. Yeah. Because what we've had to do is develop tools that block tracking you know, fingerprinting and things like that because companies just, you know, you know, they're not, they want it, they will want it. Yeah. If, if they're, if we don't tell if, if we don't tell them no.
Leo Laporte / Steve Gibson (01:41:37):
And if, if they don't suffer legal recourse in the event of ignoring what we're telling them, they're gonna do it. Yeah. That's awesome. That's awesome. So you think that thanks to Europe, Connecticut, and California they're gonna, they're gonna honor this cites will have to. Yes. Great. Yes. Good. Yes. Well, look, look what GDPR did to our cookies. I mean, it's a pain in the butt, but everybody does it. Everybody does it. Yes. You exactly. We're all scared to death of them. <Laugh> yep. Even though it's a completely meaningless regulation and they will Sue, I mean, and, and it looks like Californias say, look, you're, you're gonna honor this law. Well, you're not gonna do business in California. Well, you can't not do business in California. Right. Right. Wow. That's great. Well, thank you, Steve, as always some great information. And I am now gonna go around to all my fire foxes and do about config and turn on those global privacy control.
Leo Laporte / Steve Gibson (01:42:33):
There's two setting you just flip 'em to true. And you're right. It, it says I'm green light now, which is amazing. So another reason you like Firefox, although you said there are other browsers that will do this, Chrome is the one that won't probably that's good. <Laugh> well, now apparently they did, they did support D N T at some point. So I think they'll end up saying, okay, fine. You know, I'm not happy, but I, I hope so. Yeah. Yeah. Steve gives real that's big. I mean, that shuts everything down. Yeah. I mean, it's really big. Yeah. it's kind of stunning. Yeah. wow. Global privacy, a control.org is another place to go to learn a more about it. Yep. Steve Gibson, see, see, now, you know why you have to be here Tuesdays. You really do listen to this show.
Leo Laporte / Steve Gibson (01:43:25):
You don't have to listen to it live because you can get it of course downloaded from Steve site. He's got a couple of unique versions. He has a 64 kilo audio. That's the mainstream version, but he also has 16 kilo audio file for the bandwidth impaired and transcripts, which make it very easy to search for something you're interested in. You can even correct me if I'm wrong, Steve, but I think you can search all the transcripts all at once with Google, right? So you could find, you can use Google. And I also have a search box on, on GRC. Perfect. And it knows in order to re to constrain it just to security now, so it'll get all of them. And you know, you can find, did Steve ever talk about yes, he did. And it's right here. That's great. Great stuff.
Leo Laporte / Steve Gibson (01:44:07):
Grc.Com while you're there pick up spin. Right. We inching closer. Maybe even striding closer to version 6.1 6.0 is current though. And if you buy it@grc.com, you will be freely upgraded to 6.1, as long as you buy it. Now you'll also get to participate in the upgrade in the you know, upgrade to 6.1. So that's kind of fun. There's a forum and all sorts of stuff. Grc.Com. Steve's also on Twitter. If you wanna leave a comment at SG GRC and his DMS are open. So slide on in, as the kids say, we have on demand versions of the 64 kilo audio and video, strangely enough, on our website <laugh>, which is twi.tv/sn there's a YouTube channel full of videos. And if you could subscribe in your favorite podcast client, that's another way to do it. Steve has a link to the RSS as do we just paste that in and you'll get it the minute it's available.
Leo Laporte / Steve Gibson (01:45:04):
If you do, if you are in a hurry and you do wanna watch it live the freshest version of Security Now we do it on Tuesdays around one 30 Pacific, four 30 Eastern, 2030 utc@livedottwi.tv. There's live audio and video. So you can listen at dinner or launch, you know, and and learn listen and learn. We call it. And if you are listening or watching live, please chat with us. Live at IRC E twit TV, of course, club TWiT members are always chatting about this show and everything else going on in our discord channel, which is so much fun, highly rec recommend it. The discord channel is not just about the show we have, of course the channel for all the shows, but we also have channels about every kind of geeky subject, including sci-fi. And we have Stacy's book club in there.
Leo Laporte / Steve Gibson (01:45:57):
She's gonna do the Neil Stevenson, new Neil Stevenson book. Next month we have fireside chats. Scott, Wilkinson's coming up on Thursday, father Robert on next Thursday. We have the untitled Linox show and GIY and shows that don't make it out into the real world, but they stay in the safe, quiet, calm confines of the discord and the club TWiT feed TWiT plus feed all of that and add free versions of all the shows. $7 a month. When you go to twi.tv/club TWiT, thanks in advance. I think I've now plugged everything. <Laugh> well, one more thing there's I am told a few cabins left. If you want to go with me and Paul throt to Alaska and July on the Holland America, UAM, it's gonna be a great cruise. Lots of fun. We're gonna see we're. I'm told we're gonna see bears.
Leo Laporte / Steve Gibson (01:46:53):
Oters all the Eagles, as well as glaciers what's left of them. Cruise.Tv, still some cabins left. And I would like anybody wants to go to go. They have, you know, inexpensive cabins, if you want. How, how long are you away from it? I'll just miss a week. So I'll miss one show, July 16th of the 23rd. We're gonna go early. I think Thursday, we're gonna go up to Seattle. Spend some time there. Mary Jo Foley to us about a good dive bar we can get wasted in. So that'll be fun. <Laugh> then we'll get on the boat. All hung over. I can't wait. It's gonna be a lot of fun. Cruise.Twi.Tv. You do not have to be a club member to, to go by, by all means. Everybody should join us. You, I invited you, but he, Steve said, no, Lori won't let me go.
Leo Laporte / Steve Gibson / Rod Pyle (01:47:42):
So, Nope, you're stuck a short, short, stuck a shore. We'll have to do a land tour for you. You and Lori. Well, figure something out. Thanks, Steve. Have a great week and we'll see you next time on security now. Okay, buddy. Bye. Bye. Bye. Bye. Bye <laugh> <laugh>. Hey, I'm rod pile editor of ad Astra magazine, and each week I'm joined by TARC Malik, the editor in chief over space.com in our new this week in and space podcast, every Friday, Tark. And I take a deep dive into the stories that define the new space age what's NASA up to when will Americans, once again, set foot on the moon. And how about those samples in the perseverance Rover? When are those coming home? What the heck is Elon must have done now, in addition to all the latest and greatest and space exploration will take an occasional look at bits of space flight at history that you've probably never heard of and all with an eye towards having a good time along the way. Check us out on your favorite podcast. Catcher
... (01:48:39):
Security.
... (01:48:39):
Now.