Security Now 923, Transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte (00:00:00):
It's time for Security Now. Steve Gibson is here. We've got of course, the picture of the week. Nice little cartoon about ai. We've got an update on his software project Spin, right? We'll talk a little bit about cost software coding philosophy, even as it applies to his favorite language assembly language. And then we're gonna dive deep as we did last week into location tracker behavior in particular, the future spec that both Google and Apple want to adopt for for these little Bluetooth location trackers. It's all coming up next on Security Now podcasts you love
Speaker 2 (00:00:37):
From people you trust. This is TWiT.
Leo Laporte (00:00:46):
This is Security Now with Steve Gibson. Episode 923 Recorded Tuesday, May 16th, 2023. Location tracker Behavior Security Now is brought to you by Bitwarden. Get the password manager that offers a robust and cost effective solution that drastically increases your chances of staying safe online. Get started with a free trial of a teams or enterprise plan, or get started for free across all devices as an individual user. Bitwarden.Com/Twit and by ACI learning. IT skills are outdated in about 18 months. Stay ahead of the curve at futureproof your business competitiveness with customizable entertaining training. Fill out the form at go.acilearning.com/twit. More information on free two week training trial for your team. It's time for security. Now, the show we cover the latest security news with our champion, Mr. Steven Gibson. Hi Steve.
Steve Gibson (00:01:44):
Hey Leo. It's great to be with you for episode 9 23 where we're gonna continue. We're gonna pick up basically where we left off after last week's e episode talking about the behavior of location trackers. Hmm. And it was, it was my intention to do what I always do, or almost <laugh> almost being the operative word, this case cuz I didn't do it, which is to actually talk about some news in addition to our main Well, you had
Leo Laporte (00:02:17):
It prepared the way beforehand.
Steve Gibson (00:02:20):
Well, yes. And the problem is doing this specification of, of, you know, air tag and other location tracking behavior justice. I just, I, the deeper I got into it, the more I had to unwind it. Cuz the spec turns out to be really poorly written. It's all out of order. They refer to things in other places and it's like, okay, wait, wait, look what? So anyway, I, and I ended up with 18 pages without ever talking about any news. So this is one of our, this is a pure deep dive. We're gonna answer only two questions this week. First, why haven't I been saying anything about my recent work on spin, right? And second, what are all the details spelled out in this emerging specification for the detection of unwanted location tracking? On the other hand, I think everybody's gonna find this very interesting and fascinating and I will do the two previous weeks of news next week for our podcast. So, and of course we do have a <laugh> another good picture of the week. So I think another great couple hours of entertainment for our listeners and a lot of information
Leo Laporte (00:03:34):
As, as you always do, Steve, always. And one of the reasons we do this show and can do this show ongoing on an ongoing basis is our sponsors, our wonderful sponsors. And the show this week is sponsored by Bitwarden and you know, we've talked a lot about Bitwarden, it's the password manager. I use Steve and Steve used as uses as well. We both switched over from a last pass to something we think is a little bit more secure. And I have to say, one of the things I love about Bitwarden, because it's open source in fact, Bitwarden is the only open source cross platform password manager you can use at home, of course, but also at work on all your mobile devices. It's trusted by millions of people. They got last fall, about a hundred million dollar venture funding.
(00:04:22):
And what they're using it for is to develop something that you and I have been talking a lot about Passwordless logins. Bitwarden has always supported web often, which is kind of the, the backend for pass keys. They've always supported that. They've always had some really nice for, especially for enterprise systems for zero sign and zero, you know, zero passwords login. And the other thing Bitwarden does, cuz it's open source is, you know, they have people contributing to it. And we've talked about this on the show when we talked about how poor pbk DF two was, if you don't use sufficient iterations, and we were talking about some last pass vaults that had pbk DF two iterations of, of one <laugh>, which is not an iteration hardly in iteration at all. Very poor security. One of our listeners wrote a pa a memory hard interface for Bitwarden for both Argon two and what was the other one?
(00:05:19):
B Crypt. They've decided after some, you know, everybody, it's a community getting, going back and forth that they were gonna put all the arrows behind Argon two and Argon two is now part one of the choices in your pb in your dir key derivative function. You don't have to use the kind of not so great pbk DF two, you can use Argon two, which I have been doing as long as you're up to date, you have 20, 23 0.2 or later you can do this. Almost all of us do. I've been using it everywhere and it's, it's fast, it's effective and we now have, don't have to worry anymore about the key derivative function. This is an example. How, how, so this was I think it was Quicken who's a listener to the show who pushed this, you know, he doesn't work for Bitwarden pushed this, it was accepted, put in the repo, added the Bitwarden all within just a few months.
(00:06:08):
I love that the code is on GitHub. You can, you can view it. You don't have to trust their word. You can see that it's completely secure and because it's public they have professional third party audits performed every year. So even if you can't look at code and say, oh, that's good, experts are, and they publish the results of those audits on the website. So this is one of the reasons I like open source and really frankly prefer open source for anything like this, for encryption, for password vaults, that kind of thing. Bitwarden has a username generator now, which will create unique usernames for every account, giving you kind of twice the security. Now a bad guy has to figure out the username and the password that will work with any of five integrated email alias services. Our, our our other sponsor fast mail supports it among, I think Mozilla has won.
(00:06:59):
There are a number of, of these services out there. The Bitwarden Secrets managers, the latest thing, they just announced this, it's currently in beta, an end-to-end encryption solution that allows teams of developers to securely and centrally manage and deploy sensitive secrets. That would be, you know, it's really shocking how many times a API keys show up in people's public GitHub repositories or their dot files, right? You can use the Secrets Manager to keep those a p API keys and machine credentials secret. So this not in the source code eliminates the risks of them being exposed with a in inadvertent commit. Bitwarden wants you as a developer to test this out and provide feedback. So if you're interested, Bitwarden.com/secrets beta Bitwarden.com/secret beta. I think the more I talk about Bitwarden, the more I just feel this warm and fuzzy feeling that this is a company that is us.
(00:08:01):
It cares about its users, it's open, it works with us. It's the best way, of course to keep your passwords and, and you're sophisticated. You listen to this show, you know, you about password managers, you know you need them. It's not just for you. This is for all those friends, family and coworkers who come to you and ask you, what should I be doing? What should I use? I want you to tell 'em about Bitwarden. It is awesome. You can use Bitwarden as an individual. In fact, all the Bitwarden involves start with that free, free forever personal account, which can be, you know, there's no limitations. Unlimited number of passwords can be used on any device. All of that stuff. So you start with the basic free account. If you want Two factor or other features you can upgrade. And, and if you wanna support Bit Wood in which I do, you can upgrade to the premium account, that's 10 bucks a year.
(00:08:50):
Come on. I mean, that's nothing, right? There's a family plan up to six users. Your family 3 33 a month for every everybody one, you know, one price. Now there's Bitwarden's teams organization option, which is $3 a month for a user. So you start with the personal vault and you join your company's team and you're part of their vault or the enterprise organization plan with even more features, $5 per user. There are just lots of ways to use this, but remember that basic free account, free Forever. I think to get your family members and friends to use a password manager. That might be one of the things to get them over that hump is, look, this isn't gonna cost you anything. And once they start using Bit Word, and I think they'll see, it's not hard does the auto field does all the things that you want it to do, but it does it securely.
(00:09:39):
We, as you know, we talk about password managers, you must use one. You must use it to generate long, strong, unique passwords every time you need a password pass. Keys is coming. Bitwarden will support that. It's the only open source cross platform password manager you can use everywhere home work or on the go. Trusted by millions of teams, individuals, organizations worldwide. We've been migrating the business, the enterprise password manager here at twit over to Bitwarden. Get started with a free trial of teams or enterprise or get started for free across all devices free forever. Or do what I do, I just wanna support 'em. Give 'em the 10 bucks a year and get the premium Bitwarden.com/twit. Please use that address. I want them to, I I don't ever wanna lose him as an advertiser cuz I wanna be able to tell you about this as often as possible. Bitwarden.Com/Twit. Tell your friends, tell your family, tell all the people who you work with stop reusing your same password. That's your birthdate and your mother's maiden name on all those sites. If you listen to the show, you know, what a disaster that is. Bitwarden.Com/Twi, right? I'm gonna stop preaching. It's more Steve. Go ahead, Steve <laugh>.
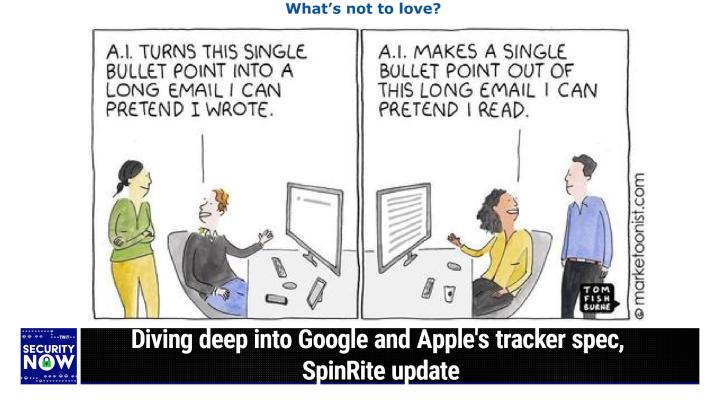
Steve Gibson (00:10:59):
So our picture of the week is a fun one apropo of many of the things we've been talking about relative to ai. It's a two frame cartoon. The the first frame on the left has someone sitting in front of his computer. He's very excited, he's explaining to a friend standing behind him. AI turns this single bullet point into a long email. I could pretend I wrote <laugh> and very excited about that. And then in the second frame, we have a gal sitting in front of her computer and, and, and, oh, I should, I should mention on the left hand screen, we like to see one little bullet point on the right hand screen. We see Iker screen is full and, and she's explaining to her friend AI makes a single bullet point out of this long email. I could pretend I read.
Leo Laporte (00:11:47):
It's almost not even a joke.
Steve Gibson (00:11:49):
It's, it's actually
Leo Laporte (00:11:52):
True. It's not. Oh, it's not. Oh my God. Yeah. Yeah.
Steve Gibson (00:11:56):
They, I think at
Leo Laporte (00:11:57):
Google io they practically showed this as a feature, right, <laugh>, which is good. Let email be, let the AI handle the email.
Steve Gibson (00:12:04):
Yeah, why don't you don't, besides no one likes typing on those touch screens. Yeah. So just, you know, give it a clue. Let
Leo Laporte (00:12:11):
AI do, do it
Steve Gibson (00:12:12):
<Laugh>. Let it know how you're feeling and it'll just go ahead and respond on your behalf. So That's right. Okay, so before I get into our main topic, which is gonna dominate the rest of the podcast, I did wanna mention why I've been mute for the past couple of weeks about ongoing work on spin, right? And that's not because of any slowdown in the action, but because of a major revamping of spin right's, primary core data recovery code. As it happens, it's, it sometimes occurs that software gets itself painted into a corner or a programmer paints themselves into a corner, or maybe the software paints the programmer into a corner. I don't know. But, you know, paint and corners always seems to be involved. This could occur when an inexperienced programmer tackles a task that they don't fully understand. You know, they, they jump right in and start writing code and at some point they realize that they can't get where they need to go from where they are.
(00:13:21):
You know, they're in a corner. And at the start of our careers, we coders, you know that has a, that's a common occurrence to many of us who love and live to code. It can also happen, however, when a sufficient quantity of new information arrives late in a software design cycle, which requires that the code be modified in a way it wasn't designed to be, to incorporate the needs created by this new information. And since I checked, I did some subtraction, since I've been coding now for more than 66, 0 years, inexperience is not my shortcoming. What happened is that I and spin Wright's first alpha release were wholly unprepared for the shocking myriad ways that today's and yesterday's highly distressed mass storage devices might and do fail. Everyone's heard me mentioning for many months that nearly all of spin rights, currently eight or 683 registered development testers have mostly been bored.
(00:14:37):
Everything has always just worked for them. You know, that's why I released an alpha, is I, I thought, okay, here we go. It's, it looks great, <laugh>. But while spin ride is valuable to those whose drives are still healthy, it's proven through several decades to be particularly adept at helping to keep drives that way. It, it really comes into its own when it's working to resurrect the data on drives that are far from healthy for whatever. Cause you know, it got dropped by mistake or just got too old, or the power failed in the middle of it, writing some data or something. So I was so close to being able to declare this work finished when a final couple of unexpected surprises landed. For example, though I have never seen this happen, a literal reading of the latest a t a eight specification, which specifies the exact operation of mass storage drives, states that if an error occurs during a data transfer, the drive will abort the transfer and indicate the sector of the first error it encountered.
(00:15:50):
Well, right? That's fine, that's what you'd expect. But it then goes on to say that nothing can be inferred about what data may have been transferred before that error occurred. Now, as far as I know, all drives will transfer all of the data preceding the erroneous sector. But the specification says they no longer need to. And who knows what technology might be used in the future or how far behind in transferring its data A drive might be when it decides to stop due to encountering an error. And since spin, right? 61 obtains its breathtaking speed by transferring 16 megabytes in a single request. That could be important. So from a practical standpoint, this means that when an error occurs to be safe, spin right needs to identify the trouble, then re-request or re-request all of the data up to, but not including the trouble. Get all that data settled, then deal with the sector that caused the transfer to halt.
(00:17:03):
That was the straw that finally broke the camel's back as they say it. It just, it wasn't just that, you know, I could have once again fixed that. It was the once again part spin right's, all new core data recovery code, which I've been so pleased with, and which I have had every intention of moving directly from spin, right? Six one into spin, right? Seven had become a mess over the past six months as I had needed to keep poking and prodding it as we kept discovering new and surprising ways that drives could misbehave On top of that spin, right? Users had drives that were so badly damaged that they were hanging. So they wanted to be able to interrupt Spin Wright at virtually any point to immediately get out and try another drive. Spin Wright wasn't ever built to support that sort of emergency user escape because we weren't seeing that.
(00:18:03):
I was so close to being done that the last thing I wanted to do was to sacrifice that investment. But my code had become so clogged up with special cases exception testing and early out, you know, like bailout code from Inner Loops that it started to feel brittle rather than robust. So I scrapped it. I recognized that the real investment that had been made was in what I had learned since that first Alpha one release. So I settled down with my favorite text outliner and I completely reconceived spin rights entire data recovery system. I'm willing to confess this today because I completed that entire rewrite last Sunday night two nights ago. And it's, it's been a long time since I have been so happy with any code. It is now immaculate. All of the worker code has exactly zero tests for any special case exceptions.
(00:19:14):
I moved that handling into spin ride's common IO abstraction. There are two top level places in spin right during this data recovery one where spin right is starting to work with a block of sectors. And in the other where Spin Right is starting to work on a single sector, immediately upon entering the top of either of those worker routines, I checkpoint the system's stack stack by saving the current stack pointer in a static global variable. Then if anything happens that requires us to immediately surface from wherever we are, no matter how deep and how nested with routines we are, the IO abstraction system through which all control passes on its way to and from the drivers now has the ability to simply reset the stack to its previously saved state when it returns that will have the effect of unwinding and discarding all current call stacks and local variable storage.
(00:20:23):
It immediately terminates anything that was going on. Whatever it was that Design expedient allowed me to have exactly zero tests or concerns for anything that might go sideways throughout the rest of the data recovery code. Now, as a consequence, it is breathtakingly clean because the data recovery code no longer needs to test for anything. And it now also adds support for the wacky a t a eight spec in case drive designers ever do take the spec as literally as it says they could. And there's a broader lesson here that has probably occurred to anyone who codes a lot. There really is an art to coding and Leo, I know you appreciate this, and the act of solving a complex problem teaches the coder so much about how to approach and solve the problem that it's really only after they finally have their program running that they understand how it should have been done. A couple hours ago, purely by coincidence during Mac Break Weekly's pre-show, Alex Lindsay told a story of the four months he first took to solve a complex program in 3D graphics, which in this case was rotating a 3D pyramid on a Commodore 64. This was obviously a while ago. This was
Leo Laporte (00:21:56):
A long time ago. Yeah.
Steve Gibson (00:21:57):
<Laugh>, shortly after he had, he finally had it working. After four months, the machine crashed and he lost all of his work. You know, maybe it was the cassette tape. That's the problem that we used back then. Yeah. <laugh> to save and load our programs. In any event, after recovering emotionally from the loss, Alex told the story of how he re-implemented what he originally had in just three weeks. And it was
Leo Laporte (00:22:28):
Much better probably cuz that's, you
Steve Gibson (00:22:30):
Know, exactly that, that which had taken him four months to do the first time. And he said it was only after that that he then realized how it should be done. So he rewrote it again, right? Yep. In four days. Yep. And the way Alex expressed it was perfect. He, he, he expressed it as three phases. He said, do it then do it better, then do it right. And he, and he said that's like his mantra now that's the way he approaches things cuz he recognizes things that are hard. You, you know, the, the reason we're engaged by them is that they're hard, right? But they're not boring because we're learning from them. Right.
Leo Laporte (00:23:15):
I love it. And that's one of the reasons I use Lisp. I'm not recommending it, but it's, well, I mean I would, but no one will ever do it is because it has that built kind of iterative style built into it. It's a very natural way to work in Lisp, especially cuz of the repel and the way the debugger works. You can actually change a program while it's running. So it's very easy to ex it's a good tool for experiment. This is how I write, I'm not writing real code like you or Alex, but the, but I like to experiment and try stuff and write a first iteration that's, I know isn't gonna be the final version. And then you're not attached to it. It's easier for you to kill it
Steve Gibson (00:23:53):
And you're able to get in so often. Exactly. Getting in just the, the first, right?
Leo Laporte (00:23:57):
The first line is the hardest. Yeah. Yes. <Laugh>. Yeah, yeah, that's right. Yep.
Steve Gibson (00:24:01):
So, and to wrap this up in my present case you know, in, in retrospect, because again, the other reason we code is we're like, okay, what happened? How, how did this happen when that first little innocuous exception was needed? The quickest answer, which seemed right at the time, was to simply add a couple of tests for it. And when it turned out to be needed in other places, I had already established a template for how to, you know, solve that need in air quotes. So I applied the same tests elsewhere. Then when another type of exception emerged, I did the same since by then I'd established a precedent. But after six months of that, my code had become a mess. I knew how to solve it, which is what I just did. But right up until the moment that I finally bit the bullet, it was more important to me to be almost finished. The good news is that now I'm almost finished again. Although the gang in the dev group will have a lot of fresh virgin code to pound on while we verify that it's working exactly the way we want. Almost
Leo Laporte (00:25:16):
Finished. When a programmer says that means something com completely different. I just wanna play that.
Steve Gibson (00:25:23):
That's exactly, and it's why, you know, my my dear wife is saying, so honey how much longer do you think <laugh>? And I just say, I just, I, you know, I have no idea. Say I would say what I would tell you, I would, I would tell everybody if I did. It's not like I'm holding out.
Leo Laporte (00:25:38):
Tell him what Michelangelo told Pope Julius when he is painting the Sistine Chapel. It's done. When it's done. Get outta here, <laugh>. I'm working. Right.
Steve Gibson (00:25:48):
So anyway, this time I will have a beautiful legacy, which spin writes seven will be able to inherit from spin, right. Six. And the just as I was reading this, I, I realized that the other cool thing about this is that I have now sequestered all of that special case crap that, that exception handling in one location. So if any additional pro like needs for special casing occurs, it's got a happy place
Leo Laporte (00:26:16):
To live. Oh, so a good idea. Yeah.
Steve Gibson (00:26:18):
It won't ever m m muck up the rest of my career. Higher
Leo Laporte (00:26:20):
Level languages, I think kind of facilitate that a little bit better. I don't, it's probably really tempting with, with you know, assembly language to just do it when you think of it and stick it in there and it's all over the, the code dates. It's
Steve Gibson (00:26:33):
Three bites. Yeah, it's three bites. But
Leo Laporte (00:26:35):
You, you're disciplined and I'm, so I'm sure that you, you do that, but the assembly language doesn't give you any it's like bowling bumpers. You, you really can't. Right? You could throw a gutter ball pretty easy.
Steve Gibson (00:26:47):
Well, there is in high level languages now, because the, the need for this has been recognized. It's called structured exception handling where you, you, you create a block of stuff where you may, you know, there may be a problem. And if there is, then it, it, like, without like con constantly having to test for it throughout your code, you, you, you've told it where you wanna go in the event that that happens. And that's a little bit like what this is though. In, in, in, as you said, in in Assembler, I had the advantage of knowing the structure of the stack, knowing all of what's on it. I did have to make sure that my code, there wouldn't be any side effects from just aborting like at any time the, you know, the, the, the inner loops of my code makes a call for some IO with the drive, which may never come back. Then, then, then that's the, that that's essentially the power that I gave the io abstraction layer is if it sees a problem, it just, you know, discards all of the stack and, and when it returns from it, it goes back to the top level.
Leo Laporte (00:27:54):
So yeah, that's another thing. Li is really well what they call it their common lisp condition system, but it has exception handling built into it. And it's nice. Very powerful. It's a really, it's kind of, I mean, I'm sure that what they're doing in other languages is, is kind of inspired by it. It's really quite, quite amazing.
Steve Gibson (00:28:14):
I would love to know whether McCarthy put that in, in he did not. Version
Leo Laporte (00:28:17):
One. No, he did not. And that's what's in the, the, I look forward to the day where you don't have anything to do <laugh>. And and then I have a friend who says, don't learn golf until I can teach you don't learn lisp until I can, we can talk about it. I can't teach you a thing. Okay. But Lisp is kind of amazing. So McCarthy was really taking symbolic logic and algebraic expressions and turned it into a programming language. But the common lisp now is, has evolved like 30 or 40 years of, of evolution since McCarthy thought of that in 1956. And is really, I think where a lot of academic research and a lot of academic thought about what's the right way to write code kind of ended up in, in common Lisp and and, and its successor scheme and racket's a very good example of that. But the common lisp condition system is, is kind of famous for exactly that. Taking all the errors and, and making sure that you can handle them. And then you don't have to worry about errors cuz they'll, you know, everything will, will be okay. <Laugh>, we'll see <laugh>.
Steve Gibson (00:29:25):
Okay, let's, we're gonna get into location tracking behavior. Let's take a break and then we'll indeed do one in the middle of this, but that would be a good
Leo Laporte (00:29:33):
Time indeed. All right. Glad to do it. And I want to tell you all about ACI learning. In fact, if you watch the shows, you see the aci banners all around because they are, we're very happy to say our studio sponsors I said, do you want us to say we're coming to you from the ACI learning twit Eastside Studios? And they said, no, no, no. You can call it twit Eastside Studios, but it's brought to you by ACI Learning. I said, that's fine. A you may say, well, wait a minute, who are these guys? I know you know the name it Pro, everybody listens to this show knows it pro. In fact, I would guess probably half the people listening to this show are customers ACI Learning and IT Pro have merged to really make a behemoth the best way to do training.
(00:30:22):
Yes. Everything you love about IT pro is still there. All the great trainers, all the great content, the 7,000 hours of library on demand content, by the way, you might note that number is going up. Thanks to aci. I learning, ACI Learning has added some additional features. Audit Pro for instance, because auditing is becoming more and more important part of your compliance strategy. Practice Labs, IT Pro always had great practice labs. You should see what they got. Now they've fully expanded with a, an astounding 30% of ACI learners are MSPs managed service providers. You know, I, I'm not surprised because MSPs are go-getters, right? They're people who said, you know what, I, <laugh> like Russell, who is our msp, I'm gonna, I'm going to have many clients. I'm gonna become the king of this stuff. They usually know more and they want to know more all the time.
(00:31:17):
ACI Learning is dedicated to supporting your MSP team through any challenge. Msps, for instance, they love the ACI learnings practice labs where you can test and experiment before you deploy new apps or updates. Not just learning. You can actually use it to test stuff without compromising your live system. You could test out your skills on virtual machine labs with multiple instances of Windows Server desktop clients OS 10 Linux, iOS, and Windows platforms. No matter what you use, even if you're on a Chromebook, you can use these practice labs. You can prepare for your challenging certification examinations with practice tests. I always think it's a good idea to take the test before it, you know, really counts. You could take and even retake tests to make sure you're ready before you actually sit for the exam. Also, just getting you used to the format and the style and getting your brain in that, in that space.
(00:32:14):
It makes a big difference in your scores. A great testimonial from a happy Ms. P team leader. I had 110 engineers in the field. He said there's a quote and we had dozens of it pro accounts last year alone. 110 engineers, they passed over 40 certs, 40 <laugh>. That's a, you know what, that's what I love about MSPs. They, it's their business usually. They're really putting their heart and soul into it. And I love that. If your I treat training is not raising your team to the level you aspire to or need, you gotta have ACI learning the training industry's completion rate and this kind of thing. Barely 30% ACI learning. 80%. And why is that important? It means the training's engaging. It's fun. People finish it cuz they're getting something out of it, right? It's not boring them to tears. Don't settle for subpar training.
(00:33:07):
This is a format IT professionals and people aspiring to be. I it professionals really want the, the interface is great for MSPs. You're gonna assign courses assign episodes. You can manage seats unassigned and assigned team members. You can access monthly usage reports to see it. Is it getting used? How well is it getting used? You can see metrics like logins, viewing time courses, viewed tracks completed. All of this in the ACI Learning Pro portal. Really, really nice. And it helps you justify the spend. You know, if you've got got a management team looking over your shoulder or board of directors, it helps. You can say, look what we're getting here. And it, and it's very easy. You'll also it's very important, stay at compliant with regulations and identify potential risks and weaknesses before they become problematic. That's where Audit Pro is so valuable.
(00:33:59):
You'll be future proofing your business. It helps you retain top talent cuz this is a benefit that companies can give their IT teams and they really appreciate it. And of course you benefit cuz your team's getting those skills. While other training companies do not comply and often do not comply with regulatory requirements. ACI learning, and this is should be important to you as ISO certified. That means you're getting the world class training your team deserves. I can go on and on, in fact, I often do. But let me just say this is what you're looking for. ACI learning their courses are easy to navigate, fun to watch the structures very straightforward. They chunk it up at a 20 and 30 minute segments. You can watch it at your convenience, try it for yourself. Then you can bring your whole team along for individuals.
(00:34:46):
The code is TWIT three zero, TWIT 30 for 30% off a standard or premium individual IT pro membership. They also have lots of free programming. You can watch, learn more about a C l learning's, premium training options across audit IT and cybersecurity readiness. But didn't even mention that. That's a huge one. The website is go dot aci learning.com/twit and there are volume discounts you, they have training for teams from two to 1000 members. I mean, they'll scale to whatever size you need, but you get the volume discounts. They start as as little as five seats. Fill out the form, go dot aci learning.com/twit to learn about a free two week trial for training your entire team as an individual. Don't forget, offer code is TWIT three zero for 30% off go dot aci learning.com/twit. I, I know I go on and on about 'em. Really proud of what the, what the team has done. And now in conjunction with ACI learning, they are, they are just a going great guns, just fantastic. Steve, sorry, back to you.
Steve Gibson (00:35:50):
Okay, not a problem. So last week I opened our look at the forthcoming standardization of consumer location tracking technology by writing. It seems that any powerful new technology gets used for both the benefit and detriment of society. In other words, it's a mixed blessing. And so is the case for air tags. Those popular and handy Bluetooth le you know, low energy Dons that are all about their location. Now as for popularity, I should note that Apple announced their $29 tags two years ago last month in April of 2021. So in the past two years, they alone have sold more than 1 billion worth of air tags amounting to around 55 million of those little buggers and tile. Another tracking tag company told Wired Magazine last year that they had sold about 40 million of their popular little devices. So we know the consumers love the concept and when tightly integrated with smartphones, they also love their ease of use.
(00:37:08):
A single Apple account can be associated with up to 16 air tags. As our listeners also know, we ended last week with a controversial tidbit that the forthcoming detecting unwanted location trackers, i e TF specification requires that all qualifying devices be registered in an online database that could be queried by law enforcement. Leo's immediate and certainly understandable reaction was that this would be a deal breaker for the technology. I then posed this question over in G R C'S Security Now News Group to gauge the feelings of those there. And many people felt the same way, often quite vocally. I would argue that nothing is gonna stop the sales of these handy little things for use in the legal and ethical tracking of people's own property. I doubt that anyone using them to keep track of their car keys or backpack will care. And I believe that the spector of a registration database, actually I hope that the spector of a registration database that can be queried by law enforcement when probable cause has been established is what's needed to help curtail the abuse of what really is a very powerful consumer technology.
(00:38:31):
So I think it's perfect that Leo and I may have differing feelings about this and that we'll be able to discuss the pros and cons, which will make for a more interesting and balanced podcast for our listeners, it's already clear that the issues are not entirely black and white, but one thing that did arise from my posting into GRCs News Group was that there was significant mis presumption about many aspects of this technology. That's understandable since this technology has not yet been elucidated, which is why we're here today. One example of mis presumption is that people assumed that Apple themselves would be aware of the location of everyone's air tags and could track them. The technology that Apple has deliberately designed makes that explicitly impossible. And it has always been possible for anyone discovering an air tag to directly query the device to obtain the last four digits of its owner's phone number.
(00:39:33):
This is done to help people determine whether a tag they may discover might belong to someone obvious, you know, who they know. Now, I recognize that querying an air air tag you have found is very different from some evil database in the sky. We'll get back to that by the end of our technical walkthrough. To me, and I may be alone within this, you know, which is fine. The idea that casual consumers should be entitled to the absolute private tracking of others, which is illegal in many jurisdictions, seems against society's best interests. Okay, before we get any deeper into the pros and cons, let's learn about how this technology operates and what it means for users and abusers. Once I had fully absorbed this detailed 22 page specification, which I mentioned was a hodgepodge, I mean it is, there's typos, there's grammatical errors. I I was wishing that I, you know, had an editor open on it rather than just reading a pdf.
(00:40:37):
It's kind of discouraging <laugh> I could have. Yeah, I mean, it, it's rough and, and all out of sequence you're having to like, it's like, wait a minute, why are we talking about that here when it should go over there? So, you know, let's hope they get this fixed. But more importantly, I was very disappointed by what was missing from it. I was hoping that we were gonna get a full working technical specification for the operation of Bluetooth low energy trackers with all of the crypto and the other details spelled out. I wanted that because I wanted to be able to present a detailed walkthrough of that level of the technology which Apple has developed to ensure the privacy of the various parties. Instead, what we have is a small subset of that hole. And I've been unable to locate anything more complete.
(00:41:31):
I don't think they've, that that's been published yet. This document does however, provide us with the common behavior that's required from small tracking devices to enforce their owner's privacy and the privacy of anyone they may be near. There's still plenty of interesting stuff to talk about, but we're gonna need Apple or Google or someone to publish another specification to fully satisfy our curiosity. What today's specification does is outline how location tracker accountability is created, and it's also about enforcing the privacy of the users of location trackers. In other words, users should not misuse tracking power and there should be fair accountability if they do, but neither should their legal tracking in any way compromise the privacy of what they are tracking. As I got more deeply into this and brought myself up to speed about the features and operation of Apple's current air tag technology, that is what we've been using for the last two years.
(00:42:42):
It appeared that most of this has already been implemented by Apple. So this began to feel more like Apple finally taking the covers off of some of the existing air tag technology that they had already developed as a means of encouraging industry-wide standardization for all of these low power short range Bluetooth and NFC tags. This is important since in this entire model location is determined by others in a crowdsourcing model. You know, whereas fancy and expensive, excuse me, technically you need to have a cellular account which costs something every month. Traditional G p s style trackers, they use both g p s satellite positioning and built-in cellular tech telephony for reporting back to headquarters. Compared to that, all of these little Bluetooth low energy tags, you know, BLE e tags rely upon having their periodic broadcasts picked up and their position relayed by other bystanders smartphones. This means that enlisting all of Android and potentially all other devices into one big happy crowdsourced family.
(00:44:13):
Pardon me, I've been been suppressing a cough there for a period. Let it go. Let it all out. <Laugh>. this means that enlisting all Android and potentially other devices into one big happy crowdsourced family will significantly improve the tracking experience and responses for everyone. One New York Times reporter writing last year about this exploding industry in consumer tracking devices planted multiple sets of three different types of trackers on her husband with his full consent and knowledge. And she noted that while he was near their sparsely populated home, she didn't get much updating on his position with any of the non G P S trackers. But the moment he ventured into the city, presumably in New York, the tracking information available exploded and became absolutely real time. That was due to the fact that so many people were carrying iPhones which were autonomously pinging the air tag he was carrying or rather it was pinging them and they were all simultaneously reporting its location as being near to them at that moment. And since iPhones are adept at knowing where they are, the tags location can be inferred from that.
(00:45:39):
For those who are not familiar with R F C style terminology, I should preface what comes next by noting that the spec in RFC style uses all caps qualifiers so that its reader understands how various requirements should be taken. Specifically the capitalized phrases used are must whose, you know, implication is obvious, must not required, shall, shall, not, should, should not recommended, not recommended may an optional. So keep that in mind. And with that in mind, it was interesting to see the section on applicability where the specification states that these best practices are required in all caps for location enabled accessories that are small and would not be easily discoverable on their own in the world for large accessories such as a bicycle, these best practices were merely recommended as opposed to required accessories are considered easily discoverable and thus recommended but not required. If they meet one of the following three criteria, the item is larger than 30 centimeters in at least one dimension. Okay? So that's about a foot. If it's, if any dimension is larger than a foot, it's it's recommended but not required. Or the item is larger than 18 by 13 centimeters in two dimensions, that's about five by seven inches or the item is larger than 250 cubic centimeters in three dimensional space. If it was a cube that would be 6.3 centimeters on a side or about two and a half inches on a side. So
Leo Laporte (00:47:39):
If it's the size of a refrigerator, you don't have to do it.
Steve Gibson (00:47:43):
If it's bigger than a bread box Leo, then that's
Leo Laporte (00:47:45):
Right. That's cuz everybody knows it's
Steve Gibson (00:47:47):
There. Yeah, that's right. Right. Yeah, it's not gonna, you know, it's like hiding. Why is this, why is R two D two following me? Well, yeah at least you know it is. Yeah. So, you know, the, this detecting unwanted tracking specification is meant to protect from any bitty trackers, you know, like apples air tags, which are discs two and a quarter inches in diameter by about 0.3 inches thick. You know, as I said, if it's bigger than a bread box, it doesn't need to rigidly follow this specification. One of the people who responded to my GRC posting noted that he had a pair of very nice electric bikes stolen from their garage and he was wishing that they had been trackable with the rapidly growing popularity of this technology. I think it's foreseeable that such high value desirable and inherently mobile objects such as a very nice bicycle will incorporate tracking as a sales feature.
Leo Laporte (00:48:48):
Oh, there already are for e-bikes. Yeah, and exactly. Yeah.
Steve Gibson (00:48:51):
Wondering whether that had al already been done. It has a quick, a quick Google revealed a story from just last month, which was titled Why A Bike With Built-In Find My Capabilities. Mm-Hmm. <affirmative> is total genius.
Leo Laporte (00:49:05):
Apple showed it art, I think when they showed off air tags, the, they ah, we're talking about third party uses of this technology. Yes. Yeah. Yes.
Steve Gibson (00:49:13):
So, and, and, and the article had three bullet points. It said VE veri, bad name Vectrix.
Leo Laporte (00:49:21):
I think it's Velo tricks.
Steve Gibson (00:49:23):
Okay, that's somewhat
Leo Laporte (00:49:24):
Better because a velo bicycles were originally called velo ps so it's electric
Steve Gibson (00:49:29):
Ves velo ps Yeah. And Velo tricks. Yeah,
Leo Laporte (00:49:32):
Got it. Electric velop.
Steve Gibson (00:49:33):
Yeah. Anyway, so it's their
Leo Laporte (00:49:35):
New you sound skeptical <laugh>,
Steve Gibson (00:49:37):
It's their new, I don't know. You know, I was calling that router the mi the micro router.
Leo Laporte (00:49:43):
Yeah, for a long time. A long time.
Steve Gibson (00:49:44):
Yeah. Yeah. I don't think they appreciate that.
Leo Laporte (00:49:46):
I don't know how they pronounce it. Mic
Steve Gibson (00:49:48):
Sounds like something you take, you know, medicine for. Yeah, no, not good. So anyway, this thing is the Thunder one V S T E bike has a builtin air tag feature says you can track your bike just like you can track your iPhone and your AirPods. He, and, and finally it said, find my is potentially more private and much cheaper than a dedicated cellular GPS tracker. And you know, to that I would add that having it built in, it can run off the e-bikes battery. So avoiding the annual otherwise needed battery replacement and more importantly, assuming that the technology is integrated into the e-bikes electronics, it cannot be discovered and removed. The final point is that hopefully the e-bikes console will prominently advertise the fact that it incorporates built-in anti-theft air tag tracking so that the lazy thief who wants a free ride will think twice and just walk away instead.
(00:50:50):
So there is every indication that for such items, especially when they become cross-platform for compatibility with both iOS and Android, that we're gonna begin seeing air tag tracking becoming a competitive marketing feature for, you know, these kinds of devices where, where a little bit of incremental price, you know, or or cost increase justifies the cost. Okay. So moving on, I want to next share some formal definitions, which the specification uses. It'll help in what comes in help in understanding what comes later, although I'm gonna also be de obfuscating this as we go. So this is more than just defining the terms since a lot of reading between the lines is also possible. So the spec says throughout this document, these terms have specific meanings. The term platform, which, you know, we sort of have a sense for, in this case, in this document, it's used to refer to mobile device hardware and associated operating systems like phones, tablets, and laptops.
(00:51:59):
So the platform is what the, is what we are carrying in our pockets, not the, the not the air tag, which they insist on calling an accessory. The term owner device is a device that is paired to the accessory and can retrieve the accessories location, you know, so a smartphone then the term non-owner device refers to a device that may connect to an accessory but is not an owner device of that accessory. The term location tracking accessory refers to any accessory that has location tracking capabilities including but not limited to crowdsourced location, G P S S, wifi cell tower, et cetera, and provides the location information back to the owner of the accessor via internet cellular connection, so forth. So that's sort of just broadly, you know, location enabled tracking accessories, non-air tag ish things and also of course air tags. The term location enabled state refers to the state and accessory is in where its location can be remotely viewed by its owner.
(00:53:15):
The term location enabled advertisement payload refers to the Bluetooth advertisement payload that is advertised is the term, you know, broadcast when an accessory has recently is currently or will in the future provide location updates to its owner. And I have no idea how it knows it will be able to in the future, but okay. The term unwanted tracking refers to undesired tracking of a person, their property or their belongings by a location enabled accessory. The term unwanted tracking detection refers to the algorithms that detect the presence of an unknown accessory traveling with a person over time. Unwanted tracking alert refers to notifying the user of the presence of an unrecognized accessory that may be traveling with them over time and allows them to take various actions, including playing a sound on the accessory if it's in Bluetooth low energy range. And there's a lot more work we will be getting to.
(00:54:21):
And finally, the term platform compatible method refers to a method of communication between the platform, which, you know, is the thing we're holding in our hand or pad or whatever, and the accessory accessory manufacturers to exchange information including but lot but not limited to, you know blue Bluetooth advertisements, HTTP and so forth. So that's sort of a dumb term. I don't know why it's even there, but it is. Okay. So I find it awkward to refer to tags as accessories, which is what the spec does. So I will tend to use the simpler and clearer term tag, but when I'm quoting the specification, I'll use its language of referring to these accessories or the, to these, you know, tags which are accessories. So tags can be in one of two major modes and this affects their behavior. They can be in so-called near owner mode or separator mode and the tag knows each tag periodically emits a broadcast hoping to be hurt to be heard by some spa by like some passing smartphone or Bluetooth enabled device.
(00:55:40):
And later we'll see that by periodically we mean every half second to two seconds. So these things are quite chatty if the tag is within range of the owner's smartphone and it's actually any of the owner's multiple devices that are on the same account with which it has previously been paired, the owner's smartphone notifies the tag that its owner is nearby. So that's what places the tag into its near owner mode is it does a ping and, and some and the owner's device says, yeah, you know, you're here. And that in other, that among other things suppresses its broadcasts. The specification states the accessory shall, again, all caps shall transition from separated to near owner mode if it has reunited with the owner device for a duration no longer than 30 minutes. But I suspect this transition is typically immediate because there's no reason for it not to be, the specification is likely leaving some latitude there.
(00:56:50):
Conversely, the specification states the accessory shall transition from near owner mode to separated mode if it is physically, if it has been physically separated from the owner device for a duration no longer than 30 minutes. Okay. Now, since BLEs range is limited, it makes sense for a tracking device to not immediately flip into separated mode. But this says that it must do so within 30 minutes of being away from its owner. One of the definitions we just noted above was for location enabled state. The specification further explains that by saying the accessory shall maintain an internal state that determines when its location is or has been available to the owner via a network. This state is called location enabled state misuse of location enabled accessories can occur when the owner's device is not physically with the accessory. Thereby the accessory should maintain a second internal state denoted.
(00:58:04):
The near owner state, which speak a little redundant here, which indicates if the accessory is connected to or nearby one or more of the owner's devices near owner state can take two values. You know, true or false, either near owner mode or separated mode. Near owner mode is de is denoted as the opposite <laugh> of separated mode. They're being very clear about this. When the device is in location enabled state, it is broadcasting a payload containing the most recent location it has been able to obtain. This payload is not surprisingly called the location enabled payload. And the spec says it is recommended that the location enabled payload is only advertised when the accessory is in its separated state. The reasoning behind this recommendation is that unwanted tracking detection relies on the Bluetooth low energy advertisements emitted while in the location enabled state to determine if an unknown accessory is traveling with someone who is not the owner.
(00:59:15):
If the location enabled payload is advertised only in the separated state that minimizes false positive unwanted tracking alerts. Okay, well now that's sort of obvious. The location enabled payload contains the most recent location information that the accessory tag was able to obtain from some nearby smartphone, which is what let it know where it was. So it would make no sense for a tag to be broadcasting its location when it's nearby and therefore in its near owner mode, the spec ads, the accessory shall broadcast the location enabled advertisement payload if the location is available to the owner or was available anytime within the past 24 hours. This allows unwanted tracking detection to operate both between and beyond. The specific moments and accessories location is made available to the owner. It's this so-called location enabled advertisement that is the primary indication of tracking. That's the Bluetooth advertisement that sets off alarms in nearby phones.
(01:00:34):
The idea being that the accessory tag is somehow has, sorry, so has somehow obtained a location fix within at least the past 24 hours. And being a good little tracker, it's hoping to find someone who will dutifully relay its location back to its owner. In other words, you know, this is tracking, it's not necessarily unwanted tracking, but it's definitely some form of tracking. This should be disabled when the device is with its owner since it makes no sense to be broadcasting its location in that situation. The false positive unwanted tracking alerts referred to earlier that are being eliminated by the suppression of location enabled advertisements occurs. For example, if two or more people each having smartphones are together and somebody also has a tag somewhere that belongs to one of them, if they're all traveling together, the tag is also traveling with the non-owners.
(01:01:43):
So if that tag were to be emitting its location enabled advertisements, then the non-owners phones would believe that they were being tracked and would generate false positive alerts. So the pro the, the fact that you have the proximity of the owner placing the tag into its near owner mode and thus suppressing these overt tracking announcements is a good thing and that's where you get your false positive suppression. And speaking of these Bluetooth low energy advertisements as I mentioned before, they are quite frequent. The specifications advertising policy formally specifies an announcement interval of between half a second and two seconds. So, you know, lots of this happening. Bluetooth low energy devices have MAC addresses and therein lies a problem in the spec. We are wanting to prevent the tag from being tracked by an adversary. So on one hand there's not having the tag being with someone who, whose owner is using it to track, but then there's also just the tracking of the tag itself that wants to be prevented.
(01:03:01):
So here's what the spec has to say about that. The Bluetooth low energy advertisement payload shall contain a resolvable and private address for the accessory, which is the six bite Bluetooth LE Mac address. The address must be private and it must rotate periodically and be un linkable. Otherwise, if the same address is used for long periods of time, an adversary may be able to track a legitimate person who is carrying the accessory. A rotation policy aims to reduce this risk. A general approach to generate, to generate addresses meeting this requirement is to construct them using a pseudo random function, taking as input a secret key established during the pairing of the accessory and either a counter or a course notion of time, the counter or COR course notion of time allows for the address to change periodically. The secret key allows the owner devices to predict the sequence of addresses for the purpose of recognizing its paired accessories.
(01:04:19):
An accessory shall rotate its resolvable and private address on any transition from near owner state to separated state, as well as any transition from separated state to near owner state. So like as soon as it realizes it's no longer with its owner, bang, immediately the MAC address changes. And similarly, as soon as it gets it, it is back within the region of of, of its owner. The MAC address changes again, but it also changes autonomously. When in near owner state, the accessory shall rotate its resolvable and private address every 15 minutes. This is a privacy consideration to deter tracking of the accessory by non-owners when it is, when it is in physical proximity to the owner. Since it is nearby, the owner device is able to maintain synchronization so that it's able to recognize, remain paired with its known accessories. When in a separated state, the accessories shall rotate its resolvable and private address every 24 hours.
(01:05:29):
This duration allows a platform's unwanted tracking algorithms to detect at the same accessory, is in proximity with it for some period of time when the owner is not in the tags or accessory's physical proximity. So this seems well thought out. Devices rotate their eight by MAC address on a schedule as directed by a secret key. This is exactly analogous to the T O T P one time passwords where you all, when many of us are using today though with six eight bit bytes rather than only six digits. By knowing each device's secret key, all future MAC addresses can be determined and no one tracking a device based on its periodic broadcasts will be able to determine any tags. Next MAC address. It's worth noting that the devices have no actual Native Mac addresses. Unlike the anti tracking technology we've developed for smartphone wifi, there is not one rotating spoofed Mac address used when roaming and another actual physical fixed MAC address used when associated or paired with a wifi, you know, home base or, or access point.
(01:06:54):
So these tags are all simply using the traditional eight bite, 48 bit mac as a short-term rotating id. And there's a galaxy of them, you know, a hundred million of them out there now and growing all occasionally changing their identifier, following a predictable pattern that only their owner knows. Another intriguing aspect of this specification is that non-owned devices are required to do I'm sorry, of the specification is what non-owned devices that is. That is the, the tags that are in their separated state are required to do, to reveal themselves. The spec calls this non-owner finding, and it has a number of components. The spec says once a user has been notified of an unknown accessory traveling with them, it is required that they have the means to physically locate the accessory. This is called non-owner finding of the accessory. These capabilities are both required and recommended and reflect hardware to be incorporated into the, to enable non-owner finding.
(01:08:19):
Now we'll explain it. Motion detection. The accessory should include a motion detector that can detect accessory motion reliably. For example, an accelerometer, if the accessory includes an accelerometer, it must all caps be configured to detect a change in orientation of plus or minus 10 degrees along any two axes of the accessory. After some number of hours between eight and 24 chosen randomly from a uniform distribution. So that would be an average of 16 hours. So no fewer than eight, no more than 24, but an average of 16, the accessory being away from its owner and in a separated state, the accessory's motion detector will be enabled. While the motion detector is enabled, it must be able to detect motion within 10 seconds. Okay, so it's sampling its position at ten second intervals, presumably to conserve power. The spec says if motion is not detected within the ten second period, the accessory must stay in this state until it exits separated state.
(01:09:43):
Okay? So, so accessory leaves the owner s after some time between eight and 24 hours, from then the motion detector is activated, and at ten second intervals, it starts sampling its angular position in space. The spec says if motion is detected within the ten second, send seconds between samples. The accessory must play a sound after any motion is detected. The movement detection period is decreased from 10 seconds to half a second. Okay, so it starts sampling much more quickly after first detecting any motion. The accessory must continue to play a sound for every detected motion. The accessory shall disable the motion detector for six hours under either of the following two conditions. Motion has been detected for 20 seconds at the half a second sampling rate or 10 sounds have been played. Okay? So, so after this thing has become motion sensitive, which after an average of 16 hours of being away from its owner, then any motion of more than 10 degrees on two ax axis will cause it to make a sound and will also cause it to shorten its sampling to, to half a second and to continue making sounds if it continues being moved until either 20 seconds have passed or 10 sounds have been played after that point, it then goes into a six hour, they call it a back off.
(01:11:32):
So it, you know, goes to sleep for six hours. It says the, the spec says if the accessory is still in its separated state at the end of the six hour back off, which has, you know, it's gone silent, essentially, it's not gonna just keep beeping or screaming, whatever it's gonna be doing. The unwanted tracking behavior must restart. So again, after six hours of quiet time, if it is again moved, it starts making sounds. Any Bluetooth LE connection from a paired device must reset the separated behavior and transition the accessory to con to connected state. In other words, the instant it's back with its owner, then it's paired and it put, and it shuts this down and it goes back in, into you know, near owner state. And finally, they said the accessory must include a sound maker, for example, a speaker of some kind to play sound when in separated state, either periodically or when motion is detected.
(01:12:34):
It must also play sound when a non-owner tries to locate the accessory by initiating a play sound command from a non-owner device. When the accessory is in range and connectable through Bluetooth le, the sound must be loud and the sound must be played for a minimum of five seconds each time. And in the spec it goes into a, a detailed specification of the measuring of loudness that the devices are able to have. Okay, so this gives us a system where after a tracking device has been separated from its owner for an unknown interval of time, randomly chosen between eight and 24 hours, its motion detector activates. At that point, it begins taking readings of its angular orientation in three space every 10 seconds. And if it finds that it's been rotated by more than 10 degrees through any two axis between successive position samples, it will emit a clearly audible sound for five seconds.
(01:13:34):
And if any qualifying movement is detected within those ten second intervals, it will have, you know, essentially that will have roused it so that it will start sampling twice per second to allow it, to make it noise much more responsibly to someone who may be attempting to discover its location by, you know, moving things around. All of this occurs whenever a tag is separated from its owner for between eight and 24 hours. It's about requiring anything that is small that can track to deliberately reveal itself periodically. And in doing so using simple sound, which does not require any technology where the tag is located. Note that a lot of attention has been given to detecting unwanted tracking tags with another smartphone, but not everyone has a phone that's smart enough to do so today. Today, unless that air tag Apple app is launched and running on an Android phone, no Android carrying user would be able to detect an unwanted nearby tag.
(01:14:48):
This spec will be changing that soon for new Android devices, but we know that there will remain many non-graded Android devices in use for years. And there are also non-smart cellular phones. I was recently listening to a talking head on some show suggesting that one way to keep young people away from the perils of social media would be to equip them with only a dumb phone capable of making and receiving telephone calls, texting and taking pictures with its camera. Now, I don't know whether this person has ever actually been around any young kids, but that would be a tough sell when they're surrounded by their peers who are gleefully deep into the social internet. So good luck with that, but still, the point being not everybody is carrying a cell phone. So there's clearly a need to expose trackers through some low tech means, and sound is the obvious choice.
(01:15:46):
This is not what someone wishing to track someone stealthily would choose, right? Because the device is gonna give itself away after that initial period of eight to 24 hours of separation from all of it of its owner's devices. Any tag that remains separated will generate attention getting sounds whenever it's significantly moved. And once it is done, so 10 times or for 20 seconds of movement in its faster sampling mode, it will go quiet for six hours after which it will again reawaken and notify of any movement. The obvious weakness in this system is that tracking requires radio, but not sound. So arranging to enclose a tag inside some sort of acoustic suppression container, which is transparent to radio, might defeat the tag's audible, you know, help me, I become separated from my owner, cries for help in addition to physical movement, which will trigger sounding any nearby device within radio blue, you know, Bluetooth LE radio range of a tag, whether a tags owner or non-owner is able to remotely command any tag to emit its sound.
(01:17:12):
So if, for example, a suspected tracker is detected, that detecting smartphone's, user interface for managing tags can request any unseen tags to sound off to aid in determining, you know, their location tags also contain a wealth of queryable information. This includes a unique eight bite token, A U U I D that serves as a unique identifier for the accessory make and model. The eight bite value will be listed in a public registry so that the tags issuing company can be determined. Tags also contain the manufacturer's name in a, in an up to 64 bite field, so plenty of length and also another 64 bites for the model's name. So that can be made clear. There's also an eight bite accessory category indicator only. The first single bite of the eight bites is presently defined, though eight have been set aside and many of the values of that bite are already defined.
(01:18:29):
To give you a, a sense for how the publishers expect these tags are gonna be used. Those, the, the, the, the enumerations of the eight B of the one bite that's been defined are things like a generic finder. Then there's also o other also luggage, backpack, jacket, coat, shoes, bike scooter, stroller, wheelchair, boat, helmet, skateboard skis, snowboard, surfboard, camera, laptop, watch, flash drive, drone headphones, earphones, inhaler, sunglasses, handbag, wallet, umbrella water bottle tools or toolbox keys, smart case, remote hat, motorbike, consumer electronic vehicle apparel, transportation device, sports equipment and personal item. Well done. You just passed our cognitive test, <laugh>, <laugh>, you do not have dementia. Steve, congratulations <laugh>. And had I been able to do that from memory, Leo <laugh>, I would feel, I would agree with you <laugh>. So anyway, that gives us some sense for the, for the people behind this are thinking about the future and about the wide potential for this location tracking technology.
(01:19:45):
I suspect that there's every chance that, as I said, that many higher end consumer products like that e-bike, you know, which are prone to misplacement loss or theft, or which might need to be located with some urgency such as an inhaler, may eventually incorporate this consumer location technology as a sales feature. The last item of the queryable data is a four bite 32 bit value, which enumerates a tags capabilities. Only four bits are currently defined. Those are supports sound supports, motion detection supports serial number lookup by nearfield and supports serial number lookup by Bluetooth. There's also some interesting specification about deliberate ment. The spec says the accessory shall have a way to be disabled such that its future locations cannot be seen by its owner. Ment shall be done via some physical action. For example, a button press a gesture or the removal of the battery.
(01:21:01):
The accessory manufacturer shall provide both a text description of how to disable the accessory as well as a visual depiction, for example, image diagram animation, et cetera. That must in all caps be available when the platform, you know the thing that the, you know, the smartphone is online and optionally went offline. Disablement procedure or instructions can change with accessory firmware updates. A registry which maps product data to an affiliated U R URL supporting retrieval of disablement instructions shall be available for platforms for reference. Now again, remember the platforms in this speck refers to smartphones, pads and similar devices with full user interfaces. And they said this U R L must return a response, which can be rendered by an H T M L view. So this says that if someone discovers an unwanted tracking device, that eight by registered product ID data, which can always be retrieved directly by querying the device over Bluetooth, will, among other things, point to a url which returns H T M L that any smartphone can render to obtain clear and updated instructions from the device's manufacturer about how to manually disable the tracker.
(01:22:39):
And this is all in, you know, capital musts. But this always requires physical access to the device, at least at this point in the evolution of the specification. It cannot be done remotely over radio. It's foreseeable that this might be allowed over NFC since that requires essentially physical proximity and it might be simpler. As we'll see, the spec does make clear some distinctions about what can be done via NFC and what can only be done over Bluetooth or rather Bluetooth and only under nfc. All devices are also serialized. The spec explains the serial number shall be printed and be easily accessible on the accessory. The serial number must be unique for each product id. The serial number payload shall be readable either through N F C TAP or Bluetooth le. So again, that can be done at a distance. The serial number payload shall be readable either through NFC TAP or Bluetooth.
(01:23:52):
Le. Note that this does not mean the serial number itself. I'll get to that in a second. They said for privacy reasons, oh, they're gonna say it for privacy reasons. Accessories that support serial number retrieval over Bluetooth. LE must have a physical mechanism, for example, a button that shall be required to enable the remote get serial number OP code command. The accessory manufacturer shall provide both a text description of how to enable serial number retrieval over Bluetooth le, as well as a visual depiction. Again, image diagram animation, et cetera. That must be available when the platform is online and optionally went offline. The description and visual depiction can change with accessory firm or updates a registry, which maps product data to an affiliated URL that will return a text description and visual depiction of how to enable serial number lookup over Bluetooth. LE shall be available for platforms for reference.
(01:24:54):
This URL must return a response which can be rendered by HTML view. So we have the same set of requirements for enabling the retrieval of a device's serial number remotely over Bluetooth as we do for disabling the device. In both cases, some sort of physical action must be taken with the device by an individual to prove that it is in their physical possession, either to disable it and or to learn its immutable serial number. It's obviously required for the serial number since unlike its MAC address, which is nothing but a keyed pseudo random sequence, the serial number never changes. And if it were available remotely without contact with the device, it could be used for long-term tracking. But as I noted before N F C, which is as name suggests, a near field contact technology is allowed greater latitude. The spec says for those accessories that support serial number retrieval over nfc, a paired accessory shall advertise a U R URL with parameters.
(01:26:07):
This U R L shall decrypt the serial number payload and return the serial number of the accessory in a form that can be rendered in the platform's H T M L view. Okay, so first of all, an fc. If the tag in the user device both support nfc, then obtaining the device's serial number is as simple as tapping the smartphone against the tag, which you have in your possession to query it. But we also just encountered the phrase decrypt the serial number payload. Okay, so here's what that's about. The get serial number OP code is used to retrieve serial number lookup payload over Bluetooth LE or nfc. This must be enabled for five minutes upon user action. On the accessory, you know, the button press for, for example, 10 seconds to initiate serial number read state. When the accessory is in this mode, it must respond with the get serial number response OP code and serial number payload operand.
(01:27:20):
For security reasons, the serial number payload return from an accessory in the paired state shall be encrypted A registry which maps product data to an affiliated url, which will decrypt the serial number payload and return. The serial number shall be available for platforms to reference. This U R L must return a response, which can be rendered by an H T M L view. So this tells us that the data contained within the public registry is encrypted and that only the tag device itself contains the information required to decrypt its own publicly stored serial number. When a user encounters a tag that's in its separated state and either presses a button on the tag or taps it for a nearfield exchange, that smartphone receives a U R L from the tag, which contains the address F of the lookup, and also the decryption keying information needed to decrypt the publicly stored and encrypted serial number.
(01:28:30):
Thus, only someone who is in physical possession of a tag may use the tag to obtain its own serial number electronically. But remember that the serial number must also be physically printed on the device. This suggests that this electronic fallback is provided in case you know, some would be malicious tracker person thinks they're getting very clever by sanding off the devices exposed an obvious serial number to make it anonymous. Well, that won't work. Hmm, since the serial number is an important piece of the hole, the spec further explains Serial number lookup is required to display important information to users who encounter an unwanted tracking notification. It helps them tie the notification to a specific physical device and recognize the accessory as belonging to a friend or relative. However, the serial number is unique and stable and the available partial user information can further make the accessory identifiable.
(01:29:45):
And we'll get to that in a second. The spec has a lot of, a lot of, as I said, out of sequence content that the spec says, therefore the serial number should not be directly available to any requesting devices. Instead, several security and privacy preserving steps should be employed. It says the serial number lookup shall only be available in separated mode For a previously paired accessory. When requested through any long range wireless interface like Bluetooth, a user action must be required for the requesting device to access a serial number over N F C. It may be acceptable to consider the close proximity as intent for this flow. To uphold privacy and anti tracking features like the Bluetooth MAC address randomization, the accessory must only provide non-identifiable data to non-owner requesting devices. One approach, oh, and by the way, doesn't wanna be repeatable either, right? Because that would also be like having something that's not changing.
(01:30:56):
So whatever it is that the device provides, it's gotta be changing. One approach they say is for the accessory to provide encrypted and un linkable information that only the accessory network service can decrypt. With this approach, the server can employ techniques such as rate limiting and anti-fraud to limit access to the serial number. In addition to being encrypted and unlikable, the encrypted payload provided by the accessory should be authenticated and protected against replay replay. The replay protection is to prevent an adversary using a payload captured once to monitor changes to the partial information associated with the accessory, while the authentication prevents an an adversary from impersonating any accessory from a single payload. One way to design this lookup encryption they wrote is for the accessory to contain a public key for the accessory network server. For every request received by a device nearby, the accessory would use the public key and a public key encryption scheme to encrypt a set of fields, including the serial number, a monotonic counter, or a one-time token, and a signature covering both the serial number and counter or token.
(01:32:19):
The signature can e can be either a public key signature or symmetric signature, leveraging a key trusted by the network server, which may be established at manufacturing time or when the user sets up the accessory. Some additional non-identified metadata may be sent along with this encrypted payload, allowing their requesting device to determine which accessory network service to connect to for decryption and for the service to know which decryption key and protocol to use who. So possession of the tag, which would usually allow someone to simply look at its serial number, is essentially duplicated electronically. The tag won't directly inform even a nearby device of its serial number, but it will provide a u r url. Once a button is pressed or nearfield has been used with embedded decryption data that such a device can then use to query and then obtain the device's. True plain text serial number, again, it was also printed on there, so it's not a big deal, but this allows it to be obtained electronically by asking a remote service for this information.
(01:33:37):
Its disclosure can be controlled. And that's a cool part too, right? So since, since someone is having to, to query a server using a URL that provides the data, you can do rate limiting and you can do various anti-fraud things. Okay? And so now we get to the so-called pairing registry where we ended our truncated discussion last week. To reiterate, to reiterate against the background of what we now understand, the spec says verifiable identity information of the owner of an accessory at time of pairing shall be recorded and associated with the serial number of the accessory. For example, phone number, email address, and so forth. Okay? So the process of beginning to use a new tracking tag is to pair it with the user's, so-called platform device, you know, phone, tablet, whatever. And most users will in turn have their real world identity and billing account information associated with their device.
(01:34:47):
So this pairing associates the tag's globally unique serial number with the user's real world identity. The point of this being to create an accountability link from the tag to the real world user with whom the tag has been paired later under the term under the heading persistence, the spec says the pairing registry should be stored for a minimum of 25 days after an owner has unpaired an accessory. After the elapsed period, the data should be deleted. We covered in detail the three steps required to obtain, decrypt and display a device's serial number. But when that serial number is displayed, so too is some deliberately obfuscated owner information that's obtained from the pairing registry. In other words, when you go through getting the serial number electronically you also get some obfuscated information from the pairing registry. The spec says a limited amount of obfuscated owner information from the pairing registry shall be made available to the platform, you know, the user's device along with a retrieved serial number.
(01:36:11):
This information shall be part of the response of the serial number retrieval from a server, which can be rendered in it platform's HTML view. This must include at least one of the following the last four digits of the owner's telephone number. You know, you know, asterisks for everything except 5 50 55 in their example, or an email address where the first letter of the username and the first letter of the domain name are visible as well as the entire top level domain. So, you know, as, as we said last week, s and then fi four asterisks g and two asterisks.com. If my email address were steve grc.com, which it hasn't been for several for quite a while, so don't send them an email at that address. Yeah, that one, that will help <laugh>. Okay, elsewhere. Under the heading privacy considerations, the spec says, in many circumstances when unwanted tracking occurs, the individual being tracked knows the owner of the location tracker by allowing the retrieval of an obfuscated email or phone number when in possession of the accessory.
(01:37:25):
This provides the potential victim with some level of information on the owner while balancing the privacy of accessory owners in the arbitrary situations where they have been become separated from those accessories. So, you know, the idea being that someone who might, who might immediately react with like, who the F is tracking me. This allows the individual to immediately obtain some, you know, it's just a matter of like pressing a button on your phone. The the phone will, will, will get the serial number, make the query the, the, the remote server decrypts it, returns it in HTML to the phone, and you'll get the serial number and some information that hopefully provides you with some relief. It's like, oh, that's what, you know, that's where that tracker went, or whatever. So it may often be someone that you know or can recognize. So we have a pairing registry which associates the real world identity of the pairer with any of the tracking tags that they have paired.
(01:38:31):
Even if a third party discovers or obtains one of these tags and uses the system to get as much information about the tags owner as possible, the absolute limit of that information will be heavily obfuscated identity information such as the last four digits of their registered phone number and email address and so forth. So who has access to the fully un obfuscated pairing registry? The answer is law enforcement, but there's some caveats. Paragraph 3.1, 5.3 titled Availability to Law Enforcement Simply reads, the pairing registry shall be made available to law enforcement upon a valid law enforcement request. Nothing in this technical specification indicates how high the evidentiary bar would be set for such law enforcement queries to be honored. But the point is that the identity of any tag pairing party is tightly controlled for non-authorized access to this information. The only information that anyone possessing a tag they are not paired with can obtain is that obfuscated identity information.
(01:39:50):
So, you know, one purpose of the pairing registry is to aid in immediately resolving the question of who might be tracking you. But since the pairing registry itself contains fully non obfuscated identity information, it's clear that the reason for this is to deliberately and explicitly create end user accountability for the use of what is quite powerful consumer tracking technology. I said earlier that I had the sense that at least part of this was Apple formalizing and publishing the technology that they had already established and deployed in the interest of making it an industry-wide and worldwide standard. In any crowdsourced model, bringing Android into the fold would make the system far more useful for everyone. So I did some further digging and actually it was earlier this morning, and what I found was that none of this is new and that this law enforcement pairing registry has always existed.
(01:40:57):
In one instance, apple writes, this is Apple Air tag, AirPods and other find mind network accessories include features to guard against unwanted tracking. They should not be used to track people and should not be used to track property that does not belong to you. Using these products to track people without their consent is a crime in many countries and regions around the world. If an air tag set of AirPods or find my network accessory is discovered to be unlawfully tracking a person, law enforcement can request any available information from Apple to support their investigation. And since even that was a bit non-committal, I dug some more on February 22nd of last year. So 15 months ago, 20 February 22nd of 20, 22, 15 months ago in their article titled quote, an update on air tag and unwanted tracking, they make this very plain and explicit. They said, we have been actively working with law enforcement on all air tag related requests we've received based on our knowledge and on discussions with law enforcement.
(01:42:20):
Incidents of air tag misuse are rare. However, each instance is one too many. Every this is apple. Every air tag has a unique serial number and paired air tags are associated with an apple id. Apple can provide the paired account details in response to a subpoena or valid request from law enforcement. We have successfully partnered with them on cases where information we provided has been used to trace an air tag back to the perpetrator who was then apprehended and charged. Law enforcement has shared their appreciation for the assistance we've provided in helping them find the source of unwanted tracking. We've identified additional improvements we can make in the information we share and the educational resources we provide. And we will be taking action including making updates to our law enforcement documentation. Well, the surprise in this specification of a registry whose real world identifying data can be made available under due process of law caught us off guard.
(01:43:34):
And I had picked up on it because the tech press was highlighting it as being a surprise. So actually no one should have been surprised. It's not a new thing. This is, this does of course beg the question, who knows? And who would care if they knew? We know that Apple has sold more than 1 billion worth of air tags and the tile has sold more than 40 million units of their own tags. No one appears to care about tag ownership tracking. But I suspect that not many people know or have stopped to wonder. <Laugh> I didn't know, or I might have thought twice. Right? So one reason is that even if they have no idea how any of this works, they implicitly trust Apple. And Apple has never given us any reason to suspect that trust is misplaced. If I were to trust anyone to work hard to keep my information private, based upon all the evidence we've seen during the 17 plus years of this podcast, it would be Apple.
(01:44:44):
So the question is, would anyone particularly care if they knew? I know that if I had something of value that I needed to track like a bicycle or my luggage, I would not hesitate now to pair those tags to my real world identity knowing that any query about the ownership of those tags would need to get past apple's legal department first. And I have to say that I've never really seriously thought about e air tags before, but I have now, even though, you know, we've covered them on this podcast whenever they've made the news. Now knowing what I know, I am absolutely gonna purchase some air tags and I am never going to, again, travel without having them in my luggage. We know that they won't begin squawking until they've been separated from us for a minimum of eight hours or on average 16 hours.
(01:45:42):
So if they're in the belly of a plane along with us, they're gonna be remaining silent until we pick them up after a flight. And just knowing that when, wherever they might be, we'd have some way to know, seems like a bargain to me for 29 bucks each. And I think that being a bit sneaky, I would have one air tag exposed and visible hanging out on an air tag dongle, which are available with another tag deeply hidden and tucked away, rolled up in a sock so that if anyone nefarious did wanna make off with our stuff, they might stop looking after removing the obvious tracker. I'm glad that we took the time to look into this deeply since I've never really thought about it. And I'm glad that Apple is making the effort to work with Google and their Android platform on this so that we wind up with a single global standard, which due to the crowdsource nature of positioning will make it much more powerful and attractive. And, and next week, back to the news. I
Leo Laporte (01:46:51):
Got a hammer
Steve Gibson (01:46:51):
Start off with <laugh>
Leo Laporte (01:46:53):
And I got an ear tag, which by the way, I gotta point out I don't see any serial number on this, but now that
Steve Gibson (01:46:59):
I, it's not like it's not micro etched around the back or no. How about if you open it up and look at the battery compartment? Yeah,
Leo Laporte (01:47:05):
But it's supposed to be visible, right? Screw that. Oh, I don't want anybody tannin this thing's this tough is Oh yeah, hide that. This thing is tough.
Steve Gibson (01:47:19):
You know that we know where your phones are, right?
Leo Laporte (01:47:21):
<Laugh>? Yeah, but I have this on my keys. Yeah, it's already gone.
Steve Gibson (01:47:29):
<Laugh>. Oh, how, how, okay. Wait, wait, wait. Turn that, turn that, turn the hammer over and and use the horrible nail pore sign.
Leo Laporte (01:47:35):
Oh, whoa. I don't know where it went. <Laugh>. It is gone flying. No, I don't, I don't wanna carry that around
Steve Gibson (01:47:45):
You. So even after this, you still feel this way?
Leo Laporte (01:47:50):
Yeah, because Apple's already said there, I'm, you're handing this information over to law enforcement. You're carry a
Steve Gibson (01:47:55):
Phone, you're carrying a phone
Leo Laporte (01:47:57):
Around. Yeah, I know, but that's a phone. This is attached. This is, I carry this on my person. If I'm wanna murder somebody, I gotta make sure the sure the phone is
Steve Gibson (01:48:04):
Not your
Leo Laporte (01:48:05):
Person. Well, I won't carry the phone when I go murder the person, but it's on my keys. You're gonna carry,
Steve Gibson (01:48:09):
You're gonna bring an air tag with you.
Leo Laporte (01:48:10):
Cause it's on my keys. I'm taking it off right now. <Laugh>. It can be in my bag cuz I, but I, you know that basically, yeah, I guess you're right. The phone is doing the same thing and I have the phone with them all the
Steve Gibson (01:48:22):
Time. And your car, you got technology out the wazoo. Leo, your, your headphones probably are tracking you.
Leo Laporte (01:48:28):
<Laugh>. <laugh>. I'm mad. Well, they didn't tell us though. That's the other thing. I mean,
Steve Gibson (01:48:33):
And you've registered your DNA n with
Leo Laporte (01:48:36):
I knew that my, I knew our,
Steve Gibson (01:48:38):
Your, your biology is smeared all over the
Leo Laporte (01:48:40):
Map. I knew that my phone was being tracked. Right. I knew that. Okay. They didn't tell me that they have all, I had no idea that that ear tag Did
Steve Gibson (01:48:50):
You need the fine print? I'll bet you the fine print print. You I'll bet it is. But
Leo Laporte (01:48:54):
I think you're right. Most people who carry air tags don't know that that is broadcasting their exact location to all iPhones in the vicinity. And then we always
Steve Gibson (01:49:05):
Broadcasting Wait, wait, broadcasting the tags location. Yeah.
Leo Laporte (01:49:08):
And we were told that that was gonna be private. Right? But the fact that Apple is now is apparently saving that information about your location and then offering it to law enforcement upon a request that's, I think that's a violation of what they told us.
Steve Gibson (01:49:26):
Okay. So it's not, it's not the air tags location that's, that's encrypted. They don't get that. It's the, it's the air tags ownership, that's all. No, I
Leo Laporte (01:49:33):
Don't care about that.
Steve Gibson (01:49:35):
Well, that's all they have.
Leo Laporte (01:49:36):
Well, what good is that to law enforcement
Steve Gibson (01:49:39):
To know who, who paired the air tag? That's very u u useful.
Leo Laporte (01:49:43):
Oh, I guess if you're using it to stalk somebody, right? But they can So you're not saying, okay, my, now I think my air tag actually is still Okay. You're not saying good because
Steve Gibson (01:49:52):
It's, it's <laugh>.
Leo Laporte (01:49:54):
You're not
Steve Gibson (01:49:54):
Saying that you just demonstrated how robust the all suck
Leo Laporte (01:49:57):
Are. <Laugh>, I tried to kill him and I couldn't. Wow. You're not, so you're not saying that the air tag is sharing my location? No, not cause they were very clear about that, that it didn't do
Steve Gibson (01:50:08):
That. It is absolutely not. Okay. It is deeply encrypted and only the para on it is encrypted so that only the device which paired the air tag is able to determine its location.
Leo Laporte (01:50:20):
Okay. That's what they were, that's what I thought. Because they were clear
Steve Gibson (01:50:23):
About only, yes. Yeah. Only the owner of the air tag is what Apple is able to reveal.
Leo Laporte (01:50:28):
So when they handed this over to law enforcement, they merely said, oh, that air tag that somebody found, you know, stuck in their tailpipe or whatever, that's owned by Leo. That kind of thing. Yes. Yeah. Well that's fine. I don't have a problem with that. Oh
Steve Gibson (01:50:41):
Good. That is all just a misunderstanding.
Leo Laporte (01:50:42):
It's just a misunderstanding. I'm sorry to air tag. I didn't mean to hit you with a hammer. <Laugh>.
Steve Gibson (01:50:47):
Oh, I'll tell you. If if that thing had any sort of a, of a GForce sensor, you know the, the Apple security people are gonna be knocking at your door. I'm just saying, what are you doing to our air tag?
Leo Laporte (01:50:59):
I'm just seeing if find my still nose where my air tag is <laugh>. Oh, uhoh. It hasn't seen in four minutes. That's a bad sign. Yeah,
Steve Gibson (01:51:08):
I think that's when the, the pounding
Leo Laporte (01:51:09):
Began. I think I may a might have killed it.
Steve Gibson (01:51:11):
Yeah, that's, I I think, you know, probably, probably, it, it could, it, it might deliberately take that as a hint and just stop, like turn itself off. Take the
Leo Laporte (01:51:21):
Hint. Yeah. Cuz
Steve Gibson (01:51:22):
It, that, that, that might be one, one of the instructions. Well, you can press the button for 10 minutes or you can just ask Leo to smash it for you with a hammer. And that will disable as tracking function. There
Leo Laporte (01:51:34):
You have it. Ladies and gentlemen. I misunderstood. I feel bad. Now you can have your hammer back. Burke, I went searching all over this. This is a good hammer. I might add some significant leverage
Steve Gibson (01:51:46):
On this. It is air tag approved <laugh>.
Leo Laporte (01:51:48):
I think I killed the air tag.
Steve Gibson (01:51:50):
It's air tag certified. I hope you did. It hasn't
Leo Laporte (01:51:52):
Heard from it in five minutes. Yeah, I think I killed it. Well, sorry, I didn't want
Steve Gibson (01:51:57):
It anywhere. In, in, in, if, if it starts beeping after 16 hours, you'll know that some part of it is still alive.
Leo Laporte (01:52:03):
Now that's Apple. Presumably doesn't mean tile or Chipo or any of the other Bluetooth trackers are as private, but you Apple had always said we're not, the location's not being shared anywhere.
Steve Gibson (01:52:15):
That's a very good point. And I actually meant to put that in the notes so I wouldn't forget to mention it. That's why I'm using air tags. Not, not, not, not weasel tags. Right. I do not want to, you know, you do not wanna use a weasel tag on, on your stuff because you know, weasel will know where you are
Leo Laporte (01:52:33):
And, and all that law enforcement gets is my email, my phone number. That's, yes.
Steve Gibson (01:52:37):
That's all they have is the pairing registry
Leo Laporte (01:52:40):
Data. Yeah, yeah. Sorry. Here Dick. Yay. Haven't heard from it in six minutes. I'm thinking it's dead. <Laugh>. Oh, it's not looking good. Leo <laugh>. It didn't smash it good, but apparently the insides were a little mud. Oh, I think it's, yeah, it's done. <Laugh>. You did it again. You scared the pants off of me. And this case, not necessarily n needed. I put my pants back on and Steve, the world has Steve lost one air tag. <Laugh> we're down one air tag, but it has, it has 55 million other ones, few others visibly beeping away. I mean, honestly, that really is the thing to underscore is that you're, everything you have is beaconing as you point out. Yes. There is no privacy. Yeah. This whole, it's all an illusion. Yeah. And and furthermore, by the way, I don't know what's in front of you.
(01:53:26):
Can you fix that? Somebody, anybody? Steve is now peering at us through a <laugh> through his address card. Hello Engineering. I sent the whole engineering team out to find your hammer and now they're gone. Okay. Oh, fixed. And you did mention 23 and me, I just recently swabbed my cheek and sent it off to a company called Nebula. Does my whole gene sequencing, not just sample Nice. Does a hundred percent of the, of the Leo's genome. So anybody's looking for that. You'll find that online. <Laugh>. Now we know where ambulance.org. You got the whole thing. Steve Gibson is@grc.com. That's where you find him. You'll also find copies of this show. He's got two unique versions. Normally we'd have a 64 Kilobit audio version. Steve's got that, but he also has a 16 Kilobit audio version for people who want to sh you know, shrink it down.
(01:54:25):
What is that one? Fifth is one, something like that. One fourth is big. He also has, that's my air tag there on the floor. Could you, you're not touching that <laugh> pounding on it. Let's do editorial online today. Okay. So I have on that laptop we also have he also has very nice human written transcripts that Elaine Fur does such a good job with. And there's one more thing he's got, which is important. He's got the show notes. Now we link to it in our show page at twit tv slash sn. So you can click there. While you're at Steve site, pick up a copy of spin, right. Version 6.0, the world's finest mass Storage, maintenance and recovery utility. As you heard, he's working hard on 6.1. When that comes out, you'll get that for free.
(01:55:12):
But you gotta buy 6.0 now grc.com. You can leave Steve dms at the Twitter. He's at SG grc. Let me put that on the screen at SG grc. You can also get a copy of the show at our website, as I mentioned on YouTube or subscribe in your favorite podcast player. That way you'll get it automatically as, as soon as we finish it up on a Tuesday afternoon. We do the show Tuesday's, you know, in theory one 30 Pacific, four 30 Eastern 2030 UTC is sometimes a little late thanks to Mac Break weekly. But we'll get there. You can watch the live stream or listen at live. Do twi.tv if you're watching live chat, live at irc, do twi.tv or in the club twit Discord, they get special access. In fact, maybe I'll auction off my damaged air tag. <Laugh>.
(01:56:04):
Anybody? <Laugh>? It's got my name Leo on it. <Laugh>, but nevermind. Interestingly, no, no visible serial number. Not that I could see. And I even took with the camera and then zoomed in on it, a picture of it. Maybe it's inside the battery compartment. Which, but it's supposed to be. But you know, those rules came later, right? That was, yes. Well that is the up. Yes. This is the new speck. So maybe that's something that never would've, I meant to ask you this spec, is it in in effect now or is it about to be adopted? It's No, no. It is a wor this is, believe me, this needs some serious grammar fixing and, and typo repair. So this is a proposed spec. Yes. But it does demonstrate Apple and Google are gonna work together. Yeah. And all the other trackers have also agreed to, to endorse, and they've already endorsed the same specification. Good. We thought Google would announce it because of this. Would announce a tracker last week at Google io. They did not. So there you go. They were busy. Enou announcing ai, ai. They were busy with ai. Yeah. thank you everybody for being here. Great to see you <laugh>. Do not track me with my air tag, but do track steve@grc.com. We'll see you next week. Steve. Righto.
Ant Pruitt (01:57:21):
Hey, what's going on everybody? I am Ant Pruitt and I am the host of Hands-On Photography here on twit tv. I know you got yourself a fancy smartphone. You got yourself a fancy camera, but your pictures are still lacking. Can't quite figure out what the heck shutter speed means. Watch my show. I got you covered. Wanna know more about just the I I S O and exposure Triangle in general. Yeah. I got you covered. Or if you got all of that down, you want to get into lighting, you know, making things look better by changing the lights around you. I got you covered on that too. So check us out each and every Thursday here in the network. Go to twit tv slash hop and subscribe today.