Security Now 941, Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Ant Pruitt (00:00:00):
Hey, it's time for security. Now I'm Ant Pruitt sitting in for Mr. Legal Report while he's out enjoying a Green Bay Packers game. That is still so funny to say. This week I'm sitting with Mr. Steve Gibson as he goes through some interesting news here in the world of cybersecurity. We have the N SS A hacked Huawei. Well, yeah, several years ago is that early news? We also take a look again at what's been going on with LastPass and some of the implications regarding [00:00:30] their previous breach and also that algorithm doesn't quite add up. Y'all stay tuned.
(00:00:49):
This is Security Now episode 941, recorded Tuesday, September 26. 2023. We told you so.
(00:01:00):
[00:01:00] This episode of Security Now is brought to you by Delete Me, reclaim your Privacy by removing personal data from online sources. Protect yourself and reduce the risk of fraud, spam, cybersecurity threats and more by going to join delete me.com/twit and using Code TWIT for 20% off and by our friends at IT Pro tv now called ACI. Learning acis new cyber skills is training. That's for everyone, not just the pros. Visit go dot aci learning.com/twit. [00:01:30] Twit listeners can receive up to 65% off an IT Pro enterprise solution plan after completing their form. Based on your team's size, you'll receive a properly courted discount tailored to your needs, and by Melissa more than 10,000 clients worldwide. Rely on Melissa for full spectrum data quality and ID verification software. Make sure your customer contact data is up to date this holiday season. Get started [00:02:00] today with 1000 records clean for free at melissa.com/twit. Hey, what's going on everybody? I am Matt Pruitt and this is Security. Now here on twit TV with the one and only demand of the hour or a couple hours. Mr. Steve Gibson. How you doing, sir?
Steve Gibson (00:02:19):
Yes, I think we could probably fill our listeners time with a couple hours of all kinds of neat security information and news and this week we are no exception. [00:02:30] We're chockfull of questions. Oh yeah, why is my new valid drive freeware not published yet? Why did Apple quietly remove P D F rendering from the Mac after 39 years? Has the N SS A been hacking China? What mistake did Microsoft recently make that would require the use of a bigger hard drive? Why did Signal just announce their use of post quantum crypto? What's the big hurry? Is it possible to create [00:03:00] a new web browser from scratch and if not, why not? Does public key crypto really go both ways? Can pure math generate pure random numbers? One of our listeners believes he has could encrypting an entire hard drive then throwing away the key be used in place of random noise wiping, which is what I'm a big fan of. Why hasn't the Unix time problem been fixed yet? Or has it? Will all [00:03:30] of the stolen LastPass vaults eventually be decrypted? Am I really leaving Twitter? And finally, why in the world is this episode titled we told you so? The answers to those questions and more will be revealed by the time we're done here today. Welcome to episode 941 of Twits Security Now podcast.
Ant Pruitt (00:03:54):
Oh man, this is going to be a lot of fun. And I got to tell you, I'm looking [00:04:00] forward to that last pass discussion because I have some thoughts and I'm sure you're going to set me straight as well as set everyone else straight here on the show for folks that are tuning in and thinking, wow, Leo's voice is really different or wow, boy, he's got a super tan going, no, Mr. LaPorte and the family, they are out of town having a good old time up in Lambo Field or actually Green Bay, Wisconsin having a good time birthday celebration [00:04:30] with their son as well as some local twit fans are there in town too and they're going to hang out together. It's going to be a good time. So if you're in that area, be sure to go by and say hello. I'm going to hang out today and get as much knowledge as I can from Mr.
(00:04:46):
Steve on all of this InfoSec stuff because it's always fascinating. But before we do that, I want to go ahead and take a few moments to thank our first sponsor of security Now today. This episode of Security Now [00:05:00] is brought to you by Delete Meme. Have you ever searched for your name online and didn't like how much of your personal information was available just floating around out there now? Did it make you feel exposed or unsafe? Since 2010? Delete Me has been on a mission to empower individuals and organizations by allowing them to reclaim their privacy and help them remove their personal data from online sources. Their [00:05:30] team is driven by a passion for privacy and commitment to making it simple for customers to use. Delete Me helps reduce risks from identity theft, credit card fraud, robocalls, spam, cybersecurity, threats, harassment, and all kinds of other unwanted communications.
(00:05:47):
Overall, delete Me is the most trusted privacy solution available helping thousands of customers remove their personal information online. Now, did you know that the average person, more than 2000 bits of data about [00:06:00] them online that Delete me can find and remove? That's key. Now think about how much time that saves you trying to filter and find all of that stuff. Oh, this is a good service. One customer said I signed up and they took it from there. Awesome service already seeing results and I have used Delete Me. They gave me an account to try out and I got to tell you, it is the simplest process. You literally just pop in and fill out a form and give 'em just a little bit of [00:06:30] information about yourself. Hit Go boom, and they're off to the races looking for all of that crazy stuff online that's attached to you.
(00:06:39):
So let me tell you exactly how it works here. First, you sign up and you submit basic personal information for removal from search engines. The next Delete Me experts will then find the remove your personal informations from hundreds of data brokers helping to reduce your online footprint and keeping you and your family safe. So that's another [00:07:00] thing, it's you and your family. You may have an online account out there somewhere, but it may also be tied to your spouse. So not only are you getting spam, but your spouse is getting spam for some crazy stuff you done. Done Delete Me is going out there to help clean that stuff up. Now once the removal process starts, you'll receive a Delete Me report within seven days and it doesn't stop there. Delete me will continue to scan and remove personal information every three months or so.
(00:07:29):
And with automated [00:07:30] removal opt-out monitoring, they will ensure records don't get repopulated after they're being removed. So tricky people. Oh, so tricky. Now this includes names, addresses, photos, emails, relatives, phone numbers, social media, property value, and a whole lot more. As data broker industries evolve, delete Me continues to add new sites and features to ensure that their service is both simple [00:08:00] and effective in removing personally identifiable information out there. And since privacy exposures and incidents affect individuals differently, their privacy advisors ensure that all of their customers have the support they need when they need it. Now this is my call to action to you to wonderful twit listeners, protect yourself and reclaim your privacy by going to join delete me.com/twit [00:08:30] and then using the code twit. That's join delete me.com/twit and code TWIT for 20% off. We thank Delete me for supporting us here at TWIT and for sponsoring this episode of Security Now. Alright, so Mr. Steve, what's going on now? What you got for us today to start the show?
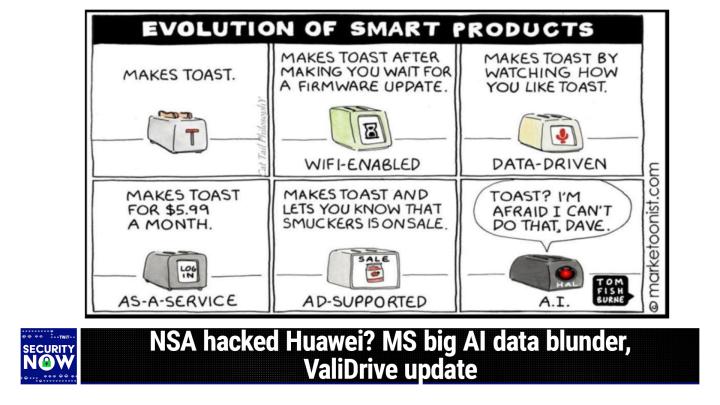
Steve Gibson (00:08:55):
Well, we always have a picture of the week, so [00:09:00] this week's no different. This one is a six frame cartoon, which shows the evolution of a particular well-known product category. This is a toaster, so we have the original toaster in the first frame, which it's got a little handle on the side and it makes toast. Perfect. Now we're going to then, right, exactly. Unfortunately that's probably the optimal condition for the [00:09:30] toaster because then the next frame, it's been wifi enabled. So we've got a screen on the side showing an hourglass. This makes toast after making you wait for a firmware update, so not clear, that was actually a benefit. Then we move to the data-driven toaster, which makes toast by watching how you like toast.
(00:09:56):
Then we evolve to the toast [00:10:00] as a service, which makes toast for $5 and 99 cents a month. And there's a screen on the side of this toaster that says Log in. So that's right. Now you've got to log into your toaster in order to brown your bread. The fifth frame here is the AB supported toaster. It's got a larger screen, it wants to make sure you see the ad and it makes toast and lets you know that Smuckers is on sale today. [00:10:30] And finally in the final frame of this, we've got the AI enabled toaster. It's got that red glowing eyeball from the how 9,000 of
Ant Pruitt (00:10:46):
What is? It's that
Steve Gibson (00:10:48):
Space? No, not space,
Ant Pruitt (00:10:50):
No, the Hitchhiker's guide. Is
Steve Gibson (00:10:52):
That the one? No, no, no. It's two bricks. 2001 A Space Odyssey. Oh, thank you. John. Of course
Ant Pruitt (00:10:59):
Used Jamer [00:11:00] bhi room. They got it.
Steve Gibson (00:11:01):
Just blanking on it. Anyway, so this AI enabled toaster is actually responding to us. It says toast. I'm afraid I can't do that, Dave.
Ant Pruitt (00:11:14):
So
Steve Gibson (00:11:15):
Yes, not exactly an advance as far as toast goes, which sort of tells you sometimes you just need to keep the microprocessors away from your appliances because there's no real value to be added there.
Ant Pruitt (00:11:26):
What's so funny is I'm looking at those images and [00:11:30] as you're going through each cell, my brain is automatically assigning a big tech company to each cell. It fits a lot of them quite perfectly. For example, the ad supporter or as a service could clearly be Amazon easily. But anyway, what's going on with value drive, sir?
Steve Gibson (00:11:50):
Value drive. So I received messages from listeners who are anxious to start testing their various U S B flash drives with GRCs forthcoming [00:12:00] valid drive freeware utility. You may not know, but it turns out that there are a lot of counterfeit or fake flash drives now on the market. Oh yeah, I've heard Amazon, they made
Ant Pruitt (00:12:14):
'em super fast supposedly, and there's nothing in there but some standard like a V 90 chip in there, which should
Steve Gibson (00:12:21):
Be something better, right there is that. And also the big problem is thumb drives that claim to be one or two terabytes but only have [00:12:30] a 32 gig chip in there. And what's diabolical is that the memory is at the beginning of the drive where the file system is. So it looks like it's formatted. You can even be storing data there and so the file system is there. And of course we actually heard a story where someone purchased a, and you'll appreciate this as a photographer, got a compact flashcard that [00:13:00] was counterfeit, stuck it in their camera, took wedding photos throughout. All of the wedding process came back. The photos were not stored because all of the file system file names were there, but actually out in the drives real estate, there was no memory. So if the camera thought it was writing them, but they were not actually being recorded.
(00:13:28):
So anyway, so [00:13:30] as is usual for me, this little side project is taking longer than I expected. I announced it a couple weeks ago, I guess three or four weeks ago. And since I paused the completion of spin right six one right on the verge of getting that finished, I do feel a great deal of pressure to get valid drive finished and back to work on spin, right? But I don't believe that I'm going to look back and feel that this was a mistake. All of my previous low level drive work has been [00:14:00] in dos where of course spin right still lives and in dos it's possible to own the entire machine. It turned out that Windows U SS B chain fought back and interfered with valid drive's operation much more than I expected. So getting this done correctly was quite involved, but it has made valid drive unique because it now incorporates a bunch of technology that's not available elsewhere and along the [00:14:30] way I've developed a lot of new code that's going to be very useful for future U S B work under Windows like for GRCs secure drive wiping utility, which will happen in the future and although that doesn't help us today, it will in the future and I always take the long view since I plan to be around and active for quite a while.
(00:14:52):
Yet please and thank you. Today Vdrive appears to be working well and it's being heavily tested [00:15:00] and used by GRCs Testing Group. It has opened my eyes about just how severe this fake U S B drive problem has become while none of us were really paying that much attention to it. So I'm not quite ready to turn it loose because once it's finished, I don't want the distraction of needing to keep coming back to fix little issues that I ignored out of a rush to publish. I want to get back to spin right six one and then immediately on to spin write seven. So little [00:15:30] things like not saving its reports properly on screens where Windows font sizing is set to other than a hundred percent or some of its UI text not appearing when a user's screen is set to high contrast mode or when a user may be unable to discern closely similar colors, clearly they've got a little bit of a colorblindness problem.
(00:15:53):
Anyway, those are details that I need to put behind me so that what's published will be finished and probably [00:16:00] useful for years to come. Anyway, I also mentioned creating and saving reports. So yes, there's been a little bit of feature creep along the way. It's a little more than I had initially expected to get finished anyway, it's become very nice and it's a useful utility, which I'll formally announce and publish as soon as possible. Anyway, so I just wanted to get that out of the way because people have been saying, Hey, where is it? So it's all working well and it's coming soon. Outstanding. So [00:16:30] the Eclectic Light Company posted a blog entry that had an interesting piece yesterday, which they titled Postscripts Sudden Death in Sonoma. Now they don't mean Sonoma, California. Well actually Apple was referring to Sonoma, California, but in this case Sonoma refers to the major, the most recent major MAC OSS release.
(00:16:59):
And their [00:17:00] article has some interesting observations about Postscript as a dangerous interpreter, which shouldn't surprise any of our listeners. So I want to share what they wrote and I'll comment a little bit in line. And on the other side they said if there's one language that's been at the heart of the Macintosh for the last 39 years, it's Postscript, the page description language developed by the founders of Adobe, the late John Warnock and [00:17:30] Adobe's team of engineers. It brought the max first commercial success in desktop publishing in Postscript fonts and early Postscript printers including Apple's game changing laser writer, although Mac OS 10 never inherited. Next steps display Postscript, its descendant courts and core graphics are still based on Postscripts relative, which is the P D F. So just to be clear, it's Postscript, which is the issue [00:18:00] here being discussed. Not PDFs per se.
(00:18:03):
PDFs are still around and obviously heavy use. So they said following a short illness that started in Mac oss Monterey 12.3 postscript has died suddenly in Sonoma. The first sign passed almost unnoticed in apple's release notes to Mac OSS 12.3 where it recorded the so-called deprecation [00:18:30] of postscript in WebKit. Apple said Support for inline viewing of postscript files is no longer available. So that was just sort of like in passing in WebKit, but it sort of did indicate where things were headed that in Mac OSS 13.0 preview lost the ability to convert postscript and EPS files. Apple said the preview app included with your Mac supports [00:19:00] Postscript PSS and encapsulated postscript E P s files in Mac oss Monterey or earlier starting with Mac os Ventura, postscript, I'm sorry, preview no longer supports these files. So again, a little more deprecation of this. They said other apps that can view or convert PS and EPS files are available from the app store and elsewhere.
(00:19:27):
Finally wrote the blog, the [00:19:30] complete removal of support for Postscript and EEPs was recorded as another deprecation in the release notes for Sonoma. So Postscript, they finish saying, is an old stack based interpreted language designed at a time when code security had barely been conceived and malicious software hardly existed. Among its attractive features [00:20:00] is the fact that any postscript object can be treated as data or executed as part of a program and can itself generate new objects that can in turn be executed. Okay, now I'll just pause here for a minute to observe that Windows meta files, which turned windows drawing primitives into an interpreted format originally had that same capability of executing [00:20:30] code. That's just the way things were done back then. When this was rediscovered many years later, everyone freaked out thinking it was a horrific bug and many people thought that I was nuts when I calmly observed that it was clearly originally deliberate.
(00:20:51):
It's definitely a bad idea today because so prone to abuse, but it was entirely reasonable at the time. Everyone [00:21:00] just forgot it was there. As this article says, postscript is an old stack based interpreted language designed at a time when code security had barely been conceived and malicious software hardly existed. Exactly. Makes sense. Yeah, and I'll just make one other note. Although stack based languages can be brittle back at the time, defining a stack based language was a terrific choice by Adobe [00:21:30] because stack based representations and interpretations can be incredibly dense and efficient and that's what you would want in a page description language where there are effectively no processor cycles and no easy memory. So Postscripts design was brilliant. So anyway, their article continues. More recently, security researchers have drawn attention to the fact that postscript [00:22:00] is a gift for anyone wishing to write and distribute malicious code as it's effectively an image format.
(00:22:10):
Embedding malware inside a postscript file could enable that to be run without user interaction. As is the case with other graphics formats, you just, any kind of preview will cause that file format to be interpreted. And we've seen exactly that happening in the not too distant past. [00:22:30] The article says there are three major postscript interpreters today in common use. There's still Adobe's distiller engine, which is built into its acrobat products. There's Apple's PSS normalizer engine, which is built into Mac OSS and artifacts open source engine built into Goss script and that's one that's widely used in Linux and other platforms because it's open source. They wrote research [00:23:00] into those engines has so far been relatively limited but has revealed some serious vulnerabilities. Most recently, Kai Lou and Brett Stone gross of Zscaler Threat Labs published an account of three vulnerabilities they found in distiller and one in apple's PS normalizer.
(00:23:21):
That was in 2022. Those were fixed by Adobe and Apple last year. In the later case in Mac OSS Monterey, which was [00:23:30] version 12.5, released on the 20th of July of last year, 2022, and its equivalent security updates for Big Sur and Catalina. They had to push those back also. And from the dates I suspect that the removal of support for inline viewing of postscript files and WebKit in moderate 12.3 may also have been part of Apple's mitigations. Anyway, they wrote, apple was most probably prompted into conducting a security [00:24:00] audit of their PSS normalizer as a result of the vulnerability which was reported and would've been faced with the choice of either re-engineering it or removing it from Mac OS completely. The problem is it was just too dangerous as it was. And these guys note, unlike the P D F engine in courts, PS Normalizer is now little used and has no significant role any longer in MAC oss.
(00:24:29):
So I mean [00:24:30] that is a reason to remove something that is inherently dangerous. So the first step was to make it inaccessible from the GUI by disabling the feature in Ventura's preview. Then following that in Sonoma by removing PSS normalizer altogether. So removing its command tool, which is PSS to P D F and the COREO graphics C G P S converter, this leaves those still wishing to convert postscript files with a choice between [00:25:00] Adobe's distiller, which you would have to pay for because it's in their Acrobat products or artifacts go script. And to be fair, that's had its own share of vulnerabilities. Again, this is not P D F is a fundamentally dangerous format. It is not easy to get it right because it is so old and is so complex. And the article did mention there's also a third option, which would be to run a late version of Mac OSS Monterey, where you [00:25:30] still have postscript in a lightweight virtual machine.
(00:25:34):
And that way you could continue to use apple's PSS normalizer through preview there and for most people, that would probably be the cheapest and simplest option anyway. John Warnock, the co-founder of Adobe and the driving force behind Postscript died on the 19th of August this year, and his page description language had brought success to the MAC for almost 39 years. And even though he [00:26:00] hasn't though the P D F format has lived on, so anyway to Apple, I say Bravo, it is always difficult to kill off features that have any audience, right? Somebody's using it, somebody's going to be unhappy. And as we've seen through the years, apple takes some heat whenever they decide to break the status quo in the interest of a better future. Postscript, [00:26:30] as I said, is a big old and very dangerous interpreter. There is no doubt that some people will complain that's inevitable, but the fact that something that's inherently dangerous could be removed with relatively little repercussion suggests that Apple has once again made the right call. So yeah, I just wanted to point out that it's gone from Mac OS P D F is still there, but not, not [00:27:00] sort of the underlying postscript interpreter and that's certainly best.
Ant Pruitt (00:27:06):
You referenced just some of the issues that we've had and known about over the years with P D F format and yet we still continue to fight to get those squared away, but it's still a problem. Are there any alternatives for A P D F? I mean we can't necessarily say TIFs or P and GSS or anything like that. Everything is fairly [00:27:30] open to being compromised. Do we have any other options out there for something that's going to give us the same performance in reliability of A P D F?
Steve Gibson (00:27:39):
Well, yeah, the problem is that image formats are not a replacement for a page description language we have. Well, the reason you are looking at A P D F of the show notes is that it is the show notes captured in basically in a printed format, and that's what makes the [00:28:00] P D F format unique. It also is not easy to do, which is what makes it complicated. And as we know, complexity is the enemy of security. So if something's going to be complex, there's probably ways to hack it and it's
Ant Pruitt (00:28:13):
Probably a hole somewhere, right? Yeah,
Steve Gibson (00:28:15):
Exactly. So has the N S A hacked Huawei and the answer is, well yeah, back in 2009, what's weird is that last Tuesday [00:28:30] China's Ministry of State Security published an extremely rare as in extremely as in the first time ever official statement on its WeChat account. It formally accused the US National Security Agency of hacking and maintaining access to servers at Huawei's headquarters since 2009. Now, okay, what's interesting is not that this is news, it's that it's not [00:29:00] news. So I'm mentioning this because this reflects a relatively sudden change in stance for China and it suggests that this might just be the beginning. The question is the beginning of what both the New York Times and S Spiegel originally reported this back in 2014, based upon documents from the Snowden links, which disclosed a program called Shot Giant, [00:29:30] which was an N S A operation to compromise Huawei's network for the purpose of finding links which existed or they thought might exist between Huawei and the Chinese P L A to learn Huawei's internal corporate structure and also to identify ways to exploit Huawei's equipment, which at the time was being widely adopted in both the US and by our allies [00:30:00] and adversaries.
(00:30:01):
So this is the first time the Chinese government has ever publicly confirmed the NSA's Huawei hack and they posted it on their WeChat channel. So sort of seems more political than not. The Chinese Ministry of State Security Statement didn't go into any technical details about the actual hacking, like they apparently didn't know any more than we've all known since 2014. It just recycled [00:30:30] information that was published by the New York Times and their Spiegel and the Snowden leaks. It does, however, spend a lot of time accusing the US of using, and believe it or not, I'm quoting this the despicable tactics of the matrix to maintain a cyber hegemony. So to that end, Chinese officials claim that the US is doing all of the intellectual property stealing and then [00:31:00] using its allies and PR machine to hype exaggerate and smear China on Chinese cyber secret stealing issue.
(00:31:10):
So a cyber threat analyst at the Taiwan based security firm team T five was quoted saying, considering the close relationship between China's cybersecurity firms and the Chinese government, our team surmises that these reports could be part of Chinese [00:31:30] of China's strategic distraction when they're accused of massive surveillance systems and espionage operations. So there've been several other recent reports of N S A penetration into China's space, into their networks, and I suppose none of us assumed that the cyber intrusions were all going one way, that there was no pushback against [00:32:00] China's much publicized intrusions into the us We have an N SS A and all of those people dressed in camo must be up to something. So it seems as though the Chinese government may have changed their policy rather than pretending to be invulnerable. They've decided that the better strategy is to acknowledge that the US is also intruding into Chinese affairs. This might also be a reaction to China's very high profile [00:32:30] and heavily publicized intrusion into Microsoft recently and their exploitation of their access to enterprise email. But there does appear to be a difference. The evidence we have suggests that when we get into their networks, we just snoop around to gather intelligence. We get when they get into our network's proactive damage results. [00:33:00] So I mean it's not just espionage, it's attacks as we recently saw. It depends
Ant Pruitt (00:33:06):
On who you ask. That's either way it's still an attack just because I didn't come in there and break something that still doesn't say
Steve Gibson (00:33:15):
That, oh no, that's less wrong than they're certainly not happy to have the N S A establishing a persistent presence within their country's internal private networks. As we recently [00:33:30] saw that Chinese attack on Microsoft took a great deal of effort that demonstrated that they have some serious cyber skills, but sometimes you just trip over a pot of gold. That was the case when a misconfigured Azure shared access signature, a so-called SS a s token, resulted in 38 terabytes of hypersensitive Microsoft [00:34:00] data being exposed, not just for the taking. Well, for the taking, but more than that. Okay, so what happened? A cloud security focused group known as Wiz Research, and just to note, that's not Wiz. There's no H, it's just Wiz as in Wizard. They stumbled over a trove and I mean trove as in we're going to need to get a bigger drive [00:34:30] over here.
(00:34:32):
Wow. Trove of Microsoft data. It was all exposed and sitting there out on the internet. The Wiz Wizards explained, they said as part of the Wiz research team's ongoing work on accidental exposure of cloud hosted data, the team scanned the internet for misconfigured storage containers. In this process, we found a GitHub repository [00:35:00] under the Microsoft organization named Robust Models Transfer, and as an aside, it sounds like maybe the models were robust, but the security was not so much. They said the repository belongs to Microsoft's AI research division and its purpose is to provide open source code and AI models for image recognition. They said readers of the repository [00:35:30] were instructed to download the models from an Azure storage r l. Okay, so that sounds kind of deliberate, right? Like that doesn't sound so bad, but okay, now we're getting to the bad part. They wrote this U R L allowed access to more than just open source models.
(00:35:52):
It was configured to grant permissions on the entire storage account exposing additional [00:36:00] private data by mistake. They said our scan, and actually they did a little more than scanning. We'll get to it in a second. Our scan shows that this account contained 38 terabytes of additional data including Microsoft employees personal computer backups. Oh boy. The backups contained sensitive personal data including passwords to Microsoft Services, secret [00:36:30] keys, and over 30,000 internal Microsoft teams messages from 359 Microsoft employees, and that's where you say Whoopsie. Now it occurs, it also occurs to be from this report that you don't know that there are 30,000 internal Microsoft teams messages from exactly 359 [00:37:00] different Microsoft employees without doing a great deal of data analysis and counting things. I mean, if you've got 38 terabytes of data, you got to dig around in there. They also knew that there were employees, personal computer backups and that those backups contained sensitive personal data including passwords to Microsoft services and secret Keys. So wow. As I said, they probably did need [00:37:30] to get a bigger drive to hold all of that. Unbelievable. I know. So the report continues to explain. In addition, they said to the overly permissive access scope, the token was also misconfigured to allow full control permissions instead of read only. Meaning not only could an attacker view all the files I know in the storage account, they could delete and overwrite existing [00:38:00] files as well. In other words, change anything they wanted. Okay, now wait a minute.
Ant Pruitt (00:38:05):
Can you imagine the attackers showing up and getting in and was like, yes, just celebrating It was like this can't be this easy.
Steve Gibson (00:38:15):
Like I said, the Chinese cyber attack that got a hold of Microsoft's corporate email that required some skills here, Microsoft literally left the door open,
Ant Pruitt (00:38:28):
Doors open,
Steve Gibson (00:38:29):
And really [00:38:30] these guys said meaning not only could an attacker view all the files in the storage account, they could delete and overwrite them, but this really does cause us to question the use of the term attacker here. If you pick up a lost U SS B thumb drive in a parking lot, have you attacked anyone? It seems to me you're just observant, right? You just saw [00:39:00] the drive sitting there. So if Microsoft is waving their arms around and saying, Hey, come over here and download a bunch of stuff using this U R L Oh, and while you're here, how would you like to read 30,000 pieces of private internal corporate communications from 359 of our employees and poke around in some of their computer's backups? Does that qualify as an attack? If you say, well, thank you. That does sound interesting. Microsoft has a weird [00:39:30] way of doing honeypots now.
(00:39:31):
Wow. So anyway, these wiz wizards said this is particularly interesting considering the Repository's original purpose providing AI models for use in training code. The repository instructs users to download a model data file from the s a s link and feed it into a script. The file's format is C K P T, which is a format produced by the TensorFlow library. It's formatted [00:40:00] using python's pickle formatter, which is prone to arbitrary code execution by design, meaning an attacker could have injected malicious code into all the AI models in this storage account, and every user who trusts Microsoft's GitHub repository would then have infected by it. In other words, this could have been really [00:40:30] bad. They said, however, it's important to note this storage account wasn't directly exposed to the public. In fact, it was a private storage account. Here's what happened. The Microsoft developers used an Azure mechanism called S a s tokens, which allows the creation of a shareable link granting access to an Azure storage accounts data.
(00:40:57):
This means that upon inspection, the storage [00:41:00] account would still seem to be completely private, but as we now know, it was anything but in Azure, a shared access signature. S a s token is a signed U R L that grants access to Azure storage data. The access level can be customized by the user who creates the U R L with permissions ranging from read only to full control. While the scope can be either just a single [00:41:30] file, just a container or an entire storage account. And as we know, that's what happened here. The expiration time is also completely customizable, allowing the user to create never expiring access tokens. This granularity provides great agility for users, but it also creates the risk of granting too much access. In the most permissive case, as was the case with Microsoft's token above [00:42:00] the token can allow full control provisions on the entire account for essentially providing the same level of access as the account key itself.
(00:42:14):
So okay, we could be glad or at least hope that adversarial cyber attackers did not stumble upon this. We can be glad that the Wiz research guys did and that they [00:42:30] promptly after doing apparently a bunch of counting to see just how much of what was there, gave Microsoft a heads up about this little misconfiguration mistake, and I noted that Microsoft's own Microsoft Research M S R C blog posting for this incident was titled, got to Love this Microsoft Mitigated Exposure of Internal Information in a storage account due to overly [00:43:00] permissive s a s token. Okay? Right.
Ant Pruitt (00:43:04):
Overly permissive.
Steve Gibson (00:43:05):
Overly permissive, and they mitigated the exposure. Wasn't that nice? I won't spend any more time on this other than a note that in Microsoft sharing of what they called their learnings, yes, they actually did call it that their learnings from this, they never got around to mentioning just how much of their highly sensitive data had been flapping in the breeze.
Ant Pruitt (00:43:29):
Well, of course they [00:43:30] wouldn't. That's how big tech works. That's how big corporations work. That's right. Yeah. We had an attack, so let's just keep this story as minimal as possible. Yep.
Steve Gibson (00:43:41):
Okay man. One more story then we'll take a break. Alright. Signals P Q X D H, quantum resistant encryption. Now the signal encrypted messaging platform was originally named Axel Lot, [00:44:00] believe it or not. Wait, what? Yes, it was called Axolotl. I'm
Ant Pruitt (00:44:07):
Glad they had a branding meeting,
Steve Gibson (00:44:13):
A X O L O T L, which still seems like it's missing some vowels or something. Axel, they called it that it is named after a Newt n e w t a new which has self-healing [00:44:30] powers because the signal protocol has some of that in some ways. Signal, which uses a re synchronizing cryptographic ratchet system is a, as I said, a similarly self-healing protocol. It was originally designed by Moxie Marlin spike of what was then named Whisper Systems and then wisely renamed from Axel Lotto to signal. [00:45:00] We have
Ant Pruitt (00:45:01):
A lot of people in our live discord giving us gifts of Axel Lottos apparently, and I will say I still stand by my branding statement folks.
Steve Gibson (00:45:10):
Yes. So of course it hit the big time when this protocol was adopted by meta to be the secure messaging protocol for their WhatsApp messenger. And if the phrase re synchronizing cryptographic ratchet system doesn't ring any bells, [00:45:30] if you are a listener who joined us after April 12th, 2016, or you're a longtime listener who would be interested in a refresher, I did one of our famous deep dives into this truly lovely messaging protocol, which thanks to META'S adoption is now in use by more than a billion people worldwide. Anyway, look for security now, episode 5, 5 5, [00:46:00] which we titled WhatsApp, and that's where I do a deep dive into Axel Lotto, which is now fortunately rebranded as signal. Okay, the reason we're talking about signal today is that signal the company made headlines last week in the tech community with their announcement that they're already extremely clever and well-designed, very secure signal protocol was being upgraded [00:46:30] with something they called PQ X D H, quantum resistant encryption.
(00:46:39):
And if I didn't already have a topic for today's podcast, this would've been it, but we have room for both. Okay. Signals move might at first appear premature since the threat posed by quantum computers to public key crypto, which we rely on today remains purely [00:47:00] theoretical and may well remain so for the foreseeable future. We've had some fun in the past at Quantum computing's expense noting that breaking R S A style crypto, which would require determining the prime number factors of a massive number represented by more than 4,000 binary bits appears to be safe for now since [00:47:30] it was considered to be a breakthrough and a huge accomplishment when today's most advanced quantum computer successfully factored the number 35. So that's the best we've been able to do so far. We need to factor a 4,000 bit number in order to break R S A style crypto.
(00:47:54):
So it seems to be the point is very safe for the time being. Now, [00:48:00] given that it might appear that signals move to an overtly quantum resistant protocol is premature, but if nothing else, it's brilliant marketing, but there's more to it than that. The security world has coined another abbreviation, which is pronounced handle because the abbreviation is H N D L. H N D L stands for harvest Now [00:48:30] decrypt later. And we know that our dearly beloved N S A has built a truly massive one, somewhere between one and one and a half million square foot data center of some sort out in the boonies of Utah. So there's more than a passing chance that the harvesting now first half of harvest now decrypt later strategy is already well [00:49:00] underway. They're sucking in all the messaging that's going on. They can't decrypt it today, but they assume they're going to be able to decrypt it someday.
(00:49:10):
So grab it now, harvest it, now, decrypt it later. In other words, what the lesson is then for us now is if you want your secrets today to remain secret past the foreseeable future, it's never too soon to begin [00:49:30] encrypting under post quantum crypto technology and that's what makes signal's announcement last week significant. Okay, so what exactly is signal done? Signal's current shared secret key agreement protocol is known as X three dh. The DH is short for Diffy Hellman, which is a well-established key agreement system. We've discussed key agreement protocols in general and Diffy Hellman in particular, many times [00:50:00] in the past on the podcast, and I know it pretty well since it plays a large part in squirrels, more tricky security features, the features that I designed into my own squirrel technology. Okay, briefly, a key agreement protocol allows two ends of an insecure and public connection to exchange some information in plain sight while each of them obtain a shared [00:50:30] secret which no one else is able to get.
(00:50:33):
I know you're scratching your head. I know it's really very cool technology. It seems counterintuitive that their conversation could be completely known while they each arrive at the same secret that only they know, but it works. Wow. The X three and the X three DH refers to the X 2 55 19 elliptic curve, [00:51:00] which is the flavor that signals diffy Helman key agreement, and actually mine I chose the same one has traditionally used. Okay. And what's really cool is that they're still going to use this in the future. What they decided to do was to add another key agreement protocol. This one believed to be quantum safe to their existing system in such a way [00:51:30] that both of the protocols, the old and reliable elliptic curve, Diffy Hellman, and the believed to be safe today and tomorrow, newfangled quantum safe system, both would need to be simultaneously broken and cracked in order for an attacker to obtain the shared secret that's used to decrypt signals communications signal selected one of the [00:52:00] N I S T contest finalists that's believed to be the best, the one known as Crystals kyber, K Y B E R, and we've talked about it previously.
(00:52:11):
They chose it because it's built upon a solid foundation, but they also wisely decided that since it's new and unproven, and actually one of the other contest finalists turned out to be broken breakable by conventional computers. So whoops, [00:52:30] it's a good thing they didn't use that one Again, not yet proven. That's why they're keeping the diffy Hellman around just to have a belted suspenders approach anyway, so because it's new and unproven, they decided not to depend upon it solely. So signal's original X three DH has been renamed PQ X DH for post quantum. The PQ is for post quantum and the X D H for [00:53:00] the existing elliptic curve. Diffy Hellman, which survives in the new combined protocol. And here's the coolest part. This new PQ X D H is already present and supported in the latest versions of signal's client applications and it's already in use protecting any conversations initiated after both sides of the chat are using the latest signal [00:53:30] software, which supports both the original and the updated P Q X D H protocol.
(00:53:37):
Then over time in the future, after sufficient time has passed for everyone to be using the new signal and to have updated, they plan to disable all use of the old non quantum enhanced X three DH only protocol in favor of all new conversations, which would then be requiring [00:54:00] P Q X D H for all new chats. So this is great. It's clear that we are moving into a post quantum world, even though it seems like we're still a long way away from quantum computers being a threat to our existing crypto. This whole concept of a harvest now decrypt later. That makes a lot of sense. Now that Signal [00:54:30] has led the pack of messaging apps by introducing quantum safe messaging. The rest of the pack who may have been caught by surprise caught off guard, they'll have no choice but to figure out how to do the same because they don't want to get left behind. So it's great. Essentially this means that we will be moving to the next generation of crypto in advance of its clear need. [00:55:00] And that makes sense too because at some point we will be surprised when a quantum computer is created, which is able to do this, we might as well be ready for it.
Ant Pruitt (00:55:11):
Yeah. Now, did you all speak last week about what was going on with Signal in the EU and the eus new plan to pass a bill? Basically giving them a back door to everything?
Steve Gibson (00:55:26):
So we've talked a lot about the privacy issues. What [00:55:30] happened in the UK was they amended the legislation, sorry, right? They amended the legislation to basically give the messaging apps an out. They said, you must, must must scan where technically feasible. And that where technically feasible clause says, oh, okay, fine. It's not technically feasible. So the politicians get to say, [00:56:00] we implemented strong new legislation, whereas none of the messaging apps are worried about it anymore. So what will be interesting is to see what the EU does. Will they also back down? Because it really looks like any government that says, we must have you scanning all content, they're simply going to lose all cryptographic services in their country and
Ant Pruitt (00:56:23):
They can't afford to do that, right? Yeah. I believe I saw Signal's leadership saying, yeah, we'll just step out of here. See you later. [00:56:30] It comes down to it, and I totally get that. Folks, this is Security now, episode 941 with Mr. Steve Gibson dropping some great knowledge and information on us in the world of cybersecurity and information security. I am Matt Pruitt, but next we're going to hop on into a quick break here to thank another fine sponsor of the show. And that is the folks at A C I Learning. Yes, yes, yes, yes, [00:57:00] yes. A c I Learning. So this episode of Security Now is brought to you by our friends at IT Pro tv, but now they're called a C I Learning in today's IT talent shortage. Whether you operate as your own department or your part of a larger team, your skills, they have to be up to date.
(00:57:19):
Get this. 94% of CIOs and CISOs agree that attracting and retaining talent is pretty daggum critical to their roles. [00:57:30] So with a C I Learning, you get access to over 7,200 hours of content. And a C I Learning is consistently adding new content to keep you at the top of your game. Your team will thank you for entertaining training that a C I Learning has put together. And what's crazy is just such a cool stat. A C I learnings completion rate is at 50% higher than their competitors. And that's because [00:58:00] it's entertaining. If you're going to do a training session, at least make it enjoyable for your team to do those sessions because if it's enjoyable, more than likely they're going to finish it up. A c I Learning is excited to introduce cyber skills. This is a solution to future-proof your entire organization, not just the IT department.
(00:58:21):
This is new cybersecurity training tools for all of the members in your organization and cybersecurity awareness training for non-IT [00:58:30] professionals. We spoke briefly here earlier in the show about picking up U S B drives off the ground and stuff like that. That's got nothing to do with being IT in it, but it is definitely an IT security risk. With cyber skills, get flexible on-demand training, covering everything from password security, phishing scams, and malware prevention and network safety. Your employees will stay motivated and engaged throughout [00:59:00] their learning process with easy to follow material. With a simple one hour course overview, your employees will gain attack specific training and knowledge check assessments based on common cyber threats that they'll encounter pretty much every day because it's just that easy for these cyber criminals out there. They'll also gain access to bonus courses and documentary style episodes so your employees can learn about cyber attacks [00:59:30] and breaches in their own style, not just someone sitting there lecturing them.
(00:59:35):
You know what I mean? A C I Learning helps you invest in your team and entrust them to thrive while increasing the entire security of your business. Boost your enterprise cybersecurity confidence today with our friends at ACI Learning. Be bold, train smart. Now. Visit go dot ACI learning.com/twit. [01:00:00] Now TWIT listeners can receive up to 65% off an IT Pro enterprise solution plan after completing their form based on your team's size. Of course you'll receive a proper quoted discount tailored specifically to your needs. That's go dot ACI learning.com/twit and we thank him for supporting the show. Alright, so Mr. Steve, [01:00:30] it's time for us to close up the loop, what you got?
Steve Gibson (01:00:34):
Yep. We got some really interesting listener feedback that drives some, I think, interesting observations. Our listener, Dustin Smith put me onto a blog posting, which was originally written three and a half years ago on March 18th, 2020. Yet if nothing, it's more relevant today than it was then. This blog posting was written by a guy named Drew [01:01:00] Devolt. It's an on point rant about what modern web browsers have become, and I think everyone here will find it interesting. Here's what he wrote. He said, since the first browser war between Netscape and Internet Explorer, web browsers have been using features as their features as their primary means of competing with each other. This strategy of unlimited scope and perpetual feature creep is reckless [01:01:30] and has been allowed to go on for far too long.
(01:01:35):
He says, I used W get to download all 1,217 of the W three C specifications. That's the Worldwide Web consortium, the W three C, so all 1,217 of the Worldwide web consortium specifications, which had been published at the time of writing. And he said, not counting web gl, which [01:02:00] is maintained by Kronos. He said, web browsers need to implement a substantial subset of this specification in order to provide a modern web experience. Is that I ran a word count on all of these specifications. How complex would you guess the web is? Okay, he said the total word count of the W three C specification catalog is 114 million words [01:02:30] at the time of writing. Wow. If you added the combined word counts, the C 11, which is C language 11 C plus plus 17, U E F I U S B 3.2, and PIX specifications, all eighty seven hundred and fifty four published RFCs and the combined word counts [01:03:00] of everything on Wikipedia's list of longest novels, you would still be 12 million words short of the W three C specifications.
(01:03:14):
I mean, okay, so it is that complex. Wow. So he said, I conclude that it is impossible to build a new web browser. The complexity [01:03:30] of the web is obscene. The creation of a new web browser would be comparable in effort to the Apollo program or the Manhattan Project. He said it is impossible to first implement the web correctly impossible. Second, implement the web securely and third implement the web at all. He said, starting work [01:04:00] on a bespoke browser engine with the intention of competing with Google or Mozilla is a fool's errand. The last serious attempt to make a new browser, which was known as Servo, has become one part incubator for Firefox, refactoring one part playground for board Mozilla engineers to mess with technology. No one wants and zero parts viable modern browser. [01:04:30] But he said web VR is cool, right? Right. The consequences of this are obvious.
(01:04:37):
He says browsers are the most expensive piece of software a typical consumer computer runs. They're infamous for using all of your Ram pinning C P U and IO draining your battery, et cetera. Combined web browsers are responsible [01:05:00] for more than 8,000. CVEs exploits flaws, bugs alone. And then drew switches from establishing some facts to making a very interesting observation. He writes, because of the monopoly created by the insurmountable task of building a competitive alternative, browsers have also been free to [01:05:30] stop being the user agent and start being the agents of their creators. Instead, Firefox is filling up with ads tracking and mandatory plugins. Chrome is used as a means for Google to effectively track your eyeballs and muscle, their anti technologies like D R M and A M P into the ecosystem. The browser duopoly is only growing stronger [01:06:00] too, as Microsoft drops edge and WebKit falls well behind its competition.
(01:06:06):
Now remember, this is three and a half years ago, so of course this is, that part is pretty much history. He said the major projects are open source and usually when an open source project misbehaves, we are able to fork it to offer an alternative. But even this is an impossible task where web browsers are concerned. The number [01:06:30] of W three C specifications grows at an average rate of 200 new sub specs per year, or about 4 million new words of specification or about one IC every four to six months. How can a new team of any forked browser project possibly keep up with this on top of implementing and maintaining the outrageous scope [01:07:00] web browsers already have now he finishes the browser. Wars have been allowed to continue for far too long. They should have long ago focused on competing in terms of performance and stability, not in adding new web features. He has in air quotes. This is absolutely ridiculous and has to stop.
Ant Pruitt (01:07:27):
Okay, so I need to interject here. [01:07:30] I get where Mr. Drew is coming from with his stop adding features and whatnot. But let's think about this. Let's just think about vehicles. Okay? We can have the Honda Civic, simple four cylinder car, but then we have the Honda Accord with a slightly larger engine. And then we have this, I don't know, like a Ford Mustang with an even bigger engine. So we have these fast cars and everybody's like, huh, I don't need that fast car. But then you throw in Bluetooth [01:08:00] features, oh, I want that. And that's what's happening here. People are sold on features and these large companies, Google and Firefox, they get that if they want to stay in business, they're going to continue to add features. That's the nature of consumerism, right?
Steve Gibson (01:08:20):
Okay. Maybe the right analogy or trying to find a good comparison. Not everybody can launch stuff into space in [01:08:30] orbit. It requires so much infrastructure, so much technology, so much other stuff that there are only a few ways of getting something launched into orbit. So similarly, his point is there's just no way to create a third browser. There is a duopoly, there is a lock-in at this point. There's no way for there to be competition. And what we see when there's a lack of competition [01:09:00] is then the rules change so that the browser creators no longer have to create the best product anymore. And so that's the point he's making.
Ant Pruitt (01:09:12):
And with all of these specifications from the W three C, do you think it's a bad idea? Considering we know about all of the security issues behind the browser? I
Steve Gibson (01:09:28):
Don't thinks a good idea
Ant Pruitt (01:09:29):
Those come from
Steve Gibson (01:09:29):
No. [01:09:30] In fact, it is the implementation of all these new things, which is where new problems get created. I'm always saying if we would just leave this stuff alone, we'd be able to fix the problems and then we'd have some security. But there are incentives for not leaving it alone. Everybody wants to force you to upgrade to the newest operating system, the newest browser. Everybody wants the newest features. Arguably, it's cool that [01:10:00] you're now able to do web conferencing with just your browser. It used to be that you had to have some extra software in order to do it. Now you don't need that. So I guess the only thing that I would change about what Drew wrote in his last line, he said they should have long ago focused on competing in terms of performance and stability, not in adding new web features. This is absolutely ridiculous and it has to stop.
(01:10:30):
[01:10:30] I would change it to, this is unfortunate in the extreme, but there doesn't appear to be any way for the industry to change that course. And I think mean he says it has to stop. I would argue how is it ever going to, why would it? And I would further add that to their credit, Microsoft perceived very early on just how important the web browser would be [01:11:00] to the future. You remember they attempted to build it into Windows and they called it Internet Explorer. And of course they got taken to court and sued antitrust issues because they built this browser into their operating system because again, to their credit, they knew this was the future. And as we know what the web has become, even outgrew their Microsoft's, [01:11:30] their ability to browse it once upon a time, i e was the most widely used browser.
(01:11:38):
It attained a peak of 95% market share about 20 years ago in 2003. It was still horrible. Yes, this podcast began two years later and we all witnessed I e's decline over this period of time leading to its inevitable death after making [01:12:00] a massive investment in a brand new post i e engine. Microsoft, again, to their credit, recognized that a modern web browser was too big for even them and that they'd be better off just hanging bells and whistles off a browser chromium, which they got from the Chrome project that someone else was maintaining [01:12:30] and evolving. So are there any takeaways for us here? No, none that I can think of. Drew's observations, which I think are valuable, pair beautifully with what I've noted to be true of operating systems. Just as no one can create a truly competitive and useful, truly new operating system from scratch any longer because there's just too much there.
(01:12:59):
Any operating [01:13:00] system that a user is going to sit in front of will need to host a web browser that is all by itself also too massive and complex to create today from scratch. So I also think all of this was absolutely inevitable and that further suggests that it wasn't a mistake. It's not a consequence of inertia, which we often observe elsewhere. And we're almost certainly going to continue moving [01:13:30] down this path from here on, this is where we're headed. So another piece of feedback from an anonymous person who actually called himself anonymous. He said, hello, Mr. Gibson. I hope it sounds like ant. Hello, Mr. Gibson. I hope I can ask you a question. Over the last podcast from security. Now around 30 minutes in, you say that you encrypt with the private [01:14:00] key and decrypt with the public key. Is this right? I think it's reverse.
(01:14:07):
What I learned is that you encrypt with the public key and decrypt with the private key. Is this right or do I have wrong information? Thanks for your response. Okay. So one of the powerful beauties of public key cipher technology is that the process does work in [01:14:30] either direction. It's obviously very useful to encrypt something using someone's public key that you know only they will be able to decrypt with their secret private key. P G P is a perfect example of this, and digital signatures of all kinds is the best example of this being done in reverse. In fact, P [01:15:00] G P does this too, to provide authentication of the sender of a message. The sender uses their private key to sign the file, which the recipient is able to verify using the sender's public key. So when the recipient is verifying the signature, they're decrypting a hash of the document that the sender encrypted with their [01:15:30] private key.
(01:15:32):
So the last time we talked about public key technology, I was really pleased with the way that I conceptualized the public and private key distinction used by non elliptic curve R s A style crypto. So you start by obtaining a private key, which is really just a large prime number. So you just get a big prime number. And remember [01:16:00] that counterintuitive though it is prime numbers do not become more scarce as we go farther and farther out, like farther and farther down the numbers you sort of think they would, right? Because the definition of prime number is that it's only divisible by one and it itself like no, even numbers are prime. But then no, every third number is prime because it could be divided by three and no [01:16:30] even number is prime. It could be divided by two two, and then every fifth number is not prime because it can be divided by five and so on.
(01:16:39):
So since because of that, you'd think that would all kind of pile up and so it'd be hard to find big numbers way out there that aren't divisible by something that's come before, but it turns out that's not the way it works. There's always plenty of them. Okay, so you take a really big prime number and that's our private key, [01:17:00] okay? Now we want to arrange to hide that private key inside the public key. We do this by taking another very large prime number and multiplying that new prime number with the original private key, which was also a prime number. Though I've simplified things, it's that multiplied key is the public [01:17:30] key. The public key contains the private key, but there's no way to know what it is after they've been multiplied together. Because to this day, despite all the best brains in math, and I mean this has received a lot of attention through the years, no one has ever come up with a practical way to multiply those two primes through the process of prime factorization.
(01:18:00):
[01:18:00] And by the way, that is the danger posed by quantum computing. There are reasons to believe that some future quantum computer might be able to finally factor a very large public key, which contains those two primes, one of which is the private key. If you could factor that back into its original two prime numbers, then you'd have the private key which could then be used to [01:18:30] decrypt things where you were assuming that was not possible. So the true magic of public key crypto is that that private key which has been hidden inside the public key by multiplying it with another prime, that it is still able to perform encryption and decryption operations despite being completely hidden by its multiplication by another large prime number. Anyway, it is just [01:19:00] so cool.
Ant Pruitt (01:19:00):
So first off, excuse me, where I let all the steam come out of my ears because I'm like, wow, what in the heck? And secondly with quantum computing, do you feel like this is still something in the near future to be able to get this? I wasn't going to sit here and say I was concerned, but I wanted to ask you first though.
Steve Gibson (01:19:23):
Yeah, as I mentioned before, the best we've seen a quantum computer [01:19:30] do is factor the number 35 into five and seven, so that's like, whoa, it worked. But I mean, so no, we're not in now. Okay, there could be a breakthrough, right? There could be some fundamental crazy ass like no one expects it comes out of right field breakthrough could happen, and so that's why we already have, [01:20:00] we're already beginning to standardize on next generation quantum safe crypto so that we will be using that if such a breakthrough happened. Because if it happened today, I often use the phrase it's the end of the world as we know it. That probably really would be, would be if you were to use really, really bad and the amount of badness [01:20:30] is how many reallys you put in front. You could be saying really, really, really, really, really, really all day long that way it would be really bad. Yeah, but for now it looks like we're safe. Yeah. Okay. Now here's a particularly interesting piece of feedback.
(01:20:49):
A listener whose name I will just say is Jerry, and I'll explain why I anonymized him in a minute, because initially it wasn't, he wrote to me, he said, [01:21:00] your assertion that no deterministic mathematical algorithm can generate a random result is incorrect. He said, non-deterministic mathematical algorithms processes can generate true random results, not pseudorandom numbers. And he finished, I developed such an algorithm, okay? Okay, so first [01:21:30] of all, I said no deterministic mathematical algorithm, not non-deterministic mathematical algorithm. Now the problem is that the phrase non-deterministic mathematical algorithm is, as far as I know, an oxymoron, one plus one equals two. And wait a minute, one plus one still equals two and oh one plus one, yes, it still equals two. [01:22:00] All mathematical algorithms are inherently deterministic. Now, if I made a mistake on my math homework in elementary school explaining to my teacher that this was my implementation of a non-deterministic mathematical algorithm, I'm pretty certain that would not have gone over very well, nor would it have changed my grade.
(01:22:23):
I can see the little Steve Gibson right now at the front of the class at the chalkboard. This is a non-deterministic [01:22:30] mathematical algorithm. That's why I didn't multiply these two six digit numbers correctly. Okay? So Jerry, if you indeed have developed a non-deterministic mathematical algorithm which is capable of generating true random results, there's probably a Nobel Prize waiting for you in Stockholm, and more importantly, what you may have actually done is uncovered [01:23:00] a provable flaw in the simulation we're all living within. Okay, but seriously, you have my attention, you have access to an audience. Are you just going to leave us all hanging like that? Because that's all he said. Okay. Now, in a bizarre coincidence, just as I was getting ready to save as P D F to cast these show notes from Google Docs where I write them [01:23:30] every week into their P D F form, I happened to glance down at my phone and saw a reply tweet from this person yesterday when I encountered his assertion not knowing how to respond to something which clearly seemed impossible, I simply replied, I hope you've submitted this for a Nobel Prize.
(01:23:53):
Now, it turns out he didn't take that very well. I wonder why now. [01:24:00] Certainly not in the somewhat carefree spirit, it was meant so, okay, the first thing I did was to anonymize his identity in the show notes, since I certainly don't want to embarrass him from this dialogue. What he tweeted in reply to my short comment about the Nobel Prize, and actually I'm kind of serious about that because really, I mean if he really did this, it would be worthy of a Nobel Prize. [01:24:30] Anyway, this morning as I was getting ready to finish the show notes, I saw his tweet. He replied, I'm very surprised by your reply, I've been a customer and promoter of your products and services for 30 plus years. I have read numerous articles of yours. I never expected sarcasm from you. He said, my bad. I developed [01:25:00] these and similar algorithms more than 45 years ago.
(01:25:05):
I have always expected others to develop algorithms, but to date, this has not occurred. Okay? That was his tweet this morning. Now again, I'm having a little bit of trouble taking this seriously, or at least as seriously as he is when he says, I've always expected others to develop like algorithms, but to date this has not occurred. [01:25:30] I'll admit, my first impulse is to say, gee, I wonder why that is. Okay. Instead, this is what I replied to him. I said, hi, Jerry. Okay, so I suppose my reply was somewhat sarcastic and I certainly would love to be proven wrong in my assertion that to quote you quoting me, no deterministic mathematical algorithm can generate a random [01:26:00] result. The trouble is I wrote, I still believe that to be true, and not just a little bit true, but very true. If you are a mathematician, then you understand that the way to proceed from here would be to offer up some proof of your assertion, which appears to defy the laws and principles of mathematics and reality. [01:26:30] I'd be more than happy to eat my sarcasm if you can demonstrate that I'm wrong, exclamation point, smiley face.
Ant Pruitt (01:26:42):
So tactful, sir,
Steve Gibson (01:26:45):
I'm serious. Really. I mean this would be great. I'll buy his plane ticket to Stockholm for him. I've
Ant Pruitt (01:26:53):
Never heard a more polite, smart assery from anyone. Sir, this was really well done.
Steve Gibson (01:26:59):
For what it's worth, [01:27:00] if I do hear anything more from Jerry, I will let everyone know because that would be big. Now, it must be that there's a confusion of definition what I'm saying, no deterministic mathematical algorithm can generate a random result, and he's talking about a non-deterministic mathematical algorithm, which again, I think is an oxymoron. [01:27:30] Okay, we're at cross purposes here. But anyway, it was an interesting bit of feedback that I had intended to share and now I'm able to share a bit of dialogue. Todd said, Hey, Steve, I listened to episode nine 40 where you explain securely wiping drives by writing random bits to all sectors of spinning drives. Lately, I've been using Vera Crypt to encrypt old [01:28:00] drives before I get rid of them. And he said, ENS using GRCs password page to generate a secure password. Is this as secure as your upcoming software that writes random noise? And I, that's a good question. That's very clever.
(01:28:20):
And so if he were to do it twice under different keys, then it would be the equivalent of writing random noise just as GRCs [01:28:30] solution will be, and I would not argue that the second pass is absolutely necessary. I might offer a single pass option for those in a hurry with my own product. Vera Crypt, like its ancestor, true crypt uses X T S cipher mode encryption, which is the industry standard, and N I S T approved way of encrypting block addressed mass storage using what's known as a tweakable block [01:29:00] cipher. And we also know that any good modern cipher like a e s generates pseudorandom noise that's indistinguishable from true random noise. It'll be slower than GRCs product since its reading and writing in order to encrypt what was already there. And I don't know how large the blocks are that it's using. If they were really small, that would slow it down. Presumably it knows how to do that quickly. It won't be [01:29:30] able to access and wipe the latent data that might exist in grown defect spared out sectors, but it is truly a nifty solution. Until GRCs product is ready, the Vera Crypt encrypt and then discard. The key solution is here today and it's free. So anyway, Todd, thanks for sharing the idea. I think it's pretty clever and it's a great application and I cannot think of [01:30:00] any downside to it.
(01:30:03):
Bill Melvin said, Hey. Hi Steve. I have a thought regarding the discussion on wiping hard drives on show nine 40. I assume true crypt and Vera crypt hidden volumes look like random noise. It seems to me that doing an extra pass of writing zeros to a drive takes you from plausible deniability to absolute impossibility [01:30:30] in an abundance of paranoia. Why take the risk of being badgered over something that's not there? Thank you for security now, which I've enjoyed for years. I have my spin right license that I'm looking forward to the new version. Okay, so when I talked about my idea, my concept for the best secure wipe is to wipe with random noise. The point he's making is that random noise looks like [01:31:00] something, even if it's not. So if a drive was filled with random noise, it might induce someone to in the extreme, put you under some coercion asking you for what the key was to decrypt the drive when it was actually just random noise.
(01:31:21):
So he says, do another wipe to zeros so that nobody will think there's anything there. Then they won't come asking for the key, and [01:31:30] I think he makes a good point. Mark causal says, I found your description of S S D wear leveling. Fascinating. It is amazing what engineers have come up with to handle issues like this. And it got me wondering, I have a portable SS S D with a single multi gigabyte vera crypt blob on it. I open the blob a few times a week and make changes to files after [01:32:00] closing the blob. Everything appears to be unaltered as far as Windows knows. So I sent Vera Crypt to change the file modification date on the blob when I realized sync thing needed that to detect a change and sync the blob to my na. Does the wear leveling capability work on the blob?
(01:32:25):
Is it active inside the blob when I have it open in Vevera [01:32:30] crypt love the show and continuing education credits, I get towards my security plus certification by listening. Woohoo. Okay for you. So Mark, the answer is yes. The wear leveling is occurring at the lowest possible level in the chain of data flow. Just before the data is written to the drive, it is not visible to anyone reading or writing to and from the drive. [01:33:00] So it functions whether the data being read or written is encrypted or not. And one slick benefit of using Vera crypt to encrypt the blob on the S S D is that since Vera Crypt always leaves the data on the SS s d encrypted, only decrypting it on the fly as necessary when it's read into the computer as where leveling [01:33:30] causes blob updates to be written to dispersed regions of the drive, thus leaving obsoleted bits of the blob behind those obsoleted and isolated blob bits are also encrypted. So that drive will never need to be wiped, at least not to protect anything that was ever stored in the blob. Once Vevera Crips volume header has been overwritten [01:34:00] multiple times, there's no way to ever recover any of that blobs data period. Meaning that the wear leveling, which you may not have access to is not a concern as it would be if you stored unencrypted data on the drive which you then wanted to secure because all of that wear leveled data would've been previously encrypted bits in the blob. So very nice application.
(01:34:30):
[01:34:30] Wayne Patton asked, how difficult would it be to change the signed integer to an unsigned something else and recompile and fix Unix time? So he's of course talking about the fact that we were recently talking about how eunuchs time the signed integer, which is technically it's 32 bits, but because it's signed, we only get 31 bits worth of range. How? Because it's signed, [01:35:00] the original 32 bit Unix time will be wrapping around in 2038. I should have then. But I failed to mention that this Unix time problem was fixed in the Unix kernel back in June of 2018. After two and a half years of research into the right way to do it without breaking other things in Linux in the process, [01:35:30] more than 88 0 source files had to be changed. So this Y 2038 problem is no longer any concern for Linux kernels ever since.
(01:35:44):
The worry is that before this time all embedded, for example, Linux kernels of the sort used for industrial automation satellites, elevators, and who knows what else [01:36:00] will have this trouble. And in those markets there's much more of a, if it's not broken, don't fix it mentality. So the concern is not that mainstream Linux or any of the various major unixes will break, they've all been fixed. It's that some satellite that's been in orbit since before this was fixed may become suddenly confused and do know who knows [01:36:30] what it might do. So maybe a long forgotten pump on an oil rig will misbehave. No, we don't know. Anyway, it's going to be interesting to see whether it's another non-event like Y two K turned out to be or whether something interesting might occur and stay tuned. We'll be here in 2038, oh Y two K, I got memories of that, fond memories of that.
(01:36:59):
So [01:37:00] Bauer, he said, hello, Steve, thank you for the many great episodes of security. Now I've just listened to episode 9 39 and have a thought about what you said regarding the last pass hack. You mentioned that hackers will go after those accounts where they suspect a big payout. I think you're right about that, but I also think we must not let our guard down. All accounts will eventually be decrypted and all accounts will be available [01:37:30] for purchase on the dark web. This will be a problem for all those including me who use LastPass to store information like social security numbers and other personal IDs. I think it's important to take precautions while we still can guide in regards Johannes. Okay, and in case you're not aware, aunt, we talked about this last, there's very good evidence leading us to believe that [01:38:00] selective decryption of specific high value LastPass vaults, which were stolen in that LastPass breach are being that is to say have been decrypted and the cryptocurrency wallets of people who stored their master crypto keys in their LastPass vaults have been emptied and about $35 million or so of cryptocurrency has been transferred.
(01:38:28):
Yeah, I saw reports on that. It's pretty scary. [01:38:30] So I wanted to share Johannes note because I understand his concern and I imagine it is shared, but I also doubt that the vast majority of the more than 25 million users whose encrypted data was stolen are actually ever in any real danger. Even the advent of quantum computing won't make any difference here since [01:39:00] we're talking about brute forcing symmetric crypto, which quantum computing does not threaten the cost of performing 100,100 rounds, which is the level we were at when the breach occurred, where most people probably had their iteration count set, and we know some were a lot lower than that and that's a concern. But the cost of performing 100,100 rounds [01:39:30] against a brute force, against a hopefully high entropy password is truly prohibitive. These crooks appear to be spending significant money on cracking gear or cloud compute cycles, and they appear to be cracking only a couple of volts per week.
(01:39:54):
That's the rate at which this cracking is occurring because it is really expensive to do this. That's perhaps [01:40:00] a hundred or so per year against a population of more than 25 million volts. It's true that someday they might eventually get around to opportunistic attacks against non-high profile targets whose iteration counts are low. But even then, if the past phrase is good, there's no clear reason to believe, [01:40:30] there's no clear reason to believe that any actual cash lies on the other end of the crack. That is they wouldn't know until they perform the crack and it still takes a significant investment of time and money to turn someone's vault back into plain text. It really is not ever going to be easy. So the original design of LastPass, [01:41:00] which is what caused me to endorse it was strong, and as long as the iteration count is high, it's always going to be expensive to crack the vaults. So I cannot tell anyone that there's absolutely nothing to worry about. So my intention is only to present some, I think probably accurate perspective cracking. These vaults will never be free and these people are probably [01:41:30] not ones to throw away good money. It will cost money and I think that the attacks will continue to be targeted and that they will probably peter out over time and that it's not the case that they will all be cracked. They're just no reason to. It's just it is too expensive.
(01:41:49):
Kevin Van Herron, he said listening to the Last Mess episode, which is what I called that podcast, he said, I realized I had [01:42:00] some info in my last pass fault. In addition to passwords, things like s s H, private keys, recovery keys for all Apple devices and various cloud services, I didn't even think of rotating all those when I moved off LastPass. I'm also thinking that some of that should not be in my LastPass replacement SS s H keys. I'll probably keep on an encrypted disc image on my computer instead. [01:42:30] Not sure on recovery keys, I may adopt your two-factor authentication authenticator app and just print out recovery keys and keep them someplace safe. So I wanted to share this because I think Kevin's observation that just because today's password managers offer us synchronized, encrypted vaults which are capable of holding all kinds of other stuff, does not mean that they are the [01:43:00] best place to store unrelated non-web secrets password managers.
(01:43:08):
They need our usernames and our passwords and credit cards and perhaps some additional automatic form filled information for convenience. But things like ss, s h Keys, server certificates and other unrelated non-web passwords don't all need to be stored there [01:43:30] in a single place. Yes, it's convenient and that convenience can be seductive, but when you combine the wisdom of not keeping all of our eggs in one basket and the old fool me once saying with last pass being that once and when we considered that today's computing environment does not have any more dangerously exposed and complex software as we saw above [01:44:00] than our web browsers, it would be difficult to make a case for storing more in our browsers than is needed for web facing activity. I think a good cross platform encrypted archiving program is probably a good solution. It can contain all kinds of stuff. It squeezes it down, and then any file synchronization tool, any of the cloud drives or third party sync systems like Sync thing [01:44:30] or sync.com can keep the copies synchronized. I'll be interested to hear if any of our listeners have a better idea.
Ant Pruitt (01:44:38):
Yeah, I wanted to talk to you about LastPass because I know where you stand on it and I've been a LastPass user since before coming to twit because I heard about 'em on TWIT and your recommendation and so forth. And when all of that went down with them, I did consider moving over to our sponsor bit word, bit word. I did consider [01:45:00] that and opened an account and started a transition, and then I just found, you know what, I'm just going to change all of my passwords, period. And I spent a weekend, a legit weekend sitting at a laptop going through everything and changing all of those passwords and then I said, you know what? I'm going to go ahead and just keep LastPass and it's, and I feel fine with that. I updated those iterations and so forth. So my [01:45:30] thought is if someone has my vault, I don't think they have my current password. Not to mention, there's still also the aspect of multifactor authentication that I have on everything. So I think I'm fine and I like to assume that just because LastPass got themselves in this mess, they probably learned from it and took a lot of losses on that and it's probably going to make them better with their product [01:46:00] going forward.
Steve Gibson (01:46:01):
I really can't find any fault in that thinking. We know how this happened. Now we know that a developer who was working at home had failed to keep his Plex server,
Ant Pruitt (01:46:13):
Plex server, right?
Steve Gibson (01:46:14):
Yeah. Up to date, and they got in through a known vulnerability in the Plex server onto his network, onto his home network. Then they jumped from there using his laptop connection through the V P N [01:46:30] into the developer side of LastPass, and then that's how they set up shop. I'm more comfortable knowing how this happened than if it was just a big mystery and they never found out because we understand the path and we now know there's no question that they have arranged not to allow anything like that to happen again. So I am of the opinion, it is why I didn't jump ship when [01:47:00] they first had the first announcement of there being some sort of problem. I think if you have a very high iteration count, and I think they're now recommending 600,000 or more for LastPass, there's no reason to believe that their technology is fundamentally defective.
(01:47:23):
I don't think it is, and there is reason to believe that they've made themselves more secure. Now, the only [01:47:30] caveat I guess I would provide or suggest is that they're owned by, I can't remember the name of it. It's a monetary fund, like an equity, a private equity fund. That's the word I was trying to remember. A private equity fund and private equity funds or firms, they're not really interested in the technology. They're [01:48:00] interested in profit. They want to turn this thing into money. So one of the ways you do that is you squeeze it, you reduce your staff, you reduce your, put all that overhead as much as you can, the off-premises backups and you reduce this and you reduce that. So I guess I would suggest that's a warning sign that the original founder of [01:48:30] LastPass, he's gone. He's no longer making sure that things continue to be done right.
(01:48:36):
So the fact that LastPass is owned by private equity, that spooks me a little bit because yeah, that's fair. That's fair. They could be cutting corners and we wouldn't know it until a problem happened. Okay, so Don k said, thank you Steve. You are the only reason I still use this Twitter or X account, so I can now look [01:49:00] forward to deleting it as soon as your email solution arrives. And Mark Newton said, I'm one of the few people who may hold out a little while and hope Elon turns this thing around. The boy does have a track record of success dropping the name Twitter was almost as dumb as buying the thing. I'll give him another year. It will either be turning around or Twitter slash x will be a thing of the past. Now, you weren't here, but last week I [01:49:30] announced that I thought that Elon's statement the previous day, Monday a week ago, that he was going to charge everybody.
(01:49:40):
It would no longer be free. I thought that spelled the end of Twitter. So I explained that I would be putting an email system in order to send what I'm normally sending by Tweet and to create a spam free means for people to get back to me. [01:50:00] Now, invariably, some people took exception to that, and I heard from people who took exception to what they called my anti Elon anti Twitter rant, and as I just said, others confirmed what I suspected, which was that the only reason they still had Twitter was to easily receive my weekly security. Now tweets, okay, so allow me to clarify all this just a bit. I'm currently paid up for a year [01:50:30] since I cannot survive Twitter without TweetDeck, and I am fine with that. You didn't see me. No one saw me budge one inch when everything else that has happened so far happened.
(01:50:45):
I'm also in no big hurry to leave. My sole concern was that a switch to a 100% paid model, which Leo thinks may never happen, and I understand that too, would represent [01:51:00] a profound change to Twitter. I don't know how big, but I mean big enough that Leo says, nah, that'll never happen. I mean, it would be huge. I've already paid up, as I said, so it makes no difference to me one way or the other. But if there are people, and I have heard from many since who are only on Twitter to obtain my weekly tweets, then I disliked the idea [01:51:30] of any of our listeners feeling that they needed to go paid just to continue to receive that Twitter feed from me. I wanted those people to know that there would be an alternative means for obtaining that information. G R C currently has no means at the moment for receiving any to, for reaching any community outside of Twitter. So as I mentioned before, I [01:52:00] had planned and do to remedy that once Spin right is released. So I'll have the ability to mail to lists, and it makes sense for me to have a list for security now listeners of this podcast. So that's where I stand, not anti Elon, not anti Twitter, just saying if he's going to force people to pay and our listeners are already only in Twitter because they want to get my tweets, I will create [01:52:30] a different free channel that everyone will be able to use. I
Ant Pruitt (01:52:35):
Dig your stance. That's a choice that you have every right to make. If he were to make the platform a dollar a month, which is not a lot, you can decline to use that service. And
Steve Gibson (01:52:50):
Too, again, as I said, I'm paid up for a year. I'll be happy to keep tweeting. The weekly show note links the picture of the week and a brief synopsis of the [01:53:00] show's topics. That seems fine, but it no longer seemed right for Twitter to be the only way for our listeners of which there are many to receive that information.
Ant Pruitt (01:53:10):
Indeed, indeed.
Steve Gibson (01:53:11):
Okay. Two pieces of miscellaneous. Conrad Xiidra, he, well, he tweeted about that, has check SS H A 2 56 fork you mentioned in SSN nine 40 last week. He said [01:53:30] it's here since 2014, and there's a GitHub link in the show notes. And then he also said another fork with additional Blake three algorithm and faster implementations of S H a 2 56, 5 12 and s h a three and another link. Okay, so remember I was talking about having an easy way in Windows to obtain a useful hash of any file [01:54:00] that you right click on. I talked about hash check. Turns out what I learned is that the fork that I was wishing someone had created was indeed created nine years ago, and it's on GitHub.
Ant Pruitt (01:54:16):
Love it when that happens.
Steve Gibson (01:54:17):
Yes. So I made it, I created a G c shortcut for it. It's not the shortcut of the week, it's the shortcut is hash check. So the URL [01:54:30] is GRC sc for shortcut GRC SC slash H A h check. If you use that link, that'll bounce you over to the GitHub release downloads page and you can grab it. It's digitally signed. I immediately installed it. It's great. It's got all the modern hashes that we want. It's exactly what I was asking for last week, and [01:55:00] it's existed for quite some time. So thank you. A bunch of people told me that there had been updates, so I just quoted Conrad. Thank you very much. And finally, last week's podcast was titled, when Hashes Collide, and it's finally safe to say that it made one library information scientist very happy, the guy who [01:55:30] inspired the podcast and that title he wrote, hi Steve.
(01:55:36):
He said, I was absolutely floored while listening to the show on Friday morning to hear that my question was turned into a truly fascinating and very useful deep dive. Our patron population that is of his library is a bit larger than 5,000 individuals. It's actually closer to 400,000. [01:56:00] He said. I did say a large public library system in Ohio and Ohio is known to be the land of the libraries, at least in certain circles. But the topic you presented is still, of course, very much applicable. And then he said the idea of deliberately using the birthday paradox and further obscuring personally identifiable information by manipulating the number of bytes produced by the cryptographic hash is an [01:56:30] absolutely brilliant way to add a meaningful layer of protection to the pseudonymized data. Controlling the probability of collisions within the population of patrons is something I didn't even realize I was looking for to give a small degree of uncertainty to the pseudonyms, once again, an absolutely fantastic explanation of such a complex topic. Bravo. Okay, well, it's a bit embarrassing to read that, but thank you, Ray. What most pleases me is [01:57:00] that Ray got it completely. It turned out to be exactly what he was looking for, and he's already turned the concept into working code. He calls it the SS stochastic pseudonym. And for anyone who's curious, I have a link to his GitHub project in the show notes. So Ray, thank you for the closure and for being the incentive and the inspiration for a little bit of deep dive Nerdism, which [01:57:30] we had fun with last week.
Ant Pruitt (01:57:32):
Pretty cool.
Steve Gibson (01:57:33):
After you tell us about our third and final sponsor, I am going to explain to everyone why I titled today's podcast. We told you so I'll tell
Ant Pruitt (01:57:45):
You. I'm looking forward to that.
Steve Gibson (01:57:47):
We'll know who told who, what.
Ant Pruitt (01:57:50):
I am looking forward to that, sir. Yes, this is another fine week here on security now with Mr. Steve Gibson. And we're going to go ahead and take a quick break [01:58:00] and thank this week's sponsor to find folks at Melissa is bringing you this episode of Security Now, the contact data quality experts. Okay, so this is holiday season. So right now you need to let Melissa help your business meet online shopping expectations and increase R O I and reduce the waste and costs associated with the loss of undeliverable packages and mailers and improve [01:58:30] your customer's overall satisfaction. The importance of early preparedness for retailers before the holiday season is indisputable. Here are some of Melissa's tips to help get started because right now we're recording this at the end of September. You need to start getting ready for these holidays. And yes, I know some of you include Halloween as a holiday.
(01:58:50):
Good grief. First start by cleaning out your contact data. With Melissa's data cleansing solutions. All of your still outdated data gets [01:59:00] replaced with verified accurate information, such as replacing old addresses for people who have moved on and got new addresses and adding new emails or updated their phone numbers. Customers always want a seamless experience with efficient delivery. So make sure your business is meeting those expectations next day and second day delivery implementation is in high demand these days. Melissa ensures [01:59:30] that addresses are verified and standardized at checkout with their auto complete tool. Not only does having a verified address at checkout ensure the address is deliverable, but it also cuts down on keystrokes by up to 75%, making your customer's experience quicker and easier. It is so cool when you online doing your shopping and doing the checkout, and you literally just type in the first couple digits of your street address and maybe the first two letters of the [02:00:00] street name and it just auto fills that.
(02:00:02):
That is so cool and it makes it accurate. Idiot proof. I love that. Offering bundles and cross-selling to existing customers is more cost efficient than finding new ones. Okay, so the holiday season is the perfect time to do this, and since customers are most likely shopping for others, profiling your data can give you a better understanding of your customer base and bestselling products, which can help you create more [02:00:30] effective marketing strategies. Matching and de-dupe in your data will clean your database, allowing you to see a complete 306 degree view of each customer. This will also help you understand your customer's allowing for more personalized marketing and a better customer experience. Since 1985, Melissa has specialized in global intelligent solutions and contact data quality. [02:01:00] Melissa continually undergoes independent security audits and is SOC two, HIPAA and G D P R compliant. She's got to have all of that. Make sure your customer contact data is up to date. Get started today with 1000 records clean for free at melissa.com/twit. One more time. That's melissa.com/twit. We thank you, Melissa for supporting the show. Now, Mr. Gibson, [02:01:30] so you told us so not exactly. Okay. Last Thursday,
Steve Gibson (02:01:39):
Apple quickly patched three iOS vulnerabilities taken together. They created a zero day chain that enabled a potent attack that the Citizen Lab in Canada and Google's TAG team, their threat analysis group, T a G team, had jointly reverse engineered [02:02:00] from the forensic evidence residue left behind by a successful targeted attack aimed at an Egyptian citizen who had made himself a political target by announcing his intention to run in a forthcoming election against Egypt's current head of government. I named this episode, we told you so in acknowledgement of our many listeners who took exception to my assertion that not all websites [02:02:30] in the world needed to be H T T P S, what Citizen Lab and the TAG team discovered was that it was when this political target was led to a plain H T T P, non H T T P S website that his network traffic was intercepted on the fly by a man on the middle box.
(02:02:53):
That device returned an HTTP 3 0 7 temporary redirect, which caused [02:03:00] his iPhone to be redirected to a spoofed website where the malicious content could be injected into his phone via this chain of three carefully designed exploits. So indeed, no argument you told me. So let's take a closer look at some of the interesting details here. The target of the attack was Ahmed Elwi, a former Egyptian [02:03:30] member of Parliament earlier this year in March, he announced his intention to run in the upcoming Egyptian presidential election stating that he planned to offer a democratic alternative to the current president who some feel is not very democratic. His following his announcement, his family members and supporters have been subjected to harassment, including reports of arrests of 12 family members. Egypt's current president [02:04:00] Abdel fta LSI has been in power since 2014 when he led the military overthrow of President Muhammad Morsey.
(02:04:11):
Cc's been widely described as an autocrat. Human rights groups Amnesty International and Human Rights Watch have documented widespread human rights abuses under L C's regime, including repression against civil society groups, activists in political opposition. So Egypt's current president [02:04:30] doesn't appear to be a nice guy who plays fair or would be in favor of free and fair elections. Ahmed became suspicious about the safety of his phone and reached out to Citizen Lab who then performed a forensic analysis of his device. Their analysis revealed numerous attempts to target Ahmed with CI TRX Predator. Spyware Citizen Lab has previously [02:05:00] documented CI TRX predator infections, targeting the devices of two other exiled Egyptians, an exile politician and the host of a popular news program who chose to remain anonymous. Citizen Lab brought Google's TAG team into the project to perform some of the heavy reverse engineering forensics, which the TAG team excels at.
(02:05:22):
This allowed them to obtain the complete iOS exploit chain that had been targeted at Ahmed. They initiated [02:05:30] a responsible disclosure process with Apple, which assigned three CVEs to vulnerabilities associated with the chain. There was C V E 20 23 41, 9 91, which was a security breach. A malicious app may be able to bypass signature validation. Whoops, 9 92. In the kernel, a local attacker may be able to elevate their privileges and 9 93 in WebKit processing web [02:06:00] content may lead to arbitrary code execution. And there again is a browser exploit, and we were just talking about the problem with browser security. The zero day chain was hosted on flare.com, and the exploit also contacted verify url.me. After fingerprinting those two websites, they scanned the internet and identified a large number of other ips [02:06:30] that matched those site's, fingerprints. In other words, there were other domains that were pointing to the same malware hosting sites, and they considered all of those ips and the domain names returned in T L SS certificates when they matched the fingerprints to be directly linked to Sidetracks as predator spyware.
(02:06:51):
They also observed that some of the domains they'd identified had names suggestive of tailoring towards specific countries [02:07:00] or regions, including the Arabian Gulf, Southeast Asia, Angola, the Democratic Republic of the Congo, Egypt, Greece, Indonesia, Kazakhstan, Madagascar, Mongolia, the U a e and Sudan. So wow, by examining the final stage of the iOS exploit chain, which was an iOS payload, they were able to attribute with very high confidence that this was indeed Ciro's [02:07:30] Predator spyware, which they'd obtained another sample of back in 20 21 2 years ago. Those two binaries, the old one and this new one, shared a key similarity which could only be accounted for through a common heritage. Okay, so what about this on the fly interception this month of September and last month in August when the target Ahmed visited certain websites [02:08:00] without h s from his iPhone using his Vodafone Egypt mobile data connection, he was silently redirected to a website at the domain C betley me via an on the fly network traffic injection.
(02:08:26):
And that domain was among those that matched Citizen [02:08:30] Lab's fingerprint for Ciro's Predator spyware. The injection was triggered by a string match on the website specified in the H T T P host header, as well as the value of the user agent header. I'll note that while the target domain can also be seen at the start of a T L S handshake, thanks to SS I server name indication subsequent T L SS encryption [02:09:00] blinds, anyone whose eavesdropping from seeing additional connection details such as the user agent header, which they use in this case. But since H T T P leaves everything in the clear, the attackers were able to use these additional signals to reduce mist targeting since they would not want non-targeted web traffic to be redirected. So as I said before, when the injection attack [02:09:30] is triggered, the intercepting middle box immediately returned a 3 0 7 temporary redirect to the user's iPhone.
(02:09:39):
That would be invisible to the user and it also, the middle box blocks the legitimate reply coming back from the server, which would've come back from the authentic server. The body of the page, which was returned from the malicious redirected website included two iframes one, which they described [02:10:00] as containing apparently benign bait content. It was a link to an a P K file, not containing any spyware, but the second one was an invisible iframe containing a predator infection link hosted on that sec flare.com site. Next, they wanted to understand exactly where in the network this injection was being made. So they performed [02:10:30] a bunch of tricky IP packet logic to localize the malicious middle box. They needed to get far more sneaky than just using atric route style T T L A time to live manipulation because they discovered that another benign traffic management middle box was also in the path and it was located close to Vodafone's subscribers.
(02:10:58):
The reason that was a problem is that [02:11:00] all the traffic that passed through it had its t t L reset, so it was not possible to, from the iPhone, send packets in a trace route style with differing TTLs causing a premature expiration of the packet that would allow you to map out the route. As soon as you hit that close middle box, it reset all the TTLs. Nonetheless, they were able to eventually determine [02:11:30] that the malicious middle box was on the interconnect between telecom Egypt and Vodafone Egypt, which is exactly where you'd expected to be if you wanted it to be able to reliably intercept and infect targeted smartphone users. They were also able to identify the specific hardware by probing it remotely and comparing its responses to other known appliances. [02:12:00] It is a commercial off the shelf device made by a company called Sand Vine who has offices in San Jose, California, Sweden, Ontario, Canada, and India.
(02:12:13):
It's one of their packet logic devices. And if anyone's curious, it's sand vine.com/products/packet logic. I looked at the data sheet for this device. It boasts features like policy-based traffic [02:12:30] management capabilities that include asymmetric traffic control, traffic shaping and filtering, traffic flow, classification and prioritization, traffic monitoring and packet rewrite. In other words, a full spyware capability. Also, they said content intelligence enables network operators, cloud providers, and high-speed enterprises to combine the policy management capabilities of packet logic with industry [02:13:00] leading U R L content, categorization functionality, H T T P, header enrichment, leveraging packet logic, stateful awareness, and subscriber awareness. Anyway, this is, it's a commercial box. You don't need to build your own. You can buy one of these things, stick it anywhere you want, and perform this kind of traffic interception using commercial off the site hardware. So this is just one SKU [02:13:30] or multiple the website, like it has multiple SKUs.
(02:13:33):
Oh yeah, they've got, basically it's how much traffic, what volume of traffic do you want? And so they keep adding interface speed and more interfaces in order to get beefier and beefier devices. Got it. But they're all part of that same family. So place the device in the link between Vodafone, Egypt and the rest of the internet when you want to be able to mess with smartphone users. [02:14:00] Citizen Lab also noted that they're unable to conclude whether this device sits on the telecom Egypt side or the Vodafone Egypt side of the link, but it really doesn't matter. They suspect it's within Vodafone Egypt's network because in order to be able to precisely target injections at a specific Vodafone subscriber, you'd require integration with Vodafone's subscriber database. [02:14:30] So that also suggests an intimate relationship between Vodafone and this device. So that's also part of the package.
(02:14:38):
And given that the intercept or the injection is operating all inside Egypt, that this class of spyware is sold to government agencies and that Egypt is a known predator customer, citizen Lab believes it's highly unlikely that this could have been occurring outside [02:15:00] of the purview of Egyptian authorities. In other words, this was sanctioned and as if all this wasn't enough, Ahmed additionally received three s m s messages as far back as September of 2021. So two whole years ago in September, as well as more recently in May and September of this year, all three posed as messages originating from WhatsApp. [02:15:30] The fraudulent messages invited him to visit a link contained within the message to terminate what the messages claimed was a new login to his WhatsApp account. It was meant to invoke an immediate reaction of, oh crap, click the link because somebody else has logged inmate illegitimately.
(02:15:54):
Interestingly, approximately two minutes and 30 seconds after [02:16:00] Ahmed read the first September 15th, 2021 s M S message, the predator spyware was installed on his phone. The researchers suspect that he did click the messages link, and that triggered the installation. Since the 2023 messages contain nearly identical bait content, they believed that those messages were also attempts to install the predator spyware on Ahmed's phone, and [02:16:30] as if the point hasn't been driven home enough. Citizen Labs writeup of their research concluded the following. They said, our research reveals the potential insecurities that run through the entire spectrum of the telecommunications ecosystem, including at the network layer, which can be exploited to inject malware on an unsuspecting user's device. Our internet communications are routed through many [02:17:00] networks and middle boxes, some of which can be misused for malicious purposes, particularly if network requests flowing through them are not protected with cryptography. Although great strides have been made in recent years to encrypt the web users still occasionally visit websites without H T T P S and a single non H T T P SS website visit can [02:17:30] result in spyware infection, just one.
(02:17:35):
This report should serve, they said, as a reminder of the importance of achieving a 100% rate of H T T P S adoption. So yes, our listeners told me so. And just for the record, I never suggested that exactly this was not possible. In fact, I outlined [02:18:00] exactly this architecture for such attacks. But there's also no question that HTTP s would have robustly blocked this particular attack, the non S M S variant. It would not have blocked the ssss M s variant, which we saw did actually infect him two years ago. But certainly the H T T P attack, which relied upon on the fly traffic [02:18:30] interception would've been blocked. Now, unfortunately, the only way to really prevent such attacks would be to remove H T T P support from the internet. And that still seems extreme, right? I mean, it would break all non H T T P SS sites.
(02:18:56):
You simply couldn't get there. The other countermeasure [02:19:00] would be to display very scary warning messages from the browser before it takes you to a link you clicked on. But as we know, users typically just push past anything that gets in their way. Exactly. So that would be ineffective or at least less effective. Now, another idea might be to begin neutering what webpages delivered over H T T P can do. Like [02:19:30] how about not allowing iframes on such pages, or how about disabling all scripting on H T T P only sites? They would still load, but they would be grossly restricted to the sorts of old school content that such sites often have while potentially dangerous and abuse prone capabilities would be absent. And this might incentivize the owners of such sites [02:20:00] to step up to H T T PS S, which after all is no longer difficult or expensive.
(02:20:07):
You just have to want to do it. And then you can use any of the free certificates that are being offered by DigiCert or Let's Encrypt or whomever. So we do have a problem. Somebody got this, got an H T T P link in front of Ahmed, and as we know now, browsers are not showing us H T [02:20:30] TP SS or P colon slash slash, right? They're wanting to simplify the URLs. So he clicked it because it wasn't https. He was trying to jump to maybe a benign H T T P site that got intercepted, redirected to a malicious H T T P server, which then loaded those two iframes and compromised his phone using a chain of three. Still at the time, active [02:21:00] zero days, which Apple fixed in an emergency update last week. So I don't know what the solution is, but as our listeners said, Gibson, you're wrong on this. And yes, they told me. So
Ant Pruitt (02:21:16):
I love that. And I got to tell you, trying to make the sites less effective, I don't know if that'll be a problem either, considering all the malicious sites could do is just stick a popup [02:21:30] there similar to what we see. Now when you go to certain websites and say, Hey, it looks like you're running an ad blocker. Can you turn that off half a second? Or it looks like you're disabling this. Can you fix that just by clicking here so we can reload
Steve Gibson (02:21:43):
The page page? Remember, the only way they can do that is running script. You can only do a popup if you run JavaScript. So my thought was don't have the browser allow any JavaScript on a non H T T P S site. I mean, really neuter the site [02:22:00] so that it cannot be malicious. All it can do is display plain vanilla content. Old school in that case, sites could still remain H ttp. They just wouldn't. They have a very difficult time being malicious,
Ant Pruitt (02:22:16):
Right? Right. Unfortunately, I still think that's a bit much to ask for some of the normal folks out here on these internets. What else? It's hard to get people [02:22:30] to stop using the same password for everything. Now you're telling them to configure their browser. Oh boy, I don't think it's going to happen, man. Mr. Gibson, this has been a ton of fun and a ton of great information. I really enjoyed being here with you today on Security Now, and it's great to have you, aunt. Thank you. Learning more and more. Thanks for standing in for Leo. I appreciate that. This is a lot of information folks with Mr. Gibson. So make sure you all are [02:23:00] tuning in each and every Tuesday to security. Now we have this go off. We're supposed to go live at about 1:30 PM Pacific. Allegedly never happens, never happens that way, but so still, just tune in.
(02:23:18):
Just go to live TWIT TV each and every Tuesday, and you'll see us in here getting set up for the show each and every Tuesday. And for those of you that want to help support us here at twit, [02:23:30] you can also check us out on Club Twit and get ad free versions of the show. Just go to twit tv slash club twit and you'll be able to check out the different plans. We have the plan that is for seven bucks a month that gets you ad free versions of the show, also gets you access to our Discord server, access to other non-public club twit only content such as an A M A that I'm going to be hosting today this Thursday with Mr. Lou Meka [02:24:00] from this weekend Enterprise Tech, as well as an interview I'm going to do next week with Sci-fi authored John Scalzi.
(02:24:07):
That's only available in the club. So check it out. TWI tv slash club twit, seven bucks a month, get you that and more. As well as we offer some single show plans too. So if you're saying I can't do $7 a month, you can do a $3 a month plan as well and just get a single show and all of that will help support us here at twit. Mr. Gibson has all [02:24:30] of his show notes here on security Now in the show, each and every week. He even offers a tiny, tiny file size of the download, right? Don't you have like this tiny kill 16 cape? It sort of sounds like this when we're doing the show, so my voice won't sound as good on that one, but it's still going to be great information for Mr. Gibson. So make sure you check that out. Alright everybody, thank you all for tuning in for security now, Mr. Gibson, good to see [02:25:00] you again. We shall see you. Thanks buddy. Next time. See you care next time. Care, bye.
Mikah Sargent (02:25:05):
Hey, I know you're super busy, so I won't keep you long, but I wanted to tell you about a show here on the Twit Network called Tech News Weekly. You are a busy person and during your week you may want to learn about all the tech news that's fit to well say, not print here on twit, it's Tech News Weekly. Me, Mikah Sargent, my co-host, Jason Howell. We talk to and about the people making [02:25:30] and breaking the tech news, and we love the opportunity to get to share those stories with you and let the people who wrote them or broke them, share them as well. So I hope you check it out every Thursday right here on twit.