Security Now 931, Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for Security Now, Steve Gibson is here with a, a, a stunning flaw in Microsoft. They say it's a feature, not a bug, and it's been around since 2011. You'll be interested in what Kaspersky has to say about all that. Microsoft also just revoked 100 malicious window drivers. Wow. Why can't you use threads in Europe? And then a look at part one of our look at satellite security, or should we say insecurity. It's next, the Steve Gibson Security. Now this episode is brought to you by Cisco Meraki. Without a cloud managed network, businesses inevitably fall behind. Experience the ease and efficiency of Meraki's single platform to elevate the place where your employees and customers come together. Cisco Meraki maximizes uptime and minimizes loss to digitally transform your organization, Meraki's intuitive interface, increased connectivity and multi-site management. Keep your organization operating seamlessly and securely wherever your team is. Let's Cisco Meraki's 24 7. Available support. Help your organization's remote, onsite, and hybrid teams always do their best work. Visit meraki.cisco.com/twit
Speaker 2 (00:01:27):
Podcasts you love From people you trust.
Leo Laporte (00:01:35):
This is Security Now with Steve Gibson. Episode 931 recorded Tuesday, July 18th, 2023. Satellite insecurity part one, security now is brought to you by Collide. Collide is a device trust solution for companies with Okta and Collide ensures. If a device isn't trusted and secure, it cannot log into your cloud apps. Visit collide.com/security now to book an on-demand demo today. And Byta Security professionals often undergo manual tasks of collecting evidence. With Drta, companies can complete audits, monitor controls, and expand security assurance efforts to scale. Say goodbye to manual evidence collection and hello to automation. All done at ADA speed. Visit drta.com/twit to get a demo and 10% off implementation. And by Duo Protect Against Breaches with a leading access management suite, providing strong multi-layered defenses to only allow legitimate users in. For any organization concerned about being breached and in need of a solution, fast Duo quickly enables strong security and improves user productivity. Visit cs.co/twit today for a free trial. It's time for security. I know you've been waiting all week long. Finally, Tuesday's here, security now's on the air and there he is. Steve Gibson, the star of our show. Hi, Steve.
Steve Gibson (00:03:09):
Yo Leo, great to be with you again.
Leo Laporte (00:03:11):
You know your episode, your Wikipedia calls you Steve Tiberius Gibson <laugh>.
Steve Gibson (00:03:17):
I, I I think it knows that's not the case. I would hope so. Every once in a while I like to call you that since you are a Star Trek fan. What's up Indeed? So, so a an interesting bit of news about a paper that was submitted and accepted and presented at a recent I E E E security symposium two months ago in May. Caught my eye because it's something in our 18 plus years of the podcast we've never talked about. We've always been talking about on the, the security, you know, fiber optic cables and stuff on the ground. We've never looked up. And today's topic, it started off to just to be, you know, today it ended up being today and next week. So this is satellite insecurity part one for today. Interesting really interesting. And not surprisingly, things are not good up there in the, in the friendly skies.
(00:04:22):
But anyway, we got a lot to talk about. We're gonna look at what Casper Ski had to say about last Tuesday's Microsoft patch event and what security consequences it has for all non subscribing Microsoft Office users. Also, what was inevitably going to happen once the power of large language model generative AI became widely appreciated and available? What does it mean that Microsoft just revoked more than 100 malicious Windows drivers 100 more than what two well-known companies have been added to lops MoveIt file transfer victim list. Oh, what does Dun and Bradstreet have to do with Android apps? Where in the world can you use meta's new threads service and where not, and what's the side effect of Bitcoin addresses looking like gibberish? And after we examine those questions, cover some miscellaneous and user feedback, we're gonna turn our attention. As I said to the heavens, in recollection of those famous words of Henny Penny <laugh>, the sky is falling.
(00:05:39):
Oh, yes, good old Henny Penny. She wasn't wrong. She wasn't wrong. No. And we do have a great picture of the week, which has already generated some, some laughter among the, the Twitter people who saw it earlier. I have not looked, I, as my new policy is to only That's good. Yeah, I, I I increased the size of the show notes to such a point that the the pictures below the fold. Nice. So I will scroll it up and share it with you in just a moment. But first, I do want to say a little word on behalf of our sponsor for this section of the show Collide, k o l i d e. What is collide? It's a device trust solution for companies with Okta. If you use Okta, you want collide and collide ensures that if a device is not trusted, if it's not secure, it cannot log into your cloud apps.
(00:06:32):
You would think, oh, well, doesn't Okta do that? No, all Okta does. All any authentication system does is make sure that that person is who they say they are without collide. It's not checking the security of that person's laptop or that person's land. That's what collide adds if you work in security or it and your company's using Okta for authentication. This is, this is for you. If you have noticed, and I think if you listen to this show, you have noticed the majority of data breaches and hacks these days all have something in common. Your employees. Sometimes an employee's device gets hacked because of unpatched software, let's say, oh, I don't know a unpatched version of say some media server software sitting on the drive. <Laugh>, we won't name names, but you know what I'm talking about. Sometimes an employee leaves you know, crypto keys in the downloads folder.
(00:07:32):
It seems like every day a hacker breaks in using credentials. They phished from an employee. The problem here is though, is you, I mean, it's tempting to say you know, blame the employees, but no, it's not the end users. It's the solutions you're using that're supposed to prevent these breaches. It doesn't have to be this way. Imagine a world where only secure devices can a access your cloud apps can get on your network. In this world phished credentials are useless to hackers. And you can imagine that this world would be a safer place because you don't have a you know, a plex server that hasn't been patched in five years, sitting on that user's network ready to invade. You can. It works with every os by the way, windows, Mac, Linux, and it all has one dashboard for the whole kit and caboodle.
(00:08:22):
Best of all, Kall is designed to help your employees, to enroll your employees as participants, as supporters in your aim to total security. It gets the users to fix the security problems before they can log in so it doesn't create more work for your IT team. And it makes everybody a part of that team. Hey, here's the good news. You don't have to imagine that world. It is here with collide, K O L I D E, visit collide.com/security. Now book an on-demand demo today. See how it works for yourself. Really cool. If you're using Octa, you need collide, K o l i d e.com/security. Now we're thrilled to have them as a sponsor. We thank them for supporting Steve's good work here. And now, ladies and gentlemen, I shall scroll up to see the picture of the week. <Laugh>.
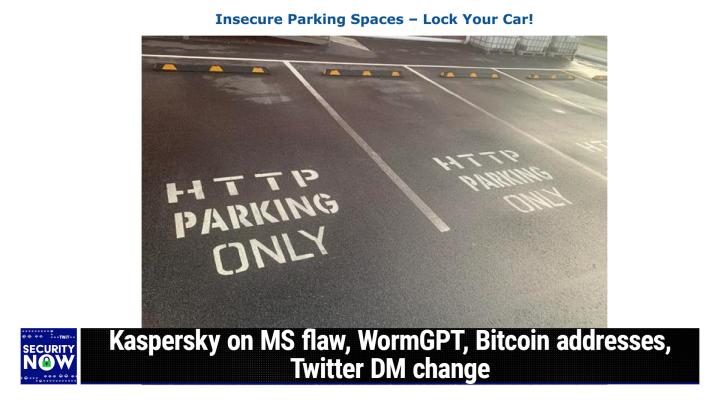
(00:09:16):
I don't know what it means, but I, but I like it. Will you explain, explain this to me, Steve. So the caption I gave, this is insecure parking spaces, lock Your Car, <laugh>. And what we're looking at is something that one of our listeners blessed their hearts, you know, being a listener to the podcast saw and thought, oh my God, I've gotta take a picture of this and send it to Steve. Wow. So you know how parking slots are often labeled with like, who's allowed to park in there. Like, you know you know, Denny's parking only kind of thing. If there's some, you know, movie theater next to it and Denny's is, is upset because people who are going to the movies are parking in their slots. I hate it when that happens. Yeah. don't, don't, yes. Worse. So I, I'm, I'm at Denny's all the time and I want to get park and have my fried egg and get on over there.
(00:10:12):
So Yes, that's right. Yes. You don't want those movie those tho those, those, those movie people get them out of there, those movie people taking up your spot. That's right. So, so here we have, you know, stencil on parking spaces who is allowed to park in them. And I kid you not what, I don't know what the initials stand for, but it says H T T P parking only <laugh>. So of course. So no no insecure yeah, that's right. That, that, that those are insecure parking places. Is there an a TPS next to it? That's the question really. You wanna, someone I can use your car? Yeah, that's hysterical. I love it. So obviously it's a company of some kind, but yeah, exactly. It's some, some companies initials. So, so that, you know, everybody who would be wanting to park there would realize, oh wait, that's, that's, I can't park in this spot that's reserved for http, which, you know, means something to us.
(00:11:13):
Yes. okay, so Casper Ski Being Casper Ski a very technologically savvy security firm had an interesting take on last Tuesday's monthly Microsoft patch event. It was the heading on their posting that first drew me in. They titled their posting that as Kaspersky did bandaid on a dot.dot Corpse <laugh>, which you know, is not the way you want to start describing Patch Tuesday, right? Bandaid on a corpse they said Microsoft i e again, and their subhead was July, Microsoft Patch Tuesday, a collection of exploited vulnerabilities. So this is all definitely worth sharing. As we look back at the past week, we often do a retrospective on Patch Tuesday. Today we're gonna start with what Casper Ski had to say, and then I'm gonna, you know, flesh it out a little bit. So Casper Ski wrote the July, the Microsoft July patch collection has turned out to be a quite surprising event.
(00:12:27):
First there once again, fixing apparently dead Internet Explorer second, as many as six of the vulnerabilities are already being actively exploited by attackers. In other words, six zero days in, in last Tuesday's patch batch, they said third, two of those six actively exploited vulnerabilities were closed, not with patches, but with recommendations. And that's what we're gonna end up talking about because this is a little distressing. So they said, here are the total statistics, 132 flaws were closed making it, you know, one of the larger ones. And this is, you know, every month this happens, nine of which are considered critical. Exploitation of 37 of those vulnerabilities can lead to arbitrary code execution, 33 to privilege elevation 13 to security feature bypasses and 22 to possible denial of service. They said not so long ago we wrote that Internet Explorer had kicked the bucket, but not quite.
(00:13:39):
In particular, we talked about Microsoft's advice to continue installing security updates related to IE. Since some of its components are still in the system. And now it becomes clear why they gave this advice. The July patch closes as many as three vulnerabilities in MS A H T M L, the engine inside the legendary browser in the C V E descriptions, Microsoft states the following. So Microsoft said, while Microsoft has announced retirement of the Internet Explorer 11 application on certain platforms, and I'm thinking, wait, are there any platforms where it hasn't been retired? I don't think so. And they said, my Microsoft said the Microsoft Edge Legacy application is deprecated, right? Remember, edge started using MS HTML and then switched to to Chrome or chro the chromium engine. So they said the Microsoft Legacy application is deprecated. The underlying MS html, edge HTML and scripting platforms are still all supported.
(00:14:51):
The MS HTML platform is used by Internet Explorer mode in Microsoft Edge, as well as other applications through web browser control. The Edge HTML platform is used by WebView and some U W P applications. The scripting platforms are used by S H T M L and Edge html, but can also be used by other legacy applications. In other words, you know, it's, they're, they wish it were dead, but it's just deeply, it's too deeply wired in to Windows to actually go away and it's got some problems. So they said updates to address vulnerabilities in the MS HTML platform and scripting engine are included in the ie cumulative updates. Edge HTML and chakra changes are not applicable to those platforms to stay fully protected. We recommend the customers who installed security only updates install the i e cumulative updates. And yes, I second that advice. Okay, so back to Kaspersky, who says the most dangerous of the freshly discovered i e vulnerabilities is C V E 20 23 30 2046.
(00:16:06):
And of course, all the CVEs I'll be talking about are 2023. So I'm just not gonna be saying that every time anyway. 30 2046 they said, and it's already being used in real attacks. It's successful exploitation allows cyber criminals to elevate their privileges to those of the victim attack scenarios. Involve the creation of a malicious file that's sent to the victim by email or hosted on a compromised website. So, you know, opening a file, bang, all attackers need then is to convince the user to follow the link and open the file. The remaining two vulnerabilities, 35,308 and 35 3 36 can be used to bypass security features. The first allows a cyber criminal to create a file bypassing the mark of the web mechanism so that the file can be opened by Microsoft Office applications without protected view mode. And both holes can be used to trick a victim into accessing a URL in a less restrictive internet security zone than was intended.
(00:17:13):
The next two vulnerabilities are also being actively exploited, but instead of full fledged patches, they've only received security recommendations. And this is the woo, the we're we, we we're gonna be spending some time on this cuz this is a little surprising. They wrote the first 1 36 8 84 with C V S S rating. 8.3 is being exploited in the storm 0 9 7 8 slash romcom remote code execution attacks on office and windows to stay safe. Microsoft advises adding all office executables to the feature underscore block underscore CrossCore protocol underscore file underscore navigation list. Okay, that's actually the name of a registry key. So feature block, cross protocol file navigation. And we'll be coming back to that as I, as I said, and have a lot more to say about that in a minute. Casper C continues the second unresolved issue. And, and again, what I just talked about is, is like a problem that Microsoft has not has chosen not to fix.
(00:18:37):
And we'll explain why. They said the second unresolved issue relates to the signing of kernel level drivers. This one doesn't have a C V E index. Casper Ski says, but only a guide with recommendations. Microsoft revoked a bunch of developer certificates used in advanced persistent threat attacks and blocks several malicious drivers, but the root of the problem remained. Hackers still manage to sign drivers with Microsoft certificates or sign them backdated to make them work as one of the exceptions and not require the MS developer portal signature. And this is something we've been talking about, right? How, you know, Microsoft really has a problem with driver signing. They said as a countermeasure, Microsoft recommends keeping both windows and E D R. You know, that's the the end the endpoint security up to date. The only small consolation is that in order to exploit such drivers, the attacker must have admin privileges.
(00:19:41):
On the other hand, if you've got privilege elevation exploits wandering around like in ie, that may not be difficult. Besides the above mentioned vulnerabilities, there are three more holes that are already being exploited by cyber criminals. We've got 30 2049 a smart screen security bypass feature vulnerability. Its exploitation allows the taggers to create a file that opens without displaying the windows warning download from the internet. We've got 36 8 74 a privilege escalation vulnerability in the Windows error reporting service that allows attackers to elevate privileges if they already have normal permissions to create folders and technical performance monitoring files. And finally, 35 3 30 35 3 11. It's a security feature bypass vulnerability in Outlook. Its exploitation helps cyber criminals avoid showing warnings when using preview. And of course, as we know, clever attacks actually do use these things in order to slip past users even when they're trained up and are wary.
(00:20:54):
Okay, so on balance, we got a bumper crop of 132 to patches this month, nine being critical, 37, allowing for arbitrary code execution, six being actively exploited in the wild as true zero days, one of those zero days being actively exploited in the wild right now. Was that 36 8 84? That's the one carrying the C V S S, which is pretty high of 8.3 being exploited in a fishing campaign being conducted by a group designated as storm 0 9 8 7. What's got people stirred up is that despite this being actively exploited in the wild and having been identified as a zero day, Microsoft has not patched it and they appear unlikely to do so. The reason is that this phishing campaign is using a feature, not a bug. Were it to be sa were it to be disabled for security. Microsoft is afraid that may, that might break too many existing things and so they're afraid to turn it off.
(00:22:16):
Now this is one of those things and we've encountered them before, which Microsoft should have turned off a long time ago, in which cases would've never been a problem, you know, or better yet should have never made possible in the first place. You know, in which case developers would've found like legitimate developers would've found some other safer way to do the same thing. But no, it's like scripting an email. You know, what could possibly go wrong? Okay, so what does Microsoft have to say about this? Microsoft's posting of July 11th, right? So that was Patch Tuesday last week. Microsoft posted about this in a separate posting titled Storm 0 9 7 8 attacks Reveal Financial and Espionage Motives. So I thought, okay, this is, as I was digging into this, what's going on here? Microsoft said, Microsoft has identified a phishing campaign conducted by the threat actor track as Storm 0 9 7 8, targeting defense and government entities in Europe and North America.
(00:23:26):
The campaign involved the abuse of C V E 2023 36,884, which included a remote code execution vulnerability exploited before disclosure to Microsoft. In other words, a zero day right, it was exploited before disclosure to Microsoft via Word documents using lures related to the Ukrainian World Congress storm 0 9 7 8. Also they have DEV 0 9 7 8, also referred to as romcom. The name of their backdoor by other vendors is a cyber criminal group based out of Russia known to conduct opportunistic ransomware and extortion only operations, as well as targeted credential gathering campaigns likely in support of intelligence operations. Storm 0 9 7 8 operates, develops and distributes the romcom backdoor. The actor also deploys the underground ransomware, which is closely related to the industrial spy ransomware first observed in the wild in May of 2022. The actor's latest campaign detected in June of 2023. So just last month involved abuse of this exploit 36 8 84 to deliver a backdoor with similarities to romcom.
(00:24:54):
Storm 0 9 7 8 is known to target organizations with Trojan versions of popular legitimate software leading to the installation of Romcom Storm 0 9 7 eight's. Targeted operations have impacted government and military organizations, primarily in Ukraine as well as organizations and Europe and North America potentially involved in Ukrainian affairs. Identified ransomware attacks have impacted the telecommunications and finance industries among others. Okay, so <laugh>, now we get to the good part of this after that background. Microsoft 365 defender detects multiple stages of storm 0 9 7 8 activity. Customers who use Microsoft Defender for Office 365 are protected from attachments that attempt to exploit 36,884. In addition, Microsoft's who use Microsoft 365 apps, versions 2302 and later are protected from exploitation of the vulnerability via office. Organizations who cannot take advantage of these protections can set the feature block cross protocol file navigation registry key to avoid exploitation. And in Microsoft's posting from last week, that registry key was highlighted and underlined like a link.
(00:26:23):
And sure enough, it was a link. So I clicked it and where did it take me? It jumped me to a page and the link used the pound sign suffix to preposition me a ways down the page to a specific section which they wanted to refer to. And that prevented me from initially seeing the title, the page, the section of the page I was jumped to was titled New Restrictions on Use of the File Colon slash slash Protocol. So of course I thought, whoa, I can't believe this. That's still around. I know Leo. Oh my God, I thought, God, I so like, whoa. That's what we're talking about here as being exploited in a zero day today. Oh Lord, we're talking about bad guys leveraging the file colon slash slash scheme to arrange to run programs on the user's machine from office documents. And that thought was followed by wait, exactly as you said, Leo, that's still possible.
(00:27:30):
So then I started to read what Microsoft wrote on this page that had been linked to by their posting from last Tuesday. And there they wrote, prior to this update, internet Explorer would allow non file protocol i e http and HTTPS delivered pages to frame, in other words, using an iframe or navigate to pages that were delivered using the file slash slash protocol scheme, ie. Will only block loading of resources from the local computer, for example, file slash slash slash c colon slash temp slash te test jif, for example, but resources from non-local paths would be allowed. And then they, they said, here's an example page displayed in i e 9.0 0.1, and I thought i e nine. So I finally scrolled up to the top of the page to see what in the world I was reading. And it was from Microsoft posted on August 12th, 2011.
(00:28:47):
Yes, 12 years ago titled Internet Explorer 9.0 0.2 Update God, oh my God. And, and sure enough, they showed where I e 9.0 0.1. You know, apparently just like office apps today will load an iframe with text content provided by the file colon slash slash scheme from, for example, live.si internals.com was the example. They go gay gave from 12 years ago, and then they show the same thing done under the new and improved i e 9.0 0.2. And what do you know, by golly, that iframe is empty then they note other browsers have blocked cross protocol interactions for quite some time. Here are screenshots of Firefox five <laugh>, you know that, that, you know, the browser from times past Chrome 14 and Opera 11.5 developer consoles in this same scenario. Okay, so just to make sure that everyone is on the same page here, this Russia located Storm 0 9 7 8 phishing campaign has been successfully installing Trojan code into unsuspecting office users machines using a tech technique that i e 9.0 0.2 celebrated ending since in August, 2011 of 2011.
(00:30:44):
<Laugh> <laugh> noting at the time that everyone else had already done that yet just last week, Microsoft wrote, and I'm quoting them again, the campaign involved the abuse of 36 884, which included a remote code execution vulnerability exploited before disclosure to Microsoft via Word documents, although they had disclosed it to themselves in August of 2011. So they've known about it since I e nine finally decided to fix it. And even then, it was the last of the bunch to do so, so it came back, they turned it back on for some reason in in office who knows when, but you know, now Microsoft is afraid to turn it off again. The, despite the fact that it's being abused in a, in a Trojan installing remote code execution vulnerability in their own office documents, they can't turn it off because they have no way to predict what doing so might cause to break.
(00:32:03):
So they're not gonna make it their problem unless you're using their online subscription office stuff, in which case they'll protect you from it. But if not, it's up to you. So there's a registry key, which will allow anyone and everyone to turn off this behavior, which is currently under active abuse, apparently by Russians to install malware into the computers of unsuspecting link clickers. I've got a, a picture from a registry snapshot showing this. The key is H key local machines, software policies, Microsoft Internet Explorer main feature control feature block cross protocol navigation. And under that key, it's necessary to enumerate each of the various Microsoft apps whose behavior in this case you would like to restore to Internet Explorer 9.0 0.2, where this was originally fixed 12 years ago. I also have a screenshot of the registry showing the enumeration of the Reg D word values under that key, you know, and Leo, thank you.
(00:33:28):
It's on the screen right now. So what are you supposed to change it to? You, well, you're supposed, you have to add all of that. None of that is there now. Oh, no. Okay. All right. Yeah, you gotta put all that in. And now isn't it possible to make a a, a red jetted file that you just double click? Absolutely, absolutely Red jetted file. And it would just be a, a simple one click and it, and it would do that. Now, as I said, this is stirred up a bunch on the net because, you know, Microsoft is literally not fixing something that is in active abuse right now in as a remote code execution vulnerability. They can't, they can't fix it because it will break things that have that, that developers are depending upon. Yeah, you should break it. Frankly, break it. Yes, it's a stupid thing they've had in the first place.
(00:34:17):
It is incredibly re incre, as I said, like scripting an email. What could possibly go wrong? The problem is all over the net, you will now foul. You find scripts that are doing this. Unfortunately, they spell PowerPoint all the way out, and that's incorrect. It needs to be power PT xe. So, so just a heads up, if you do use these scripts, you'll see that they have power. P O I xe, it needs to be power pt, do X, the actual name of the xie the, the, you know, that, that component of office. So anyway, it's crazy that they've done this. I, who knows when this came back into use, the bad guys found it and said, oh, that's nice. Just like Internet Explorer, 9.0 0.1 <laugh>. It's 2011 all over again. <Laugh>, we can come back to our own trick tricks. Oh my God. Unbelievable. Unbelievable.
(00:35:22):
Okay, so I suppose it was inevitable though it happened sooner than I would've expected. The underground now has a chat, G p T style, generative ai, all their own without any of the abuse prevention built into the front end. That is in chat G p t, it is known, and I kid you not as worm G P T and it exists. The news of this comes from a reformed black hat computer hacker named Daniel Kelly, who collaborated with the team at the business email and messaging protection security firm slash next. Daniel begins his posting by providing a background about the use of legitimate generative AI like chat G p T and discusses as we have here the fact that such AI can be hugely useful to bad guys when they're able to coerce it or seduce it into giving them what they want. Meaning chat G P T, which, you know, is trying not to, but now it appears this will no longer be necessary.
(00:36:39):
Daniel explains, in his posting, he said, we recently gained access to a tool known as Worm g p t through a prominent online forum that's often associated with cybercrime crime. This tool presents itself as a black hat alternative to G P T models designed specifically for malicious activities. Worm G P T is an AI based on the G PT J language model, which was developed in 2021. It boasts a range of features including unlimited character support, chat, memory retention, and code formatting capabilities. Worm G P T was allegedly trained on a diverse array of data sources, particularly concentrating on malware related data. However, the specific data sets utilized during the training process remain confidential, known only to the tools author and publisher. We conducted tests focused on business email compromise, you know, b e c attacks to comprehensively assess the potential dangers associated once Worm G P T or similar tools become more widely available and well-known in one experiment, we instructed worm G P T to generate an email intended to pressure an unsuspecting account manager into paying a fraudulent invoice.
(00:38:16):
The results were unsettling. Worm G P T produced an email that was not only remarkably persuasive, but also strategically cunning, showcasing its potential for sophisticated phishing and b e c attacks while appearing largely similar to TA to chat G P t worm g p t is deliberately unbounded by any ethical boundaries or limitations. It will answer any question asked, will generate any form of document required, and will author any type of malware requested. This experiment underscores the significant threat posed by generative AI technologies like Worm, G P T, even in the hands of novice cyber criminals. It renders them immediately far less novice in their presentation and skills. Generative AI can produce emails with impeccable grammar, making them appear significantly more legitimate and reducing the likelihood of being flagged as suspicious. And the use of generative AI enables the execution of much more sophisticated b e c attacks than could have been launched before.
(00:39:40):
Even attackers with limited skills and inability to use the target's language can now use this technology, making it an accessible tool for a broader spectrum of cyber criminals. And Leo, as I said, this happens sooner than I expected, but in retrospect, of course, you know, do you know what the quality of the code is? I mean, so far the code we've seen generated by other LLMs has not been superb. Well, it's been, it, it's, it, it's, it's not been bug free in the same way that if you ask me, well, worse than that, it's been kind of trivial. So it's not, I mean, in other words, there are plenty of people with the skills to write this code themselves. It just enables people who don't even have those skills to create some, right? And so we would argue that this code was trained on code that was written by skilled people, and it is just regurgitating it.
(00:40:39):
On the other hand, it's, you know, it, it it is often producing credible code. And I think what we can, what we, we can expect to see is this will only get better mo going forward. So anyway, it, it, I guess it's, it's the, the, the, the point is we've often joked at like ransom notices, poor grammar, and you know, and you see, you know, you look, if you take, if you bother to read spam, it's ob it's often obviously spammy. Oh yeah. Oh yeah. Well, we can expect that to go away now because it will be easy to, to dump that this through. A a a large language model trained up in the target language, and it will, you know, clean up the, the, the misspellings and, and the bad grammar and make spam now become indistinguishable from, you know, legitimate email.
(00:41:36):
So on our radar Microsoft revoked more than 100 malicious drivers. And when you first encounter the headline Microsoft Revokes more than a hundred malicious drivers, you know, that seems like great news, right? You know, woo, 100 fewer malicious drivers now. But then you stop and think, wait a minute, before they did that, there were 100 additional malicious drivers floating around, you know, and then, and if there were that many more than, isn't this gonna be just like bugs where we're never gonna run out of them? And of course, malicious drivers could do anything they want with the system. And that's, you know, that's not good. And then we recall that historically Microsoft's track record of keeping these malicious driver lists up to date has been sae you know, a bit less than stellar. Like, didn't we catch them for two years? Like not bothering to update the list and then going, oh, yeah, like, and then say, saying that they were going to, but even then they didn't, as I recall from prior podcast, the problem is that all of the evidence suggests that there are far too many ways to get around Microsoft's driver signing.
(00:43:01):
Bad guys apparently have no trouble doing it. Colonel Driver signing apparently poses a much greater inconvenience for the good guys than it does for the bad guys who simply arrange somehow to run a bypass. And in fairness, this isn't really Microsoft's fault, at least not today, they're still stuck with the original design from Windows nt. Now, consider that Windows NT was first released and the architecture was in place in late July of 1993. So July of 93, almost exactly 30 years ago. When the world, as I've often said, was a very different place considered that Netscape didn't invent SSL until two years after that in 1995. So yeah, very different world 30 years ago. So T'S architecture, which considers peripheral drivers to be trusted peers running alongside it in Ring zero, you know, that architecture did not foresee and could not really have foreseen the degree to which unknown and untrusted third parties would be creating what amount to kernel extensions.
(00:44:32):
It should not be necessary to fully trust some random printer driver to the same degree as Microsoft's own colonel code. But the architecture of Windows nt, which is what we're still living with today, makes what has turned out to be a very poor assumption about the trustworthiness of drivers. Drivers are sacred. They were, they were designed that way, they're meant to be, but now everybody just includes them in random things that you install. And you know, they're down in the kernel along with everything else that Microsoft created. And with full ring zero privileges. So here's how Microsoft couches the current mess, while at the same time taking more than 100 existing previously certified good and safe Windows drivers out of circulation. Microsoft said the Microsoft Windows hardware compatibility program, W H C P certifies, that drivers and other products run reliably on Windows and on Windows certified hardware.
(00:45:51):
First reported by Sophos and later Trend Micro and Cisco. Microsoft has investigated and confirmed a list of third party W H C P certified drivers used in cyber threat campaigns because of the driver's intent and functionality, Microsoft has added them to the Windows driver dot STL revocation list. Woohoo. The Windows driver STL list is part of the Windows Code integrity feature. The file contains dri digital signatures and lists of drivers that Microsoft has revoked. This stops malware from running in the Windows Boot and Windows kernel processes. Driver STL ships along with Windows, but is not part of Windows. It cannot be turned off, tampered with or removed from the system. Microsoft updates the contents of the revocation file. The updates are sent to Windows systems and users from Windows update, right? Like every six months. The Windows Code integrity feature validates the source and authenticity of the drivers that run in Windows.
(00:47:09):
The feature uses digital signatures to verify the integrity of Windows files and drivers. It prevents the loading of unsigned or tampered files. Windows Code integrity and the driver STL revocation list have existed alongside Windows since Windows Vista, okay? So what this all means is that as Microsoft themselves, themselves, say W H C P certified signed drivers are being used in cyber threat campaigns because driver signing is no longer workable. I mean, it's not useful. They're having to do blacklists of drivers digital signatures, listing them in this file, and they just added more than a hundred. I checked their previous update was December of last year. So we're getting these fixes in large batches less than twice per year. And unfortunately, this really isn't adequate, but it's what we've got. And I don't see anything that they can do now. They can't change the way Antis architecture is.
(00:48:24):
We're stuck with it. You know, they're no long, they're no more, more able to change NT than Intel could decide to give up on its X 86 family and do something else. You know, this is, you know, old legacy architecture dating back three decades, and all Windows is based on it. They keep changing, you know, the API layers moving that all forward from win win, win 32 and net. And you know, and, and then, you know, a whole series of evolutions on top of this fundamental architecture. And unfortunately, the way it's been designed, they're allowing people to write whatever they want to get it signed. And until it's found to be bad, it's allowed to run in the kernel.
(00:49:14):
Well, it's the world we've got. And Leo, let's talk about a sponsor that we've got. Okay? <laugh>, gladly, gladly. I will, I'll talk about DURATA as we continue on with security. Now, this portion brought to you by a fantastic tool for anybody who's doing manual compliance, evidence collection, drta, D R A T. Here's the question. Is your organization finding it difficult to manually collect evidence and achieve continuous compliance as it grows and scales? DDA is a leader in cloud compliance software. That's what G2 says. Drta streamlines your SOC two, your IO 27 0 0 1, your P C I dss, your gdpr, your hipaa, all the compliance frameworks providing a 24 hour continuous control monitoring so that you could focus on scaling securely with a suite of more than 75 integrations. Stratta easily works through applications you're using like AWS and Azure, GitHub, Okta, CloudFlare, 75 of 'em, I can go on, I won't.
(00:50:23):
Countless security professionals from companies including Lemonade and Bamboo hr, they've all shared how critical it's been to have drta as a trusted partner in the compliance process. Expand security assurance efforts using the drta platform that allows you to see all your controls, easily map them to compliance frameworks. You'll gain immediate insight into framework overlap. For instance, ADA's, automatic dynamic policy templates, support companies new to compliance using integrated security awareness training programs and automated reminders to ensure smooth employee onboarding. And they're the only player in the industry to build on a private database architecture. That's really important. Your data can never be accessed by anyone outside your organization. All customers receive a team of compliance experts. Strata is your partner throughout this that includes a designated customer success manager. Strata has a team of former auditors who've completed more than 500 audits between them. Your DRTA team keeps you on track to ensure there are no surprises, no barriers, and you will love the pre-audit calls that'll prepare you for that day when your audits begin.
(00:51:35):
ADA's Audit Hub is the solution to faster, more efficient audits because you, you have a place where you can both go auditor and and your company save hours of back and forth communication. Never misplaced crucial evidence makes it easy to share documentation easily. All the all the interactions, all the data gathering occurs in ADA between you and your auditor. So you don't have to, you know, go from tool to tool and say, oh, I got it right here. Go through your files. It makes it so much easier. With ADA's risk management solution, you can manage end-to-end risk assessment and treatment workflows. You can flag risks, you can score them. You can decide whether to accept, mitigate, transfer, or avoid them. Drta maps appropriate controls to risk simplifying risk management, automating the process. Finally, there's ADA's Trust Center, which provides real time transparency into your security and compliance posture that makes everybody happy.
(00:52:35):
It improves sales and improves the security reviews. It gives you a better relationship with your customers and your partners, cuz you're transparent and they've got a place they can go to Verify that. Say goodbye to manual evidence collection. Say hello to Automated Compliance by visiting drta.com/twit. That's R A T arata.com/twit drta bringing automation to compliance at drta speed. Visit drta.com/twit. Make sure you go there because that way they know you saw it here. And everybody wins drta.com/twit. Now on with the show, Steve. So following the massive Move It Massacre. Oh, that's a good name I like, yeah, yeah, <laugh>, and unfortunately it's too accurate. Boy, Russia's clop leak site has been steadily adding to the list of companies whose data it successfully exfiltrated and is now threatening and holding for ransom under threat of full disclosure, which will occur when their proprietary data are sold to the highest bidder on the dark web.
(00:53:48):
Two recent additions to the list, which now numbers more than 200 companies are noteworthy. The well-known stock photography portal, Shutterfly and the Discovery Channel are the latest victims to be listed. Yikes, that was a that was a bad hack. And of course, that's the sequel injection vulnerability that I've bored everybody by <laugh> yammering on endlessly about, because it just drives me nuts that, that know this is still being done today. This, here's one that caught me by surprise, and I'm not sure how many of our listeners will recognize the name Leo, but last Wednesday, Google posted to the Android developer's blog the news of a new policy to begin this August. It had the headline, new policy update to Boost Trust and Transparency on Google Play. Google wrote one of the many ways we keep Google Play a safe and trusted platform. Yeah, they wish is is by verifying the identity of developers and their payment information.
(00:54:56):
This helps prevent the spread of malware, reduces fraud, and helps users understand who's behind the apps they're installing. For example, we require developers to verify their email address and phone number to make sure that every account is created by a real person with real contact details. Now, that doesn't seem like much anyway. They said today we're announcing expanded developer verification requirements in our play console requirements policy. As part of this update, we'll also share more developer details on your app store listing page to help users make more confident informed choices about what to download. Okay, so it's interesting, first of all that this is happening. Now, it seems like certainly an overall good thing to do, but it's also interesting that it comes after we reported that news of us legislators threatening to have app stores proactively warning US users when an app they wanted to ha to to load had ties to, to China.
(00:55:59):
Anyway, Google then explained the specifics of their new plan and get this Leo requiring organizations to provide a DUNS number. They said when you create a new play console developer account for an organization, you'll now need to provide a Dunns number assigned by Dun and Bradstreet. Dunn's numbers are unique nine digit identifiers that are widely used to verify businesses because we'll use Dunn's as D U N S numbers to verify your business information during the account creation process. It's important to make sure the information that Dun and Bradstreet has about your business is up to date before creating a developer account. You may also be required to submit official or organization documents to help us verify your information. If you're not sure if your organization has a Dunn's number, you can check with Dun and Bradstreet or request, or request one for free. The process can take up to 30 days.
(00:57:13):
So we encourage you to plan ahead now. Okay. Anyone who's been in business for long will have encountered Dun and Bradstreet. I googled Gibson Research Corporation, dun and Bradstreet, and was taken right to our page at d and b. Dun and Bradstreet was founded by Robert Graham Dunn and John m Bradstreet in Okay, 1841 <laugh>. Yeah. 182 years ago. It's, it's how business is done that <laugh> That's exactly right, Leo. Basically they just keep records on all businesses and they serve as a clearinghouse for corporate data. I just renewed GRCs server and code signing certificates with DigiCert. And since the certificates are organization validation, you know, ov which is at one level up from DV domain validation and ev extended validation cuz I needed, I want EV code signing certs, which are slightly more trusted. It was necessary for us to have someone present to answer our corporate phone line at the number that's listed for GRC at Dunn and Bradstreet.
(00:58:37):
Right? There's no way around that, right? That you, you have to do that. It's kind of like an AV cert, an extended cert, right? It's, it's a, yeah, yeah, yeah. So anyway, I thought it was very interesting that Google is adding this layer and level of corporate authentication. It's, it's not unusual. I've had to do that in the past with as well for, for what? You know, like if you want a, a business account at Facebook and things like that. Oh yeah, yeah, yeah. You know, yeah. You just have to prove that you are the business and you know that you, you are, and again, anyone who's in business for long will have it. D and b should, should, should have discovered you by themselves. Oh yeah, we're indeed And do ought to be listed. Yeah. Yeah, yeah, yeah. So they said on August 31st we'll start rolling out these requirements for anyone creating new play console developer accounts.
(00:59:27):
And, and they said your about the developer section will be visible to users as soon as you publish a new app over the first couple of months, we'll listen to feedback and refine the experience before expanding to existing developers. Then in October they wrote, we'll share more information with existing developers about how to update and verify their existing accounts. So initially only for new accounts, you know, they'll, they'll work out that process, get all, any, any kinks and wrinkles out of it, but then they're gonna retroactively go back and tell all existing corporate, you know, organization accounts, you need to get yourself validated through d and b or, you know, we're gonna have to talk to you about that. So anyway, I just thought that was interesting and, you know it's a good thing that there'll be more accountability for where apps are coming from, especially on the Android store.
(01:00:25):
<Laugh> a titled this No Threads for You or eu the European Union's GDPR is of course a frequent topic on this podcast because it's being wielded to complain about US companies cross border transit of EU citizen data. When men are recently released, their smash hit threads in intended to be an alternative to Twitter. They deliberately did not release it in the European Union because it was pretty clear by now that various EU countries would jump up and down and file lawsuits against the privacy invasion they felt were being created by this American juggernaut. We have over here however that I mentioned, the threads has been a smash hit. Oh yeah. <Laugh> and those uhhuh, where are we now? I've, I've not last I saw 150 million users. Wow. It's been a little more than, it'll be two weeks tomorrow. So, wow. It's growing fast. And the, those same European Union citizens who are being protected by their gdpr, whether they want it, whether they want it protection or not, they're pissed. <Laugh>. Yeah. Huh? They immediately began clamoring for access to threads and they discovered that they could country hop by using a v pn. Well, that worked up until last Thursday, Uhuh, when people began complaining that they could no longer access threads over their VPNs because META decided that they better close that loophole too. So yes, once again, no threads for you in the eu.
(01:02:11):
Okay. And finally, this little bit of news was just too fun not to share. It seems that a Brit has been sentenced to three years in prison for blackmail and unauthorized access to a computer network after he tried to hijack a ransomware payment, which was being made by his employer to a ransomware gang. So this all began five years ago in February of 2018 when an Oxford based company where this British citizen, Ashley Lyles, was working as an IT security analyst, but apparently not. The sharpest IC security analyst around his firm was hit by ransomware officials in the uk say that after Ashley's company was hit by a ransomware gang, Ashley abused his position in the company's IT staff to secretly, but turns out not that secretly log into his manager's email account and replace the attacker's Bitcoin address with his own. After all, they all look alike.
(01:03:28):
Ashley also created an email account that was nearly identical to the attacker's address, obviously, so that the change would not be noticed and then presented his, and then pressured his employer to pay the ransom. But Ashley apparently wasn't very accomplished with it as he had not covered his tracks. His whole scheme collapsed when the company's security team noticed the unauthorized access to the executive's email an investigation per then you know, it into what happened tied the intrusions to Ashley's home IP address. Whoops. And then the entire plan fell apart. It took five years for the wheels of justice to grind slowly, but Ashley will now be behind bars for the next three years because his little scheme didn't work and who knows how much money he would've made. Although you have to imagine that when the bad guys said, we didn't get the payment, and the company said, you know, we sent it to you, they would've checked the address and realized, whoops, it went to the wrong address.
(01:04:41):
And then, you know, how did that happen? Would've, you know, occurred? So anyway, don't do that. Last Thursday the 13th this is just a, a bit of miscellaneous that will be of interest to our Twitter using followers. And to me, actually, last Thursday the 13th TechCrunch wrote as Twitter fends off new competition from Instagram's threads. The company today announced a change designed to cut down on spam in users' inboxes. Starting as soon as TechCrunch wrote July 14th, Twitter will introduce a new messages setting aimed at reducing spam in direct messages by moving messages from verified users. You don't follow back to your message request inbox instead of your main inbox. Only messages from people you follow will arrive in your primary inbox going forward. Notably, these changes will also now apply to everyone who has their inboxes open to allow messages from everyone, which is you.
(01:05:55):
Well, of course, yeah, exactly. The reason I'm bringing this up as pertinent is that I very much enjoy and even depend upon the ability of this podcast listeners who are also Twitter users. You know, if only, you know, occasionally using Twitter like me to be able to send dms, as Leo always reminds our listeners at the end of every podcast, my dms are open, but this just closed them at least to people to with whom I've never corresponded in the past. So TechCrunch continues. They said previously people would only be able to message you via Twitter dms if you had opted into an option as I had to receive messages from anyone through Twitter settings or if the senders were verified users, meaning they pay for a Twitter subscription. And you had specifically opted into receiving direct messages from verified users. Additionally, people could direct message you if you had first sent them a direct message at some point in the past.
(01:07:04):
The change to move messages from verified users back to the message request inbox instead of the primary inbox unless you follow them, signals another failure of Twitter's new verification system where users can pay for the blue badge that gives them elevated status on the platform before becoming pay to play verification indicated a person was a public or notable figure of some sort, a politician, celebrity athlete, journalist, or some other well-known individual by making the verified check mark accessible to anyone who had a credit card to buy it. Twitter diluted the value of verification rights tech crunch. That apparently escalated to the point that people had become bothered by verified users spamming their main inbox when they had set it to, when they set it open to receive dms from the blue badged crowd. In other words, it's a tacit adminis admission that Twitter has a verified user spam problem.
(01:08:13):
Twitter notes that if users still want to receive dms from verified users in their main inbox, they can manually switch back to that setting at any time after these changes are put into place. The update will also make it more difficult for journalists to contact sources for more information or permission to use a tweet as they not only lost their verification badges under Musk, but now even if they now pay to be verified, we'll have their dms dropped into the messages requests folder where they may remain unseen. And finally, as some users pointed out in the replies to Twitter's announcement, the update doesn't actually cut down on spam from verified users or otherwise. It simply relocates those messages to a different folder. So after encountering this news yesterday, I went over to check on my settings and sure enough, I have a screenshot of what I found.
(01:09:09):
There are three settings. Allow messages only from people you follow. Allow message requests only from verified users and allow message requests from everyone. You know, I was set to the middle one from verified users. I set myself back to from everyone as I had been before. So we are again open for business. Anyway, so regular dms will be able to flow in. I was noticing that there was something called message requests in my dm. I, my favorite Twitter interface is tweet deck. And so that I had like 10 things and I thought, well, I dunno what those are. And I hadn't bothered to look because I was getting plenty of regular tweets from people. Then I realized these were people that I had responded to in the past. So that makes sense. You know, whenever I can I will make the time to send a thanks or an acknowledgement or a comment back to someone who has sent something to me or asked a question, you know, or provided a really great picture of the week as a, as often the case.
(01:10:22):
So I suppose that it was the, because I had Previ previously interacted with these people that, you know, I, even though I was set to that middle setting Twitter knew that I had a dialogue in the past. So it allowed those to come through. Anyway, we're back to everybody again, so I'm glad for that. A couple of closing the loop tidbits. Steve Fintel, he tweeted. Hi Steve. I've been listening to security now since episode one. You were recently talking about your favorite T O T P apps. Since you're already a bit warden user, why not use its T O T P after filling in your credentials? It places the current one-time password in the clipboard automatically. So when you get to the next dialogue that's asking for the o one-time password, you just need to paste it.
(01:11:14):
This question is far more important than it might seem at first glance, because doing this significantly increases the user's risk. This has nothing to do with Bit Warden, which is, as Steve notes, the solution I chose after leaving LastPass And at the time I made that decision, I explained the rationale for my choice for, for choosing Bit Warden in that episode titled Leaving LastPass Well. And furthermore, LastPass offered its own t o t p authenticator and which we recommended against using for the same reason you're about to describe now, right? Yeah. From a tr from exactly from a trick, from a strictly theoretical security standpoint, having the same system, no matter how secure it might be, containing both the secrets for providing your username and password login and the secrets for also providing the one time password code creates a single point of failure I use and rely upon an external disconnected standalone authenticator specifically because it is all of those things.
(01:12:26):
It would make me very nervous to have my password manager not only able to autonomously provide my username and password, but to then also provide what is intended to be a separate and robustly independent, a additional form of identification, additional factor. It is absolutely less convenient to have to manually transcribe those six digits for me, it's a very small price to pay for the huge increase in security that that affords. And it serves as a classic example of the trade-off between convenience and security. I'm not saying that no one should have their password manager handle everything, but Steve asked why I'm not doing it. And I doubt that I ever would when we all received that in initially frightening news of the last pass breach and not the first one. I remember commenting on this podcast that one of the first things I did was to look over through the accounts I have registered for one-time passwords, and I was immediately relieved to see that all of my most important accounts were protected by those entirely independent secrets that were, you know, stored outside of, of the browser.
(01:13:51):
But imagine if LastPass had also offered T O T P fill in and if my account also contained all of those T TTP secrets as well. So anyway, Steve, thank you for the terrific question and the opportunity just to say, eh, you know, there is such a thing as too much convenience and I think that's crossing the line a different, Steve, Steve m he said in episode nine 30, you talked about using dynamic DNS based port forwarding for connecting your Sonology NAS devices. I have two Sonology devices at separate locations as well. I use Tail Scale, which has a native sonology app to connect them over vpn. Then they can talk to each other with no problem. I also have it installed in on my Mac so I can use the Sonology Drive client to access the shares on my NAS from anywhere in the world.
(01:14:52):
And Steve, I just wanted to say that's another great solution. We visited the topic you know, of so-called overlay networks many times. The very first one was achi. Back then Achi cleverly reused the entire five dot ipv four space that is all ips beginning with Five Dot and then something that, something that something for its own virtual IP nodes. Since at the time, none of the IP dot, you know, the, the, the, the five IP space had ever been used. That meant that any machines reference to an IP beginning with Five Dot could be assumed to be referring to a ACHI node for routing. The fact that there's a native tail scale implementation for the Sonology, NASA is just more one reason to love sonology. I haven't yet had any need to access my NASAs while roaming, but I'm sure that need will eventually arise, and I'm delighted to know that I'll be able to use tail scale to securely and transparently connect to those NASAs you know, as if they were still sitting right next to me.
(01:16:07):
So that's really cool. And LA lastly, timber, T I M B R. He said, hi Steve, when possible please teach us about Windows page file and swap regarding our recent SSDs and Lifetime. Is it recommended? Okay, so the first thing I do when I'm setting up a new machine is to make absolutely certain that the Windows page file is either moved to a spinning magnetic drive or turned off entirely. Of course, it's only feasible to turn it off entirely, or at least it's only practical. You know, to completely disable the page file when a system has sufficient main memory. But all of mine do, the first thing I do is load up ay system with as much memory as it can handle, or it, you know, makes sense as just part of my standard operating procedures. And then I disable paging completely. It works just great.
(01:17:12):
And you know, having lots of RAM is something that just keeps paying dividends over the lifetime of, of, of the machine. So anyway, absolutely you want your, you do not wanna swap on an s S D, there's just no good reason to, especially with ram. You know, ma main main system Ram being so cheap these days. And this question of writing to solid state mass storage leads me to a note from a spin right tester. Last week I talked about spin right's first release candidate and I explained about its future switch to the embedded RTOSs 32 os. At that time, I had what I had, what I'm about to share, but I didn't wanna further burden that podcast. I'll just share it now, a Spin Wright pre-release tester named Jim McHale posted to GRC Spin Wright Development News group. He wrote, I have an old Lenovo with a Samsung eight 40 S s D.
(01:18:10):
He said, loaded up Alpha 32, meaning spin, right Alpha 32 and get these rates front of the drive, 1 38 megabytes per second middle of the drive, 4 45 megabytes per second end of the drive, 56 megabytes per second. So again, spin Ride has a built-in benchmark that benchmarks the, the, the front, the middle and the end of the drive. He was getting on his Samsung eight 40 S S D 1 38, 4 45, and 56. Then he wrote, I seem to recall Steve saying you can run a spin right scan to regain the lost speeds. I tried level one and it did not improve. What should I do for SSDs? I noted the warning in the instructions about SSDs, so I didn't wanna go beyond level one without guidance. So, so first of all, spin right now notices if you are running at level, at any level that writes to, to, to the drive, and if it is an S s D or a shingled magnetic drive, you get an extra notice that, you know, writing is something you need to consider carefully with, with that particular device.
(01:19:31):
So anyway, I wrote back to Jim to explain that what's needed for s s D maintenance is a rewrite of the SSDs data. Because over time, and especially with repeated reading in the area, the disturbance caused by the reading of adjacent s s D media has been found to disturb the integrity of the SSD data. Anyone who does an internet search for the term read disturb will get an Eiffel Spin Rights. Level one is a read only pass. So what Jim needed to do was to run level two, which performs a read, followed by a right of the same data right back to the S S D. And you could optionally use level three, which follows that up with a final reread if you just wanted to be extra ca you know, extra safe. Although I don't think it's necessary. But I also explained that while it made sense to do this in what appeared to be an extreme case such as his, it should be done sparingly since writing very slightly fatigued SSDs.
(01:20:42):
So Jim replied the next day in the developer news group with his update, he wrote, thank you Steve and everyone else who chimed in, what a great group. The numbers after level three are now 5 64 across the board. He said, wow, Haba haba haba. So he went from 1 38, 4 45 and 56 megabytes per second to 564 megabytes per second by running a level two pass of spin right over his S S D. And what he experienced is what everyone has been seeing. His s s D was restored to brand new performance with spin right six one for now, rewriting the entire drive is the best I can offer, but this is one of the reasons I'm still willing to invest in developing what will be an entirely new spin. Right? Seven written from scratch under a new OS spin. Right? Seven will add what I call targeted rewriting to selectively write, re rewrite only those spots on the S S D that require it.
(01:21:57):
And this is not just for speed, speed is what you get, but it's every bit as much about storage reliability since the reason those regions are being read back more slowly is because their stored bits have been softened and have become less certain. So the SSDs media controller is having to work much harder to determine what was originally stored there. When you rewrite it freshly, it no longer has to work as hard. The data is is restored much more safely and and securely, and you get to read it back much quicker. So anyway, all of this means that much to my amazement spin right? Has every bit as much of a story to tell for solid state storage as it always had, has, has always has had for a spinning magnetic storage. Take a break before you get to the thing, right? Yep. You wanna get to the thing satellite and security.
(01:22:58):
I did wanna regarding this use of swap file on Windows 11. Yeah. for a long time historically, even if you had, you know, 10 gigabytes of ram, you would still want a swap file because Windows used it for other things besides just swapping out Ram Yes. When you ran outta memory. Yes. And I think with Windows 11, that is still the case. It uses it to at, at the it it uses it to, to store the system Ram dump during a a kernel fault. I if you crash it, it it will store that. Well, there is a swap file sis that also uses to sleep uwp apps. It uses it for other things. Then what we think of a swap file as is, as a little extra storage on the hard drive in case you run outta ram. And for a long time I've recommended, even if you had ample Ram not to have some, usually fixed size can be small swap file.
(01:23:56):
So I'm not sure not having a swap file is necessarily optimal. I'll have to ask Paul and see if he knows on Windows too many things. I'm, I I'm running well windows 10 without one, and I mean, the fact that I'm running Windows seven without one is less germane, but Windows 10 works great without it. Yeah, it's not that it won't work great, but it may not be working as well as you want it to. The other issue that I would say is you don't have to worry about an ssd. I've been using swap files and SSDs for ages. I, we, we, Mark Thompson did that test where in the earliest days of <laugh> swap files, he put it on an SSD and it burned it out quickly. But now I think modern the firmware on modern SSDs is, is good enough that I don't think you have to worry about burning out the ssd.
(01:24:42):
I've been running swap files on SSDs for Linux and Windows for years without any issues. So I'm gonna, I'll do a little more research into it, but I, I think it might actually be better for performance if you have a fixed size s s d, even if it's fairly small, not because of running out of ram, but for other uses that Windows puts it to, and they've changed it by the way. There's, there's the, there's, there's a new swap file si replacing the page file sis, they've got, it's all different. So I'm gonna check into that on Windows 11. I'll find out. Okay. And I don't think it's, I think it's harmless to do it on a swap file these days. Most people, that's a, an SSD almost. I, I will respectfully disagree with you. I really, I've, yep, absolutely. I would never write to SSD if I didn't have to. It is, it is really, it is, it, it fatigues it <laugh>, I think because of the where leveling they do these days that, I mean, you're right into it all the time anyway.
(01:25:37):
Ah, I don't like that either. I know you don't like it, but I think that it's not a problem. That's one for Alan Melvin, it seems, seems completely unnecessary to, to have a swap file if you've got lots of ram. Okay. Unless I'm wrong, so I'll check. I, I would just look, I defer to you in every respect on hard drives, but but it does sound counter to stuff I've been told before, so I will look into it just so people have that potential caveat. Our show today is brought to you by duo. Duo is awesome. Been using this for years. It protects against breaches with a leading access management suite. Strong multi-layered defensives and innovative capabilities only allow legitimate users in keep bad actors out. But one of the things DUO does that's so cool is they will raise or lower the requirements depending on the, the real time risks, which is fantastic because you know, you wanna have this high level of authentication without inconveniencing users.
(01:26:39):
And that's what DUO does so well. It quickly enables strong security, but improves users productivity as well. And if you're an organization that's concerned about being breached, you need duo. Duo prevents unauthorized access with multi-layered defenses. That's the key here. And modern capabilities that thwart sophisticated malicious access attempts. You can, as I said, increase authentication requirements in real time. When the risk rises, it's even automatic. DUO enables high productivity by only requiring authentication when it's needed. Enabling swift, easy and secure access. Duo d UO provides an all-in-one solution for strong mfa, for password lists, for single sign-on and trusted endpoint verification DUO helps you implement zero trust policies by verifying users and their devices. Start your free trial, sign up today, cs.co/twit. That's cs.co/twit duo is the best. Now on we go with the show. Let's talk about satellites. Yes. so we spent, as I said at the top of the show, we spent a lot of time looking at ground-based systems.
(01:27:57):
I mean, like virtually all of our time in the 18 plus years of this podcast, we've never looked to the sky well, unless it was to talk about aliens, of course. But just as our dependence upon ground-based fiber optic communications has crept forward, eh, kind of slowly, you know, a almost being unappreciated until we suddenly realize that we, you know, were unable to live without it. The same has been happening largely unseen, far above our heads in orbit. On March 1st of this year, Bloomberg posted a piece titled, how Do You Hack a Satellite? It had the subtitle inside the frighteningly Easy Form of Cyber Warfare. And Bloomberg wrote, it's Morning on February 24th, 2022. Ukraine has just been invaded, but you live halfway around the world. Your neighbor comes over to complain that their internet is out. Suddenly you lose connectivity. Could it be the Russians?
(01:29:01):
Unlikely as it might seem for a number of satellite internet customers, AV via Stat Inc. That's exactly what happened in a story in this week's business week, Bloomberg reporter Katrina Manson digs into the hack that disabled thousands of broadband users all over Europe. She writes across Europe and North Africa. Tens of thousands of internet connections in at least 13 countries were going dead. Some of the biggest service disruptions affected providers, big blue broadband PLC in the uk and NorNet, AB and France, as well as utility systems that monitor thousands of wind turbines. In Germany, the most critical affected Ukraine, several thousand satellite systems that President Vladimir Zelinsky government depended on were all down making it much tougher for the military and intelligence services to coordinate troop and drone movements in the hours after the invasion. So that's the end of their, of, of Bloomberg's quote, Bloomberg continues.
(01:30:06):
It turns out that satellite hacking is one of the bigger and less understood threats of cyber warfare. For many years, no one worried about someone hacking a satellite because, well, it was so hard to even launch a satellite. But in 1986, a man going by Captain Midnight jammed HBO's feeds because he was mad about paying a higher fee. There are a number of touchpoints that could be vulnerable to interference. You've got the orbiting satellite itself, it's transmitted data and the network of dishes on the ground sending and receiving information. So anyway, Bloomberg continues, but that gives us, you know, a little bit of a sense. So that's the commercial side, but what about gps and about our deep dependence upon space borne communications and surveillance technology for our national security and not just our national security, but you know, everyone's national security. What caught my eye, and first put this topic on my radar was a security research paper that was accepted for and recently presented during the 44th i e e e symposium on security and privacy.
(01:31:22):
In May, it was titled Space Odyssey, an experimental software security analysis of satellites. And as you might expect, since we're talking about it here, the news was not good. In fact, as you really might expect, it's downright horrifying. And we're talking and we're talking down at the firmware level that probably cannot be fixed from the ground. But seeing this reminded me of another recent news blurb that I had recalled. I found some coverage of that event in Newsweek with the headline, five Teams of hackers will compete to breach US satellite in space. And the subhead, protecting satellites from hacks is becoming more important as industries from agriculture to banking to insurance rely on space-based capabilities. Newsweek wrote this August at the famed Def Con Hacker Convention. The US military will stage a contest in which competing teams of white hat hackers will for the first time ever try to penetrate and take over computer systems on a satellite actually in orbit.
(01:32:42):
Steve Colenzo technology transfer lead for the Air Force re Research Laboratories Information Directorate in Rome, New York. And one of the contests organizers said it took four years, but this year we are in space for real. The hack asat for Capture the FLAG contest comes in the wake of the notorious cyber attack on the ViaSat Caat European Network satellite. Last year, the one we were just talking about, Russian military hackers sought to decapitate Ukrainian command and control of its armed forces by shutting down the network just as Russian invaders rolled across the border. Although there are conflicting reports about its impact on the fighting, the attack was completely effective From a technical perspective, every one of the ka SATs ground user terminals that was turned on at the time shut itself down and could not be powered back up. That plus the collateral damage the attack caused, such as the wind farms in Germany knocked offline underlined both the integral role in the world economy of space-based global communications networks and their vulnerability to hackers.
(01:34:05):
It also demonstrated the value of the annual Hack Asat contest, which aims to highlight the cyber threat created by space-based capabilities. Steve Col Colenzo said, we've turned a corner a lot more people now understand those threats. So today's podcast is part one of this important topic because I wanted to lay a bit more groundwork for the discussion of what this group of six serious German cybersecurity researchers discovered and reported in their I E E E paper. It's one thing, you know, to be unable to watch Seinfeld reruns, but entirely another, for a country to be deliberately blinded by its adversaries when it's most need of surveillance intelligence, it's very clear that the security of what's in orbit above is crucial to the physical, physical security of our lives we're leading down here on the ground. So I want to conclude part one of this examination today by sharing some background from the US Defense Department about the history and present status of the US' military satellite based presence. There's a lot more going on up above us than most of us know.
(01:35:33):
So they, so from the US Department of Defense, one tool, the US military has to gather intelligence on its adversaries is the reconnaissance satellite. Starting with the CIA's Corona program in the 1950s, the U the United States has employed orbiting satellites and high altitude aircraft to photograph points of interest in enemy territory. These tools allow for an immediate area to be surveyed from a safe distance, improving the efficiency of missions Throughout the Cold War overhead, reconnaissance satellites and spy planes brought attention to the US SR'S nuclear buildup in Cuba, helping the United States dispel Nikita Khrushchev's missile gap ploy. In the 1990s, the stealth plane F one 17 Nighthawk aided US missions in the Persian Gulf and Yugoslavia. More recently, overhead reconnaissance provided critical images of Osama bin Laden's, Abba ABBA compound. Much of the United States other overhead reconnaissance capabilities and missions are still classified and the portfolio will remain a critical aspect of the military's C4 ISSR apparatus.
(01:36:55):
The C4 stands for command control communications, computers, and the I SR is short for intelligence surveillance and reconnaissance. In addition to simply taking photographs, the military's nudist newest reconnaissance satellites use artificial intelligence to analyze and sort captured images. Once this process has gone through the satellite system, the sorted images are transmitted to ground stations on earth. Here, machine learning allows the stations to compare new images to a plethora of others in the station's database. The compiled images in the database act as a control group. And differences found in the new images, such as a new structure being built or a plane following an unusual flight pattern, are brought to the attention of decision makers. At the same time, new technology like the European space agencies, Fiat artificial intelligence chip allows satellites to quickly filter through images and discard the ones that are not useful. This capability is helpful when dealing with natural disruptions to captured images.
(01:38:08):
Cloud cover, for example, renders many images useless. With AI satellites can be programmed to recognize clouds and transmit only the cloud free images to earth saving military analysts valuable time, timely and reliable communication is a vital aspect of all US military missions. Over the past few decades, the United States has relied on four different satellite systems to fulfill this role. Efforts to create a military communications satellite first began, began in 1960. The first satellites were launched in June of 1966, and by July of 19 67 19, satellites made up the system then called the initial Defense Satellite Communication System, I D S C S. Data and photographs transmitted by the I D S C S system were first used in military operations during the Vietnam War. During this time, satellite technology improved in 1971. The first of 16 new satellites were launched under a new system called the Defense Satellite Communications System two DSCs, two advantages over the ds.
(01:39:26):
The I DSCs system included increased communications, privacy, and compatibility with ground portable units. The military's third system, DSCs three came after came under development in 1995. Between 1982 and 2003 14, satellites were launched as part of this network that is the DSCs three. Today, the US military relies on the wideband global SATCOM WGS Network. The Department of Defense ordered WGSS first two communication satellites in 2002, launching the first satellite in oh seven and providing communications coverage over the Pacific Ocean. Two years later, the second satellite was put into orbit expanding the communica, the communicative reach over the Middle East and Central Asia. Each W G s satellite is digitally channelized and transp. These characteristics provide a quantum leap in communications, capability connectivity, and flexibility for US military forces and international partners. Just one WGS satellite provides more SATCOM capability than the entire legacy defense satellite communication system.
(01:40:52):
Constellation WGS is an international system with Australia, Canada, Denmark, Luxembourg, the Netherlands, and New Zealand also investing in the satellite constellation. The System's 10th satellite was launched on March 15th, 2019, and an 11th is set to be completed by 2023. Looking forward, the Pentagon is already planning the next communication satellite system spearheaded by the recently created space development agency. The system will include development of deterrent capability, space, situational awareness, a resilient common ground-based space support infrastructure, command and control systems, and artificial intelligence enabled global surveillance. Additionally, the system is expected to be comprised of seven mission enhancing layers, including deterrence, navigation, and battle management. Another goal of this next program is to develop a net that has lower financial and security risks than his predecessors. In order to achieve this, the s D A is exploring the use of small smart satellites. While both the physical size and cost of satellites have decreased over the years, these smaller satellites are not yet equipped with features at the same level as those employed by larger satellites.
(01:42:28):
This shortfall, however, can be negated if a group of hundreds or thousands of small satellites we're talking, you know, swarm technology are launched as one network under this system. If one small satellite is damaged or knocked off course, the cost is minimal and the system as a whole will not suffer. The same cannot be said of the older, larger satellites. A damaged WGS satellite is costly, both in terms of financials. The 11th WGS satellite will cost the US government 605 million. So, you know, 0.6 billion and functionality of the current satellite network. That is, if one one of these big guys has knocked out, it hurts the functionality of the whole network. In order to make the small satellite plan reality defense. Advanced research projects agency, of course, DARPA created blackjack, a program designed to loft a network of 20 prototypes, small spy satellites to low earth orbit in 2021 if adopted into the FDA's future satellite network.
(01:43:42):
The Blackjack Pro prototype would first focus on surveillance and communication missions. However, there have been talks about broadening the scope to more complex assignments such as space-based battle management. Big satellites are big targets that if damaged have big and inimical consequences. While a future system will likely make use of small and smart satellites. The current W WGS network is comprised of 10, soon to be 11 large unprotected satellites, meaning adversaries need only damage one or two of them in order to dramatically disrupt the system. The biggest threats to W G S come from China and Russia. Both nations have ground-based anti-satellite weapons capable of destroying satellites in low earth orbit. Beyond that, Beijing and Moscow are currently developing what they call peaceful spacecraft. These machines are purportedly being made in order to quote, reduce the growing amount of orbiting debris and to refuel repair and refresh.
(01:44:56):
China's and Russia's existing fleet of satellites unquote designed with robotic arms. These machines can easily be utilized to remove parts from US satellites empty fuel and break antennae and solar panels. Someone in the know was quoted, quote, unlike ground-based missiles, designed to knock out orbiting satellites which give hours of warning before they can hit key targets in geosynchronous orbits. The satellite i e oh, I'm sorry, the spacecraft satellites China and Russia are developing, can destroy an intolerable number of our critical satellites with little or no or no warning. DARPA is currently building the United States own satellite repair machines once launched. These or similar machines could also serve as bodyguards for US satellites. With this defense, the W G S would be protected and able to serve the needs of the US military until the future s d a satellite network is completed. So we're talking bodyguard satellite robots up there to protect our, our low number of large, big satellites. Until we can bring high numbers of small swarm technology satellites into service. This continues we're near in the end. Another risk to current and future satellites is hacking carried out by foreign governments, non-state entities or even individual actors. Cyber attacks are relatively inexpensive endeavors. On top of that, tracing an a cyber attack back to its source often proves difficult, if not impossible. Dark readings. Robert Limos was quoted the importance of satellites make them a critical part of any nation's infrastructure and make attacking those satellites a strategy that most nations need to consider.
(01:47:13):
Over the past decade, both China and Russia have launched cyber attacks against US and NATO affiliated satellites. Because both nations are rapidly incorporating cyber attacks into their military arsenal, the threat of similar instances will only increase the information collected and transmitted by satellites is vital to the success of US military operations. 68% of U US munitions, for example, were guided u using space-based means during the US invasion of Iraq in 2003, 68%. On top of that, the US military relies heavily on GPS systems to move troops and supplies. In short, an effective cyber attack on a critical US satellite could have detrimental repercussions on the battlefield. In order to protect the satellites from hacking, the Pentagon should focus on risk reduction frameworks through communication networks and supply chains. Moreover, the United States needs to explore protective technology such as the Chinese development of ch of communications protected by quantum cryptography.
(01:48:28):
As cyber threats and capabilities continue to proliferate and evolve, so should the United States ability to deflect and counterattack. And this means shifting satellite protection of a central and that, and this means shifting satellite protection of a central priority of US c4, isr. So this concludes the first part of our two-part examination of satellite insecurity. Next week, we'll look at exactly what that team of German cybersecurity researchers found when they took a close look at the state of actually deployed satellites orbiting above us. And again, what was that? That Henny Penny said, <laugh> it's only only 300 shopping days left till Christmas. No, that wasn't. And Leo, apparently they can actually be knocked out of orbit. Wow. Yeah, I mean you, you can actually, oh, you use lasers, you can actu Oh no. I mean by hacking, by cyber hacking. Oh, by hacking them. Oh yeah.
(01:49:34):
You can drop a satellite out of Sure. I Back to ground. Yeah. Well, I look forward to part two of the show next Tuesday. We do the show every Tuesday at one 30 or 2:00 PM Pacific. That's four 30 Eastern 2030 utc. I say that cuz it is possible to watch us do it live at, if you want the very freshest version at Live twit tv. If you're watching Live Chat Live and IRC dot twit tv, of course Club twit members get special access to our really fun club Twit Discord. There are lots of special events there. And, you know, one time only things plus shows we put out that are not public, like hands on windows with Paul Thoro, HandsOn Macintosh with Micah Sergeant. We've got a fireside chat with rod Pyle coming up Thursday the 27th, a week from Thursday.
(01:50:25):
That should be fun. Of course, we do home theater geeks now in the club with Scott Wilkinson. And Ann is doing live photo critiques. He calls it Coffee Talk starting August 4th in the club. Stacey's book club is coming up as well. So lots of good stuff in the club. Twit Discord, add free versions of this show and all the shows we do special shows we don't put out anywhere else. And events that we don't put out, like our Friday night alcohol fueled party last Friday. Alcohol and ribs fueled, amp brought ribs. If you're interested, it helps us out a lot. Smooths out the bumps, the ups and downs in advertising. N none of it goes to me. It it all goes to keeping the lights on and keeping the show going. And our employees seven bucks a month. That's all it costs.
(01:51:14):
I think it's well worth it if you're interested. TWIT TV slash club twit. Now, of course we do make on-demand versions of the show available. It's a podcast after all. Ad supported Frida all at twit tv slash sn for security. Now Steve has his versions of it as well. 16 Kilobit audio 64 Kilobit audio plus the transcripts that he commissions. All of that's available at his website. Grc.Com. While you're there, check out Spin, right? The world's best mass storage, maintenance and recovery utility. It's currently 6 0 6 1 is just around the corner and you'll get a free upgrade the minute it comes out. So hurry on over to grc.com for that. You can leave feedback for Steve at grc.com/feedback. Or of course, as he mentioned on his Twitter at sg grc and his dms yes, are still open. SG GRC on Twitter. Let's see.
(01:52:13):
I think that's everything you need to know. There's a YouTube version of this show that's great for sharing little clips. You can, best thing to do really be subscribe. There's an RSS feed on Steve's site or our site. Either way subscribe and that way you'll get it automatically. Just find your favorite RSS reader or podcast player and enter in actually, if you could just search for security now and it'll, you'll find it. That's the easiest way. And you'll get it automatically every week. Thank you, Steve. Have a great week and we'll be back next Tuesday for another thrilling gripping edition of security. Yes, my friend, we've been around a while. We are well known by the search engines. Oh, by God, they, by now, they know who we are. And if they don't, they're just keeping their head in the sand. That's all. See you next week, my friend. Bye.
Jason Howell and Mikah Sargent (01:52:58):
It's midweek and you really wanna know even more about the world of technology. So you should check out Tech News Weekly. The show where we talk to and about the people making and breaking the tech news. It's the biggest news. We talk with the people writing the stories that you're probably reading. We also talk between ourselves about the stories that are getting us even more excited about tech News this week. So if you are excited, well then join us. Head to twit tv slash tnw to subscribe.