Security Now 927, Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for Security Now, Steve Gibson is here with a big, big, big show for you coming up in just a little bit. Crypto mining, who pays for all that Crypto mining. Who doesn't pay for their Google Cloud services? A Chinese authenticator or certificate authority that you really shouldn't be using if you can avoid it. And then Steve looks at Apple's security announcements from last week's ww d c, that and a whole lot more. Coming up next on Security Now
Speaker 2 (00:00:31):
Podcasts
Leo Laporte (00:00:32):
You love
Speaker 2 (00:00:33):
From people you trust. This is tweet it.
Leo Laporte (00:00:41):
This is Security Now with Steve Gibson. Episode 927 recorded Tuesday, June 13th, 2023, scanning the internet.
(00:00:53):
Security now is brought to you by a c i Learning it. Skills are outdated in about 18 months, so you better stay ahead of the curve and future proof your business' competitiveness with customizable entertaining training. Fill out the form@go.acilearning.com slash twitch for more information on a free two week training trial for your team. And by bid warden. Get the password manager that offers a robust and cost effective solution that drastically increases your chances of staying safe online. Get started with a free trial of a teams or enterprise plan, or get started for free across all devices as an individual user at fit warden.com/twitch. And by ag one from Athletic Greens. If you're looking for a simpler and cost effective supplement routine, ag one is giving away a free one year supply of vitamin D and five free travel packs with your first purchase of a subscription. Go to athletic greens.com/security. Now it's time for security. Now, the hatless Steve Gibson, but you don't
Speaker 2 (00:02:00):
Need a hat
Leo Laporte (00:02:00):
Because he's inside to do the show. Steve Gibson's here, our master in ceremonies and all of that. Hi there. <Laugh>.
Steve Gibson (00:02:09):
Hello there, Leo. Hey there. And as we know, glass is a blocker of UV B radiation, which is why we should all be taking some vitamin D cuz we don't, we're not getting it. That's true when we're inside. And that's why when you hang your ha your arm out the window when the windows roll down in the old days <laugh>, it's the farmer's tan. Yeah, that's right. You got your arms sunburn. Nothing else. I know that because I have those new transitions lenses on my eyeglasses that UVB darkens them. But you sit in the car and they don't darken, which is kind of a problem. Anyway, we're not here to discuss optics. We're here to discuss security. What's up? We are, we're going to think of this is gonna be a fun one.
(00:02:51):
Not that that's any surprise. I hope we're gonna examine what happens to monthly cloud services billing. If you get infected by a crypto mining malware, it's not good. But Google has an answer. Speaking of cloud services, is Elon paying his bills and what's about to happen? Just how fast are iot O T based D DDoSs attacks on the rise? What was the strange tale of a wayward Chinese certificate authority and why is good? What happened? <Laugh>, what useful new privacy and security features will Apple be adding to their services with their next OSS in the fall? We've got an after W d WW d c report from from last week's event. And why is France headed in another direction from Apple? How does Russia feel about foreign internet probes entering their IP space? And what, if anything, can they do about it? And after a bit of miscellaneous, some listener feedback one of which drives me into a brief sci-fi reading retrospective for listeners. We haven't talked about that for a long time. And then a quick spin right update. We're gonna take a deep dive into the backstory and the current capabilities of the Internet's premier scanning and indexing service, which is known as Census C E N S Y S. Thus, today's title is Scanning the Internet. Oh, census with a y, census With a Y. Yes. That's cuz there's no you in it.
(00:04:39):
That's right. And as they say, there's no you in in internet. That's right. That's not about you. It's all about, it's about the world. All right's. Right? We we have a great picture of the week coming up in just a second. But first a word from our sponsor, our studio sponsors ACI Learning. And you may say, well, who's that? Well, you by now, you know, it's it pro it pro Med with ACI learning to form one of the biggest and if not the best training for IT, cybersecurity audit in the world. They are fantastic. We know IT pro They've been a sponsor of the show for more than a decade, providing entertaining, engaging IT training to all of our listeners. But now, as part of the ACI learning family, their capabilities have grown. They now have 7,000 hours and counting. There's new more content all the time of highly entertaining, highly bingeable content to help you get better at your job or to help you get that first job in it.
(00:05:45):
This is interesting, and I just, I've just found this out when I talk to talk to them, that 30% of the learners at ACI Learning are MSPs managed service providers. That kind of makes sense to me because managed service providers are, need to be on the kind of the cutting edge, the forefront of technology. They're the people. We have a managed service provider. That's who Russell is. He doesn't work for us. He's on contract. He has a team of very talented technicians who go and into, into offices and buildings and, and businesses and keep them online. I mean, that they are the front line of internet security, right? They need to be up to date. So I'm not at all surprised that ACI Learning is a headquarters for MSPs. They are there to help your team through any challenge. For instance, you'll love the learning practice, A C l learning Practices labs.
(00:06:39):
These are HTML five in effect servers you can use in your browser on any machine. You can set up a window server, configure it, you can break it <laugh>, you can get clients, all of that. These labs are great, not just for learning though. They call 'em the, the ACI learning. But really also as a way for MSPs to test an experiment before they deploy new apps or updates to see what's gonna happen, how the, how the ecosystem is affected. And it, it doesn't affect your live system, doesn't compromise it. That's fantastic. You can have multiple instances of Windows server and desktop clients. And you can do it anywhere OS 10 Linux, iOS, windows, even on a Chromebook. You could prepare for those certification exams. And a lot of MSPs, you know, it's a real value for them to have their team trained up.
(00:07:30):
Because then, you know, it makes you more valuable to your customers. That one m MSA M S P team leader told us, quote, I had 110 engineers in the field. That's not unusual, right? And we had dozens of it pro accounts last year alone. My team passed four over 40 certifications. 40. So that's really, you know, that's what you wanna see with an msp. They're always staying ahead of the curve. Right? So one of the things they offer these practice exams, let your, let your students take and retake the test before they take it for real great way to prepare. And also I have to say, it's, it's something, it's a benefit that your team will love. You know, it's not like a hardship for them. It's not like, oh, I gotta go to school because ACI learning makes their content engaging and fun.
(00:08:21):
Short form 20 to 30 minutes full transcripts. They can read along different learners like that style. But also more importantly, the completion rate for ACI learnings videos is 80%. 80% of people who stardom finish 'em. Now you might say, well, really? Is that good? Yeah, the average out there in the real world, about 30%. Because most of the stuff, frankly, you know, is boring. People are bored by it. Not ACI learning. They really know how to make it fun and interesting. So this is a benefit. Msps give their teams something they enjoy. They're getting new skills, they're getting more valuable, they're getting these certs. It's a benefit all around. Of course, the MSP gets the benefit of having a upscaled upskilled workforce. Don't settle for subpart training. Get the most engaging content, the most informative content, and they, you'll like the ACA Learning Pro portal.
(00:09:15):
It lets you assign courses to individuals. You can even say this one episode or this portion of one episode. You need to learn that you can manage seats, you can assign an unassigned team members. You get monthly usage reports, metrics like logins, viewing time courses viewed tracks completed. So you, you kind of know exactly, you know, the benefit you're getting from this training. It's a really good way, very important way to stay compliant with regulations to identify potential risks and weaknesses before they become problematic to future proof your business. Like I said, it's a great way to retain top talent cuz they know they're getting great training and they're getting better and better best way ever to upskill your team. And oh, by the way, yes, it's ISO certified. So that's something not every other company can say yes. A c learning is ISO certified.
(00:10:04):
The best training possible, I mean, really is, it's a value proposition for you and your team. You'll love it. Right now. Individuals get 30% off a standard or premium membership at go dot aci learning.com/twit. If you use the offer code TWIT 30, the offer code is twit 30, 30% off a standard or premium individual IT pro membership. And you can learn more about ACI learning's premium training options across audit it cybersecurity readiness, go dot aci learning.com/twi. If you've got a team. And it could be from two people. That's a team right to a thousand people. Volume discounts start at five seats and they've got great discounts for you. Find out more. Go dot aci learning.com/twi. You can even sign up for a free two week training trial for your team. That's enough time to really complete a course and really get a sense of, is this gonna work for us?
(00:10:57):
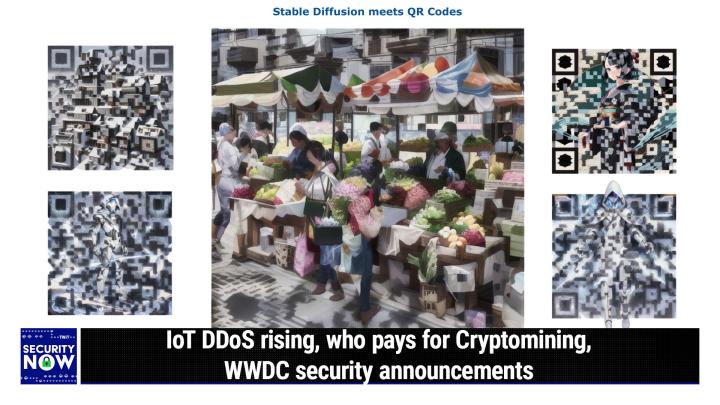
Go dot aci learning.com/twi. And again, individuals, don't forget, 30% off with the offer code TWIT 30 ACI learning. We love them. Go dot aci learning.com/twit. Now, time for the picture of the week, Steve. So this is sort of astonishing. And it's, it, maybe it's obvious in retrospect, but I, I have to salute the unnamed individual who thought, you know clearly somebody who was very much into the generative AI image stuff. Like, could I use stable diffusion to morph a real world photo, an image into something that a QR code reader would perceive as a valid QR code? And the answer was yes. This, it, this thing tore through Reddit last week. People were just blown away by it. So our picture of the week is, shows an outdoor sort of a vegetable market wi wi wi with some stands and various shoppers and purveyors some sort of underneath some sun protective awnings.
(00:12:25):
And it is also a valid QR code. You can, you know, once you under, I mean it looks maybe a little odd, but surprisingly not. And, but, but then you notice the three standard QR code targets two on the either either upper corner and one in the lower left. Where, where, you know, there, if you sort of get your eye to look at it, right, you can see that. And, and then like down on the, on the sidewalk down toward the bottom of the picture, it's, it sort of looks like shadowing, but it's actually part of the QR code. And, and, and, and the more you look around, the more you can sort of see how the stable diffusion engine fit the, the needs of the, the QR code into the image. And these were so cool that I have a second page of them in, in the show notes showing just, just two more examples, or actually four more examples of, of images that were morphed using stable diffusion to at, you know, like create what's arguably, you know, beautiful QR codes.
(00:13:39):
Anyway, so in case anyone was interested, I got a, a link in the show notes, stable hyphen diffusion hyphen art.com/qr hyphen code. And, and the, the at, at the top of the page, it said a recent Reddit post showcased a series of artistic QR codes created with stable diffusion. Those QR codes were generated with a custom trained control net model. Just like another day in the stable diffusion community, people have quickly figured out how to make QR codes with stable diffusion without a custom model. And then this page goes on to show you how you can indeed create your own, give it an image you want and a QR code you have. And presto, here's like this amazing hybrid. So anyway, just, I thought it was very cool. I wanted to share with our listeners, okay, so what happens more often than not when a cloud computing account is compromised?
(00:14:45):
Turns out the bad guys waste little time setting up and running a cryptocurrency mining operation. The bad news for unwitting users is that, as we know, the reason this is being done is to mine on someone else's dime. And the more computational resources that are available, the greater the rate of currency minting. Consequently, minting on stolen accounts is typically not throttled and it can consume massive amounts of compute time in a sh in a short bit of real time. And that brings us to the question, who pays for that stolen compute resource usage? Well, Google's June 8th announcement was titled, new Crypto Mining Protection Program offers $1 million <laugh> for costly crypto mining attacks. It's like, yes, I mean, you could get hit with a bill that you had like just astonishes you at the end of the month. And it's funny cuz what I remember was like in the early days of the internet, there was this notion it was called 90.
(00:16:05):
Well, there actually, it still exists when you're dealing with, with top tier providers, 95 5 internet bandwidth billing. The idea was that the, the, the I S P wanted to make available higher bandwidth in bursts but didn't wanna get taken advantage of. So they, they, over the course of a month, all of the, essentially the amount of bandwidth that a customer was using would be, would be sampled in small pieces. Then all of those samples would be sorted from, from greatest to least amount of bandwidth used in that sample. And then the 95th percentile was taken, maybe I got it sorted backwards. I think it was, it was sort of the other direction. And, and anyway, the idea was that, that if you had a, if, if, if you were, were using high periods of bandwidth, which wasn't like all month, it wasn't average bandwidth.
(00:17:16):
It, it was, it was weighted so that if you crossed, if you crossed more than 5% of the samples at the, the, the, the, the amount of bandwidth used at the, at that 5%, 95th percent, you know, percentile point that was then taken to be your bandwidth usage for the entire month. So the point is that if you weren't careful, you could similarly get hit with an astonishing bandwidth charge from, from an I S P that was billing in this way. So anyway, this is sort of the same. It's like, okay you're not paying attention. A bot crawled on to, you know, got into your cloud computing account and has been spent like all month grinding away generating cryptocurrency. And then Google says, ah, you owe us 5 million. It's like, what? <Laugh>? Anyway, so their announcement reads more like a promotional advertisement, but it contains some useful information.
(00:18:22):
So I wanted to share, here's what they said. They, they said crypto mining is a pervasive and costly threat to cloud environments. A single attack can result in unauthorized compute costs of hundreds of thousands of dollars in just days. Furthermore, the September, 2022 Threat Horizons report published by Google's cybersecurity action team revealed that 65%, okay, so just shy of two out of every three compromised cloud accounts experienced cryptocurrency mining. So, as I said, if they can get into your cloud account, that's what they do. Google said, stopping a crypto mining attack requires effective detection, which is why we've made it a focus of security command center premium. Our built-in security and risk management solution for Google Cloud to strengthen our customer's confidence in their ability to quickly detect and stop crypto mining attacks. Basically, they're gonna produce, they're, they're gonna give us indemnification. They said, we are introducing a new crypto mining protection program, which offers financial protection up to 1 million to cover unauthorized Google Cloud compute expenses associated with undetected crypto mining attacks for security command center premium customers.
(00:19:53):
In other words, they're basically, they're saying, you know, sign up for this, pay for this and we'll indemnify you because we're sure we're gonna be able to detect when this is happening on your account. So they said, we're able to offer financial protection because security command center premium includes specialized detection capabilities that are engineered into the Google Cloud infrastructure to detect crypto mining attacks. Security command center scans virtual machine memory for malware. It does this without agents which can slow performance and increase in organization's attack surface. Our approach enables us to detect attacks that could be missed by bolt-on security tools that rely on analysis of cloud logs and information gathered from APIs. Security Command Center can also detect compromised identities, which attackers to gain unauthorized access to cloud accounts and quickly deploy crypto mining malware. This means security command center can detect possible threats before an adversary can exploit compromised information to begin an attack.
(00:21:00):
This full set of advanced detection capabilities for crypto mining can only be delivered by a product built into the cloud infrastructure, blah, blah, blah. So, yeah commercial service. But, you know, it just sort of brings to mind you know, this is the kind of thing, unless you are really watching your, your cloud system closely or really do have your own technology for detecting when suddenly your C P U usage gets pinned and the demeanor starts running fast at Google this would make sense. I think they quoted a guy named Philip Buz, whose IDCs research manager for cloud security. Of course it's pro Google, but he said crypto mining attacks, this is idc crypto mining attacks continued to be a serious security and financial issue for organizations who do not have the right preventive controls and threat detection capabilities in their cloud environment.
(00:22:05):
So, you know, just don't go setting it up and, and forgetting about it and assuming everything's gonna be fine. He said Google Cloud is taking an important step by providing built-in threat detection of unauthorized crypto mining, backed by real financial protection available to security command center premium customers. If an attacker evades their detection defenses, you know, they're there to back you up. This shared f approach to cloud security helps increase confidence among enterprise buyers when moving to the cloud. Then of course, this is also, you know, this helps Google, right? Because they've got in their whole infrastructure, everybody is sharing this pooled compute resource. So they don't want it to be drained off by you know, a bunch of undetected malware, which is reducing the total amount of, of comp of, of compute that is available to ev everybody who's paying for the cloud service, they may not mind if you pay for it, but still they <laugh> it's probably a good thing.
(00:23:11):
You gotta wonder, I mean, this is, it's kind of a shame that crypto exists at this point. I feel like it's, the negatives of crypto have really outweighed any benefits. You know, I hadn't thought that Leo, but you are absolutely right. You know, it was, we, we talked about it gosh, we thought it was, it was interesting, you know, it was a really cool, you know, sotoshi is an original paper and all of that, but as it turns out, it just really enabled ransomware and and this kind of crypto mining hijack and, and, and all this speculation people losing their shirts. You know, I, in fact, it, I did, it didn't make it into the show notes this week, but the f Coinbase and Binance have both been sued by the S E c Yes, yes. Unregulate securities exchanges, but yes, but, but also the, the very first exchange that fell Mount GOs, it took, it turns out that 1.7 some billion dollars of, of, of current value in Bitcoin was slowly siphoned out of Mount GOs over years before the, they, it finally went under.
(00:24:26):
So it's interesting. I hadn't thought of that, Leo, but you're absolutely right. I, I agree. Not to mention the, the environmental impact of all these servers, you know? Yeah. Cranking up at hive speed. Yeah. Niagara Falls is much warmer now <laugh> than it used to be. There is got, there's not gonna be any ice this summer in the Arctic, and I think you can blame Bitcoin, huh? I plan to, anyway. <Laugh>, geez. Well, speaking of blaming people while we're on the topic of Google Cloud Services billing, and even though this is a bit more gossipy than our usual fair, but since it is potentially an intriguing event in our industry, I decided to share the news that Elon Musk's Twitter has reportedly been refusing to pay both its Google Cloud and Amazon a w s bills in an apparent StrongArm play to renegotiate its preexisting multi-year contracts, which Twitter has signed with both service providers.
(00:25:26):
And this has been going on long enough now to lead both companies to independently begin threatening termination of services. Wow. In the case of Google Cloud, this reportedly leaves Twitter's trust and safety systems, which maybe Elon doesn't care that much about hanging in the balance as Twitter's contract with Google Cloud services comes up for renewal this month. And we're, you know, we're about mid-month at this point. Although Twitter hosts some services on its own servers, the company has long contracted with both Google and Amazon to compliment its infrastructure. And prior to mu Musk's acquisition of Twitter last year, Twitter has signed an extensive multi-year contract with Google to host services related to, among other things, fighting spam, removing child sexual abuse material, and protecting its users' accounts. So those facets of Twitter's services might be, eh, well, you know, we'd like to have them, but, well, you know, Google wanted us to pay, so, sorry.
(00:26:36):
Anyway, aqui <laugh> after acquiring Twitter, Musk reportedly issued a blanket mandate to his minions requiring them to cut 1 billion from Twitter's infrastructure costs. So it may be that he feels that playing hardball with Google and Amazon is the way to at least begin the process of renegotiating those agreements, which predated his acquisition. You know, we've previously heard stories about Twitter choosing to default on its existing, you know, physical office lease agreements. Yeah. you know, and if Twitter manages to cut a billion dollars from its infrastructure costs, as I said, it may be eliminating the cost of various protective services it's able to provide to its user community. Yeah. Well, who needs them? Wow. That's, yeah. You know, yeah. Don't kitty porn. Well, what, what are you gonna do? You know, we can't wa we can't look at everybody's feed. Over on the Amazon side, since Twitter has also been delaying its payment for Amazon's web services, Amazon has reportedly been threatening now to withhold its advertising payments to Twitter, which would of course impact Twitter's revenue.
(00:27:56):
So maybe that'll get Elon's attention. Anyway, it all seems like a big mess, but, you know, messes seems to follow Elon around, so we'll see what happens. Anyway, I just thought I ran across it. I thought, well, okay, we're on the topic of paying for cloud services. So Elon says we don't have to as our listeners know, the risks posed by the rapid uptake and proliferation of today's not yet really secure i o t devices has been a constant source and topic of concern here. Last Wednesday, June 7th, the report published by Nokia's threat intelligence team gave these concerns some numbers. Here's what Nokia's report explained. They said the latest Nokia threat intelligence report released today, which was last Wednesday, has found that I o t botnet DDoS traffic originating from a large number of insecure IOT O t devices with the aim of disrupting network services of for millions of users, increased fivefold three over the past year following Russia's invasion of Ukraine and stemming from the growing increase in profit driven hacking collectives operated by cyber criminals.
(00:29:28):
And Leo, yes, paid for by cryptocurrency, Uhhuh <affirmative> in cryptocurrency. This sharp increase also supplemented by the increased use of iott devices by consumers around the world was first noticed at the beginning of the Russia Ukraine conflict, but has since spread to other parts of the world with botnet driven DDoS attacks being used to disrupt networks as well as other critical infrastructure and services. The number of I o T devices bots engaged in botnet driven DDoS attacks rose from around. Okay, so this is the number of iot o t devices rose from around 200,000 a year ago to approximately 1 million devices generating more than 40% of all DDoS traffic today. So once it was that, you, you know, you were commandeering big iron servers where you could, cuz they had big pipes connecting them to the internet and lots of, you know, network juice and you could pump out a lot of packets.
(00:30:47):
Now we're distributing, we've got a million iott devices, you know, each on residential internet connectivity. But boy, you take the typical residential internet and multiply that by a million and well, we've been talking about the size of recent DDoS attacks. They're just astonishing in size. So Nogi has said the most common malware was found to be a botnet malware that scans for other vulnerable devices a tactic associated with a variety of iott botnets. There are billions of iot OT devices worldwide, ranging from smart refrigerators, medical sensors, and smart watches, many of which have lax security protections. The threat intelligence report also found that the number of Trojans targeting personal banking information in mobile devices has doubled to 9% putting millions of users around the world at heightened risk of having their personal financial and credit card information stolen. The report, however, did find some encouraging news showing that malware infections in home networks declined from a covid high of 3% for persist.
(00:32:09):
Still 3% of home networks infected it cut, it was cut in half to 1.5%. Wow. And and they said still, yeah, close to the pre pandemic level of 1%. So hasn't that's dropped back down. That's a good job done by Windows, I think primarily by Microsoft, and I would think that's probably the case. Yes. Yeah. Yes. They said as malware campaigns targeting the wave of at-home workers tapered off and more people returned to office work environments. These findings are based on data aggregated from monitoring network traffic on more than 200 million devices globally. That's Nokia's view into the internet where Nokia net guard endpoint security product is deployed. Nokia's, senior vice president for business applications said the key findings in this report underline both the scale and sophistication of cyber criminal activity today. Of course, that's something we've been noting here constantly. This is, you know, the world has changed.
(00:33:15):
It was at the beginning of this podcast, it was, oh look, I wrote a worm, you know, now it's okay, how mu you know, like there's now a a a a dark net, which is saying, okay, we've got 200,000 I o t bots in our net. Pay us and we'll aim them wherever you tell us to. So it's completely different complexion today he says a single botnet DDoS attack can involve hundreds of thousands of iott devices representing a significant threat to networks globally to mitigate the risks. It is essential that service providers, vendors, and regulators work to develop more robust network security measures, including implementing threat detection and response as well as robust security practices and awareness at all company levels. And, you know, we've, we've offered observed Leo that a lot of this is spoofing ips. Unfortunately, when you've got a million individual i o T devices, they don't even need to spoof their ip.
(00:34:20):
No one cares if they get identified, it's some light switch or some plug. Right. You know, that just like, there's too many of them to, to deal with. You just have to, you know, do what CloudFlare does and, and bring up transient defenses in order to block, you know, block connections at the perimeter and prevent it from getting through. The darker interpretation of this is not that our computers are more secure, but that malware creators are going to the softer targets and iott and there's no softer target than iott. Right? Right. They don't care if it's a toothbrush. Right. That's generating iot, OT traffic or Right. You know, a mainframe Right. To, to them. All they are is packets, packet missiles that they're able to launch at, at, at a temporary enemy. I suspect that's really, that's the real reason. It's just these targets are easier to compromise.
(00:35:14):
Well, and now why is it happening? They're getting paid. Oh, they're money in it. They're, they're, oh yeah. There's not, yes. It's now a business. It's a business rem remember in the beginning, the original botnets were script kitties who were blasting their, their, their, their competitors was of IRC surfers. Yeah. Have you the new, or are you gonna read the new book about Fancy Bear or It's called Fancy Bear. It's really a good book. I recommend it. Oh, okay. I takes, I, it starts with the Robert Morris worm, but he takes five well-known malware attacks, fancy bears, one of them, and talks about it. His final conclusion is interesting is because he's interesting, is because these are touring machines, then they cannot be secure. It's just the nature of it. They can do anything including malware and they always will be, but, but I didn't, you know, pro aircon on that.
(00:36:07):
The stories themselves were great and fancy bear to your point which eventually became the Mira botnet and all of that. The kid who did Mira, I wasn't Fancy Bear, it was the kid Fancy Bear's a Russian group. Right, right. The kid who did Mira was a Rutgers student in his freshman year. He was pissed off that Rutgers wouldn't allow underclassmen to take the computer science courses he wanted. So he wrote his first DDoS attack to take the Rut Rucks network down so nobody could register for any classes, but to your point, and then later became more malicious and he did Mariah and eventually got caught by the fbi. It's a really good story that's been excerpted. You can read it around if you want. Cool. Sounds great. Yeah, yeah, yeah. Really the book is called Fancy Bear. That's why I was thinking of Fancy Bear.
(00:36:57):
Ah, right, right. That's a good title for a book, <laugh>. Yes, it is. It it's really much more catchy than a p T 28. Yeah. That's just, that's not gonna jump off the shelves or the G R U or whatever. Yeah, I agree. Yeah, a hundred percent. Okay, so get a load of this one. So a guy named Matt Holt, oh, actually this would be a good time for our listeners to get a load of our sponsor. Yes. And then Matt, yeah. Sponsor first. Matt second. Of course. I just bit a crunchy thing. So <laugh>, you want to let me chew for a little bit? First <laugh>, then it's our advertiser. Oh, it's a good one too. It's time to talk about Bit Warden. I love talking about Bit Warden. Yeah. bit Warden is my password manager. It's the one, you know, after a couple of, you know, for many years we talked about another password manager and after they had some severe issues I said, I gotta, I gotta do something better than this.
(00:37:57):
And I switched to Bit Warden. First of all, the switch is easy and and you know, it literally took a few minutes to export all my passwords from the old password manager. This is true of almost all password managers and imported into Bit Warden and I was up and running in in a few minutes. But why would you shift to Bit Warden? For me, it was, it's open source. I really like that. And it's the only open source password manager that's cross platform. It's on everywhere I want to be. There's even a command line version for Linux. And it also, the other reason I I, I fell for Bit Warden was I can use it personally, but you can also use it at work. So it works on your, all your mobile devices. It works on all your desktops, and there's an enterprise plan as well.
(00:38:45):
All of those were really critical factors in my decision. We're gonna, we're switching the enterprise plan here at twit. We were on that other password manager. I switched to Bit Warden a while ago. You did too. They did a very famous show in which you described why you made the switch. And I think I don't know if you're still happy, but I am very happy. Bit Warden does everything right and because it's open source, there are people contribute to it. So we were talking a few months ago about the fact that pbk DF two, the key derivative function that's used by everybody up to this point isn't memory hard, has problems, needs a lot of iterations. Most companies don't sit there at iterations high enough. In the case of laspas might be as low as one, which is effectively no iterations at all.
(00:39:37):
So you talked about Sry and argon argon two as memory hard key derivative functions. So a guy named, I think his name is Oxen, had literally, I think he's a listener to the show, written both implementations for both and Pull submitted a poll request to Bit warn bit Warren's open source. They said, we like that. Let's focus on one. They got the Argon two implementation down, it works, and now it's an option for all Bit Warden users. And I immediately switched to Argon two. I had my pbk DF two set to 2 million iterations, the maximum, but now I've got Argon two, which is not slow me down. But that's a really good example of why the open source you know, ecosystem is a probably a better way to go with something as critical as your password manager.
(00:40:26):
It's on GitHub. Anybody can see it. You don't have to take their word for it and people can contribute it and it can get approved. It's of course they, they do professional third party audits every single year. Publish the results on their website. I mean, you should never fear that Bit Warden is as good as it can get for a password manager. They just launched their new Secrets manager. This is now in beta. It's an end-to-end encrypted solution designed to allow teams of developers to centrally secure manage and deploy secrets. We've talked about this before. People sometimes <laugh> surprisingly often when they do a GI commit, for instance, to up to GitHub push the API keys or the API secrets <laugh> up. And this is why, you know, ad s AWS S three buckets are often hacked. Those credentials often get published publicly. And of course then that's a massive security problem.
(00:41:19):
The bit wardens Secrets Manager keeps those a p i keys and machine credentials. Secret encrypted not in your source code, but you can share them. So everybody working on a program can use them without risk. Bit Warden needs developers who wanna test out the new Secrets manager and provide feedback. So if you're interested this is great bit. This is another reason I just love Bit Warden. Would you like to help us develop this? Yeah. Okay. Here. Bit warden.com/secrets beta. Okay. And you know, you may not be a developer, but we all get the benefit of this work that's happening out in the open. Lots of people contributing, making Bit Warden better and better and better. If you're a business like we are, you might wanna check out Bit Warden's team organization option $3 a month per user. They have an enterprise organization plan.
(00:42:11):
That's the one we're gonna use $5 a month per user. And what I love about Bit Warden is the basic free account for individuals is always free. Free forever. Not, it's not limited free, it's just free if you want. As I do I want to use two factor. I wanted to use my YubiKey with it. So I pay $10 a year, $10 a year for the premium version of that. And now I furthered secure my bit warden with my YubiKey. I mean they just do everything right. If you're a family, take a look at the family plan. Six users. You don't even have to be blood relatives. Six users, $3 33 cents a month total. So, you know, get your, get your clan together and and use Bit Warden y I don't need to tell the Security Now audience, you need to use a Password Manager.
(00:43:00):
The only question is which one you're gonna use. I strongly recommend Bit Warden. You gotta use a Pass Manager use Bit Warden, the only open source cross-platform password manager you can use at home on the go at work, trusted by millions of individuals, teams, and organizations worldwide. You can get started right now with a free trial of the teams or enterprise plan or as I said, as an individual free forever across all your devices, unlimited passwords, bit warden.com/twit. Please use that address cuz I want bit Warden to stay on, on the show forever. I want them to know they get the results by being on the show. So if you haven't signed up or you wanna try it for free, bit warden.com/twit, they are doing a, I think you'd agree, Steve, they're really doing it right. I do. And I think every listener understands that it's just not possible to operate today without a password manager wish.
(00:43:54):
And, and Paske is not gonna change that cause it's not gonna happen in our lifetime. So, you know, using, as you know, bit Warden did acquire a company that does pass keys. They are moving forward with pass keys just as the other guys are. Yep. They're not ignoring it by any means, but you're right. Nope. I mean, it's not gonna replace passwords. It's, it's, it's a good thing and it's, it's the way we move forward. But, you know, you're still gonna need something else to, to remember your passwords for you. Yep. Okay. So a guy named Matt Holt wrote a nice little web server in the Go Language. He calls it Caddy Server, you know, as in Caddy Shack, caddy Server, and describes it as an extensible cross-platform open source web server, written and go. The name caddy refers to both a helper for tedious tasks, you know, like, you know, someone carrying someone's golf clubs and a way to organize multiple parts into a simplified system.
(00:44:53):
Okay? So we've established that Matt knows his way around web server technology. He was experimenting with acme, which is, as we know, the protocol created by the EF F'S Let's Encrypt project to automate the issuance of TLS certificates. You know, the idea being that it allows the server to proactively ask a certificate authority to please refresh its cert because under the Let's Encrypt model certificates only last 90 days. So you wanna automate that process so that you're not having to do it constantly. Okay. A low budget Chinese certificate authority named high ca h, capital H lowercase i capital C, capital a high ca only, only supported one particular Acme client. Oh, that's suspicious. <Laugh> Uhhuh <laugh> for, for its customers servers. Right? Because if it's an open protocol and it is, it should not matter. Matt found this odd just as you did Leo, you know now this, this client, this one particular Acme client is open source and it's over on GitHub as acme.sh.
(00:46:16):
So here's a bit about, here's a bit of what Matt wrote. He said, hi CA's documentation. That is the documentation, you know, with this certificate authority explains that it own as a client. This was curious to me. So I tried to learn why if it's using Acme, and this is the thing that really got him the Acme logo, it should be basically compatible with the majority of Acme clients. While observing a certificate using Acme's, I discovered that the discovery was blocked. And this is like details of the protocol we won't get into, cuz you'll get the gist of this. The discovery was blocked unless the user agent is set to a string that starts with Mozilla or acme.sh/two 8.2. Once I faked the user agent in my own client and got that working certificate issuance still failed. Curiously, the error message involved trying a URL of.dot meaning, you know, backup in a hierarchy.dot/pki hyphen validation.
(00:47:34):
This doesn't make any sense to me, even though that kind of appears in their docs because it's not standard Acme. So I dug a little deeper to figure out what the challenge object consisted of that would cause my client to be making a request to.dot/pki hyphen validation. It turns out that the challenge object looks unusual and it became immediately obvious to me why High ca only supports Acme sh they're not conforming to Acme at all. And he says, Prez bugs the heck outta me that they're using the official Acme logo on their site even though they don't implement the Acme standard. And he says, instead, high ca you're sitting down Leo high ca is stealthily crafting curl commands, <laugh> and pipe go ahead and piping the output to bash <laugh> a Acme s h is being tricked into what possibly go wrong. <Laugh>. Oh, Acme do ch is being tricked into running arbitrary code on the remote server.
(00:48:56):
Oh, okay. So let me <laugh>, lemme make that a bit clear and filled in additional details. So a small Chinese certificate authority requires their clients, their users, you know, their customers to only run a specific acme.sh Acme client specifically because this particular open source client has a bug, which the ca has been exploiting to cause their clients' web servers, their customers' web servers to remotely execute arbitrary code and commands on their own servers. Oh my God. Wow. Now obviously no one should ever run code meaning Acme clients that they don't trust on their servers. And if some certificate authority tells you that they support Acme, but only one specific Acme client, you know, even if their certificates are free, run away as fast as you can <laugh>.
(00:50:09):
So this is probably the Chinese Communist Party Chinese government Oh, Leo setting this up Plot Mike. They're trying to take over our children. No, but they're hoping that some, you know, foolish industrial enterprise will use this server <laugh> so they can keep an eye out. Right? I mean, I don't think it's hackers, it's probably the government who knows, right? No, well, from, based on the di I read the GitHub thread discussion. The guy behind this high ca got involved when this became a controversy and he appears to be benign and goodhearted. But then of course if it was actually the evil Commies then, you know, he would he explained that doing this allowed him to have more flexibility. Oh yeah, ya Oh yeah. And if he's, he's able to run whatever code that he wants on your server that's flexible.
(00:51:04):
The Acme could be benn, it could really be just some kid, right? Yes. You know, I think it was, I think it was just he saw a bug and he decided to use it. The Acme sh maintainers immediately fixed the bug that this high ca guy was exploiting for their service and high ca shut down and closed its doors. It wasn't a big deal. Oh, he was affiliated with some other ca Okay. He wasn't, it was, it was not quite free, but it was like $3 and 12 cents or something. So, you know, he wasn't making a lot of money and he said, okay, fine, I'll just stop this because this isn't fun anymore. Yeah. But still, you know, everybody who was using his certs was having his code running on their computers Christmas. So it wasn't the server, it was a certificate authority. Yes.
(00:51:55):
The Certificate authority has has a, so so he found a bug. I get it. He found a bug in the server that he was able to ex exploit. I get it now. Yes. Yeah. He, he, he found a bug in the Acme do sh client. Right? So, so, so they, his, his customers had to run by his instruction, the Acme dos.sh client in order to u to to get the search from him. And the way they were getting them from him is he was saying, okay, you want a a, a new update? Let me get, I'm gonna run a little code in your, your server <laugh> in order to make that happen. Sure. <laugh>, what could possibly go wrong? <Laugh>. And we never saw it a malicious attack from him. No, no, no. So maybe he was completely benign, right? I I think so.
(00:52:42):
But again, this is the way we keep these things from, you know, escalating. Yes, exactly. And Bravo to, what's his name Matt Volt for, for finding this? Yep. And, and, and writing it up and use Let's Encrypt. Please just use, lets exactly. Why do anything else use the one everybody uses that every that's been vetted and had, you know, real security people, you know, writing it, maintaining it. I, I I don't get the need for additional Acme clients. But again, when we're, you know, it's op it's everything's open and it should be, but you know, it does not prevent bad ones from being written. And you know, you know, I see some cars, Leo with there have been painted a that should not have been allowed <laugh> to leave like the garage cars. Forget it. We've got Victorian houses painted that way up here.
(00:53:35):
<Laugh>. Oh, fluorescent. Oh yeah. If they build it, somebody will use it. Somebody will use it. Yeah, that's right. So what a wor what a world. Okay, so Apple's 2023 Worldwide Developer Conference is now behind us with, and it was very interesting. Apple did not disappoint with their continuing focus upon the privacy and security of their users. It's very clear that they intend to offer both privacy and security as features of their products and technologies. For example, during the presentation of their new mixed reality vision goggle system, they made a point of noting that the system's quite powerful. Eye tracking technology creates an inherent privacy risk, which at first you think, huh? But social scientists have long understood where a user's eyes look when confronted with an image reveals with surprising fidelity, the innate emotional power of the content of various parts of an overall image.
(00:54:46):
Now interpreting what that means exactly may be problematic, but it's still an unintended gateway into a user's mind. So when we ask the question, you know, do you want a webpage you visit to know where you looked on that page? Less privacy centric developers might think that would be quite cool and might sell it as a feature. Oh yeah. You know, we, we we do heat maps that, you know, to see what people are looking at. Yeah, yeah. It's a usage thing to find out how they use the site. Yeah, exactly. Like, you know, having a virtual mouse pointer automatically jump to that location where then a page's Java script is able to obtain its coordinates and relay them back to the mothership. But that's not the way Apple thinks. Apple was quite clear in their presentation that where a user's eyes were looking was private information that would never leave that device.
(00:55:52):
Good, good. Yes. Only. And then again, this is Apple on our side. Only when they looked and clicked, which means, you know, did a little finger pinch thing, would the location of that click be returned just like clicking the, the mouse pointer on something. So it, it's, it's this pervasive attitude across Apple that led me last week to opine that there's no way Apple has deliberately supplied anyone, including our own, with a robust backdoor through iMessage to launch i i device malware. That's just isn't something they're gonna do. Okay. So back to the last week's ww d c although this year's advancements did not explicitly focus upon user security to the nearly, to the degree that they did last year, that was a big focus of WW DC 2022. Apple still demonstrated that this continues to be a selling point for them and they're gonna sell it.
(00:56:55):
So for their Safari browser, apple says that they've added additional tracking and fingerprinting protections which go even further to help prevent websites from using the latest techniques to track and identify a user's device. You know, this is the constant cat and mouse game and they're just continuing to tighten it up. Also, Safari's private browsing mode now locks when it's not in use to allow a user to leave private tabs open even when they've stepped away from the device. Safari will now show a locked browsing window and request a touch ID or password or face ID in order to unlock and view those tabs and safari's. Private browsing windows now automatically lock as a whole if they've not been in re in in use recently. So nice moves there in photos. A new embedded photos picker can help users share specific photos with apps while keeping the rest of their library private.
(00:58:01):
So they've made it, they, they've, they've made it more granular when users ask to access the, when, when, sorry. When apps ask to access the user's entire photo library, the user will be shown more information about what they'll be sharing along with occasional reminders of their choice. And I think that is so important. This notion of occasional reminders that previous permissions remain in effect represents a significant advancement in our understanding of the human factors side of how to offer security and privacy. It's so easy for us to grant a permission in the moment when we wanna make something specific happen, but then to leave that permission enabled well after it's no longer appropriate. So a general nudge to a, to ask, huh is this still what you want? Is that just brilliant privacy enhancing tactics? So in the case of photos, the photos permission prompt now tells users how many photos and videos they would be giving access to, as well as providing a sample of those photos.
(00:59:17):
AM is also moving to apple is also moving to, to curtail the surreptitious link tracking, which occurs in messages mail and safari's private browsing. It's becoming commonplace, more commonplace for websites to append extra information onto their URLs as a means of tracking users across sites. We've talked about, you know, this years ago how the referrer header informs advertisers of the u r URL of the page, which is pulling the ad If this U R L is needlessly embellished with, with enhanced tracking info, that information gets sent and there's all, and there's been no way to automatically limit this. Apple says that they're changing this or will be this fall in, in iOS 17 by silently removing this unnecessary information from the links user share in messages and mail and from the links in safari's private browsing and what Apple calls communication safety is also being further advanced.
(01:00:30):
Communication safety, which has been designed to warn children when receiving or sending photos in messages that contain nudity now also covers video content in addition to still images. And the new API lets developers integrate this communication safety into their own apps. So this would allow these warnings to be present in non Apple apps as well. And this communication safety will now also help kids help kids keep kids safe when they're sending and receiving an airdrop, a FaceTime video message. And when using the the phone app to receive a, a contact poster and the photos picker to choose content to send. So it's perva, you know, they're basically, they, they, they launched this under 16 verified that it's working and now they're, they're, they're confident enough to extend this out in, into additional apps that could be problematic. All image and video processing for communication safety occurs only on the device so that neither Apple nor any third party gets access to the content.
(01:01:45):
And as we've talked about before, these warnings will be turned on for the child accounts in their family sharing plan, which can be disabled by the parent. A sensitive content warning is shown in messages in the in the iPad Pro, what they, what Apple calls communication safety is what protects children receiving or attempting to send videos or photos. And the same protections are available for adult users in the form of a sensitive content warning. The features optional and can be turned on by the user in privacy and security settings. And as with communication, safety, all image and video processing for sensitive content warnings for adults occurs on the device, meaning that nobody else gets to see it. There was some some conversation of this as well. I think I saw it on some of the podcast, Leo, probably on Mac Break weekly.
(01:02:47):
Apple has also added passwords and passkey sharing with the creation of sharing groups, which is, you know, totally makes sense to do. Users can now create a group to share a set of passwords and everyone in the group can add and edit passwords to keep them up to date as needed. And in a slick new feature that I want to see in action. One, I don't, this'll be really interesting to see. Apple says that one time verification codes received in mail will now automatically auto fill in Safari without the user leaving the browser. Okay. So, okay. It sounds as though, so you're on a webpage that sends you a link or, or, or that, yeah. Where, where, where the, the webpage wants you to authenticate your email address by giving it a six digit code or whatever. So it says, we've sent you email, please populate this field with your code.
(01:03:57):
Apparently iOS will be observing that empty and waiting field and also notice that you've just received email in the background, which contains a code. So it will parse the email for the code and populate the one time code field in the browser so that it just appears. And then you just click on, yeah, there's your code, and it happens. So, wow, I can't wait to see that happen. You know, in front of me. That'll be very cool. We've talked about apple's lockdown mode, which signif, which significantly reduces the iPhone attack surface by dramatically restricting the content that the phone will accept and process. Apple is pushing this technology now even further. This was also the first time I've seen the term mercenary spyware anywhere. I love the term I'll, I'm gonna be using it. These new lockdown protections encompass safer wireless connectivity defaults, media handling, media sharing defaults, sandboxing, and network security optimizations.
(01:05:10):
So now when we get this in iOS 17, enabling lockdown mode will further harden device defenses and strictly limit functionality all in the name of security. And I think that makes a lot of sense. Oh, and it's also coming to watchOS. When you enable lockdown mode on your iPhone that is paired with your watch, the watch also gets locked down. So, you know, it's not like they, they've left a way in by sneaking in through your watch. Also Apple has something that they're calling check in, which is an interesting new feature. I'll just share how Apple described it. They said check in makes it easy for users to let friends or family members know they've reached their destination safely. Once turned on by the user check in automatically detects when the user has reached their intended destination, and will let selected contacts know via messages in the case that something unexpected happens.
(01:06:15):
When the user is on their way, check in, will recognize that the user is not making progress toward their declared destination and check in with them if they don't respond. The feature will share useful information like the user's precise location, battery level, cell service status, and the last act of time used that they used their phone with the, with the contacts and the users selected. In addition to making it easier to get help if needed. Check in is designed around privacy and security. Of course, it's Apple. Keeping the user in control by letting them choose whom to share with whom to share their information, including the destination and time duration that they set. Users can end the check-in session at any time, you know, canceling it, information sent with check-in is end-to-end encrypted, so only the user's, family member or friends who have been authorized are able to read it, not Apple or anyone else.
(01:07:20):
So again, just to kind of, you know, like some, somebody at Apple saying, what new service? What, you know, what, how el how else could we help people, you know, leverage the technology that they're now carrying in their pocket? And so they created another one. Name drop is another new feature, which allows for tightly controlled contact information sharing from one device to another, presumably enabled through nfc since the devices, you know, basically need to be in super close proximity, if not touching. And finally, a brilliant innovation, which they call live voicemail, allows the recipient of a phone call that they've chosen to let you know, go to voicemail, observe a real time textual transcript of the voicemail as it's being recorded on their phone, and then change their mind on the fly to pick up the call. It's the brilliant modern equivalent of how we used to use residential telephone answering machines to screen calls.
(01:08:36):
And then, you know, we'd, we'd grab the phone receiver to pick it up, you know, claiming that we had just walked in the door while they were leaving the message and heard them leaving it when, you know, a after we heard who it was or what the call was about. So now we have the same thing on our smartphones. All these goodies will be arriving later this year, presumably with iOS 17. And, you know, big props to Apple for, you know, doing you know, continuing to, to raise the bar on security and privacy. And, you know, I think doing everything that they can for their users and, you know, clearly selling these features as part of their product offerings.
(01:09:18):
Now, not exactly following Apple's. Example, we have France <laugh> who last Wednesday evening, June 7th, the French Senate passed an amendment to its so-called Keeper of the Seals Justice Bill. And I have no idea where that name came from, the approved changes which passed last Wednesday. Now, a law allow law enforcement agencies to secretly activate the cameras and microphones of remote devices and specifically smartphones without notifying the device's. Owner officials say they plan to use this new provision to capture sound and images of suspects of certain types of crimes. The measure would be reserved for cases of delinquency organized crime and terrorism delinquency. Okay? The same update to the bill text would also allow law enforcement agencies easier access to geolocation data to track criminals suspected of committing offenses punishable by at least 10 years in prison. What's not mentioned is exactly how they intend to make this actually happen in practice.
(01:10:41):
I had Google translate the French news webpage and they were saying that without this provision, investigators would need to plant physical bugs on the premises of their investigation targets. So this was being sold as a safer means for allowing their investigators to accomplish the same already legal surveillance. You know, like if you get a warrant to plan a bug by instead targeting their target's phones and turning the phones and other devices into surveillance equipment. Now we know that Apple's iPhones will actively resist any such abuse. You know, there's no way to ask an iPhone to do that. But what wonders whether this might be paving a legal framework for the use of, to use apple's new term, mercenary spyware, such as Pegasus, which would subvert smartphone protections and would then within the bounds of this legislation, no longer represent illegal spying, which the country needs to deny and be ashamed of.
(01:11:58):
So, France did this last Wednesday evening. Hmm. Yeah. Hmm. okay. So it chi come as no surprise to anyone that Russia has decided to begin blocking foreign vulnerability scanning at the incoming border of our U net, very much like their continuing use of Microsoft windows. My reaction to that is you're only getting around to doing that now, really? So, you know, there are services like Shodan and the one we're gonna talk about at the end of the show census. Typical you know, services. There's also other security companies and proprietary scanners, which are more or less, we know this constantly poking around the entire internet to see what they can find. When some security firm notes that, for example, some new vulnerability in a Cisco device affects more than 34,000 of them, well, that number comes as a result of scanning.
(01:13:13):
That's how we know there's 34,000 of them out there hanging out on the internet, just <laugh> waiting to hopefully get updates. So it's entirely reasonable for an increasingly hostile foreign nation, you know, like hostile to the rest of the world not to want anyone poking around in their backyard. And wouldn't you know it, the responsibility for limiting such scans falls to our favorite Russian internet watchdog Ross Comor. In their announcement of this plan, they stated that more than 10 such services are constantly scanning inside their Russian r u net for vulnerable systems that are then exploited in cyber attacks. And that number of scanners, 10. Okay, that sounds about right. The trouble is to at least degree the scanners you know about are not the scanners you need to worry about. Showan and census operate above board and scan from publicly known blocks of IP space.
(01:14:25):
So blocking them if one chose to, would not be difficult. But as anyone knows, who's ever tried logging all of the individual IP packet traffic arriving at any arbitrary I P V four address today, there's more or less a continual flux of incoming noise. And as our long-term listeners know long ago I coined the term internet background radiation to remind us of exactly that. My point is, all of the IP space of Russia's r u net is also constantly receiving this random noise flux, and it doesn't make sense to block at all, even if you could, there's no way, for example, for any central authority to know which traffic to which port is part of the services legitimately being offered there and for whom those people want that, those incoming packets, you know, look at what a mess, for example, some cable providers make when they decide to block some ports that they don't think their subscribers should be using. It's, it's not always good. So my point is, if some of those random seeming packets were actually carefully aimed NSA probes, Russia would never be the wiser. The packets they do need to worry about would never be the ones belonging to the well-known public scanning services, which, you know, they've now said, okay, we don't want you anymore. And so they'll be blocked.
(01:16:13):
Okay? we've got some well, actually one piece of miscellaneous and some closing the loops to tofus Tavis Ory whom we have quoted through the years. You know, he's at T A V I S O Tavis Orandi at Google on Friday, June 9th, last Friday. He tweeted Quick personal update. It's nearly 10 years since at Scary Beasts, and I started Project Zero. A lot has changed since then, and I've decided there are teams where I can have a bigger impact. I'm still at Google and still working on vulnerability research. I'm going to work on C P U Security with Google ise. That's the independent security evaluators we've already got. And he's got like three flame emojis. He's already, we've already got zero day reports on the way. So we're gonna be seeing some interesting, and especially interesting if they're CPU U zero day reports, you know, that's different than spectrum meltdown, which are, you know, this might not be good someday.
(01:17:31):
These are we just hacked your C P U. So stay tuned. Tavis moved, but he's certainly not gone. Dave Johnson sent, Hey, Steve, big fan of the show. I heard your stat in episode 9 26. So that was last week about school districts lacking security staff having worked in K-12 and community colleges. I have some background. Many school districts are small. I e one or two schools, they may, they might have one or two technology staff running the whole show. My last job was it director for, for a district with 7,000 students, 14 schools, which had two desktop techs, server admin, network admin, data, mace, admin, secretary, and a director. He says that's not an unusual load. It's not that the districts don't care about cybersecurity. They're having a tough time just keeping all the technology running on a daily basis. And I can well imagine that.
(01:18:40):
So David, thank you for the the viewpoint from the trenches, from the front lines. Mr. Lennox 11, he said, getting error going to grc.sc/ 9 26. And this was sort of interesting because it was in a tweet and there was a link. I clicked the link and I got the error two, and I thought, uhoh, so I looked, and the browser had https slash slash www.grc.sc/ 9 26, and there's no www. So that's an interesting sort of bad behavior on browsers because I never said www, but we do know that this is, and this is one of the things we've talked about, some web browsers have, you know, taken it upon themselves to probe www dot, you know, I'd like to add that to the url. Now, that won't resolve you know, on GRCs dns, there's no, there, there's no resolution to that.
(01:19:59):
So you'd hope that the browser would back away. Anyway, I'm not sure how the www.got there, but for any of our listeners who may have had trouble, you know, that was the shortcut for the registry. The, the, the, the little tiny registry reg file, which turns off windows querying and running any startup code when your machine boots, which are being plot which are being supplied by the motherboard. So no, www in front of the GRC sc slash 2 96. So thanks for to Mr. Lennox for bringing that to my attention. Andrew Draper sent, while the iPhone is quite locked down, the Mac less so iMessage accounts are synced. Why can't these self deleting messages be captured on a Mac? And I thought that was a great observation. Now, you know, the problem of course, is that these attacks are highly targeted.
(01:21:03):
So you'd, it'd have to be the coincidence of a user who was targeted having a Mac. And what we don't know is how long the actual attack took. That is the iMessage arrives, it has an attachment, the attachment auto executes, it causes some other stuff to be downloaded from the command and control server. Those execute go persistent and then delete the attachment and the message. So that could be a few seconds, right? I mean, this all blink, blink, blink, blink, and now the, the, the malwares has been, is in place and the message is gone. So presumably iMessage deletion also propagates, and there may not be any chance to, to grab it, but if there, if it was, if it is the case that that deletion doesn't propagate and somebody had a MAC synchronized to their phone, logged into their account and was a target, then yes, the planets could align and maybe it'd be possible to capture that.
(01:22:12):
What has to wonder though, and you know, Leo, you sort of mentioned this last week, and I I I, I think you had a really good point. If, you know, apple might not add some quiet forensic stuff in order to like just capture stuff, the problem is they're end-to-end encrypted, right? They, they don't, they, they don't break their own users' privacy. So this is the very important distinction. Messages are end-to-end encrypted unless you use iCloud storage for them, then they are stored in using a key that Apple has access to. Right? So that be, so that's the difference when they say, well wait, unless we do that other thing that they, that they just talked about, right? Where they did, they did remove that last key that they have from iCloud so that they no longer have it, nor by historically they have. But there was something that we talked about you know, like a month ago.
(01:23:19):
Yeah. That was if you turned on advanced protection though, right? So I think that takes it out of their hands. But it, but it's not on by default. Right? That is true. And it's not easy to turn it on. It's not easy. And one of the reasons it's not is because you have to have everything up to date, which tells me that there's some sort of key sharing as you point out. It's key sharing mechanism built into the latest that the, that the older devices don't have. That's right. Yeah. it's, this is unclear. We talk about this sometimes on Mac Break weekly, cuz Apple's not fully forthcoming. But we know, for instance, I mean, it's true of Telegram as well. Once you back up Telegram to iCloud, it's unencrypted or it's available. We know because Apple provided Telegram messages, Paul Manafort's telegram messages to a subpoena to the, to the law enforcement in, in response to a subpoena in it.
(01:24:18):
Response to a subpoena. So they have access to that I think unless you turn on apples, whatever they call it. Advanced protection. Yeah, yeah, yeah. The advanced data protection. Yeah. Yeah. I bet you that those iCloud messages are encrypted. Well, but not, and I wonder how, and then you gotta wonder how deep is the delete, like when it deletes it, does the delete propagate? Well, I would think so. Cuz they don't wanna store stuff unnecessarily anyway. Right? That's my thought too. Yeah, that's my thought too. So, yeah. But again, this is something Apple kind of believes in security through obscurity, and so they, they're very hesitant to really reveal, maybe there's a white paper somewhere, but I've never seen it exactly. What's going on, you know? Yeah. It's an interesting question. I don't know. I'll ask around Renee. Richie used to to be our expert on that, but Right.
(01:25:10):
Not anymore <laugh>. So well, and, and you know, they do maintain that beautiful security white paper. We used to go over it in detail. Yeah. But we've just been too busy lately. Yeah. And that's a very good source. But my, it's my understanding that it's only end-to-end encrypted if you turn on advanced data protection, I would guess. Yes. So Jared Neves says, hi, Steve. Hope you're well. I was wondering if you have any more book recommendations for us. I've enjoyed all the ones I've heard so far from you, but the last one I think I heard you talk about in security now was the Baba verse series, which was a while ago. PS just reread one of my all-time favorites. The Mote in God's Eye and its sequel, the Gripping Hand. Yes. Amazed, amazing to think they conceptualized smartphones and AI home assistance back in the seventies.
(01:26:02):
Jerry was, of course, yeah. He really knew his stuff that, that that was the, the team of Jerry Porn and Larry Niven. And they, I often ask Jerry, he says, I conceptualize, so the ideas come from Jerry and then Larry would do the write most of the writing out, I think. Yeah. So I they've the, some of my favorite books of all time so Good came from those guides. Yes. So good. Yeah. So I'd already forgotten about the Baba verse novels. They were definitely fun, and I read them all. We talked about them at the time mm-hmm. <Affirmative>, but somehow they didn't stick with me as much as some of the others, both old and new have. So I'm just gonna, I'm gonna quickly bring people up to speed. The series that I most recently read was Scott Yuhas, and that's spelled J u c h a, his Silver Ships series.
(01:26:53):
It was recommended to me by one of our listeners, and I am glad there are 24 books in that series, 20 in the main line, and four that are an offshoot which then merge with the timeline, a, a as that original series of 20 finish. That, that whole series had some truly wonderful moments and many terrific new ideas. So I'm glad that I read all 24 of those. There were an additional six books in his so-called Gate Ghosts series that caused me to do something that I almost never do, which was to quit without finishing. Now, this tendency of not quitting without finishing Annoys annoys my wife <laugh>, because we'll start in on some video streaming series, which after a few episodes, turns out not to be very good. She'll wanna abort, but my inclination is to see it through to the end.
(01:28:00):
Yeah. I want to know, I'm, I like, I'm into the story. I want to know what's gonna happen. I'm an optimist. I always think it's gonna get better <laugh> it never, rarely does. No <laugh>. So it's, it's very unusual for me to quit any sci-fi story In the middle, though I did quit the Gate Ghosts after I think two of its six books. I also, for that matter, quit Apple's Foundation series. Yep. To me too. My wife's great, my great her, her great relief. She says, oh, thank God we don't have to keep watching this <laugh>. That was pretty bad. Season two is coming is imminent by the way. I wanna finish. It was so disappointing, but, oh, I can't wait for the, for the second half. Finish season one so that you can be disappointed by season two. Ah, there we go. There you go.
(01:28:44):
Yes. dune, I can't wa wait Oh, for the second half. Lisas saying, let's watch Doo one again, cuz D two coming up. Yes, yes, yes. Absolutely. What a great movie that was. Yes. Anyway, the, the reason I dropped out of Gate Ghosts was a clear lack of action with no sign of any impending action. It turned into a mostly political narrative about the rights of sentient ais and cloned humans as slaves. You know, I'm gonna get bored after a while unless something blows up from time to time. Which leads me nicely back to my absolute favorite number one series in a long time, which is The Frontiers Saga by Rick Brown, where Rick is spelled r y k. Now, Rick was a bit slowed down by a heart attack. He suffered at two 30 in the morning last December 4th. Fortunately, thanks to very good e m s response, he suffered almost no lasting cardiac damage, but the cause was severe blockages in three of his coronary arteries.
(01:29:51):
So he underwent triple bypass surgery on January 16th. Happily, his recovery was complete, and he picked up right where he left off with his ambitious plan for 75 full-length novels. And maybe we're gonna get them all. So while reading the Silver Ship series, I had fallen four books behind when I switched over to, well, as I said, the, the the, the silver ships. Now I'm all caught up. And if I may have been just a bit unsure after starting into this third 15 book Arc that was quickly dispelled once we got to book three, I would love to share a bit about what happens. But there are some fabulous surprises awaiting anyone who is still, who still has some catching up to do. I'll just say that in Rick's work, there is no lack of action and plenty of things are blowing up all the time. Okay. So those are the two. That's what I look for in a book. <Laugh>. Yeah. Gotta have some stuff blow up <laugh>.
(01:31:03):
So those are the most recent two series earlier in this podcast I talked about The Honor Harrington novels by David Weber. There are 13 of those. They are wonderful and she's a great character. There's also Jack Campbell's Lost Fleet series, which is a also a ton of fun, nearly 10 years ago in A P D F, which is dated December 19th, 2013. So, yep. You know, almost two, almost 10 years ago, I captured all of my favorite reading recommendations at the time, which we had discussed here on the podcast. It's, I captured it into a sci-fi novels guide, which just now yesterday was, I was writing this, I reviewed it has the Honor Harrington series and the Lost Fleet series, and all of our Peter F. Hamilton discoveries you know, back then. So I've given it a shortcut using GRCs Shortcut service, and it is no, www, it is just g https slash slash grc.sc/oh.
(01:32:17):
It just occurs to me, I could have done the SC from the SC anyway. It's SC slash S C fi <laugh>. It would've been very confusing if you That would've been Yes. Too confusing. I Ffi <laugh>, you know, grc.sc ify <laugh> slash ifi. So GRC SC slash scifi, S C I ffi that will give you a pdf, which not, it's just not just a list of books. It's also some commentary a about how I felt about each book or series to sort of, you know, give you a little bit of guidance. And I, I'm gonna eventually at some point need to update that because I would definitely like to add certainly the Frontiers Saga, which is just so much fun. And, and Silver Ships, although Leo, I know you were not a fa a fan of, of Silver Ships. It was just a matter of style.
(01:33:09):
I'm not a fan of. Yeah, yeah, yeah. Okay. And I don't have to have things blow up regularly in my books. Oh, well, okay. <Laugh>, as long as you don't mind when they do, I don't mind when they do. Not too much though. Just a little bit of blowing up, you know, and, and, and, and all of those early Daniel Suarez novels, those were, those were quite demon had a lot of explosions. Yeah. That was an action Rich novel. Yeah. Yeah, I agree. Yeah. And I didn't mind that it had a pace. It had a real pace to it. Yeah. Yeah. I just, you know, the thing I don't like about Silver Ships is just the hero. He's just too Captain America for me. I just can't I get it. Yep. Yeah. Too. Perfect. I do. I like my, I heroes imperfect. Well, speaking of which I don't recall sharing any spin Right.
(01:33:56):
Testimonials since I began work on spin. Right. Six one. But we received one yesterday, which I thought was interesting. MI m e i r Mir in Montreal wrote, he said, hello, Stephen Team, my son became a university lecturer and was very busy developing his course materials. After many hours of work, he discovered that the server he was using had not synced the data reliably. So he pulled out his backup one terabyte USB memory stick only to discover that the computer could not even see it. He asked me for help. I pulled out my copy of Spin, right? 6.0, and it too did not identify the device. I then remembered that a few years ago, you read a testimonial from a user who cooled his hard disc in a freezer. Mm-Hmm. <affirmative> after three hours in the freezer spin. Right. Had no problem seeing the U S B device.
(01:35:03):
It told me it would take 25 hours at level two. So I left it for the night. But in the morning I saw this and he sent me a picture of, and it's in the show notes, division overflow error. A critical error occurred at, and I knew what it was gonna say, B zero four E. That's the, oh, how'd you know that? How did you know that <laugh>? So he, so I'll, I'll he, he, he said, disappointed. I told myself maybe it recovered some of the data and it did all the 35 or so gigabytes of it freezing a USB stick. It worked. Thank you. Steve Anxiously awaiting version 6.1 mirror in Montreal. Okay. So first of all, the error that me encountered was that infamous problem in 6.0 that we now have a fix for. It's the result of Spin Wright from 2004, encountering a drive 16 years later that it was never designed to handle.
(01:36:15):
Thanks to the reverse engineering work of Paul Farer, we have a simple patch utility that can be run before spin, right? 6.0, which will prevent this from ever occurring. Secondarily, it is because of recoveries like this one that I decided to continue moving spin right forward, even past 6.1, although the days of spinning mass storage may be numbered. So that's been predicted for quite some time and hard drives are still there and still, you know, make sense for many applications. I've previously shared many user stories of spin, right? Recovering and repairing solid state drives. I remember initially being surprised by those reports. Now we just shrug and say, yeah, it works on those two. And what's even cooler is that while not everyone always needs recovery, everyone could always use more speed over the weekend. One of our 6.1 testers from Australia, a guy named Peter Hancock, ran spin right on one of his thumb drives.
(01:37:23):
I have a clip from the spin right log. This is spin, right? 6.1 s log, which he posted in our GitLab. Among spin right, six ones many new features is the ability to have it automatically run pre and post benchmarks on the drive. Although that option is not enabled by default. I wanted to provide this option since it helps spin right users to recognize that spin right is really not only about data recovery. This is clearly valuable maintenance for thumb drives. So if the the, the numbers are in the show notes. Look at the read transfer rate at the front of Peter's Drive before running spin, right on it, it was reading at 1.07, seven megabytes per second, 1.077 megabytes per second after running spin, right? It jumped to 14.02, one megabytes per second, 13 times faster. And this is not some distant future spin, right?
(01:38:35):
X this is the free upgrade that everyone's getting. So dramatic improvement in the, in the performance of solid state media. And that's, this is not an isolated incident. Everybody who's running spin right on their SSDs is seeing this. As for putting a thumb drive in the freezer, well, that's interesting too. Meyer in Montreal may have discovered something that will turn out to be useful for recovery. We'll have to see if we're able to repeat that experience. And then we'll add it to our you know, tips and tricks for spin. Right. And Leo, we have a final tip and trick for our listeners from an advertiser, and then we're gonna talk about scanning the internet. Yes, indeed. We are. Steve Security now is brought to you by AG one, but what it really is, is a delicious tasting beverage that contains all the critical vitamins, minerals, nutrients, even pre and probiotics to balance your gut.
(01:39:39):
I just love it and it tastes really good. Now, like many people, I take supplements to makeup for, you know, my modern lifestyle, but it was getting to the point where it was such a fist full of pills, <laugh> that I really could barely choke 'em down and it was getting really expensive. So when I found AG one, I was really happy. And it turns out a lot of people use Ag One. It's been around since 2010. It's been in millions of routines. It's really a safe supplement well made with very high standards, but it's also delicious. And it gives my body everything it craves in one daily drink. You put it in 12 ounces of water, it can be cool. Water dissolves very easily. I drink it before I eat anything first thing in the morning, which has a nice benefit too.
(01:40:23):
It fills me up. So I'm not as hungry. I don't eat as much for breakfast. It's the best all in one solution for daily nutrition. Saves you time, confusion, and money. Each serving costs less than three bucks a day. And great powerful long-term results. Whether it's improving digestion, supporting your sleep, or just the highest quality supplements, AG one gives you the best bang for your buck. One scoop of Ag one in the morning covers your entire day's nutritional bases and 75 high quality minerals, vitamins, pre and probiotics. I look forward to it every morning. If you're looking for a simpler cost effective supplement routine, AG one from Athletic Greens is giving you a free one year supply of vitamin D. It's a, it's kind of cool. It's, it comes in a vial with a little dropper, so you can have, each drop is a thousand iu, so you can have as much or as little as you need which is great.
(01:41:17):
You'll also get five free travel packs with your first purchase of a subscription, athletic greens.com/security now athletic greens.com/security. Now to get the five free travel packs, which are really great. I love those. And the free one year supply of vitamin D. Thank you. Athletic Greens, ag1@athleticgreens.com slash security. Now, now we talk about scraping the internet. There was just, it's interesting, I don't know if it's related, but there was just a story came out today and Wired saying that the United States intelligence divisions are down, are illegally buying data broker information Oh yeah. To spy on the entire populace. Yep. Huge amount of huge amounts. Huge, you know, of a proprietary independent data broker. Yes. That, and it's technically not legal for them to do. The US is openly stockpiling dirt on all citizens. The article today in wired by Dell Cameron, but that's not exactly what you're talking about.
(01:42:24):
You're talking about different kind of scanning. Correct. So with the news that Russia wants to block scanning of its internal networks, you know, and again, who could blame them for that? I thought it would be interesting to take a look at a modern state-of-the-art internet scanning service, actually the modern state-of-the-art internet scanning service to see where that state-of-the-art is today. How quickly can the entire internet be scanned? What ports are checked? What controls are available to be placed on such scanning? Can Ross come nuns or ask them to please not scan Russia? So the story of the Internet's current state-of-the-art scanning begins 10 years ago, back in 2013, when a Turkish American PhD student at the University of Michigan named Zakir Dume looks at the existing and at the time, quite famous, though also quite an old Kluge N map network scanner, and thinks quite correctly this could be done much better.
(01:43:34):
Four years later, after being one of 14 students to receive a Google PhD fellowship in security for the 20 14 20 15 academic year, Dr. Doer dome finishes his PhD thesis, which is titled Fast Internet Wide Scanning A New Security Perspective. The result of this work is a new scanner, which Zakir names Zap. Okay. Now having created GRCs Shields Up service back in 1999, which required the creation of an it an IP stack from scratch for that purpose, I know my way around packets and I've seen a packet or two. So I can attest that Zak's work is beautiful. His thesis demonstrates that he has an absolutely thorough grasp of many various problems, asks all the right questions, performs the right experiments, and winds up developing extremely robust whole internet scanning and assessment technology. It's really not rocket science, but no one had taken the time to sit down and really do it right until he did, and he did.
(01:44:55):
Now, in fairness to Nmap, you know, which is, you know, many people have a strong fondness for the world had changed dramatically since Nmap was first conceived. The biggest change was to the bandwidth available to such a scanner. At the time that Zakir came along, gigabit internet connections were common and affordable. When I first created Shields up my 1.54 megabit T1 line was the envy of my friends. Since no scanner wants to create its own bandwidth denial of service on itself, the available bandwidth dictates everything else about the system's architecture. So, Zakir was able to reconceptualize internet-wide scanning at a time when doing so was feasible, like it really hadn't ever been before. To gain an appreciation for the potential importance of the ability to have true near real time visibility into the internet. I wanna share the introduction to chapter seven of Z's 216 page PhD thesis.
(01:46:15):
He wrote a book, it's a topic that all long-term security now listeners will be able to relate to since it happened on our watch. Zak's chapter seven is titled, understanding Heart Bleeds Impact. He writes, in March, 2014, researchers found a catastrophic vulnerability in open S S L. The cryptographic library used to secure connections in popular server products, including Apache and X. While open SSL has had several notable security issues during its 16 year history, this flaw the heart bleed vulnerability was one of the most impactful. Heart bleed allows attackers to read sensitive memory from vulnerable servers, potentially including cryptographic keys, login credentials, and other private data exacerbating its severity. The bug is simple to understand and exploit. In this work, we analyze the impact of the vulnerability and track the server operator community's responses using extensive active scanning. We assess who was vulnerable characterizing HeartBleeds scope across popular HTT p s websites and the full I P V four address space.
(01:47:45):
We also survey the range of protocols and server products affected. We estimate that 24 to 55% of H G D P S servers in the Alexa top 1 million were initially vulnerable, including 44 of the Alexa top 102 days after disclosure. We observed that 11% of the H T D P S sites in the Alexa top 1 million remain vulnerable, as did 6% of all HT D p s servers in the public I P V four address space. We find that vulnerable hosts were not randomly distributed with more than 50% located in only 10 ass. You know, tho, tho those are top level ISPs, right? As is is autonomous. System number 50% located in only 10 ass that do not reflect the ass with the most. H g dpss hosts in our scans of the I P V four address space, we identify over 70 models of vulnerable embedded devices and software packages.
(01:48:58):
We also observe that both, that both h that both h we also observe that both SMTP plus TLS and Tour were heavily affected. More than half of all tour nodes were vulnerable in the days following disclosure. Our investigation of the operator community's response finds it within the first 24 hours, all but five of the top Alexa 100 sites were patched. And within 48 hours, all of the vulnerable hosts in the top 500 were patched. While popular sites responded quickly, we observed that patching plateaued after about two weeks and 3% of H G D P S sites in the Alexa, top 1 million remained vulnerable almost two months after disclosure. Okay, now think about how valuable it is to have this sort of information in the wake of a significant internet-wide security event like Heartbleed. When this happened in 2014, there was no other source of this information other than Zak's new internet scanner, which he had written as a freshman at University of Michigan.
(01:50:30):
There's only one and one way to get this kind of information, which is to have the tools that are able to go out onto the internet and look at it, and they need to be fast. Okay, so chapter four of Z secure's thesis, which I won't go into here, is titled, detecting Widespread Weak Keys in Network Devices. It's another example of how crucial having this sort of visibility into the internet can be a new view, a a new vulnerability and or attack is discovered on some core aspect of our global internet, and we need to be able to assess its impact and to begin to know how to remediate its effects, where to look, who to call, what to do. In an interview which Zakir gave to the Turkish American Scientists and Scholars Association he was asked, could you describe your innovation in layman's terms and how it relates to everyday life?
(01:51:41):
He replied, the cornerstone of this research is zap a tool that I introduced in 2013 that enables researchers to rapidly measure how every device connected to the public internet is configured. ZAP p reduces the time required to perform internet, internet-wide measurements from months to minutes 10,000 times faster than previous techniques, and allows us to reason about the devices that make up the internet for the first time. Previously, many decisions were made anecdotally or through sampling. Now we are able to perform comprehensive measurements, which has allowed us to uncover new types of bugs and understand some of the more complex interactions between devices at scale. Okay, now what happened to Zakir today, he's an assistant professor of computer science at Stanford University and Chief scientist of census, which is the inevitable commercial spinoff of his work. Before, before we get to that, let's look at the non-commercial side, which is the ZAP project.
(01:53:04):
It's located@zap.io and no www in front of that either. Just ZM map.io. The ZAP project describes itself as a collection of open source tools. All of this is open source, open source tools for performing large scale studies of hosts and services on the internet. The project was started in 2013 with the release of zm a p, a fast single packet scanner that enabled scanning the entire public I P V four address space on a single port in under 45 minutes. A year later, we released Z grab a Go application layer scanner that works in tandem with zap. Since then, the team has expanded and we have built nearly a dozen open source tools and libraries for performing large scale internet measurements. Continued development is supported by the National Science Foundation, you know, the us and sf. So the project is published a series of papers that describe how the suite of ZAP tools are designed.
(01:54:21):
There's zap fast internet wide scanning and its security applications. There's another paper, Z D N S, a FAST DN s toolkit for internet measurement. There's z lint tracking certificate MIS issuance in the WILD and Z L R identifying unexpected internet services. And I found this one particularly interesting, that last paper, the Z L R identifying unexpected internet services was delivered during the 2021. Use Nick's Security Symposium. The synopsis of this identifying unexpected internet services paper has this couple of surprising findings. It says internet wide scanning is a commonly used research technique that has helped uncover real world attacks. Well, it's common now. It wasn't common in 2013. Helps uncover real world attacks, find cryptographic weaknesses, and understand both operator and misre behavior. Studies that employ scanning have largely assumed that services are hosted on their I A N aas assigned ports, right? Like, you know, HTTP port 80 HT dpss, port 4 43, Telnet Port 23, and so on.
(01:55:46):
Those are the I A N A assigned ports. The idea being that if you want, if you're given the IP of a service, you know what the service is, you know which port it's expected to be on at that IP address. So the, the that they go on overlooking the study of services on unused ports. In this work we investigate where internet services are deployed in practice and evaluate the security posture of services on unexpected ports. We show protocol development is more diffuse than previously known, and that protocols run on many additional ports beyond their primary I A N A assignment. For example, they say get this only 3% of H T T P and 6% of https s services run on ports 80 and 4 43. What <laugh> 3% of H T T HTTP is on port 80 and only 6% of HTTPS is on 4 43.
(01:57:04):
Where else is it everywhere else, like on the other 6 55, 3 4 ports. But it starts on, it starts on 80. No, it there, well like, like, like we, we know Leo, that to have a, to run a server on port 80, you have to have root, right? Right. Because you can only run, you're only able to, to, to access ports below 10 24. That is, you know, one to 10 23 if you have root privilege. That's why user land servers often use port 80 80 80, right? As their, as their http. Right? So it, so, so the point is, these services are scattered all over hell and gone, the public facing servers have to use 80 and 4 43, otherwise you wouldn't get there. Well, or you have to know to put a colon something after the url, right? Which, you know, sometimes happens, sometimes you sometimes see a u r URL that, that that says, you know, colon 1, 2, 3, 4, 5.
(01:58:07):
It's like, okay. So they conclude services on non-standard ports are more likely to be insecure, which results in studies dramatically underestimating the security posture of internet hosts. Building on our observations, we introduced L Z R laser A system that identifies 99% of unidentifiable unexpected services using five handshakes in dramatic and dramatically reduces the time needed to perform application layer scans on ports with few responsive expected services. And they give an example of having achieved a 5500% speed up identifying Mongo DB on port 2,717. So, okay, so again, who would've imagined that only 3% of all of the actual HTTP service is on port 80? The, the other 97% are on other ports that, and similarly I think it's misleading all public HTTP servers are in 80 and https s servers are in 4 43, right? No, this is a, this is a scan of the public internet I know of this is but the public internet.
(01:59:36):
Yeah, Ben, like when I set up a local host thing, it's on a different port, you know, when I'm writing stuff for a web server or whatever, right? But my website has to be on port 80, doesn't it? Yes. But other people can have other things Yeah. On other ports, but I'm not surprised they're insecure cuz they're o those often just like somebody messing around and stuff. Or you know, what's that horrible NA that keeps getting hacked? <Laugh>. Qap. Yeah, qap. It's probably got a web server working on some port, right? So there's a public service running on a non a non 80 port. It shouldn't shock you though if they're running on non-canonical ports that they might be insecure too, because, right. Like why? Right? And the point is we never looked, we never knew, right? We, so, so what happened was when we looked, it was like, oh my God, look at all this crap everywhere else that is like listening on these bizarre ports that no one ever taught thought to look at, right?
(02:00:38):
So two papers later, the Zap P project's list of published papers, we see we encounter census C E N S Y S census a search engine backed by internet wide scanning. And the synopsis of this paper shows us how we move from internet wide scanner to an internet wide search engine. And just so that I'm sure I have everyone's attention, this is free. So search.census.io, you can put some search terms in and pull from what I'm about to be reading. And you don't have to be a university researcher, you just have to be researching for a good purpose and they will give you credentials. There is a commercial side where like the, the, all the big security companies, they pay to have API backend access to this database. But people listen to this podcast could say, Hey, I wanna, I've got an idea, I wanna do some research and you can get signed up.
(02:01:46):
So here's the deal. They said fast internet wide scanning has opened new avenues for security research ranging from uncovered widespread vulnerabilities in random number generators to tracking the evolving impact of heart bleed. However, this technique still requires significant effort. Even simple questions such as what models of embedded devices prefer c BBC ciphers require developing an application scanner, manually identifying and tagging devices, negotiating with network administrators, and responding to abuse complaints. In this paper, we introduce census, a public search engine and data processing facility backed by data collected from ongoing internet wide scans designed to help researchers answer security related questions. Census supports full tech searches on protocol banners and querying a wide range of derived fields. It can identify specific vulnerable devices and networks and generate statistical reports on broad usage patterns and trends. Census returns these results in subsecond time dramatically reducing the effort of understanding the hosts that comprise the internet.
(02:03:15):
We present the search engine architecture and experimentally evaluate its performance. In this paper we also explore census's applications and show how recent questions become simple to answer. And this brings us to the second part of this, which is C E N s ys.io. The census mission statement reads, at census we believe that cybersecurity is critical to the future of our global economy. And in order to evolve cybersecurity defenses, both the public and private sector need access to best in class intelligence data. By arming our customers with the visibility and insights that they need to protect against critical threats, census provides the intelligence needed to bolster cybersecurity capabilities worldwide. So basically we now with census have access to near realtime deep intelligence, internet wide, port wide scanning of everything that is public. What does census tell us about their internet scanning? Their timeline notes that zm a p was invented in 2013, which we know Zakir did that.
(02:04:39):
Thus Z of Zap, that census was founded four years later in Ann Arbor, Michigan, probably when he'd got his bachelor's which is where Zakir had gone to university. And it also shows that two years later in 2019, the original ZAP scanner was replaced by their proprietary scanning technology. So there are two projects. There's the, the ZAP project, which is continued moving forward, advancing Zap scanner based applications, which is still open source and available. And then there's sensors which has moved to a far more sophisticated scanning technology. We don't need that because we have access to its results.
(02:05:34):
And of course it makes sense that there would be a change over six years. As I've said, the co the world is constantly changing and six years since Z zakir first created zap you can now do a much better job. And so that's what they have under the topic of scanning of, of host scanning introduction, they explain census continually scans the entire public I P V four address space on thirty five hundred and ninety two plus ports using automatic protocol detection to present the most accurate representation of the internet's current state. Census also leverages redirects and the domain name system to discover and scan around 97 million in use I P V six addresses. Now that's interesting since it's entirely possible to scan all I P V four addresses, which occupy a 32 B address space. However, there's no possibility of scanning the entire I P V six address, address space, which is 128 bits.
(02:06:55):
So it's necessary instead to discover, hold and build up a partially populated map over time of active I P V six addresses, which these guys have. And it's also interesting that this number is still apparently as few as around 79 million. Okay, 79 million is a lot, but it's not close to I P V four s essentially fully occupied 4.3 billion ips. They continue to explain census scans only obtain information census never attempts to log into any service, read any database or otherwise gain authenticated access to any system. They ask themselves the question, how often does census scan for new services? Discovery means finding a service on an IP and port that was not there last time we looked. Census has several schedules for discovery based on our experience scanning the internet. First global scan of popular ports, we scan the whole I P V four space on 137 ports with I A n aas assigned services every day.
(02:08:27):
Okay? So the entire I P V four space on all hundred and 37 I a N A assigned ports every day Cloud provider scans says many cloud hosts are ephemeral. We scan the most 1,440 popular ports on Amazon, Google, and a Azure hosts every day global scan of less popular ports. We scan the whole I P V four space on thirty four hundred and fifty five additional ports on a regular basis, completing a walk every 10 days. And finally, a global scan on every other port number. We scan the entire I p V4 address space across all ports, 6 5 5 35 at a low background rate. Okay, so stop for a second. Internet background radiation. Yeah, that means any IP address, any I p V4 address, you put a port monitor on it and these guys are gonna wind up sending a packet to you to every single one of your ip, your one IPS 6 5 5 3 5 ports over some period of time. All all hundred and 37 of the i of the I ana assigned ports every day on every single IP out there. So this is some radiation.
(02:10:09):
How often does census refresh data for known services? Once a service has been discovered, census prioritizes refreshing the information about that service to ensure it is accurate and up to date once a day, the age of each of the approximately 1.2 billion services in our data set is checked. Any unnamed service with an observation timestamp older than 24 hours is re-scanned with this process. The average age of high value service data is about 16 hours. Okay? So that means they've got 2.1 billion specific services, meaning an a port an ip and they know what's there, 2.1 billion of them and they re revisit it and verve re-verify it about every 16 hours. None of the data in that data set is older than 16 hours and it's available to be searched. How does census scan? Okay, now they don't really answer their own question, which I thought was interesting, but they, even though they asked it of themselves, they say census has invested time and technology into setting up multiple global perspectives and developing sophisticated scanning techniques to produce the richest, most useful dataset for the security community.
(02:11:45):
Okay, well that didn't really answer the question. You know, they could have just said we scan Good. Anyway, they said census peers width and scans from five tier one ISPs, N T T Tata, hurricane Electric Telia and Orange to produce nearly 99% coverage of listening hosts across the globe with enhanced protection against packet drop. The I s P that census scanned any given service from is recorded in the service dot perspective field deep protocol scans on ports with I A n aas assigned protocols, census attempts to complete a handshake with the assigned protocol. You know, for ex, you know, expecting Telnet to be on port 23, for example, they said if that fails, we try additional handshakes according to our experience with protocol and port pairings. Okay, so for example, if atel net handshake were to fail on port 23, they might try an S SSH handshake since it's foreseeable that somebody might have put S SSH over on till net's port, they said on ports without an assigned service.
(02:13:05):
We start by sending an H T T P request because as we've seen HTTP is kind of everywhere an attempt to automatically detect the protocol based on the response. Automatic protocol detection, they said the census scanner analyzes every server response to identify its service, even if it's, if even it's non-standard for the port, which allows us to uncover the vast majority of services in unexpected places. For example, if an H T D P request results in an SS h banner senses will close the H T D P connection and reattempt an h an Ss h handshake sensors can detect 25 protocols on any port. Some protocols do not have a lot of data to parse and index, you know, meaning if an initial TCP connection handshake succeeds on some random unassigned port, you know, now what? So they said census identifies 47 lightweight services and col and collects a banner.
(02:14:19):
What protocols and services do census detect? Census can detect and complete scans for over 100 layer seven meaning, you know, application layer protocols. The default layer four, you know, IP layer protocol used by our scanners is T C P. Although some protocols such as D n s are scanned with U D P and H T D P can be detected over quick. You know, Q U I C service names represent the most specific service information we have. For example, a generic H T D P service has a service name of H T D P while an H T D P service that's actually an elastic search server, has a service name of elastic search, meaning that they will get as specific as they can. There's also an unknown fallback, which means that census would not, could not identify the protocol in use by an open service either because the service is not adhering to a protocol is, and they say there are a lot of H T D P like services out there, or because census does not have a protocol specific scanner written for that.
(02:15:32):
So once a day around 2.1 billion individual internet services, which they maintain in their dataset is checked and they maintain a searchable index of everything that they have found. And what if someone like Russia doesn't want to be scanned and indexed about this census? Says census strives to be a good citizen of a security industry. We never attempt to log into any service, never read any database or otherwise gain authenticated access to any system. Can I opt out of census data collection? They said census scans help. They like, they don't want you to. So they say census scans help the scientific community accurately study the internet. The data census gathers is sometimes used to detect security problems and to inform operators of vulnerable systems so that they can be fixed. If you opt out of data collection, you might not receive these important security notifications. However, if you wish to opt out, you can configure your firewall to drop traffic from the subnets we use for scanning.
(02:16:55):
And here in the show notes and on their site, they proudly display them. There are five slash 24 networks. So, so that's a you know, 256 ips or 253 or four. So there are five of those networks and then two I p v six networks, which are slash eighties, so what, 48 bits on the machine name. And and so again, you're not gonna <laugh> you're not gonna scan all those. But, but so they, they, they do show a total of seven networks, which if you didn't want them, you know, if you didn't want your network to be in their database, in their data set, which could be searched for things. Add those to your firewall. And okay, then what happens? They did say, additionally, our http based scans, cuz they, you know, they do make http queries to see what's there on, like, on port 80, use a census specific user agent, which can be used to filter requests from our scanners.
(02:18:08):
So again, if, if you arrange to have your server reply with it's got census inspect slash 1.1 I, I'm sorry. If, if you see this coming as the user agent into your server, you could have your server, you know, do something different. Just drop the request, you know, just hang up. They said, configuring your services to drop connections from census subnets will prevent our scanners from indexing your services. Historical data is not removed from census data sets as part of this change. Host services are typically pruned from census search within 24 to 48 hours of their last observation timestamp. So it's, so they're not just accruing everything forever. If you go off the net after a couple days of you not being there, they will remove you because they want to be a current snapshot, not an archival snapshot. They said host services are typically puneed from census search within 20 to 4 48 hours of their last observation timestamp, while virtual host services can remain in the data set for up to 30 days.
(02:19:22):
And finally they explain, census started as a research project at the University of Michigan, and we continue to provide free internet data to the research community. We provide verified researchers and the verify, as I said, the verified threshold the, the verified bar is very low. Our listeners could qualify the same access to our data as our highest tiered commercial customers. I've got a link to the, the, the, the, the research access to census data here, the last, on the last page of the show notes. You know, so as I said, while they do sell access to their databases and data sets to commercial entities which they make available through an api, they also make this AC access available to pretty much anyone who has a justifiable use for such access. You know, and they say, you know, if your, if your use is, I want to make my company's hosts more secure no, but if you wanna make the world a better place welcome and, and we, we'd be happy to have you.
(02:20:35):
So I've been noticing that we've been running across this group, the name census more and more with their name being cited by other security researchers who are cur, who are clearly their co their commercial customers. So I've been wanting to do a bit of a deep dive into who they are and where they came from. Now we know, so the next time I refer to them, it won't be who it'll be. Oh yeah, those guys, they're good. I believe they are. It's fascinating and well done to census, I guess. Yes. Yeah. Yeah. I mean, to be giving the, be giving the world a a near real, I mean, as real time as it could be maintained searchable dataset of what is the internet? I mean, that is, that is the internet. Could it be misused in the way that Showan is kind of misused?
(02:21:33):
Absolutely. Okay. <Laugh> just checking. Absolutely. It's like show Dan, basically. Yeah, yeah, yeah. Okay. I mean, you know, they use that access to find and enumerate the Heartbleed vulnerable servers immediately. Right, right. So, so there you go. Yeah. Yeah. Wow. Fascinating. And another great show, jam packed episode. You this is a two hour 21 minute extravaganza. Well done Mr. Gibson. Steve's at grc.com. That's where Spin Wright lives, the world's best heart, well, mass storage, maintenance and, and and recovery utility 6.0 is gonna be 6.1 any day. Now buy 6.0 today, you get to use it, and as soon as 6 1 9 comes out, you'll get that for free of free upgrade grc.com. While you're there, pick up spin, right? No, you already got spin, right. While you're there, pick up the podcast. That's it. Yes. Steve has two unique versions. We both have podcasts, this, this show at our website, but Steve has a 16 kilobit version for masochists.
(02:22:38):
People like Scratchy sound or, or just bandwidth impaired and a very useful transcript. Ghislaine Ferris, write those up every week, takes three or four days to get it out. But after that's out, you can read along. As you listen, you can use it to search. It's very helpful. I've used it several times to search for content in the show. All of that grc.com. We have 64 Kilobit audio like Steve does, but we have a unique version on our site, the full video. So you can see Steve's smiling face that's at Twitter tv slash sn. Steve's on the Twitter sg grc. That's where you can leave questions, messages, or suggestions for his picture of the week at sg grc on Twitter. We would like to invite you to become Club Twit members. If you like this show, but you hate the ads, including this one, you get the ad free tracker free version.
(02:23:33):
By joining Club Twit, you also get a lot of other benefits, including, I don't know, did you ever read Wool? It's been turned into an Apple tv show that's been very popular called Silo. Have you watched Silo, Steve? Oh, I I've seen it advertised. Yeah, but I don't know what it is. So the author has very good sci-fi and, and the, and the people who read the books, I've never read the book, swear that it is a very faithful rendering of this great book series called Wool. Well, if you're a fan of Wool or Silo, good News Anne has arranged an interview with the author a fireside chat with Hugh Halle June 29th at 1:00 PM Another reason to join the club that'll follow Stacy's Book Club, the Transformers, Anna Neitz newest book that's at 9:00 AM on the 29th. We also have a, a a, I think somewhat inebriated inside twit after hours coming up in July, <laugh>, and you get access to the Discord.
(02:24:31):
You get ad free versions of the show and shows. We don't put out anywhere else like Scott Wilkinson's, home theater geeks, like Inside McIntosh, hands on Macintosh with with Micah Sergeant or the Hands-on Windows with Paul Throt, the Untitled Linux Show. All of which to say it's seven bucks a month. It's a great value. You get a lot for your money and it really helps us keep everything going. We appreciate it. So a semi inebriated inside twit in July. Yes. So you're, you're planning ahead on getting drunk. I don't drink, but others may <laugh>. Ah, see, okay. Others may I don't know if I'll even be there. I'm thinking I'll be a damper on the party, so I'm just go, you know, I, we'll see. I don't know. I don't know what, what Amp puts this all together. Amp Pruitt's our community manager.
(02:25:21):
He does a great job and I think it's a good idea for an inside twit. Find out the real skinny from a bunch of people that's with no inhibitions. How about that? Took around doing shots. Yeah, that's right. Seven bucks a month and you get that? Yes, twit do TV slash club twit to join. The other thing you could do for us, subscribe to this show. We know that, you know, you listen and I'm sure if you listen, you wanna listen to every episode. If you subscribe, that's effortless. Go to your favorite podcast players, search for security now, or better yet, search for twit and download all the shows if you want. There's even a all twit channel that you get all the shows automatically. But we know that if you subscribe, you're more likely to listen and we want you to listen.
(02:26:05):
So make sure you do that. If you wanna watch us do it live, we we record this show every Tuesday around about one 30 Pacific, four 30 Eastern, 2030 utc. You can watch live at live dot Twitter tv. That channel's going all the time. There's always something. If it's not live recordings, it's previously recorded episodes of the shows. It runs 24 7. You can ask your Amazon Echo, your Google Assistant, you know, play Twit live and have it going on in the background. We'll keep you company anytime of the day or night or of course, on the web at twit tv slash live if you're watching live chat, live at IRC twit tv. That IRC channel open to all. And of course, our Club TWIT members hang out in the stadium club the the club level <laugh> in our discord, which is a lot of fun. It's a great place to hang. Thank you, Steve. Have a wonderful week. Do some read and we'll see you next week. I'm gonna on security now. Hey, bye. Why bye.
Mikah Sargent (02:27:04):
Oh, hey, that's a really nice iPhone you have there. You totally picked the right color. Hey, since you do use an iPhone and maybe use an iPad or an Apple Watch or an Apple tv, well you should check out iOS today. That's a show that I Mikah Sargent and my co-host, Rosemary Orchard host every Tuesday right here on the Twit Network. It covers all things iOS, tv, os, home, pod, os, watch, os, iPad os. It's all the OSS that Apple has on offer, and we love to give you tips and tricks about making the most of those devices, checking out great apps and services and answering your tech questions. I hope you check it out.