Security Now 953 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
00:00 - Leo Laporte (Host)
It's time for security now. Steve Gibson is here. Can you believe that the FTC wants to find Facebook $200 billion by Facebook's fighting, and why some people think maybe they ought to? We'll also talk about the percentage of internet traffic generated by automation and how much the internet traffic has increased in this year alone. And then an amazing offer from Cox Media Group to sell advertisers based on the things you say around the house. Is that possible? Steve will talk about it and more. Next on Security Now Podcasts you love.
00:43 - Steve Gibson (Host)
From people you trust.
00:45 - Leo Laporte (Host)
This is Twitter. This is Security Now with Steve Gibson, episode 953 for Tuesday, december 19th 2023. Active listening Security Now is brought to you by Secure my Email. Secure my Email provides easy encryption for your current personal and business email addresses. Set up takes only minutes. Start your free account or enjoy a 30-day free trial of a premium plan, no payment info required and there's a special offer for Twitter listeners. But to find out what that is, visit SecureMyEmailcom, slash Twitter and use the code TWIT at checkout. It's time for security. Now the show. We cover your security privacy online and we talk about how the internet works. And we also share some fun stuff about sci-fi and other things with this guy right here, steve Gibson of GRCcom. Hi Steve Leo.
01:45 - Steve Gibson (Host)
This is the last podcast we will be recording in 2023. Oh yoyoy, end of the year. And the good news is the podcast itself will not be ending in 2024, as it was previously planned to be. But no, by popular demand. Literally, we're going to continue. We're going to answer some questions and look at something I think interesting and kind of horrifying, and come away with an action plan for next year. So is the US ever going to be able to introduce new child protection legislation or are we going to continue punting to the US Constitution? 2024 means the beginning of the end of traditional third party cookies in Chrome. Finally, what's the plan for that exactly?
02:41
How much did the internet grow during 2023 and why? What's the most used browser based query language currently? What's the updated ranking of sites top 10 by their popularity? What percentage of total internet traffic is generated by automation? Those and many other interesting stats have been shared by Cloudflare and we'll dig into those. Then, after catching up with a bit of spin right news which I had promised last week I have it this week and some feedback from our listeners, we're going to examine the content of some very disturbing web pages that Cox Media Group originally posted, then quickly removed from the internet, but not before the web archive snatched them up. So we still get to see them and, as always, we have a fun picture of the week to share with our listeners.
03:35 - Leo Laporte (Host)
And I will not look as always, but I do have to tell you it's time for a break, to talk about something that we talk about a lot.
03:46
Security Now is brought to you by Secure my Email. In fact, for years I told people how to do email encryption. Remember that. And I would say, okay, you got to install a GPG, you got to get on the key server Some people know you exist and you got to modify. It was just a pain, and I can literally the number of people who email me saying, hey, is this working? We're like, over the last 10 years, maybe 10 at most. At most it was it's people just don't do it. It's too hard.
04:18
But I think if you listen to the show, you know that sending emails basically like sending a postcard everybody along the way can read what you're sending. I always crack up when I see attorneys put the little disclaimer at the bottom of their emails and say if you're not the intended recipient, do not read this. It's like too late, dude, that's not the force of law. I don't think so. I think I had to read that in order to read that. I think I had to read it, but I'm just.
04:46
You know who knows the really the real answer is encryption. Obviously encrypting your email, but it's hard to do using S MIME certificates or open PGP, it's just tough. Along comes Secure my Email, and this is really great. This is the email encryption service we've all been waiting for. Look, email is important too important to be sent through the email, the email like a postcard. Unfortunately, email just doesn't have any security built in. Encrypting solves the problem, but it's very complicated without Secure my Email, pgp and S MIME or antiquated, complicated cumbersome. They're one user at a time. You know you have to exchange keys or go to a key server to find out what the person's key is. It's just not easy. Secure my Email solves all this. They allow you to enjoy the simplicity and utility of email with all the privacy and security of modern encryption. You can send and receive encrypted emails on all your devices Mac, windows, ios, android. It uses a variety of security and encryption methods, including these Steve Gibson approved Open PGP and Cha Cha 20, which, despite its name, is not a dance move but is actually a good cypher suite. Make your email fully HIPAA and GDPR compliant with Secure my Email.
06:07
You don't have to put that disclaimer at the bottom. No one can read it unless they're the intended recipient. And here's the best part you don't have to change anything. You can encrypt your current email addresses, both personal and business. You don't have to change addresses. You don't have to change providers Most of those other encrypted email services you've got to actually go use their client right and their server. You're welcome to use Secure my Emails apps to manage your email. You can keep your current apps and just use Secure my Email when you want to have it encrypted. That works fine. It's super easy to set up, super easy to use, because all the encryption, all the complications are hidden.
06:45
Your recipients and this is really important to me don't have to be Secure my Email customers to read it. They don't have to register, they don't have to know passwords. There's no sideband password exchange, anything like that. Even proton mail requires an out-of-band password for non-user recipients and you have to change your email address and all that stuff. When recipients respond to you, if you've used Secure my Email, their email and attachments are encrypted through the Secure my Email systems as well. So now your entire conversation is private.
07:18
Now the best thing is Secure my Email has a free forever plan. You can encrypt a single consumer email address from Gmail, yahoo, microsoft and more for free forever. Instant download, instant activation, no payment info, registration, no call required, and they have paid plans too. If you want to use up to eight email addresses, just $3.99 a month or $29.99 a year per user. Eight email addresses business or personal per individual user. Their business funnel is great. I really like it and they work with true, good open source encryption so you can trust it. Start your free account or enjoy a 30-day free trial of a premium plan Again, no payment info required.
08:06
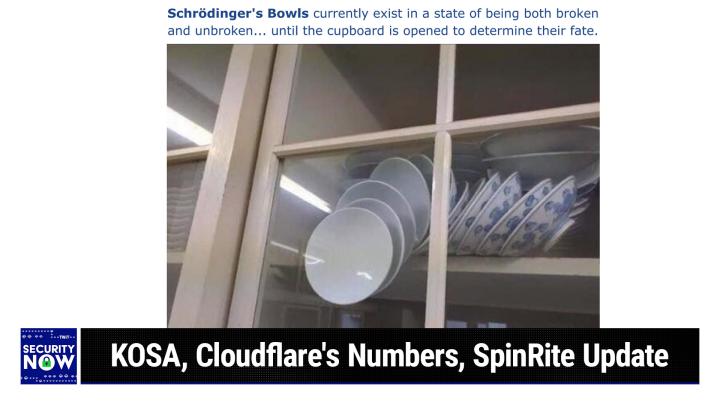
They have a special offer for Twitter listeners. Visit SecureMyEmailcom slash Twitter. Securemyemailcom slash Twitter. To get this offer, use the code TWIT at checkout. That's important. Securemyemailcom slash Twitter and use the code TWIT. Thank you, securemyemail for supporting, you know, not just Steve and Security Now, but the mission I've long believed in of securing email with encryption making it easier. All right, I have a picture. Well, you have a picture. I'm ready to look at it. Shall I look at it now? Look at it now, okay, schrodinger's bowls. I've seen this picture before. This is a nightmare scenario. Describe it for us, mr Gibson.
08:51 - Steve Gibson (Host)
Yeah, so what we have is a cabinet with four panes of glass, so we're able to see what's inside. And what's happened is, through some catastrophe maybe an earthquake, we don't know what a large number of bowls that were once stacked have fallen over inside the cabinet and fallen toward the glass, so that, like by some miracle, a whole bunch of them have not actually dropped to the bottom, because each one, in sort of almost an accordion-like fashion, is holding on to the bottom edge of the one below it. And so here's the point. This says Schrodinger's bowls currently exist in a state of being both broken and unbroken until the cupboard is opened to determine their fate. Because it's very clear you're not opening this cupboard as long as there's gravity, without breaking some bowls.
10:08 - Leo Laporte (Host)
You might slide a little paper in there, maybe like if you had some fancy expandable foam chemical foam that you just floored in there.
10:22 - Steve Gibson (Host)
But basically these bowls. The point is these bowls are already broken. I mean, they are as good as broken, but it just hasn't happened yet. So, yeah, anyway, that was a great one, and Laurie's son, robert, was over yesterday and he too had seen it before, so it was new to me, but obviously it's been a meme that's been around a while. So, anyway, a little bit of fun, okay. So here's something that's not fun.
10:57
Metta is suing the US Federal Trade Commission on the grounds that it, the FTC, does not have the constitutional authority to hold meta accountable. And the FTC is attempting to find meta. Get this $200 billion, $200 billion over meta's deliberate and flagrant violation, they say the FTC says, of the Children's Online Privacy Protection Act. We've talked about COPPA COPPA before, which requires parents to sign off before websites gather and use personal information from children younger than 13. The FTC claims that and yes, leo, I like did a double take and went back and verified it was billion with a B because $200 billion. Anyway, the FTC claims that the recent lawsuit filed by 41 states attorneys general documents that meta had knowledge that millions of users younger than 13 use its services without having obtained parental permission. Okay, now the thing that caught my eye about this is that unbiased observers believe that Metta's argument likely has merit. Even ex-FTC guys are saying oh.
12:39
FTC is probably going to lose this one, and also that the US Supreme Court may side is likely to side with Metta if the dispute reaches our highest court. So this is another of those issues and, yes, they're piling up. Where what's really needed is for US lawmakers in Congress to make some laws in lieu of continuing to over leverage and overinterpret the US Constitution. Not surprisingly, the US Constitution, largely written in 1787, which was before two paper cups connected by a string was invented offers little guidance on the issue of age-based IP-driven website content filtering. What we need are some laws here, but that turns out to be a problem too. We've spent some time looking at the UK's attempt to force some means of monitoring all encrypted messaging, and the future of the EU's legislation to force browsers to accept their country's individual certificate authorities without question remains unclear. The clear pattern here is that technology rarely seems to line up with what lawmakers want. Fortunately, that never appears to deter them or to make them want it less. They just become more insistent that they ought to be able to have anything they want. So, along those lines, we have a mess brewing here now in the US that Metta's pushback against the FTC brings into sharp focus. It promises to create another challenge that technology may not be able to deliver. When this happens, every time we ask the Internet's amazing array of technologies to do something it was never designed to do. Legislators are talking about wanting Internet content providers to protect young people in the US by blocking content based on age, and even if that was all they wanted, it's unclear how technology could provide that. But there are other legislators who believe that some young people must continue to have unfettered access to content. That's inherently controversial. So we can't even agree on what we want, even if the Internet technology could provide it.
15:17
Suzanne Smalley is a reporter for the record. She's been following this developing story. Her most recent installment last Monday covered this meta pushback against the FTC, which may actually as I say, the FTC may actually lack the legal grounds for their attempted regulation of Metta. But back in July Suzanne posted a piece in the record which captured the heart of the issue under the headline Sweeping and Controversial Children's Digital Privacy Bills Plural Bills Head to the Full Senate. After my light editing for the podcast, this is what Suzanne wrote. She said Two bills designed to bolster children's privacy and safety online advanced in the Senate on Thursday.
16:10
Again, that's a Thursday back in toward the end of July, she said, after months of infighting between children's advocacy organizations and technology civil rights groups over what the latter see as problematic freedom of speech and privacy concerns in the legislation. Despite the mixed views, commerce, science and Transportation Committee voted to advance the bills known as the Kids Online Safety Act. Okay, so this is a new one. We haven't spoken of before KOSA and the Children and Teens Online Privacy Protection Act. That's COPPA 2.0. So we're going to update that Hasn't been touched since 1998. She wrote the latter updates an original COPPA bill passed in 1998, which is considered the first and only major federal privacy legislation.
17:04
Committee Chair Senator Maria Cantwell cheered both bills' success, that is, you know, in getting to the Senate at least saying that COPPA 2.0, saying of COPPA 2.0 that children and teens can be quote overwhelmed with the complexities of online content that is manipulated and targeted at them. She said the bill strengthens protections and closes loopholes, while ensuring data of children under age 17 is protected more rigorously. President Joe Biden, who discussed the need for stricter children's privacy laws in a State of the Union address, urged the committee to approve the bills earlier this week, but there are questions about their potential to become law, particularly since there are no house versions. Coppa 2.0 changes the existing law to require online services to stop collecting data from kids under age 17, which raises it from the under age 13 of COPPA 1.0. Cosa that COSA law is far more sweeping and requires platforms to filter content directed to users under age 17 in the name of preventing, for example, suicide and anorexia. While celebrating the progress of COSA, cantwell acknowledged the profound concerns in the free speech and technology civil rights communities about how the bill would block vital LGBTQ content from older teens. Acknowledging the advocate's concerns, cantwell said quote we will continue to work with them. Unquote.
18:52
Cosa, the more politically charged of the two bills, is supported by a range of children's privacy groups and larger organizations devoted to children's mental health, including common sense media, the American Psychological Association, fair Play and the American Academy of Pediatrics. A letter to senators signed by more than 200 groups pointed to troubling statistics that advocates say are directly tied to the broad freedom of access children have to online content and the uncontrolled and often profit driven behavior of companies pumping it out to them. The letter highlighted that depression rates in teens doubled from 2009 to 2019 and cited a similar doubling of eating disorder emergency room admissions for teen girls from 2019 to now, so just in four years, that doubled. More than 90,000, 9,000,000, 90,000 pro eating disorder accounts with 20 million followers appear on Instagram, the letter said, with meta earning an estimated $230 million annually from such accounts. The letter, signed by more than 200 groups, said quote after numerous hearings and abundant research findings, the evidence is clear of the potential harms social media platforms can have on the brain development and mental health of our nation's youth, including hazardous substance use, eating disorders and self harm. The founder and CEO of common sense media, which focuses on children's privacy and safety online, echoed the letter's assertions Thursday and highlighted the outdatedness of current laws governing children's use of technology, saying the bipartisan group of sponsors were quote doing their part to bring tech policy into the 21st century.
21:01
A large number of freedom of expression and privacy and data privacy groups, including the electronic frontier foundation, the Center for Democracy and Technology and the ACLU, have lobbied hard against COSA, in particular, saying the costs it imposes to address children's online safety are too high. Cosa would mandate parental consent when children under age 13 create online accounts and require providers to give the parents of these children the ability to change privacy settings. As a result, advocates say children will be forced to tell their parents which sites they visit. They point to the bill's inclusion of a so-called duty of care provision, which they say creates an obligation for online service providers to prevent harm to minors under age 17. But in doing so, the bill's broad language will effectively block a wide range of important information, including about mental and reproductive health, lgbtq issues and substance use dependency support, they say. The requirement to prevent harm is extreme, advocates say, and will lead to expensive, extensive and often ineffective content filtering. The bill will also likely trigger an overreaction from online content providers, who, emma Lonso, founder of the Free Expression Project at CDT, said will block far more content than necessary over liability concerns. Lonso also criticized how the bill would give civil enforcement power to uphold the law to states' attorneys general, many of whom, she said, have extreme views on reproductive care and LGBTQ rights, at a time when many states are already seeking to block information about gender-affirming and reproductive health care. She said the bill puts the most vulnerable young people at a serious disadvantage, facing harassment and consistent targeting of their speech or the speech of people who might be resources or lifelines for them.
23:18
Cosa inserts itself into the parent-child relationship while ignoring minors' privacy, constitutional and human rights access to information, according to Cody Vensky, who is Senior Policy Counsel for Surveillance, privacy and Technology at the ACLU. Vensky said COSA has created a blunt technological veto over minors' right to learn, explore and seek. Advocates also have argued that age verification requirements in both bills would undermine adult and children's privacy. In a recent blog post, a CDT policy analyst wrote that because COSA proposes having online services limit by default minors' ability to communicate with other users, a provision that can't realistically be applied to adults it will be impossible to separate adults and children without asking for identification, which could include birth certificates or even facial scans. The large number of children's health organizations pushing COSA say years of failure by social media companies to protect children and adolescents from harmful effects is what prompted the bill's duty of care. The bill's provision for substantial parental controls will create a far safer digital environment, they say. Citing the 90,000 Instagram accounts promoting eating disorders, the Common Sense Media's Technology Policy Council said currently many platforms are sitting idly by, continuing to profit off a bubble like that. The council acknowledged that content filtering isn't perfect, but said COSA can be refined over time. In the meantime, she said under the new law, policymakers will learn more about how online providers' algorithms work, which they can leverage to better protect kids.
25:15
Meanwhile, over on the COPPA 2.0 side, many advocates worry the COPPA 2.0 bill would undermine privacy for substantially more people, because it will be less clear who is a child when data collection bans apply to users as old as 16.
25:34
Previously it was 13. As a result, age verification will be required from a larger number of people, they say With users under age 13,. Content filtering is easier to do, but 16-year-olds use most of the internet, making age verification much more sweeping and problematic. And finally, eric Null, who is co-director of the Privacy and Data Project at CDT, said, as with COSA, coppa 2.0's imposition of an implicit society-wide need for identification could quite possibly lead to the platforms requiring photos of all users' faces. The CDT blog said the bill is poorly designed, pointing to how the bill's quote verifiable parental consent mechanisms, unquote in some cases allow any adult to provide consent, which would make the law easy to circumvent and meaningless. Null said quote a big issue from our perspective is that when you raise the age limit, the number of websites that have to verify age of all their users skyrockets.
26:46
Okay that was long, but I think it was important to like lay out the fact that this is not going anywhere. The UK and the EU are certainly not alone in facing challenges created by the internet here in the US. As I said, what I shared what I just shared clarifies why we don't have legislation around this. It's not for any lack of recognition that problems exist. The problem is that there's zero consensus about what the problem is. Half of our legislators and action groups want to protect children from content they consider to be harmful, while the other half feels just as strongly that those same children need protected, private access to exactly that same controversial information for their benefit.
27:43
The way things are currently balanced in Congress, I don't think we need to worry about anything happening in the way of new legislation anytime soon. It should be clear to everyone why Congress is deadlocked over this legislation. As I noted earlier, suzanne's updated reporting suggests that the FTC may have broadly overreached and overstepped and that Metta, whose size certainly enables it to defend itself, may prevail in the FTC's attempts to rein in the various parties, including Metta's behavior, with lawsuits and stunning monetary fines. $200 billion is money worth fighting over.
28:29 - Leo Laporte (Host)
They're only worth $900 billion, so that's a quarter of their capex.
28:35 - Steve Gibson (Host)
It's crazy, it's crazy.
28:38 - Leo Laporte (Host)
Yes, I think the real issue is that it's a new medium and legislators or people in the EU are trying to regulate it like broadcasting. But it doesn't work that way. You're trying to attack it at the wrong end of the funnel, at the big fat end. Ultimately, it's got to be parents. They're the only people who can. Once it gets out of the house, there's nothing you can do. Trying to regulate the internet like television is nuts. It doesn't work.
29:12 - Steve Gibson (Host)
Well, the good news is, I completely agree. The good news is it's very clear this country today is not going to pass this legislation.
29:23 - Leo Laporte (Host)
It's sad when we have to rely on the dysfunction of our elected leaders to protect us. That's not ideal. Shall we say what happens if we get an effective Congress?
29:37 - Steve Gibson (Host)
Well, if we had that happen, then we have the problem of implementing the technology we own. You just can't do it. That's the problem.
29:45 - Leo Laporte (Host)
No.
29:47 - Steve Gibson (Host)
It's just not like Again. It just is in the UK and in the EU. If some law was passed that said you must verify the age of anyone 16 or younger, are you okay? How would you like us to do that?
30:04 - Leo Laporte (Host)
Yes, states have passed laws like that for pornography and Pornhub just pulled out and said look, anything that we could do to verify ages would be such an invasion of privacy that we're not willing to do it, and you probably wouldn't want us to do it. It's just. But legislators are. I don't think they're dumb, I think they're just angling for votes. This is a thing that can get votes. Protect the children always gets votes.
30:36 - Steve Gibson (Host)
I would argue, too, that they often aren't concerning themselves with the how of doing this. That's true, that's true, it's just like well, you geniuses in Silicon.
30:48 - Leo Laporte (Host)
Valley, you figure it out.
30:49 - Steve Gibson (Host)
You seem to be able to do anything, so just solve that problem.
30:53 - Leo Laporte (Host)
We can regulate TV, we can keep stuff that minors shouldn't see off television because it's a small group of people, and you can do that, but you just can't do it with either of them, or the time that it's broadcast during the day.
31:08
Once upon a time, you make laws and you can regulate that, but the internet isn't like that. They think Metta is like NBC. That's not how it works. They've just got to get some sense in their heads. But it's true. That means you can't protect children from stuff they're going to see online, so that's why, ultimately, the only people who can are parents.
31:40 - Steve Gibson (Host)
The recent developer blog discussing the release of Chrome 120 included a little blurb that reminded me that it's about to be 2024. The blog wrote and a reminder that Chrome is working toward deprecating third-party cookies in January meaning two weeks from now and experiment begins that could affect your website. So it's important that you check. And they provided a link to an article titled Preparing for the End of Third-Party Cookies for Auditing and Mitigating Steps. On that page they wrote if your site uses third-party cookies, it's time to take action. Actually, it would have been time a while ago, because you know two weeks. It's time to take action as we approach their deprecation. Chrome plans to disable third-party cookies for 1% of users starting in Q1 of 2024, to facilitate testing and then ramp up to 100% of users by the third quarter of 2024. The ramp up to 100% of users is subject to addressing any remaining competition concerns of the UK's Competition and Markets Authority, the CMA. Okay, so what Google is referring to here is that it appears that the UK's government competition and markets authority has expressed some concern on behalf of UK advertisers that they might be materially damaged by Google's removal of third-party tracking cookies from Chrome OG. So this appears to be, you know the sort of nonsense that any global technology behemoth such as Google just needs to put up with as part of doing business. Anyway, nothing will deter Google from doing this, and you know that's good news. Their posting continues.
33:51
Our goal with the Privacy Sandbox is to reduce cross-site tracking while still enabling the functionality that keeps online content and services freely accessible by everyone. Deprecating and removing third-party cookies encapsulates the challenge, as they enable critical functionality across sign-in, fraud protection, advertising and generally the ability to embed rich third-party content in your sites, but at the same time, they're also the key enablers of cross-site tracking. In our previous major milestone, we launched a range of APIs providing a privacy-focused alternative to today's status quo for use cases like identity, advertising and fraud detection. With alternatives in place, we can now move on to begin phasing out third-party cookies. Okay, so, as we know, google's replacement, which will allow advertisers to obtain some weak interest categories about visitors, is called Topics T-O-P-I-C-S. We've talked about it here several times and it's a terrific solution.
35:11
So 2024 will finally be the year when third-party cookie behavior is changed for the better. It won't be that a third-party site cannot still place a cookie into a user's browser. They can, but that same third-party site will not be able to retrieve that same cookie when that visitor is at any other site, and that's a huge change in behavior. Firefox led the way with this more than two years ago when, with Firefox 86 in February of 2021, they introduced Total Cookie Protection. But then it was present but not enabled by default. Two years later, in April of this year, it went live and was enabled by default, and the world as we know it did not end. Everything kept working. All that happened was the addition of cookie storage partitioning.
36:20
Historically, all web browsers maintained one single global cookie jar which held all the cookies being stored by the browser. This was the single fact which made tracking possible, since any advertiser offering content to multiple websites would receive their same tracking cookie, no matter where the user traveled. But with the adoption of Firefox's Total Cookie Protection, each website effectively gets its own private cookie jar which stores any cookies that anyone wants to set while the user is at that site. But once the user changes to any other site, that site's cookie jar then becomes current. So while advertisers are still welcome to set any cookies they want at every site, all cookie linkage between sites is then broken.
37:22
Google certainly already knows that catching up with Firefox in this regard won't end the internet. They understand that turning this on for 1% of users next month is going to be just fine. At the same time, there's no arguing that this really does represent a significant change to the way browsers have ever worked by default. Firefox did it a couple years ago. Since April has been on by default. Everything kept working. So it's reasonable, I think, for Chrome you know the elephant in the room browser-wise to be sticking a toe in the water, you know, at 1%, before jumping in headlong, which they're going to do by the time we get halfway through 2024. So, anyway, we know that change often needs to be forced. If anyone is still like holding on to some need for third-party cookies to be global across browsers, you know that's got to end. Chrome is saying hey, we're not kidding about this, this change is coming. You need to make sure that this isn't going to be breaking anything weird that you might be doing. So yay for that, and it's going to end up. You know, once Google has topics and third-party cookies are sequestered within their own individual cookie jars, chrome is going to then be able to continue blocking, tracking and stopping it wherever they can and, as we've also just seen with GPC and Do Not Track you know, the global privacy control and Do Not Track we're beginning to have legislation that's going to be enforcing this too. So I think it's in the not too distant future we are truly going to be seeing a different world, where browser-based tracking is no longer happening the way it has historically.
39:24
The last piece of news because there actually wasn't a lot that happened this week that I want to share before we get to my update on Spinrite and some feedback, is Cloud Flare's summary of interesting statistics which they gathered over the course of 2023. This is their fourth annual review of internet trends and patterns which they've observed throughout the year at both the global and also at the country and regional level. So probably the metric which most surprised me was that global internet traffic grew 25% in 2023. Wow, they noted. I know that's a shock. It is astonishing.
40:12
They noted that major holidays, severe weather and intentional shutdowns clearly impacted internet traffic. We'll talk about intentional shutdowns in a second. Remember all that dark fiber we once had during that initial internet overbuild. I would bet that there's far less excess today than there once was. But, leo, I agree with you. Think about that for a minute 25% growth in internet traffic in one year that is a massive increase in something that's already as mature as the internet. The only thing I could imagine that might account for that is the continuing increase in the use of streaming media for content delivery?
40:59 - Leo Laporte (Host)
Yes, of course.
41:00 - Steve Gibson (Host)
Yeah, you know, I had been a happy Tevo user for years, switching from analog Tevo to digital Tevo but remaining with traditional cable TV. But then for me, six years ago, when I was setting up my new home with Lori, I tried an experiment. We never asked Cox for cable TV, only internet service, and I've never looked back. And so, leo, that seems plausible to you too.
41:33 - Leo Laporte (Host)
The widespread access to broadband. I mean really fast broadband also probably encourages people to do things like stream more content. Right that they just weren't doing before I saw a stat I wonder if I can remember it that Netflix. How many petabytes of data Netflix sends over a month and it's many hundreds of petabytes.
41:58 - Steve Gibson (Host)
And I have a buddy whose father does nothing but sit on the couch with his phone in landscape orientation, watching Turner movie classics. That's how he spends his day. So people are watching movies on their phones now. That didn't used to happen.
42:19 - Leo Laporte (Host)
Yeah, exactly, and people have always watched TV all day, but now they're streaming and streaming a lot all day. So yeah, I guess that must be it right. Wow Netflix in 2019 took up 11% of the global downstream traffic on the internet, so I'm sure that's at least that much. And then add on top of that HBO Max, or just Max, I guess is called Disney Plus, all of this stuff. Yeah, I'm not surprised. I think it's got to be.
42:53 - Steve Gibson (Host)
I think you nailed it. Okay, not surprisingly, google was again the most popular internet service, but TikTok, which was the leader two years ago.
43:03 - Leo Laporte (Host)
We're watching more than one. We're watching more than one Two videos, yeah.
43:06 - Steve Gibson (Host)
Yep, yeah. So fourth place, the ranking among the top 10, from number one to number 10, is Google, facebook, apple, tiktok, microsoft, youtube, aws, instagram, amazon and iCloud. Thank you for watching. I have to say I'm a bit surprised that Apple's domain is in number three, position above TikTok in number four and YouTube in number six and Instagram in number eight. You know, like, what's Apple doing? Is it just Apple TV? I'm really surprised by the fact that-.
43:49 - Leo Laporte (Host)
No, because think about it, I mean all the downloads of apps. You know the App Store all comes from Apple. The music Apple's the number one streaming music service. All that music I mean Apple's doing a lot of streaming actually, if you think about it. And I guess when you buy a movie on iTunes, the stream comes from Apple too. So there you know. Yeah, I'm not surprised. Yeah. Wow.
44:18 - Steve Gibson (Host)
Wow. As we know, open AI was the most popular service in the emerging generative AI category and Binance remained the most popular cryptocurrency service. On the mobile front also no surprise over two-thirds of all mobile device traffic was consumed by Android devices, with Android commanding a greater than 90% share of mobile device traffic in over 25 countries and regions. So there were places where Android was two-thirds and iOS was one-third and there were countries where it was almost all Android. So I mean, like you know, bangladesh, for example, was, like you know, there was hardly any iOS activity there and in the skies above us, the global traffic from Starlink nearly tripled in 2023. After initiating service in Brazil in mid-2022. Starlink traffic from that country jumped by more than a factor of 17 in 2023. So I guess anywhere where you know your connectivity challenged and Starlink is offering service, you know you're going to see a big jump in Starlink traffic in that region. So again, starlink up by a factor of three.
45:47
On websites, google Analytics, react and HubSpot were among the most popular technologies and worldwide nearly half of web requests are now using HTTP slash two, with 20% using HTTP slash three and the balancing around 30% still back at slash one or 1.1. Nodejs was the most popular programming language used for making automated API requests by browsers to backend servers. Cloudflare noted that, as developers increasingly use automated API calls to power dynamic websites and applications, they're able to use their visibility, that is, cloudflare is able to use its visibility into web traffic, so they're able to see what's going on. You know, they're often serving as a proxy in front of web services, so they're able to identify the languages and the APIs that the clients are written in. So, beyond Nodejs, which holds the number one spot at 14.6%, the ranking and descending order behind Nodejs is go at 8.4%, java at 7%, python at 6.8% andNET at 4.3%. And during 2023, googlebot was responsible for the highest volume of request traffic to Cloudflare's hosted and their proxied sites. Not surprisingly, you know, google's busy sucking down web content in order to keep its indexes current.
47:36
As for internet connectivity and speed, cloudflare saw over 180 internet outages during globally during 2023, with many, they said, deliberately created by government directed regional and national shutdowns of their own internet connectivity. And we've you know, we've talked about this happening before where, for various reasons, like like on on voting day, various countries will say okay, pull the plug, we don't want anybody on the internet while we're doing whatever it is, we're doing so 180 times. So basically, what one every other day? On average, only one third of IPv6 capable requests worldwide were made over IPv6. So, even though IPv6 capable servers are still relatively rare among those services that do support IPv6, two thirds of the queries they received were to their IPv4 addresses not taking advantage of IPv6. And that's not really that surprising at this point. It's going to be a while the top 10 countries all had measured average download speeds above 200 megabits per second on average, that is, the average user among the top 10 countries had speeds over 200 megabits with, interestingly, iceland showing the best results across all four measured internet quality metrics. You ask why? Well, the reason for Iceland's outstanding performance is that over 85% of all internet connections there are over fiber, so they've got really you know, just a base of really good internet connectivity. In Iceland, over 40% of all global traffic is exchanged with mobile devices, 40% is now mobile and in more than 80 countries and regions the majority of all traffic is exchanged with mobile devices. And I guess that's no surprise, again, in countries that are, you know, basically just mobile users instead of desktop connectivity.
50:06
And finally, on the security front, just under 6% of global traffic was mitigated by Cloud Flare's systems as being potentially malicious or for customer defined reasons, so 6% of all global traffic was blocked. In the United States, 3.65% of traffic was mitigated, while in South Korea it was 8.36%. A third of global bot traffic comes from the United States and over 11% of global bot traffic comes from Amazon Web Services. And just to remind everybody, they don't mean bots as in malicious bots. Cloud Flare means anything that's automated. So any and all legitimate internet indexing bots would doubtless be a hefty part of that total of 11%. But on the malicious front, globally, finance was the most attacked industry, but the timing of spikes in mitigated traffic and the large and the target industries did vary widely throughout the year and around the world, so it's not only finance that is being attacked.
51:22
Even though the two year old log for J vulnerability remained a top target for attacks during 2023, the HTTP slash to rapid reset attacks, which we covered a few months back, emerged as a significant new vulnerability, beginning with a flurry of record breaking attacks and, as we know, they did cause a little bit of stumble on Cloud Flare's systems until they were able to update them in order to mitigate the attack and get this. 1.7% of TLS 1.3 traffic is already today using post quantum encryption, so we're beginning to get there. I know 1.7% won't get us there, but still, tls 1.3 does offer some of those protocols and they're beginning to get used in malicious email messages. Deceptive links, in other words phishing and extortion attempts, were the two most common types of threats people received. And finally, the good news is that GP is it PGP style inner? I mean GP why can't I say this BGP, whoo, bgp, yes.
52:50
Border Gateway protocol Everybody BGP style. Internet routing security measured as the share of valid routes improved globally during 2023. Significant improvement in routing security was observed in countries including Saudi Arabia, the UAE and Vietnam. So, stepping back overall, no big surprises and overall, when viewed from 20,000 feet, the internet remains largely stable. It's cool to see the emergence of some post quantum crypto protocol usage and I'm still surprised that there could be year over year growth of 25% in overall traffic. That's just, that's a that's a big bump.
53:37
Okay, the announcement I expected two weeks ago to be able to make last week which, leo, you noted I missed as a, as it was Don Adams on get smart who used to say missed it by that much the announcement was that I finally accomplished the surprisingly challenging task of on the fly remote server side EV code signing using a hardware security module. It's a capability I've wanted to have for years and, although it took far more time than I expected, since every aspect of the project fought back, that technology is now exists, is now in place and it appears to be working reliably. I brought it online last Saturday morning for cautious testing by the gang in GRC's development news group and I checked an hour ago, more than 165 instances of spin rights current release candidate number five were successfully built on the fly, signed, downloaded and tested. I decided to obtain a fresh three year, which is the maximum you can get an EV code signing certificate from Digi-Cert for the HSM, since the one I had was a year old and I wanted to get as long a run from the appearance of this new certificate as possible. As we know, reputation is now the way the world works. Not surprisingly, a few people reported that Windows Defender was upset, quarantined and deleted their download. But most people said that Defender didn't make a peep and that everything worked for them without a hitch.
55:37
My hope is that by the time Spinrite 6.1 is being heavily downloaded, microsoft will have had time to decide that all is well with it. I just grabbed a fresh copy and dropped it on virus total. It triggered zero out of 68 tests. Not one AV engine had any problem with it, but during my testing I tried that with unsigned code and at least one third of them freaked out. So I conclude that this was time well spent to get this thing signed on the fly.
56:12
Where I am today is that Spinrite is all but finished. I'm actually a bit happy that the code signing project took four weeks because during that time many more people have had the chance to use the current release candidate. This has surfaced some remaining edge cases not really in Spinrite. Well, I'll give you an example. I would like to resolve those before I formally declare Spinrite 6.1 finished. I could ship it now, but on really troubled drives we've seen that it can still stumble a bit and since really troubled drives is definitely one of Spinrite's targets, I want to at least know that there's nothing more that can be done.
57:02
For example, there have been some reports of very troubled drives dropping offline when Spinrite touches a particularly sensitive spot on the drive. This is something we encounter many times during our early testing. Spinrite pops up a scary red dialogue to explain that after being reset, the drive never reported that it was ready for more. Spinrite waits for up to 10 seconds, while checking the drive's status every 10 milliseconds before it makes that determination. If you watch the seconds tick by on a clock, 10 seconds is a long time, but over this past weekend I verified that for really troubled drives, 10 seconds might not be long enough. In this instance, spinrite needs to be even more patient. So, starting with the next release, spinrite will give drives a full 60 seconds to get themselves back up and ready to proceed. And since Spinrite's user may wonder what's going on while nothing appears to be happening, after waiting a few seconds Spinrite will display a waiting for drive and then a countdown so that its users know why nothing appears to be happening.
58:24
Anyway, so it's those sorts of things Really. I mean really just the last little bits. But since we're so close to the end of 23, and I'd like any recent improvements to have a bit of time for testing, I figure I'll fuss with Spinrite for the rest of the year and make it available at the start of 2024. I recognize that even after its official release I may still be tempted to deal with even edgier edge cases and, frankly, any improvements I'm making at this point all feed forward into Spinrite 7's design anyway. So it'll be time well invested. I have the feeling that I may be continuing to nudge it along for a while, but also in this day and age it's very easy for any Spinrite owner to update themselves and get the latest and greatest, and of course I'll let everybody know here when that happens. So at the moment, there's no reason for me to improve, for me to not to improve what I can, and it'll be an early 24 release. Perfect, and that's not very far from now.
59:31
That's just a week or so it's two weeks and that'll give me some time to add those little finishing bits of polish.
59:37 - Leo Laporte (Host)
Me too. It'll give me time to answer day five of the advent of code.
59:42 - Steve Gibson (Host)
That's right.
59:45 - Leo Laporte (Host)
Well, it all comes down to Alan's interval algebra. Actually, steve, you would have understood it immediately, but it was a little beyond my tiny brain. We have some very good programmers and there's an advent of code section in our club and I don't know, there may be a dozen people solving it in the club, which is kind of cool, because then you can say, hey, what the heck's going on here? And people are really, people are really great, it's really, it's a lot of fun. So that is neat.
01:00:16
Yeah yeah, If you're not a member of Club Twit, that's just one of the many benefits. It's a group of people who share your interests, right? Besides, just Twitch shows all things kind of geeky. Club Twit, of course, is how we're monetizing going forward. We have a very limited amount of money coming to us from advertisers these days, not enough to maintain, frankly, the operation period. So that's fine. You know, that's the way it is in podcasting in general. We set up and it's kind of my fault because I set up an enterprise that was really designed like an old, speaking of old time TV, an old school TV or you know kind of small local market TV station, which means our overhead for staff alone is over a million dollars, and then there's the lights and the cameras. So, as we kind of right size all of that, we also need to increase income from all of you. Right now, about 1% of you are members of Club Twit. That's not enough to sustain us. We'd like to get it to 5% or 10%. That'd be 35 or 70,000 people. Right now we're 9,459, which is a big jump. By the way, Thank you to all of the new users, new listeners on Club Twit. I appreciate that.
01:01:36
Here's what it costs $7 a month, $84 a year. You can also subscribe family plans and corporate plans. We have different plans for that. We use a system through Patreon called Memberful that does the billing with Stripe and all that. So don't ask us to change some of that, because we're kind of. You know we couldn't set up a membership club and do all of this, so we're using an existing one, but it works really well. Now we skip the price low because we want to make sure it was affordable. You get ad-free versions of all the shows. You get additional shows that are club-only, including our entitled Linux show and iOS today's moving into the club, things like that. You also get the Discord where you can hang out with wonderful people like John Arnold, who will help you with your day five coding and the advent of code, or talk about cars or anime or comic books or whatever you're interested in.
01:02:30
If you are interested in keeping us going, you know Steve's already said and I'm so grateful to him that he's going to keep going past 2024. We'd like to keep going past 2024 because I think, Steve, we were talking about this before the show we're about we're. For a long time tech had been stagnating a little bit, but we are in a new age of growth and expansion, particularly with AI, and there's going to be lots to talk about. Ai is going to affect security. It's going to affect everything we do. So we want to be there for you to help you understand it, help you navigate it, help you use it to your benefit, and that's that's our mission. So we'd like to keep going.
01:03:14
Twittertv slash club Twitter. If you want to help, I should have made that, just said that, and we would have been fine. Twittertv slash club Twitter. Our show. We do have, by the way, wonderful sponsors and I don't want to knock our sponsors. They do a great job. It's not their fault, it's really it's mostly my fault for designing a TV station instead of a podcast operation. Our show today, brought to you by Drata. The Drata companies can complete audits, they can monitor controls, they can expand security assurance efforts to scale. With a suite of more than 75 integrations, Drata streamlines your compliance frameworks, providing 24 hour continuous control monitoring so you can focus on scaling securely without worrying about the compliance Drata easily integrates through applications such as AWS, azure, github, okta, cloudflare.
01:04:06
Drata's automated dynamic policy templates support companies new to compliance using integrated security awareness training programs and automated reminders to ensure smooth employee onboarding. And as the only player in the industry building on a private database architecture, drata ensures your data can never be accessed by anyone outside your organization, and that's good for peace of mind, I think. All Drata customers receive a team of compliance experts, including a designated customer success manager with pre-audit calls available to prepare you for when your audits begin. Drata's audit hub is a solution to faster, more efficient audits. You'll save hours of back and forth communication, never misplace crucial evidence. You can share documentation instantly. It transforms the experience. Frankly, say goodbye to manual evidence collection. Say hello to automated compliance when you visit dratacom. Slash twit Drata. Bringing automation to compliance at Drata speed. We thank them so much for supporting the good works Steve is doing here at security so we have some good feedback, as always, from our listeners.
01:05:25 - Steve Gibson (Host)
Someone who asked for anonymity said I'm not going to pretend to understand the details of this, but at SGGRC and other authorities have deemed this a major step forward in quantum computing, and apparently he aimed this at Bitcoin Core Org. This was a public tweet, so he asked Bitcoin Core Org what is the plan for post-quantum implementation. Current ASIM crypto is threatened, so this listener was clearly referring to last week's quantum computing breakthrough topic and he's correct that asymmetric crypto using the algorithms in use today will not be in use in the future. The good news is that things like iterative PBKDF hashing of passwords to obtain a fixed size token are not asymmetric, so they will remain safe. I'm mentioning this first because it's something just by itself that's important to appreciate. The world's password accepting websites will not all need to revamp their password hashing systems, but also and blessedly, neither will the operation of the Bitcoin blockchain need to be changed. Recall that the way Bitcoins are earned is by guessing what needs to be appended to the most recent blockchain update in order to yield a hash result that ends in some number of trailing zeros, while GPUs have proven to be quite facile at performing the hash function needed to guess that at very high rates, choosing a random value and hashing. The result is not something that is suited to tomorrow's quantum computers, and thank goodness for the fact that symmetric crypto will not be affected by quantum computing, because otherwise we would be in much more serious trouble than we are now. And you know, as it is, we've got to abandon all of our asymmetric crypto. We have time to do that, but we really do have to get it done. Still, underlying all of that is symmetric crypto and, as I said, it does not need to be changed. It gets to stand unmodified.
01:08:05
Philip Griffiths tweeted hey, steve, in 952, you mentioned zero tier and tail scale as open source. Well, sort of, is my opinion. Zero tier is BSL, so open source to many, but not everyone. Tail scale is largely open source, but core parts, for example the coordination server or not, net bird or head scale, would be better examples of overlays which are open source software and allow circumvention of NAT. You could also include open ZD, though you could also argue, while it can be better used as a VPN, its true design goal is to make it easier to build secure, by default distributed apps. Okay, so, although he's right, much of tail scale is open source. Tail scale have retained some pieces. The GUI clients for Windows, mac OS and iOS are not open and that rendezvous server, the so-called coordination or control server. So head scale, which he mentioned, implements a self hosted, fully open source alternative to tail scales control server. Head scales goal is to provide self hosters and hobbyists with an open source server they can use for their projects and labs. It implements a narrow scope, essentially a small tail scale overlay network suitable for personal use or small open source organizations. Net bird looks like another interesting, fully open source overlay network which does also use wire guard for its transport, security and encryption. Open ZD isn't is not a general purpose overlay network. It's a system of technology, language, apis and SDKs that allow developers to incorporate secure overlay network technology into their apps. So it's a completely different bear than tail scale, zero tier or net bird.
01:10:23
Now, as for how those three compare, I'm unable to offer any comparison or recommendation from experience. I haven't yet had the need to deploy any of them, so I haven't given them a close look, but when I do I will definitely share a full review of what I find. Comtech engineer said a question. He said a quick question on spin right. Do the hardware specs better CPU or more RAM of the PC running spin right affect the speed of spin rights operations? I've seen this question several times before so I thought I'd answer it for everyone. The answer is almost always no. The hardware does not matter. It's been right will detect and alert its user when a SATA three, which is kind of as capable of it, has an interface rate of six gigabits per second, when a SATA three drive is connected to a SATA two interface which is only capable of running at three gigabits per second. However, even though three gigabits per second is sufficient for any spinning drive, there are some solid state drives which can benefit from SATA three speeds. So the idea there and it actually had happened to a number of our testers who were caught off guard. They did not realize they had a SATA three drive plugged into a SATA two interface. So spin right pointed that out for them and they were able to move them over to SATA three interfaces and increase their performance.
01:12:01
As for CPU and RAM, spin right six one does use about 50 megabytes of RAM, but it's rare to find a machine today that has fewer than four gigabytes, and even one gigabyte would be fine, not one, as far as I know, of our more than 800 testers have encountered anywhere in their testing a machine with insufficient RAM for spin right six one. So I just don't think that's going to be a problem, and the same is true for the CPU under six one it's. You know. What that means essentially is that almost any older hand me down PC can be used as a dedicated spin right test machine, and many of spin rights owners do just that, even though six one is way faster than 6.0. It is now, you know, and six one is able to run a directly connected drive as fast as that drive is capable of going. Drives have become ridiculously huge and it does still take time to move all that data back and forth. If you've ever tried to do an actual physical format on a drive today, as opposed to a quick format, you quickly learned that that's not something you want to do, at least not often Anyway. So almost certainly the speed of the system and the amount of RAM it has doesn't matter. I should mention there was one instance where somebody was considering purchasing a machine and was wondering about spin right. 7.0 will be more aggressive. Among other things, it'll be fully multitasking, meaning you'll be able to run it on all the drives you have in the system at once, and the technology it's going to be using for spotting slow spots is going to be much more CPU intensive. So there I. The answer will probably differ, but not for six one that we have today.
01:14:12
Another listener said I'm listening now to SN950 and wanted to share my experience with trying pass keys on GitHub. Before pass keys I had username, password and multi factor authentication, and by that he may he means an, you know, an external authenticator app. He said. After enabling pass keys and using them as the authentication method, github no longer prompts for another factor. So it seems the security of multi factor authentication has disappeared. He said I store my MFA seeds outside my password manager. If, however, I were to store my pass keys within my password manager, I would then reduce my security for any site that skips MFA when using pass keys.
01:15:13
I understand he said the pass keys are better than passwords, as the site no longer has a secret to protect, but all the necessary eggs would still be in my password manager's basket. I think pass key plus MFA would provide the highest level of security, but I don't know which sites will allow or offer that option and which will drop multi factor authentication while using pass key authentication. Under the assumption that multiple factors are now are no longer necessary, as GitHub appears to assume For those with the strictest threat model, I think I would not recommend storing pass keys in the same password manager as everything else. Am I missing something here? Also, I never use Twitter myself, so I'd be one of those looking forward to your new email lists. I had to dust off my login from years ago just to write this to you.
01:16:15
Okay, so, like this listener, I'm a bit distressed to learn that the use of pass keys automatically disables the use of additional authentication factors, especially for a site such as GitHub, where improving authentication integrity has been a recent need and issue. As we know, pass keys are stronger than usernames and passwords for a number of reasons, but this listeners correct about the vulnerability of in. You know the vulnerability inherent in allowing any single device to have authority to authenticate us, no matter how strong its authentication mechanism might be. The right solution would be to offer users who are adopting pass keys the option to disable their additional authentication factors in favor of pass keys, since pass keys are certainly stronger than passwords alone, or to keep additional authentication factors in place and enabled under the more proper understanding that any single factor of authentication, regardless of how strong it may be by itself, can still be made more strong by the requirement for an additional factor, especially one that relies upon another device and uses an entirely different technology, such as time varying six digit tokens.
01:17:45
Skynet said Hi, steve, regarding SN 952 and upstream library dependencies. What is this notion that developers have that fixing a bug will automatically introduce something new that will break? How is it not possible to fix a flaw without introducing a new feature that will break something else? It seems that everyone, including Microsoft, cannot fix a flaw or vulnerability without breaking something else. Why are they so connected and how? How is it that a bug or flaw that needs to be fixed will just automatically break something totally different, totally unrelated to the bug? I know it is most certainly possible for companies to fix flaws without breaking something new in their products, so I find it a poor excuse for developers to claim that quote it's all working right, so I don't want to rock the boat and possibly break something else.
01:18:50
To me he writes that just screams that either. Everything in their code is connected. That's bad, or they're bad coders. Okay, so last week's discussion more specifically related to a fear of updating upstream library dependencies, which are inherently black boxes, in a situation where the successful functioning of a coder's own code is entirely dependent upon the exact behavior of those black boxes. The point being, everything is working now. Let's not rock the boat. In highly complex projects. Mistakes do happen.
01:19:40
Say that a group of people decide to entirely recode some library because its code base has grown old and creaky over years of tweaking. That does happen, and recoding can be a really good thing to do. But try as they might, it could be that this new code, which is intended to behave just the same as the original code did, nevertheless exhibits some slightly different behavior around the edges, and that this change, even if it's subtle, might cause some other code that uses the newly recoded library to break. Yes, it's a mess, but it's a mess we've created, and the motivations behind the don't fix it if it's not broken is, you know, I think, understandable. As a programmer, I understand it and I am, I guess I'm somewhat surprised and thankful that Microsoft has somehow managed to keep really old programs that were running on very different operating systems still running reliably today. It really is an achievement on their part.
01:21:04
Blaine Tramel wrote I just listened to the security now podcast and want to pass on that chromium browser does not use OS root store anymore by default, and he provided a link. Okay, so Blaine's Twitter DM included a link to Google's announcement about three months ago on the, which was made on September 19th under the headline announcing the launch of the Chrome root program, and there Google wrote in 2020, we announced that we were in the early phases of establishing the Chrome root program and launching the Chrome Chrome root store. The Chrome root program ultimately determines which websites are trusted by default in Chrome and enables more consistent and reliable website certificate validation across platforms. This post shares an update on our progress and how these changes help us to better protect Chrome's users. Since we all know most of this, I'm not going to share it all, but I will. They make a couple points that are salient. They said Chrome uses digital certificates, often referred to as certificates, https certificates or server authentication certificates, to ensure the connections it makes on behalf of its users are secure and private.
01:22:28
Certificates are responsible for binding a domain name to a public key, which Chrome uses to encrypt data sent to and from the corresponding website. As part of establishing a secure connection to a website, chrome verifies that a recognized entity, known as a certificate authority, issued its certificate. Certificates issued by a CA not recognized by Chrome or a user's local settings can cause users to see warnings and error pages. Root stores, sometimes called trust stores, tell operating systems and applications that certificate what certificate authorities to trust. The Chrome root store contains the set of roots CA certificates Chrome trusts by default. A root program is a governance structure that establishes the requirements and security review functions needed to manage the corresponding root store. Members of the Chrome security team are responsible for the Chrome root program. Our program policy, which establishes the minimum requirements for CA's to be included in the Chrome root store, is publicly available.
01:23:48
Historically, chrome integrated with the root store and certificate verification process provided by the platform on which it was running. Standardizing the set of CA's trusted by Chrome across platforms through the transition to the Chrome root store, coupled with a consistent certificate verification experience through the use of the Chrome certificate verifier, will result in more consistent user and developer experiences. What they're seeing here is they used to just use the store that the OS provided, but because those could vary from OS to OS, that meant the Chrome's behavior varied from OS to OS. They decided to change that. They decided to two years ago actually three in 2020, to work on incorporating the root store into Chrome and no longer use the underlying OS. So they finished.
01:24:58
Launching the Chrome root program also represents our ongoing commitment to participating in and improving the web PKI ecosystem. Innovations like ACME have made it easier than ever for website owners to obtain HTTPS certificates. Technologies like certificate transparency promote increased accountability and transparency, further improving security for Chrome's users. These enhancements are only made possible through community collaboration to make the web a safer place. However, there's still more work to be done. We want to work alongside certificate authority owners to define and operationalize the next generation of the web PKI. Our vision for the future includes modern, reliable, highly agile, purpose driven PKIs that promote automation, simplicity and security, and we formed the root program and corresponding policy to achieve these goals. So again, that was in 2020.
01:26:06
90 days ago, they announced this went live. So Thank you, blaine, for this. I had announced Google's announcement that this initiative was ready and was now being rolled out. This, of course, means now that both Google and well, google with Chrome, all the various Chromium browsers and Firefox will be running with their own local root stores and given that, as we've seen, just six or seven certificate authority root certificates are all that most users will ever need, that doesn't seem like such a big deal. But all of this is relevant, of course, because the EU's Article 45, which brings into question what is going to happen in 2024? I have a feeling, whatever it is, it'll be next year that we see something happening, so it's going to be extremely interesting. Okay, and finally, active listening. A story blew up in the news last week that currently lacks solid evidence. Well, okay, solid evidence only in as much as it's so bad that it's hard to believe it's true.
01:27:36 - Leo Laporte (Host)
It could very well be that Cox Media Group is overselling their capabilities.
01:27:43 - Steve Gibson (Host)
Right, at least I hope so.
01:27:45
On the other hand, we have documentary evidence from, thanks to the Web Archive. Anyway, whether or not it's true, it is certainly worried and upset everyone who has heard it and, Leo, I know you talked about it on Twitter on Sunday. You know definitely an important topic. I suspect that this is the sort of thing that investigative reporters will be digging into further. The short version of the news is that the massive media giant CMG, which is the Cox Media Group, claims in its marketing materials to advertisers and in actual discussions with prospective clients that it currently has and is using the capability which their marketing materials term active listening to listen into the ambient conversations of consumers through microphones embedded in their smartphones, smart TVs and other similar devices, and that through this means, they're able to gather data which they then use to target advertising. Last Thursday's headline in 404. I need to stop every time to take a drink, Leo. Take a drink. I didn't do an ad for you.
01:29:14 - Leo Laporte (Host)
Take a drink. Pause for a little bit.
01:29:16 - Steve Gibson (Host)
Last Thursday's headline in 404 media, which broke the story, was titled Marketing Company claims that it is that it actually is listening to your phone and smart speakers to target ads. 404 media wrote. The news signals what a huge swath of the public has believed for years that smartphones are listening to people in order to deliver ads may finally be a reality in certain situations. Until now, there was no evidence that such a capability actually existed, but it's myth permeated due to how sophisticated other ad tracking methods have become. Okay, so exactly three weeks ago, on November 28th, the CMG website posted a blog page titled active listening colon and overview. They also had a permanent page linked off their domains route with the URL blah, blah, blah domain forward slash CMG active hyphen listening. So at that time, three weeks ago, it was all right out there for the world to see, and this is not some fly by night sketchy operation. This is the Cox media group. To no one's surprise, all of those pages have since disappeared, though it's really worth noting that they were initially completely public and no one at Cox thought that they, nor their active listening, was a problem. Fortunately, those pages were up long enough to have been crawled by the internet's historian, the Web Archive. In this week's shortcut of the week, grcsc forward slash 953 will take you and your browser directly to a faithful copy of the archived blog posting which was made three weeks ago.
01:31:41
So what do we learn directly from this once publicly posted page? It does not disappoint. The page shows a photo of four young hip consumers in their late twenties or early thirties gathered around a table, smiling and chatting with a Mac and a tablet, and the page says imagine a world where you can read minds, one where you know the second someone in your area is concerned about mold in their closet, where you have access to a list of leads who are unhappy with their current contractor or know who is struggling to pick the perfect fine dining restaurant to propose to their discerning future fiance. This is a world where no pre-purchase murmurs go unanalyzed and the whispers of consumers become a tool for you to target, retarget and conquer your local market. It's not a far off fantasy. It's active listening technology and it enables you to unlock unmatched advertising efficiency today, so you can boast a bigger bottom line tomorrow. Do we need a bigger vehicle? I feel that my lawyer is screwing me. It's time for us to get serious about buying a house, no matter what they're saying. Now you can know and act. A marketing technique fit for the future.
01:33:28
Available today, machine learning algorithms are improving and introducing a new era for advertising. Our active listening tech gives you a weekly roster of qualified customers who have voiced their need for your service or product. We will then upload the list to your preferred advertising platforms so you can target ads to the right people at the right time. Reactive advertising is no longer enough to get ahead. The embracing predictive and proactive strategies is the key to growth. Active listening gives organizations clarity into the most effective channels and timing for their advertising efforts. By incorporating and analyzing customer data gleaned from conversations happening around smart devices, we can pinpoint where and when customers are most likely to engage with ads. When you have this information in reach, you have the power to deploy targeted campaigns at opportune moments on the platforms where your audience spends their time. The results Maximized visibility and impact. Whether you're a scrappy startup or a Fortune 500, active listening makes the unreachable in reach.
01:35:02
How does it all work? Advertise to the exact people who need your services. Cmg can customize your campaign to listen for any keywords or targets relevant to your business. Here's how we do it. Create personas Reflesh out comprehensive buyer personas by uploading past client data into the platform. Identify keywords we identify top performing keywords relative to the type of customers you are looking for. Transparent tracking we set up tracking via pixels placed on your site so we can track your ROI in real time.
01:35:44
Leverage AI let's us know when and what to tune into. Our technology detects relevant conversations via smartphones, smart TVs and other devices. Analyze consumer behavior as qualified consumers are detected, a 360 analysis via AI on past behaviors of each potential customer occurs. Create a list with the audience information gathered and encrypted. Evergreen audience list is created. Target, retarget and transcend we use the list to target your advertising via many different platforms and tactics, including streaming TV, OTT streaming audio, display ads, paid social media, youtube and Google and Bing search.
01:36:39
Don't leave money on the table. Bring your territory Our technology provides a process that makes it possible to know exactly when someone is in the market for your services in real time, giving you significant advantage over your competitors. Darra territories will be available in 10 or 20 mile radiuses, but customizations can be made for regional, state and national coverage. And then there's a link with the phrase claim your territory now, then they provide a handy FAQ where the first question they ask themselves is is active listening legal? To which they reply we know what you're thinking Is this even legal? The short answer is yes. It is legal for phones and devices to listen to you.
01:37:41
When a new app download or update prompts consumers with a multi-page terms of use agreement, somewhere in the fine print, active listening is often included. So why exactly, then? Has CMG website been totally scrubbed of all mention of active listening? Perhaps strict legality is not the problem here? The next question they ask themselves how does active listening technology work? And they answer our technology is on the cutting edge of voice data processing. We can identify buyers based on casual conversations in real time. It may seem like black magic, but it's not. It's AI. The growing ability to access microphone data on devices like smartphones and tablets enables our technology partner to aggregate and analyze voice data during pre-purchase conversations. The result advertising efficiency and timing taken to a new level. We set specific keywords relative to your product and service, so we know who needs you, why they do and where we can target them. With this unprecedented understanding of consumer behavior, we can deliver personalized ads that make your target audience think, wow, they must be a mind reader and that's not creepy at all. 404 Media, the organization that spotted this and broke the story, also found a representative of the company CMG on LinkedIn who was explicitly asking interested parties to contact them about the product. One marketing professional pitched by CMG on the tech said a CMG representative explained the prices of the service to them. So it certainly appears to have been available.
01:40:07
Cmg's website says what would it mean for your business if you could target potential clients who are actively discussing their need for your services in their day to day conversations? No, it's not A black mirror episode, it's voice data and CMG has the capabilities to use it to your business advantage. The part of CMG advertising the capability is CMG local solutions. Cmg itself is owned by Apollo Global Management, a hedge fund, and Cox Enterprises, which includes everyone's favorite residential cable provider, the ISP Cox Communications. Cmg operates a wide array of local news, television and radio stations. So wow, I mean everybody gets this right. They talk about overseeing. On this page.
01:41:09
They say imagine this what could it do for your business if you were able to target potential clients or customers who are using terms like this in their day to day conversations and they give six examples. The car lease ends in a month. We need a plan, or overheard. A minivan would be perfect for us, or do I see mold on the ceiling. Or we need to get serious about planning for retirement. Or this AC is on its last leg, or we need a better mortgage rate. So, according to CMG's now removed web pages, the way this works is that clients can claim a territory where they want to use CMG's services, which are available in a 10 or 20 mile radius After being set up. Quote. Active listening begins and is analyzed via AI to detect pertinent conversations via smartphones, smart TVs and other devices. Unquote. Cmg also claims it installs a tracking pixel on its clients website to monitor the return on investment. With an audience created, cmg then delivers advertisements to these people through streaming TV, audio, display ads, youtube and search.
01:42:38
The marketing professional who was pitched by CMG told 404 media that, after a call with the company, they disabled microphone access on much of their own technology. The guy was quoted saying quote I immediately removed all my Amazon Echo devices and locked down microphone permissions on things like my phone Seving. Confirmation that they are doing things like this have confirmed my worst fears and I for one will take no part in it. Unquote. For its part, while CMG was busily removing all traces of this from their website, they told 404 media the following. They said CMG local solutions markets a wide range of advertising tools like other advertising companies.
01:43:35
Some of those tools include third party vendor products powered by data sets sourced from users by various social media and other applications, then packaged and resold to data servicers. Advertising data based on voice and other data is collected by these platforms and devices under the terms and conditions provided by those apps and accepted by their users, and can then be sold to third party companies and converted into anonymized information for advertisers. This anonymized data is then resold by numerous advertising companies. Cmg businesses do not listen to any conversations or have access to anything beyond a third party aggregated, anonymized and fully encrypted data set that can then be used for ad placement. We regret any confusion and we are committed to ensuring our marketing is clear and transparent. Unquote.
01:44:38
Okay, now here's something to think about. Why is Cox doing this? They would not seem to be an obvious entity to create such a service. If, as they claim, all of the data is being aggregated by third parties and they're just the middlemen, you know, who are not doing any direct data gathering themselves, then there's nothing Cox is bringing to the table. Any random organization could do the same thing, but they certainly do appear to have been all gung-ho into it when they were public about it. If I were a betting man, I'd put my money on this being an adjunct to all of the massive amount of data that Cox communications the Internet ISP is almost certainly already obtaining, from monitoring all of their Internet consumers, available Internet traffic, meaning all DNS query and TLS handshake metadata.
01:45:42
Cox, like any ISP, is sitting on a treasure trove of extremely valuable personal data. Everywhere everyone in everyone's family goes on the Internet is available to an ISP, unless consumers take extreme measures to prevent it from happening and, as we know, almost no one does and Cox consumers are not anonymous to Cox. Cox knows exactly who and where every household is. They pay their bill every month. And now we know something we didn't directly know before. Now we know who Cox is and what they're really thinking. They're quite willing to hide in the fine print of, in their words, multi-page terms of use agreements.
01:46:43
I'd be much less worried about microphones, which, at least for our very secure smartphones, seems like a red herring, then, about the fact that an organization such as Cox has just shown itself to be is the conduit through which all of its subscribers residential Internet traffic flows. I think the time has come to think seriously about bringing up encrypted DNS for residential Internet users. We do not know for sure whether active listening applies to audio or where it applies, but given what we've seen, it seems very unlikely that Cox and his ISP ilk are leaving any money on the table by not actively listening to everything they are able to obtain by monitoring all of their subscribers use of the Internet through our PCs, our smartphones and any other user directed Internet devices. In the evidence it seems clear that if they get it, and if they can get it, they will sell it and use it. As a result of what was found on Cox's website, the threat of that sort of monitoring being done by a major residential ISP just became far less theoretical and far more likely.
01:48:21
Now, at this point, I'm sure many of our listeners are thinking that seems like a good idea. How do we go about making that happen, which I think will be a great topic for us to look at closely in 2024, which, after all, is only a few weeks away and speaking of which, I want to personally wish and I know Leo and all of the Twitter network joins me in wishing all of our listeners a happy and safe holiday season. For sure we will do that in 2024 promises to be at least as interesting as recent years, and we'll be right here to watch and examine all of it as those events unfold you bet, see you then yeah.
01:49:00 - Leo Laporte (Host)
You know, I think there's a mixture of CMG overselling their capabilities because you know, honestly, if Amazon's Echo, for example, were sending that data back, we would know the processor on it is not sufficient to do that kind of AI extraction. They would have to send the content back and you'd see a huge amount of traffic coming out of that thing and we just don't see that traffic. Same thing with your iPhone and most hardware microphones. There is a light that comes on it's a little orange dot, and you know when that mic is listening, right? Yeah, I mean, I guess Apple could be lying to us.
01:49:38 - Steve Gibson (Host)
Well, or users are not. They don't know what the little dot is.
01:49:43 - Leo Laporte (Host)
Yeah, but you and I know, and we don't see that dot coming on at random. In fact, if it comes on, that's a cause for concern. We go, okay, something's listening, right. But I would also point out, you're already giving them all that information. How good is the signal? If I talk to my wife, I think my lease is running out. What should I do versus me going online and searching for new cars? Exactly, they're getting much better signals all the time from your TikTok usage, from your Facebook usage from your web surfing and if you're rapsole-y right, cox sees all of that.
01:50:16
So I think that this is you know, oh, marketers would never lie right. I think this is marketers overhyping their capabilities, perhaps out of ignorance. What's sad is I think a lot of people are going to throw out their Amazon Echoes, even if they find them useful, because they're worried about that, and I don't think there's any evidence that Echoes or Google, you know hubs listen. We would know if they did right. Yep, we would know. If your phone is listening Now, your car probably is listening, your smart TV probably is listening. There are some of the things they mention in here that are certainly yeah.
01:50:53 - Steve Gibson (Host)
I do. I absolutely agree with you. We know much less about some generic smart TV and what it might be doing.
01:51:00 - Leo Laporte (Host)
Yeah, I mean there's no reason Samsung put a camera and a microphone on my TV. I mean they may say, oh, so you can zoom. No, that's not. I know exactly why you guys put a camera and microphone on my TV. So certainly that's a reasonable thing to be concerned about. But I think there's also I hope people don't set their hair on fire on this. You can punish Cox all you want, but you know you use Cox. My mom uses Cox. It's not like you have a choice in most markets.
01:51:32 - Steve Gibson (Host)
No choice at all. There's only one broadband provider in our market.
01:51:36 - Leo Laporte (Host)
See, cutting off your nose despite your face. It just doesn't make sense. I think they oversold the capabilities. But you're already given them all that information all the time. I mean you really are, so you know. There's no secrets when you start searching for mold abatement on the internet. They know what's going on Right?
01:52:01
Yeah, exactly Really good stuff, though, and I'm really glad you brought it up and found the details and everything, because it is a topic that we will undoubtedly be covering more in the future, and the use of AI in it is non-trivial. Ai makes it see. The reason it wasn't such a thing to worry about before is because there was such a volume of stuff. Wait a minute. You're listening to everything I say every day all the time. No one can listen to all that AI, no.
01:52:28 - Steve Gibson (Host)
In fact we know that the processor in the Echo it's listening for its trigger word. We barely do that. Which then yeah, exactly which then wakes it up and it streams the audio for analysis during, you know, while it's awake.
01:52:45 - Leo Laporte (Host)
People are right to be concerned about privacy. The other thing to watch with interest is who's going to write the letter. Is it going to be Ron Wyden to Cox sing? I know what is this, but remember, if such capabilities exist, you know, the number one customer would be government law enforcement, and that's something really to be concerned about. I don't care if some car dealer contacts me because I need my leases running out. I'm sure Ford's already sold that information to every car dealer in town.
01:53:18
I am very concerned if the government thinks I'm an agitator and decides to you know, listen to everything I'm doing. That's something really much more serious. You know, I'm interested to see what government's response to this is. I expect a lot of Saber rattling and absolutely no action, because they use these tools. They don't want data brokers to go away, they're buying the information. Yep, we do this show. Well, we won't be doing it next week. We're going to have a best of episode which is awesome on December. What is that? 26th day after Christmas, and then we will be back though January 2nd. I hope you're ready 2024 is here.
01:54:00 - Steve Gibson (Host)
Oh yeah, my days of over imbibing are long since past. Me too.
01:54:06 - Leo Laporte (Host)
Yeah, I'll be just fine New Year's morning, if you want to do a show.
01:54:10 - Steve Gibson (Host)
I'll be asleep hours before the ball drops.
01:54:12 - Leo Laporte (Host)
Yeah, stay up to midnight. What are you crazy? Anyway, you youngins, you go ahead and do that. Steve and I will be in bed nice and early, and then we'll be back January 2nd for a show. We do the show every Tuesday right after Mac break weekly, which means somewhere between 1 30 and 2 PM Pacific, that's 4 30 Eastern, that's 21 30 UTC.
01:54:32
I mentioned that because we do stream live, we have decided to continue the live streams on YouTube. Only as soon as the show starts you'll see a live stream on YouTube, uh, twitter, youtubecom slash twin, and if you subscribe, you should get notifications automatically when we go live. We'll go live for most of our shows, so you'll be able to watch it live, which means you can also chat with us live in our discord. If you're a club twit member, that's nice. After the facts, the shows are available because it's a podcast on the website twittv slash SN. You can subscribe in your favorite podcaster. There's a dedicated YouTube channel as well, which is nice for sharing clips. Now you should also consider going to Steve's site, grccom, the Gibson Research Corporation, because Steve has 64 kilobit audio, of course, the kind of the default version, but he also has two unique versions that we don't have, which is 16 kilobit audio for the bandwidth impaired and a transcript created by the bandwidth impaired, as it turns out, lane Ferris, who didn't have a lot of bandwidth when she started by now she must, but we had the 16 kilobit version for her and that's a really good thing to have either read along as you listen or to use for searches. And you know, the other day I fed about 20 of your transcripts into chat GPT to create a Steve Gibson AI expert and I asked it about ransomware trends and all sorts of stuff. It's really interesting. I think that's coming soon. Let's see.
01:56:06
While you're there, pick up Spinrite. Oh boy, you are weeks away from the release of 6.1, but 6.0 is on the site. You buy it now. You will get 6.1 the minute it comes out the world's best mass storage, maintenance and recovery utility. Everybody who has mass storage should have a copy of Spinrite. So go get that right now at GRCcom.
01:56:25
While you're there, lots of free stuff. His new Validrive, which checks your thumb drives. Make sure you got what you paid for. I think if you find thumb drives in your Christmas stocking, you should definitely run them through Validrive. Almost certainly run them through Validrive. We appreciate it. Oh, and now you can watch security now on Apple TV. What's the story there, Patrick? Did you create an app for us? Well, that's pretty cool. You did, patrick, so go to the App Store. I did not know this, steve. You now have an app on your Apple TV and you can add the Security Now app and watch security now through that. Very cool. Does that have the live version as well, patrick? That's very cool. Oh, the app was released three years ago. Okay.
01:57:17
Just wasn't paying attention, I guess. Thanks for mentioning that, Patrick.
01:57:22 - Steve Gibson (Host)
Life is passing us by, Leo it's all happening.
01:57:25 - Leo Laporte (Host)
I was foggy from COVID, I think.
01:57:28 - Steve Gibson (Host)
That's right, that was COVID.
01:57:31 - Leo Laporte (Host)
Patrick says not the live stream, just the edited versions. But that's a good way to see all your episodes on your Apple. Tv. That's why we do the video. Steve, you and Laurie have a wonderful Christmas. Take some time off, enjoy your New Year's, really enjoy this week. Yeah, I get to take a week off. Are you going to? Yeah, you haven't done that in ages. You going somewhere?
01:57:53 - Steve Gibson (Host)
No, I don't have a podcast next Tuesday.
01:57:56 - Leo Laporte (Host)
Heaven for Fendt. That's, yeah, that's great and bad guys. Don't make anything bad happen next week. Okay, yeah, that's true At the beginning of the year.
01:58:07 - Steve Gibson (Host)
generally is the case that the holidays are a little slow, so I may come up with a heavy content like a deep dive episode to kick off the New. Year.
01:58:17 - Leo Laporte (Host)
That'd be great. I wanted to show you real quickly. I vastly underestimated the number of club TWIT members who are doing the advent of code. It is quite a few. Darren Oakey, who is in our Discord, is our current leader, along with Paul Holder, who helps me with the TWIT community and is a very good Java coder. I've always been impressed. John Arnold is still working on the second half of day 19. He's up there too. He's also in our Discord. And then there I am, way down here, slowly working my way up the list. Lots of people, though, participating. Some of these are from last year. Some of them are using new names, I think, but there are right now 25 people actively participating in the TWIT family in the advent of code, and if you're not a member of Club TWIT, join. If you go to the Discord, there's an advent of code channel where we are talking, and John Arnold helped me with speeding up my day five.
01:59:13
I've got to do some Allen's interval algebra when I get home. I don't even know what that means, but I'm going to work on it. You will, you will, I will. That's what I love doing this. It's not to be top of the list, it's because I learned so much. It's fantastic. Thank you, steve. Have a wonderful holiday. We'll see you next time on Security Now. See you next year, my friend hey.
01:59:36 - Rod Pyle (Announcement)
I'm Rod Pyle, editor-in-chief of Ad Astra Magazine, and each week I joined with my co-host to bring you, this week in space, the latest and greatest news from the final frontier. We talked to NASA, chief space scientists, engineers, educators and artists, and sometimes we just shoot the breeze over what's hot and what's not in space books and TV, and we do it all for you, our fellow true believers. So, whether you're an armchair adventurer or waiting for your turn to grab a slot in Elon's Mars rocket, join us on this week in space and be part of the greatest adventure of all time.