Security Now 948, Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
00:00 - Leo Laporte (Host)
It's time for security now. Steve Gibson is here. You remember Spectre and Meltdown. Nobody ever exploited those. Well, there's a new speculative execution flaw called Downfall, and it's out there in the wild. Steve has all the details. We'll also talk about a brand new sci-fi novel. Steve loves is telling you all about it, why you would never want a windshield barnacle. And finally, my cosmic rays could be a real bane of cryptography. It's all coming up. Next on Security Now Podcasts you love.
00:39 - Steve Gibson (Host)
From people you trust.
00:41 - Leo Laporte (Host)
This is Twitter. This is Security Now with Steve Gibson, episode 948, recorded Tuesday, november 14, 2023. What if a bit flipped? This episode of Security Now is brought to you by Collide. Collide is a device trust solution for companies with Aukta, and Collide ensures if a device isn't trusted and secure, it can't log into your cloud apps. Visit collidecom slash security now to book an on-demand demo today.
01:18
And by Bitwarden, the open source password manager, to help you stay safe online. Get started with a free Teams or Enterprise plan trial, or get started for free across all devices as an individual user at bitwardencom slash Twitter. And by ITProTV, now called ACI Learning. Aci's new cyber skills is training for everyone, not just the pros. Visit goaceilearningcom. Slash Twitter. Twitter listeners. You'll get up to 65% off an ITPro Enterprise solution plan. The discount depends on the size of your team, so fill out the form and get a discount tailored to your needs. It's time for Security Now. They show where we cover the latest in security the internet everything you need to know about keeping yourself safe online with this guy right here, mr Steven Tiberius Gibson. Hello, steve. Hey, he's doing the Spock thing. You know, I made that Steven Tiberius Gibson thing up, but it's actually in your Wikipedia now.
02:21 - Steve Gibson (Host)
So yeah, it, it it it's stuck, it's stuck. And I don't know whether they realize that's. You know if my middle name begins with M or not T, but I don't know.
02:36 - Leo Laporte (Host)
Anyway, I love messing with things like that.
02:38 - Steve Gibson (Host)
The nature of my wife, lori, has started doing crossword puzzles as a way of keeping her brain sharp, since she doesn't code, she you know. She wanted some exercise. Yeah, and there was one. The one of the questions that she encountered last week was an opinion that spreads quickly on the internet, and it was four letters and I said meme and she said how'd you get that?
03:04 - Leo Laporte (Host)
I was like well, you know, I thought of that immediately. Yeah, I know.
03:09 - Steve Gibson (Host)
Yeah, so those of us who are we live on the internet spreading business.
03:13 - Leo Laporte (Host)
It is, that's our business.
03:15 - Steve Gibson (Host)
So, uh, okay, we're going to answer, as we like to lately, a bunch of questions. Is your privacy badgering you and if so, and if so, what can you do about it? What's the latest on last week's bombshell news of the EU's article 45 in EI DAS 2.0, who's lost how much money in online cryptocurrency recently and is using seed phrases for your wallet to get uh, which you get from a seed phrase suggestion site? A good idea. What could possibly go wrong?
03:56 - Leo Laporte (Host)
Has there been one that I'm glad you're answering I thought you had.
03:59 - Steve Gibson (Host)
We're going to answer that question right here today, leo. We have actual evidence. Uh, also, has there finally been a truly devastating and effective speculative execution flaw discovered in Intel's processors, and could it be their downfall? What country has decided to ban all VPNs and how bad are the two flaws which are recently found in open VPN, and how quickly should you update? Why have I stopped working on spin right? What? What's the best backup for a large nas? Should vulnerability researchers learn the assembly language of their target processors? If quantum computers threaten asymmetric crypto as they do, why not return to symmetric crypto? Could someone explain exactly why article 45 is a bad thing? What in the world, leo and oh, are we going to have fun? Here is a windshield barnacle, and why don't you want one? What's my latest sci-fi book series discovery, and just how bad could it be if a cosmic ray flipped a bit at just the wrong time? All those questions and more will be answered during today's security now podcast 948. What if a bit flipped?
05:35 - Leo Laporte (Host)
What if you know? People have been mocking me for years because I would go on the radio show and say that your computer could be crashing because of a cosmic ray. Yes, and nobody believed me. But this is going to be my proof.
05:53 - Steve Gibson (Host)
We have scientific and a theory. Fact now Science Come soon to a podcast near you.
06:01 - Leo Laporte (Host)
Before we do that, can I mention our fine sponsor, the good folks at Koleid. I love Koleid. Koleid is a device trust solution for companies that use Okta, and Koleid makes sure that if a device isn't trusted and secure, it can't log into your cloud apps. Visit Koleidcom slash security now you can find out all about it. So here's the deal. Okta, as you know, if you use Okta, assures that the person logging in is the actual person, right? That's what it's about Authentication. But that's not enough. You need a little bit more because, as we've learned from the last past breach and other things, a person could be the person but have an insecure device. He's logging in with a compromise device. He's logging in with bringing that compromise into your enterprise. You need Koleid. If you work in security or IT, your company has Okta. This is a message for you.
07:03
You know, if there's one thing we know about data breaches and hacks, they almost always involve employees, right? Sometimes an employee's device gets hacked because of unpatched software. Sometimes an employee leaves sensitive data in an insecure place. Maybe you know those API keys get somehow synced to GitHub and it seems like every day a hacker breaks in using credentials. They fish from an employee. But I don't want you to blame your employees. It's not their fault. It's the solutions you're using that are designed to prevent those breaches, and it doesn't have to be that way.
07:40
Imagine a world where only secure devices can access your cloud apps. In this world, phished credentials are useless to hackers. They don't work anymore. You can manage every OS, including Linux, mac, pc, doesn't matter all from a single dashboard. Best of all, you can get employees I love this to fix their own device security issues. So that has two benefits. One no more you know extra work for the IT department has to go and fix this.
08:10
But also, this is really great. It's raising the awareness of your employees, raising their sophistication and making them part of your security platform. And, honestly, everybody has to be involved in this. No employee gets to say well, it's not my fault, not my problem, so now they're part of it and they're on your team. That's wonderful. You don't have to imagine this world. This is what you get with collide K-O-L-I-D-E. Visit collidecom slash security now. Book an on demand demo today. There's lots of stuff on the website explains how this works K-O-L-I-D-E. I think this is such a great idea and it's a must have tool Collidecom, slash security now. We thank them so much for supporting Steve and security now. We appreciate it. And without that, without collide, would we have a picture of the week?
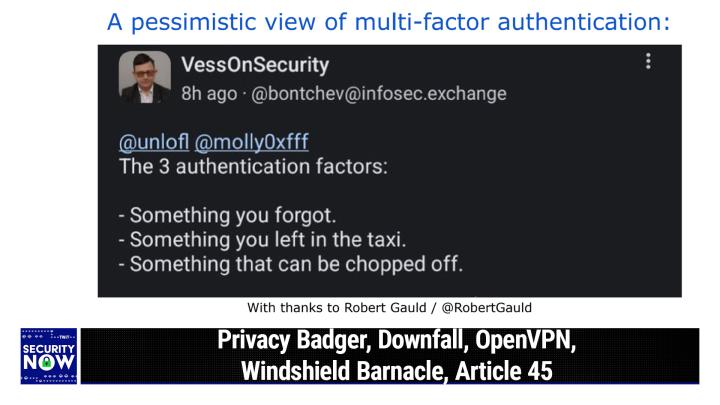
09:02 - Steve Gibson (Host)
I ask you? I think not. So this one was a retweet from one of our listeners who thought I would get a kick out of it, and he was certainly right. I titled this a pessimistic view of multi-factor authentication, where the three authentication factors are something you forgot, something you left in the taxi and something that can be chopped off. Actually, that's a really good point. I gotta say Vess on security.
09:35 - Leo Laporte (Host)
That's a really good point.
09:37 - Steve Gibson (Host)
Yep.
09:38 - Leo Laporte (Host)
Wow.
09:39 - Steve Gibson (Host)
Yeah. So yeah, instead of something you know, something you have and something you are, it's something you forgot, something that the taxi just drove away with and, whoops, something that could be chopped off if someone really needed it.
09:53 - Leo Laporte (Host)
Let's hope it's your hand, not your head. By the way, Robert got this from Macedon, I noticed, because Vess on security is on infosecexchange, which is the same message on server you're on, I think. Yeah, that is where I am. But don't send me anything there, because I'll never see it, he's a read-only guy, or not even a read-only he doesn't read at all, not even that, he's just there, I'm a placeholder guy.
10:18 - Steve Gibson (Host)
Placeholder guy, yeah, just in case it happens someday. Okay, so a bit of a follow-up on the annoyingly named but nicely functioning Privacy Badger from EFF. While assembling today's podcast, I was greeted with this in the middle of a page at a news aggregation site and you know, in the show notes I'm showing this window. It says Privacy Badger has replaced this TikTok widget, and then I can click the big orange button allow once or always allow on this site. My first thought upon seeing that was thank you. I have no interest in having my browser going to TikTok to retrieve whatever it was that this website wanted my browser to have and, in the process, of course, expose itself to TikTok as a first party. Thanks anyway. I don't know what would have been shown in that location where Privacy Badger posted a fill-in, and I don't care.
11:26
While catching up yesterday with my Twitter feed, I ran across someone who was passing along the advice he'd heard from somewhere else. That and I'm talking about it one of our listeners was said hey, steve, thought you'd like to know. He said that UBlock Origin and Privacy Badger should not both be installed because they interfered with one another and because UBlock Origin was a superset of Privacy Badger. So, just for the record, I have seen zero evidence that any of that is true. Looking at the Privacy Badger icon for that webpage I was on, I saw that it had prevented the loading of nine things on that page. It blocked blah, blah, blah dot. Applecom, api podcast dot. Applecom, embed dot. Podcast dot. Applecom, wwwapplecom. So the for Applecom properties. Also, it kept me from going to static Cloudflare, insightscom, google tag managercom, fontsgstaticcom, openspotifycom and tiktokcom, so that seemed very useful to me. For its part, ublock Origin blocked 10 fetches, preventing my browser from exposing itself to four of the pages.
13:00
19 offered domains, including sentry-cdncom and whatever data dog hq browser agentcom is. I was morbidly curious about data dog hq, which describes itself quote the data dog agent is software that runs on your hosts. It collects events and metrics from hosts and sends them to data dog where you can analyze your monitoring and performance data. That's right. Just as I have no interest in having my browser snuggle up to tiktok, I don't need data dog to be collecting any metrics about me. Thank you very much, wow. Needless to say, I've always been happy having UBlock Origin watching my back and I'm equally happy now now having privacy badger as part of that team and data dog be gone. Wow, and you know, leo, it also occurred to me if we didn't have tools like this as most users don't we would have no idea that data dog was hounding you.
14:18 - Leo Laporte (Host)
You know what puzzles me. Why doesn't UBlock Origin stop this? So maybe there's some. You know there are a lot of optional filters on UBlock.
14:26 - Steve Gibson (Host)
Origin Well, have you met EFF. Yeah, you know they don't think that a sunny day is a good thing if there's some way to monitor whether you're looking outside. So you got to. You know the badger it's. You know it's not going to let anything happen, you know. So I mean, like I'm wondering why fontsgstaticcom, but apparently that so three. It appeared on three different sites and the badger said no, no more tracking for you.
14:57 - Leo Laporte (Host)
So what? What site was this? Did you say that you got all this crap?
15:03 - Steve Gibson (Host)
I didn't and I don't want to. I don't want to finger these people. They're actually a really good news aggregator site.
15:09 - Leo Laporte (Host)
They're trying to make a living is what they're trying to do, unfortunately, exactly that's what you have to do. Yeah, stay in age, yeah exactly.
15:16 - Steve Gibson (Host)
Yeah, they're over on sub-stack. So it was, it's, you know, hosted there. Okay, so, because of last week's Bombshell news, I looked around for anything happening on further on the EIDAS 2.0 front. You know, since you know it was such a big news. Now, as you would expect, the register weighed in the following day, on Wednesday, in their inimitable snarky style with the headline bad EIDAS. You know, eidas Europe ready to intercept, spy on your encrypted HTTPS connections. But in their reporting they didn't have anything new to add. Since there's nothing new to add, as I noted last week, we haven't quite reached the ultimatum stage where the OS and browser vendors will simply refuse to turn over the management of global trust to political interests. But given what we just witnessed a few weeks before that, where UK politicians refused to back down until every encrypted messaging provider, including Apple, made very clear that they would withdraw their services rather than comply with a bad law, the next thing we see may be a repetition of that same drama. You know, I think the best way to view this is the way I concluded last week, noting that the management of today's internet and encryption technology is bigger than any single or group of governments. You know that lack of absolute control over their populace doesn't make any governments happy, but it does appear to be that the world, the way the world is shaking out and I think it's clear that you know that's the way it should shake out. So it's been interesting watching this all happen and you know we're still watching it happen.
17:18
So I have two quick news items to share in the world of online cryptocurrency, where you are constantly posing the question what could possibly go wrong? The first is the cryptocurrency exchange. Polonix I guess you know because the good names were taken lost $130 million US dollars worth of assets after hackers drained its hot wallet and I guess the wallet was hot and now its cryptocurrency is hot. Polonix confirmed the hack, paused its transactions and promised to reimburse users' losses, and this is the exchange's second heist, after it was also hacked back in 2014. This $130 million loss ranks it as the 14th largest cryptocurrency hack ever, and the fact that we're ranking them should tell you that there's a problem somewhere. And second, the decentralized finance platform RAFT again not a great name has lost 3.3 million worth of cryptocurrency after a hacker exploited a vulnerability in its platform. The company confirmed the hack on social media and paused the minting of its R, as in RAFT stablecoin, to investigate the incident.
18:56
So the one observation I wanted to make was to once again, as I said, pose our rhetorical question about what could possibly go wrong. You know, when the integrity of the storage of shockingly large amounts of real world, actual money depends upon software that very few people even understand, you know how could that be bad? Yeah, you know you don't have $130 million high-spin ranked as the 14th largest in any industry that has any idea of what it's doing. So I'll just reiterate, you know, to please be very careful and heed the age-old advice to never invest just as in never gambling, more than you can afford to lose, because sooner or later you know again.
19:57
And then this this points to the online side of cryptocurrency. There are people with with cryptocurrency in a wallet and they're very happy with it. You know, I wish I had those 50 bitcoins. I once had my PC, meant for me, in a wallet. Unfortunately, that was the most expensive reinstallation of Windows I've I've ever made. Leo, it's currently worth $1.8 million, oh my god, steve, I'm so sorry, I know, but boy, you know burns.
20:33
I upgraded XP. What's good possibly. What's good possibly be bad about that.
20:37 - Leo Laporte (Host)
Oh yeah, I mean in our defense. We didn't know it was worth anything at the time.
20:42 - Steve Gibson (Host)
Leo, in our defense there was a Bitcoin faucet that was dripping money, Right, I mean you could go get some 50 Bitcoin overnight one night.
20:53
Yes, yes, I solved one hash puzzle because nobody else was doing it, and so it's like I got the answer. Does anyone care? You know we didn't care, yeah, but I do care now, anyway, okay, so, before we run away screaming from the topic of what could possibly go wrong with cryptocurrency, get a load of this one. Uk police are currently in the process of returning around 1.9 million pounds worth of cryptocurrency that was stolen back in January of 2018 by a Dutch hacker. This individual operated a website called iotaseedio, and you're going to love this. As its name suggests, the iotaseedio site was created to generate seed phrases for the iota cryptocurrency wallets, which the wallet's users then apparently used without any change.
22:02 - Leo Laporte (Host)
So who can guess what happened next? Possibly go wrong.
22:08 - Steve Gibson (Host)
That's right. The site's criminal hacker owner was recording all of the seed phrases his site was suggesting that its visitors should use to protect their wallets. That's true, to no one's surprise, other than all of those visitors whose money this guy then stole. The crook broke into their wallets and did just that. He was caught and, following a Europol investigation, was sentenced to four and a half years in prison. What's that expression? A fool and his money are soon parted and wow. So yeah, I'm going to go to a website and I'm going to get the secret key to use for my wallet, because you know how. You know that's what the site does. It gives secret keys to people. They're not secret to the, to the site that gave them. Oh boy, oh boy. Okay.
23:15
Downfall is the name of yet another information disclosure vulnerability that was recently rediscovered in Intel's chips, and, unlike Spectre and Meltdown, this one really has some teeth. Here's what its rediscoverer wrote, and I'll explain in a minute why I'm using that term. He wrote downfall attacks target a critical weakness found in billions of modern processors used in personal and cloud computing. This vulnerability, identified as CVE 202240982, enables a user to access and steal data from other users who share the same computer. For instance, a malicious app obtained from an app store could use the downfall attack to steal sensitive information like passwords, encryption keys and private data such as banking details, personal emails and messages. Similarly, in cloud computing environments, a malicious customer could exploit the downfall vulnerability to steal data and credentials from other customers who share the same cloud computer. The vulnerability is caused by memory optimization features in Intel processors that unintentionally reveal internal hardware registers to software. This allows untrusted software to access data stored by other programs which should not normally be accessible. He wrote. I discovered that the gather instruction meant to speed up access. Scattered data in memory leaks the content of the internal vector register file during speculative execution.
25:06
To exploit this vulnerability, I introduced gather data sampling, which he calls GDS, and gather value injection GVI techniques. Okay so, in the past, whereas we never had any demonstrations for the Spectre and Meltdown attacks because they remained theoretical, the downfall site downfallpage is the URLpage shows videos of 128 and 256-bit AES keys being stolen from another user sharing the same computer. Also the theft of arbitrary data from the Linux kernel and more. All of Intel's core processor architectures, from the 6th generation Skylake to and through the 11th generation Tiger Lake, are affected. So this is 9 years worth of Intel's processors since the 6th gen Skylake chips appeared back in 2014.
26:19
And the attacks using this are practical. Its author wrote GDS, that's his gather data sampling. Gds is practical, he said it took me two weeks to develop an end-to-end attack stealing encryption keys from OpenSSL. It only requires the attacker and victim to share the same physical processor core, which frequently happens on modern-day computers implementing pre-emptive multitasking and simultaneous multithreading. So Intel has released a microcode update which blocks transient results of gather instructions and prevents attacker code from observing speculative data from gathered or, you know, gathered by gather. That's the good news.
27:14
The bad news is that, depending upon how much benefit the processor may have been obtaining from its speculative execution optimization, the impact on performance Intel acknowledges might be as much as 50%. There's one thing all of these vulnerabilities that we've talked about have in common they are all about speculative execution. In other words, intel back in oh, probably 2011, given that it takes about three years to get a chip from original concept out, and the Skylake occurred in 2014. So back around 2011, intel engineers had this terrific idea that, since the laws of physics were making it impossible to just keep increasing the processor's clock. A different way to speed up code was to create a massive overabundance of processor power by having more execution resources all running at as fast as they could go, since they couldn't go any faster. So if you can't make them go faster, just have more of them going as fast as you can and allow that access, apply that access to the task of executing code speculatively.
28:47
The idea is that the processor would be allowed to run ahead by prefetching from memory ahead of the data instructions and looking at them ahead of its actual execution. And if that prefetching system encountered a branch instruction, it would follow both code paths from the branch the one that branched and the one that didn't branch by continuing to fetch and examine those instructions. Then, at some point in the future, once the processor's actual execution had caught up to the branch instruction, then it would know which path to follow and it would, on all the work down. The other path would be discarded. That side channel edge case that Intel failed to pay sufficient attention to was that all of that extra work that ended up being discarded left some traces behind. Memory would have been fetched that didn't end up ever being needed or used, but the cache would have been filled with that and other contents that would have been in the cache would have been evicted to make room. Remnants were left behind in the branch prediction logic that's used to make decisions when insufficient information is available at the time, and on and on and on.
30:16
This has been biting Intel and, to a somewhat lesser degree, amd, for years now. In the author's Q&A on the page he posted the question why is this called downfall? And the author replies downfall defeats fundamental security boundaries in most computers and is a successor to previous data leaking vulnerabilities in CPUs, including meltdown and fallout. In this trilogy, downfall defeats all previous mitigations. Once again, at the start of this, I referred to this author as the rediscoverer of this. Wow, the reason is that Intel was informed of this very vulnerability twice before. Back in 2018, four years after Skylake began this, they chose, for whatever reason at the time, to ignore the problem. Perhaps it was due to the damaging effect it might have on their public relations, or maybe because of the massive performance hit. Any patched microcode would force. Either way, its discovery, complete with ample proofs of concept and Leo, you're playing one now into the video on the podcast ample proofs of concept and source code on GitHub cannot be swept under the rug.
31:55 - Leo Laporte (Host)
So my sense of specter and meltdown was it was so hard to implement that nobody had there hadn't been any exploits, exactly there haven't.
32:02 - Steve Gibson (Host)
This is easier. Now we have one that is practical and the source code is on GitHub.
32:10 - Leo Laporte (Host)
Now we got problems.
32:11 - Steve Gibson (Host)
Now we got problems and, predictably, a class action lawsuit has been filed by five aggrieved so-called victims and their ambulance chasing attorney. It's necessary to show actual, concrete damage rather than to simply be put out by Intel's past behavior. So it's unlikely that this is anything more than a ploy, probably to get Intel to pay out some modest settlement to make this most recent lawsuit just go away. Intel certainly has bigger problems because they have had to patch all the microcode on their processors, because this is really bad. This really does break protection boundaries in the cloud, and I mean it's. You know, this is the real deal.
33:01 - Leo Laporte (Host)
Finally, that's the main threat. Model here is shared processor right. So servers are particularly vulnerable because most websites don't own the computer or the processor. They're sharing it Right.
33:16 - Steve Gibson (Host)
So end user workstation is not a problem because you're unlikely, I mean I mean Nobody's sharing my workstation.
33:22
There. It has been noted, though, that this exploit could probably be used through a browser, so you could go to a website that loads malicious code and then, while you're not paying attention, it's busy using this exploit to try to, you know, get your the secret keys that you've got stored in your computer. So, you know, enterprise users need to be aware of this and cautious. The good news is Intel is on this, finally, and that you know, as we know, updates from Microsoft will bring microcode patches with them, you know, so this will end up getting fixed.
34:08 - Leo Laporte (Host)
And I guess Intel did fix it in every processor after the 11th generation, so they know how to fix it. Yes, without killing performance.
34:19 - Steve Gibson (Host)
No, it's a performance hit.
34:21 - Leo Laporte (Host)
I mean they're not having this To turn off speculative execution.
34:25 - Steve Gibson (Host)
Yeah, this was a real win for them and they're, by their own admission, they're saying a 50% drop in performance, depending upon how much gather was speeding things up. So basically they were. You could say that they were cheating to get this performance benefit, and certainly they were cheating after 2018 when they were told that this could happen and they said we don't think it's gonna be a problem.
34:53 - Leo Laporte (Host)
Is there no way to do speculative execution without this vulnerability? I guess it'd be the question. I mean in Apple's processors. Use speculative execution. It's new Apple Silicon, Everything does. That's a major technique used by modern microprocessors.
35:11 - Steve Gibson (Host)
Yes, and in fact they have a fix for it, which obscures the data that this gather instruction was being used to get. So lock the side channel, don't turn off speculative execution.
35:24 - Leo Laporte (Host)
So exactly, yeah. Yeah, it's interesting.
35:29 - Steve Gibson (Host)
So I think they were insufficiently cautious with these edge cases, which do allow some information leakage. And this is the beauty, the good part of the way the security industry is working now. We would not have any of this if it were not for the academic researchers who were just poking at this and exploring what could be done. There's no money in revealing this. No one's getting paid, it's just researchers who want to.
36:04 - Leo Laporte (Host)
No, this guy's a UCSD, he's a researcher.
36:09 - Steve Gibson (Host)
He's not a hacker.
36:11 - Leo Laporte (Host)
Nope. Why did he feel necessary to put out exploit code, I wonder?
36:17 - Steve Gibson (Host)
Probably out of just an upset over the fact that Intel had been so negligent. Yeah.
36:28 - Leo Laporte (Host)
Well, we've been kind of waiting for this other shoe to drop. In fact I had kind of thought, oh, it's not gonna happen, we're okay.
36:34 - Steve Gibson (Host)
I know, and it took quite a while, and Bruce Schneier's famous reminder keeps coming back Attacks never get worse, they only always get better. And here we have something that's been sitting around for nine years in these chips.
36:55 - Leo Laporte (Host)
Oh, my God.
36:56 - Steve Gibson (Host)
Actually does allow cross process information theft. And, leo, let's talk about some good news from a sponsor.
37:07 - Leo Laporte (Host)
Yes, we're at, we're 30 minutes in.
37:09 - Steve Gibson (Host)
I have a sponsor.
37:10 - Leo Laporte (Host)
Good news available to hand, ready to go? You'll be glad to know. Actually, it's one of our favorite sponsors, bitwarden oh, yes, bitwarden, we love Bitwarden and they say and they love you, steve. They say I don't want to advertise anywhere, but Steve, steve's the show we need to be on. I guess they're right. If you listen to this show, you care about security, but I think it's probably also the case that you're already using a password manager, with any luck you using the best Bitwarden. But maybe it's time to tell your friends and family. There is an open source, free to use, forever cross platform password manager. You can totally trust the one I use. I think Steve uses it.
37:52
By the way, one of the things we like about Bitwarden unlike our predecessor, it's the one we used to advertise. I don't even want to say the name. You know what I'm talking about Is they are encrypting everything, even the metadata. Last pass didn't encrypt the metadata, so bad guys immediately got all the sites you visited which helped them prioritize which passwords to crack, right? Oh, this guy's hanging out on Bitcoin sites a lot Currently, quite so let's see if we can get in this one. So Bitwarden encrypts it all. There's no data leakage at all.
38:27
It also does some really cool things. I love this and I use Fastmail. If you use a Fastmail or any of five different well-known email services that do this masked email, you can use it with Bitwarden so that not only do you create a unique, long, strong password which is the whole point of a password manager it saves it in the vault, encrypts it. You don't know it, you don't need to know it, you couldn't remember it if you tried, but the password vault remembers it. It also does the same for your email address, so it will create a unique masked email address for every site you create a new login for. And because it works with the various email providers, like when I use it with Fastmail, it seems like a strange address to me, but it works. It goes right into my Fastmail inbox and it also helps me track who's selling my emails, by the way. Very handy, so take a look at that. Very strong. Actually, it's now six integrated email services masked emails, because that's really good. You can log into Bitwarden to encrypt your vault after using SSO on a registered, trusted device. That's nice. No master password needed.
39:37
You probably also saw that Bitwarden also supports pass keys. In fact, I was thrilled. I was on a site and it said you wanna use a pass key? I said yes and Bitwarden popped up. I was so happy and said, okay, I'll handle it from here. That means that now my pass keys aren't stuck on a single device with a single provider. It's not just Mac or just Android, it's everywhere I use Bitwarden. Now pass keys kinda make sense.
40:06
Bitwarden also takes security seriously. They have professional third party audits performed yearly, published on their website. The code is all on GitHub, so it's out there Now. They have plans for everybody. As I mentioned, there is the basic free account unlimited passwords, free forever for individuals. By the way, I think these guys are nice, because usually what happens is the company takes away stuff from its free platform right? They just added hardware key support to the free ones. That wasn't the main reason. It was one of the reasons I paid for a premium account 10 bucks a year. Nothing was so I could use my YubiKey, but I don't even need to do that anymore. The free account supports YubiKey's and all of those hardware keys. I'm still giving them the 10 bucks because I really love Bitwarden. It also now will support pass keys in the free account basic version.
41:02
Every Bitward Password Manager user can use pass keys yes, love that. Use a browser extension for that. They also have Teams accounts. That's $3 per month per user. Has lots of Team Sharing features. We're gonna move to the Enterprise Organization Plan. That's $5 a month per user and, as I said, 10 bucks a year for the premium plan. But there's also a family organization plan that's six users for $3.33 a month. This is really the way to go.
41:36
In fact, if you are gonna be at the Open Source Security Summit which is coming up in December, they're gonna be there at the Fourth Annual Open Source Security Summit. This is where businesses and open source enthusiasts and developers and security thought leaders get together to explore how open source software leads to stronger cyber security. Headliners this year include Ryan Krebs, brett Krebs on security, white Hat Hacker and CEO of Social Proof Security. The great Rachel Toback will be there. Ooh and Generative AI Expert and Advisor, zach Kass. So this is a great thing. That's gonna happen December 7th online. Obviously, you don't have to go there. The Open Source Security Summit opensourcesecuritysummitcom. Register now and see Bitwarden there too. I'm guessing they're a big sponsor is probably why they're mentioning him At TWIT. We are big fans of password managers. You know, steve, and I just think if you are not using a password manager, you're doing it wrong. But I want you to consider Bitwarden. If you're not using it, tell your friends and family because it's easy to use and it really works.
42:52
Get started with Bitwarden's free trial of a Teams or Enterprise plan or start it free forever Across all your devices, unlimited passwords, hardware key support, pass key support, free, bitwardencom, slash, twit. I mean, this is why I love Open Source, because these guys, they're not trying to make a buck on you, they're literally giving you all the features that you would want in the free package. And I asked him. I said you mean you're not gonna take these away? He said no, no, we're Open Source, we can't. It's free forever Bitwardencom, slash TWIT. Okay, enough e-commerce, let's get back to Steve.
43:35 - Steve Gibson (Host)
So we've touched on this before, but I wanted to note that Russian officials are preparing to formally ban the use of all VPN services in the country. And I got to use my favorite word again Ross come non-zor, ross come, non-zor. They have been testing blocks for various VPN protocols and services over the past year in preparation for creating a formal blockage. Officials in Russia say that a formal VPN block is needed for the safety of the Russian internet, because you know they believe they have their own, and I think that's just fine, that if they wanted to disconnect from the rest of us, we would lose some listeners. That's unfortunate, but you know the listeners are not the government, so I recognize the difference.
44:33
And, speaking of VPNs, if you're using OpenVPN, check for two security updates. Neither one is super critical, but one of the two could potentially provide access to memory and, as we know, attacks never get worse, they only ever get better. So the point is, openvpn has recently been updated. If you're using OpenVPN, it's probably worth going and checking that out and bringing yourself current, because one of the two is worth patching. Again, not house on fire, but still good to be current. And as I mentioned at the top of the show and Leo, you said what. I've stopped working on Spinrite, and not because I've been distracted by anything else, but because every indication is that both its DOS and its Windows code is well and truly finally finished.
45:32 - Leo Laporte (Host)
Woo hoo, let me get some champagne. Oh, they're cheering out in the hall.
45:38 - Steve Gibson (Host)
It took five release candidates of each one of those to get us there, but there is nothing left for me to do, so I've immediately turned my attention and this was like. I posted that on Sunday and then began working like immediately on the next piece of work, which is updating GRC's servers Windows executable code delivery system to perform code signing on the fly. Until now, code signing has always just been a manual process, and this was fine when I was signing the DNS benchmark or Never 10 or in control, where that one download file would live on for years. But now I need to automate the process so that it can be performed on GRC's server. And of course, the key lives in a hardware security module, since each purchased and licensed copy of Spinrite is unique to its user. So anyway, I'm working on getting code signing automation in place. I think that should happen in the next day or two.
46:51
I just started on Sunday and I solved another problem yesterday morning.
46:55
That was a bit of a puzzle, because it turns out lots of people have wanted to do this but no one has figured out how to do it in the right way, where you're signing a blob in RAM rather than signing a file because you don't wanna have to write the file out to the file system just for the sake of signing it and then send it. The right way to do it is to do it all in RAM. So I think I figured out how to do that and I've also been thinking it's occurred to me a couple of times when I've solved really hard problems and there were a couple that I'd run across that I ought to have some way to share the source of that, so I may start doing that. So I'm leaving a little more legacy of solutions, because I know I'm often going to SourceForge or to if there's a code, something. I can't remember the name of it. Anyway, I'm often finding little bits of help here and there online and I'd like to be giving some back.
47:50 - Leo Laporte (Host)
So I may start?
47:51 - Steve Gibson (Host)
doing that too. Good, yeah, anyway. So I'm gonna get that going. Once we have code-citing automation, then the existing pre-release page at GRC, which I've talked about before, which has only been able to download the DOS component of Spinrite, will be downloading, will be offering the hybrid, basically finished code, which is what I expect. It will be shipping, since it's been now quite a while since there's been anything that's come along. That was serious. This is kind of interesting.
48:24
The problem between the thing that was in Spinrite itself where that moved me from RC4 to RC5, was I've got one really intrepid tester, whose handle is Milq, who set up a constrained RAM environment on a drive that just did nothing but produce errors and he discovered that something in Spinrite was causing the FAQ page we have an online in the program itself is a scrolling FAQ page of like a description of the commands and a bunch of frequently asked questions obviously that when the drive was producing an incredible number of errors, the log of those would end up appearing in the FAQ. So he took a screenshot of it and said well, this doesn't seem very serious, but just wanted you to know. Well, it's serious to me. So it turns out that I allocated 16 megabytes of space for the log, figuring that nobody would ever overflow that. That was 113,359 log lines. It turns out Milq overflowed that and I probably meant to get back to like dealing with the overflow case and I just forgot. So anyway, what RC5 has that RC4 didn't is that if you actually do have a log and this is the scroll back you're able to log to the file till the cows come home until you run out of storage space on your logging drive. This is the scroll back buffer that allows you, while you're in Spinrite, to scroll back and look at prior log entries. Well, when you get to 113,359 log entries now, the log starts wrapping instead of just continuing to grow without limit, which obviously it should have done. Thus, there was no other problem that we ever found on RC4, and now RC5 doesn't have that either, and Milq tested it. It works perfectly. So, anyway, everyone will be able to download the final Spinrite code.
51:02
Then I work on the documentation on the website. I wanna put pictures of the various Spinrite screens and explain what they do and how it works, so that there's online documentation. Then I launch the email facility so that I have a means of notifying all of Spinrite's owners for the last 19 years, and then I get to start on Spinrite 7. So that's where we are. We're getting there. So closing the loop, feedback from our great listeners. I have one from EdgeIT who said great show.
51:40
I've been using Sophos XG, slash, xgs firewalls for my customers for a while. They have had this automatic hotfix feature, which is enabled by default, for many years, and a few years ago when there was a vulnerability, it was patched for every customer while I slept. So you know, and you know Sophos, they're a real security company and they make a good firewall and they've already figured out how to do this. So come on. Everybody else, all the other, you know big appliance vendors need to get going because you know the disasters that we've been talking about the last few weeks are ridiculous to be having at this point where you know, literally multiple tens of thousands of victims are suffering as a consequence of the bad guys beating the good guys to patching their systems. Jim Harbin tweeted hey, steve, long time listener and so glad I can continue to be for a long time.
52:47
More Question around NAS backups. Both you and Leo mentioned synologies and sync thing. I went with a QNAP and have a 30 terabyte of RAID storage in a four bay unit, nice, but outside of this NAS this data is not replicated. What would be the best, most cost efficient way to create some redundancy, other than my single NAS you said long ago, are the old tape backup days.
53:20 - Leo Laporte (Host)
You can still get tape. It's still out there. It's not gone, Wow.
53:24 - Steve Gibson (Host)
So this really is a problem. Spinning magnetic storage has become astonishingly inexpensive, so I doubt there's any superior solution than simply using more spinning storage. As I noted last week, I run RAID six exclusively, so each array has two drives worth of redundancy. So what you might do if you just want another layer of redundancy and access in the event that the entire NAS goes down, which would not be unheard of would be to run just another single spinning drive on some always on machine and keep it synchronized with the NAS. But the bottom line is I doubt that it's possible to do better than spinning drives and then make up for the possibility of their failure with some additional redundancy.
54:27 - Leo Laporte (Host)
What I do, which gives you offsite and full redundancy, is I have a second Synology at work and I bet you CUNAP does this too or has this available. But Synology has a couple of ways you can synchronize to Synologies over the internet. I use HyperBackup, which is one of the free Synology apps. There's also Drive Share Sync, and so the Synology here is always talking to the Synology at home and they're making sure that they are mirrored duplicates of each other, and that gives me real peace of mind. I've got offsite. I've got I mean, it would be hard to lose data at this point, not that I couldn't do it.
55:07 - Steve Gibson (Host)
Yep, I do the exact same thing. I have a pair of Synologies at different locations yeah, there you go, and they are able to see each other through the PF Sense firewall. And then I use Sync Thing at each of my locations to keep the directories I care about on my workstations synchronized to the local Synology NAS, which then clones it over to the other Synology so that when I'm over on my other workstation at the other location, the Sync Thing running there automatically synchronizes it to the NAS in that location and works great.
55:44 - Leo Laporte (Host)
Yeah, I mean lots of redundancy. Yeah, because every machine I have because I have a lot, like you and I'm in different locations has the same documents folder. I mean there's some basic folders, share shared folders, source folder, a sync folder, documents folder, pictures folder, those in audio. Those all get shared everywhere, so I have copies on every computer plus the backups locally and the backups off site. Yeah, I mean Sync Thing is really a great solution, and both these solutions don't require the cloud at all, which is why you spend a lot of money on an NAS. I mean these aren't cheap, as your emailer knows.
56:22 - Steve Gibson (Host)
Jim Right, and again, my feeling is, if you need more redundancy, just set up a system with a spinning drive and use something like. Sync Thing just to make another copy somewhere else.
56:37 - Leo Laporte (Host)
Get it off site, though, if you can.
56:38 - Steve Gibson (Host)
If, you can right. That's really the best thing.
56:40 - Leo Laporte (Host)
Used to mail CDs to your mom. I remember.
56:43 - Steve Gibson (Host)
You're right back in the old days.
56:44 - Leo Laporte (Host)
That was it, that was off site.
56:46 - Steve Gibson (Host)
Wow, that's really true. She thought it was another AOL CG coming in.
56:51 - Leo Laporte (Host)
I don't know why I keep getting these.
56:57 - Steve Gibson (Host)
So Jim Moran Moran said hi, steve, knowing how skilled you are at actually producing a SEM code, I was wondering if you've ever tried to do some malware analysis or exploit development. After some time studying this, I've come to the conclusion that it might be better to step back and actually learn to write a SEM code from scratch first. What do you think? I guess I'm of two minds about that. On the one hand, everything is ultimately assembly code, since that's what our chips still run. Various attempts to create higher level chips have been undertaken. The fourth processor comes to mind. There was actually fourth. Inc actually designed Silicon that ran the fourth language, that interpreted the fourth language directly.
57:54 - Leo Laporte (Host)
And there were Symbolics, made a Lisp machine and I presume it had a custom CPU. I don't know.
58:00 - Steve Gibson (Host)
Yeah.
58:01
So the problem is we appear to be moving in the other direction, right From SISC architectures to risk instruction sets.
58:10
So being able to understand code at its lowest level can certainly come in handy, but on the other hand, we just saw two weeks ago that the code reverse engineering tool, ghidra, was producing high level decompiled code.
58:29
So it just wasn't serving as a disassembler but also as a decompiler, taking the disassembled code up another level to create much more context for what the binary bits underneath were actually doing. The code that the guys who were tracking down the Citrix bleed flaws received from Ghidra was beautiful, higher level code. It didn't know the names of the arguments that the function calls were using, but it named them ARG1, arg2, arg3, and then a human looking at the way those arguments were used could then create the context to understand more about what was going on. But I guess my feeling is, if you're looking at disassembled assembly language, you can learn a lot of assembly language by studying the disassembly. I don't know that you actually need to learn to code that yourself from scratch. These days we do seem to be seeing things moving up to a higher level, and so I think you can still be very effective even without learning assembly language.
59:51 - Leo Laporte (Host)
I mean speaking of moving up. I think we're on the cusp of using AI to generate code. Yes, a lot of people think that people won't be writing even high level code for much longer that they'll be writing codes and reverse engineering code. That's going to be tough.
01:00:05 - Steve Gibson (Host)
We're figuring out what those various variables mean.
01:00:09 - Leo Laporte (Host)
Yeah, Because if an LLM creates code, I don't know where it came from. Well, we hear it.
01:00:17 - Steve Gibson (Host)
Alex is a huge user of this generative AI and he's talked about how he just sort of says what it is that he wants code to do and, in fact, remember that our listener had AI generate the last pass vault decryptor as like a first start, and then he went in and tweaked it in order to fix it further. So we've already seen that happening.
01:00:45 - Leo Laporte (Host)
I should show you I was playing with these new open AI chat GPTs. I'll show it more tomorrow. But one of the things you can do with their GPTs is give them a corpus of information and then have the AI you can tell it. Only give me an answer that comes from this body of information I gave you. So I gave a GPT all of my Lisp books, the greatest Lisp books, the beginning books, the advanced stuff from Peter Norvig and I created a Lisp expert that can write code beautifully and I can ask questions of. I could say, oh, remind me how that for loop works and it will tell me and write sample code. You can even execute the code in the chat GPT.
01:01:32
So this is nice because it's not hallucinating, right? If you had a bunch of PDFs, you know you could do it with 68 or not 8086 assembly. You probably have all of those manuals from Intel and so forth. Put those in there and now you can say write me a sort in assembler and it would do it. It's kind of incredible. I know I'm not a skeptic and AI skeptic, but in this one regard, when they are given a corpus that it can't hallucinate, can't deviate from, it does a really amazing job. It's a little more than spell check. It's a lot more. Yeah, I'll show you at some point, if you want. I also did an Emacs expert. I took all the Emacs reference manuals and put them into it and you can ask it any question. How do I set a font? And it's always easy. Here's the code. Wow, yeah, I mean, I think we're really we're in an interesting world. Let's put it that way.
01:02:34 - Steve Gibson (Host)
Yep, we are. Yeah, so Trevor from InfoSecExchange. He said hi, steve insert often repeated logging back into Twitter for the first time in a long time. Just just to send this feel Well, and again as soon as I get spin right six one done. You know I'll be launching an email facility that will provide another means of communication, so that'll be good.
01:03:02 - Leo Laporte (Host)
Actually, you can just take all the transcripts of this show and put it into a. Gpt. Well, I don't want to say I know.
01:03:11 - Steve Gibson (Host)
But it was my plan for at $9.99. And after here's Steve Bott yeah, Steve Bott's here yeah.
01:03:22
So he said. I've been thinking about crypto and prime factorization lately and how to apply the assume breach way of thinking to this problem. My thinking is assume that a bad actor has, or will have access to a sufficiently capable quantum computer. How could you protect against this? You know something in the context of a messaging app? Public key crypto and Diffie Hellman are both in the crosshairs of quantum computing, since Shor's algorithm can effectively factorize the large primes that RSA depends upon and can efficiently solve the discrete logarithm problem on which Diffie Hellman is based. Most quantum algorithms are also still in their infancy and, as we have seen before, new crypto systems need sufficient and constant beatings until they're deemed acceptably secure.
01:04:19
My first thought was find a way to stop using public key crypto or reliance on Diffie Hellman for your communications with another person. Maybe find a way to get them a symmetric key. Well, how can you communicate a shared secret securely without having an already pre-shared key? You would need to use public key crypto, diffie Hellman, to share the key over the wire, but that transmission could be broken and your secret revealed. So I was thinking about you saying if you really want to communicate privately, strip naked and sit in the middle of a field with a blanket covering both of you while you whisper your secret. Why can't we just exchange symmetric keys with people we interact with physically? We can now share our contact information with another party by touching our iPhones together. How come we can't at the same time, just exchange a list of n number of keys and use those for iMessage or another messaging platform, and then we do not run the risk of intercepted communications being broken? We could then use a single key until there's reason to believe it needs to be changed for any reason and cycle down the list. Anyway, those were just my thoughts. As someone who's interested in, but not in, the business of secure communications Would be happy to hear why I'm thinking about this wrong or why are there better ideas. Anyway, hope you're doing well. Big fan of the show. Thanks, trevor. So Trevor is thinking about all of this correctly, though today, doing what he suggests feels like throwing the baby out with the bathwater.
01:06:12
The largest leap forward we ever made in cryptography was in switching from the early proprietary and secret non-keyed one-off encryption schemes over to open and public cyphers whose specific behavior was specific and set with a key. This, of course, was the invention of symmetric key crypto. The next huge step forward was the invention of asymmetric crypto, which gave us the ability to have public keying negotiations without fear of eavesdropping and with the incredible power that flows from the use of having separate public and private keys, each with their own roles. In the tremendous power of asymmetric keying, it is difficult to imagine returning to the limitations of a purely symmetric keying only world, for example. One of the other features made possible by asymmetric keying is the ability to have perfect forward secrecy, since asymmetric keying allows us to encrypt under a different symmetric key for every new connection or conversation. This means that if a symmetric key were ever to somehow escape, only that single conversation would be at risk. Neither any other past conversations nor any in the future would be subject to disclosure. This is a powerful feature that we lose if we are unable to safely negotiate new symmetric keys. So Trevor is right that it's only the asymmetric keying that's put at risk by quantum computing, and he's right that the new quantum safe replacement algorithms need time to mature and be tested. But since virtually all of today's applications are based upon asymmetric keying, I cannot imagine like not having that and going backward.
01:08:31
The good news is that the industries.
01:08:33
Inertia, which we spent so much time lamenting on this podcast, will not pose a problem in this regard for this industry, closed systems like apples and signals and others will be able to move seamlessly to quantum safe crypto overnight, and open systems like the web can be enforced from the end with the fewest players, namely the browsers.
01:09:06
Once Google announces that Chrome and Chromium's will have a drop dead date for non quantum safe algorithms at some point well in the future, web servers will have no choice other than to support the new safe standards or find their visitors receiving scary looking warnings meant to put pressure on those server operators to get their act together, and at some point, chrome and other browsers will stop being willing to connect all together.
01:09:39
We saw, for example, that there was a minuscule support now for TLS 1.0. Everything is 1.0 and 1.1, everything is 1.2 and 1.3. That happened pretty quickly, and that happened because support for 1.0 and 1.1 was withdrawn, and if your browser won't use it, your server can't serve it. So I suspect that the wisdom we're already seeing by the industry moving forward on next generation crypto, apparently well before it's actually needed, will serve us well and will likely keep us ahead of the day when quantum computing is first able to crack any asymmetric crypto. So I think in that in this instance it makes a lot more sense for us to move forward rather than backward, especially when what was back there was so limited compared to what we have today.
01:10:45 - Leo Laporte (Host)
On the other hand, quantum computing is not necessarily around the corner.
01:10:50 - Steve Gibson (Host)
I completely agree. They had a big party when they've managed to factor 37. So, wow, five bits or six, rather six bits. Wow, that's great. We used to be four, now it's six, we got a way to go. We're okay, because they got to get out to 1024 or 2048 or 4096.
01:11:16 - Leo Laporte (Host)
We got a way. Is it the case that if you forced everybody to use quantum safe crypto, it would be safer in a non-quantum world too?
01:11:26 - Steve Gibson (Host)
Well, we think, because the problem is it's still attackable and there was one of those algorithms that was believed to be ready for post-quantum, and they found a flaw in it. And it got withdrawn. So it's not the case that there's some new special magic. Because it's quantum safe, that then means it is automatically safe for non-quantum attack, that's not the case, so you'd have to test them both.
01:12:03
Yeah. So, for example, leo, we are absolutely relying on the fact that nobody is going to somehow figure out how to factor large numbers. If that happens, it's game over. Yeah right.
01:12:17 - Leo Laporte (Host)
And I mean like without a quantum computer and just some algorithmically say, oh you know, you can do that, it's pretty easy. And then, yeah, we'd have to do everything over, we'd be right, the Cree Crypto would die. So far, by the way, it has resisted all attempts to do that.
01:12:37 - Steve Gibson (Host)
Amazingly so. And I mean, believe me, the prize. As I was lamenting, there's no Nobel Prize for math, but, boy, you'd be tempted to make one. You make one if someone could come up with a way to factor huge numbers.
01:12:54 - Leo Laporte (Host)
That's because a lot of time has already been spent. You'd get a Fields Medal, for sure You'd get something.
01:12:57 - Steve Gibson (Host)
Yeah, yeah, okay. So someone in GRC's news group asked modestly. He said I feel really embarrassed about this, but I've never really understood how the root store in the OS and the keys in the browser give the protection or, as in last week's podcast mentioned, how having a key from a bad source like you know, a state government allows intercepted traffic to be decrypted, even if I was logging into, for example, my local supermarket. Is there a nice concise explanation anywhere to help me and a follow up with the more complex aspects? I'm looking for some context to start my understanding on a sound footing. Thanks, and so here's what I wrote. I said. Well, I should first preface this by saying that I do occasionally receive tweets from people who say that they don't understand all of what's said on this podcast, but they get enough from it that it's still worth their while. You know, somebody made a comment about sipping from a fire hose, so I thought that this person's honest question might be appreciated by others who might also feel sometimes a little bit left behind. So, very clearly and concisely, here's how all that works, and we haven't actually talked about it for many, many years, so it's worth a little refresher.
01:14:43
When a browser connects to a web server. During that so-called connection handshake the server, the remote web server, sends the browser a claim of its identity in the form of a digital certificate. A certificate is nothing more than a collection of information fields which, after having all been set correctly, are then signed. After the certificate has been signed, it becomes tamper proof. Any change in its data will break its signature. In the case of web servers, the certificate that the web server sends to the browser will have been signed by a certificate authority, and a certificate authority is nothing more than its name suggests. It's an organization that the world and the world's browsers have all agreed to trust. These certificate authorities go to varying degrees of effort to independently verify the identity of the organizations whose certificate they sign. So if the certificate authority says that the entity presenting this certificate is, for example, joe, and if we trust the certificate authority to have done its business properly, then we trust that this is indeed Joe, if the certificate that Joe is presenting us, signed by the certificate authority, is valid and we trust the certificate authority. So it's sort of transitive trust. So now the question is which certificate authorities should we trust? And that's where the root store comes in. Certificate authorities also have their own certificates which attest to their identities, and since they trust themselves to be who they say they are, they each sign their own certificate, which sounds a little weird at first, but that's the way it works. So what we refer to as the root store is the collection of certificates belonging to all the certificate authorities whose signatures of website identity certificates we have decided to trust. So now, when a website presents the browser with a claim of its identity which will have been signed by some certificate authority, the browser looks in its root store for the matching certificate of the certificate authority that signed that identity claim. If it's found that authority's certificate contains the public key, that's then used to verify the signature of the website's certificate. Okay, so that's part one. That's how the system works.
01:18:02
Part two is how traffic interception can occur. We've often talked about network traffic interception. The traditional term for it is man in the middle, meaning that some entity arranges to place their equipment in the path of communication so that they're able to monitor everything that flows through them. Normally, the use of HTTPS for web traffic, with its TLS for encryption, would render this ineffective, since all of the traffic moving past would be encrypted. But if the man in the middle themselves was also a trusted certificate authority, the man in the middle could pretend to be the website at the far end of the connection. So when the user was attempting to connect to, say, a racy dating site, that appliance in the middle would create and sign a web certificate for that racy dating site on the fly and return it to the user's browser. If that appliance's certificate was trusted by the browser, no red flags would be raised, the padlock would be present, the connection would appear to be secure and the user would 100% believe that they had connected directly to the racy dating site. But they would have instead actually connected to the appliance that has interposed itself in the middle, where all of their traffic, their username, their password and their cookies and everything they did while at that site would be decrypted and made available to that appliance. In order to complete the illusion, the appliance itself would have made the connection to the dating site, pretending to be the user's browser, so it would pass along everything that transpired in both directions, while being privy to the entire dialogue, without any encryption to get in the way.
01:20:26
Now this is already exactly what's being done in corporations that deeply monitor all of their employees' communications. To do this, every web browser in the enterprise must receive and accept that middle box appliances certificate, but that's only within the enterprise. This allows for full, transparent, deep packet inspection of all of the enterprise's network communications. And this is precisely the power that the EU is saying it wants for itself and for all of its member countries. Article 45 of the EIDAS version 2 insists that, without any oversight or governance, any member state can provide a certificate that all web browsers must, as a matter of European law, blindly and fully accept and trust without question. Being anything, any of those certificates have signed would then be trusted, and there's only one possible reason for them wanting this, which is to allow for on-the-fly internet web traffic interception, exactly as happens inside corporations, and that's acknowledged.
01:22:06
Their claim and I believe their hearts are probably in the right place is that they want to have the ability to provide additional identity verification of websites for their citizenry. They want to be able to inject top-of-page identity assertion banners into EU website properties to provide an additional assertion of a site's trustworthiness. It must be because these lawmakers didn't come up with this. It must be that some misguided techie sometime in the past cooked up this idea and sold it to the EU's legislators, sold them on the idea. This techie explained that if they could get their own certificates installed into the world's few web browsers and operating systems and after all, there are not many of those then they would have the ability to inject whatever they might wish to like national emergency warnings or other public interest messages into every one of their citizen's downloaded web pages.
01:23:24
The trouble is that the EU and its member nations are very different from the employees of a private organization. Any time an employee doesn't want to be spied upon, they could use their own smartphone to circumvent their employer's network and, of course, an employer's private network is just that a private network. The EU wants to do this for the entire public internet, from which there would be no escape. So it seems quite clear that this is not going to happen, but it's the exact way that it doesn't happen. That should prove quite interesting, and we will certainly be following along on the podcast and Leo. We now have the much anticipated windshield barnacle.
01:24:24 - Leo Laporte (Host)
It's in the show notes. Thank you, Simon Zarafa. Without it, where would we be without you?
01:24:30 - Steve Gibson (Host)
That is exactly right. Our frequent tweeter, Simon Zarafa, sent me a photo which raised more questions than an answer.
01:24:39 - Leo Laporte (Host)
This must be the UK. I don't this couldn't be in the US. Nope.
01:24:43 - Steve Gibson (Host)
It is all over the US and it is a big hit. We're going to get to the Cheyenne City Police and what they think. For those who are not watching the video, what we see is a huge bright yellow slab which is covering most of a car's windshield. It's about an inch thick and is hinged in the center. In the upper right corner we see a membrane style keypad and a display and along with the red warning do not move this vehicle.
01:25:17
In the lower right we see what is apparently the name of this thing, which is just too wonderful all by itself, since it's called the barnacle, and I love everything about this. The reason it's the barnacle is that underneath two large full contact suction cups, one on each half and if you scroll down, leo, you'll see it. I have a picture from the driver's side Two large full contact suction cups, one on each half, are adhering this bright yellow eyesore to the windshield and, like any good barnacle, it will not let go. Its creator claims that it generates in excess of 1000 pounds of resistance to being removed. So you return to your car to find that this bright yellow barnacle has attached itself to your presumably wrongly parked car. Either the meter ran out. You parked in an unauthorized location, you're taking up two parking slots, or perhaps you have several years worth of unpaid parking tickets and the barnacle has just caught up with you.
01:26:52 - Leo Laporte (Host)
See, now we have the boot. You've seen the boot. This is the replacement, this is the evolution of the boot. What's wrong with the boot? The boot is the thing you clamp onto the tire, so it can't drive away, just wait.
01:27:06 - Steve Gibson (Host)
So the barnacle has caught up with you. Now what? Now what? This large yellow thing is stuck to your windshield, totally obstructing your view from the driver's seat and making it impossible to drive. No way. So you are reduced to visiting the website that's shown on the barnacle or calling the toll free number printed there. You identified the device instance to the website or the operator on the other end or maybe it's a bot by its very clearly posted serial number.
01:27:44 - Leo Laporte (Host)
Now I'm getting the advantage.
01:27:47 - Steve Gibson (Host)
You're told how much you owe, which must be paid in full on the spot by credit card. Once you have entered your credit card payment information to pay the parking fine, you're told that your account has also been charged a separate refundable fee for the barnacle itself, whose return to a nearby receptacle you will now be responsible for once the device has released itself from your windshield. After agreeing to this secondary contract, you're given the device's current one time release code, which you enter into the membrane keyboard and then, presumably with a sigh of releasing section, the barnacle releases its grip on your windshield. You then refold it in half and slip it into the conveniently located nearby parking lot return stand. Oh there's one nearby.
01:28:49 - Leo Laporte (Host)
That's nice, yes.
01:28:51 - Steve Gibson (Host)
Yes, they have the conveniently located. Yes, the barnacle is equipped with GPS and will sound an excruciatingly loud and piercing siren if it detects that the car is moved after having been barnacled. Ah Now you could drive with your cameras.
01:29:13 - Leo Laporte (Host)
I know I could in my car.
01:29:15 - Steve Gibson (Host)
Right, yeah, right. The traditional way of dealing with scoff laws who ignore their parking tickets or other parking related violations is to boot a wheel of their car to prevent it from being driven. The trouble is this requires two visits from the booter, one to affix the boot and another to remove it, so the barnacle creates what is essentially self-serve. Unbooting A parking ticket slipped under a windshield wiper is easy to ignore, but affixing a barnacle to a windshield can be done quickly and easily. It's going to generate far more revenue and has a side effect.
01:29:59 - Leo Laporte (Host)
Everyone passing by can see it too, quite visibly barnacled. Yes, the UC Medical.
01:30:06 - Steve Gibson (Host)
the UC Davis Medical Center said our parking and transportation department has been using the barnacle for over a year.
01:30:15 - Leo Laporte (Host)
Oh Lord, this is actually almost offensive to me, but okay.
01:30:19 - Steve Gibson (Host)
It's lightweight, easy to maintain and store. Our parking enforcement team loves the fact that this device can be deployed in under five minutes. It has certainly captured the attention of scoff laws and onlookers. The barnacle enabled our department to recoup over $40,000 in outstanding parking citations. The Cheyenne police said quote thanks to the barnacle we increased collections by $30,000. In addition, people see the barnacle on a vehicle which prompts many to pay their own outstanding tickets. Yeah, you don't want to get barnacled, so they don't get barnacled. Yeah, they said.
01:31:06
The presence of the barnacle is also causing more to abide by city parking rules in the first place, and we've written 1,000 fewer tickets. We collect more parking fines and write fewer tickets. It's a win-win for the city of Cheyenne. So anyway, it's barnacleparkingcom. Youtube has a lot more for anyone who's interested. You can imagine that annoyed parkers have come back to their cars to found the barnacle and have taken pictures and made videos and such. Anyway, I thought it was a very clever use of technology. Device itself does not need any cellular radio. It just needs an inexpensive GPS receiver to detect whether the driver is somehow moving their car. Otherwise, it just uses a combination unlock on a keypad and the driver who removes the device is responsible for its return and recycling in the facility where it was attached. I think it is genius.
01:32:11 - Leo Laporte (Host)
We're going to see a lot more of these, I think.
01:32:14 - Steve Gibson (Host)
Yep, they are. They're really taken off Apparently. They've become incredibly popular on university campuses, where students are just you know, have a reputation. Yeah, they're just scoff laws. It's like I'm going to park wherever.
01:32:28 - Leo Laporte (Host)
I want to. It's $250 per barnacle per month, but how many barnacles will you need? Fewer and fewer as you use it. Boy, they're making some money on those barnacles. Yeah, that's good money.
01:32:39 - Steve Gibson (Host)
Unfortunately, I'm sure they have a patent on it, Otherwise there would be, you know, barnacle bill and other offshoots. Okay, okay. So last week I mentioned having finally landed upon a series of military hard science fiction that I was really liking. A day later, I decided that I needed to share my find with John Selina, aka, you know, Twits Jammer B. Here's what I wrote to John, because of course he's an inveterate sci-fi.
01:33:15 - Leo Laporte (Host)
Oh, he loves your recommendations yeah.
01:33:18 - Steve Gibson (Host)
So I said, john, after having real trouble putting the fourth book in the long series down in order to sleep or do anything else other than consume it. I'll be telling the podcast audience about it next week, which is what I'm doing right now, but I wanted to tell you what I found. Being the voracious sci-fi reader that you are, you may have already run across the author, md Cooper. Mallory Cooper, who has created an extensive future universe for humankind under the banner of Eon 14, a-e-o-n-14. In terms of the overall timeline, where I began without system, was not the earliest in the timeline, but it is the first book Mallory wrote. So she and her co-authors went back later and filled in the earlier timeline. Here's what she explained she said whether you're a new reader or you have a hundred titles under your belt, one thing is for sure Eon 14 is huge. Hi, my name is Mallory Cooper, md Cooper, and I created Eon 14 as an imagining ofa possible future history for humanity.
01:34:42
The story covers hundreds of characters sweeping across over 10,000 years. If you're just getting started, I recommend beginning where I did, without system. You can also check out the primer on the 42nd century to get yourself acquainted with the setting. So it's Eon A-E-O-N-14.com. Everything is Kindle Unlimited and Audible is available. It's possible to grab a single, what you called an omnibus that contains the first four books in a single download. Oddly, this Intrepid Saga includes a fourth book. It's the next book in the next series and this is the book that really hooked me. Book number four, I mean one through three were great, but four I just could not put it down. Things have really started to come together.
01:35:43 - Leo Laporte (Host)
They look a little pulpy. Is it pulpy?
01:35:47 - Steve Gibson (Host)
So here's what I wrote. So I finished book number four and I'm into the next one, and it has not disappointed. John replied to my first email that the timing of my recommendation was perfect for him because he had just finished the book for Stacey's book club and needed something next John Scalzi book Kiju Preservation Society, which he loved.
01:36:14
So I've always shared my sci-fi reading discoveries, and boy we have had some wonderful reading through the years of this podcast. So I wanted to share this one too. I, just an hour ago, asked John if he had any feedback. I cannot share all of what he wrote, since I don't want any spoilers, but part of what he replied was, quote they've made it to series and they're planning their visit to Callisto, quite enjoying it.
01:36:45
Exclamation point Love the AIs some of them have in their heads and so much cool tech. So it's still early for him and a lot more ultra cool tech is in store, but I would say that it's been a hit for John too. So the series may not be for everyone. It is more pulpy, campy, space operatic and in some ways a lot more fun and frolicy than any of Peter Hamilton's, for example, wonderful works, and it does offer a lot of action. Lots of stuff gets blowed up and there's a never-ending stream of very cool tech. It is by no means highbrow, so I won't attempt to defend it on that basis, but I've read enough to be able to hardly recommend it, and I am having a lot of fun with it.
01:37:40 - Leo Laporte (Host)
I can't wait. By the way, it's also available for free on Audible if you're an Audible subscriber. So she obviously made a deal with Amazon, a deal with the devil, but that's good for us. We can see it.
01:37:54 - Steve Gibson (Host)
So yeah, and of course, kindle Unlimited for me. We now know that Kindle Unlimited plan authors are remunerated based upon the pages that are actually read, and it's too bad that rereading pages probably doesn't create a bonus, since there are many passages I have enjoyed more than once. I mean it is really good. And something happened, I have to say, at the beginning of book four where the writing seemed a little bit less great. But maybe it was just a bad time, I don't know, but it got fixed. So if anyone gets into the beginning of book four and say what happened, just hang in there a little bit longer, because it fixes and then it really takes off.
01:38:48 - Leo Laporte (Host)
I'm downloading it now. I'm going to listen on the way home, I hope it works for you. Yeah, the cover is so pulpy, I get the idea.
01:38:59 - Steve Gibson (Host)
Oh and well, so it's easy to find eon14.com. I wrote in my notes and, speaking of 14, if that's your age, you'll also enjoy all of her books. Cover art.
01:39:12 - Leo Laporte (Host)
Yeah, there's sexy covers, yeah, yeah, well, that's okay. I mean not super, you know she's just, it's a fairly skin tight spacesuit, that's all.
01:39:21 - Steve Gibson (Host)
That's all I'm saying. Space suits Leo.
01:39:24 - Leo Laporte (Host)
You don't want a lot of excess fabric.
01:39:27 - Steve Gibson (Host)
Just gets in the way. That could just cause trouble.
01:39:30 - Leo Laporte (Host)
Yeah, it looks like the hero is a woman, so that's good.
01:39:34 - Steve Gibson (Host)
Actually, yes, all of the main characters. I mean we have guys around, but they're just sort of to keep the women busy.
01:39:44 - Leo Laporte (Host)
That's as it should be, I believe. Yeah, let the women do the work, we'll just, we'll be their toys. That's good, I like it. Yeah, okay, thank you for the recommendation. And this came from John Slanina or no, for me, I found it, you found it, john loved it.
01:40:03 - Steve Gibson (Host)
I had read the first book, or maybe the first three at some point, but then, you know, something shiny came along and distracted me. Yeah, now I'm back to it. I read them all again and really liked them again. I thought, okay, and boy, it's now. I can't wait to be done with a podcast.
01:40:20 - Leo Laporte (Host)
Oh wow, that good. Well, me neither, then Should.
01:40:23
I do a third ad and let us move along. That's where we're going to talk about what if a bit flipped? What if those cosmic rays are hitting us all the time? Our show today brought to you by our good friends, the studio sponsors, aci learning and you know them because everybody who listens to this show knows IT Pro TV. In fact, uh, it Pro TV started their whole business on this show and when we were out there in Gainesville visiting their studios, everybody said say hi to Steve. I mean every like every single person there said say hi to Steve. So I know you know it.
01:40:59
But I want to tell you about the merger with ACI learning and what's done for you. First of all, if you're in IT, congratulate yourself, and if you're thinking about getting into IT, you should. With today's IT talent shortage, whether you operate as your own department or a part of a larger team, your skills got to be up to date. 94% of CIOs and CSOs agree. Attracting, retaining talent is job one. There's so many openings out there and you know. If you've already got the job, hey you're. You're sitting in the cat bird seat, but you better be getting better and smarter and and working harder to keep your company more secure. Right. That just makes you more valuable. With ACI learning, you can access more than 7,200 hours of content. That's that's practically more than the show ACI learning consistently at. I think it is more than a show actually come to think of it. Aci learning consistently adds new content to keep you at the top of your game, and you and your team will love it because it's entertaining. Now, it's not frivolous, but the people who are doing these courses are experts in the field. I mean, they're true experts, but more than that, they care, they're passionate, so they make it engaging. They they enjoy what they're doing, and so you'll enjoy learning. That's no wonder, then, that ACI learning's completion rate is 50% higher than the other guys.
01:42:24
Aci learning also has some great tools. You like cyber skills, a solution you can use to future proof your entire organization, not just the IT department. It's a cybersecurity training tool. So it's for everybody, especially for the non IT professionals with cyber skills, who get flexible, on demand training covering all the things you know we cover on this show, like password security, what a phishing scam is, how, what it looks like, how to avoid them, how to detect them, malware prevention, network safety and, of course, because it's from ACI learning. You're going to enjoy it. Your employees will. It's so much better than the training they've been getting. You know that awful stuff that we all had to sit through with you with this stuff. It's fun. Your employees will stay motivated, engaged throughout the process.
01:43:12
The material is easy to follow. It all starts with a one hour overview where you and your employees will gain attack specific training and then knowledge check assessments afterwards based on common cyber threats they're going to encounter, guaranteed on a daily basis. But there's also bonus courses after you finish the hour documentary style episodes that are beautifully produced and full of information, but also enjoyable to watch. Your employees will be learning about cyber attacks and breaches and they can do it at their own pace, in their own style. That's kind of the watchword for ACI learning. You know the curses are short. You can watch them on a break or at lunch and you're going to. It's the kind of stuff you're not going to want to put down.
01:43:56
Aci learning helps you invest in your team and entrust them to thrive, while increasing the entire security of your business. Boost your enterprise cybersecurity confidence today with ACI learning. Be bold, train smart with ACI learning. Visit goacilarningcom. Slash twit as a twit listener, you can get up to 65% off an IT pro enterprise solution plan biggest discounts they've ever offered. But it's just it's dependent on the size of your team. So fill out the form to get the exact quote and they'll help you design a plan. They've got great people to help you put it all together. Goacilarningcom slash twit. We thank ACI learning and IT pro for their support all these years and we're thrilled that they bought studio sponsorship for 2023. That was really great. It made it possible for Steve to tell us about BitFlips. Steve.
01:44:55 - Steve Gibson (Host)
So we have a classic case of attacks never getting weaker, only ever getting stronger. In this case, a theoretical weakness that was first posited 27 years ago, back in 1996, has been found to be practical. It's blessedly rare, but still practical. What this means for us today is that the private keys protecting some SSH servers which use RSA keys can leak to an entirely passive observer and for any reason, a mistake is made during the generation of the RSA signature. So the first of two papers from back then was titled Memo on RSA Signature Generation in the Presence of Faults Ways. Into this paper the author writes this implies that even if there is the tiniest probability that an error occurs during RSA signature generation, the generator of an RSA signature must make sure that each signature generated is indeed correct. The following year, in 1997, another paper was published, titled On the Importance of Eliminating Errors in Cryptographic Computations. The abstract of this paper paints the picture very clearly and a little starkly. They say we present a model for attacking various cryptographic schemes by taking advantage of random hardware faults. The model consists of a black box containing some cryptographic secret. The box interacts with the outside world by following a cryptographic protocol. The model supposes that from time to time, the box is affected by a random hardware fault, causing it to output incorrect values. For example, the hardware fault flips an internal register bit at some point during the computation. We show that for many digital signature and identification schemes, these incorrect outputs completely expose the secrets stored in the box. For example, the secret signing key used in an implementation of RSA is completely exposed from a single erroneous RSA signature. So the point is this fundamental brittleness of RSA has been known for 27 years. Our primary takeaway at this point is the somewhat surprising news that, terrific as the RSA public key cryptosism is, it is also quite fragile to information disclosure in the event of a computational error. If any mistake is made for any reason during the computation of an RSA signature, that mistaken signature, along with any valid signature made under the same private key, can be used to completely expose that server's private key From there. This allows the server to be transparently impersonated by anyone who can arrange to place themselves in the information flow.
01:48:41
Red Hat considered the implication of this back in September of 2015 with regard to TLS connections. Their piece was titled Factoring RSA Keys with TLS Perfect Forward Secrecy, and this is what they found. They wrote back in 1996, referring to the first paper, lennstrid described an attack such that if a fault occurred during the computation of a signature, an attacker might be able to recover the private key from the signature. At the time, the use of cryptography on the internet was uncommon and even 10 years later most TLS or HTTPS connections were immune to this problem by design because they did not use RSA signatures. This changed gradually when Forward Secrecy for TLS was recommended and introduced by many websites. We evaluated the source code of several free software TLS implementations to see if they implement hardening against this particular side channel attack and discovered that it is missing in some of these implementations. In addition, we used a TLS crawler to perform TLS handshakes with servers on the internet and collected evidence that this kind of hardening is still needed and missing in some of the server implementations. We saw several RSA key leaks where we should not have observed any at all. So this issue has been quietly lurking in the backs of the minds of cryptographers for decades, which brings us to today and the recently discovered and confirmed vulnerability of many I should say several SSH servers.
01:50:48
A group of four researchers from UC San Diego at La Jolla have just published their research under the title Passive SSH Key Compromise Via Lattices. It will be presented. Their research will be presented two weeks from now during the upcoming ACM SIGSAC conference on computer and communication security, which is CCS 2023 occurring. It's being held this November 26 through the 30th in Copenhagen, denmark. They wrote we demonstrate that a passive network attacker can opportunistically obtain private RSA host keys from an SSH server that experiences a naturally arising fault during signature computation. In prior work this was not believed to be possible for the SSH protocol because the signature included information like the shared Diffie-Hellman secret that would not be available to a passive network observer. We show that the signature parameters commonly used for SSH there is that for the signature parameters commonly used for SSH, there is an efficient lattice attack to recover the private key in case of a signature fault. We provide a security analysis of the SSH, ikev1 and IKEV2 protocols in this scenario and use our attack to discover hundreds of compromised keys in the wild from several independently vulnerable implementations. So the best way to get a better feeling for what's going on here is to look at how they summarize their overall findings.
01:52:48
They wrote RSA digital signatures can reveal a signer's secret key if a computational or hardware fault occurs during signing with an unprotected implementation, using the Chinese remainder theorem and a deterministic padding scheme. This attack requires only a single faulty signature, the public key and a single GCD Greatest Common Deviser computation, and it has been exploited extensively in the cryptographic side channel literature on active fault attacks. In a 2015 report and this is the one, the Red Hat report Weimer observed that the same vulnerability could be exploited in the context of TLS by an attacker without physical access to a machine, simply by connecting to machines and waiting for a fault to occur during computation. He traced several of the failures he observed to failing hardware. In 2022, sullivan et al observed that this flaw remained exploitable on the open internet and used passive network countermeasures to compute TLS private keys from vulnerable implementations that appeared to experience hardware failure. However, this vulnerability was not believed to be realistically exploitable in the context of other popular network protocols like IPsec which, of course, is extensively used for VPNs or SSH, because the signature hash includes a Diffie-Hellman shared secret that a passive eavesdropper would be unable to compute, thus ruling out the single signature Greatest Common Deviser attack, because a passive adversary can typically collect significantly more data than an active adversary, who must participate in every Diffie-Hellman exchange. This belief represented a significant underestimate of the cryptanalytic capabilities of such passive adversaries against SSH and IPsec compared to TLS version 1.2.
01:55:03
In this paper, we show that passive RSA key recovery from a single faulty signature is possible in the SSH and IPsec protocols using a lattice attack. In this context, a passive adversary can quietly monitor legitimate connections without risking detection until they observe a faulty signature that exposes the private key. The attacker could then actively and undetectably impersonate the compromised host to intercept sensitive data. We cast the key recovery problem as a variant of the partial approximate common divisor problem and we show that this problem is efficient to solve for the key sizes and hash functions used for SSH and IPsec. And finally, we then carry out internet-wide scans for SSH and IPsec to measure the prevalence of vulnerable signatures in the wild. We find multiple vulnerable implementations that appear to be due to different classes of hardware flaws.
01:56:15
We also carry out a retrospective analysis of historical SSH data collected over the course of seven years and find that these invalid signatures and vulnerable devices are surprisingly common. Over time, our combined data set of around 5.2 billion SSH records contained more than 590,000 invalid RSA signatures. We used our lattice attack to find more than 4900 revealed, to find that more than 4900 revealed the factorization of the corresponding RSA public key, giving us the private keys to 189 unique RSA public keys and thus the servers that we're using those. We also analyze passively collected SSH network data. In addition to the signature vulnerabilities we were searching for, our analysis gives us a window into the state of SSH, ikev1 and V2 deployment landscape. We observe a number of vulnerable and non-conformant behavior among IPsec hosts in particular. Okay, so, by passively examining SSH handshake traffic on the Internet and even recordings of previous handshake traffic, they were able to obtain the secret private keys belonging to 189 different devices on the Internet. The other thing they had to say that was interesting was what they learned about the SSH devices which were occasionally generating invalid and thus vulnerable signatures. They said our research identified four manufacturers of devices susceptible to this key recovery attack.
01:58:23
We disclosed the issue to Cisco on February 7 of this year, 2023, and to ZikeCell on March 1, 2023. Both teams investigated promptly, although limitations in the historical scan data made it challenging to identify the software versions that first generated the vulnerable signatures and reproduce the issue. Cisco concluded that Cisco ASA and FTD software had introduced a stable mitigation in 2022 and was investigating mitigations for Cisco iOS and iOS Xe software. Zikecell concluded that the issue had affected ZLD firmware versions version 3.30 and earlier which had been end of life for years. By the time of our disclosure, the ZLD firmware had begun using OpenSSL, which mitigates this issue.
01:59:32
Our attempts to contact Hillstone Networks and MoCana were unsuccessful and we submitted the issue to the CERT Coordination Center on May 18, 2023 for assistance with disclosure. We received no additional information from CERT during the 45-day disclosure period. We considered notifying operators of affected devices whose keys had been recovered, but we determined this would be infeasible. Even after combining publicly available data with the historical scanning data, we were unable to determine which organization was responsible for a particular device, whether the device was still in use today or up-to-date contact information for the device's current operator. We also lacked practical and actionable advice for owners of affected devices until the manufacturers completed their investigation. So now we knew that communication protocols using RSA signature generation which have not been explicitly hardened against the possibility of mistaken signature computation are prone to having their private keys stolen if anyone is watching and paying attention and in today's world it would be difficult to imagine that, with papers about this dating back to 1996, 1997, 2015, and 2020, that the NSA might not have already done the math and may have been keeping quiet about this in case it might come in handy.
02:01:13
We don't know what we don't know, which is why I think that this sort of academic poking at the protocols we have in use can be so very important. I titled this podcast what if a Bit Flipped? And now we know what if a bit flipped. What we still don't know is why that bit may have flipped. The literature doesn't have a lot to say about it, but it boils down to cosmic rays just happening to hit a microscopic transistor at the right moment to cause an unrepeatable event or a systems power supply at the beginning of its death spiral.
02:01:57
As we know, I had this happen to me recently with my NetGate SG-1100 router. On the surface, when it was working, it was working, but was it really? What if I'd been using it as an SSH endpoint? Might it have glitched at just the right moment and caused a signature mistake? I'm sure that PF Sense was using open SSL, which had already been hardened against this a long time ago. But my point is, some hardware out there hasn't been, and if the hardware is having a problem, then that can result in a complete disclosure of that system's private keys. I think that the best takeaway is that we all sometimes see our computers do something weird and inexplicable. Since software bugs are clearly by far the most common cause, we would rarely think that we just experienced a cosmic ray event.
02:02:57
But, who knows? And the cause of a mistaken signature computation doesn't have to be hardware. A device driver might not have properly restored the machine's registers following a hardware interrupt that happened to occur right in the middle of that critical signature computation. Not long ago we tracked down some weird one-off problems in spinrite to exactly that cause. After I wrapped spinrite in its own protection, we've never had another such error occur. The best news is that the crypto industry has learned that some cryptographic processes are highly sensitive to mistakes occurring from any source, even cosmic background radiation, and the systems that were late to protecting themselves have been identified. Getting them fixed in the field may never happen, but new systems won't be shipping with those cosmic ray vulnerabilities.
02:04:00 - Leo Laporte (Host)
Interesting. Or you could just wrap your computer in tinfoil.
02:04:04 - Steve Gibson (Host)
Yeah, you know now, there you have an overheating problem and that might cause a different source of errors.
02:04:12 - Leo Laporte (Host)
Linus Torvalds said very famously a few years ago that it's insane not to have error correcting RAM in all machines, not just servers. That general purpose PCs should have ECC. He said it's undoubtedly he knows as a developer of Linux. The source of many blue screens and crashes are bit flips.
02:04:35 - Steve Gibson (Host)
But the crypto applications are even more significant of course yes, and we know that row hammer, that is, the deliberate hammering on RAM, can cause spontaneous flips. But so can chance you know RAM events Right.
02:04:53 - Leo Laporte (Host)
And cosmic rays? Yep, but ECC, I think, was correct for that right. I mean it would you know, just as you have ECC in your hard drive and, as you are often said, hard drives are incredibly unreliable. You know they're constantly making errors, but ECC fixes it without your even knowing it. Yeah, yep, I think that's a very interesting arena. Some day I want you to talk about the technologies of ECC. If you haven't already, you might have. We have done 948 freaking episodes.
02:05:29
Steve Gibson is the king. There's no doubt about it. People come every Tuesday to sit and worship at his feet and to learn to fill your brain, fill your noggin, with all this information. I hope you're here every Tuesday. Now there's a couple of ways you can consume the show. Of course, steve has a copy of his website, grccom, so why don't you mosey on over there? Get a copy of Spinrite 6, the world's finest mass storage and maintenance utility. Until 6-1 comes out, then it will be the world's finest. But the good news is you'll get a free upgrade automatically if you buy today. Everybody should have. If you've got a storage device, you should have Spinrite.
02:06:11
You can also get the 64-kilobyte audio version of the show. He also has a 16-kilobyte audio version of the show for the heart of hearing. I guess. I don't know, it sounds a little scratchy to me, but it is small. That's his chief advantage. He made it for Elaine Ferris, who does the transcription. She doesn't have a lot of bandwidth but she, I guess, is good enough she can transcribe it, and that's another format that Steve has uniquely. And of course, the show notes are there as well. That's all at grccom, along with a lot of great free stuff that Steve gives away, not only articles, but programs too, like Valid Drive, shieldsup, and on and on and on grccom. If you have a question or comment or suggestion for Steve, best way to do it is put it on Twitter. I'm sorry, x at SGGRC is his handle and his DMs are open and, as you can see, he uses a lot of them, so that's a good way to submit a photo of the week or a question or a comment.
02:07:07
We also have copies of the show at our website twittv slash SN Get it For security. Now, I say that because I think some people might not know where SN comes from. It's the initials of the show. Grc has it, we have it. We have a unique format of our own, which is video. There's also a YouTube channel dedicated to security now, and that's a nice way. People often ask me well, how can I share a clip with my boss or coworker? Youtube makes that really easy. You can just select the part you want and send it to them. So that's a great way to do it.
02:07:42
And, of course, the best thing to do is subscribe, get a podcast player. We happen to like Pocket Cast, but there's plenty out there. I just helped a guy named Ralph with a G Potter, which is a Linux tool, and he had just joined the club. He said well, how do I get the club ad free versions in the G Potter? I said well, here's what you do. You go to that page, you got a link, copy that RSS feed, you paste it in G Potter and Bob's your uncle. He said I see them all. I said now you have to listen. That's the downside. If you're not in the club, I invite you to join. That's where you get ad free versions of all the shows. It's also where you can watch the shows happen live in our Discord.
02:08:19
The Discord is a great place to chat. In fact, we're just talking. I think we're going to create some new channels, one for gamers and one for the advent of code, which is coming up in two weeks, and we have a number of people in the club who like to solve those advent of code coding problems, and we all get together and talk about it and so forth. That'll be a lot of fun. What else do you get? Oh, you get shows that we don't put out in public. In fact, tomorrow, renee Richie, youtube's creator, liaison and longtime host of MacBrick Weekly Did I say tomorrow? I meant Thursday. Yeah, thursday 9am, renee Richie will be in our Discord to ask an answer so you can talk to him then. We also do a.
02:08:59
Now this is a little controversial. We do a live stream in the Discord, but a number of people complain about the quality of the Discord. Other people say well, I like to watch on a big screen TV. I can't do that with Discord. So we've relented. I've listened to your begging and we are continuing to stream the shows as they're recording. So we're streaming right now on YouTube. So then that will be the only place you can get that. So just go to youtubecom Slash Twitter and if we're live, it'll say live and you can click that and watch. We are not going to do reruns anymore and we're only going to turn on the live stream on YouTube when the show's actually underway, because we want to preserve the pre and post chatter for club members and that kind of thing.
02:09:43
The club is seven bucks a month. Twittertv slash club it gets you a lot of benefits, but, frankly, the real reason is we want to keep doing this and advertising revenue has dwindled to a very small amount. We had a $50,000 shortfall this month, which is fine. It just means I won't get paid, but that's okay. Next year we're already $500,000 short. We got to make it up somewhere. I don't have the resources to do this unless we can only do shows that pay for themselves. Basically this show does, but it would sure help if you just get on in there and Twittertv slash club Twitter Seven bucks a month. That's all A couple of triple tall lattes and you're good to go.
02:10:31
What else? Anything else? Well, if you do want to watch us do this live, it's every Tuesday. It's supposed to be right after MacBreak Weekly, which is, in theory, $130,000. But those guys just won't shut up. I'm sitting at $105,000. I'm starting to wrap up the show and we went all the way to $150,000. They couldn't stop talking. I sat back staring watching the clock on. Anyway, I know you love that. So we'll get to Steve as quick as we can after MacBreak Weekly, no later, I think, than 2 pm Pacific, 5 pm Eastern, 2200 UTC. So if you want to watch it, go to the live stream in the Discord or the live stream on YouTube and you can watch it there. Did I cover everything, boy? There was a sure Sure was a lot of stuff. I think we're good, steve, you got it. My friend, have a great week and I'll be listening to that book on the way home and I'll see you next Tuesday on security Now yay, look forward to both of those.
02:11:28 - Steve Gibson (Host)
I look forward to your book report next Tuesday.
02:11:31 - Lou Maresca (Other)
Bye, come join us on this week in Enterprise Tech. I'm Peter Kos and I talk about the enterprise world and we're joined by industry professionals and trailblazers like CEOs, cios, ctos so it's every acronym role, plus IT pros and marketeers. We talk about technology, software plus services, security you name it. Everything under the sun. You know what? I learned something each and every week and I bet you you will too. Join us and, of course, check out the tweet, that TV website and click on this weekend enterprise tech. Subscribe today.