Security Now 928, Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Jason Howell (00:00:00):
Coming up next on security. Now Leo's off to Disneyland. So, I'm Jason Howell. I'm filling in for Leo today, joining Steve Gibson, who has all the words, actually a few very key security stories. One takes a look at what kind of security information can be gleaned from a tiny little l e d power light. You might think not a lot. I'm here to tell you you're wrong. So that's coming up. Also, this month's major cyber extortion attack. The move it maelstrom Steve goes into some intricate detail on that. Plus last week's patch Tuesday. And Steve has a major milestone to announce with spin. Right? All that more coming up next on Security Now podcasts you love
(00:00:46):
From people you trust. This is twit.
Jason Howell (00:00:54):
This is Security Now with Steve Gibson. Episode 928 recorded Tuesday, June 20th, 2023. The massive move it maelstrom. This episode of Security Now is brought to you by radda. Security professionals often undergo manual tasks of collecting evidence. With Drta, companies can complete audits, monitor controls, and expands security assurance efforts to scale. Say goodbye to manual evidence, collection and hello to automation. All done at drta speed. Visit drta.com/twit to get a demo and 10% off implementation. And by Duo. Duo protects against breaches with an leading access management suite, providing strong multi-layered defenses to only allow legitimate users in. For any organization concerned about being breached and needs a solution, fast Duo quickly enables strong security and improves user productivity. Visit cs.co/twit today for a free trial and by Collide, collide is a device trust solution that ensures that if a device isn't secure, it can't access your apps, it's zero trust for Okta.
(00:02:05):
Visit collide.com/security now and book a demo today. It's time for security. Now, I'm Jason Howell filling in for Leo LaPorte. I promise never to sing the theme song again. I'm sorry I did that right off the top. I have regrets here joining, of course, the man that you checked out this podcast for Steve Gibson. Let's talk all about security today. It's great to be here with you, Steve
Steve Gibson (00:02:28):
Jason, great to have you. This was a surprise to me, but apparently not to anybody else. So, you know, Leo, just sometimes on a, on a spur of the moment decides I'm gonna skip town and go to Disneyland. And that might sound like a joke. That's exactly what's happen. Oh, Keith, he ever done that before? No, I I I don't. I think this is the first in 18 plus years, but you know what the heck?
(00:02:49):
Hey, when you own a company for 18 years, you might as well have the ability to to take off. That's a good point. I I have done, I've done, I've done my own shares skipping out of my own company. So, so this week it, it was funny because cuz you got the show notes and you thought did I get like incomplete show notes? Is this like everything? It's like, well, yes, two big stories dominate our podcast. We start by taking a quick look back at just, just as this is not one of the big stories at last week's. Fortunately, it's not one of the big stories last week's Microsoft Patch Tuesday. But then we're gonna examine the latest surprising research to emerge from the Ben Guion University of the Negev. What these guys have found this time is startling. And I'll give a little more backstory when, when we get to that.
(00:03:42):
But then after sharing some feedback from our listeners and a long awaited big spin right milestone announcement, we're gonna spend the rest of our available time examining the story behind this month's massive cyber extortion attack. Or I'm not sure if you'd call it an attack or attacks, plural, because it's so big that it's been making all of the recent headlines and it's been causing our listeners to tweet to me things like, I'll bet I can guess what you're gonna be talking about this week. Mm-Hmm. <affirmative>, you probably get that all the time. <Laugh>, yes. Ah, that's, that's often pretty much pretty clear. Yeah. <laugh>. So anyway, I, I titled episode 9 28 for this June 20th titled it the Massive Move It Maelstrom because this is really bad. And so we'll spend some time looking at, at what happened, why it happened, how it happened, and what does it mean about the future.
(00:04:50):
All right, well, we've got a lot to look forward to. I'm super curious about that. The two big stories, oh, and of course we have a picture of the week, which I, you know, which I, if I sounded distracted is because I was looking at it, I was trying not to laugh in advance <laugh>, because, wonderful. Oh, that's pretty awesome. I do have questions about it though, but hold onto that thought all. We'll get back to it in a moment. But first, let's take a moment to thank the sponsor of this episode of Security. Now, this episode is brought to you by drta. Is your organization finding it difficult to collect manual evidence and achieve continuous compliance as it's growing, as it's scaling? Well, as a leader in cloud compliance software by G2 Drta streamlines your SOC two, your ISO 27,000 zero one, your PCI dss, gdpr, hipaa, how many other acronyms can I throw in there?
(00:05:39):
They do it all and other compliance frameworks as well, providing 24 hour continuous control monitoring. So you can focus on scaling securely with a suite of more than 75 integrations, DRTA easily integrates through applications such as aws. There's Azure, GitHub, Okta, CloudFlare, and countless security professionals from companies including Lemonade Notion and Bamboo hr. They've all shared how crucial it has been to actually have drta as a trusted partner in their compliance process working for them. You can expand security assurance efforts by using Theda platform that actually allows companies to see all of their controls and easily map them to compliance frameworks to gain immediate insight into that framework overlap wherever that happens to bera das automated dynamic policy templates, support companies new to compliance using integrated security awareness training programs, as well as automated reminders that actually make sure you have smooth o onboarding for employees.
(00:06:46):
That that goes very smoothly. And as the only player in the industry to build on a private database architecture, your data can never be accessed by anyone outside of your organization. All customers actually receive a team of compliance experts that includes a designated customer success manager and ADA's team of former auditors. They've conducted more than 500 audits, so your DDA team keeps you on track. Make sure that there are no surprises no barriers in front of you, plus ADA's, pre-audit calls actually prepare you for when your audits begin. ADA's Audit Hub is the solution to faster, more efficient audits. You can actually save hours of back and forth communication that way, never misplaced crucial evidence. That's important. You can share documentation instantly. All interactions, all data gathering can actually occur in ADA between you and your auditor. So you won't even have to switch between different tools or correspondence strategies.
(00:07:48):
And with ADA's risk management solution, you can manage end-to-end risk assessment and treatment workflows. So you can do things like flag risks, score them, and then once you have all that, you decide whether to accept, mitigate, transfer, or to avoid them, ADA maps appropriate controls to risks that simplifies risk management and automates the process. ADA's Trust Center actually provides real time transparency into security and compliance posture, which you know, goes a long way to improving sales security reviews, better relationships with customers and partners. So say goodbye to manual evidence collection, as I've spelled out here, it takes time, it takes resources. Say goodbye to all that and hello to Automated compliance by visiting drta.com/twit. That's D R A T arata.com/twit, bringing automation to compliance at ADA speed. And we thank them for their support of security now. And we can finally talk about the picture of the week, which had me kind of stopping my tracks a few minutes ago, just trying to figure this out.
(00:08:56):
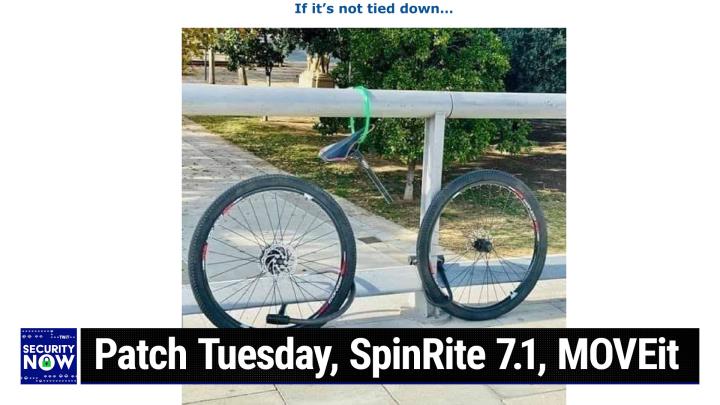
But tell tell the audience about it first. Okay, so there's a little bit, there's a little bit of backstory since you're not always the host of the podcast. Sure. there, there was ano, there was an earlier famous bicycle lockup picture of the week where, which really made you wonder because they had locked their bicycle with a big secur, he heavy security band to a post that had nothing on the top of it. <Laugh>. I mean, it was just a post. So I love that if anyone had wanted the bicycle, they could have just lifted it off of the post. Yeah, sure. You know, I mean, lifted the lock off. Anyway, so this one is great and I'm sure one of, well, one, one of our listeners did send it to me knowing that we have an, an affection for, you know, wacky pictures.
(00:09:47):
I, I gave this the caption, if it's not tied down, because what if we believe this and, you know, I mean, this could obviously be set up, but still it's great. Somebody really, really, really wanted to lock up their bicycle. So they had this, this seriously strong, you know, metal steel gate that has a bar running along the bottom and one running along the top. And so they used those U-shaped, you know, strong bicycle locks through, through, through both the front tire and the back tire. One each looped around this steel rail that runs along the bottom and just, I mean, that would, you know, you would imagine that would be enough, but they figured, no, no, I wanna, I wanna also, you know, lock something else. And since there's a a bar running across the top, they thought, well, I'll, I'll run another security cable underneath the seat through the, the, the, the, the metal mounting of the seat to, you know, further lock down the top of the bike.
(00:10:59):
What we see in this picture is exactly those three things and only those three things. Someone stole the bike out from, like the chassis out from the three things that were locked down. The frame is gone. No more frame, the frame is completely, the frame is gone. There's just a front tire and a back tire, right? Where they always were locked rigidly to the lower rail and a seat hanging from the upper security cable on, on, on, on the top rail and nothing in between. So the <laugh>, those three pieces are disconnected from each other because as, because yes, the frame of the bicycle apparently someone thought, okay, I'll show you and it's gone. So I, I guess, I guess things could have been worse. You could have lost the whole bike instead, you just lost the frame. I'm looking at it. And so what confused me earlier was when I was looking at the seat, it kinda looked at me like the seat was just hanging on the loop.
(00:11:57):
But what I realized as I look further there is kind of like a metal thing underneath the seat that it's going through. So that seat isn't going anywhere. Correct. I'm, I'm curious to know, like, what's the most expensive, and maybe I'm thinking too deeply into this. What's the most expensive part of a bike? Is it the frame? Is it the tires in the seat? Because if it's the frame, I mean, you know, whoever took that bike obviously knew what they were doing. They were like, well, still, I mean, I realize they don't want me to take this, but I can. And that still works. Something. Now I can offer some guidance, Jason, about our pictures, about our pictures of the week. Yeah, don't think too deeply. It is not possible. It is not possible to think too deeply about them. Okay. Leo and I have sometimes spent a good half hour on why is there a, why is there a gate in the middle of this field?
(00:12:43):
Yeah, that's, that's good. So you don't have to worry about overthinking this or, or thinking, you know, like going in too deep. No, I don't think it's possible to go too deep into any of this podcast's. Pictures of the week <laugh>. Fortunately it's not possible to go too deep into last week's Microsoft Patch Tuesday this being the third Tuesday of the month, we're able to look back on last week's patch Tuesday. It's still to me somewhat astonishing that just last week Microsoft Patched 26 remote code execution vulnerabilities. You know, there, you know, when Leo proposed this podcast to me, I didn't have any idea that we'd still be going strong after 18 plus years. There's no sign similarly that Microsoft is ever gonna run out of serious vulnerabilities. The, the only thing, the only way to explain this is that their, you know, everything they do is creating new ones.
(00:13:46):
And so they're fixing some of the old ones, but at the same time, creating new ones to be found in the future. So, similarly, I don't think we're in any danger, Microsoft running out of serious vulnerabilities. Four of these 26 rce remote code execution problems were critical, and three of those four were spotted and fixed in a single Windows component noted as pgm. That's the pragmatic general multicast queue because you know, the thing you really want from your general multicast cues is pragmatism. What you don't want from them is remote code execution flaws, especially when they're bearing a C V S S score of 9.8. So after applying last Tuesday's patches for the time being, there will be three fewer CEEs, which probably makes the decision to use the queuing API in the first place. Somewhat more pragmatic. So that's good. There were also 17 elevation of privileged problems fixed, only one of which made it to the critical list.
(00:14:57):
W it had a c v s score, however, of a whopping 9.8, which, you know, I think maybe we've seen a 10 once or something. You got, it's gotta be, you know, the really bad ones are 9.8 and they save the nine point nines and the 10 point ohs for like the end of the world. So, you know, we've only had the end of the world happen, I think once before anyway. If exploited an attacker could gain administrative privileges on, you know, as a consequence of one of the 17 elevation and privilege problems, Microsoft wrote an attacker who has gained access to spoofed. Jason, that's not you, Jason, that's j s o n Web token authentication tokens could use them to execute a network attack, which bypasses authentication and allows them to gain access to the privileges of, of an authenticated user.
(00:15:53):
The attacker needs no privileges, nor does the user need to perform any action. Now, since we're talking about, and I didn't mention this yet, the SharePoint server, which is the same sort of database sharing that has landed the move it transfer software, which we'll be talking about as in the second half of this podcast into such hot water later this month or in into such hot hot water earlier this month. Getting that one patched to something that should probably not be put off, especially given that it's a 9.8. You know, Microsoft is saying, yes, we're glad we fixed this and we're gonna try to not to create anymore. Overall of the 73 flaws fixed eight, I'm sorry, six are rated critical, 63 are important, two are moderate severity, and one is low. So included within that group are three issues, which were fixed in the Edge browser.
(00:16:52):
It's worth noting that during the intervening month between last month's patches and this month's, Microsoft did also eliminate 26 other flaws in edge, including among those a zero day, which Google last week disclosed, which was being actively exploited in the wild. So that's fixed. But this month is the first time in several months when none of the known and patched problems were either publicly known or under attack at the time of their fixes. So that's good. And, and we mentioned both publicly known or under attack, because Microsoft has their own definition of, of zero day. Everybody else considers a zero day to be one where it's first learned about because it's spotted being used in an attack. Microsoft broadens that to say if so, if, if there's, if they're informed of something they didn't already know about, then it's a zero day, which I don't know, seems overly pessimistic to me. But anyway, we didn't have any. The final note is that two of the remaining mo mo code, remote code execution vulnerabilities were found in fixed in exchange server. Being that exchange server is all about exchanging content with the outside world, it's generally a significant portion of an enterprise's attack surface. So absolutely want to get that fixed. Okay, so that I got that little bit of housekeeping outta the way.
(00:18:28):
Next is one of two big pieces of amazing stuff. I, I titled this, does everything in all Caps leak. This next bit of jarring news leads me to pose that question, you know, does everything leak? As in leaking information, a couple of days ago, I received a Twitter DM from Ben nai, Ben Tweeted, hi Steve. My name is Ben nai, a postdoctoral researcher at Cornell Tech and a longtime listener of security. Now, I just published a new research that I think you should see. We recovered cryptographic keys from devices by obtaining video footage of their power l e The devices were not compromised, meaning ahead of time. He says the research will be presented at Black Hat and Def Con this year. And then he sent me a link to their research pdf. Okay, so the is approaching with Black Hat and Def Con being held back to back every summer, as we know in Las Vegas, Nevada.
(00:19:53):
Ben also sent a link, as I said to the research paper, which is titled Video Based Crypto Analysis, extracting cryptographic keys from video footage of A devices power l e d. That is crazy. And I could still hardly believe this even as I'm reading it now, I can't believe that that's, that's pretty insane. I'm super curious to hear, but you're, you're gonna love the details. So first of all again, because you're not always the, the host of the podcast, the, my mentioning the Ben Guion, university of the Negev may not like ring any bells for you. It does for our listeners, Ben is one of the prolific researchers there who have for years brought us an unending stream of often entertaining, but also often sobering, extremely clever examples of data exfiltration. Our longtime listeners will recall, for example, their work with extracting audible conversations from a room at a distance by visually detecting the sympathetic vibrations induced in a birthday party balloon, the leaf of a plant or a light bulb, all of which allowed them to recover the audio, filling the rooms occupied by those objects.
(00:21:22):
I mean, and they've done all kinds of things. Wow, that's amazing. I think, yes, well, it, it's just incredible. We, we should label, we, we could safely label these guys the masters of the detection and recovery of side channel in information leakage. And so now we have another, and whereas some of their schemes have required malware to first be installed in the victim device, which is why he was careful in his tweet to me to point out, not this time you know, like for example, they've deliberately changed the sound being emitted by a machine's power supply and use that for remote signaling or changing the system's fan speed in order to signal an air gapped microphone. You know, and, and for example, when they do that, they just, it's easy to say, oh, change the system's fan speed in order to signal an air, an air gap microphone.
(00:22:24):
When they do this though, they look at how long it takes for the speed to change when they change it, and how many dis discrete levels of speed they can make distinguishable by a microphone at what distance, because the number of levels and the speed it takes to get to among each level determines the bit rate at which they're able to send in. I mean, these guys wrestle this stuff to the ground all the way every time. So, okay, in, in order to put myself in the same place as our listeners, as I share this, I have not yet even glanced at Ben's paper. Now, I have now because I've wr I wrote the, I wrote the show notes, but as I was writing the show notes, as I was first putting this down, I had not opened the paper. So we're gonna do that together in a moment when I share the paper's abstract, which as I said, I have not yet seen as I'm writing this.
(00:23:33):
But what we immediately and intriguingly ascertain from Ben's tweet is that astonishingly variations, and, and again, this, we're deriving this from everything we've learned over 18 years of the podcast, right? Variations in the work being done inside devices where that work is dependent upon cryptographic secrets must be sufficient to produce tiny variations in the power being supplied to such a devices l e d power indicator. Now that's surprising enough that any such fluctuations would be so tiny as to be detectable and that they're theoretically detectable at a distance by a standard video system or, you know, you know, despite the, the depth of digitizing resolution, the effects of video compression or the, or the frame rate of the video, right, which is gonna be limited, but to do what they've done, Ben's group apparently overcame all of these practical barriers, you know, and they've done this before, so, and they're presenting this at Black Hat and Defcon, so, yeah.
(00:25:09):
And as I've observed in the past of their work, what really distinguishes their accomplishments is that they solve the whole problem. They just, they just, you know, the, the, the headline on the paper tells you where they're headed, but where they go is typically amazing. Okay, so now let's discover together what Ben's group explains at the start of their paper. They write, in this paper, we present video based crypto analysis. A new method used to recover secret keys from a device. By analyzing video footage of a device's power l e d, we show that cryptographic computations performed by the C P U changed the power consumption of the device, which affects the brightness of the device's power, l e d Based on this observation, we show how attackers can exploit commercial video cameras, and they says, for example, an iPhone thirteens camera or internet connected security camera to recover secret keys from devices.
(00:26:25):
This is done by obtaining video footage of a device's power l e d, in which the frame is filled with the power l e d and exploiting the video cameras rolling shutter to increase the sampling rate by three orders of magnitude from the frames per second rate of 60 measurements per second to the rolling shutter speed of 60,000 measurements per second in the iPhone 13 promax. Okay, so I'm gonna pause here for a minute and say, that's brilliant with an L e D. Even if the illumination across the surface of the l e D is not perfectly uniform, as in fact they aren't being a solid state illuminator, any change in illumination will be uniform and effectively instantaneous. So this is the key that allows them to obtain a sufficiently high effective sampling rate from an otherwise grossly insufficient 60 frames per second video recording.
(00:27:45):
So continuing, they said the frames of the video footage of the devices power l e d are analyzed in R G B space and the associated Rrgb values are used to recover the secret key by inducing and, and I'm sure that's a typo, they meant deucing the power consumption of the device from the rrgb values. Okay, now pausing again for a moment. We long ago talked about variations in power consumption during cryptographic operations being a well understood side channel that could theoretically be used to reverse engineer the work being done by a device when that work is a function of secret data. But the presumption has been that, that that theory runs smack up against reality when there's no practical way to obtain instantaneous power consumption measurements without hooking deeply into the target devices electronics. These guys have quite cleverly solved the problem of doing that.
(00:29:00):
They realized that minute variations in the devices power draw would induce tiny changes in the systems supply voltage. The instantaneous brightness of an L E D is determined by the instantaneous current flowing through it. Leds will invariably have a resistor in series with them to set their operating current at the given supply voltage, but that current is not otherwise regulated, and that means that any variation in the system's total supply voltage will create a variation in the LED's current, and therefore in its illumination. I'm still surprised this works, but apparently it does. And you have to imagine that the world's intelligence services have just perked up in response to this news. So they, they finished their, their abstract saying, we demonstrate the application of video-based crypto analysis by performing two side channel crypt analytic timing attacks and recover. First a 2 56 bit elliptic curve.
(00:30:21):
D s a key from a smart card by analyzing video footage of the power l e d of a smart card reader via a hijacked internet connected security camera located 16 meters away from the smart card reader and two a 3 78 bit S I K E key from a Samsung Galaxy S eight by analyzing, get this video footage of the power l e d of Logitech Z one 20 USB speakers that were connected to the same U S B hub that was used to charge the Galaxy S eight via an iPhone 13 pro max. Finally, we discuss countermeasures limitations and the future of video-based crypto analysis in light of the expected improvements in video camera specifications. <Laugh>, oh my Lord. Okay. Okay, so before I go any further, I'll just mention like, in terms of extending this, now that we know that lights are flickering or just barely changing their illumination the light pen, which I developed back in 1983 for the Apple two had a response time of 140 nanoseconds because that was the pixel clock rate of the Apple Twos video.
(00:32:03):
140 nanoseconds is a rate of 7.14 megahertz. Now, that happens to be twice the NTSC color burst frequency of good old NTSC video back then, and that was part of W'S design brilliance for the Apple two. Okay, but my point is, since monitoring the power l e d of devices that are performing secret computations has now been proven by these guys to work, it would be trivial to take the technology of a high performance light pen, place its photo diode at the user end of a telescope and aim that scope at any power, l e d of any device containing c secrets to begin collecting data. The data gathering and secret gathering power of such a system with seven megahertz bandwidth with is somewhat terrifying. Okay? So while it would be possible to create a highly sophisticated spying scope, the brilliance of what these guys have discovered and and invented is the ability to use existing camera technologies off the shelf tech, thanks to their observation that the cameras in our devices do not actually snap an entire scene at once.
(00:33:36):
Instead, they actually scan the image from top to bottom or left to right in much the same way that the images in our original cathode ray tubes did. This brilliantly allows them to sample the illumination of a device's l e d with far greater temporal resolution than the camera's overall frame rate. Here's how Ben's paper describes it under the title, increasing a video camera's sampling rate using a rolling shutter. They wrote, we note that the fps, you know, frames per second rate supported by the vast majority of commercial smartphones and security slash IP video cameras is limited to 60 to 120 frames per second, which is sufficient for performing cryptoanalysis in order to increase the number of measurements per second sampling rate to a level sufficient, oh, I'm sorry, I, I I hope I I said 60 to 120 frames per second, which is in insufficient for performing cryptoanalysis.
(00:34:52):
Of course, that's just not enough. I mean, it's the, the, the computations happening inside are way faster than that, so that's not gonna cut it. So they said in order to increase the number of measurements per second, the sampling rate to a level sufficient for cryptoanalysis, the attacker can exploit the video camera's rolling shutter. The rolling shutter is an image capturing method in which a frame of a video in video footage is captured by scanning the scene vertically or horizontally. When this method is used, a frame per picture is not actually composed of a single snapshot of a scene taken at a specific point in time, but rather is composed of multiple snapshots taken of vertical or horizontal slices of the scene at different times With a vertical rolling shutter, a sensor's pixels are exposed and red out row by row sequentially at different times from top to bottom or left to right according to a configurable shutter speed, which determines the amount of time that the sensor is exposed to light.
(00:36:15):
Because each row, or a group of adjacent rows in a sensor with a rolling shutter is captured at a different time. Attackers can increase the effective sampling rate from the cameras frame per second rate of a hundred of 60 or 120 frames per second to the rate at which rolls rows are recorded a rate, which is based on the shutter speed. Okay. So, wow. The biggest limitation is that for this clever rolling shutter rate up sampling to work the LED's image, as I, as I briefly touched on at the start, the, but the LED's image must fill the entire camera frame, right? Because you want all of the individual row or line samples to be of the L e D. So it can't be just a tiny spot in the middle of the camera, you gotta zoom the camera in so that the LED's light fills its camera sensor.
(00:37:25):
But there are tiny external lenses that can be added to a smartphone to make that easier. And there are doubtless many applications where the installation of a device such as a smart card reader is made with the inherent assumption that its internal secret cryptographic computations are not being broadcast outside of the device. Ben's latest work has amazingly enough shown the world that this longstanding assumption has always been wrong. You know, we've often commented about the fact that the, you know, the internet activity, LEDs, which are ubiquitous on all networking equipment, routers and switches and everything, do not reveal anything about the data that's passing through their interfaces. Well, it turns out we've been looking at the wrong l e d I'm thinking of the phones that I've had, and of which I've had a lot over the years. And how many of them have some sort of an l e d light?
(00:38:34):
Like that used to be a really common thing. It used to be, you know, used for like notifications or whatever, and if you plugged it into charge that little l e d would light up. But I, I don't feel like I see that as much anymore. So at least there's that obscurity element on phones, let alone other devices, correct? Yeah. Correct. Yeah. on, on phones and in fact, one, and as I mentioned in one, in one of their documented attacks, they, they, they put a phone virtually on the l e d of a smart card reader while it is scanning the SMART card, ah, and <laugh> and, and, and all, and they, and they don't have to process it at the time, right? So all they have to do is they just turn the recorder on. Yeah, just capture, and they're just, they're just recording the, the, the, the, the video while the smart card gets scanned, and they're able to get the private key of that smart card.
(00:39:30):
Yeah. Wow. Oh goodness. That is how, how smart are people that they can be like, well, I wonder, you know, I have a hunch, and they look into it and they're able to figure this out. I'm, I'm in awe of the ability to do that. Yeah, this was a, this was a beautiful piece of work. So, Ben, I know you're listening. Congratulations. Wow. Wow, that's a big deal. Just fabulous piece of work. Jason, let's tell our listeners what is supporting this podcast? Well, indeed, we shall we'll take a break here and then we will get to, I think we've got some closing the loop coming up here shortly. But first, let's thank the sponsor of this episode of Security. Now, this episode is brought to you by duo. Duo protects against breaches with a leading access management suite, strong multi-layered defenses, innovative capabilities.
(00:40:22):
They only allow legitimate users in and keep bad actors out for any organization concerned about being breached that needs protection fast, while DUO quickly enables strong security, while also improving user productivity. Duo actually prevents unauthorized access with multi-layered defenses and modern capabilities that thwart sophisticated malicious access attempts. And you can increase authentication requirements in real time when risk rises. That's what duo's all about. Duo enables high productivity by only requiring authentication when it's actually needed, that enables swift, easy and secure access. As a result, DUO provides an all-in-one solution for strong mfa, passwordless, single sign-on and trusted endpoint verification. And Duo helps you implement zero trust principles by verifying users and their devices. And you can start your free trial right now. You can sign up today, just go to cs.co/twit. And you know, when you sound it out, it kinda sounds like Cisco slash twit, but spell it out, cs.co/twit, check it out for yourself.
(00:41:39):
Super cool stuff. We thank them for their support. Thank duo for their support of security. Now, all right, back to you, Steve, with closing the loop. Lot of lot of feedback today. Yeah. So ke Kevin tweeting from Sharpest Marble mm-hmm. <Affirmative>, he said, listening to security now 9 27, and you're praising Apple for live voicemail, which they're going to be developing, but this is something Google phones have had for over a year now. And Jason, as I said before we began, I was glad to have you here, says, you know, Android and I don't <laugh>, so, so is it all Android phones or Google Pixel devices? Well, I mean, you know, like Samsung, yeah, yeah, definitely. Samsung has the ability to do it to, I'm not sure if they're tapping into the same thing that Google can do, but the visual voicemail, transcribing voicemail that comes in, definitely Google.
(00:42:36):
I mean, Google's had Google Voice technology for more than a decade. I don't even know when Google Voice, you know, was, was bought by, by Google. It was Grand Central prior to that. And it's somewhere along the line, they started to automatically transcribe the voicemails. And I think that was kind of the beginning. If, if I'm not mistaken, the beginning of Google's kind of experience in doing this live transcription of these voicemails, and they get definitely got better with it over time. And then that feature has expanded outside of just voicemails into, you know, there's a, there's a feature that I was telling you about prior to the show that's embedded into the volume rocker on, on pixel devices and some other Android phones. And it is basically a live transcribe of any audio that's passing through the phone. So that could be a video you're watching that could be the music, you know, if there's any speaking in music, it would transcribe that.
(00:43:27):
The phone, phone call, all of this stuff is transcribed in a little closed caption box that you can drag anywhere on the screen. Google's gotten cool, really, really good at it, and it's one of, one of my major, my favorite kind of innovative features that Google's integrated in recent years. But yeah, Google's solid on this stuff, and it keeps getting cool, Kevin, thank you Kevin for letting me know so we can also, you know, give credit where it's due. Not a great innovation Apple, but you're catching up with it. They're all borrowing from each other. They, you know, yeah. One side we'll get, we will get an i a great idea and they'll implement it, and then suddenly that becomes table stakes. You know, it's, they all have, was was Apple the first fingerprint reader? I think Apple had the first fingerprint reader, so could, could be <laugh>, obviously, off the top of my head, I can't remember.
(00:44:12):
But, you know, they, they all borrow from each other, so, yeah. So Vincent, Stacy, he said, think Apple could use the same on iPhone technology protecting children from unwanted images to catch and analyze the iMessage vulnerability. So a couple weeks ago, we talked about a an iMessage vulnerability, which was probably impossible to catch because the end-to-end encryption protected the contents of the message, which once it launched, malware deleted the attachment, which the, which iMessage brought along with it, thus, thus removing all of its fingerprints you know, of, of, of the attack. And so I made the point back then the observation that, that the same really strong encryption, which is protecting the u the content of, of Apple's iOS and iMessage. User messaging is also protecting the bad guys who have an exploit that you know of something in the system if it deletes itself, how are they ever, how's ever anyone ever gonna be able to analyze it cryptographically or, or forensically Anyway in answer to Vincent's question, I suspect that it, the same technology won't be useful because one aspect which is scanning for unwanted material is within the bounds of normal operation, while the operation of this malware is explicitly out of bounds.
(00:45:44):
The trouble with catching it is that whatever it is that the iMessage vulnerability is doing, it's breaking what are supposedly unbreakable rules. It is somehow escaping from within the rigid controls and sandboxing that Apple has explicitly and deliberately erected around it to contain and neuter exactly such exploits. We know only that the malicious iMessage is bringing along an attachment. The fact that this is a zero click exploit means that for the benefit of its user, iOS must be automatically attempting to render whatever it is that iMessage has brought along with it, and that it is during this auto rendering that iOS loses control. So, you know, it, it's, it's, it's breaking the rules that iOS is using. So I can't see how iOS attempting to analyze it within the, the bounds of the rules would, would succeed. Okay? But having said that, if iOS were somehow able to record all iMessage attachments you know, before performing any processing of the attachment, and that was in an immutable audit log on the target device, which could not be being immutable, that log could not be, could not have anything deleted, even if the attachment were deleted, the record of it would, would be preserved then if a target, if a target device was to be compromised.
(00:47:35):
And if that compromised was recognized, then it would seem possible for a forensic analysis after the fact to be made. You know, this, this theoretical immutable log would need to be immutable even to apple's own software, right? Because if not, then malware running as Apple's software could delete it. But if there was something which once written, no, you know, no, no software running in an iOS device could erase it, then, you know it's certainly feasible, you know, given all the other preconditions. You know, one of the problems is that, that, that the target needs to know that they've been a victim. Probably often they don't. And if they knew it, then they would have to know that they could take their phone to someone and say, Hey, I've been victimized, you know, I need the immutable log of, of, you know, the forensic immutable forensics log, which we would then all know that iOS devices had to be analyzed.
(00:48:42):
And that's a problem too, right? Because that would say that every attachment was being recorded by the iPhone, and a lot of people don't want that. So probably in a good way to to solve this problem, unfortunately Jason Egan said, Hey, Steve, after hearing about the GRC SC situation, and please forgive me if I'm late to giving this, this option, he said, I wondered if you couldn't just solve the problem with a rewrite rule on your host. I've had to do this in the past with some of my projects. Okay, now, so just to remind everyone, what Jason's talking about is on episode nine 9 26 2, 2 weeks ago I, I ended the podcast with a, a shortcut of the week GRC SC slash 9 26, you know, sc as in shortcut, right? And then the next week I commented Mr.
(00:49:48):
Linux 11 wrote saying, Hey, I, I tried to use that, but I'm getting a page not found. It turned out that he was using www grc.sc, and so something had added www in front of the, you know, unencumbered simple grc.sc and broken it. So now Jason is saying you could do a rewrite rule, okay? As I mentioned in the past well, okay, so first, so, so he's, he's saying that I could, I could solve the problem with a rewrite rule if my DNS included star GRC sc in addition to grc.sc, but, and, and that's true. It never occurred to me that anyone would stick an arbitrary www.infrontofgrc.sc. As I've mentioned before, I do have a star.grc.com in my DNS since that's able to handle all of the many prefixes that fix that I use, like www dot forums, dot dev dot squirrel, and whatever else.grc.com.
(00:51:16):
And I do redirect any other wayward queries over to www.grc.com. Many years ago, GRCs web servers accepted connections on either grc.com or www.grc.com. Now, I figured why not? But then we noticed that Google's search results were coming up with a mixture of either grc.com and then whatever, U R L or www.grc.com and whatever U R L Google was seeing these as separate distinct websites and indexing them as separate websites. And people were linking to GRC somewhat arbitrarily as either grc.com or www.grc.com. And that was having the unintended side effect of reducing our Google page ranking by diluting the number of incoming links among both sites, what Google thought was two different sites. So I changed GRCs Web server to redirect you by returning an HTTP 3 0 1 redirect from any plain grc.com over to www.grc.com. And Google Spiders quickly learned that this was a single site which could yes, be accessed by two different domains, but they all brought you to www.grc.com, and then that consolidated all the links around a single domain.
(00:52:57):
And that worked at the time. I had to choose one or the other, and I'm really not sure that I did the right thing by choosing the longer www.grc.com, you know, as the enforced default. You know, yes, it's technically more accurate of the two, but you know, whenever I or anyone talks about grc.com, we say grc.com, not www dot grc com, and I'm sure everyone just enters grc.com into their URL bar whenever they want to visit. So anyway in the next tweet, the answer to how this www.grc.sc came about was provided a guy tweeting as CPU U Guru, he said, I found the source of the errant www that you discussed in the podcast. The hyperlink in the 9 26 P D F actually includes it. So first of all, thank you c CPU guru, good observation. And it was Google Docs that did this.
(00:54:12):
I typed in grc.sc and so know slash 9 26 and hit enter. All I saw was GRC sc slash 9 26. But sure enough, if you hover your mouse over that link, there's a www.in front of it, which Google Docs silently added, which I didn't ask for. So anybody who clicked the link in the docs as I invited them to, I mean, I made it bold and increased the font size saying, here, click me. That didn't work. Thanks to Google Docs. Jose Javier Vegas tweeted, hi, Steve, regarding SN 9 27. So that was last week. He said, there's no official let's encrypt client today. They transferred their implementation to the e f, and it's now called Certbot, which is the only one they recommended. So thank you, Jose. That's good to know. I am still issuing certs for my own servers the fashioned way through my sa, my my favorite certificate authority DigiCert.
(00:55:23):
But assuming that the world is going to switch as has been proposed to 90 day maximum life certificates, I'm glad that DigiCert also supports the ACME protocol. And I will certainly then need to find automation for this as will pretty much everyone, because nobody wants to be generating new certs every three months. That's way burdensome. And finally Michael Horowitz tweeting from his defensive computing Twitter account. He said, Steve, an FYI about HP plus printers, he said, they must be online all the time, even if connected to a PC via U S B, and you must have an HP account. He says, perfect for spying details on this page. And he sent a link. Michael has a bunch of really great pages. This one is at the domain defensive computing checklist.com. And so it's defensive computing checklist.com/printers.php. And it's interesting that it's php because as we'll be, we'll be talking about URLs ending in scriptable languages not long from now.
(00:56:48):
And so there was a perfect example of printers php, where that's actually running a PHP script, which is then pulling the contents of the page from some sort of csm, you know content or c CMS con content management system. Anyway, the first line of Michael's printers page reads, I hate printers, so too does Leo LaPorte, who is known as the tech guy on the radio. He will not take phone calls about printers. So that's <laugh>, that's Michael's lead in to his page about printers. I read through some of what Michael wrote on that page, and I recommend it to any of our listeners who may be curious to know more and who might be in the market for a printer. Michael has collected many reviews and anecdotes, and he tells a horror story of spending half a day trying to install an HB printer scanner for a friend.
(00:57:51):
Mind you, Michael knows his way around PCs as well as any of us, yet he repeatedly hit wall after wall just trying to like, play by the rules and install HP software. At one point, he, me mentioned that he downloaded the first package, which was 310 megabytes, which again, 0.3 gig for, for printer software. Anyway, his experience further supported my earlier statements when we were talking about this, this debacle with, with the HP printers that I have long found HP's software to be unconscionably atrocious. It is just the worst and and short version. Apparently, brother makes the, the printer that most people recommend and have no problems with. I think it's brother. Yeah, it is brother. It's funny that you even mentioned this because I've been going through was, it's not an HP printer, but it's an a Epson printer at home that we've had this Epson inkjet forever, and this is the third time that I've had to take it apart and try and repair it and get it back to working and everything.
(00:59:00):
And it didn't go back together. The way <laugh> the way I expected it to, I was like, you know what? I, I'm done. Like, I actually just just talked to Leo when he came in today. I was like, what? Send me the make and model. He's like, it's brother. It's a laser jet printer. He's like, get it. You won't need another printer. Like it's, that's just the way it's, that's that's exactly the same conclusion that Michael came to. Yeah, so I'm getting, I don't know which one it is. I have to look up the model number and get it from him, but we're, I'm, I'm not gonna look back. I'm just gonna do that. So, yeah, good. Yeah, and all printer software sucks. It's just so bad. It's just, oh, what, what happened? I don't know. It's just like, it's such a simple thing to do.
(00:59:35):
Totally. You would think, but it's just always horrible. That's been my experience. Anyways. Okay, so finally it is with no small amount of pride, a feeling of accomplishment and some pent up relief that I can finally assert that as far as I know, the work on the business end of spin, right? 6.1, which is its DOS executable side is finished there, are there presently no remaining known bugs, great or small, last Sunday afternoon. So two days ago I announced the availability of the al the 29th alpha release to GRCs 696, but I noted we just got one more. So now we're at 697 registered spin, right? Six owners who have been testing 6.1 for like, since we began the Alphas in November of last year. And I suggested for the first time to the group that the code we all now have would likely and certainly could with probably very few remaining changes be moved into beta status to soon become spin, right?
(01:00:51):
Six ones. Shipping code six one contains a great many new features. One of them being an integrated faq, which explains the choice of spin rights five redefined operating levels. It's many command line options and a bunch of other useful tidbits, sort of, you know power user tips and, and, and things that we've discovered and things to try and so forth. So while the dust settles on this latest alpha, I'm currently writing that faq that that'll give some time for any testers who may have become bored with the seemingly endless interim development releases to give this proposed final code. One last check. Once we had the finished dos code, that code, along with the very first work I did on the project, which was to create GRCs and disc usb drive prep utility, all of that'll be integrated into an updated spin right Windows app, and then we'll have 6.1, any new purchasers of spin right, will automatically then begin receiving six one.
(01:02:07):
But since I wanna let all of this new code breathe a bit, you know, like any nice red wine that you open, give it a little time to breathe, it'll mellow. I plan to hold off on announcing it to all of spin right's past purchasers until it's had a bit more time among a wider audience. So as soon as the official upgrade path is established, I'll be inviting all of this podcast listeners, many of whom have previously purchased spin right to update to six one. Then once it appears that it's gonna be clear sailing, I'll begin the process of informing everyone who owns 6.0 that they get a free upgrade, even though it's been 19 years, it's, it's free for them. So no new action needs to be taken by anyone who hasn't already jumped onto testing the pre-release code. I just wanted to note that the project had achieved a significant milestone along the way.
(01:03:07):
Big time. Congrats, thanks to everybody for their support, all, all along the way all this time, and thank you, Jason. Yes. Yeah, good work. It's like, yeah, I bet. Sigh of relief. You only get a week though to, to rest on your laurels, and then you gotta start working on the next version. I'm sorry, Steve. Yep, that's it. That actually is the plan. I will, I'll be starting on spin ride seven immediately. I I was gonna say, just give yourself a week. I mean, you deserve, you deserve to take some time. Maybe go to Disneyland is, is one idea. So, so that in inevitably some of the testers have been asking for this or that new feature, I mean, like extensions beyond what it currently is. And I've said, look, I've said understand this. My goal has been to update six to six, one to resolve the, the problems with speed, the problems with drive size.
(01:04:01):
And, and, and, and inevitably I ended up doing way more than that, but I said, understand this, my goal is to obsolete 6.1 as quickly as I can with 7.0, because there were some things we could not do. We could not do U E F I that re you Doss will not run on U E F I, period. So in order to move to U A F I, we have to leave dos. Well, that's a big change. So that's not like an incremental, as you, no one would call that an upgrade. So, you know and also I wasn't able to do native support for U S B, so U S B still runs through the bios as all USB always has for all of spin, right? But I wanna get to seven Oh, so I can resolve those things also. But it was just necessary to say, no, we're, we're stopping at six one.
(01:05:01):
And then after that point, my goal is to obsolete it as quickly as possible. And once everyone has six one, that'll be what they want too. So it's a win-win. Absolutely. And Jason, let's do our last sponsor insert and then we're gonna talk about the massive move it maelstrom. Excellent. Also a win-win is what we have coming up next. And what's a win-win as well is our sponsor for today's episode of security. Now that is Collide. Collide is a device trust solution that ensures unsecured devices can't actually access your apps. Now Collide has some really big news. If you haven't heard already. If you're an Okta user, collide can actually get your entire fleet to 100% compliance. Now, collide Patch is one of the major holes in zero trust architecture. That's device compliance. How do you get everybody on board? How do you get everybody up to date?
(01:05:55):
Think about it, your identity provider, only lets known devices log into apps. But just because a device is known doesn't always mean it's in a secure state. If anything this podcast has taught you, it's that in fact, plenty of the devices in your fleet probably shouldn't be trusted at all. Maybe they're running an out of date version of the OS or maybe they've got unencrypted credentials just lying around. If a device isn't compliant, if it isn't running the Collide agent, it can't access the organization's SaaS, apps or other resources. Plain and simple, the device user can't log into your company's cloud apps until they've fixed the problem on their end. So, just as one example, a device is gonna be blocked if an employee has an out-of-date browser. Using end user remediation actually helps drive your fleet to 100% compliance, and it does it in a way that doesn't overwhelm your IT team.
(01:06:55):
With, without Collide IT teams have no way to solve these compliance issues or to stop insecure devices from logging in. But with Collide, you can actually set and enforce compliance across your entire fleet. And, you know, regardless of os, Mac, windows, Linux, and collide is, is really unique in that it makes device compliance part of the authentication process. So when your user logs in with Okta Collide alerts them to compliance issues, it says, Hey, this is wrong, needs to be righted, and then prevents unsecured devices from logging in. It's just, it doesn't, it doesn't qualify. So it doesn't get in it's security you can feel good about because Collide puts transparency and respect for users at the center of their product. So in total, collides method means fewer support tickets, it means less frustration. These things can be very frustrating when they're done in incorrectly that is not collide.
(01:07:51):
And most importantly, 100% fleet compliance. Visit collide.com/security. Now you can learn more by going there. You can also book a demo to give you a better sense of what Collide is all about. That's k o l i d e collide.com/security now. And check it out for yourself and you're gonna love it. If you haven't already, you really need to do it. Collide.Com/Security. Now. We thank them for their support of security now, and now it's time to move it, it's time to get into the massive move it Is it maelstrom? I always see that word and I'm like, is it maelstrom, maelstrom, maelstrom, maelstrom, I guess Maelstrom. I think so. Maelstrom. Okay. So our main topic today arise about three weeks after the first signs of this significant problem arose. I've been aware of and watching what's been happening, but it wasn't until this past week that the scope and scale of the problem became fully apparent.
(01:08:58):
So this week we need to do a bit of catching up with what's been going on and then we'll look at where we are today. The trouble surrounds a globally popular filed transfer facility named MoveIt. Moveit Is it, it has both a, a local version called MoveIt Transfer and also a, a, a cloud-based solution MoveIt Cloud. The basically it's a file sharing and management solution from it's, its parent company progress www.progress.com/moveit, M O V E I T. And in the way they've spelled it is M O V E is all caps and it is small. So MoveIt describes itself as managed file transfer software. They, they, they said secure file transfer and automation software for the enterprise guarantee the reliability of core business processes and transfer sensitive data between partners, customers, and systems. The secure and compliant way with MoveIt secure, auditable, automated and compliant file transfer on premise.
(01:10:18):
And in the cloud, MoveIt provides secure collaboration and automated file transfers of sensitive data and advanced workflow automation capabilities without the need for scripting, encryption and activity tracking enable compliance with regulations such as pci, HIPAA, and gdpr. Okay, we've just read that it's compliant with pci, H I P P A, HIPAA and G D P R. Unfortunately, another abbreviation, its web front end is fully compliant with is SQL and not in the way they intended. That's right. The industry has been hit with another very powerful and significant sequel injection attack. I was tempted to title today's little Bobby drop tables and our longtime listeners will understand the history of that name or cartoon or joke. The last time we were on this subject, I railed against the fundamentally broken design of the sequel command model, which exposes a fully capable command language to a web server that typically only needed to issue queries against the data.
(01:11:42):
Yet the unrestrained nature of this powerful command line interface meant that the web server could do anything it wished, and if someone could arrange to get the web server to pipe their own user supplied text through to the backend SQL server, such a remote user could do pretty much anything they wished my denigration of SQL generated some pushback from some of our listeners who quite correctly noted that there were several other much safer and much more proper ways to do this with modern SQL servers. And those listeners were of course, 100% correct, but I wasn't saying that safer and more proper ways had not since been developed to do this, but that the original unsafe ways also continued to be present in the interest of endless backward compatibility and not breaking legacy systems. Consequently, nothing prevents the original horrible and fundamentally insecure approach from continuing to be used.
(01:13:00):
And so here we are today in 2023, we had the latest example of this bad architecture striking. Once again, even if someone was being as responsible as they could be with this hot potato, it would be the programmer's responsibility to try to think of all possible ways. Bad guys might attempt to sneak commands under the cover of data by encoding them strangely using an unusual language locale or who knows what. As is always the case with security, the battle is asymmetric. The programmer must block every possible avenue of conquest, whereas the bad guys only need to find one way in to progress' credit the publisher of MoveIt from the start, they have not tried to hide any of this in any way. Right there on their main product promo page. They write in a have a big yellow, bright yellow warning says product advisory, move it, transfer and move it.
(01:14:16):
Cloud vulnerability, click for mitigation measures and patch information. Okay, so here's what we knew three weeks ago as May was coming to an end, as we already know, move it's solution includes a web-based front end to manage the sharing, uploading, and downloading of files. This makes sense in an era of JavaScript, which is able to accept drag and drop uploads and manage local downloads. When we mix in web authentication, which is as we know, an entire discipline of its own, it's quite possible to create a fully functional web-based file management and distribution system. And when the alternative was email, you know, using email for that, there's no competition move. It also supports F T P, but I assume that's for legacy purposes since FTP support has, as we know, finally been deprecated and removed from web browsers and it's unclear what Advantage FTP has any longer over any modern web browser solution Once upon a time.
(01:15:39):
Sure. Today not so much as for this vulnerability. The bad news is that it was a true zero day progress learned of it only after and because the bad guys were already exploiting it, and boy, were they being responsible progress quickly patched all of their supported move IT versions and their cloud-based, you know, the, the, the, the the move it transfer local, you know, self-hosted versions as well as their cloud-based service. There are essentially four things that can be done with this vulnerability. The deletion of existing data, the exfiltration of existing data, the modification of existing data, and the implantation of new files and malware. As it turned out, two of those four have been seen happening. Mandiant, which is now owned by Google Cloud, has been tracking the move it breach activity under their uncategorized moniker U N C 48 57, and posted that the opportunistic attacks have singled out a wide range of industries based in Canada, India, the us, Italy, Pakistan, and Germany.
(01:17:12):
And Mandy also wrote that it was aware of multiple cases where large volumes of files have been stolen from victims, MoveIt transfer systems unquote, and adding that the web shell left behind, which they call lemur. Lut was also capable of stealing Azure storage blob information. So we have to start with massive data. Exfiltration and Mandis mentioned of a web shell brings us to the second of the two things that is being done, the implantation of new files and malware because the bad guy, the bad guys have also found to be dropping web shell malware before they leave. We've previously talked about web shells but here's a bit of history. In the early days of the web, web servers only delivered static HTML webpages. You gave them a url, which was the, basically the, the location of the pages text on the server, and it returned that page to the browser.
(01:18:23):
After several years of that browser side scripting, which was embodied by and enabled by JavaScript introduced the concept of running something, running code that you received from a web server on your browser, so-called client client side scripting. This brought the user's client alive, giving it some of the capabilities of a local application. A perfect and simple example is that a user's entered password could be hashed locally by scripting running in the browser so that a web server that wanted a password never received anything but the hash. That was a big benefit in security for the user. These days, of course, we're seeing the logical evolution of scripting on the client with amazingly complete and, and complex web apps, but even browser side scripted pages could be delivered by static files. You know, lots of JavaScript is just a js it's just a JavaScript file that is being delivered statically to, to, to, to drop a library of, of complex JavaScript like no JS onto the user's browser.
(01:19:42):
That's just a static download and typically it's cashed, so it's very quick. The big change on the server side occurred when web servers started running code to respond to queries being made by their clients. The earliest implementation of this was known as cgi, which stands for Common Gateway Interface. The idea behind c j I was simplicity. A web client would make a query and the web server would essentially serve as an intermediary between the user's web browser and sub code, which the web server would execute on the server. To do this, the web server would launch and run a separate CGI program in the background. Often with the extension cgi, the web server would provide the CGI program with what the user had queried, and whatever the CGI program returned through its standard output would be piped back by the web server to the user's web browser to be seen.
(01:20:50):
So with cgi, rather than delivering static textual webpages, the output of a pre-compiled program was returned to the user's web browser. This was a big application for Larry Wahls Pearl, which was often used in early CGI applications. This model was clean and simple and it remains in heavy use today, where, as I noted earlier from that printer PHP page where P H P is the backend recipient of a client's CGI queries, GRCs web forums and that link shortener I mentioned are all P H P as is WordPress, which as we know runs a huge portion of the web. Wordpress written in php. Modern web, modern web servers provide for many ways to generate dynamic content, as it's called GRCs shields Up perfect passwords, perfect paper passwords. The d the are, the GRCs DNS spoof ability test and GRCs support for squirrel are all implemented using DLLs that I wrote of course in assembly language using the Microsoft is api.
(01:22:09):
API to obtain and return data to and from users' webpages. So this is common. Microsoft also promotes their own server side interpreter, which implements their scripting language known as active server pages. A S P. When a web server which has active server pages enabled encounters A U R L referring to a file ending in ASP or aspx, the web server will look for that file on the URL's provided path and will run the code contained in that file, the active server pages code. And that brings us back to the Lamu <laugh>, I can't say it. Laur Le Lemur. Youre lemur. Thank you. Lemur Le Lemur Lu. I dunno, I'm guessing if I start, I I think, I think you're right. It it, it's Lemer Loot. Lemer Loot, a Lemer Loot web Shell <laugh> tongue twister. Yeah. Thank you Jason. That's, that's being left behind by these attackers in machines that have been attacked.
(01:23:18):
The attackers leave behind a file named Human two numeral two Human numeral two aspx. They chose that name. Since a human ASPX file is already present in the system as part of the authentic file set, so obviously they're making it look like it belongs there. They also sometimes leave additional files with the file extension dot cmd l i n e dot command line. This human two aspx file functions as a web shell. It's a sophisticated script that will provide future access to any as p script capable web server that's unlucky enough to host it. The bad guys know its name and they know its location on the server so they're able to invoke it at any time in the future remotely. Simply by querying the server for a U R L and path ending in Human two as px, the web server will immediately run that code, which typically gives remote attackers control of the system and probably of the network.
(01:24:35):
The Web Shell is also engineered to add new admin user account sessions with the name Health Check Service in an effort to appear benign and avoid detection. This means that just patching against the attack after the fact will not be sufficient protection such since a previously vulnerable server may have already been quietly infected with the Human two web shell after patching, it'll be necessary to search for any IOCs as we call them today. Indications of Compromise, CISA quickly issued a nationwide alert to let everyone know and to demand that all government agencies using the MoveIt transfer system update and check for evidence of past incursions. Our friends at the web scanning search engine census, who were the subject of last week's podcast, have identified more than 3000 vulnerable instances of MoveIt, the majority of which are located in the us. Huntress Labs was all over this at the start of the month, excerpting and editing a bit what they wrote, they said on June 1st, 2023, Huntress was made aware of active exploitation attempts against the move IT file transfer application.
(01:26:12):
Previously on May 31st, the vendor progress had just released a security advisory expressing there is a critical vulnerability that could lead to unauthorized access. On June 2nd, the industry dubbed this vulnerability C V E 20 23 34 360 2 Progress brought down Move It Cloud. As part of their response and investigation, Huntress has fully recreated the attack chain exploiting MoveIt transfer software. We have uncovered that the initial phase of the attack SQL injection opens the door for even further compromise. Specifically arbitrary code execution. We use our exploit to receive shell access with interpreter escalate to NT authority slash system, meaning full system level privileges and detonate alop ransomware payload and we'll be talking about clop in a moment. They said this means that any unauthenticated adversary could trigger an exploit that instantly deploys ransomware or performs any other malicious action. Malicious code would run under the Move It service account user move it S V C, which is in the, which is in the local administrator's group, meaning again, full admin privileges.
(01:27:51):
The attacker could disable antivirus protections or achieve any other arbitrary code execution. Another demonstration showcased compromising the Move it transfer API and application itself. With that alone, we upload, download and potentially exfiltrate files. As a threat actor would the behavior that the industry observed adding a human two aspx web shell is not necessary for attackers to compromise the move it transfer software. It's an option that this specific threat actor chose to deploy for persistence, but the attack vector offers the ability to detonate ransomware right away. Some have already publicly reported attackers pivoting to other file names that is using other than Human two because that's now become known. They end the recommended guidance is still to patch and enable logging from our own testing. The patch does effectively thwart our recreated exploit. Okay, so beginning of June, patch released, unfortunately as they say, the horses had left the barn.
(01:29:07):
Actually they had left the barn and they had traveled quite a distance from the barn. Microsoft attributed the MoveIt transfer zero day attacks to Lace Tempest, a threat actor previously linked to clop ransomware data theft and extortion attacks. On June 6th, the Clop gang posted a communication to their leak site demanding that their victims contact them before June 14th to negotiate extortion fees for deleting the stolen data. I'm gonna read without correcting the grammar, what the Ransom Note said that was posted on LOP site for their victims to respond. Tolo wrote, dear Companies, clop is one of top organization offer penetration testing service after the fact, which offer penetration testing service after the fact. That's one way to put it. They said this is an announcement to educate companies who use progress, move it product. That chance is that we download a lot of your data as part of exceptional Exploit.
(01:30:34):
We are the only one who performs such attack and relax because your data is safe. <Laugh>. Yeah, right in Russia they said we are to proceed as follow and you should pay attention to avoid extraordinary measures to impact your company. Important in all caps with an exclamation point. We do not wish to speak to media or researcher leave. Then we have three steps. Step one, if you had Move IT software continue to step two else. Leave step two, email our team@unlockrsvbox.com or unlock support multi.com. Step three, our team will email you with dedicated chat URL over tour. We have information on hundreds of companies, so our discussion will work very simple. Now we have seven steps. One, if we do not hear from you until June 14th, we will post your name on this page. Step two. If you receive chat url, go there and introduce you.
(01:32:02):
Step three, our test will provide 10% proof of data we have and price to delete. Step four, you may ask for two to three files. Random as proof we are not lying. Step five, you have three day to discuss price and if no agreement you custom page will be created. Step six. After seven days, all your data will start to be publication. Step seven, you chat will close after 10, not productive day and data will be published. Next section is all caps. What warranty? Our team has been around for many years. We have not even one time not due as we promise when we say data is delete, it is cause we show video proof. Okay? <laugh> just are gonna show someone typing the command into a console. Wow, that's proof. All right. It's definitely gone. Now they say we have no use for few measles dollars to deceive you.
(01:33:17):
They don't want any measle dollars apparently. Call today before your company name is published here. Friendly cop friendly cop. It says Plop friendly Cop P Yes. If you are a government, city or police station, do not worry. We erased all your data. You do not need to contact us. We have no interest to expose such information. Next line. And then presumably, oh, I'm sorry. No. So, so, so then, so, so we have no interest to expose, so such, such information. Okay? Then presumably after the initial June 14th contact deadline had passed, they added updates. So under updates they have Bissell, b i s s e l l.com. Bissell.Com 50 TB company data. Get ready for something interesting, Emerald d emerald dc.com, 100 tb company data. Get ready for something interesting and then a bit later, 360 equipment finance.com files. Part one published Precision medical billing.net files part one published hci.edu files part one published.
(01:34:46):
So the point of this story is over the past three weeks is that we have the internal private of thousands of US companies who have been using progresses MoveIt transfer software, first exfiltrated from their servers, and in some cases as much as a hundred terabytes worth. Apparently this was not good, but we're not done yet. After a week had passed, believe it or not, progress announced the news of additional discovered vulnerabilities June 9th. They said, in addition to the ongoing investigation into vulnerability CVE E 20 23, 40 3,362, we have partnered with cybersecurity experts to conduct further detailed code reviews. Oh, what a nice idea. Let's do it now as an added layer of protection for our customers. As part of these code reviews cybersecurity firm Huntress has helped us to uncover additional vulnerabilities that could potentially be used by a bad actor to stage and exploit. These newly discovered vulnerabilities are distinct from their previous reported vulnerability shared on May 31st, 2023, all move it transfer customers must apply the new patch released on June 9th, 2023, all move it Cloud customers please see the Move IT cloud knowledge base article for more information.
(01:36:33):
The investigation is ongoing, but currently we have not seen indications that these newly discovered vulnerabilities have been exploited. Then exactly one week after that. Last Friday, June 16th, we have more. June 16th, 2023. Yesterday we reported the public posting of a new SQL injection vulnerability that required us to take down H T T P S traffic for Move IT Cloud and to ask move it transfer customers to take down their H TT P and HTT p s traffic to safeguard their environments. We have now tested and deployed another patch to move IT cloud, returning it to full service across all cloud clusters. We have also shared this patch and the necessary deployment steps with all move it transfer customers all move it transfer customers must apply the new patch released on June 16th, 2023. Details on steps to take can be found in the following knowledge base article, all Move at Cloud customers please see the move at cloud status page for more information as investigation is ongoing.
(01:37:55):
But currently we have not seen indications that this newly discovered vulnerability has been exploited. So what happened for in the third case is that some random independent person looked at this software and said, oh, how about this one? And posted it publicly. Whoops. Okay, so what do we know about the victims so far? CNN Business had some reporting on this excerpting from what c Nnn reporting a growing number of businesses. Universities and government agencies have been targeted in a global cyber attack by Russian cyber criminals that are now working to understand how much data was compromised. Cisa said Thursday that several f federal agencies have experienced intrusions. The US Department of Energy said it took immediate steps to mitigate the impact of the hack after learning that reports from two department entities have been compromised. It's also impacted state governments in Minneapolis, in, in Minnesota and Illinois.
(01:39:04):
And on Thursday state agencies said 3.5 million Oregonians with driver's licenses or state ID cards have been impacted by a breach as well as anyone with that documentation in Louisiana, in o In other words, all of Louisiana British Airways confirmed that its staffers names, addresses national insurance numbers and banking details were exposed because its payroll provider zealous used MoveIt. The BBC said its staff had also been afflicted because zealous was its payroll provider. The UK's beauty and health company Boots said some of its team's members' information was also stolen. Brett Callow threat analyst at cybersecurity firm, Moft said the hackers have also listed a O n and the Boston Globe as victims. By my count, he said there are now 63 known slash confirmed victims plus an unspecified number of US government agencies. The hacking campaign has also spread to academia. Johns Hopkins University in Baltimore and the university's renowned health system said in a statement that quote, sensitive personal and financial information, including names, contact information and health billing records may have been stolen in the hack.
(01:40:34):
Meanwhile, Georgia's statewide university system, which spans 40,000 student University of Georgia, along with over a dozen other state colleges and universities confirmed it was investigating the scope and severity of the hack. Techcrunch added the ransomware responsible for exploiting a critical security vulnerability in a popular corporate file transfer tool has begun listing victims of the mass hacks, including a number of US banks and universities. The victim list, which was posted to Clark to Lops Dark web leak site includes US-based financial services organizations, first Source and First National Bankers Bank, Boston based investment management firm, Putnam Investments, the Netherlands based land Landau, green Parks, and the UK based energy Giant Shell Green Shield Canada. A nonprofit benefits carrier that provides health and dental benefits, was listed on the leak site but has since been removed. Other victims listed include financial software provider, data site, educational, nonprofit, national student clearinghouse, student health insurance provider, United Healthcare Student Resources, American manufacturer, Legett and Plat, Swiss Insurance Company, O K K, and the university system of Georgia.
(01:42:01):
A spokesperson for German mechanical engineering company. Heidelberg, which clop listed as a victim, told TechCrunch in a statement that the company is well aware of. Its mentioning on the tour website of CLO and the incident connected to a supplier software lop, which like other ransomware gangs typically contacts its victims. To demand a ransom payment to decrypt or delete their stolen files took the unusual step of not contacting the organizations it had hacked. Instead, a black male message posted on his dark web leak site told victims to contact the gang prior to its June 14th deadline. Multiple organizations have previously disclosed they were compromised as a result of the attacks, including the bbc, air Lingus and British Airways. These organizations were all affected because they rely on HR and payrolls software supplier zealous, which confirmed that its Move it system was compromised. The government of Nova Scotia, which uses MoveIt to share files across departments also confirmed it was affected and said in a statement that some citizens' personal information may have been compromised. However, as we know, lops Leak site said, if you're a government, city or police service, we erased all your data. Ofcom. The UK's communications regulator also said some confidential information had been compromised in the Move It Mass hack. In a statement, the regulator confirmed that hackers access some data about the companies it regulates. Along with the personal information of 412 Ofcom employees Transport of London, the government body responsible for running London's transport services and global consultancy firm, Ernst and Young are also impacted. According to BBC News, neither organization responded to TechCrunch's questions.
(01:44:02):
Boy, you know, it's one thing to say, oh, thousands. It's another thing to actually hear them listed and understand what it means that you know that many actual physical entities were affected and afflicted by this. Since we haven't yet enumerated the literally thousands of individual companies, government and educational agencies and other organizations that may have been compromised in this mass attack. Many more victims are expected still to be revealed in the coming days and weeks, and now that they know what to look for, security researchers looking back through their logs have determined that someone had been experimenting with the exploitation of these move. It vulnerabilities for the past two years, since 2021 and Clop was also responsible for previous mass attacks, exploiting flaws in fortress go anywhere file transfer tool. Remember that one recently and Accion's file transfer application. So welcome to our new normal.
(01:45:25):
A serious flaw is silently discovered in a popular, highly used web connected application. Its discoverer remains quiet for years while patiently working out exactly how to set up the attack for maximum effect in the greatest number of cases. There's a bit of a risk reward tradeoff here since it's always possible that by not jumping on and exploiting a vulnerability immediately, it'll give it some time to be discovered and remediated before an attack can occur. We've often seen this effect when, for example, a well-planned pone to own exploit fails because patches were coincidentally released on the eve of the competition to foreclose the exploit. Then all vulnerable service instances are located ahead of time and the attack is staged and readied. And finally, effectively all at once, all of that vulnerable services users have their data silently, ex exfiltrated and stored in the case of clop. All of that sensitive data probably lands in Russia and a a web shell is also installed to allow future access. Finally, victim companies are notified, threatened en mass, publicly shamed, and eventually if they don't aced to the extortionist demands have their potentially sensitive internal and client data released to the world.
(01:47:17):
The industry has observed that in this instance, the traditional don't call us, we'll call you model, has been reversed with the attackers asking their victims to initiate the contact. It's been suggested, as I noted by TechCrunch, that this is due to the fact that there are just too many victims for the attackers to manage proactively. So they've chosen to be more passive and wait to be contacted. This is probably an optimal strategy since what the attackers want is maximum extortion payments and the likelihood of being paid and being paid a larger amount is far higher if they are proactively contacted by a concerned victim than if they reach out to cajole all of their targets. Now at this point, we don't know how much money the campaign will net for clo. We're still in the early days unfortunately, but the numbers are distressing for ransomware and cyber extortion gangs in general.
(01:48:20):
RE is known to have netted 150 million reil 123 million in 2020 lock bit 91 million Dark side, 90 million Maze reor, 75 million Cuba, 44 million Conti, 25 and a half million net walker, 25 million Dharma, 24 million. All told that comes to just shy of 650 million that has been, that has been raked up by these guys. And of course everybody knows this as this podcast has observed, malicious hacking is no longer being done for sport. It's now all about money. And unfortunately, money creates incentive. And as we've also seen frequently, there are a sufficient number of undiscovered vulnerabilities lurking within much of today's software to incentivize the bad guys into finding and exploiting them for their profit. And it's not as if the bad guys are smarter. As soon as equally talented security researchers began taking a closer look at progress's MoveIt transfer software, additional previously unsuspected vulnerabilities started falling out of the thing weekly.
(01:49:54):
That widely used software turned out to be a mess. Yet good guys were never given sufficient prior reason to examine it because the economics of doing so did not make sense. No security researcher was going to earn millions of dollars by discovering those problems and turning them in for a bounty. But the economics for the bad guys did and does make sense since they will likely manage to extort millions of dollars overall from their newly acquired victim base, something needs to change. Academics in their ivory towers are busily inventing and developing new computer technologies that have none of these problems. But what we know is that down here on the ground, nothing changes unless it is forced to. When I was previously complaining about the utterly and obviously broken traditional model of SQL database access by web servers, I was scolded by our listeners and told, oh, Steve, don't you know that was the old way of using sql, right?
(01:51:13):
Old tell that to the thousands of victims of this latest catastrophe of SQL database base usage. And speaking of old, does everyone know just how old this attack is? Just how old is the exploit that created the little Bobby drop tables joke? The operation of the sequel injection exploit was first documented in 1998 by cybersecurity researcher and hacker Jeff Forrestal. His findings were published in the Hacker Magazine, frack Writing under the moniker Rainforest Puppy. Jeff explained how someone with basic coding skills could piggyback unauthorized SQL commands into legitimate SQL commands to pull sensitive information out of a website's database. Gee, doesn't that sound a lot like what just happened last week? And that warning came 23 years ago? 23 years ago. This is a fundamental database architecture that was ho horribly bad then and nothing has changed since. It happened again three weeks ago in 98 when Jeff Forrestal notified Microsoft about how the vulnerability impacted their very popular SQL Server product.
(01:52:51):
Microsoft, no one's gonna be believe this. Microsoft didn't see it as a problem, as Forrestal put it at the time in his article for frack. According to Microsoft, what you're about to read is not a problem, so don't worry about doing anything to stop it, unquote. So how'd that advice work out? In 2007, the biggest convenience store chain in the United States at the time seven 11 fill victim to a SQL injection attack. The Russian hackers used SQL injections to hack into the 7-Eleven website and use that as a stepping stone into the convenience store's customer credit card database. This allowed the hackers to then withdraw cash back home in Russia. Wired magazine reported that the culprits absconded with 2 million that same year. Cyber criminals used S QL injection to gain, to gain administrative control over two US Army related websites and redirect visitors to websites with anti-American and anti-Israel propaganda.
(01:54:01):
The next year in 2008, MySpace data breach ranks as one of the largest attacks on a consumer website. In history, criminals stole emails, names and partial passwords of almost thir 360 million MySpace user accounts. Thanks to that attack, we learned that it wasn't a good idea to reuse passwords across sites. The award for the most egregious lack of security probably goes to Equifax. The 2017 Equifax data breach, which yielded extremely personal information names social security numbers, birthdates, and addresses for 143 million consumers was, you guessed it, a sequel injection attack. And what's worse prior to the data breach, a cybersecurity researcher had warned Equifax that they were susceptible to a SQL injection attack. Whoops, every three years, the oasp Open Web application security project ranks the top 10 most critical web application security risks. Guess where SQL injection ranks? Yep. Number one, our listeners who kindly took the time to educate me about there being much better and more secure ways to use sql were absolutely correct, which only serves to underscore the tragedy of the fact that SQL will still happily operate today the same way it did 23 years ago in 1998 using sequel.
(01:55:44):
The horribly and fundamentally insecure way is unfortunately also the obvious and easy way. This thing should have been strangled in its crib the moment it was born in 1998. But instead Microsoft and others blessed it and said, oh, it's so wonderfully easy and powerful. Those worrywarts are just trying to get some ink. It's fine, don't worry about it. Just be careful, right? Mm-Hmm. <affirmative>, be careful walking on ice while carrying that dynamite. Just don't fall. Just, you know, just don't fall <laugh>. And what was interesting was that noted, notice that huntress huntress who found that second round of multiple exploits missed the third one. So even they staring at the code didn't see it. And that's the problem. This, yeah, this, this approach is insecure by default. And so it's up to, to someone attempting to filter out any possible misuse, and obviously that's not working out very well.
(01:56:59):
Mm-Hmm. <affirmative>, mm-hmm. <Affirmative>, wow, that is a lot to take in. And and to know that, that, that there is no resolve, there is no resolution on anything <laugh> what you're talking about right now. And it just gets worse and it just continues to snowball Normally, normally we're able to put some of the blame on the people who get attacked, right? Mm-Hmm. It's like, well, you shouldn't have been doing this or that, that, you know, you know, someone clicked a link and that brought the malware in and then the ransomware got you. No, this was a widely used, you know, basically it, it's a bit of a competitor to, to Microsoft's file sharing solutions, you know, SharePoint? Mm-Hmm <affirmative>. It does the same sort of thing for, for, for enterprises. And so this thing was widely used. There was no reason to imagine that it would wipe out every one of its users trust.
(01:57:57):
No one or nothing. Period. End of story. <Laugh> cuz it all, it, it's, it, it all could go to help. I've got databases here and none of them run sql. My, my, there you go. My e my e-commerce system and, and Squirrel needs a user ID database on the backend. Nope, you won't find me using that piece of, nevermind <laugh> a piece of, nevermind. I like that actually. Good stuff. I love the deep dive. Love. I mean, you, you always do fantastic deep dives, but, but I often find myself at the end of it, like, oh dear God. Like, what, what do you do with, well Jason, where do you get going with this? Now we've got the, we got the power LEDs of Walmart security equipment, <laugh>. If it's got a little l e d power on it, then it's over. We're screwed.
(01:58:45):
Like even that isn't safe. If, if power LEDs aren't safe, what is, that's what I ask you Steve, great stuff. Anyone who wants to get into everything that Steve's up to, all you have to do is go to grc.com, you'll find all sorts of Steve Gibson. Goodness there spin, right? Of course. Again, congratulations, major milestone. Thank you. And if you aren't on board, you can get it there. The best mass storage, recovery, and maintenance tool could be found@grc.com audio and video of this show. Of course, also transcripts of this show can be found there as well. If you are on the twit site, you wanna find security Now it's easy to do. TWIT TV slash sn. Of course we have our audio and video there as well, but we also have ways to subscribe to the show, which is really at the end of the day, one of the most important things.
(01:59:36):
If you love what we're doing here at twit, if you love podcasting in general, subscribe to the shows that's sending the best signal to us and to the people who help pay us to do what we do. So that could be found at twit tv slash sn. We do record this show every Tuesday. Usually it's Leo sitting here in the studio. But if not, I'm happy to fill in for Leo anytime he's out at Disneyland. But we do it every Tuesday, 4:30 PM Eastern, 1:30 PM Pacific, 2030 U T c. And just, you know, just so in case you haven't heard about it before or in case you haven't jumped on it yet, club Twit is really important to us as well. Subscribe to our podcast, very important. Club Twit is a way for you to support us directly. That's Twit tv slash club twit.
(02:00:28):
$7 a month gives you all of our shows with no ads gives you access to all sorts of bonus content shows that don't exist outside of the club. Hands on Mac, hands on Windows, the Untitled Linux show, Stacy's Book Club, home Theater Geeks. More coming soon. I'll just go ahead and say that, that I might be a little interested in, possibly involved in. Actually I think definitely involved in also our members only Discord. Lots of stuff that you get through Club Twit, aside from the fact that you're just helping us directly do what we do and keeping us going. That's twit tv slash club twit and we thank all of you who subscribe and those of you who might thank you so much to John for engineering here in the studio. Thank you to Steve. You do a fantastic show and I'm always honored to sit in the the Leo hot seat while he's out. So thank you for welcoming Steve, Jason, absolute pleasure. And I'll see you next time you're standing in <laugh>. Sounds good. We'll see you next time on Security now. Bye everybody. Bye.
Rod Pyle (02:01:31):
Hey, I'm Rod Pyle, editor-in-Chief VAT Astor magazine. And each week I joined with my co-host to bring you this week in space, the latest and greatest news from the Final Frontier. We talk to NASA chiefs, space scientists, engineers, educators and artists, and sometimes we just shoot the breeze over what's hot and what's not in space books and tv, and we do it all for you, our fellow true believers. So whether you're an armchair adventurer or waiting for your turn to grab a slot in Elon's Mars Rocket, join us on this weekend space and be part of the greatest adventure of all time