Security Now 945, Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
00:00 - Leo Laporte (Host)
It's time for security now. Steve Gibson is here coming up the end of the line for VB script, or is it another massive flaw in curl a CVSS of 10, versysco and the power of privilege, and why it's not a good thing? It's all coming up next on Security Now Podcasts you love from people you trust.
00:27 - Steve Gibson (Host)
This is Twitter.
00:33 - Leo Laporte (Host)
This is Security Now with Steve Gibson, episode 945, recorded Tuesday, october 24th 2023. The power of privilege. Security Now is brought to you by Drota. All too often, security professionals undergo the tedious and arduous task of manual evidence collection. For your compliance With Drota, companies can complete audits, monitor controls and expand security assurance efforts to scale. Say goodbye to manual evidence collection, hello to automation. All done at Drota speed.
01:11
Visit drotacom. Slash twit to get a demo and 10 off implementation. And by delete me, reclaim your privacy by removing personal data from online sources. Protect yourself, reduce the risk of fraud, spam, cybersecurity threats and more by going to join delete me. Dot com. Slash twit. Use the code twit for 20% off. And by thinkst canary. Canary tokens are a quick, painless way to help defenders discover they've been breached by having attackers announce themselves, for 10% off and a 60 day money back guarantee. Go to canary dot tools, slash twit and edit a code twit in the. How did you hear about us? It's time for security now. The show we cover the latest security news from and, of course, recommendations and explanations from this guy right here, steven Gibson. Hello, steve, yo Leo, great to be with you. Let's get ready to secure.
02:17 - Steve Gibson (Host)
Here we go. Yes, it's. It is the penultimate episode of October. I learned several years ago that that does not mean the last one, that means the second to last one because, yes we're going to be on Halloween from today. Are you going to?
02:32 - Leo Laporte (Host)
wear a costume for me.
02:34 - Steve Gibson (Host)
No, but we do have something to hang in the background. Okay, he said. Oh, you got to put this in the podcast.
02:39 - Leo Laporte (Host)
I will be wearing a costume. I just want you to know, yeah.
02:43 - Steve Gibson (Host)
I'm in mine, don't be too surprised.
02:45 - Leo Laporte (Host)
We have my dress in a black t-shirt as Steve Gibson Maybe put on a mustache.
02:50 - Steve Gibson (Host)
Hey, if you just put your wizard hat on, I think no one would find fault with that, leo.
02:56 - Leo Laporte (Host)
Okay, good.
02:57 - Steve Gibson (Host)
So today we're going to address some questions, as we often do, certainly recently. We're going to start off with a bit of fun, even after our picture of the week, which is how is it that fake drives keep being sold by Amazon? Thanks to one of our listeners and users of Validrive, we actually have some firsthand knowledge of that experience. Also, if you don't already know, it is VBScript worth learning today. Oh, ntlm authentication is 30 years old. Will it see 40? What startling flaw was just found in curl and what should you do about it?
03:40
Vulnerabilities with a CVSS score of 10.0 are blessedly rare, but today the industry has another, and also asked by our listeners how should live be produced, or is it live? How has spin right six ones pre release actually run? Is pass key export on the horizon, as it may turn out? Doesn't a server's IP address make encrypting the client Hello so superfluous? Is there such a thing as encryption preemption? Are fraudulent higher end drives also possible? What's privacy badger and why did I just install it? And finally, within any enterprise, few things are more important than managing user and device access privileges, as highlighted by the NSA's and CIS's experiences. We're going to end by examining the need for taking privilege management more seriously than ever During this week's security. Now episode 945, the power of privilege. The power of privilege. Don't abuse it.
04:59 - Leo Laporte (Host)
Can't wait. Good episode as always coming up. You know, this is why you got to tune in every Tuesday, because I mean this show has the stuff here.
05:07
You need some stuff you need to know. That's right. Our show this week brought to you by Drota. Another thing you need to know about, especially if you're doing the manual evidence collection for your compliance efforts. It is that's a lot of work and it's unnecessary and it's not accurate and it's not reliable.
05:27
Drota helps you solve this simple problem. If your organization's finding it difficult to collect manual evidence and achieve continuous compliance as you grow and scale, you need to know about Drota, a leader in cloud compliance software. As G2 says, drota streamlines your SOC2, your ISO 27001, your PCI DSS, your GDPR, your HIPAA, your whatever compliance framework. You're responsible for providing 24 hour continuous control monitoring, so you focus on scaling securely and all the important things you have to do day to day and let Drota collect the evidence to ensure compliance. With a suite of more than 75 integrations, drota easily integrates with everything you're using applications like AWS or Azure. It works with GitHub, with Okta, with Cloudflare and on and on. Countless security professionals from companies like Lemonade and Notion and Bamboo HR have shared how critical it has been for them to have Drota as a trusted partner in the compliance process. You'll be able to expand your security assurance efforts by using the Drota platform which allows companies to see all their controls, to easily map them to compliance frameworks and you'll immediately know where there are gaps, where you've got framework overlap. Save yourself money. Don't do it twice.
06:55
Drota's automated dynamic policy template support companies who are new to compliance and, by the way, you can also do their integrated security awareness training programs, which are great for employee on boarding. You get automated reminders. They're the only player to be. I'm going on and on, but this is really a great product. They're the only player. This is important to build on a private database architecture. Your data can never be accessed by anyone outside your organization. That's very important.
07:24
When you sign up with Drota, you're going to get a team of compliance experts because you're not alone. They're partners in this journey with you. You'll get a designated customer success manager and Drota has a team of former auditors Between them. They've conducted 500 audits and they're there for you to answer questions, to help you prepare for your audit. Your Drota team keeps you on track, so there's no surprises, no barriers. They even do a pre-audit call to prepare you so you can ask all those questions and really be ready to go.
07:56
Plus, you'll love Drota's audit hub. In fact, your auditor will love it too. It's the solution to faster, more efficient audits, because you save a lot of time with back and forth communication. All the evidence is in one place. All the documentation can be shared instantly. No more searching. Where did we put that? Is it here? It's all in the Drota audit hub and all the interactions, all the data gathering, can occur in Drota between you and your auditor. You don't have to switch to different tools, or you know, oh, I can't email you this. Can I send you a link? Or you know, it's all in the hub. Auditors love it.
08:34
With Drota's risk management solution, you can manage end-to-end risk assessment and treatment workflows. You can flag risks, you can score them, you can decide whether you want to accept, mitigate, transfer or avoid them. Drota will map appropriate controls to the risks. It simplifies risk management, automates the process. If you're new to it, it's great, but even if you're not, getting this all automated makes so much sense. Oh, oh, I forgot Drota's Trust Center, which gives you real-time transparency into your security and compliance posture and you can share it with others, which helps you with sales, with security reviews, gets better relationships with your partners and customers because they know you're doing the work. Say goodbye to manual evidence collection. Say hello to automated compliance. Visit drotacom. Slash twit. D-r-a-t-a dot com. Slash twit Drota, bringing automation to compliance at DrotaSpeed. D-r-a-t-a dot com. Slash twit. You need this thing. I need a picture of the week, mr G.
09:38 - Steve Gibson (Host)
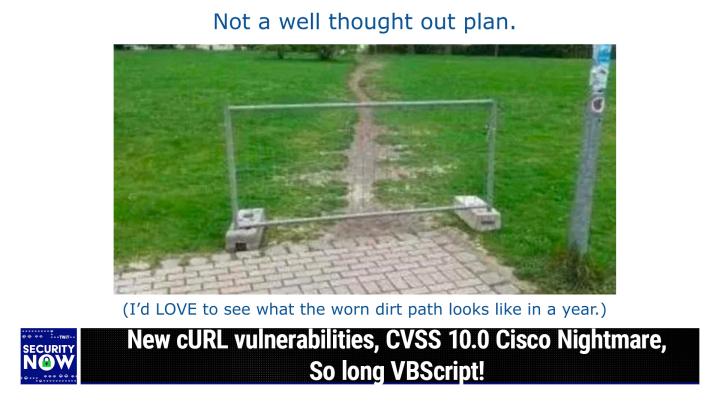
G. So, looking at this, it occurs to me that sometimes people like the wisdom of the crowd, is what ends up prevailing. We have a picture where there was in the foreground. At the bottom of the picture, we see the end of some pavers, like a paved walkway or something, and the rest of the picture is a big grassy field. It's well-kept lawn, mode lawn.
10:16
Now, clearly, the people running this facility didn't intend for the actual users of the facility to wear a dirt path through the lawn to some remote corner where presumably there's a way out, the whole point being that this demonstrates that people want to go from point A to point B, even though that was not the original plan of those who were putting this together, or, if it was, they didn't appreciate that over time there would be no grass growing along this path that everyone was walking. So, unfortunately, the proper course of action would have been to simply pave an explicit path where the people want to go, rather than putting up this lame like it looks like maybe three feet tall by six feet wide barrier at the edge of these pavers, like as if it's going to stop people from going around it, because they clearly want to use this path to get to wherever the path goes. So I gave this picture the caption, not a well-thought-out plan, because I don't think this is going to turn out the way they're hoping.
11:44 - Leo Laporte (Host)
You know, what you're going to see is a path around the fence connecting up to the other path, so people can continue to use it.
11:53 - Steve Gibson (Host)
Yes, and already on the far side of this you can sort of see some diversion from the path where it looks like maybe people have already started to go around. So you know, over time this problem is going to get worse. You know there's going to be like multiple ways to merge with the original path after you go around this ridiculous little like nothing.
12:18 - Leo Laporte (Host)
It is possible that the people who set this up were geniuses and wanted a three-way path structure going on.
12:27 - Steve Gibson (Host)
Maybe they that was very impressive. All right, Steve yeah.
12:36
Anyway another of our observations of the nature of human nature. Human nature, yeah, love it or leave it. So, speaking of human nature, as many of our listeners know, the homepage for my Validrive freeware shows a photo of those 12 1-2 terabyte drives which I purchased from Amazon last month. That page also includes links to the Amazon purchase listing for each of those 12 drives and, with some surprise, many people have wondered how this fraud can exist on Amazon. So I wanted to share the experience of one of Validrive's pre-release testers who took the trouble to purchase a drive, then to post her review of that just purchased drive. Her name is Leela and she wrote, and this was posted over in GRC's news group, so I just wanted to share it with our listeners here. She wrote I posted the following review of a cheap 512 gigabyte USB drive, together with a screenshot of the Validrive results. So the review she wrote read this USB stick is a fake. Although labeled and formatted to appear to have 512 gigabytes of storage, it in fact contains only 53 gigabytes. Anything written beyond 53 gigabytes appears to write without error but cannot be read back. The attached picture shows the result of testing with Validrive, a recently published freeware program for testing USB attached storage. If you buy a high-capacity USB stick or microSD card for peanuts, don't be surprised if it's a fake. Check out the prices charged by reputable vendors such as Sandisk and Kingston for reference. In any event, it makes sense to test all such cards and drives before putting them in your camera, dash cam, etc. Even those which appear to be from reputable manufacturers are sometimes forgeries. Okay, so that's what she posted on Amazon. Not long after she received Amazon's reply, they wrote back to her. Thank you for submitting a review of Doikob. That's not a name brand, doi KOB, the lesser known Doikob memory stick. 512 GB USB stick. Fast speed USB 3.0 drive. Mini USB metallic flash drive. Portable USB memory sticks for data storage and transfer with keychain. So that's the name of the product. And they continued. We're sorry, you did not have a positive experience. We investigated your concerns about product authenticity and the information we have indicates that the product you received was authentic. As a result, we removed the review you submitted. This ensures that customer reviews remain as accurate as possible for the benefit of future customers. So that answers that question.
16:11
Unwitting users who are taken in by this fraud. You know. Post, you know, holy crap, I just bought this 2TB thumb drive for $20. I plugged it into my computer to verify its size and it looks great. This is a super bargain for 2TB, so I'm definitely giving it five stars. Of course, you know they haven't tried storing much data on it yet. They just got it plugged it in, looks fine, off they go. So those reviews are immediately posted on Amazon, whereas an actual analysis of the drive oh, you know, we're sorry, you didn't have a good experience, but what you said was not the case. So we're not going to let anybody see it, we're just going to go with all of the happy customers. So, anyway, that's the way this happens. And you know the other people have said well, why not complain about a specific drive? Well, first of all, who are you going to complain to? Amazon won't list it because they just say no, look at all the other people who are happy. There's something wrong with your computer, okay, anyway.
17:18
Um, microsoft's VB script, which you know was the proprietary scripting language based upon Visual Basic, is officially headed for the dustbin of history, and not a moment too soon. I know, leo, I know, believe it or not, vb script has been with us since 1998. So now for 25 years. It was originally Microsoft's attempt to combat JavaScript. You know they didn't want somebody else's scripting language to prevail, so it's like wait a minute, we've got one too. And it's like okay, and you know it kind of it lived alongside JavaScript and and you know the early dot net stuff and so forth for a while. But since PowerShell is far more comprehensive than VB script, and since Microsoft had essentially already abandoned VB script, it's it's last significant release was VB script version 5.8, 13 years ago, in 2010. So the only ones who are likely to mourn its passing are malware authors, among whom it has remained a popular tool, even though, even there, not as popular as it once was.
18:47
Now that said, vb script still has a large fan base among system administrators, who have established a code base of their own. You know it's their stuff that they've written is working and it's been proven. The good news for those who do still need it is that it's not being, at least immediately completely removed from windows. Instead, what's happening is it is being moved from the you can assume it's always there by default into the so-called FOD that's Microsoft's term feature on demand, also known as optional features. Fod, fod. Yes, we're fodding it. Yeah, where those. So, you know, in those comparatively few environments that do still depend upon it, you'll be able to, you know, enable it and install it on demand, but it won't just always be there ready to go. They have said that they definitely plan to remove it entirely at some point. So anyone who does still today depend upon VB script would be advised to migrate their code over to PowerShell. That's the future. Vb script has no future.
20:14
And as for malware, it's removal VB scripts removal is expected to have some impact on malware, in the sense that another piece of lowest hanging fruit, which has been VB script, will at long last finally have been pruned from Windows. But it's not as if malware will be hugely inconvenience inconvenience. Just as when Microsoft dropped support for macros in office applications, vb scripts, new FOD status will trigger, you know, a more concerted move to PowerShell-based malware exploitation. The larger gangs have already switched over to PowerShell because there's a lot more you can do with it and, unfortunately, you know, a lot more mischief that you can get up to. But the older groups, who are more into the copy and paste mentality, they've just continued using VB script because it was there, it's like. Why not? So those guys will need to up their game once VB script stops being available on all windows unless it's installed by demand. So anyway, anyone who's listening to this podcast would be well advised to plan today for the eventual disappearance of VB script. You know, and knowing Microsoft, it will likely survive over in the optional features category for quite some time yet. I'm not sure you know why they would ever remove it, unless at some point Windows evolved to make it incompatible, in which case then they'd probably say, oh well, we had to get rid of it because it no longer ran on Windows. You know 14. But you know, still I wouldn't be counting on it in the long term.
22:01
Speaking of things being discontinued, microsoft has also announced their intention to eventually disable support for the ancient and never really secure NT, as in new technology LAN man, you know, lan manager authentication protocol which will occur, that is, the eventual disablement, in a future version of Windows 11. And of course, labeling anything NT standing for new technology after 30 years in internet time is really a stretch anyway. So NT LM authentication protocol was first introduced in 93. So, yep, 30 years ago. And that was with the release of Windows NT 3.1. It did serve as the primary user authentication protocol for Windows networks until Windows 2000, which first introduced the Kerberos authentication system, originally developed at MIT. Ever since then, nt LM has still been there in Windows as a backup authentication protocol for legacy purposes and in actually the still many situations where Kerberos could not be used.
23:25
The problem, as we well know, with keeping legacy protocols around is that the weakest link principle applies, especially when it's coupled with the. Well, let's just leave it enabled in case someone might need it. Philosophy of network administration, you know. The problem is, of course, the bad guys might be the ones who need it and if it's enabled they're happy to take advantage of it. But superior or, yes, superior as Kerberos is even today, it's not a slam dunk drop in replacement for NT LM.
24:03
Kerberos has known problems where NT LM works in offline and local use or in segmented network topologies where there's no direct line of sight to a domain controller, because Kerberos is a three party authentication system, not a two party system, so you need access to that third party.
24:25
Microsoft has indicated that it's well aware of these issues and let's hope it is and that it's going to fix, it's going to be working on Kerberos's shortcomings before completely removing NT LM, but they have signaled that NT LM is eventually going to be retired. Microsoft says it's working on two new Kerberos features, namely IA Kerb and local KDC. That will allow Kerberos to work in more diverse network topologies and in offline and local scenarios, as I said, where there's no DC, no domain controller around. And the good news is, all of this will only affect Windows 11, not Windows 10, because it's probably still going to take a while to get there and, believe it or not, windows 10 now has fewer than two years of support left. Windows 10 support is slated to end on October 14. We just last week passed the two year cutoff, october 14 of 2025. So that's 103 weeks from now, and that will be coinciding with Security Now podcast 1046.
25:48 - Leo Laporte (Host)
Which will exist thanks to you.
25:51 - Steve Gibson (Host)
That's exactly right, leo. It's a good thing that we're going to keep on going past 999, since I would not want to miss out on the opportunity to complain a lot about the about the premature ending of Windows 10 support, which by then I'll just be starting to use. So in any event, actually I'm already using Windows 10, and I'm fine with it to help enterprises to wind down their dependence upon NTLM. And here's the takeaway for our listeners who are in the enterprise profile Microsoft will be adding to Windows 11 new tools and logging capabilities to help monitor NTLM usage, along with providing finer grained group policies to disable and block NTLM so that enterprises can get ready for its eventual disappearance. Then and that also will be providing metrics back to Microsoft as they see that NTLM usage is diminishing, they've said they fully intend to announce a hard date when the protocol will be disabled in Windows 11 and then finally pull the plug. Quoting Microsoft, they said Reducing the use of NTLM will ultimately culminate in it being disabled in Windows 11. We're taking a data-driven approach and monitoring reductions in NTLM usage to determine when it will be safe to disable. So I suppose the other strategy would be keep using the crap out of it and Microsoft will go whoa. I guess it's not safe to disable it and maybe everyone will keep having access to it.
27:41
The problem is NTLM has been a real problem. I mean, it has been a source of many conversations during the 18 plus years of this podcast when it has had serious vulnerabilities. So it absolutely would be good to go to an updated, modern protocol. I mean, you know, legacy protocols are not those that you want to keep around, especially when you know they're in crucial positions like network authentication. Vulnerabilities in the massively widely used curl command and library are always a concern, since the library is so often included inside other projects, because the features and services that curl offer are incredibly handy. So it is significant when Daniel Stenberg, who is the curl projects lead developer, calls one of two just discovered vulnerabilities quote probably the worst curl security flaw in a long time. Unquote.
29:01 - Leo Laporte (Host)
That's saying a lot, by the way.
29:03 - Steve Gibson (Host)
Boy. Yes, it is the two flaws which were found by JFrog impact live curl versions 7.69.0, which is where they first appeared, through 8.3. Daniel wrote, quote we're cutting the release cycle short and will release curl 8.4 on October 11, including fixes for a severity high CVE and one severity low. The one rated high is probably the worst curl security flaw in a long time. The new version and details about the two CVEs will be published around 600 UTC on the release day. So there was CVE 2023 38 545. That was the severity high, which affects both live curl and the curl tool, which is built from the live, and also 38 546, who's, which has low severity and affects live curl only, not also the tool. He said there is no API nor a BI change in the upcoming curl release. He said I cannot disclose any information about which version range is affected, as that would help identify the problem area with a very high accuracy, so I cannot do that ahead of time. He said the quote last several years, unquote of curl versions are as specific as I can get. In other words, the last several years of curl have had these problems, one which he characterizes as the worst curl security flaw in a long time, meaning that and this is the significant part anything built with those libraries, anything that incorporated any curl within the last few years, is also potentially at risk and thus the severity of this overall. He said we've notified the distros mailing list allowing the member distributions to prepare patches. Now you know, plan accordingly, unquote. So the worst of the two problems sounds quite bad and is easy to exploit on its face, but fortunately it's required. Preconditions will prevent the world as we know it from ending.
31:46
The curl maintainers wrote in their follow up advisory. They said, quote the flaw is a heap based buffer overflow in the socks five proxy handshake. When curl is asked to pass along the host name to the socks five proxy to allow that to resolve the address Instead of it getting done by curl itself, the maximum length the host name can be is 255 bytes. If the host name is detected to be longer than 255 bytes, curl switches to local name resolution and instead passes the resolved address to the proxy. Due to this bug, the local variable that means let the host resolve the name could get the wrong value during a slow socks five handshake and, contrary to the intention, copy the two long host name to the target buffer instead of copying just the resolved address there. Okay, unquote. So we have a timing based race condition that could lead to remote code execution via a buffer overrun. The curl dev said that the overflow could be triggered by a malicious HTTPS server performing a redirect to especially crafted URL, the JFrog grot. The JFrog guys who found the problem said, quote seeing that curl is a ubiquitous project, it can be assumed with high confidence that this vulnerability will get exploited in the wild for remote code execution, with more sophisticated exploits being developed.
33:37
However, the set of preconditions needed for a machine to be vulnerable is more restrictive than initially believed. Unquote. So this feels exactly like another one of those vulnerabilities that, while it doesn't explode, the internet will be latent. It will be entered into those massive exploit databases I've theorized about in the past. Something like that must be maintained by our NSA and, unfortunately, by all other sufficiently sophisticated malign actors on the global stage. There's likely a huge dependency tree that knows which version ranges of every utility and library that uses curl was built using any of those vulnerable curl libraries during the years that that that curl, it was now known to have been vulnerable.
34:42
So, whether it's next year or 10 years from now when we or some hostile actor, you know some hostile foreign power, wishes to penetrate a network, that database might serve to remind such an actor.
34:59
You know that, for example hey, you know the set of circumstances you're facing just happened to perfectly fit the use of a long ago patched but still present in the target system flaw that we could take advantage of today.
35:17
You know, as I've often observed, given the Swiss cheese that is our industry's legacy of interdependent, flawed libraries, which continue to persist because they're embedded in other things that are still being used. You know, and in this environment of slow moving updates, there's just no way that that's, such a capability does not exist, and it's a little creepy because that's a lot of information. So you could just imagine that would be a perfect place to apply AI. Some AI has ingested all of the of the past history of vulnerabilities and interdependences, so that you, you aim it at a given scenario where you want to to penetrate, and it looks and finds a way in, based on the, the, the, the current versions of the things that are detectable and knowing everything about the past still vulnerable interactions among them. So you know, we may be entering, excuse me, a whole next generation of of of ways of penetrating networks. Sometimes you don't have to work very hard, leo, to penetrate a network.
36:45
Sometimes the network penetrates you Sometimes it just says come on, baby, you know what are you waiting for. Cisco has recently been dealing with a problem that is anything but latent, as we've often observed really, really bad vulnerabilities I mean really, really bad ones are typically awarded a CVSS score of 9.8. And that's generally as high as it goes, and even that, even a 9.8, is quite difficult to earn, and I respect the reticence to go any higher, since we would like to reserve any assignment of 9.9 or 10.0 for those really just too horrible to believe problems.
37:42 - Leo Laporte (Host)
It's not a common issue of exploits.
37:46 - Steve Gibson (Host)
Indeed. So this means that Cisco's recent award of a CVSS of 10.0 really does mean something. What does it mean? It means that, almost overnight, more than 42,000 of Cisco's high and publicly exposed internet routers and switches were compromised and taken over. Like I said, that's what you want to reserve those 10.0s for the first known instances of attacks against Cisco's iOS and you know that's not Apple iOS for Cisco iOS is Internet operating system. So Cisco's iOS XE based routers and switches, which appear to have been that is, the the first instances of attacks appear to have been initial proof of concept.
38:50
Probing incursions Occurred at the end of last month on, on September 28. Then, more than three weeks past, before Cisco finally released the first fixes last Monday, on October 16. So eight days ago, during those intervening three weeks, more than 42,000 42,000, not, like you know, 100, you know critical on the edge internet connected switches and routers. 42,000 of these iOS XE based devices were, are known to be compromised and, again, not were scanned by show Dan and found to be vulnerable. No were known to be compromised because the malware was detected in them and, as I said, compromise means full and effectively devastating takeover of the device. We know that it was 42,000 devices because scanners were quickly created by security firms who wanted to track incursions. And in response to the visibility of their initial implants, the perpetrators of these attacks then updated their malware to make it less visible.
40:21
To all of this the tech press responded as we'd expect. Just yesterday, sc media led with what the Cisco iOS XE0 day reveals about potential risk management blind spots. Helpnet Security wrote Disappearing Implants, followed by first fixes for exploited Cisco iOS XE0 day. Crn wrote Cisco releases first in series of patches for iOS XE vulnerabilities. A day earlier on Sunday, bleeping computer's founder Lawrence Abrams wrote Hackers update Cisco iOS XE backdoor to hide infected devices. Dark Reading wrote Cyber attackers alter implant on 30,000 and they meant 42,000. But okay, compromised Cisco iOS XE devices. And the register did not disappoint with their headline. Cisco fixes critical iOS XE bug, but malware crew way ahead of them.
41:32
Initial fall in infected devices indicates evolution, not extinction, of attacking code. So in today's show notes I have a chart which shows the initial infection rise, which looks like it took about two days, from the 16th of October to the 18th of October. Two days and we hit 42,000 infected devices. Looks like the majority were in Asia. They barely outflanked North America, which was in number two, then came Europe, then Africa, then then Oceana and then others. So it peaked two days after, on October 18th, and then just around the 20th, we see it dropping like right back down to zero. We already know that there's no way 42,000 devices randomly scattered out on the internet got themselves patched in like a day. That was the malware deciding whoops. We made ourselves too easy to spot. We're going to go undercover. In other words, what we now have is a very real first class CVSS of 10.0 mess. As I mentioned, the news of this broke publicly for the first time on the 18th and the chart that that chart in the show notes shows that this corresponded with the peak of the detectable infections.
43:29
The problem that Cisco revealed was a zero day, now known as CVE 2023 20198, which exists in the web I can't even believe I'm saying this the web admin panel of its iOS XE operating system. I can't count the number of times I've said on this podcast that all of our experience teaches us that it is absolutely never safe to expose any web based administration to the public internet. As an industry collectively, we've proven that we simply do not yet know how to do that safely? We keep thinking we do, but all of our experience says no, you don't. If a network's management environment absolutely requires remote management access to a publicly addressable router or switch, then use a VPN to connect to the private network behind the device, then access its web interface from the inside and never expose any management level web interface to the public internet. There's just no reason to. Ease of access obviously also applies to the bad guys. You're making their access easy. That's not what you want and really in this instance, cisco is at fault here in the year 2023. Not because they made a mistake as we know that can happen to anyone but because it's even possible in this day and age to configure their devices to expose a web admin interface to any publicly routable network. It should not be possible. This is all enterprise grade, high end equipment. Anyone using it should have VPN technology falling out of their pockets. So only exposing web admin to private networks would never impose a burden on their administration and if Cisco had implemented such a policy, 42,000 plus recently compromised and now much more difficult to find routers and switches would not be compromised and Cisco could then safely make all the mistakes they might want with their web admin authentication without it ever creating what essentially is a global catastrophe, and also note that this does not only apply to the enterprise. That is this as strongly wording as I could word it, as I could possibly make it.
46:37
Advice does not only apply to the enterprise or to enterprise class devices. It applies right now, today, to every one of us. Remember? It was an exactly analogous flaw in a Plex media server web admin interface, which was located in the home of a last pass developer that was responsible for all of us having our last pass vaults stolen and now being targeted for selective decryption, unlike the Cisco case. It's probably asking too much for Plex to disallow internet facing administration, but that individual, that last pass developer you know, who was deep into the security space as a developer at last pass, should have done so. Him or herself, and everyone listening to this podcast, should consider that too. Vpns and overlay networks are now so freely available that it's only a matter of taking the time to set them up. Okay, enough preaching and ranting.
47:47
In today's case, with Cisco, the zero day allowed threat actors to create an admin account with the highest level of privilege in Cisco land it's level 15 on devices that had their web UI panel exposed to the internet. After some additional investigation, the presence of a second zero day was also discovered, being used by the attackers to inject commands into the iOS XE file system that would execute with root privilege. Well, that's never good. Cisco revealed that the exploit chain was being used to inject a Lua based backdoor on devices across the world. Cisco initially believed that the second zero day was the exploitation of a previously fixed bug, that was from 2021 CVE 2021 1435. But in an update late last Friday, cisco said the attackers had discovered and were using a new zero day, now assigned CVE 2023 2273. But, believe it or not, both Cisco and CISA confirmed that the two year old patched flaw was also being exploited in the wild by a different threat actor in a different campaign. In other words, there are still machines out there for who where flaws are being exploited a zero day of flaw from two years ago, further demonstrating that those 43,000 known to be penetrated routers and switches didn't just get miraculously patched in a day. We've still got them out there that haven't been patched for the last two years. So, like I said, there's never a good reason to expose all of this management with a web interface management UI to the internet. Just turn it off. Don't do it. Manage from behind and use an overlay network or a little VPN server Trivial to set up these days, if that's the, if you need remote access.
50:01
The other thing that was interesting was that the Lua backdoor that was originally placed on all 42,000 plus hacked Cisco iOS XE devices since late September started disappearing over this last weekend. Estimates from both census and shadow server, who were scanning the internet doing all this, put the number of hacked devices at the number I've been quoting 42,000 plus iOS XE routers and switches and over the course of a couple days, as we know, that number of exposed, known compromised devices dropped down to between 500 and 1000. So who knows why it didn't go to zero. There are apparently more than one, more than one actor at work here and consequently it's believed that this change was made by the threat actor itself. The Lua backdoor was not originally a particularly strong method of persistence, since it could be removed with a device route reboot. So it was only Ram resident at that point and its public visibility was attracting too much attention to the attackers operations.
51:26
Several security researchers pointed out that the Lua backdoor would likely have been replaced by something much more insidious, very similar to the way Chinese hackers evaded Barracuda's patches earlier this year to entrench themselves so deeply into the compromised appliances that Barracuda wound up telling their own customers that they probably should just replace the gear to be safe. There was no other way to really know for sure. Yeah, is really really bad. So at this point we don't know that anything like that has happened. But when vulnerabilities have been discovered, which we, which we know, allows for the injection of commands into the device's file system with root privileges, given sufficient time and these attackers had three weeks it's clear that anything could have been done. So today the internet might well currently have something on the order of 42,000 compromised Cisco routers and switches where their compromises have gone stealth After some threat actor somewhere we don't know who, who finished burrowing in, and at this point you know, we'll never know exactly which routers and switches are affected.
52:53
Once a device as we know, once a device or network has been compromised, can we ever fully trust it again? Today we have patches for both the known zero days that have made this possible. But applying the patches, of course, is only the first step. Even if some of the horses have left the barn, it's still worth closing the door, but you may still have some loose horses. Any enterprise whose Cisco edge gear may have been compromised would be well served to, unfortunately, perform a full and deep security audit into what may have happened on that device over the last month.
53:36
At this point, no one in the infoset community has made even a tentative attribution. No one is suggesting who the bad guys are. There's no malicious actor who would not be interested in penetrating Cisco's iOS XE gear. You know, from hacktivists to advanced persistent threat operators, from initial access brokers. You know IABs to botnet operators could be anybody. And we do need to give Cisco a little bit of credit where it's due. It was they who discovered this new pair of zero days during their investigation of a customer's support ticket. Another vendor might not have bothered to engage a competent security team to really dig into the troubles root cause Cisco did.
54:29
What they found was certainly troubling, and I would argue it should not have happened in the first place, because you just should not be able to put a management, a web management UI, out on the public interface. Anyway, the takeaway for each of us individually should be that our own networks should never expose anything like that publicly. You should never have your own routers web management interface enabled on the internet, regardless of how well chosen your username and password may be, and the same goes for Synology, plex and everything else. You know, as I said, just take the time to set up a simple overlay network or your own VPN server to allow you to access those devices from the inside. And I'll just note that this made me think of this.
55:27
One of the things I have long wanted to do was to expand GRCs shields up service port only scan to check all 65536 ports for its users. Back when I first wrote all of that code, I was running GRCs server from here at home over a pair of 1.54 megabit T1 connections. I was unable to offer to scan 64 times more ports in a reasonable amount of time. Today I could do that easily from level three. So you know, on the back of my list, once I get to a place where I can turn my attention back to shields up, which won't be until after Spenright 7 exists and has been released I think it would be fun to boost shields up so that it's able to scan all of an individual's ports, because you know who knows what. It would show you that you might not even be aware of has opened incoming traffic through your router. We need to find out, leo. We need to find out who our second supporter of this podcast is, and then we're going to look at some listener feedback questions.
56:50 - Leo Laporte (Host)
I do happen to know, I think you do If you'd like to know.
56:55
Security Now is brought to you by Delete Me. It's actually a really timely one for anybody who is, you know, starting to become aware of how much of our personal data is now controlled by data brokers. This is really a gummy business, and all you have to do is search for your name online. Oh my God, actually you could just take my word for it. If you don't, if you don't want to be terrified when I did it, you know not only my name, my home address, my various phone numbers, my income, my relatives, practically my blood type, all on VeilMall online. That might make you feel unsafe or exposed. You might want to contact our sponsor, delete Me. Since 2010, delete Me has been on a mission to empower individuals and organizations by allowing them to reclaim their privacy and help them remove personal data from online sources. But there's a security angle to this which is really important.
58:00
Most phishing scams involve knowledge, especially spear phishing about you or your company. So, for instance, we had a phishing scam where people impersonated Lisa. Our CEO sent emergency of course, urgent text messages to everybody who reports to her. How would they know that? First of all, they have to know Lisa. They have to know her, who she works for, who her employees are. They have to know information about them, to get their phone numbers. Where do you think they get that from? Our entire org chart is basically available through data brokers. That's why Lisa immediately signed up with Delete Me this was a year or two ago to reclaim her privacy and to remove that personal data. The Delete Me team is driven by a passion for privacy and a commitment to make it easy for customers to use.
58:55
You know you probably I'm no security analyst especially. You're probably thinking well, I could do that. Yeah, you could. There are problems with that. First of all, there are hundreds of data brokers now and more every day. I mean, it's like they're growing because it's not illegal. They're growing like topsy. Until Congress passes a real data privacy law, this is going to be a big gold mine for people. It's a big business. Furthermore, these guys you can. You know they all have forms to delete yourself. You could do it.
59:31
One week later, all your data is back. Well, we found it on the internet. It's. You didn't say forever, you just said that's the problem. That's why you need to delete me. It's the most trusted privacy solution available. They know who to contact. They know how to contact them. The average person has more than 2000 pieces of personal data about them online PII that delete me can find and remove. One customer said I signed up, they took it from their awesome service, already seeing results. That could be the direct quote from Lisa she's. She's been with them for more than a year now. She's really, really happy.
01:00:05
We have many of our staff members using it. You know, for security, if nothing, not just privacy, but literally for security for our company. Your executives, your company's executives, should all be using this for sure. Here's how it works you sign up. You're going to give them some personal information. Don't be afraid of doing that. That's how they find you. Right, they need to know enough about you to be able to find you on these brokers. Now they know all the data brokers, hundreds of data brokers so they will find and remove your PII from all of them. You'll receive a report once this process begins, within seven days, so you know what's been done.
01:00:40
But this is more important They'll continue to scan and remove personal information. They'll do that every three months with a new report and with automated removal opt out monitoring. They will make sure that they don't do that because the data brokers don't do that scuzzy thing where they repopulate it after they're oh yeah, we'll delete it. We deleted it. What do you want? Oh, it came back. Huh. I'm talking names, addresses, photos, emails, relatives, phone numbers, social media, property, value.
01:01:07
All of this stuff is public in one place or another. The data brokers pull it all together for a full dossier and, as this industry evolves, delete may continue to add new sites and new features to make sure their services both simple to use and fully effective in removing personally identifiable information. And they have a privacy advisor, by the way, because it affects everybody differently. If you're an executive at a company, you have a higher responsibility to get this stuff gone because of spear phishing, right, so they'll help you. They'll let you know what it is you need to work on, what you need to do and what we've done, what they'll tell you, what they've done to help you. That's really great.
01:01:44
Protect yourself, reclaim your privacy. We know this works because we use it. Join, delete mecom, slash twit. The code is TWIT for 20% off. That's join, delete mecom, slash twit. Prominal code twit, twit. Do that at checkout. You'll get 20% off. All privacy plans Delete me, this is a security and a privacy issue. Join, delete mecom. Slash twit. Offer code is twit. We thank you for their support. Of security now, steve.
01:02:18 - Steve Gibson (Host)
So I listener Steven Lee. He said love your show. I was wondering if you pronounce live for library as rhyming with vibe, do you pronounce there for variable as rhyming with air?
01:02:37 - Leo Laporte (Host)
I say live in var, I mean, that's just me.
01:02:40 - Steve Gibson (Host)
Yeah, and I'm sure he's asking because everyone's heard me say live. You say live. I do say live, as in library, but I do say var as in, for variable as opposed to ver.
01:02:53 - Leo Laporte (Host)
But I don't think you can. You can tie the pronunciation of the full word to the pronunciation of the short version. I agree, yeah. So if you, what's lived to you is live to me, what's in var, I should say ver. If I say live, I should say ver. But I don't, I say var. So yeah.
01:03:16 - Steve Gibson (Host)
Yeah, that's a fork, tom. How do you say that?
01:03:22 - Leo Laporte (Host)
How do you say?
01:03:23 - Steve Gibson (Host)
that Tom Frillman. He said hi, steve, I got the SR 6.1 XE, but Win 10 won't run it. How may I use it? Thanks for all you do. By the way, valid drive is great. I must be lucky. All 25 of my drives are fine, except for one that won't even format. Maybe Spinrite will help. Okay, so a bunch of people were confused by and I apologize for this for my mentioning that the pre-release was available, because what's available is very different from the one, from what the full release will be.
01:04:02
Spinrite, the Spinrite 6 that everyone is used to, is a hybrid Windows, and is a hybrid Windows and DOS XE. It's kind of a cool trick that I came up with, where that one XE is both a signed Windows app and it's a DOS app, because what Windows did when Windows first began to happen was there were still a lot of DOS around, so people would be running a Windows app in DOS, and so Microsoft thought, okay, well, we have to have some way to fix that. So what they did was they defined the XE so that there's a it's actually a DOS executable. On the front, a little stub, and all the the little stub, which is a DOS executable, says this program must be run in Windows. And then, when you run the same executable in Windows, windows is smart enough to know oh well, we don't, we just ignore this little stub and we jump over it to go to the Windows app. So so what I did was I take the Spinrite DOS app and stick it on the front as the stub, so that when you run this, the Spinrite Windows app in DOS, instead of saying whoops, this is a Windows app that you need Windows for. It runs Spinrite like in DOS. And when you run the same thing in Windows, you get the setup utility which allows you to create the USB drive and or format a floppy and install Spinrite on a floppy or burn an ISO to CD-ROM and so forth.
01:06:02
So anyway, that's all sort of hidden from most users, so unfortunately I didn't make all of that clear last week. The pre-release that I invited our listeners to download is a DOS app, which means that you need to stick it on some DOS boot drive. Anyway, I spent the weekend updating GRC's forums and I created an FAQ entry that has very clear instructions for how to do this. So if anybody else was confused, first of all the people in the forums would be glad to help you, forumsgrccom. You can also go there and find much cleaner instructions, and I actually have them also in the show notes. I just sort of skipped over them by giving a more longer winded explanation, but that's the backstory for why it wasn't as easy as just running the thing you downloaded from Windows. Windows would say what Like this is a DOS app. That's not what you're here for and there's no Windows app behind it, as there is an actual Spinrite.
01:07:13
Doug Smith, a listener said, regarding exporting and importing pass keys, I saw this from a one password employee on their forums. Quote at this point in time, this is the one password employee speaking. At this point in time, you cannot import or export pass keys from any managers like iCloud, keychain or OnePassword. The good news is that we're working closely with platform vendors and other password managers through the FIDO Alliance to create a secure way to import and export pass keys. We believe it's your choice where to store and use your pass keys. Hopefully we'll have more to share soon. Unquote.
01:08:08
So that is wonderful news. That's exactly what we need. The user's experience, in my opinion, is paramount, and what users would do would be to provide their own strong password under which they would be exporting one or more pass keys. That would be that strong password would serve to keep their pass keys safe while it's outside of whatever environment, password manager, whatever. Then they need to again provide it when they wish to import that into something else. So that's the way I design things with Squirrel, and the technology to do this safely and unspoofably and verifiably is widely available. That's just not difficult. It's just a matter of establishing it as a standard that everybody can use. So it is very good news that the FIDO Alliance recognizes that this is something that has been missing and that will go a long way toward making pass keys a lot more transparent, I think, and more useful for most of our users.
01:09:27 - Leo Laporte (Host)
This is something we talked about in the original piece you did on pass keys, which is that they had never put anything in the spect about portability, and I think the reason they didn't is because pass keys relies on a secure enclave, like the hardware enclave in your iPhone or your Google phone, to store those pass keys, and it is. I think they're worried that it's inherently insecure to let them out of the enclave. So they've got some work to do. I'm not convinced the FIDO Alliance will agree. We'll go along with it.
01:09:56 - Steve Gibson (Host)
This is just what It'll be interesting to see if that's gonna happen.
01:09:59 - Leo Laporte (Host)
Now the fact that they left it out tells you. Surely they knew this was an issue, but they explicitly. Well, I guess it's implicitly left it out, right.
01:10:08 - Steve Gibson (Host)
Right. Well, and we've also suggested maybe that it was just an attempt by the initial Right, the initial providers of pass keys, to create walled gardens within their own environments. Maybe they've already seen that. Whoops, the number one thing people are asking for is I wanna be able to export these, I wanna be able to import them from somewhere else. I don't like not having that ability. So they may have said, okay, well, we tried not to do that, but users are saying they're not gonna use pass keys unless and until they're able to have them be portable.
01:10:46 - Leo Laporte (Host)
It's kind of a non-starter, right, I mean I have to be yeah, I mean, is my pass keys all live in this phone? What happens when I get a new phone? Well, actually it does move over to the new phone, because mine did. But if I got an Android phone and I have an iPhone, it doesn't.
01:10:59 - Steve Gibson (Host)
Nope, yeah, nope, and you can imagine that a password manager, like one password, or a Bitwarden, they would-.
01:11:09 - Leo Laporte (Host)
They would love to be the host right.
01:11:10 - Steve Gibson (Host)
Yeah, yes, yes. They would like to be able to come along later and say well, you may have started with all your pass keys in your iPhone, but now you can put them here and then, and because we're cross-platform, you'll have cross-platform access.
01:11:26 - Leo Laporte (Host)
The problem in general with pass keys is that there's always the password fallback and people are gonna always fall back to passwords.
01:11:34 - Steve Gibson (Host)
At which point that is exactly right, Leo.
01:11:36 - Leo Laporte (Host)
They say why am I using pass keys?
01:11:38 - Steve Gibson (Host)
That is exactly right, if you know, show me a website that does not say I forgot my password, right, right.
01:11:49 - Leo Laporte (Host)
Right, they can't. They're always gonna do that Exactly.
01:11:53 - Steve Gibson (Host)
Same reason, and so there will always be there will always be script fishing scams, and you know, yep, yep, victor. He said I powered on a couple of years old desktop that had been unpowered for about a year. It took ages before the desktop was loaded no errors anywhere. But I decided to try your read speed and look at those SSD speeds. Is it time to invest in Spinrite now? If Spinrite fixes this, I will try to encourage my employer to get a site license. Thank you, mr Gibson.
01:12:32
Victor, longtime SN listener, keep up the good work up to 999 and beyond. So you have it on the screen, leo, and this is what we discovered to our surprise. Actually, nothing quite this horrible, but not good. So what you have on the screen and what I have in the show notes is this system that has three drives. There are two four terabyte Western Digital spinners and the primary drive, the boot drive, is a 512 gig Western Digital SATA SSD. Well, we can see that it's optimal performance, because remember that what read speed does and this is what opened our eyes so much is it does separate identical benchmarks at five locations the beginning, the end, the middle and then the 25% and the 75% points. This SSD speed is maximum at the 25% point where it's getting 482 and a half megabytes per second. It does not perform well elsewhere, but it performs the worst at the front of the drive where, believe it or not, read speed measured it at 2.2 megabytes per second, down from 482. And, of course, at the beginning of the drive is where the OS lives and, as we know, what we've learned is that the phenomenon of read disturb is that, since those files are being read over and over and over, the successive reading without ever rewriting causes the bits to become fuzzy and it means that the SSD takes much longer to read them and to correct them properly.
01:14:42
To answer Victor's question, yes, running spin right right now on that drive would fix it, and the slight downside although I wouldn't give it another thought in this case is that rewriting the entire drive, which is what spin right does, is less desirable than exactly locating the spots on the drive which are slow and targeting them for selective rewrite. That will be the feature that spin right seven brings, along with what I think is gonna be an extremely interesting map of the read performance across the entire drive surface. So that's why I'm so excited about there being a seven why there will be a seven. I can't wait to develop the technology to do that, based on what we've seen, which is what read speed showed us. And for these spinning drives, we see exactly what we would expect. The beginning of the drives are fast, at 182 megabytes per second, then 169, 151, 122, and 83, where toward the end of the drive, because the circumference of the inner tracks is shorter, you've got a lower data rate there. So anyway, victor, yes, I would love to hear what happens after you run a one of spin rights read, write passes you need to refresh the data. It'll be a little slow going there at the beginning, just as it was slow to get your system booted, but afterwards before and after read speed and spin right six one you could certainly use six or six one, because it's half a gig. So even spin right six will deal with it pretty quickly. Either one will work, but six one offers before and after benchmarks specifically for this reason, and they're built into the system. So anyway, I'm excited about the future.
01:17:03
Andy Suarez said hi, steve, great to hear you cover ECH. That was encrypted client Hello from a couple episodes back. He said the whole time, though I kept thinking that something was missing from your coverage and that was that people should not be thinking that this is providing them cloaked internet access at all. Knowing what IPs are associated with what websites and services is definitely a thing For anything other than the smallest websites. There is absolutely a known correlation between IP addresses and the site behind them and that is not in any way being obfuscated here. Services know the IPs for porn sites and political sites and messaging services, et cetera. And even he gives an example, http//wwwgoccom, as 4.79.142.202. He said they may not be able to see the DNS query with encrypted DNS or the header request with ECH now, but they are certainly still seeing the IP of the web server that you are sending and receiving packets from right. So won't tracking just change to keep fresh lists of sites and what their associated IPs are? And Andy is right of course IPs are still IPs, but the more sites move behind large aggregators like Cloudflare and thus share IPs, the less clear the user's destination becomes. But, as he says, those are more likely to be smaller sites. Big sites typically have their own block of IPs themselves, but it's also unclear how this may change as the popularity of IPv6 grows. At the moment, the lack of IPv4 address space is forcing some of the sharing of IPv4 address space because it's so limited, but IPv6 promises to at least offer the opportunity of demultiplexing websites once again. So I agree that Andy's reminder is a very good one.
01:19:32
Not only was the internet not initially designed to provide the security and privacy that we increasingly need, it was also never designed to hide where we go. That just wasn't on anyone's radar back then. Tor's concept of so-called onion routing is the best solution we've come up with for obscuring our traffic explicitly. A trusted VPN is another good solution, at least for keeping your ISP and anyone snooping along the way from seeing what you're doing. So we would need no one to be able to know what domain IPs and ECH public keys we look up through DNS, then encrypted client hello to hide the domain within our traffic, and then something like Tor's routing or a trusted VPN provider to hide our traffic's destination. Any one of those three missing and it's still possible to know what we're doing on the internet. Someone using the handle new EOL he asked a question that sort of took me a bit by surprise. He said will ransomware be able to encrypt an AES-256 encrypted 7-zip archive and as I said, that one caught me a bit by surprise.
01:21:05
Sort of an interesting thought. This listener is wondering whether encrypting something before ransomware comes along to encrypt it itself could essentially get there first to prevent any further encryption. Unfortunately, it's definitely possible to encrypt something that's already been encrypted and in fact, speaking of Tor, that's something that Tor, this onion routing, relies upon. With Tor, a destination URL is encrypted using the public key of the last router in the chain. Then that One time encrypted URL is again encrypted using the second from the last router's public key. Then that twice encrypted URL is again encrypted using the third from the last router's public key, and so on. Then that multiply encrypted blob is sent to the first router. It decrypts the outer layer of the onion to obtain the identity of the next router in the chain. But since the destination URL is still deeply buried under multiple rounds of encryption, it doesn't know where you're ultimately going to go. It can only forward it to the next router that decrypts the current, now outer shell of the onion, which then forwards it to the next one. So anyway, multiple encryptions definitely do work, you know, and they're corresponding multiple rounds of decryption, and they do even have powerful uses, you know in the case, for example, of onion routing. So yeah, unfortunately, encrypting something before ransomware encrypts it won't keep it from encrypting it again.
01:23:05
Daniel Hodgin. He said Hi, steve, thank you for the new Validrive product and thank you for everything you guys do with security. Now I decided to try it out this morning with a few USB keys and SD cards around our office. I then realized I wonder if this can work with SSDs as well, with a USB connected cloning station. Sure enough, I was able to test a one terabyte silicon power brand SSD from Amazon, which turned out to be exactly as advertised. It made me wonder if the same kind of scam can be done with hard drives, ssds, m dot, two SSDs, etc. Which we're placing in corporate devices and assume our corporate data is being stored just fine Once Windows reports the size is as expected.
01:23:58
Well, it's funny, he should ask. I actually I was curious about a high end device that was available. It has it looks. It was advertised as a USBC style connectable MVME. So a high end device, and you can see I'm holding it up to the camera. It has that physical profile. It looks, you know it's got a beautiful metal case. You know beveled edges that are that are chrome. Well, I opened it up and what do you think I found, leo?
01:24:41
I found it, I think I think you can see it here and I also have it in the show notes is literally it's your favorite hot glued SD card sitting in there. Somebody took the trouble of creating a chip to interface a USBC connector to an asset, to a to an SD card, to create an incredibly cheap drive. It does not have nearly the advertised memory. So not only is it not an NVME, it is an even offering the amount of storage available. So, yes, it is certainly the case that there are, that the Internet is sadly full of scams.
01:25:27 - Leo Laporte (Host)
Wow, you've really become the king of this. You've got a whole collection now, wow.
01:25:32 - Steve Gibson (Host)
I'm so impressed.
01:25:34
Well, I wanted to make sure that my software would work and as I kept getting these things I mean even really nice looking drives like, with beautiful packaging and user manuals and stuff it's like wow, ok, just amazing. So, to last, feedback inspired things I wanted to share. Marcus Hitchens, not Hutchins Hitchens he said privacy badger on rewrites, google's rewritten links in search results. Well, that caught my attention.
01:26:11
Everyone knows how annoyed I am that Google's link hacking, where the link they show you in the search results is deliberately not the link you get when you click it. They are tracking my choices by bouncing my browser through their servers. The one beneficial reason I could see for doing this would be to use human feedback to help tune their search results, but we're all certain that they're also profiling everyone individually for their own profile building. They make all this noise about their privacy sandbox and how they want to do away with third party tracking, but what about tracking every link I click on in the search results? So privacy badger is a creation of the EFF. They are people whose intentions we know we can trust, but I've often thought that it was an unfortunate name. You know privacy badger really.
01:27:15
It's like OK.
01:27:17 - Leo Laporte (Host)
I think it's a plan honey badger, but OK OK.
01:27:21 - Steve Gibson (Host)
It fell flat. For me. Nevertheless, the idea that I could have something I trust stripping Google's URL link mangling out of Google search engine results was too good to pass up. So I added it to Firefox and immediately confirmed that. Sure enough, just as Marcus said, the links presented to me in Google search results are exactly now as they appear visually no more subterfuge. Ah, interesting. Yes, it is very nice.
01:27:55
So I want to take this opportunity to pause for a moment and touch on privacy badger a bit more. First of all, you can find it at privacy badgerorg and it's, you know, p-r-i-v-a-c-y-b-a-d-g-e-rorg, and it is also GRC's carefully numbered shortcut of the week, so GRCSC-945. And I'll just bounce you over to privacy badgerorg, and I'm glad that I'm taking a longer look at this, since what it does sounds really cool and interesting and unique. So in describing it, the EFF writes they said privacy badger is a browser extension that stops advertisers and other third party trackers from secretly tracking where you go and what pages you look at on the web. If an advertiser seems to be tracking you across multiple websites without your permission and it ends up that number is three websites without your permission I'll get that in a second. Privacy badger automatically blocks that advertiser from loading any more content in your browser. To the advertiser, it's like you suddenly disappeared.
01:29:23
Privacy badger was born out of our desire to be able to recommend the EFF's desire to be able to recommend a single extension that would automatically analyze and block any tracker or ad that violated the principle of user consent, which could function well without any settings, knowledge or configuration by the user, which is produced by an organization that is unambiguously working for its users rather than for advertisers, and which uses algorithmic methods to decide what is and is not tracking. As a result, privacy badger differs from traditional ad blocking extensions in two key ways. First, while most other blocking extensions prioritize blocking ads, privacy badger is purely a tracker blocker. The extension doesn't block ads unless they happen to be tracking you. In fact, one of our goals is to incentivize advertisers to adopt better privacy practices. Second, most other blockers rely on a human, curated list of domains or URLs to block.
01:30:41
Privacy badger is an algorithmic tracker blocker. We define tracking behavior and then privacy badger blocks or restricts domains that it observes tracking in the wild. What is and isn't considered a tracker is entirely based on how a specific domain acts, not on human judgment when you view a web page, that page will often be made up of content from many different sources. For example, a news web page might load the actual article from the news company, ads from an ad company and the comments section from a different company that's been contracted to provide that service. Privacy badger keeps track of all of this. If, as you browse the web, the same source seems to be tracking your browser across different websites, then privacy badger springs into action. You can just see the badger springing. It springs into action.
01:31:49
Grabbing those URLs and ripping them out by its teeth, preventing your browser from loading any more content from that source. And when your browser stops loading content from a source, that source can no longer track you, voila. They wrote. At a more technical level, privacy badger keeps note of the third party domains that embed content, images, scripts and advertising in the pages you visit. Privacy badger looks for tracking techniques like uniquely identifying cookies, local storage, super cookies and canvas fingerprinting. If it observes a single third party host tracking you on three separate sites, privacy badger will automatically disallow content from that third party tracker. As for their browser support, it's as universal as it could be. Their FAQ asks Will you be supporting any other browsers besides Chrome, firefox, edge and Opera? And they said we're working towards Safari on macOS support. Safari on iOS appears to lack certain extension capabilities required by Privacy badger to function properly. Chrome on Android does not support extensions. To use Privacy badger on Android, install Firefox for Android. Privacy badger does not work with Microsoft Edge legacy. Please switch to the new Microsoft Edge browser. Note that Microsoft Edge does not support extensions on mobile devices, and they also noted that Privacy badger sends the global privacy control signal. That was the GPC. We did a podcast on a few months ago to opt you out of data sharing and selling, and they do not track signal to tell companies not to track you If they ignore your wishes. Privacy badger will learn to block them, whether they're advertisers or trackers of other kinds. And also I finally. I thought this was very interesting and cool.
01:33:58
From their FAQ. They asked they had someone ask I run a domain that uses cookies or other tracking. How do I stop Privacy badger from blocking me? So they say. They reply One way is to stop tracking users who have turned on global privacy control or do not track signals. Privacy badger will stop learning to block that domain. The next version of Privacy badger to ship with an updated, pre-trained list will no longer include that domain in the list. Most Privacy badger users will then update to that list. You can also unblock yourself by promising to meaningfully respect the do not track signal. To do so, post a verbatim copy of EFF's do not track policy to your URL. You know, whatever your domain iswell-known, forward slash dnt-policytxt. If your domain is compliant with EFF's dnt policy and declares this compliance, most Privacy badgers will see this declaration the next time they encounter your domain. Also, the next version of Privacy badger, to ship with an updated pre-trained list, will probably include your declaration of compliance in the list. Note that the domain must support HTTPS to protect against tampering by network attackers. The path containswell-known per RFC 5785. Also note that you must post a copy of the policy at each compliance sub-domain you control. For example, if you wish to declare compliance with both sub1.examplecom and sub2.examplecom, you must post EFF's dnt policy on each sub-domain. So to me this reads like a solid piece of mature technology.
01:36:14
I hate the name, but I'm glad that I added it to my browsing experience so I wanted everyone to know about it. I have been looking at it and so far I've been impressed with what it's been doing. There's a little badger-like icon in the upper right now of my toolbar and I see that it is blocking trackers. So cool and immediately. It cleaned up all the links that I'm getting from Google's search results, so they no longer know what I click and I would really mind them doing it. But it's the idea that they're showing me the URL that I think I'm clicking on and they've deliberately changed that in the HTML behind the scenes. That's just not okay.
01:37:06
Finally, recall the guy from last week whose tweet asked about obtaining the pre-release of Spinrite. That was the tweet that prompted me to mention that it was available to everyone who was interested. This listener was Brett Russell and, as a reminder, what he tweeted was Hi Steven, I realize this is a request out of the blue, but my hard disk is failing. On my main machine I own a copy of Spinrite. And then he posted the code which I redacted, but the disk is set up as GPT, meaning you know, grid partition format, as opposed to old-school MBR. So he said, which Spinrite 6 does not support, which you can give me a pre-release of 6.1 to run, please. There's nothing crucial on the drive, but if it dies it will take some time to bring it all back. So I replied with the instructions about obtaining the current Spinrite DOS executable pre-release.
01:38:11
And then yesterday, when I was catching up on my Twitter feed, I found three tweets from Brett. Apparently he had sent them shortly after I replied. First said Thanks, steve, much appreciated running it now. Second one, he said Wow, it's fast, feels a lot faster than 6.0. He said I like the new drive identification screen as well. And then this third tweet. Finally, he said it worked. Machine is up and running faster than ever, although no errors were picked up, which I've seen before. He said Setting up a raid mirror for when the drive does die. You saved me a lot of time and effort, thank you.
01:38:56
So anyway, brett's comment about no errors were picked up is a common and sometimes mysterious experience for Spinrite users. After running Spinrite, whatever was wrong will have been fixed, but Spinrite might not explicitly show that anything was done. The reason for this somewhat unsatisfying outcome is that Spinrite induces the drive to deal with marginal problems internally Before Spinrite's deep recovery is needed. The drive will remove a sector from use and everything after that will be well again, but drives typically don't report doing so. So all Spinrite and its users know is that things are better afterwards. Anyway, just wanted to close the loop on that. I guess that's sort of our first testimonial for the upcoming Spinrite 6-1. So thank you, brett, for that, and Leo, let's talk about our last advertiser and then we're going to talk about the power of privilege.
01:40:00 - Leo Laporte (Host)
Awesome, this is great and, as always, and I'm looking forward to it. This is our sponsor and you know what it is already.
01:40:10 - Steve Gibson (Host)
The power of network monitoring.
01:40:12 - Leo Laporte (Host)
It looks like there might be, you know, like an SD card in here with a hot glued circuit, but no, it's not. It's actually it looks like an external hard drive. That's a canary, and that thing is the best little security device money can buy. Because, I'll put it simply, you spend a lot of time and money on your perimeter defenses, but what happens if a bad guy gets in? And we know they do, but do you know if they are? That's the question. That's what this is for. It's the canary in the coal mine. It's a little device you hook up to your network. It's just got two connections power and Ethernet. You hook it up to your network and, bingo, that looks like a Windows server, a Linux server, a NAS, a SCADA device. It could be a variety of hundreds of different devices. It's a honeypot that's designed I mean down to the MAC address, to look like the real thing. But when an attacker hits, it logging in for instance, is my Synology NAS. When they log in, they see DSM7, they go oh yeah, let's log in. It doesn't give them access to all of my private secrets. It gives me an alert, the one alert I need, the alert that matters. No false positives or false negatives. I guess only true positives with this. It's incredible. And you can get anywhere. You want SMS email, you know there's a console. You get system log, there's an API, web hooks. I'm going on and on. Plus, every canary can create canary tokens, tiny tripwires you put in hundreds of places. So it's not just this device on this IP address, but all over our network. There might be PDFs and Excel files and document files that aren't. They're tripwires and if somebody tries to open them, we know there's somebody in the network Thinks Canary's founding team is a background in offense.
01:42:15
They have taught governments and businesses how to break into systems, but they've taken their knowledge and prioritized defensive thinking in developing these canaries. They're uber conscious of your trust in their project. That's why they use extensive measures to make sure that you're not, when you add these devices, adding another security problem to your network. Canaries are designed to be secure. They use memory, safe languages and sandboxing. The architecture ensures no critical network secrets are stored here on the canary and to maintain secrecy, they're not allowed to be dual home. You can't span VLANs because we don't want to give bad guys a chance to span networks.
01:42:57
Right, they've put a lot of thought into this. This is a safe device that you can put in your network that will not introduce new vulnerabilities but will introduce things that look like vulnerabilities to attackers. And when that bird is attacked you will know. It could just let off one warning before it's owned and live up to its namesake. Customers have the option, by the way, to break the back end authentication link so you can prevent think staff from accessing the console. And there is a third party assessment you can read on the canary site. It commends the secure design of the platform and the software stack implemented by thinkst.
01:43:38
They're really committed to your security and they make a device that every network should have. In fact, you probably should have several spread around your network. A small network like ours might have a half dozen. A big bank, a casino back end, might have hundreds, because you really want to catch that intruder once they get into your system as quickly as possible. Right, you don't want to wait for them to discover this one canary in the corner here.
01:44:04
Let me give you a pricing example Go to canarytoolstwit. $7,500 a year gets you $5. That's your own hosted console. You get upgrades, you get support, you get maintenance, you sit on your canary or anything, and anything goes wrong, they'll send you a new one immediately. If you use the code TWIT, by the way and how did you hear about us box, you'll get 10% off your canaries for life, not just for the first year, month or whatever for life, okay, there are hardware canaries, there are VM canaries, there are cloud-based canaries. They are deployed and loved on all seven continents. If you want to see who likes and uses the canary, go to canarytoolslove and you'll see all the testimonials Unsolicited, genuine customer love for the Thinxt canary.
01:44:53
I think this is a must for every network, but Thinxt is so confident you will like it. They give you a 60-day, two-month money-back, full refund guarantee, so there's no risk to trying these. So go out and order some, Take a look at them. You have two months to get them back for your money-back. I have to say, in all the years we've been doing these ads and it's I don't know, it's almost a decade now no one's ever asked for their money-back, because this is just a brilliant idea that belongs on every network. Visit canarytoolstwit. The code TWIT, get you 10% off for life. Put that in the How'd you Hear About Us box, canarytoolstwit. This is really brilliant and easy to use, easy to configure honeypot with all the bells and whistles, all the features you'd want. That doesn't add risk to your network. That adds security and the peace of mind when you don't hear from it and I haven't heard from it in literally a couple of years now that no one's in the network. I feel pretty good about that. Canarytoolstwit offer code TWIT and we thank him so much for the support of Steve and the great work he is doing here.
01:46:08
Privilege Now see, when I see this title I think I'm not understanding what you're talking about. You say the power of privilege. You mean the power of having money and power. Is that what you mean? Uh-oh.
01:46:27
Either either my watch has stopped or this man's not moving. Ah, we will reconnect with Mr G the power of your privilege. Ooh, tech Break 7894, capturing console game clips with Elgato's HD60X. Oh, there he is. Hey, what happened, dude?
01:47:15 - Steve Gibson (Host)
Um, it's actually. The timing of these little outages has been coincidental. I dropped off the net during the previous sponsorship and got back on.
01:47:24 - Leo Laporte (Host)
Before you finished I saw the thing I thought maybe you walked away. Oh my God. So this is now so. Somebody's watching the show and every time you go into an ad, there could only be one person. They're inside the house, steve.
01:47:38 - Steve Gibson (Host)
Well, either that or it's time to reboot my router and see what's going on. Anyway, I will, I will. We don't have much more to go.
01:47:45 - Leo Laporte (Host)
I was just saying I might misunderstand this title, but of course we who are privileged have power. What could possibly be wrong with that?
01:47:54 - Steve Gibson (Host)
That's right. So today we're going to continue our examination of the NSA's and CIS's top 10 cybersecurity misconfiguration mistakes by drilling down deeply into their number two misconfiguration, which is privilege. What strikes me most about this publication is that each item is quite beefy and worthwhile, you know, unlike some recommendation lists that we see. You know the feel like they were written by someone pontificating from an armchair. These resulted from their active, successful penetration of networks. So here's what they had to say on the topic of improper separation of user and administrator privilege, and then I'm going to embellish a little bit on that afterwards. So they wrote, administrators often assign multiple roles to one account. These accounts have access to a wide range of devices and services, allowing malicious actors to move through a network quickly after obtaining one compromised account, without triggering lateral movement and or privilege escalation detection measures. In other words, don't do that. That's not good privilege management. They said.
01:49:19
Assessment teams have observed the following common account separation, misconfigurations, excessive account privileges, elevated service account permissions and non-essential use of elevated accounts. Under excessive account privileges, they elaborate Account privileges are intended to control user access to host or application resources, to limit access to sensitive information or enforce a least-privileged security model when account privileges are overly permissive. Users can see and do things they should not be able to do, which becomes a security issue as it increases risk exposure and attack surface. And I would add that bad guys that are able to get in as that user are then also able to do things that they should not be able to do. They said expanding organizations can undergo numerous changes in account management, personnel and access requirements. These changes commonly lead to privilege creep, the granting of excessive access and unnecessary account privileges. Through the analysis of topical and nested AD active directory groups, a malicious actor can find a user account that has been granted account privileges that exceed their need to know or least privilege function. Extraneous access can lead to easy avenues for unauthorized access to data and resources and escalation of privileges in the targeted domain Under elevated service account permissions.
01:51:11
Applications often operate using user accounts to access resources. These user accounts, which are known as service accounts, often require elevated privileges. When a malicious actor compromises an application or service using a service account, they'll have the same privileges and access as the service account. Malicious actors can exploit elevated service permissions within a domain to gain unauthorized access and control over critical systems. Service accounts are enticing targets for malicious actors because such accounts are often granted elevated permissions within the domain due to the nature of the service and because access to use the service can be requested by any valid domain user. Due to these factors, curb-erosting as it's called curb-erosting, a form of credential access achieved by cracking service account credentials, is a common technique used to gain control over service account targets.
01:52:22
And finally, non-essential use of elevated accounts, they said. It personnel use domain administrator and other administrator accounts for system and network management due to their inherent elevated privileges. When an administrator account is logged into a compromised host, a malicious actor can steal and use the accounts credentials and an active directory-generated authentication token to move, using the elevated permissions throughout the domain. Using an elevated account for normal day-to-day non-administrative tasks increases the accounts exposure and therefore it's risk of compromise and it's risk to the network. In other words, don't do that. Don't be lazy admins and use your fancy elevated accounts if you're not actually needing to do so at the time.
01:53:26 - Leo Laporte (Host)
We still have to tell people this.
01:53:31 - Steve Gibson (Host)
And what's interesting is that these are the ways they have penetrated. They, the NSA and CISA, their red and blue teams have penetrated users' networks. They said malicious actors prioritize. Well, and Leo, again, of course, we believe it's true, right.
01:53:50
Because, it's easier just to use your God login, because then you're going to be able to do anything that you want to do. Their point is that if you happen to contact a compromised machine under that persona, the malware there can automatically compromise your credentials. By the way they said, malicious actors prioritize obtaining valid domain credentials upon gaining access to a network. Authentication using valid domain credentials allows the execution of secondary enumeration techniques to gain visibility into the target domain and active directory structure, including discovery of other elevated accounts. And, where the elevated accounts are used, such as domain administrator or system administrators performing day-to-day activities, provides the most direct path to achieve domain escalation. Systems or applications accessed by the targeted elevated accounts significantly increase the attack surface available to adversaries, providing additional paths and escalation options. And finally, after obtaining initial access via an account with administrative permissions, an assessment team here in the real world. After obtaining initial access via an account with administrative permissions, an assessment team run by these guys compromised a domain in under a business day. The team first gained initial access to the system through phishing, by which they enticed the end user to download and execute malicious payloads. The targeted end user account had administrative permissions enabling the team to quickly compromise the entire domain. Okay, so there are two primary things that I want to elaborate on and highlight. The first is that idea of mission creep. They called it privilege creep, and anyone who has been in charge of managing any complex environment of privileges will have seen and been fighting this.
01:56:21
I've often observed that code generally does not evolve well. By its nature, code is not designed to evolve. There will generally be an initial grand organizing concept for a project, and that vision will be then realized in code. But that organizing vision influences the code at all levels the way the large project is decomposed into smaller, manageable components, the way those components talk to each other and what they're able to say, and how the data structures those components use to capture and manage the project state. Every one of those things is individually generally static and they're interdependent, and thus the whole system is quite resistant to change. I've also observed that it's often the case that once a project is finished, it really should be entirely discarded, then redesigned and reimplemented from scratch. The reason for that is not necessarily that the project itself evolved during its implementation, but that those who were implementing it evolved. In other words, they were changed by doing the work, because the process of solving any sufficiently complex problem teaches those who are solving it how it should have originally been designed in the first place. So for sufficiently complex projects, several iterations of that sort can be required. Unfortunately, of course, outside of academic settings, the luxury of multiple iterations is seldom available.
01:58:10
Okay, so how does that apply to account privileges? The primary message here is that the management of privileges provides a tremendous amount of power and, as always, with power comes responsibility. Any major enterprises account privileges hierarchy needs to be carefully designed. In a sufficiently complex environment, the concept of least privilege is much more easily espoused than it is implemented. Mistakes in either direction of privilege result in problems. Users need varying levels of access, and differing groups of users may have both disjoint and overlapping regions of access at the same level. Autonomous devices also need their own access privileges, like printers scattered around, and it's difficult enough to get everything set up correctly, given a static environment without any change. But when did nothing ever change? The real test is the test of time brought about by an enterprise's evolving structures and needs. What this means is that any initial design will be almost immediately obsolete once it faces reality.
01:59:37
The asymmetry of privilege is another factor. Too little privilege and things don't work or break. Printers don't print, users are unable to do what they need to do and the boss is not happy. Too much privilege and sure everything works, but users can get up to mischief and things are made much easier for the bad guys once they get in, and again the boss is not happy. So assigning and managing privilege is a bit like walking a tightrope Stepping off in either direction does not produce a good result.
02:00:16
I think the best advice that can be given is to clearly recognize and accept that the proactive management of privilege is a truly important aspect of the enterprise's entire operation. Designing and managing an enterprise's account and access privileges should never be a grudging afterthought. Be sure to give it its due. Fortunately, it's never too late to repair an organization's no longer strictly applicable privilege model. It can be fixed. If this is your responsibility, you likely already know what needs to be done. Don't wait until it's too late. Next week we'll continue moving through this excellent joint NSA CISA document as we keep up with the news of the week.
02:01:09 - Leo Laporte (Host)
You know, it strikes me that Linux users and Unix users in general are constantly warned not to use the root account and they're provided with a great little command, as you do, so that they can easily escalate for one command and one command only. Then it reverts back to the normal user privilege.
02:01:31 - Steve Gibson (Host)
And we know that even Microsoft finally came up.
02:01:34 - Leo Laporte (Host)
They invented that split token system where you know I was going to say I think Windows users are a little brain damaged because so many of them operate as administrator. And then you know that's why you're right, they created UAC. But they created UAC because people were not operating as limited users, so they had to create the user access control as a automated way of keeping you from getting in trouble. Well, but I think that's caused brain damage. I think that's caused people to think it's okay to operate as an administrator.
02:02:07 - Steve Gibson (Host)
Well, and you point out that SUDU was easy to use and it was the ease of use that made it feasible to run with non elevated privileges. Exactly, windows didn't have an easy way. No, exactly, honestly, no one wanted to log off and then log back in as an admin in order to install a piece of software.
02:02:35 - Leo Laporte (Host)
And, by the way, we should say Apple's done pretty much the same thing with Mac OS. They have a limited user and in fact when you create a new user, by default that's a limited user, but everybody runs it in admin, and so Apple does the same thing that Microsoft does with this kind of temporary escalation process. But so much better to do it like Linux does, I think.
02:02:54 - Steve Gibson (Host)
Yes, and as I've said before, operating a truly secure OS is just no fun. Because, you can't get anything done. You spend all your time saying yes, I'm sure. Yes, it's me. Hello, I'm still here.
02:03:12 - Leo Laporte (Host)
Yeah, I think you could argue that SUDU is a better way to do it than user access control, than the escalation prompts. I mean you, fairly frequently you'll run a command and says you don't have enough privilege to do that and in many Linux, distressed many terminals, there's a simple command keystroke that adds SUDU to your previous command so you can easily escalate. I don't know, I just maybe it's just me, but I prefer that way of doing things and nevertheless run as an administrator both on Mac and Windows. There you, by the way, you cannot, without some, without basically rooting it, run as an administrator on either iOS or Android. Why do you think it's dangerous? Right, they don't even have a way to escalate privilege. You know you're a user, whether you like it or not.
02:04:05 - Steve Gibson (Host)
Yeah, and in those environments it really makes sense to for the OS to be the sole arbiter of what runs and how Right.
02:04:19 - Leo Laporte (Host)
I love this show and I'm so glad you're going to keep doing it. Here we are at episode 945. At this point I would have been kind of like counting down the days. Oh, there's only a year left. Oh no, but we're going to go until one or the other of us, or maybe both, kills over, whether it's with exhaustion or the final journey, the final Well.
02:04:43 - Steve Gibson (Host)
I'm glad I'm going to be here for the end of support of Windows 10.
02:04:47 - Leo Laporte (Host)
Yes, and I hope you'll be here for the end of the Unix Epic and oh, that'd be good. 2038, baby. Oh wow. That's my goal.
02:04:59 - Steve Gibson (Host)
Steve Gibson. We only have 15. We only have 15 more years. That's not it. We've more than halfway there.
02:05:03 - Leo Laporte (Host)
Steve, exactly, it's easy peasy. Steve Gibson is a grccom. That's where you can get Spinrite, the world's best mass storage maintenance and recovery utility. I mean, you've seen some of these even today, some cool stuff you can do with Spinrite Now and, by the way, a lot of other programs in the office for free. Now it is important to note that Spinrite 6.1 is imminent. He's already giving people copies. If you buy 6.0 now, you will get an automatic upgrade to 6.1, a free upgrade.
02:05:36
Grccom you should pick this up. Everyone who has mass storage needs this, plus Validrive and all the other fantastic free things you offer. I use Shields up every time I set up a new network. I can go on and on grccom. You can leave a message there for Steve at the feedback form, grccom. He's also on X at SGGRC Not a regular user, but I guess you still are looking at DMs and stuff there, yep, yep.
02:06:07
And we have copies of the show at our website, twittv. There's also a way to get ad-free versions of the show. Actually, there's two ways. If you go to twittv, you can. If you just if you say I don't care about anything else, you do 2.99 a month, you get ad-free versions of security now. But if you want a little bit more, for a few bucks more $7 a month you can get ad-free versions of everything we do. You can get access to our Discord, which is a great place to hang, much better than Twitter or anywhere else, because it's all kind of engaged and interesting people who are geeks. So every topic under the sun there you can talk about whatever you like, including our shows. Plus, you get special programming we don't put out anywhere else, including on Thursday at 3pm Pacific, 6pm Eastern.
02:07:01
I'm going to put on my wizard's hat and we are going to do an escape room. I don't know if six of us I'm not sure which of the twits will be there, but I will be in my wizard's hat and we are going to attempt to escape and you can mock us in our stupidity. It should be so much fun. That'll be in the club. We do shows like Home Theater Geeks with Scott Wilkinson, hands on Mac, hands on Windows and Deadly Linux show All sorts of great stuff just for the club. We're trying to make it of value and I think that's seven bucks a month is very well spent and really the most important reason to spend it is because you want to support what we do and you want us to continue on, and in today's economic climate, especially for podcast advertising, it's it's touch and go. Right now, your support really makes a difference. Twittv slash club twit. You can chat about the show if you watch it live at IRCtwittv or in the club twit discord.
02:07:55
We are live every Tuesday 1 30 Pacific, 4 30 Eastern 20 30 UTC for one more week, and then we're going to slip into, say, a standard time. So that will change, that'll change. We'll fall, spring back, fall forward, right, we'll fall forward. That means what's weird and would always confuse me. If we fall forward, we're going to happen an hour earlier for you, right? Or am I wrong? I don't know, it's crazy, or is it an hour later? Anyway, I will figure it out before then. Just remember. Just remember it's a 20 30 UTC. It'll be 21 30 UTC in two weeks. Let's put it that way. I know that.
02:08:36
What else? You too? There's a fully devoted to securing out video YouTube Plus, of course. You can subscribe. The easiest way to do that is go to our webpage Twittv slash s, and you'll see some buttons for popular podcast apps like Google's and Apple's and pocket casts, but you can use it for anyone. Obviously, there's an RSS link there you can use for that and if you subscribe that way, you'll get it automatically and you can start building your collection of all 945 episodes of security. Now it's about this many episodes and you can have them all and you should have Steve. Have a wonderful week. I will see you next time on security. We'll do, my friend next week for 946.
02:09:21 - Steve Gibson (Host)
Bye, bye. Today.