Security Now 1060 transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
Leo Laporte [00:00:00]:
It's time for Security now. Steve Gibson is here. We're going to take a look at code signing crazy. We're going to find out what Whatabad, Idaho has going for it. Steve's going to talk about these three day code signing certificates and I'm going to give you a little demo of Claude code. I've been using it to write applications. All of that coming up next on Security Now.
Steve Gibson [00:00:26]:
Podcasts you love from people you trust.
Leo Laporte [00:00:30]:
This is tw. This is Security now with Steve Gibson. Episode 1060 recorded Tuesday, January 13, 2026. Three day certificates. It's time for Security now, the show where we cover the latest in security news. We attempt to protect you and your loved ones from bad guys in the outside world. We even talk a little bit about TV shows, books and vitamins with this guy. It's whatever Steve's into, frankly.
Leo Laporte [00:01:05]:
Mr. Steve Gibson, hello from GRC.com great.
Steve Gibson [00:01:08]:
To be with you again for. Well, I'm not superstitious so the fact that this is the 13th is just fine with me. It's not a Friday Tuesday.
Leo Laporte [00:01:17]:
That would be worse. Yeah, that's not a bad. I, I did have bad luck yesterday. Did you hear me talking about this on Mac Break Weekly? I got fished yesterday.
Steve Gibson [00:01:25]:
No, and it's funny because I forgot to mention it. It's not in the show notes but I saw if I got a phishing text which said that. What was it? The Amazon. It was supposedly from Amazon saying that the quality of something that I'd ordered did not meet their standards and so they were giving me a refund. Click here. And it was a plus nine one something something, you know, phone number. So I was like what? It's not. But I mean again I was like, I, they kind of had me almost.
Leo Laporte [00:02:03]:
Well, I got had and the, and, and, and I got some insight from it. So it was, wasn't a complete waste of three credit cards. I got a text from T Mobile saying your points are about to expire. If you'd like to use them, click this link. What? I really didn't pay attention because for two reasons. One, I'm a T Mobile customer and I get a lot of promotional texts from them. And this is. Companies got to knock this off because they're setting their users up.
Leo Laporte [00:02:32]:
Oh yeah, I, this is, I see this all the time.
Steve Gibson [00:02:35]:
Oh, you mean the legitimate companies need to stop this.
Leo Laporte [00:02:39]:
T Mobile should not be texting me with promotional stuff legitimately because it sets me up for phishing. That looks exactly the same. Now if I notice the link Was to L U O S a CC T mobile dot L U O S a C C I probably would have been smart enough not to click on it. I clicked on it, it said, hey, look, you got, boy, you got a lot of points. You could get an iPad, you could get some headphones. What would you like? I said, well, I don't really need any of this, but these headphones I could do give as a, as a gift. Click the link, all look very legitimate. It said, well, okay, we need your credit card.
Leo Laporte [00:03:16]:
It's free, but there's $0.99 shipping charge. So we need your credit card for that. That should have been. Then I clicked the link and it took a long time. That was the real giveaway. So I'm waiting, put in my credit card information and said, okay, they're going to send you a text. Got the text, Took a long time because there's a man in the middle, right, waiting for that text so that they can get the credit card number in the text and authenticate it. And what they did, which is really interesting, the text said to add this credit card to your Apple wallet, enter the number.
Leo Laporte [00:03:48]:
And I should, I mean, there was so many red flags again.
Steve Gibson [00:03:54]:
I mean, I'm sure everybody listening understands that, you know, our guard is down briefly. Maybe you're distracted.
Leo Laporte [00:04:03]:
It was, it was early morning. I wasn't paying attention and there was urgency. Right. These are going to expire.
Steve Gibson [00:04:08]:
Yep.
Leo Laporte [00:04:09]:
And it was a nice, you know, nice set of Sony headphones. I thought, well, that's pretty good. So I entered the first credit card. I said, no, this one didn't work. Oh, and the second credit card, no, this didn't work.
Steve Gibson [00:04:20]:
And they'll just suck them out until.
Leo Laporte [00:04:21]:
You find three credit cards. Before I went, wait a minute, hold on there, buddy. Fortunately, the first credit card was an Apple credit card, which Apple. It's great. You go in and you say, make that number no good, give me a new one. And that's it, it's done. The other two, I had to say the bank, I need a new credit card. I had to say to American Express, I need a new credit card.
Leo Laporte [00:04:47]:
There'd be a little pain in between reconnecting stuff, which I deserve fully. And in fact, shortly after, you know, as soon as I realized.
Steve Gibson [00:04:57]:
But you're indemnified from any charges.
Leo Laporte [00:04:59]:
Well, yeah. And as soon as I realized it, I immediately stopped all those credit cards so I was not going to get bit. They don't. They're quick. So that was the interesting thing I thought was smart of them to put it into a wallet. So they put it into a Apple wallet because that's anonymous. You can then use it anonymously at a store and the store doesn't know who you are. And Lisa called down to me about an hour later saying, did you just charge some 500 bucks worth of stuff at Lowe's? I said, no.
Leo Laporte [00:05:26]:
She said, well, America's plus blocked it. I said, well, good. And so I haven't seen any others because they're all blocked. Yeah, they. Less than an hour for them to get the credit card numbers, authenticate it, add it to a phony Apple wallet, which they own.
Steve Gibson [00:05:42]:
And Leo, just imagine how many people are being caught. I mean, you're as aware, you're as aware as could be, but still. And, and, and again, even I like, I looked at that text and I thought, huh, that's interesting. You know, and, but I mean it, it. Whereas normally nothing would have happened. And, and I just, I, but then I look at the phone numbers plus 9:1. I thought, I don't know where that is, but it's not Amazon.
Leo Laporte [00:06:12]:
So I feel so dumb.
Steve Gibson [00:06:15]:
Well, I had, I've told the story before. I had a, my main credit card I could not buy, I could not purchase gas. It was so frustrating because, and it would stop, it would kill the card it, if it approached a gas tank, a, a gas pump. Because it turns out that's what they.
Leo Laporte [00:06:34]:
Use to validate it.
Steve Gibson [00:06:36]:
Yeah, exactly. When, when they get hold of a card. Yep.
Leo Laporte [00:06:41]:
Anyway, I, I, I, I, you know, I'm tempted to never tell anybody that this happened, but I think on this show especially, I think it's important to say this because we're all vulnerable.
Steve Gibson [00:06:51]:
These are not hypothetical issues that we face. I mean, and, and this actually will be what you and I will. At our presentation at Threat Locker at the beginning of March is I titled our talk the call is coming from inside the house. True, because that is the threat now. And it is the messiest, least easy to deal with. Most pushback from your own employees and staff are all the things you have to keep them from doing in order to protect themselves, protect your organization from, you know, inside. So anyway, we have a great podcast today. Maybe it is the 13th.
Steve Gibson [00:07:43]:
This didn't happen this morning, did it?
Leo Laporte [00:07:45]:
No, it was yesterday. Fortunately it was on a day off, so I had time to fix everything.
Steve Gibson [00:07:49]:
So we've got security now. Episode number 1061, which I titled Three Day Certificates after which was inspired by a blog post that my continuing poking around in the code signing world led me to that I'm going to share. So we're going to take a look at Microsoft's Azure cloud code signing a topic we opened last week. Boy, turns out Leo bunch of our listeners are in enterprises where they need to be signing code and so last week's topic had extremely high resonance and relevance for them. We're going to talk about that some more. Also California's implementation of drop to provide global data broker opt out is interesting. I've got some details about that actually. I did it also.
Steve Gibson [00:08:45]:
I don't know, don't know if you have. I did also where's the town? What a bod. Idaho. We're going to look into that also I discovered What a bod. IOS's built in map app worked itself out of a job for me. I'm going to explain the backstory there. We've got a. I found a 30 minute tutorial for non coders about how to get into how to get started in AI coding.
Steve Gibson [00:09:18]:
Like how to ask the questions. Right. Which I want to share with our listeners. Also the fact that Claude Code appears to be winning over the AI coding world. I'm going to share share two pieces of information about that and then have you tell us about your own recent experiences which I, which I have a. I got some sense for. We've got a bunch of listener musings on code signing, a little bit of magnesium feedback and then we're going to take a look at what use could there possibly be to three day certificates. I mean it's like it barely gets off the ground and it's landed.
Steve Gibson [00:09:54]:
So yeah. And of course we've got a great picture of the week for everybody. So I think another great podcast.
Leo Laporte [00:10:00]:
Love it. For this second of the before we get to the picture of the week because I have it already all queued up here, maybe I can tell you about our sponsor for this segment on Security now and it's kind of, kind of appropriate. This episode of Security now is brought to you by Material, the cloud workspace security platform built for lean security teams and man I wish I didn't. This, this, this text came over my Apple messages, not my Google mail. If it had I wouldn't have had to worry. Managing security in the cloud workspace as you know is tricky. We are a Google workspace company. A lot of you use workspace, maybe use Microsoft 365 but it's hard to do security in those clouds.
Leo Laporte [00:10:49]:
Phishing is not the only way in. By the way, what I got but today's email Security basically stops at the perimeter. New attacks are hard to detect with siloed email data and identity security tools. But that's why you need material. Material protects the email, protects the files, protects all the accounts that live in your Google workspace or Microsoft 365. Honestly, effective email security today needs to do more than just block phishing and other inbound attacks. It needs to provide visibility and defense across the entire workspace. Threat surface Material ingests your settings, your contents, your logs, churns them up and provides holistic visibility single pane that looks into the threats and risks across the workspace.
Leo Laporte [00:11:38]:
It also gives you the tools when you see something to automatically remediate it. Material delivers comprehensive workplace security by correlating signals and driving automated remediations across the entire environment. You get phishing protection, you get email security. It combines advanced AI detections with threat research. So you know you've got a lot of data points. You also have user report automation so your users can say hey, something happened. You also get detection and protection of sensitive data. This is really important across inboxes and shared files.
Leo Laporte [00:12:12]:
You know in a soon you're going to be mailing your tax info out to your accountant. That's sensitive data, isn't it? There's all sorts of stuff going through the over the transom into the inbox account threat detection and response with comprehensive control over access and authentication of people and third party apps. You get all this with material. Material. It empowers organizations to rapidly mature their ability to detect and stop breaches with step up authentication for sensitive content, blast radius visualization for accounts and the ability to detect and respond to threats and risk across the cloud. Workspace Material enables organizations to scale their security without scaling their team. Material drives operational efficiency with its simple API based implementation and flexible automated and one click remediations for email file and account issues. So you don't have to spend a lot of time fixing stuff, you just go fix it.
Leo Laporte [00:13:10]:
This includes an AI agent that automates user report triaging and response. It's such a big help. Material protects the entire workspace for just the cost of email security with a simple and transparent pricing model. But it's so much more than just email security. Secure your inbox and your entire cloud workspace without adding more toil to your day or costs to your balance sheet. See Material Security to learn more or book a demo. That's material Security. What a great solution.
Leo Laporte [00:13:43]:
You need to check this out. Material.security. we thank them so much for our their support of security. Now and Mr. G. Okay, let me, let me tee up the picture of the week.
Steve Gibson [00:13:56]:
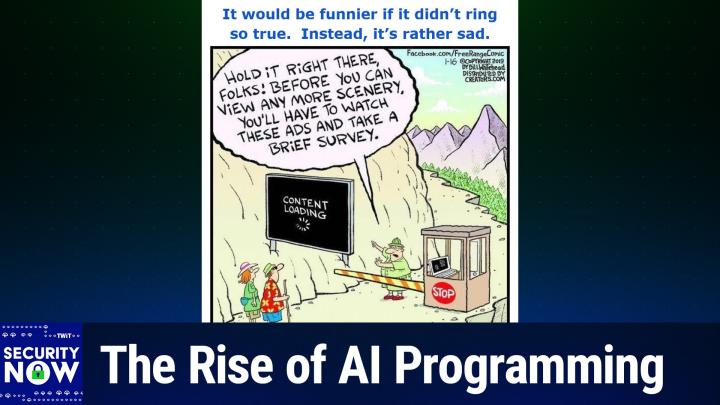
I gave the. This picture of the week the caption. It would be funnier if it didn't ring so true.
Leo Laporte [00:14:02]:
Oh dear.
Steve Gibson [00:14:03]:
Instead it's rather sad.
Leo Laporte [00:14:05]:
Yes. Okay. This is a free range comic. I'm looking at it right now. Let me show it full screen so you can read the entire caption.
Steve Gibson [00:14:19]:
So, so we, so we have a, a neat looking couple of hikers. She's got her little fanny pack and he's got a walking stick. And they're on a path clearly in some park. And they've come to a arranger who's stepped out of his booth. The, the arm is down on the gate preventing them from moving through. And he's holding up his hand saying, hold on, stop. Pointing to a kind of a billboard sized screen which is off to the side of the path. And on the screen we say we, we see it says content loading with the little spinning thing.
Steve Gibson [00:15:02]:
Right? And he is seen to be saying, hold it right there, folks. Before you can view any more scenery, you'll have to watch these ads and take a brief survey. So as I said, yes, it would be funnier if it's true. Didn't ring so true. The. You know, even nature is being commercialized and you're needing to be made into the product yourself if you're wanting to do any communing.
Leo Laporte [00:15:33]:
No. No communing allowed.
Steve Gibson [00:15:35]:
No communing here. Okay. So based upon the feedback I've received, as I said over the past week, we appear to have hit it out of the park with our first podcast last week of 2026. I received a bunch of feedback about each of the major topics we covered. And no one complained about my spending time sharing what I learned firsthand about magnesium. In fact, many of our listeners want more. So from time to time, you know, again, this is not going to be the nutrition podcast, but again, we're all together, all what, 100 or 100,000 plus of US aging as a group. And we've been at this for 21 years.
Steve Gibson [00:16:22]:
So we're getting there. I was gratified to find a great deal of unity over what's going on in our industry regarding the shortening of certificate lifetimes coupled with the concomitant rising costs of code signing since last week's three hour podcast, which, you know, couldn't have handled any more content. I stumbled upon a terrific blog post that was so on point that I want to begin with it this week. Much as I began with this same topic last week by looking at, in this case a a different aspect of code signing. The guy's name is Rick Straw. His post was this past Summer on July 20th and he made a he he he tweeted a few days before that. I'll share that in a second. But He he posted July 20, 2025 from Hood River, Oregon.
Steve Gibson [00:17:24]:
He gave his posting fighting through setting up Microsoft Trusted Signing. And while I share what Rick wrote, please keep in mind that no matter how much this guy may sound like me and may be echoing my recently expressed sentiments, this is really his own original writing. So you know, he's further evidence, I guess, that, you know, I and our many listeners who have expressed an opinion are not alone and are not off base in raising an extremely skeptical eyebrow at the recent changes that have been occurring and which will be adversely affecting everyone who wishes to author code going forward. So here's what Rick wrote. He he said so it's that time of year, actually the time of several years to renew my code signing certificate. I always dread this because it's a manual process and invariably if you're not intimately familiar with the complexities of public key cryptography, the terminology is enough to drive you batty. It's gotten easier since I made some decent notes the last few times I went through this, but all that's out the window this time around because the code signing rules have changed drastically. It actually happened a few years ago, but I was lucky and got my local still exportable certificate just before the rules changed.
Steve Gibson [00:19:07]:
So I was able to freeload for at least nearly three years on the old certificate plan. The new rules don't allow for locally stored exportable certificates. Instead certificates have to be served from one of a few certified online authorities or the certs must be stored in a FIPS142 Level 2/compliant hardware security module. The keys cannot be exportable so they effectively cannot be copied and stored or used elsewhere. So you got the option of a server provided keys or hardware keys. The idea behind this is to stop keys getting jacked and being used by the non originating organization so the new keys are one time generated and non exportable so that they are much more restricted. Online services issue certificates that are good for only a few days when you can use them to sign with and then automatically roll over to a new certificate. What all this means the complexity of getting a certificate has gotten exponentially worse and along with that prices have gone up significantly.
Steve Gibson [00:20:31]:
Base non EV certs run in the 350 to 500 range with fully verified EV certificates starting around $500 per year. What used to cost me $180 for three years the same provider now wants nearly $1,000 for, he says. Yikes. It all seems like a huge grift. Okay now in his posting Rick, as I mentioned, then posts he quotes a separate tweet which he had posted two days prior to this blog posting. On July 18, Rick posted to X He said as it is the whole code signing thing has turned into another scam of X and ification of a captured audience. If you're publishing software or even packages on nouget now you pretty much have to have a code signing certificate. Certificates that used to be 100 to 150 or less for multi year certs per year a few years ago now cost 300 to 400.
Steve Gibson [00:21:46]:
For basic certs the EV certs start at 500 and go up from there. The validation rules for businesses have not changed and you would think most of the expense is all in that. But this isn't about security, it's about gatekeeping and just one more hurdle for a small business to have to jump over. So that was his his tweet then he continues turning his attention to Microsoft's Azure Cloud Signing solution. He writes, Microsoft is in the game too. Microsoft, who requires these code signing rules in the first place for Windows Smart Screen validation and also for other things like NuGet packages, is also providing an Azure service called Trusted Signing to provide code signing services. So they're on both sides of that transaction, create the problem, provide the solution. To their credit, their pricing is much better than what most traditional SSL cert providers are now charging Azure Trusted Code Signing is still in preview, but then again it's been in preview for well over two years.
Steve Gibson [00:23:07]:
But it looks like what you see and what and what can sign up for now is in the final stages before going to a proper release as a service. One reason to look at Microsoft solution despite the potential pain and suffering, he writes, is that the pricing is quite good as of the time of this post. So and then he has a little chart. The base price monthly is $9.99. The premium as opposed to basic per month is 99.99. The quota as in maximum number of signatures per month for the basic 9.99 cents is 5,000 signatures per month. Then an over quota is half a cent per signature. So $0.005, you know, half a penny per signature.
Steve Gibson [00:24:05]:
Once you've gone over 5,000 per month for the premium plan, which Is that, that the hundred? Basically $100 99.99. You get 100,000 signatures per month and then the same half a penny for each of the signatures over that. So he said these are non EV base certificates. Oh, so that means the, the basic, the, the difference between basic and premium is not signature quality. Which makes sense, right? Because we know you don't get any benefit anymore for EV from Microsoft, so why charge more for it? But it's, it's quantity of signatures. So for 5,000 signatures, for $10 a month, basically for 10 times that fee, a hundred dollars a month, you get 20 times the maximum number of signatures. Before you start having to pay per signature, you get a hundred thousand signatures. So he says these are non EV base certificates that only do basic vetting.
Steve Gibson [00:25:09]:
For fully vetted EV certificates you'll need to look elsewhere. This pricing, which ends up at a hundred and about $120 per year for the single cert, is cheap compared to most of the SSL vendors, most of which start at around $300 for certificates with mailed hardware keys, meaning they, you know, postal mail, they, they send the key to you, then you plug it in and you're, you're good to go, he says. So you got to give Microsoft credit here for keeping costs down and providing reasonable pricing. The certificates issued by Microsoft are very short lived with expirations that last only three days to aggressively thwart invalid signing attacks in case a certificate, this certificate is compromised. Thus the title of today's podcast, three day Certificates. We're going to look at the mechanisms behind that, he says, doing a bit of research. Out of all the bad options out there, Microsoft's trusted signing seems like the least bad solution that's also cheaper than traditional certs from various SSL vendors. The good news is that it works and pricing is reasonable.
Steve Gibson [00:26:31]:
The bad news, I wasted nearly an entire day trying to get it to work. Hopefully this post will help you. Reading will help you Reading this not to wait will help. So he means those of you reading this not to waste quite so much time. And he then his next section he titled Navigating the Azure Jungle. I'm not going to go through it all, but I'm going to touch on the beginning of this. He said if you end up going the Azure trusted signing route, plan on having to wade through the Azure dependency jungle of setting up several resources and trying to understand what all the mumbo jumbo Azure jargon amounts to. If you're doing Azure all day, then much of this infrastructure dance will be familiar to you.
Steve Gibson [00:27:26]:
But as someone me, he wrote, who only occasionally jumps in for some very specific services like Trusted Signing, it's incredibly painful to deal with Azure security and the resource dependencies and the endless nesting of services with badly defined and overlapping naming boundaries. For trusted signing, finding documentation via search engines was hit or miss. The docs for this are buried behind deeply nested links, perhaps because it's still in or just out of preview, he says. Parens even that's hard to tell since some prompts show preview. None of the headlines do, he said. And also because previous releases of this technology used a completely different publishing pipeline through the Azure key vault, he says there's official documentation, although it took me a bit to discover it. And he put a link in the blog posting and I copied that link into the show notes, so that's there, he says. This has everything you need, but the instructions require some interpretation.
Steve Gibson [00:28:42]:
The tools are terrible and the docs don't make working with them a lot easier by making you figure out where to find files and dependencies and how to install tools. Don't believe you're lying AIs, he wrote. In this day and age of AI assistants and chatbots, you would think that that things like Azure configuration instructions for setting up an Azure task would be readily available. Heck, there's even an Azure specific copilot model that you can use from the VS Code Copilot integration. But that actually yielded surprisingly bad results and did not work well with Trusted Signing either for setup or for the signing part. Part of this might be because Trusted Signing is still in preview or because the documentation for this is almost non discoverable and because things have changed so much with the tooling. Long story short, after a very pissed off day of going down many wrong paths, I managed to get Trusted Signing to work for my projects and I'll try my best to provide the details and how I have this set up, hopefully sparing a few of you all the pain I ran into. Okay, and that at this point I'm going to stop almost, he said.
Steve Gibson [00:30:09]:
So so this is about the first 10% of Rick's entire blog posting. Throughout the next 90% of his posting, he painstakingly and charitably details that the entire process of setting up Microsoft Azure Cloud Code signing. I've got a link to his detailed instructional posting in the show notes and I also gave it a GRC shortcut just to make it easy for everybody to find GRC SC Code sign all one word GRC SC code sign will bounce you over to this blog posting of Rick's where you'll see the first 10% is what I just shared and the other 90 are like how he solved the problem. He finally wraps up this terrific setup walkthrough with a summary that's also worth sharing here. As you'll hear. Some of this assumes that by now, by the time you've gotten to here, you've managed to slog through everything that he wrote which preceded it. So he sums it up by saying the process to set up trusted signing was way harder than it should have been. In fact, the entire process took me the better part of an entire workday.
Steve Gibson [00:31:26]:
The server process is complicated primarily because the nomenclature is so crazy confusing and the dependency management on Azure is such a pain in the ass. The missing rights from the account to create an identity is particularly maddening, and how you fix it is even more so. But it wouldn't be Azure if you weren't cursing the thing every step of the way. The signing process is also a pain in the ass with three different tool chains required. The fact that an Azure Trusted Signing command line interface add in exists but doesn't actually support signing is just ridiculous. With all the resources that are thrown in Azure, it seems petty to not support the one feature that everybody is going to need without having to jump through hoops of managing several tool installation instructions. But somewhat grudgingly, I have to say that at the end of the day, the process works, warts and all. Microsoft's comparatively lower pricing for the service compared to others maybe makes it worth it.
Steve Gibson [00:32:44]:
And frankly, the fact that I have my cert running as a service that hopefully doesn't ever need to be updated unless I quit the service is enticing. Yeah, it costs more than it did last time around. I'm now paying almost as much every year as I used to pay for three years. But given the circumstances and and the insidification that now surrounds the entire code signing process, this is the best we can do for now. I'm hoping writing this up is helpful to some, and that these instructions won't be obsolete in a few short months because Microsoft changed their designs again, as is so often the case. Despite that I finally got it to form, one would hope that they fix its performance. Maybe he meant to perform one. Oh yeah, despite that I finally got it to perform one would hope they fix its performance.
Steve Gibson [00:33:44]:
He and he said five to eight seconds per file to sign with no parallelism for multiple submissions is bad.
Leo Laporte [00:33:57]:
That's pain.
Steve Gibson [00:33:57]:
And could we yes, like you just sit here waiting for eight seconds for this thing to sign a file. And apparently lots of companies are signing. They have like heavy signing burdens, he said, with no parallelism for multiple submissions. And could we please have self contained tooling for signing, for heaven's sake, he wrote. Provide one tool that can handle the signing process in one pass without having to install 50 other things. Or better yet, have it built in to the Azure command line interface with the trusted signing add in that's already there. One could hope some of this is due to the relative newness of Azure Trusted signing, but we shall see. So Rick's blog system supports reader comments, and that posting back in July generated a bunch of feedback.
Steve Gibson [00:34:56]:
I'll share just the first one of many, which followed up and posted I just like to say that I've been reading your blog for probably 12 years now and I also went through this. I've learned to parse Microsoft documentation as if I were a machine and it's nice to know that someone else is turning in to the cranky old man of developers. I feel like something has been lost. From the time we were excited, it all worked. Meaning, you know, computing. This guy wrote the days where you could slow down the genie effect on Mac with the shift key just to stare at it when when connecting to a system seemed like magic. Now we deal with artificial gatekeeping, auditing, roadblocks, deprecations for seemingly no productive reason. What happened to the joy of being excited that it all worked? He finished Keep on trucking, but also get off my lawn.
Steve Gibson [00:36:06]:
So yeah, it's not just me and many of our listeners who have sensed that what's happening here is not for the benefit of the world, but for the enrichment of a very few large gatekeeping bureaucracies.
Leo Laporte [00:36:21]:
Yeah.
Steve Gibson [00:36:22]:
Now I should say that after last week's podcast I did some additional scouting around and I found that the fast SSL brand offers a standard like Microsoft non EV code signing certificate if you buy three years for 129 per year. So and now we're talking hardware. So since it's still possible before March 1st to obtain a 3 year plus 3 month remember, 39 month certificate, that's what I plan to do. Fast SSL certificates are available from the site from from the site cheapsslsecurity.com C H E A P SSL. You know, no hyphens or anything. Cheap SSL security.com As I said, that's what I'm going to do. There's no longer any apparent benefit from obtaining and wielding extended validation Certific certification. Microsoft doesn't even offer it because they, they, they don't care.
Steve Gibson [00:37:34]:
And since obtaining it means paying a lot more, that is EV paying a lot more. After first being subjected to basically a full body cavity search in order to qualify for ev, my next code signing certificate will be the bottom of the barrel fast SSL brand. You know that, that one will take me from when I get it, which will be late next month, late February of 2026 through to late May of 2029. And at that point, and that means, you know, installed in, in my little hardware USB dongle so I can sign as much as I want to. Actually my server will be signing as. Everybody who buys a GRC product has code signing on the fly of their own executable. That's stuff I all got worked out when I talked about it a couple years ago. So three years from now, May 2029, we don't know what shape the world's going to be in.
Steve Gibson [00:38:35]:
We don't know what else will have changed. They may have further shortened certificate lifetimes. There may be more pressure in the cloud. Maybe some competition will have stepped up to offer a better deal. We don't know. So anyway, I've got a link to, for anyone who cares, the FAST SSL code signing certificate. It's $387 for the three years. So 129 per year you get to, you get to install it into, you know, an, an, an existing dongle you probably already have if, if you've already been doing code signing for the last two and a half years because it was all already dongleized.
Steve Gibson [00:39:15]:
And that's what I know. Leo.
Leo Laporte [00:39:20]:
Unbelievable. I actually, it's funny because we're going to talk about it in a little bit later, but as you know, over the weekend I wrote some of my own code and I just moved it over onto this machine so I can show you. And the Apple operating system said, you can't open that. It's not signed.
Steve Gibson [00:39:41]:
Yeah, it is, it is. I mean it really, it's astonishing essentially. I mean, you can understand what they're trying to do, right?
Leo Laporte [00:39:55]:
Oh yeah.
Steve Gibson [00:39:57]:
Except that bad guys are signing their bad code because they're able to pretend. I mean, we're, we're hiring North Koreans. We obviously aren't good at figuring out who people are.
Leo Laporte [00:40:12]:
It's an imperfect system, so why enforce it, is what you're saying.
Steve Gibson [00:40:15]:
Yes, and, and that's, you know, that's what I'm, I'm beginning and I guess this is the old man, get off my lawn thing, I'm, I'm seeing more and more examples of where trying to, to fix the last 5% is creating 95% overhead. You know, again, it's like we need to protect some endangered, some endangered rodent somewhere in Sacramento. So we can't run light rail through the, you know, through that area without all kinds of environmental exceptions and permits and things. And as a consequence, we don't have, you know, any good transportation in California. It's, again, I get the, I, I get the intent, but sometimes you end up. It's like case of being your own worst enemy. And, and in this effort to, to, to squeeze, to, to try to use technology to go all the way to a hundred percent, no malware, first of all, you're gonna fail. You know, even goodware has bugs.
Steve Gibson [00:41:23]:
As the point that I made. The fact that it's signed doesn't mean that it's not. That does, doesn't have remote code execution vulnerabilities. It just means, you know, who made it. Well, you pretty much know anyway.
Leo Laporte [00:41:35]:
Oh.
Steve Gibson [00:41:39]:
Okay. I need to, I need to take a. Take a breath, have some coffee. Then we will, we'll talk. We'll share some optimistic news about California.
Leo Laporte [00:41:48]:
Good. And while Steve is rehydrating and rejuvenating, let me talk about our sponsor for this segment of Security now, zscaler. This episode of Security now brought to you by Zscaler. It's the world's largest cloud security platform. You know, the potential rewards of AI are obviously too great to ignore, especially for businesses. But businesses also has to recognize there are risks also too great to ignore, right? Loss of sensitive data, attacks against enterprise managed AI. Generative AI increases opportunities for threat actors. It lets them quickly create very realistic phishing lures, as I know well.
Leo Laporte [00:42:33]:
Write malicious code, automate data extraction. I mean, there's script kiddies out there now who have the best skills of all because they are able to use AI. And then there's also this issue of legitimate users of AI in your business accidentally exfiltrating vital information, proprietary information. There were 1.3 million instances, for example, of Social Security Numbers leaked to AI applications last year. 1.3 million. ChatGPT and Microsoft Copilot, they saw nearly 3.2 million data violations. 3.2 million. It's time to rethink your organization's safe use of public and private AI.
Leo Laporte [00:43:18]:
Chad Pallet, who's the acting CISO at BioIVT, says Zscaler helped BioIVT reduce their cyber premiums by 50% and at the same time doubling their coverage and improving their controls.
Steve Gibson [00:43:33]:
Take a look.
Leo Laporte [00:43:34]:
Chad's got this to say with Zscaler.
Steve Gibson [00:43:39]:
As long as you've got Internet, you're good to go. A big part of the reason that we moved to a consolidated solution away from sd, WAN and VPN is to eliminate that lateral opportunity that people had and that opportunity for mistrust, direction or open access to the network. It also was an opportunity for us to maintain and provide our remote users with a cafe style environment.
Leo Laporte [00:44:03]:
With Zscaler Zero Trust plus AI, you can safely adopt generative AI and private AI to boost productivity across the business. Their Zero Trust architecture plus AI helps you reduce the risks of AI related data loss and protects against AI attacks to guarantee greater productivity and compliance. Learn more@zscaler.com security that's zscaler.com security thank him so much for supporting the important work, the good work Steve's doing here at Security Now. Now back to the crazy world we all live in.
Steve Gibson [00:44:41]:
Some good news and a nice acronym. The acronym is drop, which stands for Delete, Request and Opt Out Platform. Ars Technica's headline was the Nation's Strictest Privacy Law Just Took Effect to data brokers chagrin with the subhead Californians can now submit demands requiring 500 brokers I don't know where 5 where Dan got 500, I got 170, but still 170 to delete their data. So this was written by Dan Guden, Ars Technica's security guy and and technical guy. He wrote, californians are getting a new supercharged way to stop data brokers from hoarding and selling their personal information. As a recently enacted law that's among the strictest in the nation took effect at the beginning of the year, according to the California Privacy Protection Agency, which is short as Cal Privacy, more than 500 companies actively scour all sorts of sources for scraps of information about individuals, then package and store it to sell to marketers, private investigators and others. The non profit consumer watchdog said that in 2024 brokers trawl automakers, tech companies, junk food restaurants, device makers and others for financial info purchases, family situations, eating, exercising, travel, entertainment habits, and just about any other imaginable information belonging to millions of people. So the interesting takeaway for me so far and for us is to appreciate that this is not passive eavesdropping, right? I mean the these guys are proactively assembling portfolios on individuals.
Steve Gibson [00:46:52]:
I mean, the more data they get on us by person, the more valuable it is. They are turning it into a cash flow. Yes, so Dan said. Two years ago, California's Delete act took effect. It required data brokers to provide residents with a means to to obtain a copy of all data pertaining to them and to demand that such information be deleted. Unfortunately, Consumer Watchdog found that only one person percent of Californians exercised these rights in the first 12 months after the law went into effect, a chief reason? Residents were required to file a separate demand for each broker. Yeah, okay, what, 500 I or even 170 that I'm aware of. So wow.
Steve Gibson [00:47:50]:
With hundreds, he writes of companies selling data, the burden was too onerous for most residents to take on on January 1st, meaning 2026. A couple weeks ago, a new law known as Drop, delete request and opt out platform took effect. Drop allows California residents to register a single demand for their data to be deleted and no longer collected in the future. CAL Privacy then forwards it to all brokers starting in August, meaning this coming August, brokers will have 45 days after receiving the notice to report the status of each deletion request. So it's not just going out into the blue and you never hear anything back. It's got to be a proactive report of what action they took, dan said. If any of the broker's records match the information in the demand, all associated data, including inferences, must be deleted unless legal exemptions such as information provided during one to one interactions between the individual and the broker apply. To use Drop, individuals must first prove that they're a California resident, Dan wrote.
Steve Gibson [00:49:17]:
I used the Drop website and found the flow flawless and the interface intuitive. And I'll I'll just add here I did too and I'll report on that in a second, he said. After I provided proof of residency, the site prompted me to enter personal information such as any names and email addresses I use and specific information information such as VIN, you know, vehicle information, numbers and advertising IDs from phones, TVs and other devices. It required about 15 minutes to complete the form, but most of that time was spent pulling that data from disparate locations, many buried in system settings. He says it initially felt counterintuitive to provide such a wealth of personal information to ensure that that data is no longer tracked. As I thought about it more, I realized that all that data is already compromised as it sits in online databases, which are often easily hacked and of course, readily available for sale. What's more, CAL Privacy promises to use the data solely for data deletion. Under the circumstances enrolling was a no brainer.
Steve Gibson [00:50:34]:
It's unfortunate that the law is binding only in California. As the scourge of data broker information hoarding and hacks on their databases continues, it would not be surprising to see other states follow California's lead. Okay, so I thought that I ought to take this out for a spin also. Why not? As Dan wrote, and as Leo and I both discovered, it's all out there already anyway. And trusting what? One more entity who is only asking for my information for the purpose of preventing its warehousing and resale? Well, that makes sense to me. So I went over to the new drop site at Consumer Drop Privacy Cav Again Consumer Privacy Sorry, consumer drop.privacy ca.gov they appear to be behind Cloud Flare since I first encountered that increasingly familiar let's verify your human intercept page with the little spinning icon doing whatever it's doing. After a few seconds it finished and I was taken to the delete request and opt out platform paren drop site which identified itself with that web page title. One of the first things I noted was a drop status menu item.
Steve Gibson [00:52:03]:
Clicking that out of curiosity, I was taking to. I was taken to a short page that said enter your drop ID to check the status of your drop deletion request. Your ID contains 8 to 10 characters, letters and numbers. Okay, so that seems sort of cool. You receive a drop ID which you can can use to check back at any time in the future. So, you know, I'm thinking that I'll store that in bit warden safe and also alongside my credit bureau credit freeze info. You know, just as a collection of stuff I want to hold on to. Since this was serious business, I decided that I ought to actually read the terms of use fine print.
Steve Gibson [00:52:46]:
And I'm glad I did.
Leo Laporte [00:52:48]:
I just skipped over them completely.
Steve Gibson [00:52:51]:
I don't blame you.
Leo Laporte [00:52:52]:
What'd you find?
Steve Gibson [00:52:54]:
It explains that everything I provide will be forwarded to data brokers and the more I provide, the better job they'll be able to do of scrubbing me from their systems.
Leo Laporte [00:53:07]:
That's nervous in making I know you.
Steve Gibson [00:53:10]:
Know and it does make you know it. You know you. It gives you a big gulp. But anyway, so, so the relevant parts here it says by using the delete request and opt out platform drop, you agree to the following terms of use Terms provided by the California Privacy Protection Agency Cal Privacy referred to herein as we, us and our they said use of drop. By submitting a deletion request through drop, you consent to to disclosure of your personal information to data brokers for purposes of processing your deletion request pursuant to Civil Code Section Blah Blah blah unless or until you cancel your deletion request. Additionally, you acknowledge that data brokers receiving your deletion request will delete any non exempt personal information as defined in another Civil Code which pertains to you and was collected from third parties or from you in a non first party capacity. In other words, through an interaction where you did not intend or expect to interact with that data broker. Before submitting a deletion request, you'll be required to verify your California resident as defined in Section Blah Blah of the California Code of Regulations.
Steve Gibson [00:54:38]:
As that section read, blah blah. Verification is made with assistance from state contracted third party vendors, including so cure and login.gov through the California Identity Gateway. If you're unable to confirm your California residency through these verification service providers, you may request review of your residency classification pursuant to section Blah of the California Code of Regulations. You may contact CAL Privacy by visiting this webpage and there's a link in the Show Notes for anyone who doesn't want to find it in the Terms and Conditions. In addition, you will be prompted to provide personal information such as name, date of birth, and email address. Certain information is required to verify your residency. Otherwise, the type of information and how much you provide is up to you. However, you must only provide true and accurate information about yourself through drop.
Steve Gibson [00:55:40]:
Adding personal information about multiple people in the same request is prohibited and probably screws things up at the other end too. Information received will be used and disclosed to facilitate your request to delete and opt out of the sale. Sharing of your personal information maintained by data brokers registered with CAL Privacy. The more personal information you provide, the greater the likelihood of registered data brokers finding the personal information they maintain about you and deleting that information. Yikes. Okay. But you know, it makes sense if if I choose to volunteer the size of my underwear. On the one hand, everyone whose business it is to collect and resell such information will have that authoritatively directly from me.
Steve Gibson [00:56:37]:
You know the the juiciest and 100 verified information directly from the source that they could ever hope to have. But because this disclosure came through CAL Privacy, its very existence means that disclose or sell it they must not, and that in fact they must use it so that information solely for the purpose of identifying me and having done so, delete it and everything else they may have previously aggregated over time about me The Terms of Use continues Data brokers are required to process deletion requests at Last once every 45 days beginning 8-1-2026, your submission of personal information through Drop is governed by by Cal Privacy's Privacy Policy, which is incorporated into these terms by reference and so under Prohibited Uses. They say while using Drop, you agree you will not use Drop for any fraudulent, unlawful or prohibited purpose, impersonate any person or entity or misrepresent your affiliation with any person or entity, interfere with or disrupt the operation of Drop or the servers or networks used to make Drop available, including threatening the integrity or security of Drop, restrict, Disrupt, interfere or inhibit any other person from using Drop and finally reproduce, duplicate, copy, sell, resell or otherwise exploit for any commercial purposes any portion of, use of or access to Drop. Violating these Terms may, on a case by case basis, result in restriction of your ability to access and use Drop. And then they did add aiding another person with their request, which you know could be necessary. They said you are only permitted to aid another consumer with their deletion request if that person has authorized you to do so and you meet the requirements described in some section. In addition, the consumer must first have their residency verified as described in the Use of Drop section above. When aiding a consumer with their request, you or the consumer must disclose your full name, email address, and business name if applicable through Drop when prompted in submitting because you are asked is this for you or for someone else that you're doing it on their behalf? In submitting information on behalf of another person person, you certify that you have authorization to do so and that the information you provide is true and correct.
Steve Gibson [00:59:22]:
Adding personal information about a person who has not authorized you to submit a deletion request on their behalf is prohibited. And then finally anyway there's a little bit more but we we've got enough of this. Everyone has a sense for that. They do talk about third party vendors involvement and just and they're disclaiming their liability or over third party conduct which is not very comforting. But you know that's what you get anytime attorneys are asked to review and revise you know, anything like this. So the term ends with something titled Notice at Collection of Personal Information which says your data. When you use Drop, the California Privacy Protection Agency collects personal information you enter such as names, emails, phone numbers, dates of birth, zip codes, mobile advertising IDs, connected TVs, vehicle information numbers. We also collect usage time, device ID and IP address.
Steve Gibson [01:00:21]:
We use the data to provide your deletion request to registered data brokers, enhance the product, respond to questions and ensure safety. Providing information and using the service as voluntary do not provide unrequested personal information and. And finally, your rights. You may access records with your personal information collection is subject to the Information Practices act and state, private and state policy. If you have any questions or concerns about this policy, contact us. Blah, blah, blah. Okay, so I did what Dan did and it did take about 15 minutes. I chose to use login.gov since I already have an account set up there.
Steve Gibson [01:01:05]:
I don't recall why, but the email address they have.
Leo Laporte [01:01:08]:
Global Entry.
Steve Gibson [01:01:09]:
Yeah. Oh, that. That could be easy.
Leo Laporte [01:01:11]:
That's what Global Entry uses. Yeah.
Steve Gibson [01:01:13]:
Although for me, the email. The email address they have for me is the one that I was using in 2018. So it may have been set up for my Social Security stuff in advance of my turning it's.
Leo Laporte [01:01:27]:
Or Social Security. That's right. Yeah. Yeah.
Steve Gibson [01:01:30]:
So in any event, after providing my phone number to login.gov, the site used SMS to send my phone a link. Clicking that link took me to a page which requested access to my camera so that it could manage capturing the front and back of my California driver's license. It did that with a cool Arnold Schwarzenegger Terminator green grid overlay kind of thing. And for each of the two. Exactly. And for each of the two captures, it asked my permission to send it for verification, which took a few seconds each time. After that, I was returned to the drop page where I provided both Steve and Steven. And as my first names, I.
Steve Gibson [01:02:23]:
I avoided Leo, adding the Tiberius as my middle name.
Leo Laporte [01:02:28]:
Probably a good idea.
Steve Gibson [01:02:30]:
I didn't want to get. I didn't. Yeah, I didn't want to confuse anything. Then I provided.
Leo Laporte [01:02:34]:
There's a lot of verification going on here. I got a round tripping a bunch of times with this.
Steve Gibson [01:02:40]:
Yeah.
Leo Laporte [01:02:41]:
And you have to verify your email and.
Steve Gibson [01:02:43]:
Right, right. I gave him my last name, my date of birth, my Social Security number, my residence address, my. My vehicle identification number. There were places to add a mobile advertising identification number and a smart TV ID until Apple refreshes their Apple TV hardware, which I'm just holding my breath for. I'm using Roku. And while Roku does have an advertising identifier, that number is not user displayable without side loading a Roku channel for displaying such internal stuff. And that was more than I was interested in doing. And I also.
Leo Laporte [01:03:24]:
Most people wouldn't know that kind of thing at all.
Steve Gibson [01:03:27]:
Exactly. And I. I do have app tracking turned off in my iPhone, so there was nothing to share there either. Once that was all complete, I was taken to the deletion request submitted success page and there I received my promised 8K. Well, I was gonna say eight character, but it's actually two sets of four characters hyphenated, so I guess that's nine characters. That's that drop ID, which I can then use to check back on my drop status at any time in the future. Although nothing's going to happen until late August. Or actually, I guess maybe even early September.
Leo Laporte [01:04:11]:
Serious. So much easier to get a delete me account. I'll be honest with you.
Steve Gibson [01:04:15]:
Okay, it did occur to me that. That. Yes, but then delete me must be asking the same things, right? Anybody who's going to be at.
Leo Laporte [01:04:23]:
Is wanting more, you give them the better data. That's right. Yeah.
Steve Gibson [01:04:25]:
Yeah. Anyway, so one cool thing is that having done this, the drop pages menu, the main menu on the drop page added two new page links. One was for my data profile, which was that form that I filled out, which was all then viewable with a whole bunch of asterisks, you know, blanking out most of the information but letting me know like what the last four digits of things were. And the other was the data broker list pages.
Leo Laporte [01:04:57]:
Delete me is a sponsor, I should mention. Benito's saying you gotta. You gotta disclose. Okay.
Steve Gibson [01:05:04]:
So the my data profile page shows a ring chart which is, you know, like a pie chart but with the. With the center hollowed out, where we are informed that a total of 170 named individual data brokers are registered with the state of California and are thus subject to this new law, which as I said, went into effect on January 1st with an 8 monon grace period. But what's most cool is that once this happens, the ring chart has categories, you know, that'll be like a pie chart for deleted, opted out, exempted, record not found and pending. So I'm going to be very. Going to have. We have to all wait, you know, eight months. But I'll be very interested in seeing both the deleted and the record not found counts. Currently, all of this stuff is 0,/170, you know, 0 out of 170.
Steve Gibson [01:06:11]:
So what will they be in September? It's going to be interesting to see how that goes. The data broker list, that second new page actually displays the current status of. Of each of those 170 individual data brokers. At the moment, they're all currently shown as N A. And the filter option, which is a column in the table, contains the same itemizations as the ring chart. Deleted, opted out, exempted, record not found and pending. So you'll be able to select by those or Sort by those. Which again, I think will be very interesting to see.
Steve Gibson [01:06:56]:
And I'll just say, and we've sort of touched on this several times already, but looking at all of this, I was reminded of what Dan wrote. You know, he said it initially felt counterintuitive to provide such a wealth of personal information to ensure that data is no longer tracked. As I thought about it more, I realized that all that data is already comprehensive as it sits in online databases which are often easily hacked and of course readily available for sale. So again, yes, it's somewhat creepy to be volunteering all that information, you know, providing it to the, you know, like, like indirectly to the trackers who have been doing all of this. Whose business is it, you know, it is to do this. But we can presume that only a tiny fraction of Californians are actually going to even know about this or take the time. It would be nice if it were, you know, a big groundswell, but I doubt that's going to happen. And as we said, Leo, you know, even using our sponsor delete me, you got to tell them all this in order for them to tell the bad guys what they have to delete.
Leo Laporte [01:08:07]:
Right.
Steve Gibson [01:08:07]:
So.
Leo Laporte [01:08:08]:
Exactly. Yeah, way. So you saw how many data brokers. Because I'm only seeing 89.
Steve Gibson [01:08:14]:
Oh, I got 170.
Leo Laporte [01:08:15]:
Well, you are a lucky man.
Steve Gibson [01:08:17]:
I don't know why. Maybe. Yeah. Sure enough.
Leo Laporte [01:08:22]:
Isn't that weird?
Steve Gibson [01:08:24]:
Yeah. I wonder. Let me go, let me go click on mine.
Leo Laporte [01:08:27]:
Maybe they're going to add more over time. We know there are more than 500 in the real world. So I, you know, I, I just feel like, I don't know, I feel like it's not going to happen for till August.
Steve Gibson [01:08:46]:
Yeah.
Leo Laporte [01:08:46]:
That gives the data brokers lots of time to lobby.
Steve Gibson [01:08:49]:
On August 1st, the 45 day beginner starts. Yes.
Leo Laporte [01:08:55]:
Which gives the data brokers a lot of time to lobby our state legislators to change their mind.
Steve Gibson [01:09:01]:
I clicked on, I accepted it made me scroll down, down to the bottom of the terms of service. Even though, even though I already said, oh, now I got to log in and okay, I'm not, I'm not going.
Leo Laporte [01:09:11]:
To do that during the, I think carefully engineered to discourage the maximum number of users. To be honest, I, I, I feel like, see this there's, this is the first state to ever do this and we certainly have no federal law doing this. And I feel like that the reason is law enforcement doesn't want it. They love this information. Marketers have big checkbooks to write to.
Steve Gibson [01:09:34]:
And it's what runs the Internet? Unfortunately, it's what finances the Internet. Yes.
Leo Laporte [01:09:40]:
You know, the FCC just said, hey, by the way, Verizon, you don't have to unlock phones. You can leave them locked. This. We live in a world now where the people with the pocketbooks dictate the laws, not the consumers. So I just, I feel like go through this is probably worth it. We'll see. I'll watch with interest, but I don't have high hopes. Why do you have 159 data brokers and I only get 89? Yeah.
Steve Gibson [01:10:07]:
How's that all I got 170. Yeah. In fact, you. You can see in the show notes that is a picture of my status screen on 110 20.
Leo Laporte [01:10:16]:
I got robbed. Do you think it did it? It was 189 right out of the box.
Steve Gibson [01:10:22]:
Huh? No, it's 170 or 170 right out of the box. It was what you see there at the top of page 10 of the show notes.
Leo Laporte [01:10:29]:
Yeah.
Steve Gibson [01:10:30]:
And. And we compare it to yours and sure enough, maybe Southern California has got them extra crawling around. I don't know.
Leo Laporte [01:10:39]:
The whole thing feels a little, I don't know, suspect. We'll see. We'll get back to you in August.
Steve Gibson [01:10:47]:
Yes, September, actually, because August, the one, the fourth 45 day timer starts. So it won't be until a little past the, the middle of September that we're going to actually get some. They have 40. Well, it could be sooner. They, they have a maximum of 45 days, so this all lands on them.
Leo Laporte [01:11:06]:
You think they're gonna rush to do this? It's gonna happen on day 44, 23 hours, 59 minutes and 59 seconds. And right up to that very second, they're gonna sell it like crazy.
Steve Gibson [01:11:19]:
And it does feel like, you know, it's like there are those of us who have set our browsers to say, do not track. And, and my, My global privacy, my GPC or whatever it is, my global privacy control. You know, it, it, it's saying, no, Every so often I come to a site that, that says, oh, we're gonna honor your global privacy control wishes. And I'm thinking, oh, yeah, well, that's good. Thank you.
Leo Laporte [01:11:44]:
You're the one.
Steve Gibson [01:11:47]:
Okay, break time and then we're going to find out. Leo, where is what a bod.
Leo Laporte [01:11:56]:
Not Whataburger. No, because I know where that is. It's just down the street.
Steve Gibson [01:12:01]:
It's in Idaho. It's two words. W, H, A, T, A, and then. And the second word is bod. B. O D. What a bod.
Leo Laporte [01:12:09]:
What a bod.
Steve Gibson [01:12:09]:
What about what a bode?
Leo Laporte [01:12:12]:
That's what Lisa says whenever Reacher's on. But that's another story entirely. Our show.
Steve Gibson [01:12:18]:
And boy, he does like to take his shirt off.
Leo Laporte [01:12:21]:
He's got. Yes. Every episode. Yeah. You know, This one, I. I really think I needed to take this training. This episode of Security now is brought to you by Hawks Hunt. If you're running a company, you get paid to protect your company as a security leader, right? Against cyber attacks.
Leo Laporte [01:12:47]:
It's not easy, is it? It's getting harder with more cyber attacks than ever. And the phishing emails are better than ever generated with AI. They look exactly like those T mobile texts. Legacy one size fits all awareness programs, which, by the way, I was forced to take at iHeartradio and obviously that didn't sink in. They don't stand a chance. They Send at most 4 generic trainings per year. Most employees ignore them. And then, you know, and they did this at iheart all the time.
Leo Laporte [01:13:19]:
They send out those fake phishing things and when somebody actually clicks on them, oh, then you're forced into an embarrassing training program that really feels more like punishment. Like, you dummy. That's not the way to teach your team not to click on phishing links. That's why more and more organizations are trying HOX Hunt. H O X H U N T Hawks Hunt goes beyond security awareness and, and changes behaviors. And they do it the way you know your favorite iPhone game does, by rewarding good clicks and coaching away the bad. They gamify it. They make it fun.
Leo Laporte [01:13:59]:
Whenever an employee suspects an email might be a scam, Hox Hunt will tell them instantly with a gold star and yay, you found it. It's not a punishment, it's a reward. They get a dopamine rush. This gets your people to click it also, and we know this from research, gets them to learn. You can only learn when you're positively reinforced, not not negatively reinforced. It also ultimately protects your company. And you're going to love it if you're administering this. Because Hocksen makes it easy to automatically deliver phishing simulations across email, across slack, across teams.
Leo Laporte [01:14:34]:
It uses AI to mimic the latest real world attacks. Simulations are personalized to each employee based on department location and more. All while instant micro training solidify understanding and drive lasting, safe behaviors. You, as the administrator, can trigger gamified security awareness training that awards employees with stars and badges. It boosts the completion rate, it ensures compliance. And you know what? It's fun. Your employees will Love it. You could choose from a huge library of customizable training packages, or use the AI to generate your own that are just as brilliantly persuasive as the ones the bad guys are doing.
Leo Laporte [01:15:15]:
Hoxon has everything you need to run effective security training. It's all in one platform, meaning it's easy to measurably reduce your human cyber risk at scale. And you gotta do that. Don't take my word for it. Over 3,000 user reviews on G2 make Hox Hunt the top rated security training platform for the enterprise. Easiest to use, best results. It's also recognized as customer's choice by Gartner and thousands of companies like Qualcomm, AES and Nokia use it to train millions of employees all over the globe. You need this.
Leo Laporte [01:15:48]:
I need this. Visit hoxhunt.com securitynow today to learn why modern secure companies are making the switch to Hawkshunt. That's hawkshunt.com security now. We thank him so much for supporting the good work Steve's doing here at Security. Now I'm just gonna, you can spank me. Just, I'll give you a paddle. Just, just whack me.
Steve Gibson [01:16:13]:
It's, you know, the. We are the weakest link in the chain and when all the lower hanging fruit has been plucked, when all of the, you know, obvious ways of, of compromising networks and systems have been, you know, technology has, has squeezed we.
Leo Laporte [01:16:32]:
That's the truth of it. Right? That's how it works, you know, and that's why your num. Your biggest issue right now is, and we're going to talk about this at Zero Trust World is your users.
Steve Gibson [01:16:44]:
The human factor.
Leo Laporte [01:16:45]:
The human factor, yeah.
Steve Gibson [01:16:47]:
Okay, so I wanted to share a wonderful bit of AI hallucination news from this past weekend. The US National Weather Service has withdrawn a wind forecast from its social media platforms after its new AI powered system generated a map of Idaho which included two fictitious town names.
Leo Laporte [01:17:12]:
Oh my God.
Steve Gibson [01:17:14]:
Orange O Tilled and what a bod. Oh my God. The wind weather forecast map, which was initially shared on social media by the weather office in Missoula, Montana on Saturday, depicted those two non existent towns occupying Idaho's Camas Prairie region. The forecast posting helpfully encouraged residents to quote, hold on to your hats indicating that Orange O Tilled at least a 10% chance of high winds while what a bad to the south would experience calmer conditions.
Leo Laporte [01:17:58]:
Well, hold on to your bod.
Steve Gibson [01:18:00]:
Hold on to your bod. That's right. Beyond. Beyond the gratuitous synthesis of those two prominently Featured towns. The National Weather Service's map also contained multiple spelling errors and geographical inaccuracies. The Weather Service was quick to blame these mistakes on the use of generative AI technology. That's right, blame the AI.
Leo Laporte [01:18:23]:
And nobody looked at it.
Steve Gibson [01:18:27]:
No, no, no, Leo. Because we, you know, they've all been, they've all been let go.
Leo Laporte [01:18:33]:
Well, that's the thing. That's what happens when you fire everybody. Yeah.
Steve Gibson [01:18:37]:
I have an interesting adventure to share. Several months ago I began noticing that my beloved email, my EM client email client that I've talked about, that I discovered and talked about on on the show had stopped notifying me of incoming email in a timely fashion. Someone would say, you know, that they just sent something, but you know, after waiting a reasonable length of time, nothing arrived. I discovered that by completely closing and then restarting EM client, then it would again for a while be reliably notifying me of newly arriving mail. I haven't mentioned this until now because I hadn't been able to affirmatively verify that EM client was the problem, though it certainly seemed to be. And I mean, I was upset. This has been going on for months. But then a few weeks ago, something, I don't remember now what it was, but something caused me to look at the logs of GRC's H mail server.
Steve Gibson [01:19:46]:
What I discovered was that the server had been crashing and restarting, leaving a trail of of mini dump crash log dumps behind. And before the server would crash, it would log the source of its pain. It appeared to be something about IMAP and the retrieval of large file attachments and they were the IPs of my two locations. So that made sense too. So I spent a few hours having a heart to heart with chat GPT to see what it might have absorbed and and chasing down the various leads that it was generating. For me, there really didn't appear to be any reason to suspect that EM client was behind the trouble. And the H mail server discussion boards, you know, they were not of any help. They were filled with the typical threads of people commenting without actually knowing what they were talking about.
Steve Gibson [01:20:46]:
So, okay, look elsewhere for a solution. What I did realize was that if EM client, or for that matter any email IMAP agent that, you know, m that by nature of the way IMAP works, maintains an open TCP IMAP connection where it was expecting to be proactively notified of newly arriving email, which is one of the things that IMAP is able to do. You're able to put a connection into an idle status when the other end of that connection would crash and restart as the server was, that TCP connection would be left hanging. So EM client would never receive the news of no new email, nor would it know that the connection had gone down if it wasn't like, you know, proactively pinging for like some life at the other end. So my Environment contains both EM client and a collection of iOS devices, iPhones and iPads. And as I was correlating the times of the server crashes with with my own actions, it appeared to be more connected to iOS than to my use of EM client, which I have on on desktops. Some googling revealed that to my surprise, iOS has historically had a surprising degree of trouble getting the IMAP protocol correct. And this has been a source of great annoyance to to those tending IMAP servers before me.
Steve Gibson [01:22:34]:
The moment I deleted the troublesome account from all my iOS devices, all server crashing stopped. This was about a week ago and the server has never crashed since. And I even checked LEO just during our last break. My EM client on the desktop has resumed its previous perfect behavior of immediately notifying me of any new incoming email. So the reason for my having dragged everyone through this sordid tale is that my strong, in fact overriding proclivity is to live off the land right wherever possible. You know, since every One of my iOS devices came with a built in iOS email client, the last thing I would ever consider doing would be installing a second redundant email client. But yes, indeed, things had come to that. I remembered that the EM Client folks offered their mobile clients at no charge.
Steve Gibson [01:23:41]:
So I thought, okay, let's give it a try. I downloaded EM Client from the Apple App Store. Naturally, although I specified exactly the client name I wanted, EM Client was not first in line. No, it was preceded by sponsored apps that were paying to have my search results contaminated for their benefit. Like many others, I'm beginning to feel that the shine is fading from the Apple, which is truly sad. Hmm. Nevertheless, I was able to find, download and run EM Client. The first thing it asked upon running was whether I would like to import my existing world from a desktop instance.
Steve Gibson [01:24:30]:
I thought, what? Yes please. So it told me to open any already configured desktop instance of EM client in its menu under Tools I would discover QR Export. Sure enough, my Windows desktop EM client displayed a massive QR code which my mobile instance saw, and it was immediately set up with all my accounts, logins, passwords, tweaks, preferences, everything. So it's now been about seven days since I made that switch across all five of my iOS devices. You know, I'm still, I'm still not accustomed to how much better the mobile version of EM Client is compared to Apple's built in, but uninspired mail client. EM Client even runs on my oldest iPad, which I now have to keep plugged in. It's so old that chat GPT's client refuses to install, scolding me that I need to Update to an iOS version from sometime this century. But, but you know, I'm, I'm running the latest one that will run on that hardware.
Steve Gibson [01:25:50]:
So I don't, I just use, I use Chat GPT from the browser when I'm on that little iPad. And I am also, not only am I waiting for new Apple TV hardware, I'm dying for and hoping for an oled, you know, new iPad, hard.
Leo Laporte [01:26:06]:
Yeah, me too. Although that's going to be end of this year. You're going to be waiting a while or maybe.
Steve Gibson [01:26:10]:
Okay, in that case, I'm going to, I'm going to have to make the, I'm going have to, you know, I can't wait.
Leo Laporte [01:26:15]:
The bullet. You know, when I bought that, I, because I didn't want to wait either. And I'm very happy with it. The new Lenovo. Well, this isn't the new one, actually. This is January's Lenovo X1 carbon with an OLED screen. And it's. Yes, it's super light.
Leo Laporte [01:26:30]:
It's really great. I just, I'm madly in love with it.
Steve Gibson [01:26:34]:
I, I get it now. I did something different. I bought a Lenovo little, you know, the, the small form factor block because.
Leo Laporte [01:26:44]:
Yeah, yeah. Oh, we talked about this. That's right. You bought the desktop.
Steve Gibson [01:26:47]:
Yeah, yeah, I bought the desktop because it can drive three screens.
Leo Laporte [01:26:50]:
Right.
Steve Gibson [01:26:51]:
But, and then I, I remember hearing you talk about your laptop, looking at it, thinking, you know, that's gorgeous and everything. I was almost gonna pull the trigger when I sweat. Wait a minute. No, I don't ever go anywhere.
Leo Laporte [01:27:07]:
You don't need a laptop.
Steve Gibson [01:27:09]:
I, Well, I want to be able to be downstairs, you know, and be socializing with, with Lori, not hiding up in my cave for like in the.
Leo Laporte [01:27:18]:
That's why I have a laptop. I don't go anywhere either, but I move around the house.
Steve Gibson [01:27:22]:
I spent $400. I bought the cheapest terminal. Yes, it is. It's the largest screen, dumbest Windows laptop available.
Leo Laporte [01:27:35]:
Terminal.
Steve Gibson [01:27:36]:
It is. Well, because remote desktop. I, I remote desktop to GRC servers. I can remote desktop upstairs.
Leo Laporte [01:27:44]:
Exactly.
Steve Gibson [01:27:45]:
To my machine.
Leo Laporte [01:27:46]:
Yeah.
Steve Gibson [01:27:46]:
So I get all the speed and performance. I don't have to worry about synchronizing everything and, and all that. I just, I have a, A, A, a mouse screen and keyboard that I can have out on the patio, you know, in the family room, wherever I am talking to the computer that I left running upstairs. So I think that was, for me, it was the right solution because again, I don't, I, I, you know, if I travel, I, I just take a pad with me and I'm fine because I'm not actually doing any work.
Leo Laporte [01:28:13]:
Right. Yeah, actually. And then I did buy this, and at CES, they announced the next generation, 14th generation, which has some major improvements, but the OLED is very nice. That's the thing I really wanted was the OLED. And I think you're right to wait for the MacBook, but it's going to be a wait, so maybe as long as a year Wait.
Steve Gibson [01:28:35]:
Not MacBook. IPad.
Leo Laporte [01:28:38]:
Oh, you want an iPad? Oh, they have an OLED iPad. Yeah, the iPad Pro is fantastic. I have the OLED iPad Pro.
Steve Gibson [01:28:44]:
No, I'm sorry. I want a Mini. I like the Mini. It's the right form factor for me.
Leo Laporte [01:28:47]:
I mean, well, you can have any OLED screen you want with a mini. The Mini's great. I love the Mini.
Steve Gibson [01:28:53]:
The none. No, Mini is oled.
Leo Laporte [01:28:55]:
Oh, you're talking about imac. Imac has a screen. The Mini has no screen. It's just a nuc.
Steve Gibson [01:29:02]:
I'm sorry, I'm talking about the iPad mini. I'm.
Leo Laporte [01:29:05]:
Oh, the iPad mini. But who's on first? That's what I want to know. Oh, the iPad mini. No, they don't have an OLED that's going to come out, but that'll come out sooner than that.
Steve Gibson [01:29:16]:
Yeah, I was thinking.
Leo Laporte [01:29:17]:
Yeah, that'll probably be out this spring. Yeah, I.
Steve Gibson [01:29:20]:
Okay.
Leo Laporte [01:29:20]:
Yeah, they try to get those out for the school year, so certainly by June. Yeah.
Steve Gibson [01:29:25]:
Okay. So I just wanted to say that EM client for the. The is. Is a, Is free. GRC server never crashed. Not that everybody else is going to have that problem, but I was. And I just wanted to give everyone a heads up that whether or not you are running em client on your desktop, the 100% free em client for iOS or Android is truly lovely. And if you are one of our many listeners who switched to the desktop EM client after my discovery of it, or if you're one of our other listeners who wrote to me rhetorically asking what took me so long to find the EM client for the desktop, both groups will get the additional joy of instantaneous account setup by cloning via a QR code from your from your desktop to your mobile device.
Steve Gibson [01:30:19]:
Anyway, I you know, before I close the topic, I do want to acknowledge that I know someone's going to write to me. There's no excuse for anything some wrong remote email client might do to cause the email server that I'm running to crash. I'm 100% in alignment with that sentiment. But I love Hmail server. It is everything I want in a Windows hosted open source email server. In addition to many great features, many that I use, it publishes a. Com interface that's allowed me to automate parts of its operation to integrate it into GRC's email system. Because it's open source, you know, I was able to engineer its operation to get it to do exactly what I needed, but since I'm not in the position to spend lordly knows how long it would take to fix its actual problem.
Steve Gibson [01:31:20]:
I am treating the symptoms. Yes, and in this case that worked to my advantage since it allowed me to stumble upon EM client which, you know, doesn't induce those crashes because it's not iOS, which does. And then it turned out to be a much more pleasant user experience than Apple's own native mail app, which I would otherwise have never discovered. I would I'd be using Apple until the end. So now I'm glad I am not I have two pieces that I want to share next and then Leo, I want, as I mentioned you, to share a little bit of your recent Claude code revelations.
Leo Laporte [01:32:00]:
Certainly.
Steve Gibson [01:32:01]:
One of the AI newsletters that I keep an eye on is called the Batch. It's published by DeepLearning AI and last Friday an issue of the Batch arrived that caught my eye because I was pretty certain it would appeal to many of the non coders who follow this podcast. The issue of the newsletter opened with Dear friends, we just launched a course that shows people who have never coded before in less than 30 minutes how to describe an idea for an app.
Leo Laporte [01:32:39]:
Wow.
Steve Gibson [01:32:39]:
And build it using AI, they wrote. It's now time for everyone marketers, product professionals, operations specialists, analysts, students to build software applications with AI. And I know, Leo, that this is singing from from from from your hymn book. They they said. I've often spoken about why everyone should learn to code. I'm seeing a rapidly growing productivity gap between people who know how to code and and those who don't. For many job roles I hire for, I now require at least basic coding knowledge. Many times after I speak with a non technical audience about the importance of building software using AI People ask me how to get started.
Steve Gibson [01:33:29]:
In the past, I didn't have a great answer. That motivated the DeepLearning AI team to build to. To create, quote build with Andrew. It's the best way for someone who wants to try Vibe coding to get started. This course requires no prior knowledge of AI or coding, and it's vendor agnostic. Specifically, learners can use these techniques with whatever tool they're most comfortable with, like Chat, GPT, Gemini, Claude, or the chatbot built into the Deep Learning AI platform. Okay, so the Andrew cited here is Andrew Ng, the founder of Deep Learning AI. Yes, Leo, the website that's hosting this free course.
Steve Gibson [01:34:22]:
For those who don't know, Andrew also co founded Google Brain and Coursera. Yeah, and led AI at Baidu. He's an adjunct professor at Stanford University, former associate professor and director of Stanford's AI Lab Sail. So Andrew is certainly not some random YouTube influencer trying to get likes. To help everyone find this free 30 minute course, I've created a GRC shortcut using Andrew's first name. So GRC SC Andrew. So, just to be clear, I cannot vouch for this myself since I did not take the time to explore it, but Andrew is obviously the real deal and it would certainly seem worthwhile for anyone who might have been wondering how to take the first step toward AI driven coding. So GRC SC Andrew.
Steve Gibson [01:35:17]:
And that bounces you over to Build with Andrew under courses eeeplearning AI. And the second piece I wanted to share is from a listener, Al Liebel, who said hi Steve, I've listened to the podcast for years and have thoroughly enjoyed it. I currently work in cloud security and find your content informative. Keep up the great work. I'm writing to you because of an open source project I've been working on. I should tell you I'm a terrible programmer. I'm 54, wear progressive glasses, hunt and peck, and likely have mild add. And he has a little grin there in his note.
Steve Gibson [01:36:00]:
Having said that, I've been around computers since my dad built a Heath Kit H89 in our basement and I learned to use it. And as an adult, I've worked for software and security companies in various roles. So I know what looks like. I know what looks like. And with my current role in cloud security, I I understand what gets attacked and how. I've grown tired of the lack of security, privacy and trust online and decided to start Vet id. I've spent a bunch of time creating the design and then tried to figure out how to find people to help me get it built. That failed spectacularly.
Steve Gibson [01:36:43]:
So I dusted myself off and decided to go with plan B AI a few months ago in my free time he says I work full time. I went through some online classes for using AI for coding. They were helpful in teaching me the basics and I started using Chat GPT. It worked kinda. I I could prompt for what I wanted and Chat GPT would spit out the code and I would have to paste it into VS code and and do the things build, commit, push, deploy, etc. In this situation I was still the clumsy bottleneck. So I did a quick search and found CLAUDE code and it has been life changing exclamation point he says. I pointed it at my repo and the rest is history.
Steve Gibson [01:37:41]:
I trained Claude code on my design and and refined it. I had Claude code develop a plan to implement it leveraging multiple Claude code instances. One for iOS development, one for Android development. The main instance as the back end, front end lead and a Raspberry PI as a tester. The plans were broken into issues assigned to each repo and the different instances could communicate via issues for troubleshooting. Working part time over the last few months I'm close to having the first version done. All the best Al. So what occurred to me was when I read that and also that this really cool, you know, Build it by Andrew is that Leo.
Steve Gibson [01:38:31]:
You had just been saying something similar in in the pre show on Sunday so I thought I would, you know, give our listeners a chance to get caught up with what you have found apparently.
Leo Laporte [01:38:44]:
Well get ready because you're good. It's not just going to be me you're going to be hearing from or Andrew or anybody else. This is I think going to be a drumbeat. I really feel like that we have turned a corner in AI in general but a lot what people mostly experience is ChatGPT, you know, a chat interface and that kind of thing or maybe image generation. The people who are really in my mind Most impressed with AI at this point are coders who are using AIs to doing code. And I think the we've universally coalesced. There have been a lot of choices for a while. Chat GPT's Codex was the best one out there.
Leo Laporte [01:39:26]:
You know there there are coding models from China as well, QN and others. In fact Deep Sea got a new coding model coming out sometime soon that people say this thing is amazing but I think most of us have kind of, at least for the time being, centered on Claude code Anthropics Claude they did a big update November 24th with Opus 4.5. And they've been adding a lot of features since, but they've also been really focused on code and making Claude code be better and better. And the thing that's really accelerated the development is lately they've been using Claude code to improve Claude code. And I've seen a number of people who work at Anthropic say, yeah, most of the stuff we've released has been written by Claude itself, not by us. And that's a big change. So I, you know, I've been using Claude code with the $20. I have $20 subscriptions.
Leo Laporte [01:40:18]:
You're the cheap ones for everybody. Perplexity, open AI everybody, including Grok, because I get it for free, because Elon's given me an unconsensual blue check. So I've, I've tried them all. But I was, when I got this, this new ThinkPad, I started, I set up Linux and I started configuring it using CLAUDE code. And instead of me looking up, oh, what's the syntax for this? Because the. I'm using Sway, which is a very text based, you could probably use Nix or other things, very text based configuration as opposed to a GUI configuration. And CLAUDE was great. It knew everything, said, oh yeah, let me.
Leo Laporte [01:40:53]:
I said, can I put an icon up there? Can I make that wider?
Steve Gibson [01:40:55]:
Can I?
Leo Laporte [01:40:56]:
And it was doing all that. I thought, this is pretty good. I've used it so much. I would start getting to the point where I would say, okay, well, you've used all your credits. You have to wait for a couple of hours now. And it's usually just a, like you have to wait till 2. It's usually just a couple hours. But I thought, all right, I'm going to bite the bullet.
Leo Laporte [01:41:16]:
There's a $200 plan and there's a $250 plan. The $250 plan is 20 times the number of tokens. The context window is huge. It's 200,000k. The bigger the context window that the more it can hold in its head. 200,000 tokens is about 150,000 pages of stuff that it can hold in its head while it's doing stuff. The bigger the context window, I don't want to say more effective because it can maybe be less effective, but it's, but the more it can know about at the same time, it's kind of like our own brains, right? In fact, that's one of the problems I had with coding always. Even when I was younger, my brain was More adept is the complexity got rapidly got out of my context window, got too big.
Leo Laporte [01:42:00]:
So, and this is how coders handle it, you know, this is, you divide it into smaller pieces that you can readily solve and then they become black boxes. And so you reduce the complexity and you add to it.
Steve Gibson [01:42:13]:
Modularity.
Leo Laporte [01:42:13]:
Yeah, modularity builds a complex system. Anyway, I, I spent some money and then I thought well, now that I've spent the money on cloud code, maybe I should do something with it. So one, I was trying to think what do I need? And I'm on just to do something simple. I, I wrote an RSS reader, a text based RSS reader. And this is by the way, the discussion I had during the show. I said I can't run this. And then it said oh, that's because of Gatekeeper. So I've removed the quarantine attribute from your RSS reader binary.
Leo Laporte [01:42:49]:
Now you can run it without macOS blocking it. Wow, thank you, Claude Code it also, I found some little other issues. For instance, I didn't realize this, but on Linux the configuration file, which is a TOML file file, is kept in a different directory on the, on the Mac. So I said well, what's going on? So it did this is, it's debugging. It went through a whole debugging process. It wrote a debugger, it said what, what's the error message you're getting? I pasted it in and said oh doy. I've fixed the config location issue. I've added your API keys to the correct config location on the Mac.
Leo Laporte [01:43:26]:
It's in an application support folder. I should have known that eventually this is the point. I would have probably figured that out, but I didn't have to.
Steve Gibson [01:43:35]:
And that has been exactly my experience. Leo. It is really an accelerant. Yes, I mean it, it allows an expert to just run much more quickly by, by, you know, I don't have.
Leo Laporte [01:43:47]:
To go through manuals, I don't have.
Steve Gibson [01:43:49]:
To and, and do Google searching and dig through a bunch of nonsense links of people guessing what the problem is. It's like, no, okay, let's try.
Leo Laporte [01:43:57]:
So this is the GitHub and I, it's public on GitHub if you want to look at it. My GitHub handle is Leo Laporte and it's the RSS reader. But the point is this is not for the general public. I didn't write a general program. I wrote a program that's specifically for what I wanted. It's terminal based, it's Very fast. It does AI article summaries, it bookmarks it to Raindrop IO. It does a lot of things.
Leo Laporte [01:44:22]:
That's just what I wanted. Now it built it in Rust. It said, you want Python or Rust? It said, oh, well, if you can do it in Rust, go ahead. This is all the Rust code. There's quite a bit of code. It built this in a morning with very little interaction. I interacted with a little bit, but not a whole lot of interaction. I did some, you know, there was some back and forth.
Leo Laporte [01:44:49]:
There's some things I didn't like. It didn't work. So I said, can you do this? As it built it, it used GitHub Actions to create binaries that work on Linux and Mac, intel and Apple Silicon. I didn't even ask it to do that. But it did. It has. It added a help. It's got a Help feature.
Leo Laporte [01:45:07]:
It's got a bunch of single keystrokes it automatically made. I said, hey, is there a way that I could automatically update these RSS feeds every hour? I said, sure, let me just set that up for you. So let me show you the, the app because it's, it's, it's. First of all, I like it out of it. In fact, let me make my. Well, I'll do the screen bigger in a second. So this is it. It's RSS reader.
Leo Laporte [01:45:33]:
It's loaded in a series of RSS Oops didn't want to print RSS things that I had. Make it bigger so you can, you can see it. Which is not the best UI because as you can see now the headlines go off the side of the page. But so I am on this is stories. If I, if I say no, I never want to have actually that one I won't delete. I don't need this in my, you know, any of our shows. So I'm going to delete it. Delete this.
Leo Laporte [01:46:00]:
Going to delete this. Governor Clears Path Robo Taxis in New York. So let me hit Enter and it's going to generate. It goes out to Claude and generates an AI summary. If I want to, I can just hit oh and it will open it in the browser so I can, I can read it in the browser. It added that all by itself. I didn't even ask it for that. The navigation is single key VIM style navigation.
Leo Laporte [01:46:23]:
I can refresh the feed. Once I look at a feed, a summary. Oops, I forgot to hit Enter. Once I. Oh, and you see it. I said, hey, I don't know what's going on when you're generating, could you put a little. So I said, let me put a little hourglass there. Then you'll know this is the AI generated.
Leo Laporte [01:46:39]:
Now this is the thing that was specific to me. I save all the articles I want to use to raindrop. So capital S saves it to raindrop. It says, what's the tag? I'm going to say, that's for twit. And I am. And hit return. And now it's bookmarked on raindrop. See, it even put a little raindrop at the bottom.
Leo Laporte [01:46:58]:
So these are the. So this makes me a very. What I wanted was a very quick way to scan through hundreds of stories. I do this every single day, look at the headline, and then say, yeah, tell me more about that. Yeah, bookmark that. No, delete that. It wrote it, it's done. And, and it's easy for me to.
Leo Laporte [01:47:18]:
To fix it so that I, you know, if I add. Want a new feature, I can easily do that. In fact, I'll show you. We'll go, go back to a Claude code and I could say, can you add a key for, I don't know, emailing the story? By the way, it's pretty good on misspellings. And so this is what Claude code looks like. Let me get rid of the lower third here so you can see it. Because it's kind of. It uses a lot of fun verbs.
Leo Laporte [01:47:49]:
It says fermenting. You can go into. And then it will ask you questions. You can go into plan mode or coding mode. So how would you like to send it? Do you want to open the email app? Default email app you want to send by smtp. Do you want to use an email? I think I'm just going to have it open the app. So I'm going to hit one and it will do that. Oh, I'm not here.
Leo Laporte [01:48:13]:
Okay, and then what content should be included? Oops, I'm sorry, too many buttons. I need Claude to help me switch the show. Don't worry, Benito. Your job is safe. Trust me. What do I want? I want article, title, ua, AI summary, full article, content. I think I just want. I did it again, sorry.
Leo Laporte [01:48:41]:
And just want one here. So we'll just hit one. Oh, I guess I can check. Oh, it's check boxes. Oh, that's. Yeah, let's do it all. Okay. Wow.
Leo Laporte [01:48:55]:
Submit. Thank you. How would you like to send emails? What content? Okay, now submit those answers. So it did a little back and.
Steve Gibson [01:49:02]:
Forth thing and it's crafting right now.
Leo Laporte [01:49:04]:
It's, it's doing it, it's doing it in Rust by the way which I don't know and I've wanted to write Rust now it could probably do assembly language, it can certainly do common Lisp, it knows a variety of languages. It's probably best at Python I would imagine. Python seems to be the native language of a lot of AI but I thought well let's try it with Rust because it'll be memory safe, type. Type safe anyway, we don't have to go on. But you see it's coding right now. It's doing the actual work of implementing email functionality which I didn't have built in. So now I, now I will.
Steve Gibson [01:49:44]:
So something turned a corner and yes consequence that. I mean this suddenly got Claude code got very real and we have build with Andrew from you know, GRC SC Andrew, which is a 30 minute YouTube video basically from an, from an AI founder who is explaining how to talk to AI how to explain what, what you, what you're. What you want from an application that you want it want the AI to write for you. So I would also suggest interesting gap bridging.
Leo Laporte [01:50:22]:
You can, you can do quite a bit with the free plan. The 20 buck plan will be enough for almost everybody. Play with it is the best way because one of the things that I've noticed is this stuff is moving so fast that stuff gets out of date right away. I'm sure Andrews is not out of date. It's brand new so you know, stick with stuff that's brand new. And, and, but, but I think experimenting is often the best thing. There's something else Darren was telling me about that I was not aware of. Google also has something called Opal which is designed to use Gemini to do mini AI apps for people who are not tech technical.
Leo Laporte [01:51:01]:
It's a no code version of doing this and this is free. So there's other ways to get into this even if you're not a coder. I think it's probably the case that even as good as Claude is, it's good if you know a little bit about technology. Oh by the way it's done. The email will include the summary if you've generated other. Just the title. Okay, try it out. So, so that's how fast it did it.
Leo Laporte [01:51:34]:
And now if I run RSS reader it'll have a new capability. See at the bottom it says E for email. And I'll just. Let's, let's generate a summary for this. The summary is a little slow. I could probably use a different model that would be a little Bit faster. I'm using the most, the heaviest model right now, Opus. But let's email that.
Leo Laporte [01:51:56]:
Let's see if email works. Should it. Yeah, there you go. And I'll just mail this to you, Steve. How about that? How about that? And that's not his address, that's an old address. So how about that? Pretty cool, huh? Very cool. I just, I just added a massive feature that I could never have added in five minutes.
Steve Gibson [01:52:17]:
Yep. And oh, look at that. I just got your email.
Leo Laporte [01:52:21]:
Isn't that wild?
Steve Gibson [01:52:22]:
Because em client is now working.
Leo Laporte [01:52:24]:
Yes. Now I think there's still going to be lots of room for hand coded stuff like you do or even stuff like em client. But I think what's changing is a lot of the little stuff, you know that great Jonathan Colton song Code monkey, going to write a login. A lot of the stuff that's just kind of wrote. You don't need a code monkey for anymore. You just have Claude do it and then you get the higher level thinking, the overall planning, the architecting and maybe if you want some fine tuning or refinement, you do that. So there's still a human in the loop. But I think increasingly bullet boilerplate code will be written by AI.
Leo Laporte [01:53:06]:
It's just too easy. And by the way, it writes pretty good code. I mean everything I've looked at the code is pretty good.
Steve Gibson [01:53:13]:
Yeah, very cool.
Leo Laporte [01:53:14]:
Thanks for asking. I've been wanting to tell somebody about.
Steve Gibson [01:53:17]:
This and now you've let our listeners know that. Well, and I love it because it works perfectly with this build by Andrew to get started and then this sense that something like it's really getting better.
Leo Laporte [01:53:31]:
It'S doing a much better job, it's massively better. And that's the other thing is so many people are now into this. There is a lot of resources. There's a wonderful GitHub page called awesome Claude that has hundreds of resources for using Claude. Because Claude uses skills, it uses a lot of extra tools. There's a tool called Ralph Wiggum that's a hysterical. I know that's a Simpsons character. It's a hysterical tool that you turn on and you say what the parameter is like, don't come back until there's no more errors.
Leo Laporte [01:54:08]:
And then you also, if you want optionally can say, but only try 20 times. You can limit the iterations, but it will keep iterating until it reaches the goal that you set it. So it can, it will, it can. You know, instead of you interacting with it, it'll just, you just set it off. And it goes. And a lot of people are doing that Now. They're running 20 different versions of Claude code all at the same time and.
Steve Gibson [01:54:34]:
Okay, time for a break.
Leo Laporte [01:54:36]:
Yeah, sorry, Burke. Burke says your point, Leo, you could tell you've been wanting to talk about this. I apologize. You can edit this out if you want. You're watching Security now with Steve Gibson. We're so glad you're here and special thanks to our club members that make this possible. If you're not a club member, we'd love to have you Twitt TV Club Twit ad free versions of all the shows, access to the discord where Burke yells at me. You can also get a special programming, including our great AI user group.
Leo Laporte [01:55:07]:
We talk about a lot of stuff like this Twit TV Club Twit. Let's continue on with Security now, Steve.
Steve Gibson [01:55:16]:
So we have listener feedback, although I already shared some little bits that have dribbled in over the last week already. But TJ Asher wrote Steve, I'm all too familiar with the current state of the move to pure revenue generation by certificate authorities around code signing. We were first hit by this we with the change to HSM storage, meaning got a stored in hardware right two and a half years ago. He said our corporate policies prohibit allowing multiple users to access a computer under a common id. Which makes sense then because one of our development environments installs some aspects per user under the HKEY current user tree of the registry. Our current licensing of certain add ons would require an additional license for every possible user on that computer, so we're unable to implement an HSM solution to hold our code signing cert. As a result, we have no option but to store the key in the cloud. MsAzure has an option to allow this, but I was informed by our IT group that this costs a minimum of $30,000 to set up.
Steve Gibson [01:56:36]:
Yes, that's the number we were told. Okay, now I'll just interrupt TJ's note to mention that that Rick Straws detailed you know how to set up Ms. Azure Code Signing blog posting which we shared at the top of the show might be something that that that TJ would like to show his IT group. They may have some other situation that imposes a $30,000 cost, but it's difficult to imagine what that might be. Maybe there's a way around that. In any event, TJ's note continues writing the other option is for our certificate authority to host it, but then we need to pay for each and every signature that happens. We have dozens and dozens of files that need to be signed frequently because we release updates every month. This quickly adds up and you have to prepay for the signatures in blocks of a thousand.
Steve Gibson [01:57:35]:
That fee just went up and is now 26.4 cents per signature. So $264 per 1,000 and no refunds bought. Too many. Too bad. So sad. We go through enough signatures that we now buy in blocks of 5,000. Okay, so let me just pause here to remind everyone just how absolutely and utterly insane this has all become. TJ's enterprise that needs to be performing lots of code signing is stuck paying for the privilege of of signing its own code on a per file basis.
Steve Gibson [01:58:23]:
It should all be a non issue. They should be able to sign their code just as readily as they compile the code to be signed. But no. By making it increasingly difficult to sign code for no good reason other than because they can and by shortening certificate lifetimes. Again because the cabal of certificate authorities vote their own self interests, the industry's certificate authorities are able to force everyone into a cloud based service model where our use of our own signing key will be monitored and we will be charged essentially a fee per signing. TJ finishes the certificate authority group has the entire software industry over a barrel and there is not we can do about it. Whoa. Help you if you have a problem like we're experiencing now.
Steve Gibson [01:59:26]:
Need good support? Buy a business account. It's no wonder this change to yearly expiration is happening because they're going to lose out to free TLS certificates from let's encrypt. They need to recoup that revenue somewhere. I can't imagine being a small or solo developer. Regards, TJ Asher and then Jay Thompson wrote are you interested in starting a service to issue certs? I put grccerts.com and grccodeserts.com on hold just in case. Sign J so first of all Jay, I very much appreciate your consideration. There are many considerations but addressing the name of such a service first if and it's not going to happen. But if I were to start a certificate authority, I wouldn't tie it to GRC in any way.
Steve Gibson [02:00:26]:
It would need to have some sort of long lived new neutral name, you know like DigiCert or Identrust or VeriSign. You know those are good names for a certificate issuing authority. And I said first of all because you know there's more. You know the saying everyone has their own version of hell in my case having anything whatsoever to do with running or in any way managing a certificate authority would definitely be right up there, near the top of the most hellacious ways I can imagine me spending the remainder of my life. So thank you, but no thank you. I know that I bitch and moan and carry on about the annoying cabal that has been allowed to form, but at the same time I deeply appreciate that there are people who are able to do what is completely beyond me. In the early days of grc, I ran a larger organization because I thought I was supposed to. And while my employees may have been happy, I was mostly miserable.
Steve Gibson [02:01:33]:
You know, thanks to one rough Monday morning of firings during which I reduced the company size in half, followed by a great deal of welcome attrition. I wound up with sue to deal with operational stuff and Greg to run interference for me with tech support, which leaves me mostly completely free to sit in a quiet corner by myself with elevator music, a PC, mouse, screens and keyboard. That's my bliss. But Jay's note brings up the interesting question of the contemporary creation of a new certificate authority. It's not a simple thing and it would require a concerted effort. But that said, I would imagine that the apparent greediness that is overtaking parts of the certificate authority business might be creating an opening for a well financed newcomer. The first problem any newcomer would encounter would be the establishment of their own root certificates into the heart of every single system where their signed certificates would need to be trusted. You know, this might seem like a classic chicken and egg problem since you cannot sell any certificate whose signature will not be trusted.
Steve Gibson [02:02:56]:
Not not even one. And it'll be difficult to convince the various root store programs to accept any new and unproven and currently unnet new necessary root certificate without good cause. Let's Encrypt solve this chicken and egg problem by borrowing the trust relationship which Iden Trust had already long established at let's Encrypt Launch, which was 11 which was now 11 years ago in 2015, its own root certificate was was not present in a single trust store. So in order to bootstrap trust, let's Encrypt certificates were cross signed by Ident Trust's well trusted root certificate. The way this worked was slick. Let's Encrypt first created its own new intermediate certificate. This intermediate certificate is what was used to sign all of let's Encrypt TLS web certificates which it was issuing. But the signatures made by this intermediate certificate needed to be trusted by all of the world's web clients.
Steve Gibson [02:04:15]:
To make that happen, let's Encrypts new intermediate certificate was co signed. Technically it's the term is cross signed by let's Encrypts newly minted and not yet trusted root certificate and also by Iden trust's own already well trusted root certificate. So two different root certificates trusted. You know, they signed and therefore demonstrated their trust of the intermediate certificate which let's Encrypt was then able to use to sign the end certificates, the TLS web certificates certificates. The use of Ident trust's root certificate to anchor the certificate chain meant that the the signatures let's Encrypts intermediate certificate was placing on TLS certificates would be trusted from day one by all web clients since those TLS web certificates chained up through let's encrypts intermediate certificate to a root certificate everyone Already trusted for three years from 2015 to 2018, let's encrypt certificate trust chain relied solely upon identity root cross signing. And then finally after three years in 2018, which I suppose finally after let's Encrypt had demonstrated the success of their concept, their own operational integrity and the feasibility of their new Acme automation technology. And I imagine the existing CAs were not happy, but their own root certificate which was named ISRG root x1 was added to all of the major trust root stores. And then finally in 2021, three years after let's Encrypt root had been added to everyone's root stores, the root certificate that identrust had originally used to cross sign let's Encrypt's intermediate certificate itself expired, ending the cross sign phase and leaving all modern systems trusting let's Encrypt's own root and the intermediate certificate it had signed.
Steve Gibson [02:06:41]:
So the lesson taught by this bit of history is that creating a new trusted certificate issuing authority is neither quick nor easy, nor should it be. It would require an entity to first demonstrate both their strict commitment to rule following and their ability to rigorously follow the rules that they set. They need to demonstrate that imbuing their their signatures with widespread global trust would not in any way endanger the current status quo. If someone really wished to do so, they could arrange to bootstrap themselves into business the same way let's Encrypt did. And I doubt that the members of the CA browser forum could prevent that from happening, much as they might not wish to have a powerful new lower price, easy to use certificate authority, undercutting their well established cash printing business. And taking the opposite view for a moment, we should all definitely require any upstart newcomer to prove themselves worthy of our trust. There's big money to be made in the certificate issuing business. The bigger the big guys get, the more deadweight overhead they accrue and need to carry, and the costlier their certificates become, the more tantalizing will be the opportunity for newcomers to attempt to get in for a piece of that action.
Steve Gibson [02:08:17]:
Anyone should have the ability to become a certificate authority in good standing. But as we've often noted, along with the right to print money comes the burden of being very careful whose certificates are signed and thus trusted. So interesting question Jay. Being a CA is not for me. I like the way my life is right now, but I really I can see, you know, let's encrypt manage to start and they were, you know, that was 11 years ago. So I could see an entity deciding that they want in and and see an opportunity because I think the the flip side of all the grumbling and grousing we're doing is demonstrating that there's some opportunity here for somebody who is, you know, serious about it in the long term. But it's not something that you do easily or quickly. Scott wrote Steve, I've listened to you for years for your comments and sage advice about security matters and general comments about it.
Steve Gibson [02:09:18]:
Do I want he said, do want to say I appreciate your thoughts on oh on vitamins and after the last podcast have increased my intake of magnesium, please continue to include the occasional thoughts about how vitamins might prolong our lives. Definitely not a bad diversion from the usual themes. Thanks Scott. And I just wanted to mention I put that in here as a placeholder to say that I as I had said earlier, I I received similar sentiments from our listeners and a couple young listeners. One in particular said, hey, supplementary nutrition is not just for older folks. So I appreciate that and I will share what I find from time to time. To that end, I wanted to update a little bit of the news from last week. Steve Penfold said, hi Steve, thank you for the info on magnesium.
Steve Gibson [02:10:08]:
Last week I found your previous leads on vitamin 3 and now K2 as well, plus the ketogenic way of eating, but I wasn't aware of any of the magnesium stuff. He said. Your book recommendation caused me to take a look at it on Amazon's site here in the uk. It seems that there have been two updates to and he has in quotes the Magnesium Miracle book by Carolyn Dean that you said you read in 2009. A quick summary of these updates, he said. First of all, in 2009 the version you read must have been the original 2003 version. I think that's probably likely. He said there was an updated version released in 2017 with the same title.
Steve Gibson [02:10:53]:
And he said, additionally, there is a now even newer book from 2023, billed as, quote, an up to date summary that includes the advances in clinical magnesium research and therapy from the past five years. He said, this is the version that I bought in Kindle format for only 3.92 pounds. He says equates to just over $5. Note that he. He said, note that the word miracle has been dropped from the title. He remembers me grumbling, you know, it's like, it's not a miracle. Stop saying that. Yeah, this book is just titled Magnesium, the Missing Link to Total Health.
Steve Gibson [02:11:35]:
So anyway, I'm taking my gram of magnesium now.
Leo Laporte [02:11:39]:
I gotta say. Good, it's working. It's working.
Steve Gibson [02:11:43]:
Good, good, good, good.
Leo Laporte [02:11:45]:
My sleep's been better too, which is nice.
Steve Gibson [02:11:47]:
Yeah, it does that. And be aware that after some length of time.
Leo Laporte [02:11:52]:
No, it's already. That's already happened. Yeah.
Steve Gibson [02:11:54]:
Okay.
Leo Laporte [02:11:55]:
That's what I was looking for, that actually, because. Yep, it's helpful.
Steve Gibson [02:11:59]:
Yes, it is. Exactly. It is.
Leo Laporte [02:12:01]:
Yeah.
Steve Gibson [02:12:01]:
Laurie and I both love it.
Leo Laporte [02:12:02]:
I'll back off a little bit if I need to, but so far, so good.
Steve Gibson [02:12:06]:
Nice. So anyway, that was Steve Penfold. Spin Right Owner and club Twit member Joey Albert said, thank you, Steve. You started me on the Lazarus Project series yesterday and it is outstanding. He said, rotten tomatoes meter is 100% fresh. Just bummed it's leaving Netflix this month, the 27th. I have to binge now. Signed, Joey and Mr.
Steve Gibson [02:12:31]:
Ron said, thanks for the tip about the Lazarus Project. I had never heard of it. I just finished attentively binging it, which really is the only way to follow the plot. It's the most outstanding time travel story I've ever seen. So I just wanted to mention that Joey and Mr. Ron's opinion was widely echoed among those who wrote one Lister reminded me of Apple TVs for all mankind, saying that he thought it was fabulous. For those who don't know, it's an interesting speculative fiction that extrapolates an alternative history where Russia wins the early stages of the space race by beating the US to the moon. I didn't watch the entire series, so I'm unable to offer my own opinion.
Steve Gibson [02:13:19]:
Lori and I watched, I think, like maybe the first four or five episodes until we had. Until we had caught up, but it seemed to kind of just be lumbering along and not really much so. I don't really recall it being amazing, but maybe I didn't give it a chance. It does rate an 8.1 on IMDb, which is a good score, but I've also seen like, you know, anime things rate highly, so it's a matter of who's rating them, right? And that's not me. So Philip said hi Steve, Many thanks for the valuable lowdown on reduction in the lifetime of code signing certs. Does this mean that eventually all software will need to be updated every two years? What does that mean for software for which I've bought a perpetual license or freeware? What if it's no longer maintained? And I guess that you and I probably the last two users are probably the last two users of Paint Shop Pro.
Leo Laporte [02:14:25]:
No, Paul Thurat loves it too.
Steve Gibson [02:14:26]:
Okay, good. He says it might have to find something else at last. Best regards, Philip okay, so Philip's quandary about this was echoed by a number of our listeners, many of whom wrote wondering how shorter certificate code signing certificates would affect the long term verifiable legitimacy of the code those certificates were used to sign. And right on cue, Bleeping Computer posted a story last Wednesday with The headline Logitech Options+G Hub Mac OS Apps Break after Certificate Expires yeah, Whoops. So Bleeping Computer.
Leo Laporte [02:15:14]:
They fix that, by the way?
Steve Gibson [02:15:15]:
Yes. Bleeping Computer began their coverage by writing Logitech's Options plus and G Hub apps on Mac OS stopped working after their code signing certificate expired, leaving users unable to launch them on Apple systems. Options plus is Logitech's input device configuration app, while G Hub is a similar app focused on customizing compatible Logitech G gaming peripherals. Both allow setting app profiles, button remapping, lighting options, scroll wheel, and sensor sensitivity. Multiple users reported that Logitech apps on macOS did not load, making custom gestures, mapping scroll settings unavailable and forcing them oh the horror. To use basic input functions. Impacted users express their frustration with the sudden loss of productivity enhancing customizations, while many wasted time reinstalling the Logitech apps, trying out Safe mode, or wiping their configuration files. Eventually, Logitech published a statement on its support portal admitting that the issue was caused by a certificate that had expired.
Steve Gibson [02:16:30]:
Okay, at the same time, I signed GRC's Never 10 Windows executable program on Sunday, April 21, 2019, and the code signing certificate I used to do that then expired on April 4, 2022. Yet a check on the validity of Never 10's code signing certificate today reels reveals that it remains valid. So what's going on? This brings us to this week's topic. An examination of code signing, certificate expiration and the answer to the question how could Microsoft be issuing three day code signing certs?
Leo Laporte [02:17:26]:
I do not know.
Steve Gibson [02:17:27]:
And I'm going to have a cup of coffee or.
Leo Laporte [02:17:29]:
I just want to say one thing. I'm very proud. While you were talking, I just submitted two pull requests and did a rebuild on GitHub. Version 0.2.2 of the RSS reader is now out including email functionality. And I sped up the AI summaries by switching models, plus better error messages. So thank you very much.
Steve Gibson [02:17:50]:
You have had a productive day coding. Leo.
Leo Laporte [02:17:53]:
I feel like a real developer while.
Steve Gibson [02:17:56]:
Co hosting a Security now podcast.
Leo Laporte [02:17:59]:
It's pretty amazing. I have. I mean it even uses GitHub Actions to build the software to put the binaries up there so people can download it. I think open source software is going to really see a revolution. And what's even more, more interesting to me is that this means you people can write their own custom personal stuff. This was always kind of the goal. Right.
Steve Gibson [02:18:20]:
And Apple was. What was the card deck thing that Apple had?
Leo Laporte [02:18:25]:
That was the idea. People have been trying to do this for decades.
Steve Gibson [02:18:30]:
Yes.
Leo Laporte [02:18:30]:
In fact, I remember John C. Dvorak telling me what was the. What's his name? Morris. The guy who. Morris Moro. George Morrow, who did little. Remember the Morrow computers that were a little bit like the Osbornes. They were suitcase computers.
Leo Laporte [02:18:45]:
George Morrow told Dvorak, he said, you know, everybody should be writing their own software. Nobody should be using off the shelf software. Which was hysterical at the time because, you know, not everybody's listening.
Steve Gibson [02:18:56]:
It was impossible.
Leo Laporte [02:18:57]:
It was impossible. But I mean, look, you're not going to write your own word processor, a video editor, but you might write a lot of little tools I have been that make your life better.
Steve Gibson [02:19:07]:
Everybody's needs are different.
Leo Laporte [02:19:09]:
I mean, and they could specifically be your needs. Yeah.
Steve Gibson [02:19:12]:
And the brilliance of Bricklin's spreadsheet was that it was a programming language. It was, you know, VisiCalc allowed you to, to put numbers in and do with them what you wanted. And you know, so it was a type of programming language and you know, and there are some databases that have been like that through, through the years where they were really. They really helped you get the job done.
Leo Laporte [02:19:42]:
Yeah, well, and the other thing that has always been the holy Grail is natural language interfaces to computers. You know, and this was, you know, hello, computer, use the keyboard.
Steve Gibson [02:19:52]:
Keyboard.
Leo Laporte [02:19:53]:
How quaint. We've we've, we've known that this is really the natural way to interact with a computer. Let it do the computer stuff, you do the human stuff. But we haven't had that capability.
Steve Gibson [02:20:03]:
Well, and imagine Leo, when we can put the AI loose on co on existing repositories and have that find the bugs.
Leo Laporte [02:20:13]:
Yeah, well, I think you mentioned this a couple of weeks ago. There's already tools to do that. I think that's going to be a revolution as well. And as we were saying, I mean, yeah, there's security issues that come up, but you can pretty much be sure that Claude is not going to use STR copy instead of STRN copy when it's writing, you're not going to see buffer overflows as much because it's, it's smart, it's, it knows that's a bad idea. Humans forget.
Steve Gibson [02:20:40]:
Yeah, and I said last week I even had chat GPT when I asked it what was the port number for the Mongo db. Right. Gave it to me and said, and by the way, you should not expose that to the public Internet.
Leo Laporte [02:20:54]:
Isn't that great? I think we're in a brave new world. It's certainly an interesting world. There's no question about that. You're watching Security Now. This is Steve Gibson. We're so glad you're here. Thanks for watching and let's go on with the show. Steve.
Steve Gibson [02:21:08]:
Okay, so the title for today's podcast was inspired by the sentence that Rick Strahl casually dropped into his blog posting. In passing, he noted, quote, the certificates issued by Microsoft are very short lived with expirations that last only three days to aggressively thwart invalid signing attacks in case a certificate is compromised. Okay, now this raises the obvious question, how can it possibly be that Microsoft would be using code signing certificates that only last for, for three days before they expire? The answer to that question brings us to a fundamental difference between the traditional web server authentication TLS certificates, which we're all by now intimately familiar with, and code signing certificates, which we spent considerably less time exploring in the past. So exactly what are the differences between these two in the case of a web server's TLS certificate, our goal, the purpose, is to validate and authenticate the identity of a remote web server during a real time transaction. Right now we need to be assured that the remote server we have just this moment connected to using its DNS provided IP address is in fact the server we expect DNS could have been compromised to lead us astray, or our Internet packet traffic could have been intercepted and diverted to a malicious web server. So to do this, we need to verify that the certificate we've just received from over the connection we've just established matches the domain we intend to connect to, and that the certificate is valid, not expired, in good standing, not revoked, and was signed by a certificate authority whose signatures we trust. If all of those things are true, we would have very we would have every reason to believe that we're connecting to a web server serving the domain we intend so. Now look, it's code signing.
Steve Gibson [02:23:35]:
What about code signing? The assurances we seek from signed code are obviously very different from the application of TLS web certificates. We want to ascertain two things from the signature of of any signed code, we want to determine the verifiable identity of the entity that signed the code, and we want to verify that not a single bit of the code that was signed has been altered since its signing. And that's it. That's the entire purpose of signed code, who signed it, and nothing has changed since. We understand the general reason why certificates have expiration dates. While I complain a lot about certificate lifetimes being so short that their renewal becomes burdensome, at the same time, it would be somewhat unnerving to be issued a trusted certificate that never expired. Yikes. If that certificate were to ever get loose at any time, ever, bad guys could abuse its trust, potentially forever.
Steve Gibson [02:24:59]:
GRC has a code signing certificate stored, as they must all be now, in a SafeNet 5110 USBE token. And it's actually sort of comforting to know that it comes with a drop dead date, after which it will become useless to anyone. If it didn't have that, I would need to wipe its contents and then probably still smash it into tiny bits to make absolutely sure that it could never be reused. Once I was finally finished with ever needing it again. You know, I mean, it has to be completely destroyed. But what about the code that it was used to sign? Let's take the never 10 for Windows executable I mentioned before. If you're curious, you can go to GRC and download that executable right now. Never 10exe to see for yourself.
Steve Gibson [02:25:59]:
I signed that executable on Sunday, April 2 or April 21, 2019, using a code signing certificate that still had very nearly three years of life left on it, since it would expire on April 4, 2022. Signed on April 21, 2019. Certificate with a certificate that's expiring on April 4, 2022 that did expire, had to on April 4, 2022. At the time I signed that code, the certificate was in good standing. It was issued by my company, Gibson Research Corporation. I'm sorry. Issued to my company, Gibson Research Corporation, by DigiCert. The signing process meant that.
Steve Gibson [02:26:51]:
The signing process meant that an unsprufable cryptographic hash was taken of the code, the Never Ten code, whereupon the private key I was in possession of, because at this time and still today, I own my own code signing private key, it would be used to sign the hash. And GRC's certificate that was issued by DigiCert containing the matching public key was affixed to the end of the code. From that moment on, anyone who obtained that never 10 code could check its certificate to see that the certificate was validly issued by DigiCert, a certificate authority that has carefully earned everyone's trust. The signature of the code's original hash could be verified using the public key contained in GRC's certificate. And that validly signed hash could be compared with a fresh hash of the code taken right then to verify that not a single bit of the original code had been changed after it was signed. Remember the two assertions that are made through code signing? The identity of the certificate that performed the signing, in this case Gibson Research Corporation, and that since the time of the signing, not a single bit has changed. Okay, now jump forward to 2026. There's still a never10 executable program that can be downloaded from GRC, and not a single bit of that code has been changed since the day it was signed in.
Steve Gibson [02:28:43]:
In April of 2019. Yes. The certificate that was used to perform the signing expired three years after the signing, which is almost four years ago, in April of 2022. But do we care? The signature accompanying the code. The signature accompanying the code remains valid. The certificate that's attached still contains a public key that can be used to verify that not a single bit has changed since the moment it was originally signed. And Gibson Research Corporation's name is carried in the attached certificate, all of which was signed by DigiCert. Here's what's common between TLS and code signing certificates.
Steve Gibson [02:29:38]:
In both cases, the only requirement is that the certificate is valid at the time of its use. So in the case of tls, that means it must be valid and remain valid. Every time a web browser initiates a new connection and that certificate is offered up as proof of the remote server's identity, connecting to the server is the time of the certificate's use. But in the case of code signing, the only Requirement is that the certificate used to sign the code be valid at the time the code is signed. Since the only thing code signing is asserting is the identity of the signer and that nothing has changed since, requiring that the certificate be valid at the instant of the signing is sufficient. And now we can see why and how. Microsoft's Azure code signing uses certificates having a very short life of three days. Technically it could be as short as an hour.
Steve Gibson [02:30:54]:
But creating certificates is not without overhead. So I imagine they probably cash any certificates they've created for a couple of days in case the same signer returns with more signatures that they need signed or more code they need need signatures signed for. But there's an exploit we haven't addressed. What's to keep a bad guy who manages to get their mitts on someone else's expired code signing certificate from using that certificate to sign their malicious code. The signing certificate may have expired, but what's the enforcement mechanism for its expiration? We might suggest that the PC used to perform the signing would examine the certificate and see that it had expired. Okay, the bad guys know that their stolen certificate has expired, so they simply turn back the clock on the signing PC that they're using to a point where their certificate is valid. Now, the PC believes that the certificate is valid and in good standing. It has no way of knowing what day it is.
Steve Gibson [02:32:15]:
The obvious answer to this dilemma is for anyone who might be relying upon that certificate to examine for themselves the signing certificate's expiration date and time, just as they would for a real time TLS certificate and refuse to trust anything signed by any certificate of that has expired. Okay, but then we have a new problem. As we've seen, what we really intend for code signing is for any code that's signed by a certificate that is valid at the time of the signing to forever hence be judged as validly signed. So how do we accomplish that? Introducing the the tsa. A different kind of tsa. This is the Time Stamp authority. A timestamp authority is a trusted third party. It's typically a certificate authority and is often but not necessarily the same CA who provided the signing certificate in the first place.
Steve Gibson [02:33:23]:
It is a service that CAs offer during the code signing process. Once the code has been signed, the signature the the the after it's been signed, that signed signature is itself hashed and forwarded to a timestamp authority. The hash is forwarded and it's bundled with a UTC format timestamp and that package is signed with the timestamp authority's private key. They then returned this signature along with their own TSA certificate containing their public key. The result is a counter signature containing a verifiable timestamp. The result of all these machinations is that the final signed code actually contains two certificates. The code signer's own certificate indicating their identity and the validity time window of their certificate, and a signing timestamp that can be verified using the timestamp authority certificate, which is also attached. So now we have exactly what we want.
Steve Gibson [02:34:48]:
The signing certificates validity window, from the not valid before to the not valid after times is enforced by an unspoofable timestamp provided in real time on the fly at the moment of signing by a third party time stamping service whose certificate, whose own certificate their public certificate is also attached to to allow their time stamp to be verified. It's because GRC has always signed its code with the aid of a time stamping service that the validity of our apps never expires, even long after the certificate that was used to sign them is long gone. So what happened with Logitech? The truth is we don't know because we can't tell from what they've said. They said that a certificate expired, but we don't definitively know what certificate expired. Adding a timestamp to executable code and to libraries and whatever you need code signed is now so routine that I'm a little skeptical that, that they could have actually somehow failed to do that. I mean, it's built in timestamping. Everything ought to be just, I mean, like completely in the core of whatever signed their executable code. I suspect it's more likely that they have some sort Logitech being who they are, some sort of their own installer or patcher or updater or who knows what where they were using their own certificates internally in some fancy system of their own design, and they tripped over their own tail.
Steve Gibson [02:36:50]:
To me, that seems more likely. It's important to appreciate that it's only commercial certificate authorities who arbitrarily enforce short expiration policies. When you're creating your own certificates for your own internal purposes, you can set whatever expiration date you like. So someone may have, someone at Logitech may have created a 25 year certificate back in 2001, figuring that the system they're using it for, for, you know, would be replaced long before that certificate could expire. But we all know how that goes, right? So after a few years, everyone completely forgot about it and never thought about it again until Whoopsie 25 years had flown past and that long lived certificate surprised everyone by reaching its end of life date and expiring. To me, that seems the most plausible explanation. But again, until more is known from Logitech, there's no way to tell. In any event, now everyone knows exactly what goes on with code signing certificates and how the static assertions they're designed to make differ from the real time assertions made by TLS web certificates.
Steve Gibson [02:38:17]:
And it should be clear how Microsoft's Azure code signing cloud code signing service is able to sign with three day lifetime certificates. Those signatures are immediately timestamped. While that short lived code signing certificate is valid after that the certificate's expiration doesn't matter. It can expire and no one cares.
Leo Laporte [02:38:53]:
I'm.
Steve Gibson [02:38:54]:
You're muted.
Leo Laporte [02:38:55]:
I turned my. I somehow. I don't know what's going on. Turn myself off. I complete. I was just saying and. But are we safer, Steve? That's the question. Is it safe yet? No.
Leo Laporte [02:39:09]:
Thank goodness. Because if we were, then we wouldn't need Steve Gibson in security now. We would just go on with our humdrum lives, never worrying about security.
Steve Gibson [02:39:18]:
I was going to say we're not safe as long as a. A human has their finger on the button. But on the other hand, there is Skynet and we don't want that to happen either. So. Yeah, I know.
Leo Laporte [02:39:29]:
I think we're getting close to Skynet.
Steve Gibson [02:39:31]:
Well, the temptation, right? It's like, oh, that would be really great. It's like, no, no, just go watch Colossus. The Forbin project.
Leo Laporte [02:39:39]:
Exactly. And by the way, you know that Elon Musk has named his two two massive data centers Colossus 1 and Colossus 2. He is, of course, clearly a fan.
Steve Gibson [02:39:48]:
Yes. Too bad he didn't rename Twitter Colossus because then we'd have a name that we would recognize.
Leo Laporte [02:39:55]:
We could use, that you could search.
Steve Gibson [02:39:57]:
For instead of saying X, formerly known as Twitter. Because X is just a crappy name for any.
Leo Laporte [02:40:02]:
I know. He's loved it since before PayPal. This was. Is always his dream is to have X the Everything app. I think he doesn't understand that the SEO of the letter X is as bad as you can get. Literally, there wouldn't be a worse letter you could choose. Anyway, that's a subject for another matter, another day. Ladies and gentlemen, we have concluded this spectacular edition of Security.
Leo Laporte [02:40:30]:
Now, I apologize for dragging it down into the clud, but we had some fun.
Steve Gibson [02:40:36]:
I wanted, I wanted our listeners to understand that. I mean, again, we, we know there are people who do not fancy themselves coders. They may have dabbled in it or they just, it just made, you know, their interest in security and they'd like to cross that bridge. I think, I think it's. The world is changing so that nobody is not a coder.
Leo Laporte [02:41:00]:
The other side of this, people who haven't coded that I find encouraging. See, I am a coder hobbyist. Right. I actually enjoy coding. I love coding. So it gives me the opportunity to focus on a.
Steve Gibson [02:41:16]:
Maybe problem and not on the details.
Leo Laporte [02:41:18]:
Yeah. Unless maybe a less practical kind of coding. If you don't have to write the login code, you can think at a interesting higher level.
Steve Gibson [02:41:28]:
Or for me, I. When I was implementing GRC's email system, I, I love Nuevo Mailer. It's all PHP. I've never had it because all of my server side stuff is in assembler. Crazy as that is. I've never learned PHP so. But I wanted to make some changes to it. So I asked Chat GPT, blah blah blah blah blah.
Steve Gibson [02:41:50]:
And it gave me the code and it was.
Leo Laporte [02:41:52]:
That is amazing, isn't it?
Steve Gibson [02:41:54]:
Well, that happened a couple years ago, so it was still a little bit rough. I had to do some try it now but it gave me a good head start.
Leo Laporte [02:42:01]:
The other thing I, I pointed out on Sunday, I think it's really true is this is all possible because for the last 20 years, people like you, the open source community, web developers, everything online have been putting everything they know online. I remember saying for years, get a blog and put your. Put your personal view up on the public Internet. What I didn't realize is it was going to be used for training these AIs. And it's because of that that they can be so good. You know, we've given them our, our information, our brains and people are very upset about that, but I don't think they should be. I think this is a phase change in humanity that is going to be. And this is the other thing.
Leo Laporte [02:42:44]:
You know, everybody talks about the AI bubble and it's going to collapse and people. It's overhyped and it's over. I don't think it is. No. I really think this is going to be the year that people are going to go, oh yikes, yeah, we, for better or worse.
Steve Gibson [02:42:59]:
I'm impatient for the economics to make sense. I keep coming back to that.
Leo Laporte [02:43:03]:
Yeah, I don't know if it ever will. The good news is, look at Nvidia announced at CES the Vera Rubin platform, which they say is 10 times more efficient. And I Think this is because there's so much cost and so much pressure on this that a lot of energy is being.
Steve Gibson [02:43:19]:
It's going to drive.
Leo Laporte [02:43:20]:
Yes. And that's good news, right? That's good news. China's doing the same thing because of risk constraints in the kind of processors they can get. They've made very efficient models that are very small and very effective. That's good. Those constraints, those pressures are very good in improve and making us improve our processes.
Steve Gibson [02:43:38]:
Yeah, people will be able to buy second hand GPUs at a really good.
Leo Laporte [02:43:43]:
Price too by the way, in about five years ram's going to be very cheap.
Steve Gibson [02:43:48]:
That's right baby. Because all those, you know, Colossus 1 and Colossus 2 is going to have to scrap its entire investment, start over. Yeah, that's right.
Leo Laporte [02:43:57]:
That's already the case. Vera Rubin if it is 10 times more efficient and faster.
Steve Gibson [02:44:00]:
Right.
Leo Laporte [02:44:01]:
Well your H2 hundreds, your Blackwells, throw them out, I'll take them. I put them right here for my little personal club. That's what I'm really going for.
Steve Gibson [02:44:10]:
In the winter. It is cold up there in the attic. Ask a couple heater, ask a couple like what is, what is the meaning of 42? And that'll heat up the attic in no time.
Leo Laporte [02:44:23]:
That's what the mice are up to. Steve Gibson is@grc.com that's his website, the Gibson Research Corporation. That's where you will find two fabulous programs. The only two things he asks money for spin, right. The world's best mass storage maintenance, performance enhancing and recovery utility. If you have mass storage SSDs, even Kindles hard drives, you need Spinrite. You'll also find the incredible DNS Benchmark Pro which just came out. A great way to make sure you're getting the best speed you can out of your Internet connection.
Leo Laporte [02:44:58]:
It's really amazing the difference a fast DNS resolver can, can make in your overall browsing. You know, I'll watch Lisa open a webpage and it's no, there it is. And that's just the DNS resolution and that can be sped up by so much. You need Steve's little tool, the DNS Benchmark Pro. All of that GRC. Com. While you're there, go to GRC.com email get your email address whitelisted. Steve does that automatically.
Leo Laporte [02:45:25]:
It's very easy for you, for you to do. You just give them the email address. Reason you might want to do that. Of course you can send him pictures of the week and comments and suggestions. But you can also check those two boxes below. They're unchecked by default, but that add you to Steve's mailing lists. The weekly mailing list with the show notes for this show that come out the day before. Great way to kind of get all the information.
Leo Laporte [02:45:46]:
Steve puts links in there and graphs and charts and of course all the text. And then he also has an mailing list which he still doesn't use that he will let you know when new sufferers comes out. Someday you may get an email from that. Might as well check the box. GRC.com email There are great forums there. Another way to give Steve feedback and to talk with other Security now fans. Of course we have our own forums. TWiT TV has forums at Twit Community.
Leo Laporte [02:46:11]:
We also have our own Mastodon instance at Twit Social. We'd love to see you there as well. What else? Oh, Steve has the show, of course. He's got all the uni. All his versions are one of a kind, unique. He's got a 16 kilobit version of the show. So small that it sounds like we're in a tunnel, but, but it's small. That's, it's, that's its real virtue.
Leo Laporte [02:46:35]:
There's also a larger, but not as large as our 64 kilobit audio. That sounds great. He also has the show notes there. You can download them from the link there. He also has transcripts written by a human, not an AI. Elaine Ferris does great job with those. Those are up a couple of days after the show. And of course he has the shows themselves.
Leo Laporte [02:46:54]:
He only has the audio. We have audio and video, 128 kilobit audio and video at our website, Twitter TV SN. There is a YouTube channel dedicated to Security Now. So if you want to share clips, a lot of people, you know, say I kind of got to tell the boss about that or my friends about that. You can just clip it on YouTube. Makes it very easy for them to see because Everybody can watch YouTube, right? And then of course you can subscribe in your favorite podcast client, get it automatically, audio or video as soon as we're done. As soon as Bonito chops it up into little pieces and reassembles it like Frankenstein. Do leave us a five star review by the way, if you, you know, subscribe in a podcast client and it has reviews, that really helps spread the word about Security Now.
Leo Laporte [02:47:37]:
And I think anybody listens to this show will agree this is kind of a must listen for anybody in the security field, the IT field Anybody who works with technology, you gotta keep up on this stuff. We do stream the show live while we're doing it if you really want the freshest version. I don't know if you do, but if you do, you can go watch us. Well, club members can watch in the club Twit Discord, but we also put it up on YouTube, Twitch, X dot com, Facebook and LinkedIn and Kik. Six different platforms. That is every Tuesday right after Mac break weekly. Theoretically 1:30. Or I should say I'm going to start doing 24 hour clock now because I got tired of PM.
Steve Gibson [02:48:18]:
AM.
Leo Laporte [02:48:19]:
I can't wait. You know, I realize we're seeing 1:30 o' clock post meridian. What the hell is that? That's like medieval sorcerer language. How about this? 1330. We're also at 1630 on the east coast in Eastern time. Best one though. You really should just. Everybody should be just using UTC and then you would know that is exactly 2130 UTC.
Leo Laporte [02:48:44]:
You can make the conversion yourself on any of those streams. Steve. Have a wonderful week. I'm gonna go watch episode four of the Lazarus Project. I'll see you right here.
Steve Gibson [02:48:54]:
It really ramps up. It's. It really. It really ramps up.
Leo Laporte [02:48:58]:
See you here next.
Steve Gibson [02:48:59]:
Okay, buddy, thanks, Bye.
Leo Laporte [02:49:05]:
Security now.