Security Now Episode 854 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for Security Now, Steve Gibson is here. Lots to talk about one week into the January patch Tuesday update. Steve says it's decidedly a mixed blessing. There's a new router exploit. That's gonna want you gonna get you to wanna reboot your router. And then a step by step examination of a real world. Zero day Log4j exploit. It's all coming up next on security now
Leo Laporte (00:00:27):
Podcasts you love from people you trust. This is TWiT.
Leo Laporte (00:00:34):
Lthis is Security Now with Steve Gibson episode 854 recorded Tuesday, January 18th, 2022. Anatomy of a Log4j exploit security now is brought to you by new Relic. That next 9:00 PM call is just waiting to happen. Get new Relic before it does, and you can get access to the whole new Relic platform and 100 gigabytes of data free forever. No credit card required. Sign up at new relic.com/security now, and by thanks Canary detect attackers on your network while avoiding irritating, false alarms. Get the alerts that matter for 10% off and a 60 day money back guarantee. Go to canary.tools/twenty it and into the code TWIT in the, how did you hear about his box and by collide get endpoint management that puts the user first visit collide K O L I D e.com/twi to learn more and activate a free 14 day trial right now, no credit card required. It's time for security. Now the show we cover your safety, security, privacy online with the man in charge. Steve Gibson. Hello Steve
Steve Gibson (00:01:51):
For the 854th time. Wow. You know, we're getting the hang of this Leo. It's like, okay, just increment the counter. Okay. At add seven to the day of the month, unless it wraps. And off
Leo Laporte (00:02:05):
We go, in fact, I can almost always go, oh, there'll be, there'll be Microsoft patch Tuesday points. That's right. There'll be something wrong here. Some ransomware there you can. It writes itself, Steve.
Steve Gibson (00:02:18):
It you're right. What am I doing here? I can. No, no,
Leo Laporte (00:02:21):
Please. You don't get out of it. No
Steve Gibson (00:02:22):
Way. <Laugh> so we're gonna start off by looking at how well I should say this is episode 854 for the 18th of January. The anatomy of a Log4j exploit. We're gonna start off by looking at how the us pin Agon is dealing with log for Jay and how the us administration at the white house wants to improve the security of open source software. This being, as you said, Leo, the third Tuesday of the month will be looking back at last week's once again, unfortunately, decidedly mixed blessing patch Tuesday, the good and the bad will then look at a very serious new remotely exploitable problem, which affects millions of popular routers and provide a shortcut of the week to immediately check everyone's own router, to see whether they might be vulnerable to this. And <laugh> and if so, just unplug. Oh, oh man.
Steve Gibson (00:03:29):
And oh, I it's bad. And then over a new and very welcome access control standard being introduced by the w three C, which Chrome is already in the process of adopting. We'll talk about that. That's this is really a, a nice piece of technology. We'll wrap up the top portion of the podcast with yet another set of very serious WordPress add-on blunders. I think it was 84,000 sites affected now as like, oh goodness. We're gonna share a little bit of listener feedback, including answering the very popular questions about how to refill empty soda stream
Leo Laporte (00:04:10):
Tanks turns out the topic of the week last week.
Steve Gibson (00:04:13):
<Laugh> it was you and I just briefly mentioned it in passing. I, I got swamped in was like, what? You can do that. How do you do that? So we'll talk about that. And then after a brief spin right progress update, we'll take a look at the inside of the operation of an actual Iranian log for J exploit kit. Oh, wow. So yeah, I think a fun podcast for our listeners. Right. And of course, an engaging picture of the week. Yes. I
Leo Laporte (00:04:47):
Love it. <Laugh> you know, this is the geekiest show we do. I just love the level of, well, you'll see, when you see the, the picture the week, I just love it. I just love it. Actually. We know there are a lot of people who listen to the, this show who are engineers and it person, CIS admins and those, those sort of people. And I wanna talk to you specifically, software engineers, CIED mens. If you, you, you know what, I'm the scenario I'm about to describe you, you know, just got in bed, maybe even had an hour or two sleep. The, it used to be a pager now it's, you know, your phone or your alerts or your, you know, your your DevOps beeper, whatever it is, you've got goes off. Something's not working. Your mind is racing. What could be wrong?
Leo Laporte (00:05:37):
Is it the back end? Is it the front end? Is it a globe global problem? Is it a server problem? Is it us? Is it them? Is it the network? Is it the cloud provider? Do we have slow running queries on the Mongo DB? Did I push a bug in my last deploy? You know what I'm talking about? The mine just goes round and round and round. And now of course your whole team is scrambling you're tool tool, trying to message each other, trying to figure out what the hell's going on. That's the story. If you don't have new Relic now about half of you, <laugh> actually, I saw a study from new Relic that said only half of all organizations have implemented observability for their networks and systems. Those are the people who don't get those 3:00 AM calls or when they do, they go, they look at the new Relic dashboard.
Leo Laporte (00:06:29):
They go, oh yeah, shoot, let me pull that back and push this out. Or let me call Joe up up at ops and have him flip the switch or whatever it is. And it's fixed in your back to bed. That's kind of how you want it set up. You need observability. This new Relic report showed how maintaining network observability is a big issue for companies all over the world, but not if you have new Relic, new Relic is actually 16 D at monitoring products. They started Ruby on. I think it was Ruby on rails when I first became aware of them. But they've so far gone beyond that. These are monitoring programs. You might get separately, but you'd like them all in one place so that your team has full stack observability. And these things just do it. I'll give you some examples.
Leo Laporte (00:07:16):
If you've got an application, you'll definitely want to use their APM, their application monitoring unified monitoring for apps and microservices that even knows. I mean, it goes down, it has the symbol table. It knows the line of code. It could say, oh, here's, here's a procedure that broke. You must have just pushed this, fix it, that kind of thing. Are you using Kubernete you'll love pixie instant Kubernetes, observability there's distributed tracing. So you can see all your traces without any management, headaches, fine and fixed issues. Fast there's network performance monitoring, of course, stop guessing where the performance issues start ditch those data silos for a system-wide correlated view. And that's just four of the 16 tools. It's amazing pinpoint issues down to the line of code down to the node, down to the router, know exactly why the problem happened, what happened, why it happened and resolve it right away.
Leo Laporte (00:08:16):
I mean, this is why 14,000 companies in including DoorDash and GitHub, epic games use new Relic to debug and improve their software, to monitor their performance, to make sure their stack is up and running. And if it's not how to fix it fast. So whether you run a cloud native startup or a fortune 500 company, it takes five minutes to say it up new Relic in your environment, and I've saved the best for last it's free. This is not some trial offer. You get access to the entire new Relic platform and a hundred gigabytes a month of data free forever. You don't even give 'em a credit card, so they couldn't charge you if they wanted to, but they don't cuz they know you're gonna love it. And you're gonna use it more and more. And pretty soon you're gonna say, I want more, but I'm telling you use it free right now.
Leo Laporte (00:09:08):
Every single one of those monitoring tools and a hundred gigabytes of data, which I said is that a lot per month? Is that a lot? And they said, yeah, that's actually pretty hefty operation. You would know it's it's it's a lot. It's not like some, oh, here have a cup of tea. You want the whole bag? Oh, well that's a no and no credit card required. If I were you, you don't have to ask the boss. I would just go new relic.com/security now and do install it right now. N E w R E L I c.com/security. Now that next 9:00 PM call is just waiting to happen. Get new Relic before it does. And if you don't, when you get that 9:00 PM call next week, think of me. Will you? New Relic and new Relic, of course, new relic.com/security. Now you need this thing. You want this thing, go get it. It's free. No credit card needed new Relic. All right. I have a picture of the week that made me laugh out loud. I love this.
Steve Gibson (00:10:13):
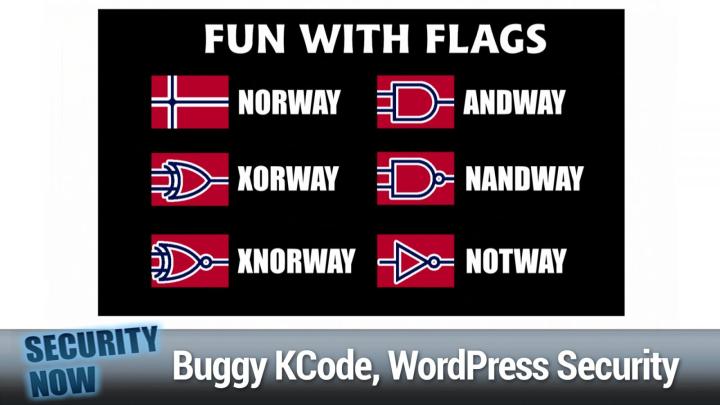
So yes for those who are not looking at the, the screen or the show notes this begins with the inspiration of, from the flag of Norway, which is set against a red field. And basically it has what looks like. Well, when you see it sort of like two wires crossing perpendicularly and there insulated by some whiteness anyway, somebody realized, well, we could do some other flags. For example, you could have the, instead of Norway you could have and way where, you know, those who are familiar with logic diagrams would replace the crossed wires with an and of course, then that would lead to Nway X or way X, Norway, if you invert the output of the X or way. And of course not way. And having looked at those, I realized, well, it's really too bad that we began with Norway nor should have nor right. Because I mean, that's a Norgate. Yeah. So yeah, but no that was the inspiration. So we're leaving that one alone
Leo Laporte (00:11:23):
And by the way that and gate is the inspiration for the TWI logo.
Steve Gibson (00:11:28):
Ah, the TWI logo. Yes. Yeah. That's
Leo Laporte (00:11:31):
Very cool. There you go. All right.
Steve Gibson (00:11:34):
Yeah. Okay. So hack the Pentagon with log for Jay at the end of last year, 2021, the Pentagon pivoted its ongoing hack, the Pentagon bug bounty program, which we've talked about years ago. I think it was 2016 that they launched it. And, and that's something that's being managed through hacker one through the hacker one program, as opposed to like trying to do it in house, which I think was a good idea. They pivoted not surprisingly to track down log for J vulnerabilities on, you know, what, what amounted to potentially thousands of public facing military websites. This was the first time that the us department of defense had marshed the ethical hacker community to tackle an emerging digital crisis in essentially real to time. So, you know, normally it's just sort of like, oh, well, if you find something and you are you're prequalified, remember that they, I think they have 50 something like 50 vetted cybersecurity researchers.
Steve Gibson (00:12:47):
They're, you know, they're not like saying anybody anywhere come hack us. That <laugh> a, I'll probably get you in trouble. You need to be pre-approved. So just after days from the time that the public was made aware of the log for J problem, the, the, the branch of the D O D known as the defense digital service or DDS in connection with hack who, as I said, manages the department's bug bounty program had broadened the scope of the ongoing competition to, you know, for, for testing their own systems and software Katie Olson, the director of the DDS told the record that it was a, a quick effort and a really elegant solution to use a contract that we already had in place with the crowdsource research community to very quickly do a scan of what might be affected within the D O D. Okay.
Steve Gibson (00:13:53):
So as a result, the roughly 50, as I said, previously, vetted cybersecurity researchers who were already participating in the existing hunt were given the additional assignment to scour all dot mill websites and report any potential weaknesses or exploits caused by the log for J vulnerability. This on the I change that is in their targeting coincided with the decision we talked about last week by the us department of Homeland security whose own bug boing program was just in the process of being launched to similarly broaden the scope of its own bug search, major tech companies and federal officials you know, also have scrambled to grasp the full extent of the log for J flaw warning that potentially, as we know, hundreds of millions of devices around the globe could be compromised. The CSA C I S a last month issued an emergency director requiring all civilian federal agencies to mitigate the threat as re as, as I've often joked, no Christmas until you do, even though Christmas did happen on schedule.
Steve Gibson (00:15:08):
Though top agency officials on Monday last Monday, repeated that they have not seen a malicious actor use the vulnerability to breach federal departments and agencies at the same time. There's the expectation that if that had been done, it would be, you know, definitely kept on the down low during a conference call with tech reporters, Eric Goldstein, who's the SA's executive assistant director for cybersecurity stated that the effort had already that is the, the, the government's effort had uncovered 17 previously unidentified assets that were vulnerable to log for Jay. All Eric said, which were remediated before any intrusion could occur. He added that it demonstrated the extraordinary power crowdsourcing brings to the research community to help not only the us government, but the broader nation to find vulnerabilities before ER adversaries can abuse them. So, anyway, although the Pentagon was already using an ecosystem of passive scanning software and technology to continuously monitor its assets, as we know, log for J differs from previous cyber, I, by not centering around specific types of hardware or software, you know, like VPNs or firewalls, the trouble was at the time of its initial disclosure.
Steve Gibson (00:16:43):
There was no mature automated solution available to track down locate and verify exploitable vulnerabilities, a guy named Lance clay horn. Who's a digital services expert at the DDS, told the record. He said, that's where the crowd really comes in to save the day. They cannot only tell you, Hey, I actually went and found this and it's vulnerable. Like for sure they are able to also say, here's the evidence and it's exploitable. And that's a problem. So at first blush public facing military websites may not seem like an attractive target for hackers. Again, <laugh> you do risk bringing down the wrath of the us government and the D O D however there's long been a concern within the DOD that a sophisticated threat actor could use a previously unknown vulnerability to penetrate us network. Yeah. Like anybody on the net should be worried and to gain a foothold in the department's systems.
Steve Gibson (00:17:50):
And there is that massive non-classified internet protocol router network known as Nier N I P R net literally stands for non-classified internet protocol, router network hacker one's CIS. So, and who also calls himself the, his, the chief hacking officer. Chris Evans said that once the bug bounties were expanded to explicitly include log for Jay hackers responded immediately and competently with numerous valid reports pouring in within the first hours of that explicit expansion, the DDS paid competitors $500 per discovered, vulnerability, and an additional 500, if proof of exploitability was also provided. And I don't know, Leo, you know, given the amount of money that, that us has every time I look at those numbers, that seems that cheap. Isn't it? It, it does. Yeah. It's like, if you, if you're serious about getting these problems rooted out, you know, a couple grand at least, you know, really.
Steve Gibson (00:18:58):
Yeah. I agree. Wow. However, neither Katie Olson, nor Lance kho, both at the DDS were willing to disclose how many vulnerabilities had been during the retooled bug bounty. Lance did say we've paid out a chunk. Okay. But, well, a whole $700. <Laugh> exactly a lot of money. <Laugh> exactly. And Katie hopes that even more us government agencies will move to establish their own bug bounty program. You know, it does require some focus, but one would hope that they already have, you know, they've already gotta have it. Right. And they've gotta have security people if they don't, they've got bigger problems. So how, how tough can it be to establish a relationship with hacker one and just, you know, copy what the, what, what, what the DHS and the E O D have done it's been done, right? There's already agreements and contracts in place.
Steve Gibson (00:19:55):
Just change the, you know, the, the heading on the top of the page and, and get the, the other agencies going it's I can't understand why they wouldn't have done that already. Speaking of the us government and specifically the white house last Thursday, 13th, the Biden administration convened what they called the open source software security summit. <Laugh> having the state a goal of getting public and private sector organizations to rally their efforts and resources with the aim of securing open source software and its supply chain. Okay. <laugh> good goal. Although not only about log for J log for J was the clear catalyst behind the summit in the public sector. The list of participants pretty much was the who's who, including the de the deputy national security advisor for cyber and emergence emerging technology. That's a <laugh>, that's a department that was Anne Newberger, national cyber Chris English officials from the office of the national cyber director, office of science and technology policy.
Steve Gibson (00:21:15):
The department of defense, the department of commerce, the department of energy, the department of Homeland security, the cyber security and infrastructure security agency. Of course, the, the CSA, the N I S T and the NSF, the private sector was well represented by AAI, Amazon, Apache, apple, CloudFlare, Facebook slash meta GitHub, Google IBM, the Linux foundation, the open source security foundation, the opensource security foundation. I didn't know there was one good Microsoft, Oracle, red hat, and VMware that participants focus their attention onto three topics. First preventing security defects, and vulnerabilities in opensource software. A guess, good, let, let let's do that. Improving the process for finding security flaws and fixing them. And third shrinking the time needed to deliver and deploy fixes all worthy goals. The white house's after action report wrote most major software packages include open source software, including software used by the national security community.
Steve Gibson (00:22:36):
Opensource software brings unique value and has unique security challenges because of its breadth of use and the number of volunteers responsible for its ongoing security maintenance. So this sounds a little bit like what the FTC we talked about last week, what they said, you know, they did appreciate the, the particular challenges it represented because it, you know, it was not commercial. It was all free and just done by random people. During the summit, Google proposed the creation of a new organization that would act as a marketplace for open source maintenance that would match volunteers from participating companies with critical projects that need the most support Kent Walker, Google's president of global affairs and chief legal officer, both for Google and alphabet. He was quoted saying quote for too long. The software community has taken comfort in the assumption that open source software is generally secure due to its transparency and the assumption that many eyes were watching to detect and resolve problems.
Steve Gibson (00:23:54):
But in fact, while some projects do have many eyes on them, others have few or none at all growing reliance on an open software means that it's time for industry and government to come together to establish baseline standards for security, maintenance, Providence, and testing, to support it with money for Christ's sake, at least exactly. You know, that's the problem. They use the stuff for free, and then they go, oh yeah, it's broken, it's broken, supportive <laugh> to ensure national infrastructure. He said, and other important systems can rely on open source projects. At least he's not saying only use proprietary, but it is Google after all. So, right. Yes. These standards should be developed through a collaborative process with an emphasis on frequent updates, continuous testing and verified integrity. Yes. Wouldn't that be nice if only as you said, Leah, we had the money. So yeah, this is nice to see, but for me, at least I have no idea how we would get from where we are today to there.
Steve Gibson (00:25:06):
The end of the white house's report suggested that the government's purchasing power could be and would be yaw used to bring about that change. What was written said, president Biden has made software security, a national priority, his executive, okay, I'm gonna just bite my tongue. His executive order on cyber security requires that only companies that use secure software development life cycle practices and meet specific federal security guidance will be able to sell to the federal government for are the first time. Okay. Wow. Leveraging leveraging the purchasing power of the federal government to drive improvements in the software supply chain improvements that companies and governments around the world will benefit from. Yeah. So if we had not been paying attention to the way, things never seem to get done in Washington, that buying power statement might be encouraging, but it's just more bureaucracy. We know that our present system is far from perfect.
Steve Gibson (00:26:25):
It's a constant and necessary theme of, of this podcast, but efforts like Google's project zero trend micros, zero day initiative, hacker one's, bug bounty management, Theone to own competitions, the annual black hat and DEFCON conferences. Everyone contributing to chromium the academic research and the occasional crowdsourced funding of intensive security audits of mission CRI critical packages. These are all existing proven and high, highly effective solutions within their own realms, which have all emerged organically. They have thrived year after year because they have been effective. And they've made sense if the us government wants to help its time would be better spent. I think exactly. As you said, Leo in peeling off some taxpayer money and not too much said, you don't wanna, you don't wanna wreck the status quo. You know, you don't wanna direct all this by just throwing money at it and how it all go sideways and put some additional funding behind these initiatives that are limited in what they can do due to lack of support for personnel or the size of bug bounty motivations.
Steve Gibson (00:27:55):
Back in 19 65 back in 1965, the us Congress created an independent agency known as the national endowment for the arts. It offers support and funding for projects, exhibiting artistic excellence, artists, write proposals and apply for grants to receive funding. I'm all for change and for improving what we're doing. But we're also largely doing the right things. Now doing more of what we're already doing. Seems like a nearer term solution that could be implemented today with a greater guarantee of results, a national endowment for the improvement of software quality, if properly administered might be a worthy consideration. Good. So yeah, maybe, maybe about it. Yeah.
Leo Laporte (00:28:52):
<Laugh> yeah. There's just so many open source projects that end up as part of commercial software, but nobody's paying for 'em, they're maintained by one guy's, you know, volunteer and you know, that's kind of long forge a story and but they're used as infrastructure. These companies need to kind of pony up and support this. Yeah, I
Steve Gibson (00:29:12):
Think, yeah, that, that fabulous picture of the, it's not a house of cards. It's like a tower of crazy blocks with, you know, down at the very bottom one little toothpick size thing. That's like holding up the whole, whole crazy mess and, you know, maintained thankly by some guy in Nebraska, you know, it's like, okay, okay. Speaking of software quality <laugh> last Tuesday was another of Microsoft's all too frequent, mixed blessing patch Tuesdays. Okay. So first here's the good news. A total of 97 vulnerabilities of varying severity were patched and there were also an additional 29 vulnerabilities fixed in Microsoft's edge. The browser of the 97 non-ED vulnerabilities nine were classified as critical and the other 88 as important overall, the patches cover windows and windows components, edge exchange server no surprise there. Office and offices components, SharePoint server.net framework, Microsoft dynamics, some open source software, even hyper V defender and the remote desktop protocol RDP.
Steve Gibson (00:30:32):
Dustin Childs with trend micro zero day initiative said, this is an unusually large update for January over the last few years. The average number patches released in January is about half this volume. We'll see if this volume continues throughout the year. It's certainly a change from the smaller releases that ended 2021. Okay. So Microsoft patched 67 bugs last month in December. Now we're at 97. Okay. Now Microsoft classes a zero day vulnerability differently than we do here. My feeling is that we need to reserve the term zero day, which has unfortunately taken hold as click bait for a vulnerability, which is first discovered when it is observed being used in the wild. The point is that patching that puppy, which is currently being exploited is much more important than patching a problem. That's only potentially exploitable and which has been reported responsibly and privately. So nobody knows about it except the, the, the group that can fix it.
Steve Gibson (00:31:45):
But Microsoft also classifies vulnerabilities that have been irresponsibly and publicly disclosed as zero days. And also regardless of how bad they are. So like, you know, somebody discloses a vulnerability, the it, you know, has the pizza come out cold? Oh, that's a zero day. Oh, okay. That's a CVE of 10 babies. <Laugh>, that's, that's critical, man. Don't mess with that. <Laugh> you know, but, okay. So that's what Microsoft wants to call 'em. I can see their point since the race is then on to get the world path before the publicly disclosed vulnerability can be weaponized and actively deployed. So I accept their definition in this case. And that also means that a total of six unex exploited, but published zero day vulnerabilities as they want to call them were also fixed last week. So overall the breakdown by type was 41 elevation of privilege vulnerabilities.
Steve Gibson (00:32:53):
And we know those are bad. Once you gain a foothold 29, remote code X and X execution vulnerabilities, obviously never good nine security feature bypass vulnerabilities, which <laugh> could be anything, nine denial of service vulnerabilities, which mostly means it's easy to crash something. Six information disclosure vulnerabilities, something leaks and three spoofing vulnerabilities. Okay. And separately those six unexploded, but published zero days as they call them, which were patched were. And remember, there was a mention of open source. There was the open source curl, remote code execution, vulnerability, but we'll, we'll, we'll look at that in a minute. It's not clear to me how that executes remote code it's it's in interestingly funky, but anyway, there's also a live archive. Remote code execution. Vulnerability definitely looks like you could execute code with that one. Then four, both of those are the open, the two open source ones.
Steve Gibson (00:33:59):
Then we have wind windows, user profile, service elevation, or privilege windows certificate, spoofing windows event tracing discretionary access control list, you know, DLE D ACL denial of service. So that crashes something and windows security center, API remote code execution. Okay. Those first two, as I said, curl and lie of archive which are the only remote code execution problems among those six had already been fixed by their maintainers, but the fixes had not yet been incorporated into windows until last Tuesday. So last Tuesday's patch, Tuesday updated windows use of those windows include of those. Now reading the details of the curl problem. It's unclear, as I said, how it, if could like offer remote code execution, here's what they said when curl version greater than, or equal to 7 20 0 and less than or equal to one that fixed it 7 78 0 connects to an IMAP or pop.
Steve Gibson (00:35:08):
So this is curl connecting to an IMAP or pop three email server to retrieve data using start TLS to upgrade the connections, LS security, the server can respond and send back multiple responses at once that curl CAS curl would then upgrade to TLS, but not flush the NQ of cash responses instead continue using entrusting the responses it got before the TLS handshake as if they were authenticated using this flaw. It allows a and in the middle attacker to first inject the fake responses, then pass through the TLS traffic from the legitimate server and trick curl into sending back data to the user under the assumption that the attackers injected data comes from the TLS protect server. Okay. So that's a cool hack, right? Somebody figured out that, you know, curl is gonna want to elevate its its security to TLS, assuming that the I map or pop three server in the hello handshake indicated that it supports start TLS.
Steve Gibson (00:36:36):
And so that would happen. So this is a very subtle and clever bug that comes about as a side effect of the start TLS clues, which is really what it was. You know, it was the original way of providing email encryption over the traditional SMTP IMAP hop ports before they obtained their own dedicated TLS connection ports, which they have now. And it's exactly the sort of bug that tends to creep into systems that were being pushed to do things they were not originally designed to do such as on the fly switching an UN encrypted connection to using encryption. Okay. So that's the curl bug. And as I said, someone claimed that it could be used for remote code execution though. Didn't explain in this disclosure how that could be. So just looked like you could get some, you know, a bad guy, a man in the middle could sneak some stuff in into an email client query that didn't actually come from the then authenticated server, but the live archive bug affecting versions 3.4 0.1 through 3.5 0.1 is a use after free flaw in its copy string function when called from either do uncompress block or process block.
Steve Gibson (00:38:05):
So that one might well be leveraged for remote code execution. If a bad guy found some way to get the user or the system to use live archive, to decompress a specially and maliciously formed archive. That one, I believe in any event, patching should not be postponed since many of these already do have proof of concept exploits published. Remember their Microsoft zero days. And as we often observe attacks never get worse. They only ever get better mostly though, compared to other things going on right now, this is certainly not a four alarm fire. So, you know, not for that reason. Oh, and if you encountered some of last weeks breathless, oh my God patch. Now windows contains a wearable flaw press coverage. The reason I didn't lead with it is that for windows IIS server, to be vulnerable to it, which is what that breathless press coverage was about requires enabling an obscure and non default registry key under services.
Steve Gibson (00:39:18):
You know, current control set services, HTTP parameters. You need to have someone needs to have enabled something called enable trailer support and set that to one we're all familiar with the way HT TP headers work, where they form metadata, such as cookie information and assets creation, timestamp, probably its lifetime before expiration. You know, like, you know how long the client is allowed to cash it before explicitly checking to see if it's been updated and so on. Well, to turns out that it's also possible who knew for additional headers in this case called trailers to be included after a chunked style encoded query or response just a few weeks ago, we've clearly covered chunk styled in coding. Cuz that came up in something we were talking about. Okay. So you can have headers after the content. Okay. What, this really feels like the HTTP designers ran out of important work to do and sat around asking themselves what else could we add?
Steve Gibson (00:40:40):
You know? And that, that never ends well. So they invented a previously unappreciated need suggesting that it might be that a client or a server would not be able to fully form its query or response headers until after the body of the query or the response had been formed. No one knows why that might be true. <Laugh> but Hey, it could happen. Remember that since the Dawn of the web, this had never actually apparently been a problem, but perhaps they got their important work finished early. So they decided to define a solution for this one. Anyway. So yes, it turns out since HTTP 1.1, in addition to headers, it's also possible to have trailers, but as I said, windows IIS server does not have that feature turned on by default. And since no one actually uses trailers, it's unclear why anyone would've ever turned it on, but okay.
Steve Gibson (00:41:56):
Until last Tuesday, if someone had actually turned it on, then yes, IIS could theoretically be exploited by leveraging some mishandling in its non default enabled support for HTTPS unused and unnecessary trailers feature. Now, as for that flaw being wearable, it seems to me that requires somewhere for the worm to go. And if no one else running IIS has that unused and unneed and disabled feature enabled, that's gonna be one lonely, wanna be worm desperately trying to propagate, which kind of reminds me of my adolescence. Anyway, <laugh> despite all of this not reproduce prop <laugh> despite all of this, since we all agree that worms are bad. And since the attack complexity is quite low, this non threat earned itself a CVSs of 9.8. So that alone must be what the other tech press saw. Yeah. And thought, oh my God, the pizza gonna be cold.
Steve Gibson (00:43:16):
It is gonna be a, it's be cold. Cold pizza. Now actually I've been told cold pizza could be quite tasty. It is. So it's an excellent breakfast. Maybe this treat, maybe wasn't the <laugh> wasn't the best example to use in any event? What was never a huge problem, no longer any problem? Well, it might be that was patch. Tuesday's good news. Here's the other shoe as threat, post headlined, their coverage, Microsoft yanks, buggy windows, server updates. So maybe there's hope for that worm after all threat post wrote, since their release on patch Tuesday, the updates have been breaking windows causing spontaneous boot loops on windows, domain controller servers breaking hyper V and making the R E S volume SI systems unavailable <laugh> whoa. Microsoft has yanked the windows server updates. It issued on patch Tuesday after admins found that the updates had critical bugs that broke th those three things, people who were quite frustrated were venting all over Twitter.
Steve Gibson (00:44:37):
I saw one posting, <laugh> asking the question. Does Microsoft even test these things before releasing them? There was actually a great deal of frustration. I heard about this directly from many of our listeners and Twitter followers. In addition, it's been confirmed that Tuesday's updates for windows 10 desktop machines were also breaking L two TP VPN connections. They no longer worked bleeping. Computer was tracking this saga day to day and blow by on Thursday. They reported that Microsoft had pulled the January windows server cumulative updates and were no longer accessible, accessible via windows update. But as of that afternoon, Microsoft had reportedly not also pulled the windows 10 and windows 11 cumulative updates that breaking L two TP VPN connections. And that was confirmed. So it's unclear how that went. This is all the mixed blessing of windows updates. Recently we're pushed to install them immediately with breathless though, in this instance, unwarranted warnings of a sky falling from a server worm, but installing these things through most of 2021 and continuing that trend into 2022 has resulted in the loss of mission, critical functionality. So damned if you do damned, if you don't actually don't appears the increasingly attractive option, given Microsoft's recent side effect, latent updates, you know, let somebody else go there first, see if they survive. And if so then cautiously follow and Leo, we're not gonna have to cautiously follow your advice about this next sponsor. I'm gonna have some water
Leo Laporte (00:46:30):
<Laugh> while you tell us, okay, that's a bit of a stretch, but I'm glad you did. This is actually something you all know all about. And like a lot, one of our very first episodes I think was episode two was about honey pots. Yeah. Of course at the time making a H pot was a non-trivial task. We interviewed one of the, the creator, one of the very first or not interviewed. He was on a panel in Boston with us for last Bruce who was it? It was Steve, was it Steve Bevin? No, anyway he implemented a, a honey pot, I think, in the sixties. And then of course, a monk honey pot, honey monkeys that we were talking about in episode two, which is now 15 years ago almost. We're all also, you know, a little tricky to set up.
Leo Laporte (00:47:16):
Thank goodness. Times have changed. We've come a long way, baby. And now you can have a honey pot. I got my own honey pot right here. It's my thanks. Canary. This is a desirable object on the network that doesn't look vulnerable. It looks valuable. It looks like, well, whatever you want it to look like a skated device or a windows server or in this case, it's my network attached storage. And it doesn't just look like one. It behaves in every respect. Like one, the Mac address is consistent. The inner her face is consistent from the point of view of a bad guy, it looks like something on your network that he or she really wants to get into. This is the things Canary, it's brilliant. So easy to configure. So easy to set up. You just set it and forget it. It sits in your network, but here's the thing.
Leo Laporte (00:48:06):
If somebody breaches your network, if they use for Jay to get into your network, and then you close the barn door. Yeah. You may say, well, now our network is safe from new intruders, but do you know if somebody's inside already? How do you know? Thanks to Canary? It's like the Canary and the coal mine. It lets you know, the, the problem is companies usually find out too late that they've been reached, right? Even if they've spent millions of dollars on it, security, cuz nothing's perfect. You thought you were, you thought you were in great shape. And then long for Jake came along. Attackers are sneaky. Once they get in, they lay low they'll prowl around. They'll examine the network. They're looking for things they can export them might be valuable. They're looking for where you back up your data so they can make sure if they're using ransomware.
Leo Laporte (00:48:55):
It, it gets that as well as everything else. They're they're, they're hunkered down and they're in there on average, it takes what was the number 191 days for a company to realize there's an intruder on the network. That's six plus months that somebody can wander around inside your network, doing whatever they want. The problem is, as soon as they see the things Canary and they try to log in, you know about them because you instantly get an alert and I'm not talking about those avalanche of useless alerts. I mean, I'm talking an actionable alert. You can do something with right away. You know, there's a dev somebody just hit this network attached storage with this login. They came in from IP address XYZ. They spent three. You get everything you need to know so that you can act and remediate. It can be on active directory.
Leo Laporte (00:49:48):
It can be registered as a device or a person on active. Well, we can also serve files. They call 'em Canary tokens. So I can create with this, a bunch of PDFs, word documents, Excel, spreadsheets, anything I want. Well, that's what they look like. But when the hacker tries to open and examine them immediately, I'm notified. I just love this idea. Canaries can be deployed throughout your entire network. You can make 'em look like anything. You want a router, a switch, a NAS server, Linux box, a windows server. You can put fake files on them. You can name them in ways that gets the attention of a bad guy. When attackers investigate, they give themselves away. You're instantly notified. And by the way, way notified in exactly the way you want with your Canary. You'll get a console, but you also can get an email, a text message.
Leo Laporte (00:50:35):
You can do it through slack. You can. They supports web hooks, which means you pretty much do it anywhere. It supports CIS log. They even have an API. If you wanna write a custom front end, you won't be inundated with false all alarms. Just the alerts that make a big difference. Canary was created by people who have trained companies, militaries, governments, how to break into networks. They really know exactly how it works. And with that knowledge, they built the best honey pot out there. You'll find canaries. They're deployed on all set and continents. One of the best tools against data breaches and a very affordable taboo. Now I'll give you an idea of how this works out. You, you might want one or two canaries for a small business, hundreds of some banks and casinos and places like that have hundreds of canaries all over.
Leo Laporte (00:51:24):
They're just, it's easy to manage. In fact, you even get a service. If anything goes wrong. If you sit on your Canary, they'll send you new one right away, go to canary.tools/twi. As an example, let's say you want five Canary, 7,500 bucks a year. You get that hosted console. You get free, upgrade, support and maintenance for that whole year. By the way, if you use the offer code TWI in the hated, you hear about a box 10% off that price for life. So that's a very good deal. And because they know you might be listening to me and saying, well, I don't know. They offer a two month money back guarantee for a full refund and hardly anybody ever says, I, I don't like this. I wanted my money back. But if you do, if you feel that way, no ask two month money back guarantee. I think you're gonna love your Canary. If you go to Canary dot tool slash love, you'll see all the love that people are bestow upon Canary, go to Canary dot tool slash TWI to get yours. Don't forget the offer code TWI in the, how did you hear about his box? C a N a R Y the Canary in the coal mine, Canary tools slash TWI. This is such a great idea. Everybody ought to have some canaries in their coal mine. If you know what I mean. Now let's get back to Steve
Steve Gibson (00:52:44):
Gibson, Steve. Okay. So this is important and everybody gets to participate. Okay. <laugh> this was not good. Okay. So the, the, the bottom line is, might be time once again, to check for router firmware. A updates. Yeah. Darn, but I know, but you can go to GRC dot S C and this episode number GRC DOTC slash what is this? 8 54. Yeah. And that will tell you uhoh whether you are okay or not. And maybe is this set up? It should have given you more than that already. Let me go directly. There we go. There you go. Probing my port tooth 20,005. Yes. Okay. That's not a port I'm familiar with not a port anybody's familiar with. Okay. So oh, the security. Yeah. It's your stealth. Good. The security research firm Sentinel one has discovered that some common code licensed by a of prominent router manufacturers contains a highly critical remotely exploitable flaw among the routers known to be affected.
Steve Gibson (00:54:14):
Are those by net gear, TP link Tenda eTax delink and Western digital. Holy cow. I know. So here's what we know. They, or rather he at Sentinel one, his name is max discovered a high severity flaw in the what's known as the K well, K codes is the company K codes, net USB kernel module used by that large number of network device vendors, and affecting millions of end user router devices. This allows attackers to remotely exploit the vulnerability to execute code in the kernel Sentinel labs. Max's company began the disclosure process last year on the 9th of September. And the patch was sent to licensee router vendors on the 4th of October. So it should be incorporated into router firmware updates. By now that's more than 90 days at this time, Sentinel one has not discovered evidence of in the wild abuse. Okay. So here in the author's voice is how this all began.
Steve Gibson (00:55:23):
He said, as a number of my projects, start when I heard that PO to own mobile 2021 had been announced. I said about looking at one of the targets, having not looked at the Netgear device when it appeared in the 2019 contest, I decided to give it a look over while going through various paths through various binaries, I came across a kernel module called net USB, as it turned out, this module was listening on TCP port 2, 0 5 on the IP 0 0, 0, do zero provided that there were no firewall rules to, in place to block it. And typical consumer routers don't have any. That would mean it was listening on the wan as well as the land. And he says, who wouldn't love a remote Ker bug net USB is a product developed by K codes. It's designed to allow remote devices in a network to interact with USB devices, connected to a router.
Steve Gibson (00:56:40):
For example, you could interact the printer as though it is plugged directly into your computer via USB. This requires a driver on your computer that communicates with the router through this kernel module. But of course you don't have to be using this to have it there alive and running in your router. If it just has that net USB feature, which they licensed router manufacturer licensed from K codes, okay. He then proceeds to provide a detailed take down description of his successful hunt for a critical vulnerability in the K code code. He discovered a dangerous switch function driven by a command type that's by the user and the rest does not end well. I provided a link in the show notes for anyone who wants all the gory details. So it's insane. And it is so wrong that this buggy K code service is bound to the routers wan essentially 0 0, 0, 0 is all interfaces on the stack, as opposed to, you know, if, if it were bound to 1 92, 1 68, zero.one or.one, do one that is bound to the, to the to the gateway interface.
Steve Gibson (00:58:03):
Then it would be listening on local ports inside the land, which is what everyone wants. Nobody wants th this thing listening on the land, but it turns out by default. It is. That means it is instantly discoverable by bad guys anywhere. And of course, by showdown, it also means that it's instantly testable as we started out talking about by any port probe. And I just happened to offer a free online port probing service. So the other link I provided is a GRC DOTC shortcut to instantly allow our listeners at anyone to check any router there behind for this vulnerability, open your browser and just put in GRC DOTC slash 85 4. This week's episode number. This will jump you to GRCs shields up custom port probe pre-loaded to check port 2 0, 0 5. You'll see, on your browser screen, it sends a bunch of TCP SIM packets spread out over a few seconds.
Steve Gibson (00:59:15):
I think it's five seconds. I send one every half second, so it's not to overload anything and to redundantly send TCP sins to make sure that we'll see if we get back a, a Sy that will be sent to the IP address. Also shown on that page to quickly and privately check your browsers publicly exposed wan interface, to determine whether it's accepting incoming TCP connections over port 2, 0 5. It should not be if it is unplug it, I mean really unplug it. Or if you can, at a firewall rule, if your router allows you to, to explicitly block that port on the, when interface, until you're able to update your routers firmware, hopefully for a, a update is available. As I said, max, who discovered and responsibly disclosed this and waited patiently for more than 90 days until last Tuesday, the 11th before going public with it finished his disclosure by writing this fall, vulnerability affects millions of devices around the world.
Steve Gibson (01:00:26):
And in some instances may be completely remotely accessible due to the large number of vendors that are affected by the vulnerability. We reported this vulnerability directly to K codes to be distributed their licensees instead of targeting, just for example, the TP link or the Netgear device in the contest. This ensures that all vendors receive the patch instead of just one during the contest, while we're not going to release any exploits for it, there is a chance that one may become public in the future. Despite the rather significant complexity involved in developing one, we recommend that all users follow the remediation information above in order to reduce any potential risk. And we have another example of something good that came from Theon Theon to own competition. Now let me just say, I did read in detail, his posting. He did not develop an exploit, but he walked anybody who's competent right up to one.
Steve Gibson (01:01:37):
Also this is because this is a common code across a large number of routers, all Linux based, the tools are there for developing it. That means that if you create one exploit, you literally you're getting millions of devices, which are trivial to find, and you're able to execute your own code on those all common Linux platforms. So it's not just one make and model. It's just not one make it is cross vendor. This is really gonna be juicy. No, have to be clear if it says closed, are you okay? Instead of stealth, obviously open is bad. Open is yes. Open is the bad news. Closed is fine. Oh, okay. Meant, yeah. Closed is fine. All it means is that your router bounced back a no, it responded. Yeah, exactly. Yeah, exactly. Probably sent back a TCP reset saying, you know, I got your probe, but I'm not open for business.
Steve Gibson (01:02:51):
That's fine. Stealth is cooler. It just means that no, no response was returned as no one, no one's business that there's even anything at that IP listening open is the danger. And you can't do this from outside your house. You have to do it from within the correct. Correct. I, I did that. I that's clearly the design intent of shields up because otherwise it would allow bad people to probe other people's IPS and that would've been not good. Yes. Yeah. Yeah. So you've got to do it, you know, from the land, which you want to verify, but just, again, let, this is not a small thing. Let, let me please encourage our listeners grc.sc/you know, 8 54, if you're at work and, and you've got you know, a, a family member or kids are at home, give 'em a call, have them do this.
Steve Gibson (01:03:45):
You know, you definitely want this thing. There's no way this is not gonna be exploited. There's no way because it's Linux because it's cross browser. I mean, cross router vendor, there's just no way. This is not gonna and getting exploited. Okay. Chrome is going to be limited or limiting its access to private networks. And this is a win and a half. It will soon be implementing probably the first of the Chrome. Well, the Chrome chromium I, we, we can hope that safari and Firefox follow a newly proposed web standard, which is known as private network access or PNA. If anyone's interested, I've got a it's a w three standard, just like, I think it was January 2nd was the date on this. So the ink is not dry or the HTN ML not yet set. I've got a link in the show notes.
Steve Gibson (01:04:46):
It will apply new and welcome. In my opinion, controls to block external internet websites from querying and interacting with devices and servers located inside local private networks. And of we've, we've talked about this problem. A number of times already, as I mentioned, this change will occur as Chrome implements this new w three C spec known as private network access. It'll be rolled out in the first half of the year for Chrome PNA adds a mechanism through which external internet sites must first ask systems inside local networks for explicit permiss before being allowed to have any sort of connection. Okay. Now that's what some of the coverage says, and it's not exactly the way this works. What happens is Chrome will notice when an external internet based server is doing something that requires internal access, and then Chrome will take responsibility for saying wait a minute.
Steve Gibson (01:06:07):
Let's see if that's okay. Okay. So Chrome and any other PNA compliant browsers will first send a, what's known as a cores pre-flight request C O R S is cross origin resource sharing. A nice addition to the web standard for, for controlling, who gets to talk to who cross origin. So Chrome will first send this. What's known as a cores pre-flight request to the local server or service, whatever it is on the land before granting any internet originating request for a private network resource. This cores request will ask for a needs to obtain explicit permission from the inter from the internal target server or service, the pre-flight request, which is just a fancy name for an extra header is a new header. It is access hyphen control, hyphen request, hyphen private hyphen net works access control request, private network colon true is what Chrome sends out and the response to it must also contain a header access control, allow private network colon true.
Steve Gibson (01:07:38):
If the targeted local device such as servers or routers failed to respond, internet websites will be blocked from connecting as they never should probably be allowed to. Anyway, I can't imagine why that, like what that's used for. Maybe there is a legitimate use. We know it's been exploited a lot. So this is a wonderful improvement in cross origin access control. As we know, and have devoted a number of podcasts to explaining bad guys have figured out that they can use a browser as a proxy to relay connections to an individual's or a company's internal network. For example, a malicious website could contain code that tries to access an IP address like 1 92, 1 6 8 0 1, which will often display the routers the, the land routers local admin log on page, which is only accessible by design from the router land interface. But because the request is coming from the user's browser on the land, the router assumes that the user wants to log in.
Steve Gibson (01:08:48):
So as we've seen, when unwiting users access a malicious site, it's been possible to in their browser to make a request to their router without their knowledge, this can send malicious code to bypass the router's authentication and modify router settings. It's happened variations of these internet to local network attacks could also target other local systems such as internal Sur rivers, domain controllers, firewalls, or even locally hosted applications. So by introducing the PNA specification inside Chrome and within Chrome's permission negotiation system, Google will be moving to prevent such automated attacks. And I say, yay. A according to Google, a version of PNA has already been slipped or shipped. <Laugh> slipped into and shipped with Chrome 96, which was released back last November. But full support will be rolled out in two phases this year with Chrome 98 in early March and Chrome 1 0 1 scheduled for late may in this coming marches, Chrome 98 Chrome will begin sending pre these preflight requests ahead of, of private network sub resource requests.
Steve Gibson (01:10:15):
These preflight preflight re failures will only display warnings in the dev tools of the browser without otherwise affecting the private network requests. So they remain allowed and unblocked. So this, you know, this gives devs who are wanting to bring up support for this affirmative information about the fact that this is going on Chrome, gathers compatibility data and reaches out to the largest affected websites. So Chrome will be using this for instrumenting their own research. And if it turns out that there are, you know, major websites doing this, they'll notify them that, Hey, you know this is gonna start getting blocked here before long Google expects this to be broadly compatible with existing websites and, you know, yeah. Why wouldn't it be? It doesn't break anything yet then know earlier than late Mays scheduled Chrome 1 0 1, assuming that established compatibility data indicates that the change will be safe enough and that sufficient outreach has successfully occurred.
Steve Gibson (01:11:27):
Chrome will begin enforcing that pre-flight requests must succeed and it will otherwise fail those externally sourced requests. They said a deprecation trial will start at the same time to allow for websites affected by this phase to request a time extension. The trial will ask for at least six months. So, you know, the concern that's evidence here is that as is always the case tightening up security may break something that was happening, you know, little known and unseen in the background. But overall, this is a welcome improvement. If there is something on the land that really does intentionally wish to be able to receive and respond to requests originating from the user's browser, but triggered from an outside external source, then, you know, such devices will need to be updated with an awareness of these new forthcoming PNA controls. And that simply entails replying with the newly added header to continue enabling what had always been allowed before.
Steve Gibson (01:12:47):
So not a big change to make easy to do. And I just think this is a big, useful step forward. So yada, and actually it was a couple of Google guys who apparently were responsible for getting this thing through the w three C so props to them just finish with three high severity flaws, you know, just mentioning them in WordPress. As I mentioned at the top of the show, as a consequence of these three 84,000 WordPress based websites are affected, and they're very serious. The guys at word fence titled their disclosure, 84,000 WordPress sites affected by three plugins with the same vulnerability they wrote on November 5th, 22, 21. So, you know, November of last year, the word fence threat intelligence team initiated the responsible disclosure process for a vulnerability. We discovered in login slash signup popup, a WordPress plugin that is installed on over 20,000 sites.
Steve Gibson (01:13:58):
A few days later, we discovered the same vulnerability present in two additional plugins developed by the same author sidecar woo commerce installed on over 60,000 sites and wait list. Woo commerce. The back in stock notifier, which is installed on over 4,000 sites, this flaw made it possible for an attacker to update arbitrary site options on a vulnerable site, provided that they could trick a site's admin into performing an action, such as clicking on a link. They said we sent full disclosure details on November 5th, 2021. After the developer confirmed the appropriate channel to handle their communications. After several follows a patched version of login sign up signup popup was released on November 24th while patched versions of sidecar, WooCommerce and wait list w commerce were released on December 17th. So they waited 90 days again. And now they're well, not December. Yeah, not in that case, but you know, they, they gave time to get these things pushed out and updated.
Steve Gibson (01:15:17):
They said we strongly recommend ensuring that your site has been updated to the latest patched version of any of these plugins, which is version 2.3 for login slash signup popup version 2.5 0.2 for list w commerce and version 2.1 for the sidecar w commerce at the time of the publication. So anyway, just a heads up it's, you know, when I hear that something like w commerce is running on WordPress. Wow. You know, we hear about commerce sites being attacked all the time. And WordPress is not a place you want to do something that is really security, sensitive, you know, blogs and and comment scrolls and comment threads. That's one thing. But more than that, I don't know. Okay. a couple closing the loop pieces Pete more said expanse season complete. You'll love it. So I just wanted to note to our listeners who are interested if, if you've been waiting before you jump on the final season of expanse, I have been waiting.
Steve Gibson (01:16:27):
So Peter, thank you for that. I wanted to let everybody know Chris miles or Miley. He said, Steve, have you guys seen the huge QAP vulnerability that has ended up with hundreds of thousands of units infected with ransomware code? Even a unit of mine with strong passwords was hit. Thankfully one way version backups meant nothing was lost. So, and I'll just, I wanted to take this opportunity. Thank you, Chris, for the heads up. I keep trying to get to it in the show, but there's been so much else to talk about. You know, we've said before there is available non QAP, open source software that looks like it does a much better job. QAP just perennially seems unable to get their act together here. They've had one serious remote code execution problem after another. So at some point, just, you know, go find the, I don't remember if it's free BSD based or open BSD or what it is, but it's one of them that you can run on the QAP system in order to do network attached storage features and just get away from QAPs solution hardware.
Steve Gibson (01:17:47):
Yes. Software pair, not okay. Two listeners via DM. So I didn't put their name in since DM is inherently private and I wasn't sure they wanted me to disclose who they were. First one said, hi, Steve. I was intrigued by your mention of refilling soda stream bottles. In last week's SN 8 53. I use soda stream a lot to replace buying soda. He says Pern called sparkling water here in the Oso, pretentious UK. He said in plastic bottles, but the refills meaning of soda stream are expensive. Do you refill from brewing gas bottle or some other source and listener two? Hi, Steve, would you be so kind as to share the link to the soda stream, refill adapter you're using? I would very much appreciate it. And of course I will keep this confidential. I apparently will not. <Laugh> although I did keep his name confidential.
Steve Gibson (01:18:51):
So anyway for those who don't know this all this interest was stirred up by Leo. And me talking about the fact that I have been for years refilling my empty soda stream, you know, steel CO2 canisters for a while I was taking them to my local. What is it? ACE hardware was a, a provider. You know, they talk about how easy it is to swap the canisters. Well, you take your empties back and it may be easy, but it sure ain't inexpensive. And after a while, I don't know how it occurred to me, but I thought, you know, I wonder if there's a way to refill these. So a little bit of Googling. Sure enough. There is a common source of food grade CO2. You wanna make sure you get like, you know, food grade, everything and that's people who do home brewing.
Steve Gibson (01:19:59):
It turns out about a mile from me is a nice little home brewing retailer on Bristol avenue in Costa Mesa. And I guess it's more than a mile, but still it's convenient. And home brewing people use CO2. And so on Amazon, I purchased first a 20 pound C two canister with a siphon that's important. The siphon is a key unless you wanna have your big canister upside down the, the siphon just, it's just a little a little tube that runs down to the bottom of the tank so that it's pulling liquid CO2 from the bottom out the spigot, as opposed to taking the, the gas off the top. So you get that that's $150 if you're interested. And then a refill adapter is nothing but a cleverly simple threaded it's it's female threads on both sides. So you screw one end, it's got the proper threads for the, the standard CO2 connection. And then on the, on the side, that's facing outward is the threading that matches the universal soda stream bottles. And so basically all this does is it just makes an a now empty soda stream bottle to the, to the liquid CO2 filled big 20 pound you know, re re refillable at your local source of CO2 bottle. Now
Leo Laporte (01:21:51):
I would just caution people cause I, you know, I did this, bought all this but and I'm still looking, but Russell, who is a home brewer says he has used to be, he could bring his bottles in and they would fill it. Now they exchange him at the places he's gone or they with for some crap tended up bottle, or they require this whole testing process before they'll do it. The, they say, leave it here and you can come back tomorrow. That kind of thing. So I would check before you jump whole hog into this, to make sure you do have a good source of CO2 that you can been used to refill it, you know, call around very good. Cause apparently, you know, and I'm not surprised these guys they're kind of maybe cuz of COVID, they're tired of dealing with people. I don't know. It's getting maybe a little harder to get this, these filled.
Steve Gibson (01:22:43):
That's interesting. I I've I've
Leo Laporte (01:22:45):
You're lucky you got somebody who can do it.
Steve Gibson (01:22:47):
Yeah. I, I, and they're, they're nice people and are, you know, bring
Leo Laporte (01:22:51):
'Em candy, see me and be yeah, exactly. They like you now. So they trust you. Yeah.
Steve Gibson (01:22:55):
So I, I thought I would share a, a, a couple pointers and then we'll, won't talk about this again. <Laugh> first is first is you absolutely want your, your soda stream empty canister frozen. That is what we do is we have a, like a spare freezer and so it's got our empties in there. So you want to refill them when they're cold, that minimizes the re-pas of a, a liquid CO2 and you get a much, you get a much fuller bottle. The second is that the, that the, the top of the, of the soda stream, basically, it's got a little push valve that when, when, when you, when you push the soda stream down a, a pin pushes down in the center, in order to release the, the, the compressed CO2, they
Leo Laporte (01:23:50):
Charge so much money for what is essentially a mechanical lever, a plastic thing with a mechanical lever, cuz all it's doing is pushing that that's button and it goes in the spout and it goes in your
Steve Gibson (01:24:02):
Soda pop that, that that's right. How the, the, the, the one got you here is that if that is, if that is pushed too far in, it stops again. So, so the trick of refilling these is to bleed it in. If, if, if you hook everything up and just open the main valve, nothing happens. You'll hear like, eh, and then it's like stopped. So, so what, what I've learned is first of all, cool, the receiving canister and then, and then just ever so slightly twist the, no, the, the valve open and you'll hear, you know, you'll hear the, of gas or fluid flowing. That's all you need to do, walk away. As I mentioned jokingly, but actually sincerely last week, don't stand directly in front of it. That's just especially, I mean, every at crotch height, it is at crotch height, but it could
Leo Laporte (01:25:02):
Impede your propagating. So don't do that.
Steve Gibson (01:25:06):
I would live it even practicing. Yeah. Yes. So and, and it takes, you know, a couple minutes and if it slows down, then, then you, you can, you know, creep the valve open again and, you know, restart the little, the little E sound. But boy, it's just so gratifying when, when you're unable to put more in you turn off the main valve, remove the cylinder, it is heavy, cuz it is now filled with liquid CO2 and then you're good to go for a whole long. And I think I paid, I think I paid $14 to have this 20 pound big, big, you know, floor standing, canister, refilled which, you know, beats the hell out of, you know, going and buying. Oh yeah. New, new canisters from, I mean, and cuz we love soda stream. We AB we
Leo Laporte (01:25:56):
Use any, the idea is to save money in the long run anyway. So yeah. And eliminate single use
Steve Gibson (01:26:03):
Plastic bottles. Yes. That's why we've got it. Yeah. okay. So Sunday evening night before last, after a weekend spent scratching my head and experiment what experimenting with an older motherboard, which I had purchased through eBay in order to duplicate what at least one of our testers had seen. I figured out what was going on an adjusted, spin rights, core technology to accommodate it. And any other similar systems the trouble I had been having was occurring due, due to Intel's 82, 3 71 PCI to ISA slash IDE accelerator as they call it. It's known as the P I I X four. And the chips spec is dated April of 1997. So yeah getting this version 6.1 release of spin, right to run everywhere is turn turning out to be far more work. And I'm not surprised since the whole point of 6.1 is to bypass the bios and talk directly to the hardware.
Steve Gibson (01:27:11):
The bios may not have been, you know, terrific for performance. It did not have performance on its side, but it does have compatibility. I knew that this was likely to be where a lot of time was gonna be spent. Fortunately, we have a really amazing group of development testers. The instance of GitLab that I brought up in mid-December currently has 241 registered participants. So, you know, by far, most of them watch and silently test the code as it evolves, if it does something wrong, then I'll hear about it. But it's very gratifying to know that spin writer is receiving this level of pounding at this stage yesterday or day before yesterday, rather in that end of, you know, end of the weekends work update, I posted to the news groups. I said, I think Inc that with the super micro, the Asus E E E PC 9 0 1 and now mill cues, 82, 3 71 chip issues all resolved.
Steve Gibson (01:28:18):
That's the last of the big mystery behavior problems. This just leaves me with a bunch of less interest ding and already understood things to fix and clean up once those are finished, I think we'll be ready to thoroughly pound on what we have to see, whether anything else falls off. It feels like we're getting close to having this operational foundation fully functional. So the, that will be a major milestone. We will get to a point where the code I have is identifying every drive that everybody has connected using every controller on every system they have correctly and running benchmarks on those to demonstrate that it, you know, it is able to talk to the drive. And part of that is a, a read write test, which I perform way out at the far end of the drive. And at that point it's just time to basically finish spin, write that is all of this hardware, compatibility layer will be resolved. And I get to move forward you know, update the screens for, to hold larger numbers and, and that kind of thing. And so it'll be a nice milestone to get to. And you know, we're probably within a week or two of that, so yay.
Leo Laporte (01:29:42):
And Leo time to break is that
Steve Gibson (01:29:44):
Final break. And then we're going to look at the anatomy of a log for J exploit. Awesome. What did, what did those evil in this case, cuz they're hackers and attackers, Iranians do
Leo Laporte (01:29:58):
Evil doers, evil doers, evil doers. I, I wanna talk about collide because I think this is a really good idea for endpoint management. Now you maybe are aware of Apple's MDM solution, which locks down employees devices, their smartphones, things like that without considering their needs or even attempt to educate them about the security of their laptop. MDM is widely used mobile device management collides, a better way, a much better way, a collaborative way, a way your, your employees will like or your customers or your or your clients will like a way you'll like too because collide K O L I D E is built by like-minded security practitioners who have seen in the past just how much MDM was disrupting end users, frustrating. 'em So badly, they throw up their hands, forget, you know, all right, I'm take, I'm using my own laptop, right?
Leo Laporte (01:31:01):
I'm not using this, this isn't ridiculous. I hear story a lot without telling anyone. And of course opening you up to all sorts of problems in that scenario, in which everybody loses the user and you and your business and everything collide is different instead of locking down a device. I really like this. I really like this collide takes a user focused approach that communicates security recommendations to your employees directly on slack. So after clients set up, in fact, I I'm sure Russell wants to use this cause we use slack device security turns from this, you know, on or off police state, basically into a dynamic conversation. The conversation starts with the users installing the endpoint agent on their own. So they're already kind of empowered, right? We're, you know, we don't deliver this to you locks down. We say here, install, collide through a guided process that happens right inside their first slack message from there collide regularly, sends employees recommendations, suggestions, if you will, when it notices their devices in an insecure state ranging from, you know, simple things like your screen lock is not set up correctly, or it doesn't come on or there's no password to turn it off.
Leo Laporte (01:32:14):
That kind of thing to somewhat more nuanced, maybe even difficult able to solve issues like, you know, suggesting people secure two factor backup codes sitting in their download folder. <Laugh>, you know, that's probably not a, it can't see post-it notes on the screen, but that's the next worst thing. And because it's talking directly to employees, collide is educating them about the company's policies and how to best keep their device is secure. Using real examples, right. You know, from this is what's actually happening. Not some theory, plus they feel listened to and engaged. And honestly, they're more likely to become a partner in security rather than fighting at every step of the way, collide Linux, Mac, or windows us platform endpoint management. It puts end users first, but make sure your security's taken care of. And it's of course, for teams to slack get endpoint management that puts a user first collide, K O L ide.com/twi to learn more.
Leo Laporte (01:33:15):
You can activate a 14 day free trial today. No credit card needed. So I like that when they do that, that really, you know, that makes me feel better. K O L I D E collide.com/twi. If you're looking to a better alternative to MDM that doesn't make users feel like children locks down, doesn't, doesn't encourage them to try to go around your MDM. This is a really good, silly ocean. And I think it works really well. Collide. K O L I D e.com/twi. I think you'll be impressed. Give it a try. Anyway. collide.com/twi. Now I see the soda stream bottle.
Steve Gibson (01:33:58):
That was my soda stream bottle I was drinking from. Yep.
Leo Laporte (01:34:01):
I see. See Steve soda stream. And of course he has the world's largest soda stream bottle, just like everything
Steve Gibson (01:34:07):
Else. <Laugh> okay. So many security firms are tracking threat actors who immediately and predictably jumped aboard the log for Jay bandwagon. You know, it's been a, it's been a feeding frenzy for the security firms to help bring this home and make it a bit more real. I wanted to share a piece of checkpoint research's reverse engineering work on a typical threat. The internet is now facing. I've got for anyone who wants more detail as always a link in the show notes last week checkpoint documented the efforts of an, of an Iranian government backed group known again, not just Iranians Iranian government backed group known as a P T 35, also known as charming kitten TA 4 53 and phosphorus. This group started widespread scanning and attempts to leverage the log for J flaw in publicly facing systems. Four days after the vulnerability was disclosed.
Steve Gibson (01:35:20):
And you know, all the bad guys knew now that this was public. It was, you know, it was gonna get remediated at some speed. The point being let's be first, you know, get in there before that gets before the, the, the back doors get closed. I since this actors, this particular actor's set up was hurried. They simply grabbed one of the publicly available open source GitHub hosted J N D I exploit kits. Yes, they were on GitHub initially, but that kit has been removed from GitHub due to its enormous popularity, following the vulnerability emergence you know, why bother reinventing that particular wheel when time is of the essence, they also based their operations upon their preexisting infrastructure rather than like creating a whole new one. And that infrastructure was already well known to checkpoint thus making its detection and attribution all the easier.
Steve Gibson (01:36:23):
And the show notes. I have a flow chart, which shows the path that the exploit takes and it could hardly be any easier or direct first the attackers send a crafted request to the victims publicly facing internet exposed resource, whatever it is a server of some sort in this particular case, the weaponized payload was sent in through either the user agent or the HTTP authorization headers. Remember that all that needs to happen is that something somewhere that's Java based logs, part of the query that contains this weaponized string in order to log the query log for J examines, what its logging sees a J N D I component and goes about its job of obtaining the content from the L D a URL contained in the query, which is being logged. So the vulnerable machine as, as has been instructed to do, basically, although not after it's been patched, but until then reaches out to a, what they labeled in their diagram, a log for a exploitation server, which assembles the Anne returns, a malicious Java class, which will be executed on the vulnerable machine.
Steve Gibson (01:37:51):
The class runs a power shell command with a base 64 encoded payload. And I actually have a picture of the actual payload the exploit dot command power shell, and then the encoded payload that power shell command downloads a power sh module from an Amazon S3 bucket URL. And it actually is HTP colon slash slash S3, Amazon, aws.com/library sales slash test dot text and executes it. And we have a picture of that in the show notes, the actual thing that's downloaded, the downloaded power shell payload is the main module. That's then responsible for basic communication with the command and control server and the execution of additional modules which may be received. So the main module performs the following operations. It validates the network connection upon execution, the script waits for an active internet connection by, by repetitively making HTTP post requests to google.com with the parameter high high hi equals hi, just to see if it can succeed.
Steve Gibson (01:39:20):
That's how it detects whether or not it's got an internet connection, assuming that it does then it knows that it also performs basic system enumeration. It collects the windows OS version, the computer's name and the contents of a file. I me text in app data in the app data path. The file is presumably created and filled by different modules that will be downloaded by the main module. It then retrieves the command and co control servers domain, the malware decodes, the command and control domain retrieved from a hard coded URL located in the same S3 bucket from where that back door was downloaded. So the, the, the bad guys have dynamic control over that by deciding what goes in this AWS bucket. It also retrieves decrypts and executes follow up modules. Okay. So once all the data is gathered, the malware starts communication with the command and control server at the domain, which it determined by pulling that from the Amazon AWS cloud bucket.
Steve Gibson (01:40:40):
And it does that. It com communicates with the commander control server by periodically sending HT DP post requests. I mean, none of this is high tech. None of this is rocket science. You know, this is easy to do, which is why this is terrified everybody so much. So this thing send HT DP post requests to a preconfigured URL with each post request containing information from which to build a session key, the OS version, the computer's name and the contents of that file in the app data direct. So that ends up being something unique, which it uses to identify itself each time. And I think as I recall, it puts it in a session header in the post query in response to the command and control servers receiving these, these post requests. It can either ch choose not to respond in which case the script will keep sending post requests periodically to continue to provide the server with a stream of response opportunities, or the server will return a base 64 encoded string.
Steve Gibson (01:41:51):
Now, just as a reminder, base, 6 64 is a means for sending binary data over an ask E channel that is over a text only channel groups of three, eight bit binary bites. So three, eight bit binary bites is 24 bits. They're regrouped from three eight bit bites to four, six bit bites. Six bits can have 64 combinations so that, so we take the lower and the upper alphabet gives us two times 26 characters or 52 characters. We add the 10 decimal digits that brings us up to 62 characters. And then we toss in two additional ones, the plus, and the forward slash which brings us to 64. So, so in groups of three, binary is taken from the source binary. Those, those 24 bits are regrouped into four characters. Each can each of each one of 64 different possibilities that's then all munched back together and sent down with a client which reverses the encoding process to restore or the original binary.
Steve Gibson (01:43:17):
This allows the malicious server to squirt anything it wants into the victim machine. That's making the queries, the malicious, the modules downloaded in this fashion are either power shell or C sharp scripts. The modules by the command and control server are executed by the main module with each one, reporting data back to the server separately so that the original module comes in, looks around, sets up, shop figures out who to talk to initiates the dialogue. And does that periodically, if in response to one of its of its multiple post queries, it receives a blob of basics, 64, it goes, oh, okay. Something to do it, decodes it back into whatever it was before, you know, moves the base 64 ENCO. We know that that's gonna be a power shell or a C sharp script and runs it at that point, that subsidiary module takes off on its own, and it establishes its own communication directly with the command and control server.
Steve Gibson (01:44:31):
The command and control cycle continues indefinitely, which allows the threat actors to gather data on the infected machine, run arbitrary commands and possibly escalate their actions by performing a lateral movement or executing follow up malware, such as ransomware. In other words, you know, this thing can do anything it wants to, once it gains a a foothold. So the modules, every module is auto generated by the attackers based on the data sent by the main module, each of the modules contains a hardcoded machine name and a hardcoded C and C domain. Every module checkpoint observed contained a block of shared code, which makes sense, cuz there's a bunch of stuff that they're all gonna do regardless of their specific function. And that is encrypting the data to be sent exfiltrating the gathered data through a post request or uploading it to an FTP server that also happens and sending execution logs to a remote server.
Steve Gibson (01:45:41):
In addition to this, each module performs one specific job that is in addition to those things they all have in common checkpoint, retrieve and analyzed modules for six different functions list, sting installed applications that is applications installed on the machine, taking screenshots, listing the running processes, getting OS and computer information, executing a pre-defined command from the command and control server. And then finally cleaning up any races created by any of the other modules. The applications module uses two me two methods to Fe and return a list of installed modules. It can either enumerate the uninstalled registry values or use the management the windows manage an instrumentation command in order to get an enumeration. It gets those it encrypts them and sends them back to, to headquarters the screenshot module. They found both C sharp and power shell scripts for the screenshot.
Steve Gibson (01:46:53):
They both have the capability to capture multiple screenshots at specified intervals and upload the resulting screenshots to an FTP server whose credentials are provided by the script. The C sharp script uses a base 64 coded power shell command to take the screenshot from multiple screens. So again, you might have this thing in your computer, not know it, you're doing things. And this thing is spying on you sending shots of your screens back to headquarters, the processes, module obtains, a list of the machines running process using the task list, command gathers them and codes them sends them back. The system information module contains a bunch of power shell commands. What was interesting was that in the instances that checkpoint saw the bad guys had commented out all of these potential sources of information they just weren't using it. This told checkpoint that this whole campaign was hastily assembled since the entire you know, as we know, attacker community was well aware that systems would be closing their doors very quickly.
Steve Gibson (01:48:10):
So there were, there was like all these different suggestions of, you know, the moment this thing be went public, the attackers jumped on it and said, let's quickly get something together that we can exploit this with. And finally we have the command execution module, which is able to essentially download and execute any actions, any commands that are provided by the command and control server. They saw, for example, listing the contents of the C drive route listing the specific wifi profile details using net SSH the WLAN sub command of that and also listing all the drives using get PS drive a, a power shell enumerator, and finally the cleanup module it's dropped after the attackers have finished their activity and wanna remove any traces that they've been inside the system. The module contains cleanup methods for persistence related artifacts in the registry and the startup folder you know, any files created and any running processes.
Steve Gibson (01:49:24):
It contains five hard coded levels of sort of like stages of cleanup, depending upon the stage of the attack. Each one, serving a different purpose checkpoint said that the design and the intent of the cleanup module made it clear that the threat actors wanna keep the infection on the machine, first of all, for as long as they deem necessary. But then after once their goal has been achieved, they wanna disappear without a trace so that, you know, no one believes that there that an attack occurred as for attribution, of course, we know attribution of network remote attacks off of and falls somewhere between difficult to impossible, but not. So in this case, most advanced, persistent threat actors put some effort into making sure to change their tools and their infrastructure to avoid being detected in the first place and to make attribution much more di difficult if they were detected.
Steve Gibson (01:50:28):
And in fact you know, we know that the, the solar winds attacks were famous for like really working to obscure the path by which the infection happened. If it were to be discovered, however, a PT 35 does not conform to this behavior. Apparently the group is famous within the, the cyber security community for the number of operational security mistakes they've made in previous operations. And they tend not to put too much effort into changing their infrastructure once it's been exposed. So it's little wonder that their operation as checkpoint has detailed. It has significant overlaps in the code and the infrastructure which previously identified the activities of a P T 35 as for code overlaps four months ago in October of 2021 Google's tag team, remember their threat and analysis group published an article about a P T 35 S mobile malware, you know, because Google and Android, even though the samples checkpoint analyzed were power shell scripts, the similar meaning, you know, power shell as opposed to Android.
Steve Gibson (01:51:48):
So windows only the similarity of coding style between them and the Android spyware that Google attributed to a P T 35 immediately caught checkpoints attention. For one thing, the implementation of the logging functions was identical, but to between the Android app, which Google analyzed and this present campaign's power shell modules, which use the identical logging format, even though the commands are commented out and replaced with another format, the fact that these lines were not removed outright, checkpoint felt might indicate that the change was done only recently. And the syntax of the logging messages themselves being logged is identical as for infrastructure both then and now campaigns, October, and now apparently used the same server side infrastructure. When a client posts data to a remote HTTP server, the server side path of the query is called the API endpoint. Google's mobile analysis and checkpoints both revealed the use of the common endpoint slash API slash session now, okay, that's not a high entropy name could have just been a collision of, of, you know, convenience but checkpoint felt encouraged by the observed overlap.
Steve Gibson (01:53:28):
And they stated in their report that other API endpoints are similar, but not entirely identical due to the differences in the functionality of the platform. So didn't make sense for them to be completely identical checkpoint also observed that out. Not only are the URLs familiar, but the command and controlled domain of the power shell variant responds to the API requests that are used in the mobile variant, huh? This suggests similar if not identical server side support for both campaigns. So checkpoint concluded its re port by observing that every time there's a new published critical vulnerability, the entire InfoSec community holds its collective breath until its worst fears come true scenarios of real world exploitation appear, especially by state sponsored actors, as they demonstrated in their report, the breath holding weight in the case of the log for J vulnerability was only a few days. The combination of its simplicity, its publicly available, open source code samples and the massively tantalizing number of vulnerable devices made this a very active vulnerability for actors, such as a PT 35. And I have no doubt that you know, while I don't think I will continue giving this in depth coverage because we know pretty much everything there is to know about it. Well, if something major happens it'll certainly be newsworthy, but that's how this stuff works again. Just it's frightening. How, how non Rockett science, how, how script kitty level. Yeah. This thing is, and that it can get up to so much mischief.
Leo Laporte (01:55:22):
It's amazing. Even a even a, what is it, a kitty, what kind of kitty charming kid, even charming kitten can do it, who comes up? Is that like a V who comes up with, I mean there's fancy bear for the Russian group, charming kitten for the Iranian group somebody's coming up with these must be the, yeah, I dunno. Must be the CIA or the NSA. That's just wild. Steve, you did it again. Here we are at the end of another fabulous episode. If you would like to know more, Steve has the show notes at his website. It's not all it's, there is a lot of stuff@grc.com, including that shields up test where you can test your port 20 2009. What was it? Some please do 20,005, 20,005. And so it's grc.se/are episode number 8 54. Okay. actually I, every time I, I set up a new router or a new network, I use shields up to check, make sure it's properly configured.
Leo Laporte (01:56:27):
It's a very useful tool. One of many things Steve gives away the only thing he doesn't that's his ver bread and butter spin, right? His very, very popular mass storage, maintenance and recovery utility. If you don't have a copy, you really ought to have one. If you gets 6.0 the current version right now, you get a free upgrade at six one it's imminent. You can help in the development of it as well. There's a forum there, all of that@grc.com 16 kilobit versions of this show audio as well as 64 kilo audio versions of the show are there the transcripts, which are very handy if you like to read while you listen or just to search through, to find a particular part of any given show, all@grc.com and lots of other stuff as well. We have 64 kilo audio versions and full video as well.
Leo Laporte (01:57:15):
If you wanna watch available to our site, twi.tv/sn there's a YouTube channel, dedicated security. Now all the videos all the time, you can also subscribe in your favorite podcast player, cuz it is a podcast and download it automatically or even go to the website, TV slash SN and download it from there. If you subscribe in a podcast player, you get it automatically, which is probably a good idea. Cause this is one of those shows where I think you want all the episodes, right? You know, you can go back at the website to of episode one and come forward from there. The feeds only have the last 10 episodes for reasons of economy, but that'll get you started anyway. So look for, look for security now on your favorite podcast player, if you wanna watch us do the show live we stream live@livedottwi.tv 24 7. This show is every Tuesday, one 30 Pacific four 30 Eastern 2130 UTC. You can watch live listen, live chat, live@ircdot.tv or in the club tweet discord server which always a lot of fun to be in there. And I think that pretty much covers it all. We'll be back next Tuesday with another thrilling gripping edition of where the hackers are. <Laugh> ah, right. Oh, thanks Steve. We'll see you next time. Thanks buddy.
Mikah Sargent (01:58:35):
Hey, you don't have to wait till the weekend to get the tech news. You need join Jason Howell and myself, Mikah Sargent for Tech News Weekly, where we talk to and about the people making and breaking the tech now.