Security Now 979 transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show
0:00:00 - Leo Laporte
It's time for security now. Steve Gibson is here. You're going to get to watch us try out some new technology. If you're watching the video, we're using Restream to produce this show today, which gives us some interesting new features. Steve's going to talk about Patch Tuesday. Holy cow, microsoft patched one of the worst flaws I've ever heard. It gives Microsoft and all of us reason to think. Maybe recall should be recalled. In fact, that's exactly what happened. Do you use Wget? Maybe you shouldn't. And then, finally, steve's going to talk about how that kind of DNS poisoning that he talked about last week at codemicrosoftcom, how that happens and how you need to configure your DNS to prevent this. I'm talking to corporate IT folks. It's all coming up. Next on Security. Now Stay here. Podcasts you love.
0:00:54 - Steve Gibson
From people you trust.
0:00:56 - Leo Laporte
This is Twit. This is Security Now, episode 979, recorded June 18th 2024. The angle of the dangle it's time for Security Now, the show where we cover the latest news in security, privacy, security, healthiness and sci-fi, with that guy falling over because I'm going on so long with his intro. It's Steve Gibson of GRCcom.
0:01:28 - Steve Gibson
Hi Steve, hello Leo, I hope I sound the same to everyone, as good as I have for the last 20 years. We're on new technology today. Yes, we are.
0:01:36 - Leo Laporte
We're testing out something called Restream the sound. If you're an audio listener which 90% of you are should not be any different.
0:01:45 - Steve Gibson
You sound just the same to me, except your headphones are distracting because the cord's coming off of the wrong side.
0:01:51 - Leo Laporte
Well, it'd help if I do this.
0:01:54 - Steve Gibson
Oh, that's much better, now I recognize you.
0:01:57 - Leo Laporte
There's Leo.
0:01:59 - Steve Gibson
Who is this guy with no headphones?
0:02:00 - Leo Laporte
I recognize your voice, okay, actually, for years, people have told me that I'm wearing my head where it's headphones backwards, because this is supposed to be the left ear. So I was actually doing it. Oh no, I'm strangling myself. I was actually doing it. This is correct. Let's go back, um, anyway, to explain what's going on.
If you're watching video, it does look a little bit, and that's because we're using a new program called Restream, and this is so that we can, sad to say, but sad necessity, close the studio in a month or so and move to a local recording from my house, and this is how we're going to do it. We won't be able to bring the TriCaster and all the beautiful telus, axia hardware and that we use for audio, uh, but restream is a really great solution that allows us to, um, pretty much do the same thing that we've always done. Uh, we have benito's here. He's our, our td remotely, uh, and so he's at his house. He can is, everybody can work from home, yeah, cool, and the, and so he's. He's going to watch the show. Kevin king's probably going to do it too. It depends who ends up producing it, but the producer of the show will watch the show. Can, can switch, but I said no, I want the capability to do things like this and this. Oh, it's fun. Steve was flipping himself back and forwards like this earlier. So in a way, this is kind of a cool platform because it gives me some interesting capabilities, one of which I really think we're going to enjoy, which is I can pull up from chat people talking. So if you're in the chat room, like emmanuel is, uh, you can chat with us. Now we can see from the little icon that he's watching on youtube.
The other thing that happens with this is we're able to stream on to twitch, youtube and other platforms as well. Did we lose discord? We don't stream video into discord, but you know what? Video on discord was always kind of bad. It was, so I would keep losing the audio when I was trying to watch. Yeah, it's not good. So we're going to push people and and we can actually do x, instagram and other platforms as well. So eventually this will give us a capability to to be in more places, and you know that that emmanuel's post was a chat, was from the youtube chat. So chatters from everywhere everywhere watching on any stream will will actually be able to converse with us and if there are good comments, instead of me reading them, I can. I can pull them up. So that's pretty nice.
So the the the discord chat is still there and the video. That's Patrick, our engineer. The video is not. It was meh. As Patrick said, I think this is going to be once my fingers become trained. It's a lot of stuff to learn for me, but I think there's a lot of benefit to this. One big dysfunctional family. As DC or d crash says, everybody's included lou. So this is going to be fun now steve. Yes, the real question is what's coming up on the show today?
0:05:20 - Steve Gibson
so, um, we've got a bunch of interesting things to talk about. We're going to learn why updating your Windows laptop with last week's patches is potentially more important than it has been for a long time. Also, today's June 18th, copilot Plus's recall feature will not be released today. Nope, what happened? Victory Was recall recalled, I think, so I can't recall.
Also, what does John Hopkins, well-known cryptographer, think about Apple's new private cloud compute concept? How could the WGET command line utility possibly have a CVSS vulnerability rating of 10.0, which we know is reserved for end-of-the-world events, or does it? What order did Google, cloudflare and Cisco recently receive from a Parisian court? And, after a brief GRC email update and three pieces of closing the loop feedback from our listeners, we're going to examine exactly how Microsoft lost control of their codemicrosoftcom subdomain and why the underlying problem is far bigger than them. And why the underlying problem is far bigger than them. Thus today's podcast title the Angle of the Dangle. Now number 979. Closing in on that magic 999. Will we be able to go to four digits? That's the question. What will break? It's our own Y2K. We'll find out. Is 999 going to break? Doing this in 20 years? We're never going to. You know, maybe we're going to run out of steam after the 15th podcast, but here we're going Well we're going to have to face it.
0:07:39 - Leo Laporte
But you know what? I think there's probably more than a few people who say whatever it takes in 21 episodes.
0:07:49 - Steve Gibson
We're glad that there's going to be an episode 1000. Yes, and I will spend some time to figure out actually the the. The problem was that I was redirecting clicks at grccom through pod track in order to give twit credit for, but you don't have to do that anymore. We don't do that anymore well, so then there's no good, I'm gonna be any problem, I'll just pull the. I'll just pull the plug on the pod track. Quit, quit.
0:08:12 - Leo Laporte
Redirector code and we're good to go okay, yeah, all right, we're gonna pause, uh, and leo's gonna push a bunch of buttons, including shift nancy, which apparently I'm still here after that then then we'll have a podcast.
Shift nancy did the job and now I'm going to click this link and welcome nora. That was nora shift. Nora will also work. Yes, uh, it removes our, uh, our, um, uh, lower third names. Yeah, so we don't, so they don't know who we are. But it replaces replaces it with our fine sponsor, bitwarden, the password manager, offering a cost-effective solution that can dramatically increase your chances of staying safe online.
Both Steve and I have switched to Bitwarden we did more than a year ago now and I couldn't be happier and Bitwarden, because it's open source, really keeps up with the times. We told the story of how one of our listeners, quexon, actually did a pull request to the Bitwarden code, wrote an Argon2 implementation, and now Bitwarden has added Argon2 in addition to PBKDF2 for your password hashing. It's a much better way of doing it. It's memory hard. I switched immediately. That's the benefit of being an open source project. They're always kind of keeping ahead of the game. In fact, they supported PassKeys from day one. Now they just announced they're supporting PassKeys not only in the desktop, but on the browser extension and the mobile devices too, which is really the only way, in my opinion, to use PassKeys. Instead of being tied to your phone or specific device, passkeys is now tied to your Bitwarden account, which means you take it with you wherever you go. Passkeys are available on mobile on iOS right now. It's an open beta on Android and, of course, that's the beauty of open source. It will develop and it'll be out, I'm sure, officially soon, but you can get into the open beta right now. We'll tell you more about this.
As it happens, bill Wharton did a survey. This is really an eye-opener. They did an enterprise survey 2,400 individuals from US, uk, australia, france, germany and Japan asking about their password practices, and it was really kind of a shocker. 31% of US respondents admitted they reuse passwords across sites. You're, as a Security Now listener. You know why that's a terrible idea, one of the most common security problems. 42% incorporate personal information birth date, mother's maiden name, dog's name into the password. Again, that really reduces strength and security. 58% of respondents admitted they store their passwords up here. They're using their memory, which also probably means they're putting post-it notes on the side of their monitor with your company's login written on it, because no one's got enough memory to remember all those passwords. 34% say yeah, we use pen and paper for password manager at work. We put it on those post-it notes.
A quarter of respondents knew that their workplace security habits were iffy. 45% were storing passwords insecurely. 44% were using weak credentials. They knew it. So if you're an enterprise and your employees are saying, yeah, we're not doing the right thing, you need to give them a better way. You need to give them Bitwarden.
Bitwarden is free, always, forever for individuals, but they also have great team and enterprise plans, all of which start with the basic Bitwarden individual account and then you add your organization's vault. It's a very elegant solution. It means you can also not only store passwords, but all your secrets securely, including things like API keys, s3 keys, things like that the secrets that you don't want to accidentally post on GitHub. With a transparent, open source approach to password management, bitwarden makes it easy for users to extend robust security practices to all of their online experiences. Get started right now with Bitwarden's. Free for individuals, across all devices. Unlimited passwords, hardware support, passkey support. It's open source, free, forever. Get started right now with Bitwarden. They have a free trial of the Teams or Enterprise plan when you go to bitwardencom slash twit. It's great for teams, it's great for businesses, it's great for individuals. It's the only one I use Bitwardencom slash twit. We thank him so much for supporting security now and our fine Steve Gibson and his continuing quest to make us all safer online. It's all yours, steve.
0:12:38 - Steve Gibson
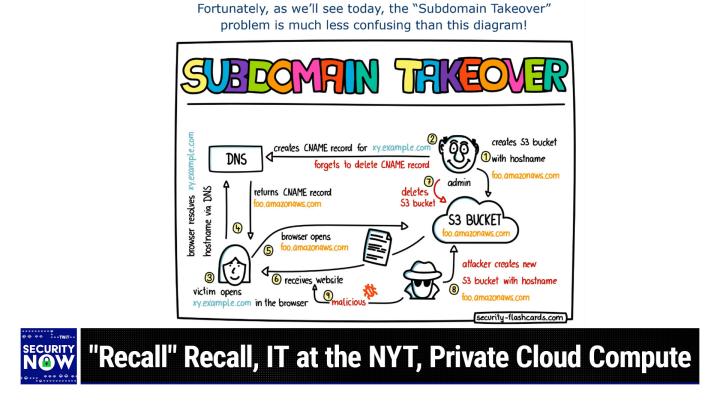
So to that end, we actually do have, we're going to end up with some interesting takeaway. Our picture of the week is sort of a placeholder. You know, it's not one of our crazy fences out in the middle of nowhere with a bunch of sheep standing behind the fence not willing to go around for some reason. That one was a real puzzler. This is a diagram that demonstrates the process of CNname dns record based subdomain takeover oh, I gave this.
well, yes, yeah, and it's got lots of pretty. It looks like something you would get in. You know you'd use your box of crayola crayons to color in. I gave it the the title. Fortunately, as we'll see today, the subdomain takeover problem is much less confusing than this diagram, because, I mean, I understood the problem immediately when I realized that's what had happened at Microsoft, I think maybe Leo. Every one of our listeners said I know what happened, I'm going to tell Steve. So, boy, does the email system work. But anyway, I had to sort of figure out the diagram after already knowing what the problem was. So, just for what it's worth to anybody who's like it's lost in these arrows, don't worry, by the end of the podcast you'll understand what's going on. Good, because it's not obvious.
No, it's not. The diagram does not help much. I need to begin this week by making 100% certain that everyone listening is aware of a flaw that was patched during last Tuesday's Windows Patch Fest. It's CVE-2024-30078. And the only reason that it only has a CVSS score of 8.8 rather than 11 on a scale that maxes out at 10 is that an attacker needs to be within Wi-Fi radio range of any Windows machine Any Windows machine with Wi-Fi enabled that has not been updated with last Tuesday's patches. That's terrible. It's unbelievably bad.
0:15:05 - Leo Laporte
Because one network might have multiple Windows machines and one that's close. It's it's unbelievably bad because one network might have multiple windows machines and one that's close to the window.
0:15:10 - Steve Gibson
Yes, being right. You know that it's windows, yeah, and yeah, uh, or somebody has a laptop and you know, for whatever reason, they've learned, for example, that well, you may not want to apply those patches immediately. Let them kind of sit for a while to see if Microsoft made a mistake and apply them later. Okay, in this case we have the worst of all possible problems. Last Tuesday eliminated a fortunately very rare remote wireless radio takeover of any Windows machine which is using its native Wi-Fi protocol stack. This affects all versions of Windows, ever. So that means that any machine that was not updated, as I said, for whatever reason, last Tuesday is vulnerable. Today Microsoft is only saying quote all supported versions of Windows. But that's what they always say, and that typically means all earlier versions too. But they don't want to say that because they've decided they don't want to support those anymore. So good luck to you. And the fact that this appears to be Windows-wide suggests that the flaw was in a core component that they have not been messing with for the last 15 years, because, as we know, mostly Windows is just new layers of candy coating on top of the core which they're afraid to touch, which, thank God, you know, leave some of it alone at least. So to provide some additional color and perspective, I'll share what Forbes cybersecurity guy wrote under their headline new Wi-Fi takeover attack. All Windows users warned to update now.
The guy wrote Microsoft has confirmed a new and quite alarming Wi-Fi vulnerability in Windows which has been rated 8.8 out of 10 in terms of severity using the common vulnerability scoring system. The vulnerability assigned as CVE-2024-30078 does not require an attacker to have physical access to the targeted computer. Exactly as you said, Leo, just be standing outside the building, although physical proximity meaning you cannot do it from Russia. In fact, that's why it's not a 10.0. If you could do it from Russia it would be a 10.0, but you got to be nearby. You know Wi-Fi range.
Exploiting this vulnerability, he writes, can allow an unauthenticated attacker to gain remote code execution on the impacted device. What's perhaps most concerning, though, is that this Wi-Fi driver security flaw affects all supported versions of the Windows operating system. Driver security flaw affects all supported versions of the Windows operating system. Microsoft has confirmed that, with no special access conditions or extenuating circumstances apart from the proximity requirement, an attacker could quote expect repeatable success against the vulnerable component. Unquote. Microsoft also warns that an attacker requires no authentication as a user on that machine before exploiting this vulnerability, nor any access to settings or files on the victim's machine before carrying out the attack. Further, the user of the targeted device does not need to interact at all there's no link to click, no image to load, no file to execute.
Jason Kitka, chief Information Security Officer at Automox, said that, given its nature this quote vulnerability poses a significant risk in endpoint defense environments, including hotels, trade shows or anywhere else. Numerous devices connect to Wi-Fi networks. In these kinds of environments, it would be all too easy for an attacker to target users without raising any red flags. To protect against this vulnerability, it's recommended that you apply the latest patches as soon as possible, assuming, that is, you are using a version of Windows that still receives security updates. Anyone using an end-of-life version of Windows without an extended service contract is recommended to update to a supported version as soon as possible. Kitka said If patching immediately isn't feasible, you must use endpoint detection to monitor for suspicious activity related to this vulnerability. Due to its unique nature, it's unlikely to be visible to network level detection methods, meaning you know it's down in the kernel, you know deep stack, before this even gets up to the network interface level. At a higher level, he says the risk of running outdated software cannot be overstated.
The article then concludes in case you need any further incentive to get patching as soon as possible, kitka said this close access vector threat potentially bypasses network-based detections and mitigations. It circumvents most threat modeling. So this is an immediate patch priority for me. He said Most security experts agree that publicly available exploitation tools will be available before long. So the window of opportunity to patch before the attack start is getting smaller every day. And I should note that GitHub does indeed already have a vulnerability detection and command execution script posted. So that has happened. Not malicious, but you know it's easy to take that script to make. Actually they did have. They had a. It commented out where you're able to provide the command. It commented out where you're able to provide the command. So technically not malicious, but it doesn't even take a script, kitty, in order to make this do something bad.
Microsoft, in their own tracking of this CVE, enumerates the following characteristics, which are bracing. They said under attack vector, they said adjacent and they wrote the vulnerable component is bound to the network stack, but the attack is limited at the protocol level to a logically adjacent topology or IEEE 802.11, which is Wi-Fi or logical local IP subnet network, or from a secure or otherwise limited administrative domain Under attack. Complexity this is not what you want to hear. Low complexity attack, they said. Specialized access conditions or extenuating circumstances do not exist. An attacker can expect repeatable success against the vulnerable component. Wow, privileges required. This is bad, leo. This is as bad as it gets. This is a shocking flaw for Windows to have.
0:22:16 - Leo Laporte
Cbits wants to know if the firewall stops it. No.
0:22:19 - Steve Gibson
Oh my God, the firewall is at the border. And this the the the boundary that the firewall protects Unbelievable. For privileges required None. The attacker is unauthorized prior to attack and therefore does not require any access to settings or files to carry out the attack. User interaction None. The vulnerable system could be exploited without any interaction from any user.
Confidentiality they said high threat. There is total loss of confidentiality. And this is where the favorite comment I saw on the internet was but don't worry, your recall, data is encrypted. It's like uh-huh, right. So I mean, this is exactly the kind of problem that Microsoft ignores when they say oh, storing all the history of your computer? Not a problem, we've got you, we've got your back. And here's a flaw in the Wi-Fi protocol stack that probably dates back 15 years. This is you know that the, I think seven is out of extended service now, but eight is still in it and eight is vulnerable. So we're talking, this has been around for a long time and we don't know who already knows about it. We just know that it finally came to light.
And for integrity, they said high threat. There is a total loss of integrity or a total loss of protection. This is Microsoft saying this of their own flaw. For example, the attacker is able to modify any slash all files protected by the impacted component. And then they wrapped it up with two FAQ questions. They said Q question. According to the CVSS metric, the attack vector is adjacent. What does that mean for this vulnerability Answer exploiting this vulnerability requires an attacker to be within proximity of the target system to send and receive radio transmissions. And then the second question how could an attacker exploit the vulnerability? Answer an unauthenticated attacker could send a malicious networking packet to an adjacent system that is employing a Wi-Fi networking adapter which could enable remote code execution.
Case in point demonstration of why the presence of recall running in Windows machines represents the threat that it does. I have no doubt that Microsoft's heart their heart, not their brain is in the right place. They're not an evil empire, but they're now attempting to add an extremely powerful and high-risk feature to an old, creaky and bug-ridden operating system. That's the only way you can characterize Windows an old, creaky, bug-ridden operating system. Again, they keep adding and they change the UI and make the desktop look different. But we all see dialogues that we remember from Windows 95. So it's still in there. Well, okay, windows 2000. Which is that Windows is not up to the task of protecting anything as valuable as everything that our machine has ever displayed on its screen.
0:26:13 - Leo Laporte
The scenario is very simple. You've got recall running. Grandma has recall running on her home network. She's got Wi-Fi running. Some guy sits out on the curb, joins her computer. That's in the window. She doesn't even have to be on that. One can then easily get into the other computers and access the data. Yeah, I mean, it's a very it's it is why you hated the idea of recall in the beginning.
0:26:41 - Steve Gibson
Yes, yes, yes exactly you know we. It's just they don't. You know. Here microsoft has come up with a, I would argue, a killer idea the idea of of storing all of the history and then, probably in the future, creating your own personal AI expert that knows everything you've done. That, I mean, as I said when we first discussed it, that is transformative. It could change, it would will change people's relationship with computing. I mean, I think it's really huge. The problem is they haven't been spending any time on the security of their system. They keep giving us ridiculous crap features that nobody wants. And we had what? 53 flaws, I think, this month more than 100 last month, which is low.
0:27:39 - Leo Laporte
53 is low, that's the thing. It's a small number relatively.
0:27:44 - Steve Gibson
And then here this comes along, which is in every version of Windows. It's been in there for who knows how long. So I just you know it. Just I mean I'm sure, as I said, somebody, the smart people at Microsoft, are thinking wow, wouldn't it be cool if we actually had an operating system that was safe to put this kind of capability into? They don't and they just can't get one by saying they do. We have a history of Microsoft declaring each version of Windows is more secure than the last one. Meanwhile, this has been in there the whole time, and who knows what else? How many flaws have they got queued up for July?
0:28:33 - Leo Laporte
So I mean just to be clear, recall is not a crap feature. It's a feature people would want and really cool. It's just you're putting it on a platform that isn't secure.
0:28:41 - Steve Gibson
Right, it is a rickety, insecure platform and that's fine if you want to run Excel. Okay, leo, I know you've messed with security certificates in the past. Have you ever looked at a certificate just to sort of make sure that it was correct? No, you know, we all know what they look like, right?
0:29:03 - Leo Laporte
I mean, I've used let's Encrypt, I have let's Encrypt certificates on my NAS and on various places. I would never look at them.
0:29:10 - Steve Gibson
I would imagine. Well, they're just text. It's a little text file, a 2K or 4K text file, and if you look at it you can see that it's a nicely. You know it's a base 64 encoded blob, blob, if that appears on your screen and recall, snaps it you've just lost.
0:29:31 - Leo Laporte
You've just lost privacy of your private key. I never thought of that. So the information that somebody would need the private key is in plain text in that.
0:29:37 - Steve Gibson
Yes, yes certificates are view, are visible, are viewable as text the private key.
0:29:43 - Leo Laporte
So in public private crypto the public key can be given to everybody, and it is and that's why it works. But you keep that private key close to your chest because if somebody got it they can impersonate you and if you ever open it on your computer and look at it, recall.
I never thought of that you know, of course they can fix this. They can have a switch that says oh yeah, if there's, there's a certificate, don't look at it, cause they have some things. Exactly yeah, cause we do stuff, private stuff, on our computers.
0:30:18 - Steve Gibson
You know and and we want to be able to I I've been thinking about this a lot and I'm thinking okay, what if you were conscious of the fact that your computer was spying on you because you want it to? I mean, like, with your permission, it's trying to collect all of this, but then this does for anyone who's privacy minded, they've got to be constantly turning it off before, not after, although I guess you are able to go back and kill, like some period of time. I forgot the turn off.
Again you've got to remember. So if you want this and you want privacy and you're serious about it, then you're constantly toggling this thing on and off so that it doesn't capture things that it shouldn't capture, that you don't want to have your expert know. Otherwise Russia gets in your computer and says show me all of the private keys that have been on the screen. There they are. So, yes, super search, wow. Speaking of recall, first they switched recall to opt-in, which we covered last week. That was a welcome move, but, as we know, I was still quite worried that Microsoft would nevertheless be promoting the heck out of it. And why would Microsoft ever mention the very real danger inherent in having any machine storing its entire history? You know they're not going to say oh well, we want you to do this, but danger, will Robinson? No, they're not going to tell you what could go wrong. So the latest good news is that Recall, that recall, has now been completely removed from today's June 18th production release of Windows Copilot Plus. It will initially only be available to users participating in the Windows Insider program. Last week I shared Microsoft's blog posting where, amid all of their mumbo jumbo about how they're putting security first, they're explaining. You know. You know that they're going to be switching recall to opt in and only decrypting. You know, on the fly, after you've given them a blood sample and tapped your heels three times. In an update to that blog posting last Thursday, they added update June 13th, 2024. 2024 today we're communicating an additional update on the recall preview feature for co-pilot plus pcs. Recall will now shift from a preview experience broadly available for co-pilot pcs on june 18th 2024 to a preview available first only in the Windows Insider program. In the coming weeks, following receiving feedback on recall from our Windows Insider community, as we typically do, we plan to make recall preview available for all co-pilot PCs coming soon. So again, yay, they backed off. They said we're adjusting the release model for recall to leverage the expertise of the Windows Insider community to ensure the experience meets our high standards for quality and security. This decision is rooted in our commitment to providing a trusted, secure and robust experience for all customers and to seek additional feedback prior to making the feature available to all Copilot plus PC users. So nobody gets recall, yay, until the insiders have played with it. People have experimented with it and we've learned collectively more about it. So this is terrific news and I'm sure Microsoft will get there eventually if it wishes to, and I'm quite certain that it wishes to.
As I said, I believe Microsoft has more in store for a machine's entire usage history than just scrolling back through time, since the actual delivered security of anything can only be judged retrospectively. That means that only time will tell whether they've been able to sufficiently protect any machine's entire usage history. What they were on the brink of was obviously half-baked, if that so it appears that they allowed their enthusiasm for this new capability to get the better of them and, as we saw from the reactions of the entire industry, this sort of immature exuberance does not inspire confidence. The main point I wanted to make is to note that we've never seen anything like recall before. It is not just a change in degree. This represents a change in kind, and it presents a security challenge of an entirely different scale. And that's just something Microsoft glossed over because you know they wanted to, yeah, and you know, maybe they're reading their own press, I don't know.
0:35:33 - Leo Laporte
I think they you know I mean in their defense they heard you and all the other security researchers howling and they did respond to it.
0:35:42 - Steve Gibson
I mean no, no, no, I'm 100 percent in agreement. They they realized this thing was going to come out and just get panned by you know problems.
0:35:55 - Leo Laporte
Everyone, yeah, yeah, all right, you want to take a break here, my friend? I do. Indeed, I have my finger hovering over the button.
0:36:05 - Steve Gibson
They're going to talk about Matthew Green and what he thinks about Apple's private.
0:36:09 - Leo Laporte
It's funny because you're going to talk about Apple in the next one and I'm thinking it's very easy for me, an Apple user and not such a big fan of Windows, to go, yeah, Microsoft, but now, when the shoe's on the other foot, let's see. I may not be so sanguine about the whole thing. We'll be listening Just a moment, but first I think, oops, I got to do the right thing Shift Nancy and tell you about I'm still learning the keys here. Tell you about our sponsor for this section, this portion of security. Now, one big thing, the number one big thing. Let me tell you what one big thing does.
If you are a small to medium-sized business, if you're a startup, if you're, you know you're really gunning and running. You're going out there trying to make the world a better place. There's a problem Because the world has changed and privacy regulations and AI compliance that's here to stay. Regulations around the world, and even state by state, are in constant flux. New regulations are coming out every day and as an organization, you've got to start embracing things like privacy by design, transparency, purpose limitation, data minimization, data subject rights the stuff we talk about every day, every week on Security Now, and you now have a legal obligation to do it. But you know, as I said, you're focused on making your mark in the world. You don't have the volume of work to keep a full-time data protection officer or privacy team busy. Nor, if you're a small to medium-sized business, do you have the ability to track the top talent. They're all going to the big companies the big tech, where they've got big stock options. The big companies, the big tech where they've got big stock options. Well, this is what OneBigThink offers. This is a really great idea. With OneBigThink's services, you're guided by an experienced executive who basically, in effect, becomes your DPO, your data protection officer. It's an enterprise security leadership role responsible for overseeing both data protection strategy compliance and, of course, implementation, so that you're compliant with GDPR, CCPA, the California Privacy Act, CPRA all of the things that the regulations affect your business, Things that, if you're like me, you're going. Yeah, I know I have to do it, but I don't have the bandwidth for this. I'll just let's put this on the back burner. But you can't, you can't, you have to do something about it.
Thank goodness for one big thing your DPO will have expert knowledge of data protection laws and practices. He or she will have a broad and deep information, privacy, compliance and data processing background skill sets across all industries. They'll know your industry, They'll understand it. They'll have a complete understanding of the IT infrastructures you may want to use or may be currently using, about the technologies, technical and organizational structures that are specific to your industry. You don't have to train them at all. They come in ready to go to keep you compliant. And, of course, they have to have excellent management skills because they've got an interface with internal staff at all levels, not just you, but everybody right. That's what you get.
An AI expert, a data privacy officer. One big think has the smarts, the knowledge, the team to do this for you. Their AI compliance service, for example, is designed to integrate with your organization's privacy program to provide the required governance, compliance and assessment activities under these regulations. And you could see with just what we're talking about with things like Microsoft Recall, that it's more than just complying with government regulations. You have to comply with your customer's expectations. That's just as important, maybe even more important to your business. And one big thing will do something that's really important. They will help you raise the awareness of your staff and train them into all the AI and privacy, compliance and regulatory issues, so that your staff is working. You're all rowing in the same direction, right? They're working with you. This is something every company needs, and One Big Think can give it to you at a price, at a scale you can afford To learn more about how to give your organization sustainable privacy and AI compliance.
You just go to the website onebigthinkcom. That's the number one B, G, T, H, I N K. This is no longer optional. This is a necessity in today's world. It's part of being in business. Fortunately, one big thing is there to steer you right One big thinkcom. We thank him so much for supporting the security Now program. Why are you laughing, Steve? What are you?
0:40:56 - Steve Gibson
laughing at. I'm just smiling. He's a happy.
0:40:59 - Leo Laporte
Steve Gibson.
0:41:01 - Steve Gibson
To remind everyone of Matthew's pedigree, this is Matthew Green. He's an American cryptographer and security technologist, associate professor of computer science at the Johns Hopkins Information Security Institute, and we're fond of quoting Matthew. He's great Because he's often outspoken about security issues and speak.
0:41:22 - Leo Laporte
English Super trustworthy?
0:41:24 - Steve Gibson
Yes, so in a series of I think it was 21 individual sequential postings under his Mastodon account, he outlined his feelings about what Apple described and about the nature of the challenge that they're undertaking with their private cloud compute concept, and I'm going to share this because it was great and then we'll also talk about it. So he said so. Apple has introduced a new system called private cloud compute that allows your phone to offload complex he says, typically AI tasks to specialized, secure devices in the cloud. He said. I'm still trying to work out what I think about this. So here's a thread.
Apple, unlike most other mobile providers, has traditionally done a lot of processing on device. For example, all of the machine learning and OCR text recognition on photos is done right on your device. The problem is that while modern phone neural he has in quotes hardware is improving, it's not improving fast enough to take advantage of all the crazy features Silicon Valley wants from modern AI, including generative AI and its ilk. This fundamentally requires servers, but if you send your tasks out to servers in the cloud, this means sending incredibly private data off your phone and out over the internet. That exposes you to spying, hacking and the data-hungry business model of Silicon Valley. The solution Apple has come up with is to try to build secure and trustworthy hardware in their own data centers. Your phone can then outsource heavy tasks to this hardware. Seems easy, right? Well, here's the blog post.
Then he provided a link to Apple's own disclosure about their private cloud compute and he said TLDR, it is not easy. Building trustworthy computers is literally the hardest problem in computer security. Honestly, he wrote, it's almost the only problem in computer security, but while it remains a challenging problem, we've made a lot of advances. Honestly, he wrote, it's almost the only problem in computer security, but while it remains a challenging problem, we've made a lot of advances. Apple is using almost all of them. He said the first thing Apple is doing is using all the advances they've made in building secure phones and PCs in their new servers. This involves using secure boot and a secure enclave processor to hold keys. They presumably turned on all the processor's security features. Then they're throwing all kinds of processes at the server hardware to make sure the hardware is not tampered with. He says I can't tell if this prevents hardware attacks, but it seems like a start.
Okay, and then Matthew includes a screenshot from Apple's posting which explains. This is Apple, quote private cloud compute hardware secure. Get a load of this. Wow, I mean this. I'm a bit of a fan boy for this Security.
Hardware security starts at manufacturing, where we inventory and perform high-resolution imaging of the components of the private cloud compute node before each server is sealed and its tamper switch is activated. When they arrive in the data center, we perform extensive revalidation before the servers are allowed to be provisioned for PCC private cloud compute. The process involves multiple Apple teams that cross-check data from independent sources, and the process is further monitored by a third-party observer not affiliated with Apple. At the end, a certificate is issued for keys rooted in the secure enclave UID for each PCC node. The user's device will not send data to any PCC nodes if it cannot validate their certificates. I'm just. You know, nobody has ever done anything like this before and, as I said, I need to confess that I'm a bit of a fanboy for the idea that Apple is performing high resolution imaging of each node's components in order to detect anything that might have been done to the server between its design and through its manufacturing. That's very cool, and just the fact that it's now widely known that this is being done likely serves as a deterrent to prevent anyone from even trying to mess with them.
Matt continued he said they also use a bunch of protections to ensure that software is legitimate. One is that the software is stateless and allegedly does not retain any information between user requests. To help ensure this, he writes each server, slash node, reboot re-keys and wipes all storage. So the idea is wipes all storage. So the idea is that it's like Apple has provided a large and growing collection of remote servers and an individual iPhone user is able to be connected to one of these exchange keys independently. Validate that specific connected nodes, security, establish a secure tunnel, send the data to this big computation engine, have it do whatever it needs to do on behalf of its user, return the results and then it's. It shuts down, reboots, wipes memory and then comes back up again so that it's fresh and clean for each request for every request yes, it reboots for every request.
It cleans itself out, rekeys, wipes all storage, that's seems like a lot.
0:48:18 - Leo Laporte
That's, that's apple, but that's what you have to do, right, yeah? But yeah, I mean, there's gonna be millions of people using this in a second. They're gonna have a million machines rebooting every second.
0:48:30 - Steve Gibson
I maybe it. Maybe it boots fast or they have a part they're running in ram or something I don't know.
0:48:35 - Leo Laporte
That's wild, yeah again.
0:48:38 - Steve Gibson
He quotes apple's announcement saying this is apple. We designed private cloud compute to make several guarantees about the way it handles user data. Three of them first, a user's device sends data to PCC for the sole, exclusive purpose of fulfilling the user's inference request. Pcc uses that data only to perform the operations requested by the user. Two user data stays on the PCC nodes that are processing the request only until the response is returned, that are processing the request only until the response is returned. Pcc deletes the user's data after fulfilling the request and no user data is retained in any form after the response is returned. And then three user data is never available to Apple, even to staff with administrative access to the production service or hardware I mean. So they've literally created a system that they themselves cannot penetrate.
Matt continues a second protection is that the operating system can attest to the software image it's running Specifically. It signs a hash of the software and shares this with every phone and client. If you trust this infrastructure, you'll know it's running a specific piece of software. Of course, knowing that the phone is running a specific piece of software doesn't help if you don't trust the software. So Apple plans to put each binary image into a transparency log and publish the software. But here's a sticky point not with the full source code. Well and again, apple is still a private company, right, they're not Linux. So Matt quoted Apple saying Right, you know they're not Linux. So Matt quoted Apple saying our commitment to verifiable transparency includes and here we have four short points publishing the measurements of all code running on PCC in an append only and cryptographically tamper proof transparency log. Making the log and associated binary software images publicly available for inspection and validation by privacy and security experts. Publishing and maintaining an official set of tools for researchers analyzing PCC node software. So they're going to create and provide tools that allow researchers to examine everything that they've done. And fourth, rewarding important research findings through the Apple Security Bounty Program. Matt says security researchers will get some code and a VM they can use to run the software. They'll then have to reverse engineer the binaries to see if they're doing unexpected things. He says it's a little suboptimal but again, you know there's a limit to what you can ask Apple to give. So he says when your phone wants to outsource a task, it will contact Apple and obtain a list of servers, nodes and their keys. It will then encrypt its request to all servers and one will process it. They're even using fancy anonymous credentials and a third-party relay to hide your IP from themselves. So they're even masking the IPs of the people using this incredible resource in their own data centers.
Quoting Apple about this, they wrote target diffusion starts with the request metadata, which leaves out any personally identifiable information about the source device or user and includes only limited contextual data about the request that's required to enable routing to the appropriate model. This metadata is only part of the user's request that is available to load balancers and other data center components running outside of the PCC trust boundary. In other words, the metadata is not encrypted in the tunnel, it's just used to get the tunnel endpoint connected within the compute center. They said the metadata also includes a single-use credential based on RSA blind signatures to authorize valid requests without tying them to a specific user. Again, you can't even figure out who's doing the asking. Additionally, pcc requests go through an OTTP relay operated by a third party. That's an anonymizing HTTP relay which hides the device's source IP address before the request ever reaches the PCC infrastructure, sort of like a mini Tor. This prevents an attacker from using an IP address to identify requests or associate them with an individual. Again, apple has gone so far beyond what anyone has ever done. It also means they write that an attacker would have to compromise both the third-party relay and our load balancer to steer traffic based on the source IP address.
So again, matt says okay, there are probably half a dozen more technical details in the blog post. It's a very thoughtful design. He said. Indeed, if you gave an excellent team a huge pile of money and told them to build the best private cloud in the world, it would probably look like this, he says. But now the tough questions Is it a good idea and is it as secure as what Apple does today? Most importantly, can users opt out entirely from this feature? He said. I admit that as I learned about this feature, it made me kind of sad. The thought was that that was going through my head. This is going to be too much of it. Is this going to be too much of a temptation? Once you can safely and he has that in air quotes once you can safely outsource tasks to the cloud, why bother doing them locally? And, leo, I think the answer is what you just said there's a limit to what this cloud like, how much processing Apple could possibly provide in their cloud.
0:55:25 - Leo Laporte
Oh yeah, Everybody wants to do this on device eventually, not just for privacy, but for economy.
0:55:31 - Steve Gibson
Right, right, yeah. He says once you can safely outsource tasks to the cloud, why bother doing them locally? Outsource everything. And the answer is exactly as you said. You know it's way better if your distributed computing is in everybody's hands instead of you know, monster servers in the cloud. He said as best I can tell, apple does not have any explicit plans to announce when your data is going off device to private compute, and his saying that does not feel Apple-esque to me.
It feels like Apple will provide these controls. We just haven't seen any of it yet. But they haven't said you know, they haven't talked about that. Matt said you won't opt into this. You won't necessarily even be told it's happening, it will just happen magically. He says I don't love that part. Now, maybe Matt knows something we don't, or maybe we haven't seen that yet from Apple.
He said, finally, there are so many invisible sharp edges that could exist in a system like this Hardware flaws, issues with the cryptographic attestation framework, clever software exploits Many of these will be hard for security researchers to detect. That worries me too. Now then, that's an interesting point. We've talked about how, because Apple's smartphone handset technology is so tightly locked down in order to keep bad guys out. Unfortunately, it also keeps good guys from being able to see what they need to see in order to know what's going on. Remember that Kaspersky, who are among the best people there are. They had malware in their phones that they couldn't detect until they detected some strange network activity that was being driven by the malware and that allowed them to begin to pursue what was going on. But you know, they can't see inside Apple's iPhones any more than the bad guys can.
0:57:40 - Leo Laporte
And that's been a secure complaint of security researchers forever, right To which Apple, by the way, has responded by saying OK, we're going to give select researchers access. I think they need to have kind of a valve valve, an escape valve, so the researchers can legitimate researchers can look in. But I understand why they don't want to do that.
0:57:58 - Steve Gibson
They don't want to right and and and matt's sort of contradicting himself, because he I mean he's he's just saying, okay, you know, he's playing devil's advocate, because he just told us that Apple will also be making a lot of this as open as they reasonably can. I mean providing virtual machines for people to poke at.
0:58:23 - Leo Laporte
Wow, that's really great. I mean, that's what they need to do.
0:58:27 - Steve Gibson
So he said. Wrapping up on a more positive note, it's worth keeping in mind that sometimes the perfect is the enemy of the really good. In practice, the alternative to on-device is ship private data to open AI or someplace sketchier where, who knows what might happen to it. He says and of course, keep in mind that super spies are not your biggest adversary. For many people, your biggest adversary is the company who sold you your device and software. He says, this pcc system represents a real commitment by apple not to peek at your data. That's a big deal. And his final tweet was or whatever you call it on Mastodon.
0:59:16 - Leo Laporte
Toot. We call them toots, toot. Well, okay, final toot Bean eater.
0:59:25 - Steve Gibson
In any case, this is the world we're moving to. He says your phone might seem to be in your pocket, but a part of it lives 2,000 miles away in a data center. As security folks, we probably need to get used to that fact and do the best we can to make sure all parts are secure, and I think Matthew's take is exactly right. Matthew's take is exactly right. The design of this system is what you would get if a bunch of very good engineers and cryptologists were to deliberately design a system that was meant to transiently extend an individual smartphone's local computing into the cloud for the purpose of performing some very heavy lifting. It takes advantage of everything we know about how to do this safely and securely. It will enable Apple's devices to do things no other mobile devices can do. But I have a concern that Matt did not raise concern that Matt did not raise, which is that, because Apple has made this transparent to their users, no one will be able to appreciate the lengths Apple has gone to to securely offer this capability.
The listeners of this podcast understand that Apple is visually inspecting the motherboards of their servers prior to deployment. For example, we've covered the worries over tiny chips being added to server hardware or Cisco routers when they're intercepted during trans shipping. Even though that's way out there, it's a factor Apple has preemptively considered. Who else is going to go to these extremes?
It's not that I'm worried about Apple being underappreciated. It's that I can easily see me to vendors popping up and offering their own outwardly similar capabilities that appear to be the same yes While providing none of the same true protections. They'll be able to say we're doing the same thing Apple is doing, thus riding on Apple's coattails, while providing far less true security for their users at a far lower cost to themselves. The concern is that Apple is legitimizing and popularizing the idea of exporting what could be an extremely personal mobile device data blob to the cloud for cloud-based processing. Other vendors are going to do the same, but users of those lookalike services will be placing their users' data at far greater risk than Apple. And who would ever know?
1:02:25 - Leo Laporte
Well, I'll tell you who would know. People who listen to this show would know, right, and I think what Apple counts on, you're right, the normal people will not know this. But what Apple counts on is that the people who do understand it, who listen to this show, will then kind of spread the word and when their less sophisticated friends and family say, well, is this trustworthy? They will say oh yeah, you should see what Apple has done. They don't need to go into the details. That's why you should listen to the show.
1:02:53 - Steve Gibson
Hey, leo. We have a big improvement with this new technology.
1:02:56 - Leo Laporte
Your mug is still giant.
1:02:58 - Steve Gibson
Steve, it isn't darkening my screen. You can't get it, but it is darkening my screen.
1:03:06 - Leo Laporte
I should mention.
You know, this show is really, I think, very important to people, not just people like you who are listening and watching, but your friends and family. The word goes forth from this show to everybody, and Steve has a huge impact because of that, and that's why it's really so important that we keep doing this show. One of the reasons I know people watching at home are saying it looks so crappy. Now, what's going on? And we are going to refine this. This is the first time we've done this in public, but we are working to make our production much less expensive, and that's not because we want to look crappier we don't, you know but because we want to make sure we can keep doing this for as long as possible, and part of that is just being fiscally responsible and doing what we can to make this affordable.
Here's the problem. Podcasting is in a crunch, a fiscal crunch. Right now, podcast advertising has died pretty much, and it's not just us, it's across the board. The audiences have gotten much smaller because there's so much more to listen to. That's a good thing, but it also means you make less money. Fewer advertisers, fewer listeners, means lower revenue.
Let's say, 20 years ago I came from mainstream media, from television and radio. So we created basically what was a small TV station. But it's a crazy enterprise and it's very expensive. Our payroll is phenomenally large the cost of the studio, the lights, everything, the staff. But the good news is for 19 years we could sustain it. Advertising was strong, audience numbers were strong and so, as long as we could, we did it without putting a burden on you. But those times have changed and we need to come to our audience now and say if you like what we do, if you think it's important and we certainly do we'd like to keep doing it, but we have to ask you to help out. That's why we created Club Twit two years ago.
Lisa, our CEO, was very smart, realized we're going to need some support from the audience, so she started Club Twit, set the price at a ridiculously low seven bucks a month. She's been told. I've been told. We've been told again and again. Why is it so low? I should say if you join, you want to pay more, you can. I'm not going to stop you. But we didn't also want to put up too big a barrier. We want people to listen to the shows. In fact, we're not even requiring that you pay to listen. There's not a paywall here. As long as we can, we'll offer everything for free, but we would like to ask those of you who can't afford seven bucks a month, who think this content is important, to join the club, because your support will keep us going.
I hate to beg, I'm terrible at this, but I would feel bad, I would feel remiss, if we went out of business without giving you some warning. So here's your warning this is not sustainable. Warning that this is not sustainable. Uh, one of the things we're doing and this is the experiment you're you're being subjected to right now is setting it up, so we don't need a studio. We would like to vacate the studio by the end of this quarter. Uh, shut down the lights. We don't have to pay the insurance. Get whatever part of the lease back that we can send people home to work at home, uh, and that will save us huge amounts of money. But the other side of that is to get more people to join the club. I'm really proud, I'm really pleased.
Oh, we dropped, we lost a paid member. When the show began, we were at 12,000 double oh seven members. We're now at double oh six. So somebody decided I ain't paying for this anymore. That's fine, that's fine, that's fine.
But I would like those of you who enjoy that, I only want you to support us if you think we're worthy of supporting. It's your vote, right? So, if you are interested, lots of benefits. We get ad, free versions of the show. You get a video on shows we only do an audio. You get additional shows we don't show anywhere else. You get access to our discord and it's thanks to our members that we are able to. We're using restream right now, which I think we're going to start using. I'm going to go home. Our staff is right now at home, uh, because we're practicing this technology so that come, come next couple of months, we can move everybody home and do this from home and save a lot of money. We're doing our part. I would like to ask you to do your part if you're not a a member yet.
Twittv slash club twit, we want. We want to go past episode nine, nine, nine, steve, I think we can get through the next 20 episodes. I don't think that's going to be so hard. It's a episode 2000. I'm thinking of seriously, cause I think what we're doing is really, uh, vital. Uh, it's entertaining, sure, but it's also getting the information out that people need to understand computing better. So please help us out. Twittv slash Club Twit. We also thank our sponsors. I don't want to be rude or anything here, but we have some pretty darn fine sponsors and we thank them for their support as well. In fact, right now I'm going to thank one of our sponsors, the fine folks at Collide.
You've heard us talk about Collide before. They had some very good news the other day. Collide was just acquired by 1Password. Now you might say, whoa, what does that mean? It's good news because both companies are leading the industry in creating security solutions that put users first. That's what 1Password does and it's always been what Collide does.
Collide is for companies with Okta. You know Okta does the authentication to make sure that that user is the user they say they are, to get them into your company network or using your company apps. But Collide does the other half of that, which is to verify that that authenticated user's devices are secure, their software is up to date. That's pretty darn important. Collide's going to keep doing that, but now as part of 1Password. So if you're an Okta company and you've been thinking about checking out Collide, this is a great time. Don't slow down. Go right ahead. And if maybe what's worrying you is how hard this is to implement, it is super easy. Collide comes with hundreds of pre-built device posture checks. The stuff you know you want is this operating system up to date. It's a browser patch, things like that. But then it's very easy to write your own custom checks that are specific to your circumstance Just about anything you can think of.
Here's another great feature of Collide I really like you can use it without MDM, which means you can use it on contractor's devices. You don't have to say, hey, please install this MDM, you can use it on contractors devices. You don't have to say, hey, please install this mdm. You can use it on linux devices. You can use it on every byod, phone and laptop in your entire company. That is the way security should be. You're suddenly your employees, your users are part of your security team keeping you safe, and now that collide's part of one password, it's just gonna get better. Check it out. You've heard it before. Maybe you thought about looking at the demo. Do it now. Collidecom slash security Now there's a demo. All the information you need K-O-L-I-D-E, collidecom slash security Now for companies with Okta. Collide is the very important second part of that authentication process. Collidecom security now. We thank them so much for their support of security now. Now leo's going to push some buttons. He's going to click up on here. Click a button there. He's going to press shift november.
1:10:27 - Steve Gibson
And now steve can now I know my name, no, steve knows his name and we'll continue with security now. Thank you, okay. So there's buzz in the industry today, today, tuesday, june 18th, of a recently discovered flaw in the widely used wget command line utility.
1:10:49 - Leo Laporte
Oh no, yeah, I use this, I use it all the time.
1:10:53 - Steve Gibson
Actually, it's the way I download the podcast audio every week to recompress it for Elaine.
Some outlets are claiming that this flaw carries an attention-getting CVSS score of 10.0. But anyone reading that, anyone who's been listening to this podcast for long, should immediately be skeptical. As we've seen, 10.0 scores are pretty much reserved for end of the world as we've known it flaws and it's hard to see how you could have an end of the world flaw that's not remotely exploitable and probably also wormable without any user interaction at the receiving end. But Wget is not a server or a service, it's just a convenient command line tool used to retrieve files. As I said, I use it every week to grab this podcast's audio for recompression before I post it for Elaine. So how any flaw in any command line tool that's not publicly exposing a vulnerable service to the internet could rate a 10.0 is beyond me. I mean, we've seen bad ones that like get to 9.8 and it's like oh, it's got really close, but no, and they're bad, but okay. So I did some digging and it's true that there is a problem with wget up through version 1.24.5. The problem surrounds incorrect parsing of semicolons appearing in the user info portion of the URL that's passed to WGET.
Okay, now for those who have been around for a while. You may remember that URLs are technically able to carry a username and password which appears before the host name, username and password which appears before the host name. So rather than, for example, actually example, I'll use is example Rather than https colon slash slash examplecom, you could have https colon slash slash username colon password at examplecom. Username colon password at examplecom. Therefore, and it's that username colon password and the at sign, which is the user info portion of a URL. It's sort of been deprecated. There's still some use for it, but you have to be careful because a username and password in a URL is now considered bad form. So you know, use with caution. So the concern is that mishandled semicolons in that portion of a URL might lead WGET's parser to confuse the user info with the host name which follows it in some way.
I located the dialogue with the guy who patched this flaw a few weeks ago. He wrote I just pushed a fix for the issue. Indeed, the URL parser implementation of WGET 1.x is based on RFC 2396, a standard from 1998. But even by this outdated standard, he wrote, the implementation of the user info parsing was not correct. It hopefully is correct now. Anyway, nobody is going to lift the whole URL parsing of WGET 1.0 to newer standards. But we have WGET2, and Fedora 40 recently switched to using WGET2 instead of WGET. And he says of course there are corner cases that break backward compatibility regards Tim.
Okay, so if you see anyone running around screaming about a CVSS of 10.0 in WGET while looking up to see whether the sky is falling, you can put their mind at ease. Up to see whether the sky is falling, you can put their mind at ease. All anyone ever had was a concern raised by seeing that semicolons were being mishandled. No exploit, no worms, no remote code, anything. The CVE for this minor parsing flaw appears to have just been assigned and published this last Saturday, june 15th. So it's quite recent. Nist's National Vulnerability Database lists the CVE but doesn't yet have any CVSS assigned. I just looked this morning, as I was going over all this again, just before the podcast, I did find a new reference at Red Hat which lists this with a CVSS of 5.4, which is far more sane. So anyway, I just wanted to put everyone's mind at rest.
Wget I'm still using, I'm sure one point, something or other, but again, not in any way. That's insecure and just to typically just to grab podcast audio once a week, a French court has ordered three very popular, well-known public DNS providers Google, we heard of them, cloudflare, we know them. And Cisco, oh yes, to selectively edit their DNS domain name resolutions in order to block the lookup of around 117 individual pirate sports streaming domain names. And you know why, not just sue Copperwire for having the audacity to carry electrons at this point? We've covered this sort of conduct before and it's just as wrong now as it was then.
Torrent Freak posted an article last Thursday which explained how this battle has been slowly escalating for the past year, went to court in France to tackle pirate sports streaming sites, including foodie, biteco, stream check, dot link, sport bay Dot, sx TV, football Dot info and catchy streamcom. Canal plus said that, since subscribers of local ISPs were accessing the pirate sites using their Internet services, how dare they, I know, and how dare those wires carry those electrons with those people? It's just, you know, we should. The ISPs, they said, should prevent them from doing so. When the court agreed, all major French ISPs were required to implement technical measures to comply.
Since the ISPs have their own DNS resolvers for use by their own customers, these were configured to provide non-authentic responses to deny access to the sites in question, all 117 of them. Naturally, in response to this blackout, savvy Internet users that had not already done so simply changed their settings to use different DNS providers. Yes, of course, I mean. You can just imagine people texting each other shoot, you know, sportybytescom just went dark. Oh nuts, just change your dns 1.1.1 yeah and off you go.
so they just changed them in different providers cloudflare, google and cisco whose resolvers had not yet been tampered with, at least at that time. Use of third-party DNS providers to circumvent blocking is common, so last year Canal Plus took legal action against those three popular public DNS providers Cloudflare at 1.1.1.1 or 1.1.1.1, google at 8.8.8.8, and Cisco at 208-69-38-205. In each case demanding measures similar to those which had already been implemented by French ISPs. And once again the court agreed. And once again the court agreed. Torrent Freak writes that quote tampering with public DNS is a step too far for many Internet advocates, but for major rights holders, if the law can be shaped to allow it, that's what will happen in this case.
article l333-10 of the french sports code, which became active in jan I know well, there you go. Sports code, we knew that they're good sports anyway which became active in january 2022, seems capable of accommodating almost anything, torrent Freak says. It reads when there are quote serious and repeated violations by an online public communication service whose main objective is the unauthorized broadcasting of sports competitions, rights holders can demand all proportionate measures likely to prevent or put an end to this infringement against any person likely to contribute to remedying it. So that's about as broad as any language could be. As a consequence, two decisions were handed down by the Paris Judicial Court last month, one concerning Premier League matches and the other the Champions League. The orders instruct Google, cloudflare and Cisco to implement measures similar to those in place at local ISPs to protect the rights of Canal+. The companies must prevent French internet users from using their services to access around 117 pirate domains.
According to the French publication which broke the news. Google attorney Sebastian Proust crunched figures published by government's anti-piracy agency, arcom. So, using figures from their own government, google crunched some numbers and concluded that the effect on piracy rates, if any, is likely to be minimal, starting with a pool of all users who use alternative DNS for whatever reason, users of pirate sites, especially sites broadcasting the matches in question, were isolated from the rest. Users of both VPNs and third-party DNS were further excluded from the group. Since DNS blocking is ineffective against VPNs, proust found that the number of users likely to be affected by DNS blocking at Google, cloudflare and Cisco amounts to a whopping 0.084% of the total population of French Internet users. Then, citing a recent survey which found that only 2% of those who face blocks simply give up, shrug and don't bother to find some other means, he reached an interesting conclusion 2% of 0.084% is 0.00168% of internet users. In absolute terms, that would represent a group of around 800 people across all of France. Who would be? Who would find that oh shoot, my pirate. Sports are no longer available and I'm just giving up because it's just not worth typing anything into my keyboard. It's just not worth typing anything into my keyboard to get it back, they said.
In common with other courts which have also been presented with the same arguments, the Paris court said the number of people using alternative DNS to access the sites and the simplicity of switching DNS are irrelevant. We don't care. Canal Plus owns the rights to the broadcasts and, if it wishes, to request a blocking injunction. A blocking injunction is what it shall receive. The DNS provider's assertion that their services are not covered by the legislation was also waived aside by the court. Google says it intends to comply with the order. As part of the original matter brought in 2023, it was already required to de-index the domains from search results under the same law. At least in theory, this means that those who circumvented the original blocks by switching to these alternative DNS services oh my will be confronted by blocks all over again. But given that circumventing this set of blocks will be as straightforward as circumventing the originals, that raises the question of what measures Canal Plus will demand next and from whom, and next and from whom. So, like I said, let's sue copper for having the audacity to indiscriminately carry anyone's electrons, just as we have in the European Union regarding whether or not, and exactly how and when communications can be encrypted and when communications can be encrypted.
Here again, we have another instance of a collision between the power of the courts and the power of technology. Technology desperately wants to be, and to remain, content agnostic. The electrons just don't care. But those who are in the position to impose their will upon the electrons only want them to carry the content they approve of. Google has capitulated, and I presume that Cloudflare and Cisco will follow suit Before long.
Dns is going to become a mess that doesn't actually solve any real problem, since pirates will just switch over to some lesser known, well off the map. Dns provider that isn't on anyone's radar is really only a convenience. In the first place, it's a pretty good bet that these pirate content hosting services are using a fixed IP, so just placing an entry into a machine's local hosts file will permanently solve the DNS problem by preventing the system from even querying external DNS. And we should also not forget that these piracy streaming sites are being hosted somewhere by someone. They are the true culprits and it's they who should be shut down, not honest and well-functioning free internet services offering DNS resolution.
1:27:16 - Leo Laporte
Wow, it's yeah, go after the, but this is how they always do it and it's frustrating.
1:27:22 - Steve Gibson
Because they can get to Google. Google has people Right, you know, snootystreamqr doesn't.
1:27:31 - Leo Laporte
Piratebootynet.
1:27:32 - Steve Gibson
no, that's right, well, you, you know, we sent them a letter and nobody replied. The service the service didn't go dark, so what, what? What can we do?
yeah, yeah, yeah, wow, it's kind of okay, during the run-up to today's podcast, I almost this was yesterday finished, or I mean sund evening finished with a code I wanted to have in place for automating the handling of undeliverable email. So it's still the case that nothing. I just wanted to let everyone know who's been registering at GRC and subscribing to the Security Now list. Nothing has ever been sent, so the reason you haven't received anything is that I haven't sent anything. But that should start happening this week. Among other minor announcements, I am now pre-checking the domain name portion of user entries by performing my own DNS lookup before I try to submit an email address that might bounce. I'm now you know anyway. So the point is that typos in the domain name portion are being caught before the user leaves the page, and GRC now supports plus signs in email addresses. So anyone who wishes to filter incoming mail by, for example, adding a plus GRC or a plus SN to the end of their mailbox name, may now do so. There's also a simple delete button on GRC's mailhtm page. So if you're enjoying using you know, if in general you enjoy using plus signs you can easily delete your original non-plussed email account and create a new one with a plus. Yeah, so for anyone who wants, and I have three quick pieces of useful feedback.
Talos Blalack he wrote long time SecurityNow listener and Spinrite owner. What was the program you used to download your email into something you could easily search? You mentioned it on an SN episode a few years ago. My domain host originally offered free email. The cost went to $4.80 per year when my email storage went over two gigabytes and I was willing to pay that instead of making the time to reduce my email size. Now they've moved to an email as a service and have increased the cost to $48 per year. It's time to back it up and clean it up as I move to a new hosting service. Thanks for all you do.
So, talus, this is my periodic opportunity to share one of my best discoveries ever. It's the free and wonderful MailStore Home, which is MailStore's free personal home edition. As I said, it remains one of my most valuable discoveries, which I'm happy to recommend without reservation. Through all the years I've been using it, it has never let me down. After installing it, you can aim it at your existing email archive or service and it will suck it down, index it and build an instantly keyword searchable you know, substring searchable local database. The way I have my own personal email system set up is that all incoming mail to me is also cloned into a separate archive email account and everything I send is also automatically blind copied into the same archive account. That way, the Everything coming in and going out, then in the very early morning at 3.30 am, a Windows task scheduler task fires off, starts at MailStore to retrieve, index and permanently add to its archive everything in my day's worth of email. So it's always kept up to date within a day. And, astonishingly, all of this is 100% free. And I should note that, while I've never looked into it, they also have enterprise solutions available for a refreshing one-time purchase, no subscription, for $260, you get an an enterprise wide email archiving and retrieval solution that integrates with Microsoft 365, google workspace and other email providers you know, and even whatever you are using yourself. So again, mail store is the company at just at mail M-A-I-L-S-T-O-R-E dot com. They're a German outfit and the home version is completely free and you know, just hats off to them. It's a beautiful solution.
Eric, a listener of ours who has some firsthand info about how IT goes over the New York Times, remember last week we talked about them losing 270 gigabytes of like. Basically, they lost everything all of their code, all of their website technology, everything. So he says hello, steve. I want to share a comment regarding the New York Times and a bit of history. Around 2010, I was working for a company that provided endpoint security and New York Times was our customer. They were stuck on an old, unsupported version of our software. Despite all the advances in behavioral-based machine learning and non-signature-based detection technologies, they insisted on running as AV only. We had countless emails and phone calls documenting our strong recommendation that they upgrade and apply the full security stack which they were entitled to this is 14 years ago.
Yep holy cow, he said the recommendations were ignored wow, and they were successfully attacked. They proceeded to publicly name us as their security provider and the technology that failed. Of course we could not go public with a big. We told you so and we were forced to take the black eye to protect the customer relationship. So, with whatever cybersecurity incident happened to the New York Times recently he said I do not believe a word they say. I have no doubt the story about the company's it guy leaving the private github access token exposed somebody yeah is only a cover story for a far worse problem.
So anyway, eric, thank you for sharing that this. This really makes me wonder how many of the problems we examine each week are effectively self-imposed. Right, you know we hear about a critical shortage of qualified it professionals, but I suppose there's no shortage of unqualified it wannabes. It would be interesting to know what the real reason was for them not wanting to improve their own security when an improvement was being offered, and even pushed From what Eric described, it sounds like it wasn't money, because they were already purchasing technology they refused to deploy. Incredible, mark Newton said.
Steve, I was searching through the show notes. I was thinking you mentioned having a remarkable two or something similar and how much you liked it. It appears there are a couple of different manufacturers out there. I thought you specifically mentioned the remarkable two or perhaps their version. You would not believe how often the word remarkable applies in the notes from multiple Security Now podcasts. I guess I'm saying remarkable, remarkable, remarkable. There's three. Anyway, he said you sparked my interest, pricey, but it looks like it would be helpful. Okay, so Mark Leo turned me on to the Remarkable 2 stylus-based e-ink tablet and I never want to use anything else. Okay now, in fairness, I did once feel the same way about the Palm.
1:36:31 - Leo Laporte
Pilot. How many do you still have in the fridge?
1:36:36 - Steve Gibson
I don't know. Extras of them went into the fridge for long-term storage and availability and safekeeping and they've never come out. So instead I have iPhones and iPads that didn't exist at the time. So I can't say something better. May not come along someday. So I suppose the lesson is to never say never.
But what I can attest to is that through the years since college, I kept trying over and over to use every spiffy new technology to replace my longstanding use of those wonderful light green quad rule engineering pads with the grid printed on the backside of the paper. Those pads with a soft lead mechanical pencil were always the ultimate solution when I was brainstorming or working on a problem. When I'm coding, I'll often make sure I don't make one of those common off-by-one errors by drawing simple diagrams of reduced complexity cases and then check it as I'm running the code in my head. After 50 years with those green engineering pads, the Remarkable 2 tablet finally replaced them for all time. I mean, it is absolutely my go-to tablet. I love it. So, yes, the Remarkable 2 is the device. And, leo, after sharing our last sponsor relationship with our listeners, we're going to discuss, dare I say, the angle of the dangle you dare not Also known as the saga of bingo bango dot com.
1:38:35 - Leo Laporte
Okay, well, we'll find out, we'll learn more.
1:38:38 - Steve Gibson
The dangerous dangling domains.
1:38:40 - Leo Laporte
The dangerous dangle of the angle. Yes, well, right now let's learn a little bit about our fine sponsor. You know their names. I've said it many times before. Actually, you probably know the name, it Pro, better than any of them.
This episode of Security, now brought to you by ACI Learning, who provides IT Pro? Okay, binge-worthy video, on-demand IT training and cybersecurity training that is not only engaging and fun to watch, really informative, really teaches you. It's the best way to learn IT, whether you're an individual or a team. With IT Pro you'll get cert ready with access to their full video library. It keeps growing. You know they've got seven studios running all day, monday through Friday. They are now up to 7,250 hours of on-demand training. And that's not dusty old stuff. You go blow it and dust off the DVD and pop it in. We're talking up-to-date material because the changes, the certs change, the questions on the cert tests certainly change, the versions of software changes and there's always new certs coming along, so they're always adding to their library $72.50.
And, by by the way, you should take a look at the premium training plans because you get additional features like practice tests. There's nothing like taking the test before you actually take the real test you really know. You go in prepared. You say, hey, I know I can ace this. You also get virtual labs, which facilitates hands-on learning. You don't even need a Windows server or Windows client to set up Windows servers and clients right there in your HTML5 browser on any device. It's also great don't tell anybody for MSPs as a way to try software before you install it on your client's computers. I just think it's a really nice tool.
It Pro from ACI Learning makes training fun. Aci Learning IT Pro training videos are produced, as I said, in an engaging way. Here's the secret. They're hiring experts in the field, people who do this day in, day out. More importantly, people who love it, and their passion for the subject matter not only makes them better teachers, it's more engaging for you, it's more fun to watch. They call it edutaining.
I think it's more than that. It's the kind of training you need to get the job in IT you want. Or, if you've got a team, to keep your team up to snuff. Or if you've already got a job in IT, to go to the next level. Right, it's fantastic. Take your IT or cyber career to the next level. Right, it's fantastic. Take your it or cyber career to the next level. Be bold and train smart with a c I learning.
Now we've got a great discount for you. Visit goacilearningcom. Slash twit the offer code twit30, twit30. Use that at checkout, you'll save 30 on your first month. Or if you sign up for a year, your whole first year 30. Goacilearningcom, slash twit. The offer code is twit30 and we thank aci learning so much for their support of security. Now we thank all of you for your support of security.
Now we're just something a little different today, a little weird. We're doing different software, doing a different studio, different cameras, and I apologize because I don't have a mic on off switch. So everybody said hey, leo, you cracked a beer during that last segment. It wasn't a beer, I promise. This was, uh, this was zero calorie sparkling water, okay, tropical fruit flavor, if you must know. And, by the way, before the next show, yes, we're going to have a mic switch Every once in a while. Leo needs to slurp. All right, steve. When I heard the name of this show, I said I don't think Steve knows what that means. But then I forgot You're a boomer, you know what it means you know who doesn't know what it means.
All of those people watching us now and they're almost 500 of them on YouTube, a same number on Twitch on on our channel, a discord channel for the club. We've got a big audience today. Thank you, all of you, for joining us. I appreciate it, and maybe it has something to do with the title, I don't know. What do you think, steve?
1:42:50 - Steve Gibson
If so, we may be disappointing some of our viewers. I think so, or maybe not, because you know, sometimes you don't want any dangle. Yes, actually, as a general rule, especially when DNS is concerned, dangling is not good. No, dangling is not good. No, as I said, this week's picture of the week presents a step-by-step flow of how domain takeover happens. Even though it's entertaining, even though I understood how this happens by the time a listener sent me that fun diagram, untangling the diagram was more work than following an explanation of how this happens. So I want to thank everyone who wrote with their explanations, since I love my rack of router, firewall switch and server hardware at level three, as I noted at the start last week, I've never so much as glanced at the architecture of cloud-based hosting. It just't. It has never been on my radar. You know, maybe in another 15 years when I can no longer lift a fully loaded server into the rack, but not yet. So the moment a listener mentioned that the trouble was almost certainly with a DNS CNAME record, the entire story became clear, and since we've somehow never talked in detail about how DNS CNAME records are used and how badly they can go wrong, I thought this would be the perfect opportunity. All of this, of course, is in reference to last week's topic the rise and fall of codemicrosoftcom and specifically to how it happened that a malicious actor managed to, however briefly, install their own presence into the code subdomain of Microsoftcom. The root of the problem is the potential for any organization's DNS records to point to something anything that they do not themselves control, because if they do not control the resource that their DNS records point to, the presumption would be that someone else may. Which brings us to the question how could that possibly happen, which many of our listeners will recognize as being the close cousin of what could possibly go wrong. The first thing to appreciate is that this general problem has existed since the beginning of the internet, when DNS was first created. So the issue of anyone's DNS pointing to anything they don't control itself is not new, and that's never been good. But what is new is the way cloud-hosted resources have evolved and how, as a result of this, the old problem of DNS misconfiguration has quickly become much greater.
Okay, so let's take the fictitious site bingobangocom. The people running it decide that they're fed up with running their own website and other services. It's time to move to the cloud and for the sake of this discussion, they've chosen Microsoft's Azure web hosting service. When Microsoft created Azure, they obtained the domain azurewebsitescom to act as the root anchor for all of their subscribers' services. So when someone wishes to have Azure host a site and their services, they register with Azure and choose a name for their service. It might be a human, readable and meaningful name like Bingo Bango, or it might be just anything that's available, like BB123. That's available like BB123. Regardless of what they choose, their new site is reachable as a subdomain of the azurewebsitescom domain, so it could be reached at bingobangoazurewebsitescom. Or, in the case of not caring much about the site's subdomain name, bb123.azurewebsitescom. But the Bingo Bango folks already own bingobangocom and no one wants to type bingobangoazurewebsitescom every time they want to visit the Bingo Bango website.
Microsoft was well aware of this, as was Amazon and all the other cloud providers. They knew that the names of their services and its subscribers' subdomains did not matter, because DNS could be used to hide whatever they were. We're all aware of the way good old standard DNS IP address lookup works right. A DNS you know typical IPv4 A address record or IPv6 AAA address record is used to turn a DNS name into one or more IP addresses. Name into one or more IP addresses. When a user's client wishes to connect, it uses DNS to look up the domain's IP address and then connects to one of the IP addresses returned. So it's a one-step process. But the success of this one-step process requires that the server's IP address does not change. If Microsoft could guarantee a fixed IP address for their subscriber's website, bingobangoazurewebsitescom, then standard DNS A record lookup could be used. Just like the bingo bango people once pointed their bingo bango dot com IP address at their own server, they could instead point their bingo bango go to the server at the IP provided by Microsoft.
But DNS provides a better and much more flexible way to achieve the same goal, which allows cloud providers total freedom in the way they set up at their end. For example, it might be useful to allow different regions of the world to be accessing cloud resources at different IP addresses, so that offering a single fixed IP to everyone would be less convenient. So this is made possible by a different type of DNS record known as a CNAME. The C of CNAME stands for canonical. Whereas a DNS-A address record returns one or more IP addresses, a CNAME record returns another domain name.
In programming. We would refer to this as introducing a level of indirection, because instead of a domain name pointing directly to an address record, it points to another domain name, which then probably points to an address record. And this domain name indirection using DNS CNAME records is the way cloud hosting providers are typically accessed. Using our example, once the Bingo Bango people have established their services at bingobangoazurewebsitescom, they replace their DNS's bingobangocom A record with a CNAME record pointing to bingobangoazurewebsitescom. Now, anytime someone wishes to visit the bingobangocom website, their web browser will look up bingobangocom and will find a CNAME record there. That CNAME record tells the browser that the name they were looking up, bingo-bangocom is actually a canonical name for the actual host name, and that CNAME record provides the actual host name, which is bingo-bangoazurewebsitescom. So that is the domain name that it should pursue in its quest to find an IP address for its connection. The user's DNS resolver then looks up the IP for the domain bingobangoazurewebsitescom, obtains that IP from the azurewebsitescom DNS servers and returns that to the user for their connection to the bingobangocom website. What's significant here is that two DNS resolutions were required and that the second lookup was for a property located under the azurewebsitescom domain. This allows Microsoft to host their subdomains at whatever IP addresses they choose and affords them the flexibility to change this at any time they wish. The bingo-bangocom DNS simply refers anyone who asks to the bingo-bangoazure-websitescom DNS for its IP. This CNAME resource creates a very powerful system of DNS pointers and, as we know, with great power comes great responsibility, so it should come as no surprise that things have not always worked out well.
The problem occurs, as happened to Microsoft with their codemicrosoftcom subdomain, when an organization deletes the hosted services and domain being pointed to by some other canonical DNS name. At that point, the canonical name is said to be left dangling because it's pointing to a non-existent host name. The bad news is that this opens the way for someone else, who would almost always have to be malicious, to re-register their own cloud service under the same domain name as what was previously deleted. In the case of the codemicrosoftcom subdomain, the subdomain would have had a DNS CNAME record. When that record codemicrosoftcom was retrieved, it would have provided the name of the host that had been deleted. So the bad guys would simply register their own host under that CNAME record's name, and anyone then accessing codemicrosoftcom would be referred to their probably malicious services and note that their servers would appear, and this is important. The malicious servers would appear to any web browsers to be within Microsoftcom. This creates additional potential for various browser domain origin trickery.
Three and a half years ago, on November 25th of 2020, the Daily Swig Cybersecurity News and Views newsletter at Portswiggernet posted a piece under the title rampant cname misconfiguration leaves thousands they should they could have said hundreds of thousands of organizations open to subdomain takeover attacks. They wrote and this was three and a half years ago. Security researchers had discovered more than 400,000 subdomains with misconfigured CNAME recordsarenz canonical name record used to map their canonical domain and subdomains to the third-party host domain. This means that the canonical rather than the host domain appears in the browser's address bar. Panaki Mandal of the security firm Redhunt Labs, based in India, wrote in a blog post that when a cloud-hosted website is deleted but the DNS entry pointing to the resource is retained, attackers can potentially re-register the host at the organization's subdomain as an alias and thus control what content is hosted under the original canonical name. Attackers can then serve malicious content to visitors and potentially intercept internal emails, mount PDF-based clickjacking attacks, hijack users' cookies and sessions by abusing OAuth whitelisting and abuse cross-origin resource sharing to harvest sensitive information from authenticated users. In other words, you really don't want bad guys to appear to be in your own primary domain.
Using a tool they write that conducts mass DNS resolution, red Hunt Labs found more than 424,000 subdomains with misconfigured CNAME records during an automated trawl of 220 million hosts. The number of sites that were abandoned, for example, if they belonged to defunct organizations, was unclear due to the additional need to look up company registries to obtain that information. But by adding HTTP response grabbing, the researchers uncovered evidence that 139 of Alexa's top 1,000 domains may have fallen prey to subdomain takeovers 139 out of the top 1,000. Red Hunt Labs identified 33 third-party services that allowed for potential subdomain takeovers, with nearly 63% of vulnerable DNS records pointing to Shopify. Most vulnerable domains belonged to e-commerce operators. Landing page creator Unbounce accounted for the second highest number of vulnerable domains, at 14%, followed by Heroku at 10%, github pages at 4% and Big Cartel at 2%. Drilling into the data, red Hunt said www was wow. That actually makes sense, right Was the most frequently vulnerable subdomain. So think about that.
1:58:32 - Leo Laporte
Wait a minute, you can have a wwwbingobangocom.
1:58:39 - Steve Gibson
Exactly so. Bingobangocom might still have their email being handled by their own bingobangocom, but wwwbingobangocom Leo, you know why it goes that name?
1:58:51 - Leo Laporte
just because it was so fun to say it. Well, you saw that our chat room found somewhere. You can register it for a mere $8,000. So go for it.
1:58:59 - Steve Gibson
Oh, that's interesting because when I looked last night it was at $15,000.
1:59:04 - Leo Laporte
Yes, that's what Galeas said, so maybe he got a deal. He found a deal.
1:59:08 - Steve Gibson
Nice Half off, steve. Now I have to tell you that my first thought was to go with bingotipscom, because I thought, okay, how can you have bingo tips, but there is a bingotipscom.
1:59:21 - Leo Laporte
Of course there is Dude. You're quoting security research from a company called Portswigger who's number one, by the way, I'm sorry, I pushed the wrong button who's number one product is burp sweet, although I gotta say there's a certain consistency to that's their naming they're stink. Faithful to the name, they're actually legit, but I just know they are.
1:59:52 - Steve Gibson
Yeah, that's why I quoted them is there, are they're a real group?
1:59:54 - Leo Laporte
yeah, it's hysterical oops, I gotta zoom you, here we go. Nope, not that. No, oops, not you, no, no, here, wait a minute, there you go command nancy, command nancy, okay, okay.
2:00:15 - Steve Gibson
So it totally makes sense that www would be the most frequently vulnerable subdomain, because somebody who doesn't want to host their own website yeah would would send www off to some third party. So yeah, wow, this guy, panaki Mandal at RedHut, pointed out that by suppressing and removing the www remember when Google did this and the msubdomains from the Chrome browser's address bar, that was at Chrome 69 onwards he said Google had inadvertently made it more difficult for users to determine whether they might be browsing attacker-controlled content. Redhunt found around 200 non-functional gov site subdomains with misconfigured CNAME records, and one had a wildcard CNAME record, which poses a particularly dangerous security risk. And Mondal noted that prestigious universities owned some of the roughly 1,000 misconfigured edu subdomains. And anyway, I guess my point here is Microsoft certainly is not alone in having tripped over this problem.
The findings show that, despite the potentially calamitous impact of subdomain takeovers, many well-resourced large organizations are struggling to comprehensively discover and track their own ever-expanding infrastructure. You can just imagine what the DNS must look like of some of these organizations. Yikes Mandel also noted that Roblox, starbucks and the US Department of Defense are among the organizations to have remediated subdomain takeover flaws through HackerOne in the past year that was, two and a half or three and a half years ago the article ended with the Daily Swig noting that the year before they posted this, in 2019, it had previously reported on subdomain takeover flaws stemming from Windows 8 live tiles feature and the year before that, a misconfigured Microsoft subdomain back in 2018. So not even Microsoft's first subdomain problem. Before this article, which is from November of 2020, and before Red Hunt's research, researchers from the University of Delaware and the College of William and Mary published their research titled and this is back in 2016, all your DNS Records Point to Us Understanding the Security Threats of dangling DNS records. So my point being not a new problem, very powerful, but very easy to get wrong. So our takeaway for today's podcast is that Microsoft definitely made a serious mistake when they left their code subdomain dangling, but they're far from the only organization to have ever done so.
In today's increasingly complex IT landscape of overlapping services, where such services are increasingly being outsourced, dns can become quite complex and convoluted, and we once talked about how one of the tricks being used to track website visitors is to point a CNAME record of a website to an advertiser's domain as a means of giving them first-party cookie tracking status. That struck us as being ultra slimy at the time, but it's the times we're living through. So just a heads up reminder to any of our listeners who have responsibility for the management of DNS within their organization. You likely already know that DNS is not as simple and straightforward as it once was. It might be worth making sure that you know who any of your organization's C-name records are pointing to and that they have a good, ongoing and legitimate reason for being granted such a potentially powerful position, since they're your organization's root domain.
2:04:49 - Leo Laporte
Wow, absolutely A chilling thought, although if you figured out how to get bind working, you probably know enough to keep yourself from getting C-name poisoned.
2:05:03 - Steve Gibson
Well, I don't know. You know, what happens is it's one little thing after another. You add this, you add, add that it gets increasingly complex and then some certain you like someone doesn't renew a contract, right, and so they disappear. But it doesn't automatically delete that record from dns. Dns is still pointing to them, even though they're no longer offering the service.
2:05:29 - Leo Laporte
It's amazing amazing what a world we live in. Steve, you're the best. Thank you for putting up with this crazy situation. Here we're trying out new software trading in the TriCaster for a software-based solution called Restream, which unfortunately allows me to put chat comments into your feed.
2:05:53 - Steve Gibson
I just decided I'm not going to try to read them while it's going on. Don't look at them. I can't do that.
2:06:00 - Leo Laporte
And I'm having a little fun with it, but so are the chatters. It also gives us the opportunity to stream this video into multiple places once again, which is great. We've got Twitch watching. There's 445 people on YouTube, 138 people on Twitch. We can expand it to beyond that, to X and to Insta, you know. I think this is just a really nice way to be able to share what is such an important show with a broader audience. So thank you.
Now, of course, if you want to watch us live, you should know that we are on every Tuesday right after MacBreak Weekly. Eventually, macbreak Weekly will also be streamed in this format. In fact, eventually, all of our shows in the next couple of months will be streamed this way. Couple of months will be streamed this way, but right now, macbreak Weekly is on Tuesday morning and then right after that, around 1.30, 2 pm Pacific, 5 pm Eastern, 2100 UTC, we'll fire up the Security Now servers and we'll get the show on the road. You could find Steve's show notes at his website, grccom, theson research corporation. Steve also has some unique versions of the show. After the fact, he has the 16 kilobit audio use, ffm, peg and some long command line right to do that. That's what I do. You compress the hell out of it and then you send that to elaine ferris, who is a very talented uh, I want to say luthier, but no, she's a fair farrier. Luthiers make loots, she sure? Horses shoe horses. Horses shoes shoe horses, she shoes horses I don't know that she actually does.
2:07:44 - Steve Gibson
I think she once said to me why does leo keep thinking that I'm a farrier? I think she just has. I think she just has horses oh, she just has them.
2:07:52 - Leo Laporte
Well, somebody else does the ferrying. Okay, fine, but she lives on a ranch with very little bandwidth.
2:07:57 - Steve Gibson
I do know that she's also a court reporter, so she is able, she lives in the high desert and she once sent me a picture of a cactus with snow on it, which is really something that's very high uh, wow, um, so she does it all.
2:08:12 - Leo Laporte
She does a nice transcript, which is also available on his on his website, grccom. While you're there, check out uh, spin right the world's finest mass store. Let's see if I can get this right, because it's continually changing mass storage performance, maintenance and recovery utility yes, I got it all perfect well, he keeps getting more abilities.
The version 6.1 just came out. Somebody was in the youtube chat saying is steve still do it? Was that's been right? I said, yeah, 6.1 just came out and now it supports ssds will improve the performance of your ssds, sometimes dramatically. Uh, does a lot of really cool things.
Find out more at GRCcom, and Steve has a lot of free stuff there. Like everybody knows about Shields Up, you did that really Never 10 thing. If you buy USB storage on Amazon, you need his Validator program to make sure that it actually has as much storage as it says. It is very scammy out there, and validator again a free program, one of many you offer really is a necessity. So thank you for doing all of that. We really appreciate it.
We have audio, a 64-kilobit audio, like Steve does on our show site, twittv slash SN. We also have a video if you want to see, because that's the only way you can see the chat comments see Leo screw up, find out about shift November and all of that stuff. That's on the video. We offer it on our site. There's another way you could do it, though. Youtube also has a dedicated channel for security now I think it's youtubecom slash security now, something like that. And well, the best thing to do is subscribe, because if you get a podcast player and look for Security Now, you'll find both the audio and the video versions. You can subscribe and you'll get it automatically.
Frankly, here we are. How many episodes in 979. With 979 episodes under our belt, let's see. Do I have a click for that? I think I do. No, that's not it. Is this it? No, that's not it, although you might want to scan that QR code right there so you can join Club Twit. That makes it easy. Go right to the club. I guarantee you it's a secure qr code, although our team, our, our viewers know better than the scan qr codes. Where's the? Uh, where's the show title thing? Well, I guess I don't. I don't know where that is anyway. Um, I have always there'll be a show title. Oh, you'll see, I have all these buttons everywhere. It's crazy. It's crazy, but it's fun for me, because it's been a long time since I actually had to do any of this. We used to have people doing it. So, anyway, phyllis thinks I'm doing this on purpose. I'm not doing it to you on purpose, phyllis. I'm not. Now, steve is Steve's doing that on purpose. Knock it off, steve.
Knock it off, oh no no, no no, no, I'm going to put an epileptic warning on the show now. Uh, um, what else? Is there anything else? Uh, yeah, I clicked that and it doesn't give me the show title. There may be an overlay. I have to click here or something like that to do that. I don't know.
2:11:35 - Steve Gibson
Maybe Nancy's upset. You didn't call her Nora.
2:11:39 - Leo Laporte
Nancy shift, nancy shift, nora. I decided to go with the November is good. Yeah, with the official NATO phonetic alphabet shift November. Anyway, we're done, steve. Go have a great week and I'll let you come back next Tuesday for Security Now Tomorrow, windows Weekly and Twig as we continue to try to make the world a better place, one computer at a time, and everybody who has signed up to receive email from GRC Security Now list should probably get something from me this week, so I think that they, the first mailing, will go out.
2:12:14 - Steve Gibson
Oh, something magical. Well, uh, the weekly, uh, summary show notes, picture of the week and so forth oh good, yeah, that's nice, that's part of that's what.
2:12:24 - Leo Laporte
That's what the mailing is. Is the show stuff? Oh, that's good. Yeah, do that. Sign up for the show notes. What is that? It's grccom slash mail Mail Easy to remember. Steve, if you haven't heard earlier episodes has a very clever system for making it possible to email him without being a spammer, and at the time when you sign up for that and get validated, you can also subscribe to his newsletters Optionally if you like.
The check marks are off by default. He is an opt-in kind of guy. They are, so thank you for opting into security. Now To all the people who watched us and said wow, I didn't know this show was still on the air. There's still people who watched on YouTube. You guys still do this show. Yes, how many years, steve? We're closing in on the end of our 20th year unbelievable.
2:13:15 - Steve Gibson
I think it's month after next, it's in august sometime, that we, we, we start in our, we finish. We're 20 years old and we start into year 21, which is where we'll be.
2:13:25 - Leo Laporte
We'll be an adult when we finally cross 999 yeah, you and I have gotten gray doing this show, but I have to tell you we're on a mission and this mission is not over. As you can tell from listening. The show doesn't get shorter, the security problems don't go away. So you come back next week.
2:13:44 - Steve Gibson
Now I will say the angle of an angle may change.
2:13:49 - Leo Laporte
I keep looking back, hoping to see you, but you're not there anymore. You're here. Thank you, steve. Thank you everybody. We'll see you next time on Security Now.
2:13:56 - Steve Gibson
Bye Security Now.