Security Now 952 Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
00:00 - Leo Laporte (Host)
It's time for security now. Steve Gibson is here coming up. Ron Wyden's fight to protect our metadata. Why is metadata a risk? We'll find out. We'll also talk about Sony. They lost that big case, yeah. And then Steve explains why he thinks quantum computing just had a breakthrough moment. It's all coming up next. On security now Podcasts you love from people you trust.
00:30
This is Twitter. This is security now with Steve Gibson, episode 952, recorded Tuesday, december 12th 2023. Quantum computing, breakthrough Security now is brought to you by our friends at ITPro TV, now called ACI Learning. Aci's new cyber skills is training that's for everyone, not just the pros. Visit goacilarningcom slash Twitter. Twitter listeners you'll get up to 65% off an ITPro Enterprise Solution Plan. That's a lot. The amount of the discount varies depending on the size of your team, so fill out the form and find out how much you can save at goacilarningcom slash Twitter.
01:19
And by Lookout, whether on a device or in the cloud, your business data is always on the move. Minimize risk, increase visibility and ensure compliance with Lookouts Unified Platform. Visit lookoutcom today. And by Bitwarden, the open source password manager, to help you stay safe online, get started with the free teams or enterprise plan trial, or get started for free across all devices, free as an individual user at bitwardencom slash Twitter. It's gonna be good because it's Steve Gibson that's what I hear everywhere because Steve is the hero of the hour, the host of the show you're now listening to. Security now, where we cover security and privacy and how computers work, how technology works, this one's gonna be a big one, I think. Hi, steve.
02:12 - Steve Gibson (Host)
Hey, leo, great to be with you. We let's see yeah, this is airing before anyone will have seen what we did on Thursday. Oh yeah, on a holiday show we should mention that yeah the old prostate show, and it's.
02:27 - Leo Laporte (Host)
The good thing is because we're all old, we had to make it a short show so everybody could get to the bathroom. It's our Christmas Eve twit, which Steve was a part of With Doc Searls and. Jeff Jarvis and Rod Pyle and it was. It was great. So if you're around Christmas Eve, make sure you get twit. It'll be up on the feed December 24.
02:46 - Steve Gibson (Host)
So here we are, and I'm more conscious of than ever that we're moving past 999 because we've just crossed the 950.
02:56 - Leo Laporte (Host)
We're into 952 now, yeah, and it would be shaking my boots right now.
03:00 - Steve Gibson (Host)
It would be a little sad if we were, like you know, heading to the end, but we're not. Well, the end of the podcast, at least we may be nearing the end of traditional asymmetric crypto, and I don't don't don't ever want to get upset. We still have plenty of time. But today's podcast is titled Quantum Computing Breakthrough because there has been one and it's appears to be significant. I appreciate in, and our listeners will hear this, what I'm quoting, the scientists who are involved, everybody around it is. You know they're adding the caveat of you know if this indeed works the way it appears to. You know, that's what scientists say. I mean that that's science instead of you know the marketing hype, people. But I really believe everybody's going to understand what happened because it's under well, it's understandable and in fact, it's also this week's picture of the week, not yet something that people are going to have on their desktops, but you know, the first computers weren't either right. I mean they were. They had, you know, power generation stations all dedicated to them in order to light them up.
04:23 - Leo Laporte (Host)
Given that these have to operate at absolute zero, I don't think there's going to be a desktop quantum computer.
04:29 - Steve Gibson (Host)
Not soon, no. So we're going to get there, but first we're going to answer the question why is metadata such a problem? What massive new audience just got end to end encryption by default? What's the latest on Iran's cyber Avengers? What are the most exploited vulnerabilities of 2023, which we can now examine because we're near in the end of 2023? How are things looking two years after the discovery of the log for J-Flaw? Whatever happened with Sony's attempt to force quad nine to block a pirate domain that was offering some of Sony's music? Whatever happened with that lawsuit we talked about a couple years ago? That's right, I forgot about that, yep. What exactly is the dark web and where is it? And, after closing the loop with some of our listeners, we're going to examine last week's surprising news of a significant breakthrough in quantum computing. Wow.
05:35 - Leo Laporte (Host)
That's almost scary to be honest with you.
05:42 - Steve Gibson (Host)
It definitely has advanced the timeline significantly, Holy cow. So we'll talk about that and everything that it means here by the end of the podcast.
05:53 - Leo Laporte (Host)
Yeah, I want to know more. I really want to know more because, honestly, I've been skeptical, to be honest, about what quantum computing, whether it would even happen. It's like huge energy.
06:04 - Steve Gibson (Host)
When they're bragging that they were able to factor the number 37 or something. Then it's like okay.
06:11 - Leo Laporte (Host)
Yeah, nevertheless, I trust you, and if you say there are big things ahead, I'm thinking uh-oh.
06:20 - Steve Gibson (Host)
Everyone will get it by the end of this podcast.
06:23 - Leo Laporte (Host)
Good, Good, good, good Good. All right, let me get a. I should stall a little bit because I don't have. I don't have the ad in front of me, but I shall get it soon.
06:36 - Steve Gibson (Host)
I heard that Wix is now an advertiser.
06:38 - Leo Laporte (Host)
Yeah, do you use.
06:39 - Steve Gibson (Host)
Wix no, but Lori does. Oh yeah, she's a Wix maven, it's good stuff. Yeah, leo, I use a text editor.
06:47 - Leo Laporte (Host)
Yeah, excuse me, of course.
06:49 - Steve Gibson (Host)
HTML.
06:50 - Leo Laporte (Host)
There's nothing wrong with HTML, no, sir. Well, our sponsor actually is somebody we know well. They've been with us all year as the studio sponsors. We really appreciate what they've done to keep us flying high in 2023. And I just want to give them a pat on the back and a thank you. And, of course, when I say ACI learning, some of you might go well, who are they? But they are. They merged with a IT pro TV and I know everybody listens to security now is very well aware of IT pro TV. It's now called ACI learning and it is a great place to know about if you have an IT team, and I'll tell you why.
07:28
There is a massive IT talent shortage out there. In a recent poll of CIOs and CISOs, 94% of them said that attracting and retaining. Attracting and retaining talent is job one. You know it's so hard to fill an empty slot, so you don't want to lose anybody you've got. But ACI learning is really a great partner in this, because one thing we know about IT teams is they're they're lifelong learners. They want to get better at their job. You want them to get better at their job and if you give them training they love and appreciate, it helps keep them happy. It helps keep them retained.
08:12
Aci learning has more than 7200 hours of 20 to 30 minutes short form content. That's that. I guess that's more than 14,000 videos about all, and it's all brand new, fresh. They they're recording it constantly in their studio, seven studios running all day, monday through Friday, so it's always up to date content about all of the things your team needs to know to keep at the top of their game. And it's entertaining. It's well done. You know IT Pro TV. They know how to do it. Instructors who are experts working in the field who have a passion for what they're doing, which makes the videos engaging. Of course, very informative. In fact, that's one of the reasons ACI learning's completion rate on their videos is 50% better than the rest of the industry. People love the video. They also have a way of future proofing your entire organization against the threats that are floating around now out there.
09:09
They call it cyber skills. It's a training tool for the. I guess the IT guys probably could take it in fact should take it but it's really intended for the non IT professionals in your company Cyber security awareness training that they very much need. With cyber skills, you get flexible, on demand training. You know what they're famous for for everything that they need to know, things like password security, what a phishing scam looks like, how to avoid them, malware prevention, overall network safety. They're going to love it because it's great content, well produced. It's a simple one hour course overview that they can take and then which will give them, by the way, you know, kind of the basics. They need a specific attack, specific training. There are knowledge check assessments based on cyber threats that they're going to face day to day, but there's also bonus courses. If there's something they want to know more about or need to know more about, there's documentary style episodes they can learn in the way they want to learn about the stuff you, as the, as the boss, need them to know. So important because almost all these breaches now begin with employees. That's really they've got to be up to date.
10:21
Aci learning they help you invest in your team, both the IT team and your employees at large, and entrust your team to thrive while increasing the entire security of your business. Boost your employees, enterprise cyber security confidence today with ACI learning. Be bold, train smart. Visit goacilarningcom, slash twit to find out more. And, by the way, you'll be glad to know this as, as a twit listeners a security now listener you can get up to 65% off your IT pro enterprise solution plan. 65% off Now the discount space and the size of your team. So here's the deal Fill out the form, find out how much you save. Go to goacilarningcom slash twit. It's been a great year with ACI learning. We love these guys and we're really glad to be able to tell you about it. So check it out Goacilarningcom slash twit. Steve, I have queued up the picture of the week. Do you want to introduce it?
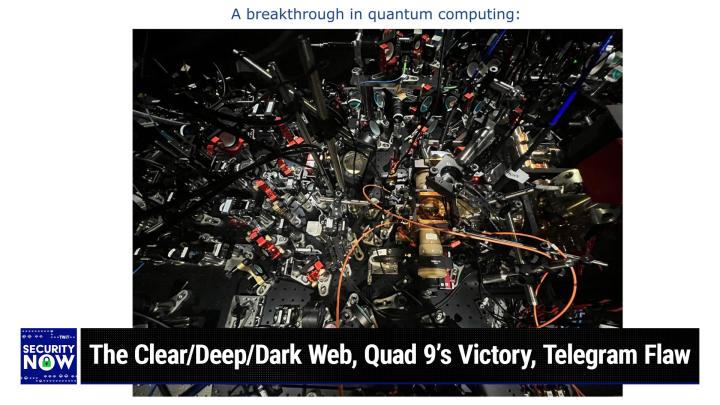
11:25 - Steve Gibson (Host)
So, yeah, this is a, an actual picture from the lab at Harvard University that we'll be discussing at the end of the podcast. One of Michael McCullum's sci-fi novels is titled the sales of sales. As S A I L S, as in light sales, the sales of Tau Setti. And light sales is an actual thing. You can use a large, very, you know, gossamer, thin fabric which is aimed at a star in order to get propulsion, which is to say that photons, light coming from the star, actually do create pressure, which can be used in the, in the case of Michael's book, to to power a starship, to to propel a starship through the universe, well, through the galaxy, because, you know, between galaxies you've got a problem with insufficient starlight.
12:36
But in this picture that is being done that, somewhere buried in this insane looking machine and this is one of those where, like you know, you don't let the janitor come in to clean this is, you know, painstakingly assembled and you can see a sort of see that it's like a high-end Lego set. Right, you know, these things are screwed down. They all have slots which allowed them to be adjusted before the screw is tightened on the base in order to hold a, you know, whatever one, whatever that is in place. But in here and you'll hear me talking about it later are laser tweezers which use lasers to manually move molecules of super cool rubidium atoms around. Yeah, what? So we're talking serious. I mean, you know, this was sides fission 20 years ago. So now here it is and it actually works.
13:46 - Leo Laporte (Host)
This would make a great jigsaw puzzle. Oh, it really would. Yes, wow. Yeah. Wow.
13:54 - Steve Gibson (Host)
Yeah.
13:54 - Leo Laporte (Host)
So the tweezers? Everybody find the tweezers. By the end of the show.
13:58 - Steve Gibson (Host)
I'm not saying that this will make any more sense than it does now, but at least we'll have an overview of what this contraption has accomplished. Last Wednesday, december 6th, one of our favorite privacy rights crusading senators Oregon's Senator Ron.
14:18 - Leo Laporte (Host)
Wyden Love this guy.
14:19 - Steve Gibson (Host)
He's been so well, we need somebody like this to be doing this. So I'm sure glad he is. He addressed a letter, to quote the honorable Merrick B Garland, attorney General, us Department of Justice. Here's what Wyden and his team wrote. They said Dear Attorney General Garland, I write to urge the Department of Justice, the DOJ, to permit Apple and Google to inform their customers and the general public about demands for smartphone app notification records. In the spring of 2022, my office received a tip that government agencies in foreign countries were demanding smartphone push notification records From Google and Apple. My staff have been investigating this tip for the past year, which included contacting Apple and Google. In response to that query. The companies told my staff that information about this practice is restricted from public release by the government. So your democracy's tax dollars hard at work, tying the hands and gagging these to prevent them from disclosing what they're being forced to do in what the name of national security? Anyway, ron's letter continues with Ron explaining.
15:52
Public applications are the instant alerts delivered to smartphone users by apps, such as notification about a new text message or a news update. They aren't sent to the public from the app provider to user phone. Instead, they pass through a kind of digital post office run by the phones operating system provider. For iPhones, this service is provided by Apple's push notification service. For Android phones, it's Google's fire-based cloud messaging. These services ensure timely and efficient delivery of notifications, but this also means that Apple and Google serve as intermediaries in the transmission process, as with all of the other information these companies store for or about their users.
16:45
Because Apple and Google deliver push notification data, they can be secretly compelled by governments to hand over this information. Importantly, app developers don't have any options. If they want their apps to reliably deliver push notifications on these platforms, they must use the service provided by Apple or Google respectively. Consequently, apple and Google are in a unique position to facilitate government surveillance of how users are using particular apps. The data that these two companies receive includes metadata detailing which app received a notification and when, as well as the phone and associated Apple or Google account to which that notification was intended to be delivered.
17:35
In certain instances, they also might receive unencrypted content, which could range from back-end directives for the app to the actual text displayed to a user in an app notification. Apple and Google should be permitted to be transparent about the legal demands they receive, particularly from foreign governments, just as the companies regularly notify users about other types of government demands for data, these companies should be permitted to generally reveal whether they have been compelled to facilitate this surveillance practice, to publish aggregate statistics about the number of demands they receive and, unless temporarily gagged by a court, to notify specific customers about demands for their data. I would ask that the DOJ repeal or modify any policies that impede this transparency. Thank you for your attention to this pressing matter. If you have any questions or require clarification, please contact Chris Sigoyan at my office Right on Ron Wyden.
18:45 - Leo Laporte (Host)
And, by the way, I didn't know, chris. Sigoyan was working for Ron Wyden. Just yet another reason to respect Ron Sigoyan's one of the best security he's out there. He absolutely is.
18:58 - Steve Gibson (Host)
So Reuters picked up on this and did some additional reporting. They wrote in a statement. Apple said that Wyden's letter gave them the opening they needed to share more details with the public about how governments monitored push notifications. Apple wrote quote in this case, the federal government prohibited us from sharing any information. Now that this method has become public, we're updating our transparency reporting to detail these kinds of requests. Unquote. And for their part, google said that it quote shared Wyden's commitment to keeping users informed about these requests. Unquote.
19:43
The Department of Justice declined to comment on the push notification surveillance or whether it had prevented Google or Apple from talking about it. Wyden's letter cited a tip as the source of the information about the surveillance. His office did not elaborate on the tip, but a source familiar with the matter confirmed that both foreign and US government agencies have been asking Apple and Google for metadata related to push notifications to, for example, help tie anonymous users of messaging apps to specific Apple or Google accounts, in other words, de-anonymizing them. The source declined to identify the foreign governments involved in making the requests, but described them as democracy's ally to the United States. The source said they did not know how long such information had been gathered in that way. Most users give push notifications little thought, but they have occasionally attracted attention from technologists because of the difficulty of deploying them without sending data to Google or Apple. Earlier this year, french developer David LeBeau said users and developers were often unaware of how their apps emitted data to the US tech giants via push notifications, calling them a privacy nightmare.
21:07
So we've talked before about the power and value of metadata. While it may be that Apple and Google's messaging encryption technology deliberately prevents them from being able to comply with lawful government subpoenas for the content, we know quite well that Apple doesn't want to. The fact that messages are flowing and between whom they are flowing is not something that is nearly as easy for Apple to have no way of knowing. They've designed their technology so that they cannot respond to the subpoenas they don't want to, but this is not something for them to like, for them not to know. You know these subpoenas doubly require Apple and Google to provide all information they have of any kind, including, specifically, metadata, for the individuals targeted by the subpoenas and relating to the apps and other users those targets are interacting with. So metadata itself is a pervasive problem.
22:20
You know we've talked about how even today's ISPs who are unable to see into today's web connections. The fact of those connections is not hidden without the use of a VPN to tunnel everything past an ISP's prying eyes. We also talked recently about the move to encrypt the initial TLS handshake packets, since they were also carrying useful metadata, and even the Tor network, whose entire existence is about obscuring endpoint connection metadata, has a difficult time doing so. We've seen that a correlation attack mounted by examining packets entering and exiting the Tor network assuming that there's some way to obtain that sort of near global visibility can be surprisingly effective. So it's significant that Wyden and his team are only, at least in this instance, asking about Apple and Google. It's significant because this is very likely the tip of the iceberg.
23:28
It would be safe to say that any and all social media enterprises operating inside the US, such as Meta with WhatsApp and, of course, facebook and Facebook Messenger, are subjected and being subjected to the same sort of metadata requests accompanied by the same sort of gag orders.
23:50
Although law enforcement and other government agencies may be thwarted in their examination of messaging content, the social graph networks through which their targets move remains a significant source of valuable and, in fact, vital information, and it's not at all clear how Apple, google, whatsapp and the rest can eliminate that loophole. I mean, even Tor has technically a difficult problem doing so, because these service providers are maintaining explicit accounts with the users of those devices. In all of this worry over encryption, backdoors and privacy, this ubiquitous presence of notification, connection and messaging metadata is almost always overlooked. So again, as you said, leo, bravo to Wyden for pointing at this and probably eventually hopefully prying this open as a much bigger problem than it's been given Very few people know how useful metadata is and obviously law enforcement does, and I'm glad that he recognizes that and I think, credit to Chris Segoian because he's got a good cybersecurity advisor.
25:15
Yes, and you could also argue that third-party cookies are nothing but metadata. It is literally a token which follows you around, and it's by. It is your movement around the internet metadata, which is then all aggregated and pulled together to mean something.
25:41 - Leo Laporte (Host)
And people were wondering. Yes, chris Segoian is a relative of Sal. It's Sal's nephew, sal Segoian, of course, a longtime contributor on the network, the creator of a big guy in Apple Script at Apple for a long time the creator of Automator and a regular on our shows in the early days. So yeah, comes from a good family too. Yeah, good on you, ron.
26:02 - Steve Gibson (Host)
Good on you. Yeah, thank goodness we have him, you know, jumping up and down about this stuff. And while we're on the topic of end-to-end encrypted conversations, also last Wednesday Facebook announced that their gradual rollout of encryption for Facebook Messenger, which we talked about when it first appeared as an encrypted conversations option in Messenger, is now switching to always on by default. This took a long time, since it meant that all endpoints would need to have been upgraded. That has happened, so now Facebook is flipping the switch. Since I was curious about what underlying technology they were using, I did a bit of digging and learned that they had the wisdom to not roll their own encryption system. Facebook Messenger is based on the signal protocol, even to the extent of borrowing from signals open source libraries over at GitHub. Facebook needed to tweak signal here and there, since their platform models are different, but it's nice to know that messengers billion plus users will be using a stable and well proven encryption technology by default.
27:23
Moving forward, last week we noted that widespread attacks were being seen targeting PLC systems made by the Israeli company Unitronics. These were particular concerns since the systems in question were controlling water management systems in the US and throughout the world. The shocking piece of this was that the systems being attacked and you really need to put that word attacked in air quotes here, since, given that these systems had never bothered to change their manufacturers original default established password of 1111 connecting remotely to any of the between 500 and 800 systems now known to be vulnerable. Really, you know, it amounts to more of a visit than an attack. You know, yeah, you know, we're just visiting your system from Iran.
28:26
You know what's up. So, in any event, these Iranians are reportedly continuing to busily scan the internet for the appearance of any of these PLC systems and we now have the six Iranian IP addresses they're using. I've added them to the show notes for anyone who might be interested in watching their honeypots or their public WAN interfaces for probes from any of these six IPs you know 88.135.36.82. And there's five others. I won't. I won't recite them all here. They're at the very bottom of page three of the show notes for anyone who's interested. Thank you, Leo, for putting it on the video there. So yeah, if, if any of those IPs visit you, they're coming from Iran and they're just coming over to say hi and to see whether you might be, you know, have your sprinkler system connected to the internet through a Israeli Unitronics PLC.
29:32 - Leo Laporte (Host)
They're probably not geolocated in Iran either. Right, they're probably. You know come they look like. They're coming from Indiana or somewhere, I would imagine.
29:40 - Steve Gibson (Host)
I did note that there's a five dot which is interesting because remember that. Remember that Hamachi used the five dot network extensively because it had not a single IP had ever been allocated from from from five dot anything and of course we gave we had to. We had to give up on that a while ago as we began to run shy of IP for address space.
30:03 - Leo Laporte (Host)
I'll add these to my ubiquity block list. I block nations, you know. I block China. I block Russia, but, like I said, I bet it doesn't all. If they're not all Iranian, I'll block Iran.
30:16 - Steve Gibson (Host)
Probably not, but probably specifically in order to get around those sorts of blocks. Yep, Yep. So Cisco's Talos Group have just published their annual cybersecurity year in review, and the thing that caught my eye there was their breakdown of the most targeted vulnerabilities. Before we look at the top 10, here's what the Talos Group said about their findings. They said in 2023, cyber threat actors exploited older software vulnerabilities in common applications. In many cases, the vulnerabilities were more than wow it's hard to even read this. The vulnerabilities were more than 10 years old, Consistent with Sysa's finding that adversaries have targeted old security flaws more than newly disclosed recent ones in recent years. In fact, four of the top five most targeted vulnerabilities we observed were also cited by Sysa as being frequently exploited in prior years. Further highlighting this point, this underscores the need for entities to regularly install software updates, as many of these systems were likely unpatched, given the age of the targeted vulnerabilities, meaning they're so old, they obviously never received a patch since then. Which right, Okay. So they said the top targeted vulnerabilities were found in common applications like Microsoft Office. This finding is also substantiated by Sysa, which noted that actors in 2022 prioritize CVEs that are more prevalent in their target's networks. In other words, you know they're going to attack the ones that are there right. Adversaries likely prioritize targeting widespread vulnerabilities because the exploits developed for such CVEs can have long-term use and high impact. That's a good point If you're targeting, if you're able to target and exploit a very old vulnerability that says the system has never been updated since then, which further says it probably won't ever be again. So if you can get in using that, you could probably get to stay a long time, they said. Lastly, most of the vulnerabilities on our list would cause substantial impact if exploited Right. They're all like in the high nines in the CVSS score and a lot of them are remote code execution. So ouch, they said, with six of these top 10 receiving a maximum vulnerability risk score of 100 from Cisco Kenna and seven receiving the highest critical score from the common vulnerability scoring system, CVSS. Most of the CVEs are also listed in CIS's known exploited vulnerabilities catalog. That their their kev KVE, which is meant to inform users on the security flaws for which they should prioritize remediation. The high frequency of targeting systems against these CVEs, paired with their severity, underscores the risk to un-patch systems. So I have in the show notes the chart from Cisco's Talos group.
33:43
What's astonishing is that this year okay, 2023, we're talking about the number one most often, most often exploited vulnerability with a high CVSS of 9.3 is CVE 2017 0199. That's right 2017. This is a vulnerability that is six years old. Yes, Six years ago. This thing was found and we talked about it on the podcast extensively. This affects Microsoft Office and WordPad. It's a remote code execution vulnerability that leverages RTF files and a flaw in Microsoft's equation editor, which is exploited through Microsoft Word. I know For six years, Leo. It's remote code execution, it's a CVSS of 9.3, the maximum vulnerability score of 100. And it is the number today, the number one most exploited vulnerability.
34:52 - Leo Laporte (Host)
Yeah but I have to point out it's not the oldest on this list. No, it's not by a long shot, In fact no, it's not. Holy cow.
35:01 - Steve Gibson (Host)
You know, and what's absent from these discussions and from my ability to imagine are any details about the machines which are today still not only running Microsoft's Office software from 2017, unpatched even once since then, but also have no other AV defense of any kind in place, even Microsoft's free solution. And this is not just one lonely abandoned system somewhere forgotten in a closet. The exploit enters through an email attachment, so the system's being compromised. Not only have no defenses of any kind and haven't received a single update in six years, but they are in active use. Somebody is receiving email on them and clicking a link to get themselves exposed to this, and it's the number one, most often thing that happens.
36:08 - Leo Laporte (Host)
Oh, my God.
36:10 - Steve Gibson (Host)
Where are these systems? Who's are they? Okay, I want to take a guess at the number two problem among the top 10. Believe it or not, it also has the same high CVSS of 9.3, and its CV was also issued back in 2017. Oh my God, cve 2017 11882. And that beauty is brought to us by Microsoft's exchange server. Now, obviously, the same thing applies as above, although an unattended machine running exchange server might well be in some dusty old, forgotten back closet somewhere.
36:52
And lately I've been pushing the idea that automatic updates would solve many of the problems we're seeing in our industry today. But Microsoft pioneered the idea of automatic updates. They're enabled by default and have been for a very long time. Yet somehow a huge number of machines enough to put that they're exploit at number one in the first place in the ranking are still not being patched. They've remained unpatched. So it would really be interesting to look at case studies of the specific machines and the environments that surround them that allow six year old Microsoft flaws to remain present today. I, you know who has these things. Where are they? We don't know, but Leo, we are going to know. Who's helping to support this podcast and the Twitter network?
37:58 - Leo Laporte (Host)
Very important. We would not want to forget such important people. You didn't mention that there is a CVE from 2010. Apple. Safari, Safari but oh, don't worry, it's only a 9.3. Nothing to nothing to worry about. Yeah, there's a CVE from 2012, microsoft Office GZIP 2012. I mean, some of these are pretty dang old.
38:26 - Steve Gibson (Host)
It's kind of incredible. It does demonstrate what a problem we have with software that isn't getting updated Yep and that we'll be talking about the log4j library next. But first a word from our sponsor.
38:39 - Leo Laporte (Host)
I can't imagine anybody's still using a 2010 version of Safari. I don't even know if that would work. But if you are, stop, okay, just stop. Stop the insanity Our show today brought to you by Lookout.
38:55
Speaking of stopping the insanity, business has changed forever, you know. I mean the boundaries to where we work, even how we work, just completely disappeared. Your data these days is always on the move, whether it's on a device that's at somebody's house, it's in the cloud, across networks in the local coffee shop. You know, and now your workforce loves that, right, but it's a challenge. Let's face it for IT security, and that's where Lookout comes in. Lookout helps you control your data and free your workforce. With Lookout, you'll gain complete visibility into all your data, so you can minimize risk from internal and external threats. You can ensure compliance by seamlessly securing hybrid work.
39:41
Your organization does not have to sacrifice productivity for security, and Lookout makes IT security a lot simpler. You know, right now they're probably working with multiple solutions, multiple legacy tools. Legacy that's the bad word of the day, and in today's environment, not only is that too complex, you got to remember. As soon as somebody switches context from one tool to another, even one tab to another, stuff gets left behind. That's how our brains work, and so what you need is a single, unified platform. What you need is Lookout. It reduces IT complexity and then gives you more time to focus on whatever else is coming your way. And trust me, if you'd listen to this show, you know there's a lot coming your way. Good data protection it's not a cage. It's a springboard, letting you and your organization bound toward a future of your making. That's the way it ought to be. Visit Lookoutcom today. Learn how to safeguard your data, how to secure hybrid work and how to reduce IT complexity. Lookout, l-o-k-o-u-t, lookoutcom. We thank them so much for supporting the work Steve's doing right here on security.
40:57 - Steve Gibson (Host)
Now, so, while we're on the topic of long lasting vulnerabilities, it's not only the deep past that seems to be behaving irresponsibly. Two years ago 2022, we kicked it off here with the news that a potentially devastating flaw in the Log4j library might rock the internet. Fortunately, that never happened because the flaw was not readily exploited, except in the one instance where it was found in a zero day attack. So it was never the lowest hanging fruit and, as we've seen, the bad guys, you know, use the easiest route, in which Log4j turned out not to be. But that didn't mean that the flawed library didn't still need to be fixed and replaced, because, as long as this known to be vulnerable library is present, a resourceful hacker might find a way to exploit it in its particular use case. Last Sunday, on the second anniversary of the discovery of this flaw, bleeping Computer reported on the findings of the application security company Veracode, who took a look at the status of Log4j. Today, here's what Bleeping Computer reported. They said roughly 38% of applications using the Apache Log4j library are using a version vulnerable to security issues, including Log4shell, a critical vulnerability identified as CVE 2021, because it was at the very end of 2021. And we began talking about it at the beginning of 2022, 44228,. That carries the maximum severity rating, despite patches being available for more than two years. Okay so, 38% of applications that have a version of Log4j bound into them include a critical vulnerability. They said Log4shell is an unauthenticated remote code execution flaw that allows taking complete control over systems using Log4j 2.0, beta 9 through 2.15.0. The flaw was discovered as an actively exploited zero day on December 10, 2021. And its widespread impact, ease of exploitation and massive security implications acted as an open invitation to threat actors. The circumstance promoted an extensive campaign to notify affected project maintainers and system administrators. But despite numerous warnings, a significant number of organizations continue to use vulnerable versions long after patches became available.
44:02
Two years after the vulnerability was disclosed and fixes were released, there are plenty of targets still vulnerable to Log4j. A report from application security company Veracode, based on data collected between August 15th and November 15th, highlights that old problems can persist for extended periods. Veracode gathered data for 90 days from 3,866 organizations that use 38,278 applications relying on Log4j with versions between 1.1 and 3.0.0 alpha 1. Of those apps so those 38,278 apps 2.8% use Log4j variants 2.0, beta 9 through 2.15.0. That was the original Log4j disaster. Which are directly vulnerable to Log4shell. Another 3.8 use Log4j 2.17.0, which, although not vulnerable to Log4shell, is susceptible to the same CVE, a remote code execution flaw that was fixed in version 2.17.1. Finally, 32% get this are using Log4j earlier Log4j version 1.2.x, which reached its end of life support in August of 2015. And all of those versions are vulnerable to multiple severe vulnerabilities published until 2022. Cve 2022, 23307, 305, and 302. In total, veracode found that about 38% of the apps within its visibility use an insecure Log4j version. This is close to what software supply chain management experts at Sonotype report on their Log4j dashboard, where they show 25% of the library's downloads in the past week include known vulnerable versions.
46:26
The continual use of outdated library versions indicates an ongoing problem, which Veracode attributes to developers wanting to avoid unnecessary complications. Veracode found that 79% of developers chose to never update third-party libraries after their initial inclusion in their code base to avoid breaking functionality. In other words, this is deliberate in 80% 79% of developers, and this is true even if 65% of open source library updates contain minor changes and fixes unlikely to cause functional problems. Moreover, the study showed that it takes half of all projects over 65 days to address high severity flaws. It takes 13.7 times longer than usual to fix half of what's in their backlog when understaffed, and over seven months to handle 50% of it when lacking sufficient information. Overall, veracode's data shows that Log4shell was not the wake-up call many in the security industry hoped it might be. Instead, log4j alone continues to be a source of risk in one out of three cases and may be one of the multiple ways attackers can leverage to compromise a given target.
48:12
The recommendation for companies is to scan their environment, find the versions of open source libraries in use and then develop an emergency upgrade plan for all of them. Okay, now there are many places where our industry is limping along and hoping for the best, such as with the use of very useful open source libraries. One of the problems is that developers could truly spend all of their time just keeping their code current with upstream library version changes. You know I love and I've mentioned this before the Notepad++ application for Windows. It's really terrific, but its developer refuses to leave it the F alone. It's fine, it works. Just stop messing with it.
49:13
It is constantly wanting to update itself and since it does everything I want, I finally disabled its checking for updates, because it was just so annoying every time I launched it, oh look, new version. Stop everything, hold the presses Up. You know, upgrade, but now with version, you know, with updates disabled, just for the sake of sanity. Now I have a real problem because I wouldn't know if a serious vulnerability turned up in it, because it was just too noisy, because the developer abused the automatic update system. So I can imagine just how much chaos there would be if a project was using a large assortment of open source libraries which were themselves dependent upon other open source libraries and so on up the dependency tree. It likely would be truly a full-time job just keeping everything current.
50:20
And I totally sympathize with the idea that you update some library and it breaks a bunch of things because the functionality changed. It wasn't just fixing a bug, it was oh look, we realized the blub. Whatever it is, you know, you don't want new, you just want secure. So you know it's not difficult to imagine a developer thinking look, everything's working right now. I don't want to rock the boat and risk breaking things that are working just for the sake of having you know the latest and greatest version of everything. Maybe they're more secure, or maybe a bug was introduced when the change was made, right, I mean it's not like when we're adding new features we're not also bringing new bugs along. Otherwise, you know, windows would have been perfect a long time ago, but it sure isn't Okay.
51:17
Two years ago we reported on the despicable tactic Sony Entertainment was undertaking of blaming the DNS resolving service, quad nine. Just single them out because you know they're non-profit, so they ought to be easy to squash and step on and set a precedent. So they sued quad nine for the fact that they were providing random people on the internet, who have their browsers pointing at quad nine, the IP address of a pirate domain whose server was making some of Sony's copyrighted recordings available. Sony said that the domain owners didn't respond and couldn't be located, and I don't know about the hosting provider. So they decided to sue quad nine because you know they could find them and they would respond to email notice they didn't sue Google.
52:22
Exactly yeah. Exactly.
52:25
You know, and at the time, leo, you and I were both livid at the idea that Sony might prevail in this, since it might set a precedent where anyone with a grievance could sue someone who was providing some of the internet's infrastructure, regardless of how incidental to the underlying complaint. So here we are, two years later with the news that the German court where Sony brought this case has ruled in favor of the defendant how quad nine, thank goodness Denying any appeal and instructing Sony to pay all of the defendants defense costs, which certainly is a way it should go. Here's what Quad9 had to say about all this. They wrote. Today marks a bright moment in the efforts to keep the internet a neutral and trusted resource for everyone. Quad9 has received word from the courts in Dresden, germany, in the appeal of our case versus Sony Entertainment Germany. The court has ruled in favor of Quad9 clearly and unequivocally. Nail is to say. We are elated at the news.
53:45
Sony Entertainment Germany started illegal proceeding against Quad9 more than two years ago to force Quad9 to stop resolving certain domain names which they claimed were involved in copyright infringement behavior. We believe this lawsuit was an attempt to set a precedent such that commercial rights holders could demand that sites on the internet be made unreachable by forcing recursive resolvers to block content. We contended that recursive resolvers have no commercial or even remotely indirect relationship to any of the infringing parties and that Sony's demand for blocking was ineffective, inappropriately specified and not related to Quad9. What made this case more problematic, in our view, was that the servers in question in this case were not located in Germany and the links they pointed to were on servers also not in Germany. The domain name canna c-a-n-n-a, dot t-o was not registered in Germany and was under the top level domain operated by the nation of Tonga. Sony Entertainment further asserted that we blocked the domains globally, not just in Germany, as GOIP does not block for users based in Germany. With certainty, for that matter, quad9 has no office or standing in Germany. We're a Swiss entity, but due to the Lugano Convention Treaty, it was possible for Sony to serve an injunction in Switzerland and drag Quad9 into legal proceedings there.
55:30
The appeal with the higher regional court in Dresden follows a decision by the regional court in Lepsig in which Sony prevailed and Quad9 was convicted as a wrongdoer. Before that, sony successfully obtained a preliminary injunction against Quad9 with the regional court in Hamburg. The objection against the preliminary injunction by Quad9 was unsuccessful and the appeal with the higher regional court in Hamburg was withdrawn by Quad9, since the decision in the main proceeding was expected to be made earlier than the conclusion of the appeal in the preliminary proceedings. You have to read that paragraph five times to understand what they said. But basically they appealed their initial loss and they won on appeal. They said the court has also ruled that the case cannot be taken to a higher court and their decision is the final word. In this particular case, sony may appeal the appeal closure via a complaint against the denial of leave of appeal and then would have to appeal the case itself with the German federal court. So while there is still a possibility that this case could continue, sony would have to win twice to turn the decision around again.
57:03
They said we would like to clarify that even though Quad9 benefits from the liability privileges as a mere conduit, it is possible that a DNS resolver operator can be required to block as a matter of last resort if the claiming party has taken appropriate means to go after the wrong doer and the hosting company.
57:30
Unsuccessfully, which is interesting because two years ago we said that it's so wrong that Sony didn't do those things. It turns out that the way the language is written, and here Quad9 is saying, if a complainant did first go after the wrong doer and the hosting company and do everything you know, all their due diligence, which Sony didn't then it might be ruled that a DNS resolver operator could be required to block a domain. Quad9 said such measures could be legal action by applying for a preliminary injunction against a hosting company within the EU, meaning that would be regarded as sufficient. These uncertainties still linger and we expect that this ongoing question of what circumstances require what actions by what parties will continue to be argued in court and in policy circles over the next few years. I'll just pause you to say this on a broader level. This cannot be allowed to happen. You know, recognize what this would mean. This would mean that anybody, any big bully with money, could sue DNS resolvers to force them to block domains that they're not happy with for any reason.
58:53 - Leo Laporte (Host)
What is worse than that?
58:55 - Steve Gibson (Host)
Countries could do it.
58:56 - Leo Laporte (Host)
Well, it's worse than that, because it wasn't just DNS resolvers, it'd be any infrastructure any infrastructure, because it's all using that infrastructure. I mean that's ridiculous. They're not alive. I mean that's like suing the phone company because somebody phoned in a bomb threat. It doesn't make sense and it's just untenable. You can't continue that way.
59:20
Yes, please don't bring this up to that judge in Texas, because that would be the end of life on the end, and I always get nervous when stuff goes to courts because you don't know what you're gonna get. You know right right.
59:34 - Steve Gibson (Host)
So Quad9 says we remain committed to the concept that resolving a domain name is not an action that should be prohibited for commercial goals. The DNS does not contain content. It is a system designed for delivery only of pointers, not for data transport. The courts in Cologne also recently ruled in favor of Cloudflare in a similar case involving DNS recursive resolution, although that case also includes a separate consideration of issues relating to CDN and proxying services, and we are pleased to have consistent and clear statements from both courts in this matter of DNS recursive resolution. Today was a significant win in Germany, but there is some disappointment as well. We received a notice from a consortium of Italian rights holders Sony Music Italy, universal Music Italy, warner Music Italy and Federation of Italian Music Industry who have demanded that Quad9 block domains in Italy, and there is potentially another court process ahead of us. Wow, okay. So on the one hand, this is good news, but it's also clear that this is not over yet.
01:00:59
Sony is at it again, attempting to use their muscle to force Quad9, a non-profit DNS resolving company, to bend to their will. Here's the status of this second new lawsuit Quad9 wrote while our case in Germany has been found in favor of Quad9. We've been served with another demand from commercial interests in an EU nation to block domain names, again based on alleged copyright violations. Italian legal representatives have presented us with a list of domains and a demand for blocking those domains. Now we must again determine the path to take forward fighting this legal battle in another nation in which we are neither headquartered nor have any offices or corporate presence. Unsurprisingly, the group of media companies that are represented by the plaintiff and it's an Italian legal firm, lgv Avocati Milan Italy, on behalf of the Italian of the Federation against Music and Multimedia Privacy or Piracy, are Sony Music Entertainment Italy, universal Music Italy, warner Music Italy, as well as the Federation of the Italian Music Industry. The short answer from us is that we're going to fight this demand for censorship, but it may take us time to be certain of a full victory and completion of our case in Germany before we are able to take on another court process.
01:02:37
Quad9 can only have a few legal fronts open at once. We are nearly entirely dedicated to operational challenges of running a free, nonprofit recursive resolver platform that protects end users against malware and phishing. We are not a for-profit company with lawyers on retainer. We've complied with a request and these names are now blocked on Quad9 systems. Since the courts have provided, again, no guidance on how we determine if a request is made by someone under Italian jurisdiction, we have applied this block globally.
01:03:19
The German courts entirely disregarded our use of GOIP lookups on queries and asserted that, since tests via a VPN were able to resolve the domain, we were in breach of court orders. We wish to avoid that same distraction again. For the time being, we've created an attributed blocking list with these domains on it, and they are searchable on the front page of our website in the search bar, and the results will contain information about the status and origin of the blocking requirements. When Quad9 decides to take action on this issue, we will post updates on this blog and modify our block lists accordingly.
01:04:02
Well, you know Aglio saying again this is so wrong. I am so glad that the court in Dresden made Sony responsible for all the costs of Quad9's defense, and I hope Quad9 may be able to use their success in Germany to help with this next case. What Sony, universal and Warner are doing cannot be allowed to happen, and what we really need is some higher level intervention somewhere. I mean somehow this, just as you said, leo, this is just one handy part of the infrastructure, but the separation has to be made.
01:04:49 - Leo Laporte (Host)
It just makes you not want to do good things. It's like you know they're doing this great it's sad. Thank goodness that they have the fortitude. I would have just say, well, screw you bye, but good for them that they stuck it.
01:05:05 - Steve Gibson (Host)
I mean it's got to cost them a ton to do this, I mean yeah, well, and the good news is they're getting their expenses reimbursed, and so I hope so. So the problem is, sony is so huge. They have attorneys our retainer who they're paying a salary to, so it doesn't cost them anything.
01:05:23 - Leo Laporte (Host)
It's not a fair fight.
01:05:25 - Steve Gibson (Host)
No, I hate bullies, that's just. I'm a problem with that. So a group known as Searchlight Cyber posted an analysis about the state of the DDoS for a higher business which exists on the so-called dark web. That made me realize that, while I've referred to the dark web often in the past, we've never really stopped to talk about it. For anyone who's unsure, the dark web is actually a thing, or rather a place. It's not just an expression and you cannot get there from here. It's not just a matter of using some secret URL to bring up a dark website.
01:06:13
There are three terms used within the cybersecurity community to refer to three classes of the web. There's the clear web, the deep web and the dark web. The web that we all use every day is more formally known as the clear web. It's what Google indexes and where anyone can easily wander with links that are shared with us either by a public search engine or by other web pages. This is the traditional web that Tim Burners-Lee first conceived of when he was at CERN and, interestingly, this clear web only contains roughly 4% of the entire web content. It's like the tip of an iceberg. So where's the rest? Most of the rest resides in the so-called deep web. This is the web content that is not indexed publicly because it requires authenticated access through a portal of some kind. So this includes things like our credit reports, irs tax records and medical histories, fee-based content, membership websites and confidential corporate web pages. Those are all considered to exist on the deep web, and estimates place this deep web content at roughly 96% of the total browser accessible web. And finally, a small subset of this deep web is known as the dark web.
01:07:59
The dark web's servers are deliberately hidden and are accessible only through the Tor browser on the Tor network. It's necessary to use Tor because those servers and the services they offer wish to remain hidden and quite difficult, if not nearly impossible, to locate. And it's worth noting that, despite its ominous sounding name, not all of the dark web is used for illicit purposes, though this is another place where the emergence of cryptocurrency has transformed the place from a backwater hacker curiosity into a significant collection of criminal enterprises. My advice would be to stay as far away from the dark web as possible, so I won't be offering any guide or tips to accessing this dark underbelly of the internet, but if you're really curious and want to go poking around down there, you'll find that the clear web contains many step-by-step how-to guides into setting up a secure sandboxed OS, obtaining the Tor browser, putting on your hazmat suit, holding your breath and taking the plunge. Good luck.
01:09:23
And as for what the Searchlight Cyberguys found out about DDoS for hire services being offered on the dark web, there was nothing really noteworthy. It's pretty much what we would expect. Portals exist where people can create an account and transfer some of their cryptocurrency to it to create a positive balance. Then they select the type of DDoS attack they wish to launch either at OSI stack level four, which is the down-to-the-transport layer, so using either UDP or TCP flooding packets, or up at level seven, which is the application layer, so an HTTP connection and query flood. Then the target IP or URL is provided and the size and duration of the attack is specified, and the site takes care of conducting the attack from there.
01:10:19
One thing that did surprise me was that one of these services, named the Nightmare Stressor, claimed to have 566,109 registered users. That number cannot be verified, of course, but it does perhaps support the view. From up here. Out on the clear web, up in the light, we see more or less constant DDoS attacks, so much so that they're just prevalent. Talk to any Tier 1 internet provider and it's like oh yeah, that's just happening all the time. So 566,109 registered users of this one service where, if you want someone to be attacked, it's not hard to do and actually it doesn't even cost that much, which is another reason we're seeing so many of them. Okay, let's close the loop with a few listeners.
01:11:23
Mike Ward, via DM, said hi, steve, I just discovered a major privacy and security flaw in the messaging app Telegram. Telegram, he wrote, automatically informs users you've joined if that user has your phone number and has previously uploaded it to Telegram as part of their contact list sharing, even if you deny Telegram access to your contacts. He said. I discovered this first hand just now.
01:11:57
After downloading and signing up for Telegram and specifically denying it access to my contacts, a friend sitting right across the table from me received a notification on his phone that said that I had joined Telegram. Mike wrote this is a major privacy and security flaw, as a stalker or domestic abuser could upload a victim's number and be automatically notified if that person ever joins Telegram. For that matter, so could any law enforcement or government agency. It may also explain why spam and scams are so prevalent on the service as mal actors are able to upload your phone number, acquired from somewhere else than in a date, you with messages the moment you join. So that was an interesting observation, mike, and I agree that this appears to be a significant privacy failing of Telegram. The system ought to require mutual sharing of intersecting contact information in order to provide any notifications, not just one way, unilateral contact use. They likely use the less private approach as a means of promoting the further use and adoption of Telegram, but that's not what anyone wants from a secure messaging solution.
01:13:23 - Leo Laporte (Host)
It's actually very annoying because I get so many messages from Telegram saying your friend has just joined Telegram, and I never give. By the way, let's emphasize this never give your contacts to any third party. You're basically turning over information about your friends to a third party without their consent. Never do that, right? Not for the very mild convenience of getting notified when your friends join Telegram, but you know that's not why they want that information, right?
01:13:57 - Steve Gibson (Host)
Yeah, yeah, I'm still using an old and long since retired landline as the phone number that I give out in those places. That's a good idea. I just won't let them have even my phone number because I look at other people whose phones are just exploding with nonsense and I'm glad I don't have that. Yeah, justice, justin Eekus. He said have you ever seen something like this? Looks like my cell carrier is forcing me to trust an additional route CA. This is unacceptable. I'll be switching at the earliest opportunity, thought my fellow listeners would like to know, and he included a link to a Twitter media snapshot which was of his Xfinity cellular provider asking him to accept a route certificate and give it full trust on his phone.
01:15:00 - Leo Laporte (Host)
Sure, why the hell wouldn't? I want to do that.
01:15:03 - Steve Gibson (Host)
I obviously we agree with Justin completely. There's only one possible reason for this, which is that Xfinity wishes to insert a transparent proxy into his Internet connections.
01:15:17
So why so they could put ads in there, right Well, and it will decrypt everything he does with his phone. All of his use of the Internet browsing will be decrypted by certificates which Xfinity is able to build on the fly, which will be trusted because he accepted their route cert. I mean it is full on spying and so, yes, that should certainly raise warning flags for anybody who understands what's going on.
01:15:50 - Leo Laporte (Host)
I should mention, steve, that this link that you put in here is actually a link to direct messages, so I can't see it. No one else could see it, because it's a message to you. So, yeah, so don't get all excited folks. Thank you, leo, I would love to see that screenshot. That's why I clicked it. But geez, Louise Right.
01:16:12 - Steve Gibson (Host)
So, yes, anyway, do not accept any requests from your cell provider saying hey, in order to continue our relationship with you, you're going to have to add this route certificate to your phone. No, no.
01:16:29 - Leo Laporte (Host)
Is that a condition of using Xfinity Cellular?
01:16:33 - Steve Gibson (Host)
If it is, don't Right. Right, justin was very right to bring this up. Thank you, elliot Anderson said instead of pulling all but six CAs, meaning you know six CA routes couldn't someone make an extension that just shows green for one of the main six, yellow for another CA, red for HTTP and a duck for a quack, you know, qwac cert? Maybe need blue, orange and pink or something for colorblindness, so that you know. That's an interesting thought, but my concern would be that this places the burden on the user to observe some visual flag. If our goal in removing the ridiculous number of barely, if ever, needed certificate authority route certs is to improve our security in the event that one of the fringe CAs mints a malicious cert, then I still think that the cost of running with only the top six is likely very minimal and represents the best solution. Michael Smithers says hi, steve, I'm a longtime listener and spin ride customer. Thank you for all your work. Can you recommend a hardware VPN solution for home that's not complicated to set up? I need to access my home server from around the world, mainly for version control access, and I presently have some ports internet facing with port forwarding. Yes, I know this is not good. I can see from the logs that bots are continuously attempting to guess login credentials and are causing user lockouts for some more common usernames. Many thanks for your help. Here's to 1000 and beyond, michael. Okay, so VPNs are definitely useful when you want to protect your use of the internet, For example from your prime ISP who's like trying to scavenge all the metadata they can from you. But setting up your own VPN server to provide incoming access is probably no longer the optimal solution for all of those who's who. For all of those needs, you really want to look at an overlay. Overlay network Think tail scale or zero tier. Overlay networks is the newer, better, more secure and much more powerful and flexible way to solve this sort of problem. We've talked about these before and I've received a bunch of feedback from our listeners who have said that they have been astonished by how easily the system was installed, set up and and running, and another advantage is that they run through NAT routers without needing any static port forwarding, so no bots are going to be probing for a connection. Tail scale has a companion page where they compare themselves with zero tier, and I've looked at that page in the past. It appears to be quite even handed, since nothing else has claimed GRC's shortcut of the week so far. Grc dot SC slash 952 will take you directly to that page. It's at tail scalecom slash. Compare slash zero tier. Z E R O T I E? R. I'm very glad that Michael asked this question, since today's new overlay network solutions really do represent a useful advance and a much better way to solve the need for roaming access to a remote network. Once upon a time it was Hamachi and their five dot networks. We covered this a long time ago. Now these things have gone mainstream. They're open source, they're free, they are, they have been audited, they are bulletproof and they really work. Tail scale or zero tier and tail scale, by the way, runs on top of wire guard, which is the, you know, the rewrite of a state of the art secure tunneling technology. You know it just really works and it is very fast. So that's what I would look at for any of that sort of problem.
01:21:15
And finally, chris Hatch says Steve, very thankful you're continuing. Sn pass 999 long time listener. Just heard you mention API monitor. When I put the URL in Firefox, malware bytes blocked. Going there with the warning website blocked due to Trojan. He said I checked with virus total and it had two AVs that thought it was malicious. What do you do to check of a site is safe to visit? Looking forward to upgrading spinrite when 6.1 is released. Thanks for the great show, chris.
01:21:52
Okay, so unfortunately that amazing API monitor tool that I talked about before and impressed me so much when I had to do some reverse engineering of some Microsoft undocumented stuff. It's about 10 years old and it has not been touched in all that time. It is also not digitally signed. Since 10 years ago Few things were, and I recognize that many people feel that any software that has apparently been abandoned is automatically worthless. That's not my feeling at all. I strongly prefer software that has become stable because all of its bugs have been found and eliminated, making that software complete and finished.
01:22:42
I'm fully aware that's not the way our industry has evolved, where many programs are full of bugs or where commercial interests require that software remains forever in flux, with people continually paying in the hope that it will finally someday be finished For what it's worth. Only triggering two out of all of virus totals AV scanners generally about 70, means that there's nothing whatsoever wrong with that code If the screen had lit up with 20 or more out of 70, then yeah, I would never have let it get near my machine. Just now, like two hours ago, I dropped my copy of api-monitor-setupcom, which I downloaded and then tested against virus total. I dropped it on virus total, I just now received a zero out of 71 score. So virus total agrees that code being served by that site, old and unsigned as it is, is clean and safe to use. And, leo, this brings us to our third sponsor and then I think what is going to be a really illuminating and interesting discussion of a recent quantum computing breakthrough.
01:24:10 - Leo Laporte (Host)
I am fascinated by this whole thing and, as I said, skeptical, so I'm looking forward to hearing this Our show today brought to you by something I am fully not skeptical of, I'm fully behind, which is using a password manager, and the only one I use one. Steve uses the open source cross-platform password manager that works at home, at work, on the go. I'm talking about you know, say it with me Bitwarden. We love Bitwarden. We were talking about the danger of metadata earlier on the show and some password managers last pass notably, do not encrypt the metadata. Like all of the sites you have passwords for are in clear text, visible, which gives an attacker way too much information.
01:24:59
Bitwarden encrypts it all. It's all encrypted, strong, encrypted, end to end, not just the passwords, but everything in the vault. And why wouldn't you? But they do it right, and that's the point. Bitwarden protects you in many ways. You can use unique user names in addition to a unique password for every site. That works with five different email companies, including our sponsor, fastmail. So you can, you know, you know how with a password manager. You get the button generate a password, you also get generate a login and you can do both and they all work because they're connected up to your email provider, so your email provider goes yeah, no, I know, when we mail comes to that address, we'll forward it. It's really good. It's really a good solution. You can log into Bitwarden and decrypt your vault using SSO on a registered, trusted device, which means you can eliminate that whole master password. Now you've got no password. They now support, by the way, they support pass keys, so they are a great trusted provider for your pass keys that you can take with you from device to device and platform to platform.
01:26:07
Not only is it open source, but they have professional third party audits performed every single year and the result the entire result is published on the website. You can look at Bitwarden's code on GitHub. You can even submit a pull request. In fact, one of our listeners did last year or maybe it was this year, not that long ago when they heard us talking about the problems with PBKDF2 and the memory hard alternatives that are better, like S-Crypt and Argon2. And next in I think or Quexin his name is he said oh well, I'll code that up. Code it up in Argon2 implementation, submitted the pull request, bitwarden folded it in. It's now in there. This is why open source is so great. I mean, once they vetted it and made sure it was secure, made sure it's safe and of course, it'll be subject to the future third party audits and all of that. Now you have a much better way of protecting your password than PBKDF2. I turn it on immediately.
01:27:07
They have features like for business sharing private data. Actually, you could do that with personal plans too. And the best thing about Bitwarden the personal plan is free Free forever for unlimited devices. For a while. The personal plan you know you had to buy the premium plan to use a Yuba key or a hardware key like this, which I use all the time. That's how I unlock my vault. I love that. Now that's available for free as well. They even have included pass key management in the free version free forever. But I pay them 10 bucks a year for the premium. It's less than a buck a month. I give them that because I just want to support them. I love these guys.
01:27:48
You can get the premium features for the family, and a family can be any six accounts for $3.33 a month. So you could all chip in the enterprise plan, the one that we're switching to right now just $6 per user per month. There's a team's starter plan. That's a flat $20 a month for 10 users and that's a $1.00 per month. For a $1.00 per month. That's a flat $20 a month for 10 users. So very affordable $4 a month per user with teams of 11 or more. On that team's plan They've got plans for every possible use. But I really want to stress this you I mean you're listening to SecurityNow. You're obviously using a password manager. That's fine. It's easy to switch to Bitwarden. You can use that free plan and it will be free forever. I promise, they promise they're not going to go take it away at some point because they're open source. They can't you. But, more importantly, you're going to go home for the holidays.
01:28:44
You're talking to friends, loved ones, who don't listen to SecurityNow or maybe not as security conscious. Tell them to use Bitwarden. One of the main objections is well, I'm not going to pay for something. It's free. It's free and it's such a good solution. It's easy to use, they'll get used to it very quickly and they'll be a thousand times more secure because you know what they're doing now. They got the dog's name, their birth date, their middle name. They're putting that and wishing that to a password and they're using it everywhere.
01:29:13
Don't stop At TWIT. We are I think it would be an understatement to say fans of the password manager. You got to use it and it's easy to get started with Bitwarden. Get a free trial of the teams or enterprise plan, or get started for free across all devices, unlimited passwords, hardware key support, pascii support free forever with an individual plan. Bitwardencom slash TWIT we you know they're spending some of their hard-earned money to advertise on the show and I just I think we appreciate that support and I'm so glad to support them back and I hope you will too. Bitwardencom slash TWIT it's the best. I love it. Okay, now we got to find out. What's all this about? Quantum computing, steve.
01:30:06 - Steve Gibson (Host)
So the podcast actually has an extended title. It's quantum computing breakthrough, a breakthrough for the turbo-encabulator, and all your qubits are belong to us.
01:30:22 - Leo Laporte (Host)
Yeah, we couldn't fit that in the lower third Steve.
01:30:24 - Steve Gibson (Host)
No, do people know what the?
01:30:27 - Leo Laporte (Host)
turbo-encabulator is.
01:30:29 - Steve Gibson (Host)
I think maybe now would be a good time to introduce them, Leo.
01:30:32 - Leo Laporte (Host)
A little short. This is just a short audio, Just a piece of the beginning. Only clip, just so you understand what we're talking about here.
01:30:38 - Leo's Laptop Audio (Other)
It will prepare them for what is to come For a number of years now, work has been proceeding in order to bring perfection to the crudely conceived idea of a transmission that would not only supply inverse reactive current for use in unilateral phase detractors, but would also be capable of automatically synchronizing cardinal grammeters. Such an instrument is the turbo-encabulator.
01:31:01 - Leo Laporte (Host)
There you have it, ladies and gentlemen, you've wanted it, you've needed it.
01:31:07 - Steve Gibson (Host)
Yes, and that lingo will sound familiar in a minute.
01:31:10 - Leo Laporte (Host)
By the way, that's double-speak nonsense, but what you're going to tell us is real.
01:31:16 - Steve Gibson (Host)
We got some of the double-speak in here, but it's not nonsense.
01:31:20
So DARPA funded quantum computing research conducted at Harvard made headlines last Thursday with what those in the know are pretty certain represents a significant step forward in the quest for a practical quantum computer. One of the big problems which is currently and has been limiting the practical application of quantum computers is the need for extensive error correction. One way to think of this is that quantum bits, the so-called qubits, spelled Q-U-B-I-T-S qubits are powerful but imprecise. So when you need precision for things like, you know, cryptographic computations, where quantum fuzziness is a bug not a feature, it's necessary to use a whole bunch of fuzzy qubits in an error-correcting system.
01:32:24 - Leo Laporte (Host)
Is it using let me just ask pre-familated amulet surrounded by a malleable logarithmic case?
01:32:30 - Steve Gibson (Host)
It's a foundation of pre-familated amulet. Yeah, yeah.
01:32:34 - Leo Laporte (Host)
Just checking.
01:32:36 - Steve Gibson (Host)
The individual fuzzy qubits are referred to as physical qubits, but what we want and need for many of the types of calculations that quantum computers promise are what's known as logical qubits. And, as I said, traditionally the number of physical to logical qubits has been around 1,000 to one, which is to say it takes 1,000 fuzzy physical quantum bits in an error-correcting mode to reliably obtain a single solid logical bit, and it's only the logical bits that are able to do most of the useful work. Okay, now, in a minute I'll share a useful explanation of what was recently accomplished and just published, and that will come from a non-physicist who speaks English as his first language rather than quantum. Good Reading the actual paper published in Nature last Wednesday, written by those who do speak quantum fluently, I was reminded of our favorite turbo-encabulator, which made good use of those flambulating differential reverse trunnions. Oh yes, so to give everyone, you've got to have those, and they have to be differential to give everyone a flavor of just how far out this science has wandered. This is what they wrote for the abstract of their paper, which was titled Logical Quantum Processor Based on Reconfigurable Atom Arrays. They wrote Suppressing errors is the central challenge for useful quantum computing requiring quantum error correction for large-scale processing.
01:34:30
However, the overhead in the realization of error-correcting logical qubits, where information is encoded across many physical qubits for redundancy, poses significant challenges to large-scale quantum. Large-scale logical quantum computing Makes sense so far. Here we report the realization of a programmable quantum processor based on encoded logical qubits, operating with up to 280 physical qubits, utilizing logic-level control and a zoned architecture in reconfigurable neutral atom arrays. Our system combines high-2-qubit gate fidelities, arbitrary connectivity, as well as fully programmable single-qubit rotations and mid-circuit readouts. Of course, how about that, when you have to have that mid-circuit readout?
01:35:31
Operating this logical processor with various types of encodings, we demonstrate improvement of a 2-qubit logic gate by scaling surface code distance from D equals 3 to D equals 7. Oh, preparation, yeah, that was yeah. Preparation of color code qubits with break-even fidelities, fault-tolerant creation of logical gigahertz states and feed-forward entanglement, teleportation, oh, as well as operation of 40 color code qubits. Finally, using three-dimensional, that's 8 by 3, by 2 code blocks, we realize computationally complex sampling circuits with up to 48 logical qubits entangled, with hyper-cube connectivity, with 228 logical 2-qubit gates and 48 logical CZZ gates. Oh, and we, yeah, we find that this logical encoding substantially improves algorithmic performance, with error detection outperforming physical qubit fidelities at both cross entropy benchmarking and quantum simulations of fast scrambling. Yes, these results herald the advent of early error-corrected quantum computation and chart a path toward large-scale logical processors.
01:36:58 - Leo Laporte (Host)
Well, of course.
01:37:00 - Steve Gibson (Host)
Well, naturally.
01:37:02 - Leo Laporte (Host)
Oh, my God.
01:37:04 - Steve Gibson (Host)
What you're looking for is high-fidelity feed-forward entanglement teleportation Uh-huh, wow, yeah, and that was not nonsense. That was actually the abstract from the paper published in Nature last week.
01:37:20 - Leo Laporte (Host)
I bet there's only 100 people in the whole world who could understand that. Do you understand that? No, no, okay.
01:37:28 - Steve Gibson (Host)
But we're going to get to the gist of what it means. Okay, everyone agrees that, if this turns out to work, as it appears to, it would represent a bona fide breakthrough in quantum computing by dramatically reducing that previous 1,000-to-1 physical-to-logical qubit ratio thanks to a breakthrough in quantum error correction technology. And when I saw this, it immediately became this week's podcast topic. Okay, so now I want to share English. I want to share something that was written by a non-physicist, where there will be no mention at any point of feed-forward entanglement teleportation. Oh well, okay, it begins with this powerful claim widespread quantum computing may now come to a conclusion, may now come years sooner than widely expected. Wow, yes, thanks to a Pentagon-funded project, as in DARPA, which, as we know, also brought the world the internet, with implications for everything from rapid vaccine development and weather forecasting to cyber warfare and code breaking. If the Harvard-led experiment can be replicated and scaled up, it would still take a long time to make quantum computers widely available to run new forms of artificial intelligence for medical research, scientific experimentation and military command and control. Thus DARPA's interest. But early adopters would almost certainly include intelligence agencies eager to crack encryption protocols widely used by governments and businesses alike. That makes it all the more urgent to implement the new quantum resistant encryption algorithms that National Institute of Standards and Technology, nist, aims to finalize next year, in 2024.
01:39:35
On Wednesday afternoon, that's last Wednesday, the Defense Advanced Research Projects Agency and a paper in Nature announced results from a team of almost two dozen scientists, most of them from Harvard, funded by a DARPA program known as ONISQ Optimization with Noisy Intermediate State Quantum Devices. By manipulating individual atoms with precise, low-powered laser beams, known in the trade as laser tweezers, the team was able to create quantum circuits that correct for errors much more efficiently than alternative techniques, potentially overcoming the biggest barrier to practical quantum computers. Darpa's program manager for ONISQ said quote quantum error correction is fundamentally challenging. Mikhail Lukin, one of the Harvard scientists actually, it's Lukin's lab where this was done said you cannot quote, you cannot copy quantum information and you also cannot measure the quantum state without destroying it. Unquote. Different corporate, government and academic teams have tried various approaches to error correction, but they all waste an exorbitant amount of the quantum computer's power. But the Harvard team has found a radically more efficient way to guard against errors. Darpa's program manager said quote this is truly revolutionary. Having been demonstrated and even validated in this paper. We are off to the races. Unquote. Back of the envelope. Calculation suggests that the Harvard team's experimental quantum computer is potentially four times as powerful as the most advanced quantum chip available for purchase, ibm's Condor, unveiled on December 4th. Condor boasts 1,121 qubits, which is almost a three-fold increase over last year's record-breaking IBM osprey.
01:41:55
So what's a qubit? The term turns out to have multiple meanings. While a normal classical computer uses bits that can represent either zero or one, a qubit exploits the fuzzy nature of quantum phenomena to let it represent all the infinite possible values in between. That's a nifty trick that could shortcut previously impossible calculations. But because quantum phenomena are so strange, it's also much harder to figure out whether a qubit is working properly or glitching. So all quantum computers to date have had to devote most of their qubits to double-checking each other. That means the number of usable logical qubits that can actually do reliable calculations is orders of magnitude smaller than the number of a machine's physical qubits. Using error-correcting methods, it takes more than a thousand physical fuzzy qubits acting together to form one logical qubit. Ibm is now exploring a new, more efficient error-correcting technique. It says it should allow a mere hundred physical qubits to form one logical qubit. So, depending on whether the technique is used, a high-end chip with a thousand physical qubits like Condor could generate as little as one usable logical qubit or as many as ten.
01:43:41
The Harvard team, however, used a radical new approach to error-correction that turns a mere 280 physical qubits into 48 logical qubits. That's about 20 times better than what IBM is hoping it may be able to achieve in its next-generation chip and 200 times more efficient than the 1,000-to-1 ratio that current techniques are trying to reach. One of the Harvard physicists said quote up till now, the state-of-the-art people have realized. All the state-of-the-art people have realized was one logical qubit or maybe two. At most we have done 48. For the first time, we've actually built a processor which operates on these logical qubits. We demonstrated the key basic elements of this processor, namely the ability to encode, decode and perform logical gate operations. For the first time ever, we executed algorithms with logical qubits.
01:45:01
Skip Sansari, a co-founder of Qsecure, which builds software to defend against quantum-powered hacking, said logical qubits are the holy grail for quantum computing. He explained that physical qubits are very ethereal. They can be disturbed easily, which is what leads to errors. Sansari said. With the Harvard team's approach you don't need thousands, hundreds of thousands or millions of physical qubits to error correct. If it works, it's a huge speed-up. I want to flesh this out one bit more with some additional background coverage and quotes from other researchers quoting about this breakthrough.
01:45:51
The system is the first demonstration of large-scale algorithm execution on an error-corrected quantum computer, heralding the advent of early fault-tolerant or reliably uninterrupted quantum computation. Professor Lukin, who runs the lab at Harvard, described the achievement as a possible inflection point akin to the early days in the field of artificial intelligence. The ideas of quantum error correction and fault tolerance, long theorized, are starting to bear fruit, he said quote I think this is one of the moments in which it is clear that something very special is coming. Although there are still challenges ahead, we expect that this advance will greatly accelerate the progress toward large-scale useful quantum computers. The National Science Foundation's Denise Caldwell, who is the acting assistant director of the Mathematical and Physical Sciences Directorate, which supported the research through the NSF's Physics Frontiers Centers and Quantum Leap Challenge Institute's programs, agrees. She said quote this breakthrough is a tour de force of quantum engineering and design. The team has not only accelerated the development of quantum information processing by using neutral atoms, but opened a new door to explorations of large-scale logical Q-bit devices which could enable transformative benefits for science and society as a whole.
01:47:33
In quantum computing, a quantum bit or Q-bit is one unit of information, just like a binary bit in classical computing. For more than two decades, physicists and engineers have shown the world that quantum computing is in principle possible by manipulating quantum particles, be they atoms, ions or photons, to create physical Q-bits. But successfully exploiting the weirdness of quantum mechanics for computation is more complicated than simply amassing a large number of Q-bits which are inherently unstable and prone to collapse out of their quantum states. The real coins of the realm are the so-called logical Q-bits, formed from bundles of redundant, error-corrected physical Q-bits, these can store information for use in a quantum algorithm. Creating logical Q-bits as controllable units like classical bits has been a fundamental obstacle for the field, and it's generally accepted that until quantum computers can run reliably on logical Q-bits, the technology cannot really take off. In other words, that's what just happened, folks. To date, the best computing systems have demonstrated one or two logical Q-bits and one quantum gate operation akin to just one unit of code between them.
01:49:10
The Harvard team breakthrough builds on several years of work on a quantum computing architecture known as the neutral atom array. This was also pioneered in Lukens lab. It is now being commercialized by Q-era, which recently entered into a licensing agreement with Harvard's Office of Technology Development for a patent portfolio based on innovations developed by Lukens Group. The key component of the current system is a block of ultra-cold suspended rubidium atoms in which the atoms the system's physical Q-bits can move about and be connected to pairs or entangled mid-computation. Entangled pairs of atoms form gates, which are units of computing power. Previously, the team had demonstrated low error rates in their entangling operations, proving the reliability of their neutral atom array system. With their logical quantum processor, the researchers now demonstrate parallel multiplexed control of an entire patch of logical Q-bits using lasers. This result is more efficient and scalable than having to control individual physical Q-bits. The papers first named author Dolev Bluvstein, a Griffin School of Arts and Sciences PhD student in Lukens Lab, said quote we're trying to mark a transition in the field toward starting to test algorithms with error-correcting Q-bits instead of physical ones and thus enabling a path toward larger devices. So everyone agrees that this is almost certainly a benchmark on the road to moving quantum computing from a promising curiosity in the lab to a place where it can be commercialized for use in solving previously intractable problems in the real world.
01:51:23
Cryptography is not in trouble yet, but that trouble just jumped significantly closer. Remember that it's not symmetric crypto that's endangered by quantum computing. So algorithms such as AES's Rindall cipher and hashing-based solutions they've always been and will likely continue to be quantum safe, but asymmetric crypto such as RSA, based on the previously intractable problem of factoring a huge number composed of two half as huge prime numbers, and elliptic curve crypto are both on the chopping block. So it was prescient that the academic crypto community began worrying about this years ago and has now generated a series of quantum safe replacement algorithms that are rapidly being moved toward adoption. The challenge is that almost everything that's currently being done in the world today is still using traditional quantum unsafe, asymmetric cryptography. I say almost everything because remember that three months ago in September, signal announced their adoption of quantum safe crypto, running in parallel with traditional time proven but now potentially unsafe crypto.
01:52:49
The other entity that has proven itself to be prescient is the US National Security Agency, our NSA, as we know, having watched them build that massive data center facility out in Utah. They've taken advantage of the astonishing reduction in the cost of electromagnetic storage, or spinners as we call them over in GRC's news groups and forums, to suck up and store mass quantities of internet and other communications that they cannot decrypt today, but which they will likely be among the first to be decrypting once they receive their standing order for serial number one of a sufficiently powerful quantum computer. I'll bet that the facility already has a room set aside just waiting for something to be installed there. What this means for the industry is that we're not going to be able to enjoy the traditional luxury of upgrading our communications encryption. When we eventually get around to it, it will be necessary for the finally approved standards to be moved into preliminary implementations with more speed than normal. The good news is that this is not our first retirement of creaky older crypto in favor of shiny new crypto, so we've gained experience with doing this and can expect it to go smoothly Once sufficient testing has been done.
01:54:23
These next generation algorithms will need to be deployed, and again, not eventually, but as soon as possible. The wisdom signal demonstrated of running any new and inherently less well proven algorithm alongside and in parallel with a traditional, well proven, asymmetric crypto system may be the best in the near term, requiring that the results from both systems are needed for encrypting and decrypting. An ephemeral symmetric key provides protection against the possibility of an unexpected weakness being found in the newer post quantum system, which would break everything, and later, once the new system has been shown to be entirely safe, the secondary parallel backup system could be dropped to obtain a boost in performance. The surprise this week is yet another reason for taking this podcast past 999. We definitely want to be here to chronicle the adventure and the arrival of post quantum cryptography.
01:55:33 - Leo Laporte (Host)
Well, and I know your focus is crypto, of course, but you mentioned it. You know, in glancing, we are at a kind of already at an inflection point for AI and throwing kind of this kind of massively advanced computing against the software we've developed. I mean, right now it's a software thing running on existing hardware. We're getting better.
01:55:58 - Steve Gibson (Host)
We're running on the fastest available monstrously crazy GPU. You know arrays. Now you just drop one rubidium atom on it and it says well, hello, how are you feeling?
01:56:11 - Leo Laporte (Host)
Well, and I also think that there's a kind of a nice nexus between what is not exactly determined these are not deterministic computers. These quantum computers and AI shouldn't be deterministic either. We're not deterministic, it should. So there's a certain the fuzziness of it kind of lends itself. There. There's a synergy Right.
01:56:30
So honestly, we may think, oh yeah, crypto, fine, but we had no idea how 9000 was just around the corner, or Skynet or worse. And of course, if it is security and privacy you're concerned about. Remember that big data facility that the NSA built in the Midwest, storing every electronic communication for the last two decades, much of which they couldn't decrypt. Well, now, thanks to stuff like this, maybe they will be able to decrypt it, unless it used perfect forward secrecy and with modern analysis techniques, ai style analysis techniques extract the juice out of it in new and terrifying ways. So we are, we could well be. This could be a watershed. I think you're right. We want to go past nine and a nine, because I think right now we are in a technology watershed that is the equivalent of the invention of the personal computer or the internet, maybe even more significant. I don't know. Is that, is that overstating it?
01:57:33 - Steve Gibson (Host)
I don't think that's overstating it, my friend Nope.
01:57:36 - Leo Laporte (Host)
Nope, we live an interesting time, steve, and it gives us something to talk about, which is good, and it gives you something to think about, which is really good, listeners, that's you know. I mean. That's why we think you know what we do here at Twitter is so important, because staying on top of these developments and understanding them, you know, that's why we've always been here, going back, you know, 15 years, 18 years, but now more than ever, I think that it's important that we as citizens kind of stay on top of this. We can't let Ryan Wyden do all the work and and and have and be able to act rationally around it. That's why I want to put in one plug before we go on.
01:58:19
For our club You've heard us talk about, we had some layoffs last week. We're going to have some show cancellations to not this one, thank goodness, but times are a little tough for podcasting in general. Podcasts industry as a whole is laying off. People, networks are shutting down. We don't want to shut down. We think, for the reasons I just mentioned, what we're doing is super important, but we cannot rely on advertising to go forward. I'm sad to say, uh, there, there wasn't a benefit to that. It gave us the chance to give you for free this, this content, um. But I think, with advertising dwindling, it's going to require our audience to kind of step up and if you are not yet a member of club, this is we've given you an avenue to do that Now. It's not expensive. It's seven bucks a month. I just spent more than that on a triple venti latte, um, but for seven bucks a month you get ad free versions of this show and all the shows we do. You get the discord, which is a wonderful place to hang out and talk about topics like this. We have some very active uh discord discussions about AI. I bet you will have a quantum section before the end of the day. Uh, you also get content we don't make available in public for the club, club supported content like home theater geeks and hands on Mac and hands on windows and stuff like that.
01:59:38
Uh, if I may, I don't like to beg. You know I'm not big on that, um, I'm not good at marketing either, but I want to keep doing what we're doing. I think it's so important. So please, twittv, slash club, twit by a subscription for yourself, by one as a gift for a geek in your life. Uh, tell your friends, um, because that's we've got an important mission and we want to keep doing it. Twittertv slash club twit Patrick says I bought a pint of Ben and Jerry's yesterday Yesterday. We're more than seven bucks. So, and as you point out, patrick twits a lot healthier, maybe not as satisfying. Thank you, mr Gibson. You'll find Steve's work at GRCcom, the Gibson research corporation. That's where spin right lives his bread and butter the world's best mass storage, maintenance and recovery utility available. Uh, right now at 6.0,. You did say you were going to have an announcement today. Okay, I'm not going to hold you to it. I did I.
02:00:38 - Steve Gibson (Host)
I, I slipped I everything. Last week fought against me. I did a big posting in my news group to explain what happened. Don't worry, Definitely next week we don't hold it against you, Steve.
02:00:49 - Leo Laporte (Host)
We love you and we know you're working as hard as you can.
02:00:51
I'd rather get the bugs out now than later. Do it right, absolutely. That's one of the reasons we totally respect you. You don't any of us have a choice. So, uh, if you go there, you'll get the latest forms. Are there? Are the? Uh squirrel forms were there, and now the spin right forms If you buy six. So now you'll get six, one, of course, automatically a free upgrade.
02:01:13
Uh, grccom, while you're there, check out so many other wonderful things Steve does, including his latest effort, valid drive of free program to make sure you got what you thought you were getting when you bought that USB drive, that thumb drive. Uh, shields up. There's so much good stuff there, grccom, um, and of course, the show 64 kilobit audio versions, 16 kilobit audio versions For the bandwidth impaired and those great transcripts. So you get Steve's show notes but also the transcriptions created by Elaine. Uh, all of that at GRCcom. Go to twittv slash SN. We have 64 kilobit audio, but we also have our unique version video. If you want to see Steve's shining face, uh, we are shining glasses, shining glasses, um. You'll see a link at twittv slash SN to the uh, um YouTube channel. That's video there. That's actually a good way to share. If you said oh, you know, I really want to share this clip of the show that's on the YouTube channel and they make it very easy to share clips like that.
02:02:20
Uh, you also can subscribe. There's links to your favorite pod catchers, including Google, apple and, um, my favorite pocket casts. So you just click that link and it'll add to your pocket casts. Makes it easy for you to get each episode we do security now. Tuesdays this is our penultimate Steve's favorite word uh episode for the year. Uh, we'll have an episode on the 19th and then it will be a best of for the week after Christmas. We'll be back in the new year, of course, as we continue our saga.
02:02:53
Um, so make sure you come back next week and every uh, every Tuesday and 2024, 11 am Pacific Sorry, I'm apologize, it's right after MacBrick weekly, so it's one 30 to 2 pm Pacific, that would be 430, uh Eastern time, that would be 2130 UTC. The live stream is only on YouTube. Now, to save money, we've cut off all the uh costly streams, but we do turn on the YouTube stream whenever a show is in production, as it is right now. Uh, at twit, youtubecom slash twit. You can subscribe to that channel if you want to get notifications whenever we go to live. We go live when the shows are going on. Uh, to make it easy. Thank you, mr Gibson.
02:03:38 - Steve Gibson (Host)
My pleasure, my friend Yep and I'll see you next week with whatever has happened in the meantime.
02:03:43 - Leo Laporte (Host)
Okay, you and your turbo and cannabulator can go.
02:03:47 - Steve Gibson (Host)
Thank you, yeah, and I'm going to go find Patriot.
02:03:49 - Leo Laporte (Host)
That's not. Oh, I think you'll enjoy it. Yeah, Especially that piping episode. Take care Bye.
02:03:55 - Rod Pyle (Announcement)
Hey, I'm Rod Pyle, editor in chief of Adaster magazine, and each week I joined with my cohost to bring you, this week in space, the latest and greatest news from the final frontier. We talked to NASA, chief space scientists, engineers, educators and artists, and sometimes we just shoot the breeze over what's hot and what's not in space books and TV. And we do it all for you, our fellow true believers. So, whether you're an armchair adventurer or waiting for your turn to grab a slot in Elon's Mars rocket, join us on this week in space and be part of the greatest adventure of all time. Thank you.