Security Now 1036 transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show.
0:00:00 - Leo Laporte
It's time for Security Now. Steve Gibson is here. He's decided to change his browser of choice. He'll explain why. We'll also talk a little retraction. Passkeys are still secure. Fido's passkey was not bypassed by a man in the middle. And then we're going to take a look, a deeper look, at that SharePoint zero day. What a nightmare. All that and more coming up next on Security. Now Podcasts you love.
0:00:30 - Steve Gibson
From people you trust.
0:00:33 - Leo Laporte
This is Twit. This is Security Now with Steve Gibson, episode 1036, recorded Tuesday, july 29th. Gibson. Episode 1036, recorded Tuesday, july 29th 2025, inside the SharePoint Zero Day. It's time for security now. Oh, I know you're so excited. I see people jumping up and down. We wait all week for Tuesday and the arrival of it's the Santa Claus of security, mr Steve Gibson.
0:01:04 - Steve Gibson
No beard but a very nice mustache uh, hello, steve, people are jumping up and down. I think that's the vertical hold. Remember those days, leo.
0:01:14 - Leo Laporte
Oh yeah, you try to see between the lines on the encoded channels. You go what's?
0:01:17 - Steve Gibson
going well. You had knobs on your tv and you had and, and, and those. Those tweaked the frequency of oscillators which caused the, the, the cathode ray tube beam sweep frequency to change so that it had to line up with what was being sent from central headquarters.
0:01:37 - Leo Laporte
Can you imagine being married to Steve Gibson and you're trying to get the TV to work and he says well, you know, it's the oscillator that needs to line up in there. Oh, yeah, yeah, you know it's the oscillator that he's to line up in there. Oh yeah, yeah, you know it's funny somebody's been uploading. I'm thrilled these old screensaver shows you and I did back in 25 years.
0:01:53 - Steve Gibson
I have every one of them maybe it's you.
0:01:56 - Leo Laporte
Uh, you have them. Oh, the ones that you were on, you have, but there are. There are literally hundreds and hundreds of yeah, somebody must have put them on vhs. I know because I'll watch them on YouTube and you see the scan or the bottom of the screen isn't quite locking in anymore.
0:02:12 - Steve Gibson
Yeah, yeah.
0:02:13 - Leo Laporte
You can know immediately. Oh yeah, I remember that from the bad old days. All right, what's coming up on security now, today?
0:02:20 - Steve Gibson
So for episode 1036, for this last podcast of July of 2025, we're going to talk about a mess.
0:02:32 - Leo Laporte
Of course, what else?
0:02:34 - Steve Gibson
It's a complicated mess which most of the press hasn't quite locked onto, Locked on to. They haven't grokked it fully, because this actually is a descendant of something we talked about in May. Remember that in May was the first relocated Pwn2Own competition. Normally, it has traditionally been held in Toronto every year. This was the first time that Pwn2Own had moved to Berlin.
One of the winners, who earned himself $100,000 in Berlin's Pwn2Own in May, revealed a remote code execution exploit in Microsoft's SharePoint servers which, oh my God you know, there's 38,000 of them, I think, online at the moment. And so this is not SharePoint in the cloud, where Microsoft is trying to push everyone because, of course, they would love to have a subscription from everybody, but these are people who have previously, before Microsoft, decided they wanted to get everyone to subscribe to. Everything would sell you a server. And so there's SharePoint 2013 and 15 and 16 and 19. And they're just doing fine, installed in enterprises everywhere. Unfortunately, it turns out they all have a very bad bug which Microsoft tried and failed to fix in this month's Patch Tuesday. Oh boy, they bungled the update once again, patching the symptom, not the cause.
0:04:30 - Leo Laporte
That's an AI thing. I bet they did an AI patch.
0:04:33 - Steve Gibson
That's exactly what AI would do Well you wouldn't take AI, because we know they were doing this years ago, before AI. They just don't really care. Is what it really looks like. It's like oh look, you do this and this happens. So let's put a little jump instruction in there or something, so they're not fixing the underlying problem, they're just making what the security guy showed them in the proof of concept could happen. Stop happening. Anyway, oh Leo, what a mess. At least 400 enterprises have been compromised. It's got to be more than that.
0:05:14 - Leo Laporte
Some of the government even.
0:05:15 - Steve Gibson
Yes, anyway. So the good news is much. As I've just said, there's a lot more to say, so we'll be getting to that. We're going to talk about the Brave browser randomizing fingerprints. The Brave, the next version of the Brave browser, blocking Microsoft recall by default. I saw that. In keeping with its you know its approach Clorox you know the famous bleach company. They are suing their IT provider for whoa $380 million in damages. What Uh-huh. And we're going to talk about the backstory there. We also have that six-month offer for Windows 10 users to extend their security patches. Those offers are beginning to appear. Some interesting stories demonstrating that warfare has really significantly turned to cyber. The Alliance Insurance Company, alliance Life, has lost control of 125 million of its customers' data.
0:06:25 - Leo Laporte
That's almost all of them, and by the way, I'm one of their customers, so I'm thrilled about this.
0:06:31 - Steve Gibson
And was it they who waited a year? I don't know. We got a lot to talk about here. We also had the CIA's Acquisition Research Center website being hacked, and I think I know how, but the Pentagon says that the SharePoint RCE didn't get them, although again, the gal Katie I think her name is didn't seem to quite understand what exactly happened here, because she's like oh, don't worry about it of a DPRK, you know, north Korea laptop farm, which is being used to impersonate Americans. Turns out that Fido's passkey was not bypassed by a man in the middle.
0:07:13 - Leo Laporte
Excellent, as we reported it was last week.
0:07:15 - Steve Gibson
Good news All right and I raised the question is our data safe anywhere? No, I'm coming to think. No, it's just. You know, I don't want to give up, but still, uh, the uk is now trying to backpedal out of apple's adp mess that it got itself into. Meanwhile, the eu resumes its push for what's called chat control. Uh, and then we're going to take a deep dive into what happened after Microsoft fumbled its patch of this very powerful, pwned to own discovered exploit. So lots to talk about, and we've got, I think, a picture of the week that a lot of our listeners are going to get a kick out of. I know that it rang true for me, so I think maybe, leo, this time we finally got the hang of how to do this pod 1036 episodes later, we finally figured it out.
0:08:14 - Leo Laporte
We're gonna maybe we're gonna have a good one. Yeah, I'll tell you, I have not looked at the picture of the week. You will get my raw, unadulterated reaction.
0:08:21 - Steve Gibson
You're gonna, you're gonna this, this is gonna. You're gonna go, uh-huh, you're gonna get it. Hey, thanks to is gonna.
0:08:25 - Leo Laporte
You're gonna go, uh-huh, you're gonna get it hey, thanks to adam puckett, who just shared a little bit of uh, filthy lucre 10 bucks. Thank you, adam, I appreciate it. In our youtube chat we are streaming live, as adam knows, on youtube and xcom and tiktok and facebook and linkedin and kick your favorite kick and of course, in our club, twit Discord. So if you're watching live, we'll see you in the chat room. We're glad you're here, we appreciate it. Our show today, brought to you by the Thinkst Canary, in fact, I can show you.
This is the cute little device. It looks about the size of I don't know. It's about as big as my hand. It's like an external USB drive, but this thing simple connection, just an Ethernet port and a power connection. This thing, though, could be almost anything. It is a honeypot that can impersonate just about anything, and the thing is that's great it doesn't look like some sort of vulnerability to a hacker in your network. It looks like it's super valuable. Thinks canaries are honeypots that could be deployed in minutes. If someone's accessing your allure files or brute forcing your fake internal SSH server fake mind you then thinks canary will immediately tell you you've got a problem, you've got a malicious insider or a bad guy inside your network. No false alerts, just the ones that matter.
Let me show you my configuration page. This is for our Thinks Canary and the one I just showed you. This attic on my studio desk right now is a Windows Server 2019 Office File Share, and when I say that I mean it. It's even got a Mac address tied to Microsoft. It looks, for all intents and purposes, to be a Windows file share. Furthermore, look, I opened some ports. I got an RDP port open. I got a file sharing. I love opening port 139.
That attracts a lot of bad guys, but it doesn't have to stay that. It's so easy to configure and make it be almost anything you want, from IIS to, yes, sharepoint 2010. That should be a nice thing to it. Just turn that on, see what happens. It could be Linux, it could be a Mac OS X file share. It could even for crying out loud, it could even be a skater device of a sofa firewall. It could be a Rockwell Automation PLC. You choose a personality or make a custom personality. You can light it up with all the services in the world, or just pick a few juicy services. Then you just sit back and wait and a bad guy or a malicious insider who's in your network cannot resist it, and the minute they log in, you'll know.
By the way, the other thing Thinks Canaries can do is these trip wires. They call them canary tokens. You can create canary tokens that look just like, well, almost anything A credit card, an API key, a Microsoft Word or Excel document. It could be a WireGuard configuration file. I mean, the sky's the limit. The wonderful thing is, the minute somebody tries to access this, you will immediately get notified. Somebody's trying to use that fake credit card you created. Stick those Canary tokens anywhere on your network, including, by the way, I keep a few in our cloud servers, on our Google Drive and other places because, again, bad guys just can't resist them. They're like candy to the hackers in your network.
It turns out that it takes companies on average 91 days before they realize somebody's in their network. This is the problem. You've got all those great defenses, but how do you know if somebody's penetrated them and is wandering around? Thinks Canary will tell you no false alerts, just the alerts that matter. Visit canarytools. Slash twit.
Some big banks might have hundreds. Maybe I don't. Nobody has thousands, maybe it. Some big banks might have hundreds, maybe I don't, nobody has thousands, maybe. They're on all seven continents, including Antarctica. Apparently they are everywhere in business, in government. They taught for years. They taught governments and companies how to break into computers, so they know exactly how the bad guys think. But also they're security experts and they've made sure that this thing is bulletproof. You're not putting anything vulnerable on your system, you're just putting something that looks valuable, that a hacker cannot resist.
Let's say you want five of them. That's typical for a business our size, small business. You certainly would want one on every network segment. Go to canarytoolstwit. $7,500 a year gets you five Thinks Canaries. You get your own hosted console, you get upgrades, you get support, you get maintenance and, by the way, if you use the code TWIT, t-w-i-t in the how did you hear about us box, you'll also get 10% off, and not just for the first year but for life.
You can always return your Thinks Canaries. They have a two-month money-back guarantee for a full refund. I do have to tell you, during all the years Twit has partnered with Thinks Canary, their refund guarantee has never been claimed. Visit canarytoolstwit, don't forget that offer code Twit. Put it in the how Did you Hear About Us box. And man, you really need these. Go get yourself some, some canarytools slash twit. I'm going to give a new slogan it's the easy way to honeypot. Not a great slogan, but there, it is. Okay, mr g, I'm ready. I will scroll up the picture of the week so I I gave this picture the caption.
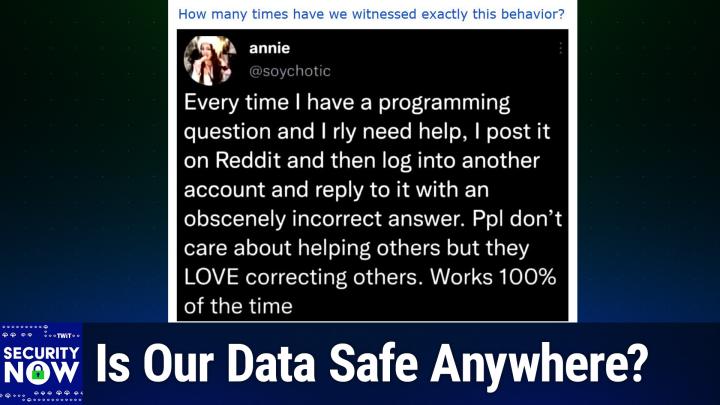
0:14:01 - Steve Gibson
How many times have we witnessed exactly this behavior? Okay, I'm going to scroll up and this will be me seeing it for the first time you read it silently to yourself and then I'll tell everybody it's a, it's like a tweet or something, okay, yeah that's brilliant, isn't it?
0:14:24 - Leo Laporte
and all right, I'll let you describe it so true, so that is so brilliant.
0:14:28 - Steve Gibson
This is a snapshot of a tweet from uh annie uh, whose handle is at uh psychotic which is a great handle.
0:14:36 - Leo Laporte
By the way, she's obviously very creative psychotic so annie posts.
0:14:42 - Steve Gibson
every time I have a programming question and I really need help, I post it on Reddit and then log into another account and reply to it with an obscenely incorrect answer. People don't care about helping others, but they love correcting others. Oh, they do. She said, works 100% of the time and I've seen this happen to somebody. They'll just be like this lonely posting on some programming forum that nobody replies to. It's just their useful question, but nothing happened. Because people, you know, they just look at it and go but, oh boy, you post a wrong answer and there's a everybody piles on. It's a feeding frenzy, correcting this person who doesn't know what they're talking about.
0:15:38 - Leo Laporte
You're going to get the reply.
0:15:39 - Steve Gibson
Guys in spades, yes A little bit of brilliant reverse psychology there is. It's like here's the answer. It's like no that's not right.
0:15:46 - Leo Laporte
Here's what's right. It's like okay.
0:15:48 - Steve Gibson
Okay, all right Thank you.
I already got some great. The email went out to 18,121 people yesterday Jiminy, wow, around this time and a bunch of our listeners replied saying, yep, seen that myself, and I think several of them are going to adopt it now as their standard practice when they're looking for a reply. So, okay, before I forget, as I did last week because this was two weeks ago, I wanted to acknowledge all of our listeners who wrote to let me know that the Brave web browser deliberately randomizes its browser fingerprints, that is, the fingerprints they're using, as reported by EFF's excellent Cover your Tracks online testing facility, which we talked about a couple weeks ago, and disturbed by the fact that, in my case, neither uBlock Origin nor Privacy Badger both which I was using in Firefox were of any help in that regard, we went through all of the bits of significance that the EFF's Cover your Tracks site was able to glean from running script on my browser to lock me down, and I was what One? I was unique among 244 some thousand browsers that they'd seen in the last 45 days. So the Brave browser looks like the right answer for that, and that's a screenshot I have in the show notes. Says blocking tracking ads yes. Blocking invisible trackers yes, I had both of those on Firefox, protecting you from fingerprinting. No, and that's where, for me, it said this browser is unique. So if you're using Brave and you go to the Cover your Tracks site, it says your browser has a randomized fingerprint. So, thanks to our listeners, I wandered over to the Brave browser site to look around and when I saw that the browser natively supports vertical tabs, that clinched the deal for me. I have made the switch to Brave, so we'll see how that goes.
I've I'm not nearly as fickle as paul thurot, who changes browsers, you know, as often as he changes his pants, uh, but I I don't. I've been using firefox forever, as our listeners know. I'm now using Brave, so I've been very impressed with everything I've seen. One thing that I immediately checked was one of my enduring annoyances with Firefox. Which on Windows? Is it 10 or 7? I'm not sure which, maybe both. Anyway, it has this ridiculous refusal to allow me to simply drag a URL from the browser's URL bar into a Windows Explorer folder or to the desktop. I know that it won't let me do it under Windows 10. I'm not sure about Windows 7.
Day before, on Saturday, I needed to save some URLs, so I was forced to copy the URL from Firefox over into Chrome, paste the URL into Chrome, then drag and drop the URL from Chrome into Explorer, then drag and drop the URL from Chrome into Explorer, which Chrome allows me to do. And I understand this is a security measure, but, guys, please allow me to turn it off if it's interfering with my workflow as it continually does. I've looked into disabling this nonsense. There is a way. Mozilla knows about this. There's a way to turn that off. It's supposed to be able you're supposed to be able to append to the command line that launches Firefox the option hyphen, hyphen, no, hyphen de-elevate, because what's happening is Firefox's authorization, its security privileges, are being deliberately de-elevated to protect the user from things that the browser might try to do if something malicious gets a hold of it. It doesn't work for me, apparently, because there's also some interaction with my desktop's UAC settings. I'm sometimes annoyed by the URL of a page that I'm at into a folder, and neither Chrome nor Brave similarly harassed me. So I imported my Firefox settings into Brave. That worked flawlessly. It allowed me to turn off the unnecessary title bar up at the top. Of course, I had to reauthenticate to Bitwarden and re-log into a few different sites, but I'm up and running now with Brave and I'm happy. So anyway, the more time I spent looking around Brave's site, the more impressed I was about their philosophy and their approach. And boy, if you look at the list of things that they tweak from the Chromium which Google uses, they've done a lot in order to brave eyes, the common open source Chromium browser template. So anyway, I'm liking a lot so far and, by pure coincidence, a piece of welcome news regarding the Brave browser surfaced last week. I'm sure I would have shared it with everybody, even if I hadn't become a Brave user myself.
Anyone who might have been curious about Brave's stance on Microsoft Recall would have their curiosity satisfied by the headline which read Brave blocks Microsoft Recall by default. They wrote, starting with version 1.81, and the world is currently at 1.80. That's what I have under Windows 10. So, starting with version 1.81 for Windows users. So it'll be the next update Brave browser will block Microsoft recall from automatically taking screenshots, they wrote, of your browser activity and privacy advocates Recall saved full screen screenshots every few seconds and stored them in a local plain text database, leaving it open for exploitation by anyone, including malware, who had access to the machine.
The outcry caused Microsoft to hastily roll back the feature and rework it significantly. A year later, rec recall is back and Brave is ready for it. We will disable it by default for Windows 11 and beyond users, with a toggle to turn it back on. For users who really want recall, microsoft has to their credit, they wrote made several security and privacy positive changes to recall in response to concerns. Still, the feature is in preview and Microsoft plans to roll it out more widely soon. What exactly the feature will look like when it's fully released to all Windows 11 users is still up in the air, but the initial tone-deaf announcement does not inspire confidence, given Brave's focus on privacy-maximizing defaults.
And what is at stake here? They said your entire browsing history. We have proactively disabled recall for all Brave tabs. We think it's vital that your browsing activity on brave does not accidentally end up in a persistent database which is especially ripe for abuse in high privacy sensitive cases such as intimate partner violence. Wow, okay, they said. Microsoft has said that private browsing windows on browsers will not be saved as snapshots. We've extended that logic to apply to all Brave browser windows. We tell the operating system that every Brave tab is just astonishing. I mean, it scrolls, it's just all these things they've done. Technical details see the GitHub issue for this feature.
Brave is the only major web browser that disables Microsoft Recall by default in all tabs. And they finished by saying we were partly inspired by Signal's blocking of Recall. Given that Windows does not let non-browser apps granularly disable Recall, signal cleverly uses the DRM flag on their app to disable all screenshots. This breaks recall, but unfortunately also breaks the ability to take any screenshots, including by legitimate accessibility software like screen readers. Brave's approach does not have this limitation. Since we're able to granularly disable just recall, regular screenshotting will still work, they said. While it's heartening that Microsoft recognizes that web browsers are especially privacy-sensitive applications, we hope they offer the same. I'm sorry, we hope they offer the same granular ability to turn off recall to all privacy minded application developers. So you know, I don't know if I coined the, the phrase, the, the phrase which I'm now pointing at. What could possibly go wrong? No, the tyranny of the default, the tyranny of the default.
0:26:54 - Leo Laporte
You did not coin that. That's been around for a while, yeah.
0:26:57 - Steve Gibson
Anyway, wonderful, I've been saying it for at least 20 years because it occurred to me. Well, maybe you did then I may have, because it has been. It was one of our, maybe it was. You know, tno trust no one but but you know, Mulder did have that on his poster on the down in the basement of the X-Files, so I think that I probably picked that one up from from Give, give the X-Files credit.
Yes, exactly. Anyway, we know the defaults matter and I have little doubt that Brave browser users will be glad to know that, regardless of anything else that might be going on, Microsoft Recall will not be able to snoop into their browser windows unless they explicitly choose to permit it. You know all these things that Brave does. They're just defaults, so you can. If that's too much for you, you can back Brave away from that. Anyway, I sort of have a good feeling about this. I feel a little self-conscious and kind of like I'm abandoning Firefox because I want to support Mozilla, but I like what Brave's doing, and so I'm there now and we'll see how long that lasts.
0:28:09 - Leo Laporte
Good, I think you did coin tyranny of default. If you, if you coined that 20 years ago, I think you get credit.
0:28:16 - Steve Gibson
We've been using it, I think, for the duration of the podcast.
0:28:18 - Leo Laporte
Okay, wow, I'm going to give you credit from now on.
0:28:22 - Steve Gibson
I apologize, so get this. In the wake of a whopping $380 million damages lawsuit being brought by the famous bleach maker Clorox against its IT provider, cognizant IT provider cognizant, it's foreseeable that future IT contracts will be adding some sort of maximum damages clause to their boilerplate. Because, wow, $380 million. Here's what Reuters, the Reuters news service, wrote. Under their headline Clorox accuses IT provider in lawsuit of giving hackers employee passwords. So they're saying that their provider was giving out Clorox's employee passwords. They wrote. Bleachmaker Clorox said Tuesday, that's a week ago, that it has sued information technology provider Cognizant over a devastating 2023 cyber attack, alleging that hackers gained access by simply asking the tech company's staff for its employees' passwords.
0:29:43 - Leo Laporte
Hey, they were just trying to be helpful.
0:29:45 - Steve Gibson
That's right. We wouldn't want you to get locked out of your accounts now, would we? Clorox was one of several major companies they added, hit in August of 2023 by the hacking group dubbed Scattered Spider and we'll be hearing about them a lot during this next couple hours which specializes in tricking IT help desks into handing over credentials and then using that access to lock them up for ransom. The group is often described that is Scattered Spider of unusually sophisticated and persistent, but in a of being unusually sophisticated and persistent, but in a case filed in California state court last Tuesday, clorox said one of Scattered Spider's hackers was able to repeatedly steal employees' passwords simply by asking for them Repeatedly, repeatedly, repeatedly.
0:30:49 - Leo Laporte
Yes, employees passwords simply by asking for them repeatedly, repeatedly, repeatedly.
0:30:51 - Steve Gibson
Yes, according to. That's not good. According to a copy of the lawsuit reviewed by reuters, quote cognizant was not duped by any elaborate ploy or sophisticated hacking techniques. The cyber criminal just called the Cognizant service desk, asked for credentials to access Clorox's network and Cognizant handed the credentials over unquote. Now, in an email statement, because Reuters said to Cognizant what? Because Reuters said to Cognizant what, cognizant pushed back, saying it did not manage cybersecurity for Cloroxognizant for a narrow scope of help desk services, which Cognizant reasonably performed unquote. Now I'll leave it as a question for our listeners why, if that's true, did Cognizant have the ability to give out Clorox employee authentication credentials? Anyway, reuter says three partial transcripts included in the lawsuit obtained by Reuters allege conversations between the hacker and Cognizant support staff in which the intruder asks to have passwords reset and the support staff complies without verifying who they're talking to, for example by quizzing them on their employee identification number or even their manager's name. Like quote I don't have a password, so I can't connect. The hacker says in one call. The agent replies oh, okay, okay, so let me provide the password to you. Okay, do not hire these people or do not give them access to your company's authentication.
Maxie Reynolds, a security expert who has specialized in social engineering and is not a party to the case, said, quote the apparent ease with which the hackers got what they wanted wasn't necessarily an indication that they weren't skilled. They just tried what typically works unquote. She said the full transcripts were needed to offer a full and fair evaluation of what happened in 2023, but said that, quote if all they had to do was call and ask straight out, that's not even social engineering and it is negligence. Non-fulfillment of duty unquote. Unfulfillment of duty unquote. The lawsuit said, wrote Reuters, that the 2023 hack at Clorox caused $830 million in damages, about $50 million of which was tied to remedial costs. That might have been them paying the ransom, if there was one, or maybe just restoring from backup, but how could that be $50 million? And they said the rest attributable to Clorox's inability to ship products to retailers in the wake of the hack. That's not good.
That's not good. So they're saying 50 million in remedial costs and 330 million in lost revenue as a consequence of the downtime Clorox said. The cleanup, which Clorox would know all about, cleanup right was hampered by other failures by Cognizant staff, including failure to deactivate certain accounts or properly restore data. So it does sound like if Cognizant was in charge of restoring data again, not just help desk stuff. So it should be noted that Clorox is asking for. The fact that they're asking for $380 million in compensatory damages does not mean that's what they're going to receive from a court or a jury trial. You rarely do you get more than you ask for. However, just looking at Reuters reporting of this, I am, as I've made clear as already, immediately skeptical of Cognizant's rebuttal. Skeptical of Cognizant's rebuttal. If, as they claim, they were only hired to perform limited help desk services, how did they have access to Clorox's network and the ability to reset employee passwords at will? Those limited help desk services don't appear to have prevented that. So, anyway, my feeling is, with the ability, the capability to arbitrarily reset Clorox employee passwords, comes responsibility to do so with the proper oversight, which doesn't seem to be the case. What we clearly appear to have here is a case of outsourcing gone awry.
Outsourcing, as we now know everyone has seen this right is the new 21st century business model. It's the idea of hiring for the services you need rather than growing them yourself in-house. It's got a name it's formally called BPO business process outsourcing. It's now an industry and frankly, I'm not a fan. I understand the promise of agility and scalability. Today's startups typically are a small group of people with a bunch of contracts for the services that they need.
But what about a company like Clorox? Really, surely they could afford to operate and manage in-house IT services, but they've been around forever, so I would wager they once did. Certainly they once did their own IT right. They could afford to operate and manage in-house IT services and they must have once. I would bet that some pencil-necked C-suite executive got greedy and decided to trim the fat and demonstrate how they could shave what half the cost of running IT in-house, and they may have reduced their IT operating overhead by half, who knows, right up until it cost them $380 million. So it's easy to point fingers at some lame IT contractor and it certainly is worth asking why Cognizant, who doesn't appear to have been quite cognizant, were ever given the opportunity to screw up so badly. But in this business you get what you pay for, and I'm not going to shed too big a tear for Clorox. You know they clearly set themselves up for this and but again, having you know outsourcing this means you know you get what you ask for.
Leo, before we began recording I think it's before we began, I guess we were live but weren't recording I was talking with you a little bit about the fact that for all of this year my wife and I have been involved in remodeling a home a home. I've had much more contact as a consequence of that with what has happened in the world to support. Where you need to call somebody to get some help with something, you need to widen this ship or where is this or that. It's really we're in a sad state of decline, but Steve, let's be fair.
0:39:06 - Leo Laporte
Did you outsource the plumbing?
0:39:09 - Steve Gibson
no, actually I haven't. You did all the plumbing yourself oh okay, that's true.
0:39:14 - Leo Laporte
Uh, did you outsource?
0:39:16 - Steve Gibson
the carpentry.
0:39:19 - Leo Laporte
The thing is it's not that the outsourcing is inherently bad. We outsource our it because we're too small a company to have an IT department and Russell has much more expertise, even though we're a technology company, than anybody in the company. They just hired the wrong company. I don't think it's necessarily bad to outsource. I think that's actually often the best way to go if you don't have the expertise. Often the best way to go if you don't have the expertise, and especially in tech, because there's such a land rush for skilled technologists these days. It's pretty hard to to build your own it department in a lot of companies because they can't afford these people.
0:39:58 - Steve Gibson
So maybe the problem is just that they didn't hire the right well, that's clearly the problem, right, you know, or, and who knows, maybe cognizant got so busy. They, they, they had to grow, they trained their people.
0:40:13 - Leo Laporte
That's pretty clear.
0:40:14 - Steve Gibson
Yeah, yeah, that's what really happened, so and I think, I think many of their people sit in front of a screen and a screen pops up and they just push some buttons. You know they're so there's. There's no sense of loyalty there, there's no connection. They don't know. You know who?
0:40:30 - Leo Laporte
yeah, but just because somebody is paid by clorox doesn't make them loyal or effective, I gotta point out. So I mean, I think this could happen internally as well as externally. Um, I think just poor training on cognizant's part, and I think they are on the hook, as they should be, for this.
0:40:49 - Steve Gibson
Yeah, yeah, there needs to be accountability. Let's take a break, and then we're going to talk about the beginning rollout of Windows 10 ESU, the way Microsoft found of not terminating security updates this coming October.
0:41:09 - Leo Laporte
Yeah, let's hope Microsoft isn't. Maybe they should outsource their security, maybe that somebody else would do a better job? You never thought of that. You ever think of that? Our show today brought to you by, I'll tell you what this would be a company everybody could benefit from a threat locker. I am a big fan of threat locker. They do what we call zero trust, right. Ransomware is just killing businesses worldwide. Right? Threat locker can prevent you literally prevent you from becoming the next victim, regardless of how smart the bad guys are or what technologies they're using, even if they're using AI.
Threatlocker's zero trust platform takes a proactive and these are the three words you need to know, the most important three words deny by default. Deny by default. The tyranny of the default right. Deny by default approach. That's what zero trust is all about. It blocks every unauthorized action. If you didn't say they can do that, they can't do it. That protects you from both known and unknown threats. Zero days right, because you didn't say, yeah, zero day, go ahead, hack my system. No, so the zero day just gets stopped. Cold, trusted by global enterprises like JetBlue, companies that can't afford to go down, not for one minute, by infrastructure companies like the Port of Vancouver Ransomware takes them out of commission for a day. Everybody suffers. That's why they use ThreatLocker. Threatlocker shields you and them from zero-day exploits and supply chain attacks. By the way, this is kind of a side effect of zero trust, providing complete audit trails for compliance, because you know exactly who did what when.
Right as more cyber criminals turn to malvertising are you familiar with that term? You are, if you listen to this show. You need more than just the traditional security tools Attackers. They're creating very convincing fake websites impersonating popular brands like AI tools and software applications and then distributing it through ads. Because these ad companies, they don't check right, it's all automated. So social media ads hijacked accounts. Then they use the legitimate ad networks to deliver the malware affecting anyone who browses on work systems. Traditional security tools often miss those attacks because the attacks use fileless payloads. They run completely in memory. They exploit trusted services that bypass typical filters, but guess what? They can't get through ThreatLocker. Threatlockerers, innovative ring fencing technology, strengthens endpoint defense by controlling which applications which scripts can access or execute containing potential threats. Even if malicious ads successfully reach the device, they can't do anything of this.
Threat locker works across all industries and supports Mac environments. They've got very good 24-7, us-based support. You get completely comprehensive visibility and control and, by the way, they don't put this in the ad, but I will tell you. Go check the website Very affordable. Every company needs to know about ThreatLocker.
Jack Senesap, who is the director of IT infrastructure and security at Redner's Markets maybe you shop there says quote when it comes to Threat Locker, the team stands by their product. Threat Locker's onboarding phase was a very good experience and they were very hands-on. Threat Locker was able to help me and guide me to where I am in our environment today. He's not the only one. I hear this from every customer Get unprecedented protection quickly, easily, yes, and cost-effectively with ThreatLocker. Visit ThreatLockercom slash twit. You'll get a free 30-day trial and learn more about how ThreatLocker can help mitigate unknown threats and ensure compliance. That's ThreatLockercom slash twit. Thank you so much for supporting Steve and security now. Thank you, threat Locker. I think we're going to try to get out there this spring for Zero Trust World. I think it would be a lot of fun to go out there.
0:45:17 - Steve Gibson
Anyway, on we go with the show, steve. So we talked about this recently and last Tuesday Windows 10 end users will have begun, according to Microsoft, seeing the notices we talked about before. So here's what Microsoft posted about this last Tuesday. They said from modern security to faster performance and the latest features and experiences, windows 11 is built to help you work, play and create with ease. With support for Windows 10, ending on October 14th 2025,. We're here to ensure your transition is smooth, secure and up-to-date. In other words, you need to be moving to Windows 11. However, of course, as we know, half the world hasn't yet and shows no interest in doing so. Microsoft said we understand that moving to a new PC can take time and we're here to support you throughout the process. Windows 10 Extended Security Updates that's, the ESU program is designed to keep your current Windows 10 PC protected after support ends, helping you stay secure during the transition. Starting today, individuals will begin to see an enrollment wizard through notifications and in settings, making it simple to select the best option for you and enroll in ESU directly from your personal Windows 10 PC. Okay, well, I've seen no sign of it so far.
Six days after that announcement, I went poking around in Windows 10, which has been fully updated, looking for any sign of this ESU offer. I couldn't find it Nowhere in settings. I hadn't received any notifications. So you know it's in rollout mode. I did check. I don't have one of the fancy MSDN long-term servicing versions, it's just Win 10 Pro or Enterprise rather, so it doesn't have all the extra Win 10 nonsense. So I would expect that people are going to begin to see this and we'll have the option for moving forward. Now maybe Enterprise, having just said said that maybe enterprise won't be getting that, because they'll be presuming that an enterprise version is part of an enterprise, even though I'm not hooked into active directory or anything. Anyway, uh, for what it's worth, that'll begin happening. And, as we know, I think you need what was it? 1900 Bing points. Anyway, I had more Bing points than I needed, so I qualified for six months of extended updates. Or if you let Microsoft back back your system up, back your system settings up into the cloud, then you qualify that way too. Basically, they're trying to give it away without looking like they're giving it away. So, uh, you know again, six months of free updates for win 10 and you get to stay there and after that, probably zero patch is the way people will be able to continue to stay secure even after Microsoft finally says if indeed they do ever finally say that OK, enough is enough and we're not giving you anything more. We'll see.
The following story appeared last Friday in the online news publication RBC Ukraine. Now, while we might expect there to be some nationalistic bias in their reporting of the facts, the facts reported do line up with that from other sources. Their headline was Cyber Blast in Crimea blast in Crimea. Ukrainian intelligence crashes, russian occupation servers. And I wanted to share this because obviously there's just no longer any question whether Russia and Ukraine are at war. You know it's no longer. What was that? A limited military experiment, or whatever it was?
0:49:45 - Leo Laporte
It hasn't been that for quite some time.
0:49:46 - Steve Gibson
Yeah, yeah. So this story shows just how cyber today's modern warfare has become. Rbc Ukraine reported cyber specialists from Ukraine's Defense Intelligence, which is abbreviated HUR, have carried out a large-scale special operation targeting the occupation authorities in Crimea. According to a Ukrainian intelligence source speaking to RBC Ukraine, the operation lasted several days. A powerful DDoS attack effectively paralyzed the information systems and network infrastructure in Crimea. Now that lines up with what we know of Ukraine's offensive cyber capabilities. They previously demonstrated a number of times that they have the capability to launch and sustain significant DDoS attacks against their adversaries. The article continues writing.
While the Russian occupiers were scrambling to identify the cause of the government system's failure, ukraine's cyber experts I'm pretty much sure. I have a feeling they knew the cause. Ukraine's cyber experts infiltrated the electronic accounts of the leadership of the occupation administration in temporarily occupied crimea. Okay, well, they've obviously spitting the facts here, but okay. They gained access to the following digital resources the electronic document management system, dialogue, theed and Dello, and accounting platforms 1C, document Flow, directum and Atlas to the occupation authorities of the peninsula were downloaded. Among the files were top-secret documents containing data on military facilities and logistics routes used to supply occupying forces in Crimea. A Ukrainian source said, there's so much data extracted that we're about to learn a lot of explosive details about the operations and crimes of Russian occupiers in Ukrainian Crimea. After copying all available information, ukraine's cyber specialists wiped all data stored on the servers of regional and district government bodies, ministries and agencies of the Occupation Administration in Crimea and agencies of the Occupation Administration in Crimea.
The successful Ukrainian hacker operation did not go unnoticed in Moscow. Russia's state Duma has already labeled it an element of hybrid warfare, meaning the so-called Ministry of Internal Policy, information and Communications of Crimea stated that quote technical specialists are taking all necessary steps to restore services. However, some services may remain unavailable to users. Notably, earlier this month, ukraine's cyber specialists targeted the Russian company Gascar Integration, one of the largest suppliers of drones for the Russian army. In June, ukrainian hackers also attacked one of Siberia's largest internet providers, orion Telecom, and earlier RBC Ukraine. Sources reported that Ukrainian intelligence cyber experts hacked into the online system of Russian railways. As a result, the official website of Russian railways went offline. So I encountered another interesting piece of related news, which was that Russia has established free and open Wi-Fi access zones so that their citizenry in Russia could continue to access the internet where cellular services have been discontinued. It turns out that Russia has been forced to shut down large areas of cell phone service because Ukrainian drones were using those services for their navigation services for their navigation. So it's clear from all of this that the battlefield is becoming more and more cyber. Not only is more cyber technology being employed for kinetic military operations, but all nations have become quite dependent upon the convenience created by today's networking for operational management.
The fact that nearly well, apparently more than 100 terabytes of bureaucratic, operational and apparently some military data, some of it apparently marked top secret, were sitting on databases online and internet accessible, would surprise no one today. But that doesn't make it any less irresponsible. You know we've had fun through the years covering proof of concept stories where data was cleverly made to jump to and from air-gapped systems, stuxnet by far being the most famous of those. But the practical truth is, air-gapping is a huge pain in the butt to employ, specifically because it works so well. Disconnecting things like completely disconnecting them works.
It may not be perfect, but it actually doesn't need to be, even if it only drastically limits the bandwidth available to leakage due to operator errors. Even that would be a massive benefit. There's no way anyone is going to exfiltrate 100 terabytes of data from a camera that can see the blinking activity lights on a network router. When we've talked about monitoring the keystrokes of people typing or bouncing a laser off of a balloon in a conference room and reconstructing the audio, well, those hacks and gimmicks work, but they're not high bandwidth. So I get the convenience of everything being connected, but with that convenience comes the liability of it being connected to everybody else and, as you know, what we talk about on this podcast so often, leo, is authentication failure, you know you know, it is?
well it's. It's arguably the hardest thing, right? You know it is. It's what separates the real world from the cyber world. Is the question who am I really talking to?
0:56:50 - Leo Laporte
My name is Steve Gibson. I forgot my password. Could you give it to me? It's just that easy, steve. Oh by golly, no problem. Oh by golly. Oh, we wouldn't want you not to be able to get in there.
0:57:06 - Steve Gibson
no uh right, wow. So while we're on the topic of being able to keep the data we have inside our networks from getting out, tech crunch carried the news of yet another major data breach. And just wait till you who did it and how it happened. Tech crunch, wrote us insurance giant. Alliance life has confirmed. Yes, leo, to tech crunch that hackers stole the personal information of the quote majority almost all of its customers, financial professionals and their employees, which sounds like a complete database breach.
During a mid-July data breach, when reached by TechCr used by Alliance Life, the director was able to obtain personally identifiable data. You know this is like an insurance company right Related to the majority of Alliance Life's customers, financial professionals and select Alliance Life employees using a social engineering technique.
0:58:40 - Leo Laporte
Sound a little bit like Scattered Spider maybe. Uh-huh. Hi, my name is Mr Alliance, Forgot my password.
0:58:45 - Steve Gibson
It's right there in the title my password.
0:58:47 - Leo Laporte
Right there in the title. It's right there in the title yeah, we use them for uh years for our travel insurance, so I'm in their database many times yep.
0:58:59 - Steve Gibson
The company disclosed the data breach on sat Saturday in a legally required filing with Maine's the state of Maine's attorney general, but did not immediately provide a number of how many Alliance Life customers are affected. According to the spokesperson, alliance Life has 1.4 million customers, while its parent company, alliance, has more than 125 million customers worldwide. Allianz Life said it notified the FBI and added it had no evidence that any other systems on its network were compromised. On the other hand, remember that we've also seen companies now telling their IT people don't look, please Don't look for the evidence, because you might have to swear under oath. Wow.
The insurance giant would not say if it had received any communication from the hackers, such as a ransom note. In other words, they're not saying no, they're just not saying the company also would not attribute the breach to a hacking group. Alliance Life is the latest company in the past month to have been hacked during a wave of data breaches targeting the wider insurance industry, including Aflac, a major provider of supplementary health insurance. Security researchers at Google said in June that they were quote aware of multiple intrusions unquote across the insurance sector attributed to Scattered Spider, a collective of hackers and techniques that rely on social engineering, such as deceptively calling and tricking help desks into granting them access to a company's network. Imagine that.
1:00:41 - Leo Laporte
How could that possibly work? Who?
1:00:43 - Steve Gibson
would fall for that, leo. Prior to targeting insurance companies, the scattered spider hackers were seen targeting the UK retail industry as well as the aviation and transportation sectors, and are historically known for hacks targeting Silicon Valley technology giants, for hacks targeting Silicon Valley technology giants. Per the main filing, allianz plans to begin notifying affected individuals around August 1st. So, leo, you can look for the notice in your email sometime later this week or next week. Okay, so let's just step back for a minute here. I have a bit of a rant. Here we are again. As long as I forgot my password and oh, I love this one I don't have my authenticator with me right now remain acceptable options. Remain acceptable options. We're just pretending to have security and we're never going to move past our current online impersonation problems. I mean, really, what is the possible security benefit of even bothering with fancy time-based one-time token identity authentication if, oh, but I don't have it with me right now is acceptable? Really, if you don't have it with you right now, that's just too bad. No login for you. Does that inconvenience you? Good, that's what you asked for, that's what you signed up for, that you might be unable to produce the exact thing that you want. No bad guys to be able to produce. You can't have it both ways. You either have true security, which might mean and it would be on you that you might be inadvertently locked out and be unable to log in when you're unable to meet the requirements you had previously arranged and agreed to. Otherwise, we have the world we're actually living in today. We're all in this world where we're allowed. The only thing available is money, some feel-good security theater using an authentication system which would most fairly be described as optional right With optional authentication. Not being able to produce the required magical six digits on demand simply means that it will be necessary to jump through some additional hoops to get yourself authenticated. That's all. The problem is, the bad guys are more than happy to jump through those same hoops. They wake up every morning in anticipation wondering just how many hoops they're going to be able to jump through today. How many lazy fat Westerners accounts are they going to hack today? But seriously, whenever I see one of those I left my authenticator at home links to click on underneath the authentication prompt I just shake my head. Why even bother with it if you don't need to actually use it?
A cool and underappreciated feature of the Squirrel system was that after its user became comfortable with the system, they understood they'd figured out how it worked. They backed up their single global encrypted identity. They could enable a feature in Squirrel's user interface which requested every website they subsequently logged into with Squirrel. To please, immediately, squirrel, to please immediately, completely and irrevocably disable every alternative login solution and plant a flag in the account to prevent any human agent from ever overriding authentication, no matter what anyone else ever says and no matter how much anyone begs. What anyone else ever says and no matter how much anyone begs. That is what true security looks like, but the world is clearly still not yet ready to take their own security that seriously.
And, leo, when you step back from this, when you think about it, what's the cost of having that level of security? So you forgot your phone with your authenticator, so you can't log in to check your tweets. The world is not going to end. Life is not going to be over as you know it because you're unable to authenticate on some given instance. And the point is you have to not be able to authenticate because if you can, then anybody can, potentially a password manager or an authenticator.
What it really was was really just an accelerator. It made it easier and quicker to authenticate because it provided that stuff. But if you didn't have that stuff, you'd have to jump through a few extra hoops in order to authenticate. Many people you know just say oh, I just forgot my password. They wait for a login link to be emailed to them and then they log in. That way. It's a little slower, but it works just the same. So it ends up being that email is actually the thing that we have to protect. Everything else is just theater. That email is actually the thing that we have to protect. Everything else is just theater. Anyway, again, I see this especially with an authenticator. You say I've added this, I want the extra protection, I want multi-factor authentication, I'm going to do this. And then underneath the authentication is I don't have my authenticator with me right now.
1:07:49 - Leo Laporte
Really, Put it in Bitwarden.
1:07:54 - Steve Gibson
Let's take a break. I have to calm down.
1:07:58 - Leo Laporte
Well, it's good that you're upset, because our sponsor for this segment of Security Now is Bitwarden. Guess what you can put your Now is Bitwarden. Yay, guess what you can put your password in Bitwarden. And you know, we talked about this a few episodes ago. I, for a long time I was reluctant to put the two-factor in Bitwarden. I wanted a separate, you know, two points of failure kind of thing. And you said you know, yeah, I mean theoretically you shouldn it's, but it's fine, these are. This is well secured. And I can't tell you how great it has been to move my two factor codes into bitwarden. Now it auto fills my name, my password and my authentication. It's like a hundred times easier. And the point is, I trust bitwarden, you should trust Bitwarden. Open source encryption done right. Bitwarden is the trusted leader, not just in passwords, not just in authenticator codes, but in pass keys, even in secrets management, including things like SSH keys. I keep my private keys in Bitwarden. In fact, it facilitates that. My API keys I store keys in Bitwarden. In fact, it facilitates that my API keys. I store them in Bitwarden.
Bitwarden's consistently ranked number one in user satisfaction by G2 and software reviews more than 10 million happy users across 180 countries, over 50,000 businesses. That kind of surprised me. I know Bitwarden's great for individuals. I'd kind of surprised me. I know bitwarden's great for individuals. I'd kind of forgotten it's great for enterprise too. You know, we were just talking about the alliance breach breach. That's a lot of customers whose private information, including probably their passwords, are available. More than 19 billion with a b passwords are available. More than 19 billion with a B passwords are available on the dark web right now, which would be fine if you only use that password for one thing. But it turns out 94% 94% of those breached passwords have been reused across multiple accounts. The truth is and I know it probably breaks your heart, Steve, it certainly worries me most people, including most of the people I know, most of the people in my family, don't create new passwords for every account. But you really have to. You do, and Bitwarden makes it so easy. Info Stealer, malware threats we were talking about Info Steelers last week. Last year, sur searched 500% Bad guys are using this stuff because it works. 500%. Modern hackers no longer hack accounts. They log in with weak or reused passwords. If you use strong passwords and you keep them in your Bitwarden, you're a lot safer.
Bitwarden Access Intelligence something new they've just added. It's an enterprise feature that enables enterprises to proactively defend against internal credential risk, because you know your employees are reusing passwords. They're doing all kinds of bad stuff. It also helps protect you against external phishing threats Two ways it does this. Risk Insights allows IT teams to identify, prioritize and remediate at-risk credentials. So if your company's credentials are all stored in Bitwarden, bitwarden will tell the IT team okay, here's some reused ones, here's some problem ones, here's monkey one, two, three. Advanced Phishing Blocker that's another tool will alert and redirect users away from known phishing sites. It does it in real time using a continuously updated open source block list of malicious domains. Now, this is great for enterprise, but even personal users like me benefit from the fact that Bitwarden will not fill in your password on a phishing site. It knows better. It knows better than you do and than I do. It's not fooled.
Passwordless authentication that's the new thing. Today, google announced that they were having problems on Workspace and that they were going to encourage all Workspace users to turn on passkeys. I said Lisa, turn on your passkeys. She said, are they safe? I said yes, lisa, they're safe.
Passwordless authentication is the best way to go and, as always, bitwarden is right at the forefront offering support for pass keys. So all your pass keys are in the Bitwarden vault, which means it's there everywhere. Your Bitwarden is on your phone, on your tablets, on your laptop, everywhere on your computer. It offers support for passkeys and FIDO2 standards to strengthen and simplify the login experience. Bitwarden passkey support includes enhanced passkey support across web, desktop and mobile platforms. Like I said, it enables users to store and sync passkeys, and it's with end-to-end encryption. It'll also support two-step login with FIDO2 and WebAuthn, allowing hardware key authentication as a secondary factor or even a primary message.
That would be a great way to secure everything. Biometric unlock enhancements on mobile and desktop that's a fantastic improvement, ties in perfectly with Bitwarden. I unlock my vault with my fingerprint on my mac, with my face id on my phone, streamlining access without compromising security. In fact, I would say it improves security. An improved autofill experience is now in Bitwarden for passkeys. Cards and identities are designed to work seamlessly across modern browsers and apps. I will also add the two-factor, the one-time passwords. Fantastic. Bitwarden's setup only takes a few minutes. Supports importing from most major password management solutions, so your company can move fast one day.
In most cases, bitwarden's open source code and this is important to me can be inspected by anyone and is regularly audited by third-party experts. I don't use crypto. That's not open source. I want to know is there a backdoor in there? Bitwarden meets SOC 2, type 2, gdpr, hipaa, ccpa compliance. It's ISO 27001-2002 certified, so they check all the boxes. Get started today with Bitwarden's free trial of a Teams or an Enterprise plan, or get started for free across all devices and individual user. Bitwardencom slash twit. That's bitwardencom slash twit Back, mr Gibson, okay so yes, thank you.
1:14:24 - Steve Gibson
The Washington Times last Thursday headline is breach intelligence website used by the CIA.
1:14:32 - Leo Laporte
Oh, boy, you'd think they'd know how to secure their website. Maybe they outsourced it. One would hope that our CIA yeah.
1:14:41 - Steve Gibson
OK, so I'm just going to share the intro of this. Ok, so I'm just going to share the intro of this. They wrote Unidentified hackers recently compromised a major intelligence website used by the CIA and other agencies to submit details of sensitive contracts. According to the National Reconnaissance Office, the spy satellite service that runs the site, the breach targeted proprietary intellectual property and personal information submitted on the Acquisition Research Center website in support of several innovative CIA spying programs. A National Reconnaissance Officer spokesperson told the Washington Times we can confirm that an incident involving our unclassified Acquisition Research Center website is currently being investigated by federal law enforcement. We do not comment on ongoing investigations, especially those that are embarrassing.
The extent of the breach is not fully known, but people familiar with the activity said hackers likely obtained information on key technologies for CIA operations. Other potential areas of compromise could include the Space Force, its efforts to build surveillance satellites and space weapons oh boy and the Golden Dome Missile Defense Program. Data from one highly sensitive program, digital Hammer, was compromised, said people familiar with the hacking. Digital Hammer compiles cutting edge technologies for human intelligence gathering, surveillance and counterintelligence operations. The program focuses on the threat of Chinese intelligence and information operations. The program focuses on the threat of Chinese intelligence and information operations. Anyway, the story continues at some length, so I put a link to the entire piece in the show notes for anyone who's interested in knowing more. It's unclear whether we're going to obtain more reporting on this, given that it's the CIA, but my hunch just based upon the timing of the event and the nature of the breaches that are resulting from the exploitation of Microsoft's recent SharePoint disaster, which we'll be digging into when we get into today's main topic. I would not be surprised to learn that this CIA site, whose role and profile require it to be all about sharing files, might not have been another victim of that recent SharePoint zero-day remote code execution vulnerability. And I should note that this is not. I know this is unusual, but this is not a failure to update problem. Everybody who updated on Patch Tuesday got attacked. So it's not the CIA's fault, as we'll see, but it sure does fit the profile of a SharePoint breach a SharePoint breach. Now the Pentagon, however, says no, they didn't get us Speaking of the SharePoint hack.
Nextgov's headline last Thursday was Pentagon not impacted by Microsoft SharePoint hack, says their tech chief. Nextgov wrote the Department of Defense has not been ensnarled by a broad intrusion into on-premises versions of Microsoft SharePoint, its chief information officer said Thursday, and Cloud Security Summit on Thursday. In a stage interview. Quote as of right now no, not that I'm aware of unquote Arrington said she's been doing daily calls with Microsoft while the department has been conducting forensics investigations since the zero-day vulnerability was publicly identified this past weekend, meaning a weekend ago. Thus far, they wrote, several federal agencies have been impacted, including the Departments of Energy, homeland Security and Education, and up to a dozen federal agencies have been notified of possible compromise by CISA, the Cybersecurity and Infrastructure Security Agency. According to a source familiar, dhs issued a statement that its investigation into the hack remains ongoing but quote there is no evidence of data exfiltration at DHS or any of its components at this time.
Arrington said the latest series of hacks and attempted hacks reiterate the constant threats posed by state actors to US and defense systems. When zero-day vulnerabilities, which have not yet been, which have not been previously uncovered and therefore give developers zero days to patch them not quite the case in this instance, but we'll get there are found, cybersecurity professionals need to act immediately and apply those patches. Well, everybody did in this case, arrington said. Quote Russia, china, iran, north Korea. Are they going to continue? Yes, are they going to look for? Are they going to continue? Yes, are they going to look for any hole they can find? Yes, it's a zero day the day you found out about it.
A patch was made that same day. And how fast we deploy the patches, how fast we work as a unified body. To I say turn the lights on an adversary when they do something. That's how fast resilience will be unquote. Okay, now I have no idea what any of that double speak, mumbo jumbo there at the end was, but, as we know, patches, especially from Microsoft, often take much longer than to quote Katie that same day. But I really wonder, seeing what she said here, is whether Katie is aware that this entire quite serious mess was primarily created because Microsoft botched and fumbled the original Patch Tuesday patch release by, once again, as I said, only patching a symptom and not the underlying cause of the vulnerability.
Anyway, we'll be getting to that shortly. We have our first photo, leo, of a DPRK laptop farm. Now, this was not a farm set up by the DPRK, you know, aka North Korea. Oh no, this was a 50-year-old American woman who was busted. Who was busted? Yeah, I had formed an image, I guess in my mind's eye, when I'd previously discussed and described the so-called laptop farms it's not, doesn't live up to the image, doesn't?
no, no, the tchotchkes hanging from the from from the right metal uh rack, and there's some purses and handbags and things. It's not exactly what.
1:22:07 - Leo Laporte
I was not your high-tech laptop farm, I'm thinking this lady said to her friends I found this great way to make money. It's really easy. They just send me the laptop, so all I have to do is connect it to my internet.
1:22:19 - Steve Gibson
Put them on my Wi-Fi. I had imagined something more glamorous than three metal wire racks containing about 30 assorted random-looking laptops with large fluorescent post-it notes stuck on them. That's probably the password on there, I'm sure. Yeah, exactly. Or to identify which one is which, because you've got to associate them with your fake employees and so forth.
1:22:47 - Leo Laporte
Yeah, anyway I bet she didn't do any of that, though really, all they had to do was give her, give them a us ip address, right?
1:22:54 - Steve Gibson
probably, yeah, yeah. So this is christina marie chapman, recently sentenced to a term of eight and a half years in prison, probably will actually serve less on good behavior for this operation of an illegal North Korean laptop farm, whose purpose was to help North Korean IT workers pass, you know, spoof, being US residents. We've talked about this a number of times. This is an actual serious problem currently in the US. You got to know, talked about this a number of times, this is an actual serious problem currently in the US. You got to know who you're hiring, when you're hiring. You know remote, you know online help as part of your outsourcing.
Altogether, the workers managed to land more than 300 jobs at US companies and generated more than $17 million in revenue for the North Korean regime. And, of course, they're under sanction by the US. So this is all against the law. Us employers are not allowed to be paying North Korean workers anything and you know it's a mistake if they do so. Unfortunately, facilitating that illegal conduct will get you eight and a half years in prison. I wonder if it's like three months per laptop, leo.
1:24:20 - Leo Laporte
I hope she gets to bring her tchotchkes, that's all.
1:24:22 - Steve Gibson
Yeah, that'd be good. Yeah, that'd be good. Okay, so last week I shared a blog posting and a forensic analysis by Expeled to a classic real-time website intercept and forwarding attack. The only way this could have been possible was if it was not necessary for the passkey-equipped FIDO authenticator to communicate with the authenticating user's local desktop browser in real time, because the authenticating user would be the man in the middle and the FIDO authenticator would be in the hands of the unwitting victim. As I noted last week, the nature of this vulnerability is well understood. That's why why, in my case, I had incorporated a squirrel client to browser link using the local host IP on that desktop to allow the user's browser to talk to the system's resident squirrel client resident squirrel client. Now, many of our on-the-ball listeners wrote to say that they were pretty sure that in Fido's cross-device authentication model, this client-to-browser link was not optional and that it must be present, created by Bluetooth, and they are 100% correct. By Bluetooth, and they are 100% correct. Fido explicitly prevents this attack and will not successfully authenticate without a local Bluetooth link between the user's web browser and their cross-device authenticator. Oh, that's smart, which means that what Expel described is impossible. Now, given that the presumably FIDO-based man-in-the-middle attack that Expel Security described having witnessed should not have been possible. It turns out that the attack was not possible and did not happen, at least not as they described they wrote.
On July 17th we published a blog posting covering a recent incident we observed. On further review, we found our original findings are unsupported by the evidence. Oh boy, the original post described a new form of phishing attack that allowed an attacker to circumvent a FIDO passkey protected login, a FIDO passkey protected login. It stated that this attacker used cross-device authentication to successfully authenticate while not in close proximity to the authenticating client device. The evidence does show the targeted user's credentials, their username and password, being phished, and that the attacker successfully passed password authentication for the targeted user. It also shows the user received a QR code from the attacker. This QR code, when scanned by a mobile device, initiates a FIDO cross-device authentication flow which, according to FIDO specification, requires local proximity to the device which generated the QR code, the web auth and client. When properly implemented, but without proximity, the request will time out and fail. So at the time of the original post, they wrote, expel believed the attacker successfully completed the authentication workflow, resulting in access to protected resources.
After discussing these findings with the security community. We understand that this is not accurate. The octalogs show the password factor passing successfully, but all subsequent MFA challenges failed and the attacker is never granted access to the requested resource. So that solves the mystery. I am sure I also once knew that a Bluetooth link was required and not optional for FIDO cross-device authentication, and I'm very glad that's the case. But I got swept up in their report, which I assumed to be correct, and I doubted what I knew. I suppose I also gave away the fact that I'm not a frequent user of FIDO PassKeys cross-device authentication, since anyone who likely deals with the need for Bluetooth linking all the time would be well aware of that requirement, as many of our listeners were. So we've got that figured out and it is very good news, as you've noted, leo, that the device must be in proximity to the browser and that they have to communicate by Bluetooth link.
1:30:02 - Leo Laporte
It just makes sense, it does, yeah, it does.
1:30:07 - Steve Gibson
So, okay, is our data safe anywhere? No, don't you start to get the feeling that our data is not, in fact, safe anywhere and that no one can be trusted to keep anything that we might disclose and often need to disclose, like if we're dealing with hospitals to set up appointments and doctors and so forth? It's just not safe online. So here's another example we can add to the pile and talk about sensitive personal data, personal data TADTS. Those are the initials TADTS of the Alcohol and Drug Testing Service. As their name suggests, they perform drug and alcohol testing and they do so for multiple US states, apparently not being in a great hurry. Perhaps they were waiting for some statute of limitations to expire.
The organization now admits that they were hacked and that those bad hackers stole the highly personal alcohol and drug testing data of three quarters of a million users. 750,000 people had their alcohol and drug testing service data stolen, yep. And, even more gallingly, they waited. The TADTS people waited a full year to disclose this. They became aware of the data breach last July, 9th, 2024, which is why I wonder about some statute of limitations. The organization is only now notifying affected users those three quarters of a million affected users. But don't worry. They're offering free credit monitoring folks to prevent the use of those highly confidential data which they were entrusted with but turned out to be unable to protect a year later.
1:32:29 - Leo Laporte
I just hate it when they do that.
1:32:30 - Steve Gibson
I you know, leo, I have no plans to unplug from the grid and live in a cave. It turns out you were speaking of plumbing earlier. My wife is a huge fan of indoor plumbing. Yes, yes, me too, so I'm with her.
So it doesn't really seem as though the rate at which I mean doesn't it seem as though the rate at which we're losing this battle is accelerating. I mean it's nuts and feel, though, because we've been at this now for 20 years, I feel as though these are chickens coming home to roost. I mean, it does no one any good to say that we told you so. I mean I'm speaking to the ether. I mean our listeners are doing everything they can to be safe. Certainly, they're very security concerned. No one can help it that underneath the authentication link or the authentication field, is a link saying, oh, I don't have my authenticator with me, let's do something else. Okay, we didn't design these systems, but this is the consequence of the fact that security is really not even, has it never been taken seriously. It's still, today, not really being taken seriously. It's considered an inconvenience if someone can't log in.
So we make it very simple. The lowest common denominator is email. If you can get email, then you're okay, and unfortunately that means oftentimes you can say, oh, but I don't have access to my email right now and I have really, really, really, really, really, really, really have to log in. Please, can't you? Oh well, okay, in that case, here's your password. Really, really, really, really, really, really, really have to log in, please, can't you? Oh well, okay, and in that case, here's your password. They literally in one of those examples I didn't share, but it was in the lawsuit they reset the person's password to clorox123.
1:34:41 - Leo Laporte
Oh, that's secure. You're gonna change that as soon as you get home, right.
1:34:47 - Steve Gibson
Yes, but it wasn't monkey. One, two, three. It was Clorox one, two, three, so who could ever guess that?
1:34:55 - Leo Laporte
No, no, never would guess that.
1:35:00 - Steve Gibson
Okay, so thank God we have a bit of good news here. The Financial Times reporting is locked behind a paywall, but many other outlets are reporting on the Financial Times report, the Verge being one of those, wrote. The UK government is reportedly set to back down from its battle with Apple to obtain backdoor access to secure user data protected by the company's cloud encryption. Victory hasn't come through the courts, wrote the Verge, or government figures changing their minds on privacy matters, but thanks to ongoing pressure, it turns out from the US during the two countries' trade talks, turns out JD Vance apparently is not happy with this.
Multiple unnamed UK officials told the Financial Times that the UK government is working on a way out. One of those sources said, quote the home office is basically going to have to back down, adding that Vice President JD Vance was especially opposed to the UK's demand, which may violate the Cloud Act treaty between the two countries. Saying, quote it's a big red line in the US. They don't want us messing with their tech companies. Unquote. Another official. Echoed that, explaining that you know. Echoed that, explaining that the UK wants to avoid pushing too hard for quote anything that looks to the US vice president like a free speech issue unquote. A third official said the UK had quote it's back against the wall and wants a way out. Quote it's a problem of the home office's own making and they're working on a way around it now now.
So this entire Apple advanced data protection mess now appears destined to disappear. Now that's great news, and hopefully politicians and their governments won't put themselves and the rest of the world through many more of these no-win standoff cycles. They need to realize, at least as regards privacy, they cannot simply demand anything they want. The laws of nature are not theirs to establish. There are problems, no doubt about it, arising from the abuse and illegal conduct enabled by the powerful privacy protections created by encryption technology. But stripping privacy from everyone else, that cannot be the solution.
1:37:57 - Leo Laporte
Now, if anybody's going to spy on us citizens, it's going to be us.
1:38:02 - Steve Gibson
Yes, we don't want it. We're jealous of that.
1:38:05 - Leo Laporte
No, it's allowed. It's our job, right yeah?
1:38:10 - Steve Gibson
OK. There is a little bit of cloudiness on the horizon, however, because Denmark is reintroducing chat control. You know how the control of the EU moves around from one EU state to another. Eu Today posted the news under their headline EU reconsiders chat control as Denmark reintroduces controversial encryption scanning bill. They write, known informally as chat control. The proposal has re-emerged under Denmark's EU Council presidency, which began on the 1st of July. Lawmakers are scheduled to debate the latest iteration of the bill on October 14th 2025. Okay, now we can hope that the EU takes note of the egg that the UK has ended up with on its face with reporting that they're now trying to backpedal and oh no, that's really not what we meant to do, because they've gotten themselves in a big mess. The reporting continues.
Originally introduced in 2022, but repeatedly stalled due to political opposition, the legislation seeks to impose obligations on messaging platforms such as WhatsApp, signal and Telegram to scan user content for child sexual abuse material CSAM, abuse material, csam. If adopted, the law could lead to widespread. Now this is interesting that, if adopted, the law could lead to widespread client-side scanning of messages before encryption, a measure that critics argue poses a serious threat to digital privacy and data protection. Okay, now, nobody wants that to happen, but, as I've been noting earlier this year, the solution I can see to this, if we have to have one, is to employ device-side local AI to examine what's being sent. I get it, it's creepy and it's a mess because, for example, parents ought to be able to take photos of their own young children without the police being alerted. But if this must be done, doing it device-side and not messing with encryption backdoors. To me, that's the only way to get there. The article said the Danish presidency has placed the proposal among its top legislative priorities. Yikes been publicly released. Copenhagen has signaled its intention to find a compromise that balances law enforcement's goals with legal and technical concerns raised by member states, civil society and industry stakeholders. Well, good luck with that. Of course, nobody wants to have Big Brother spying on them, even if Big Brother is inside their own phone.
The article said the European Commission originally tabled the regulation in May of 2022, aiming to bolster the detection and reporting of CSAM online. Despite its stated purpose, the proposal was criticized for its scope and method, particularly the inclusion of end-to-end encrypted services in the scanning regime. Attempts to pass the measure under previous presidencies, including Belgium and Poland, so this is a hot potato that keeps getting passed around failed to secure a qualified majority in the council. Belgium proposed a version in June 2024 that restricted scanning to shared media and URLs contingent on user consent. Poland's February 2025 proposal classified scanning as a voluntary preventative action. Though regarded by some experts as an improvement, it, too, failed to gain traction. Denmark now assumes the role of broker, hoping to navigate between longstanding opposition from digital rights advocates and calls from several member states for stronger tools against online exploitation. The Danish presidency's official program states its intention, to quote strengthen the abilities to make use of the digital development for law enforcement when fighting serious crimes, while also addressing the misuse of new technologies. Unquote.
Criticism of the CSAM bill centers on concerns about weakening encryption. Client-side scanning center, central to earlier drafts of the proposal, involves monitoring communications on a user's device before encryption takes place. This method is seen by experts as equivalent to surveillance and is considered by many to be incompatible with the principle of confidentiality of communications enshrined in EU law. In 2023, the European Court of Human Rights issued a ruling that effectively prohibited states from requiring the weakening of secure encryption standards. This legal precedent, while not explicitly blocking the chat control proposal, adds a layer of complexity to its adoption and enforcement. Digital rights organizations and privacy advocates have described the initiative as a disproportionate response to a serious problem. They argue that mandatory scanning mechanisms risk creating vulnerabilities that could be exploited by malicious actors and set a precedent for broader surveillance.
At present, the contents of Denmark's revised proposal remain undisclosed, so we don't know what's going to happen in October when they bring this thing back up for discussion, because again, this hot potato gets passed around from country to country. Now it's in Denmark's lap. Analysts suggest they wrote that the fate of the bill may hinge on Germany's position. The new federal government has not yet indicated whether it would support the measure, and without its backing, a qualified majority may remain out of reach. According to Patrick Breyer, former MEP for the German Pirate Party and a vocal opponent of the proposal, the Danish presidency's success will depend heavily on its ability to secure Germany's approval. Even if the CSAM proposal were adopted in October, it would still need to proceed through trilog negotiations with the European Parliament and Commission where further amendments are likely.
The chat control bill is part of a wider series of initiatives by the EU aimed at giving law enforcement greater access to encrypted data. On June 24th of this year, 2025, the European Commission unveiled the first phase of its ProtectEU strategy, which proposes the development of decryption capabilities by 2030, which sounds ominous. Decryption capabilities what the strategy is still at a conceptual stage, but indicates the long-term policy direction of the European institutions. While efforts to curb the spread of CSAM enjoy broad political support, the methods employed remain contentious. The question facing EU lawmakers is whether security objectives can be met without eroding the privacy rights of European citizens.
As the debate resumes under the Danish presidency, it is clear that any legislative outcome will need to reconcile fundamental rights with the imperatives of public safety, a task that has so far eluded consensus. And, leo, I think it's impossible. Yeah Right, I mean what they're asking for? What they're asking for? Like everybody wants something that crosses a no man's land for the other side. You know they basically they want censorship without censorship, or they want censorship without any violation of privacy rights. They want to see what you're sending, but they don't want surveillance. Well, seeing what you're sending is surveillance.
1:47:08 - Leo Laporte
Right, they don't want surveillance for themselves, right? Which is the thing protecting us, frankly, because I don't think they care about surveillance for us. But yeah, I worry. I mean, governments are forcing these things through. Governments are forcing these things through Already. In the UK, they've got age verification requirements that people are already cracking. I can't wait till next week. I'm sure you'll talk about this. What is the story? They're using images from video games. There's a great website where you can enter in your British zip code and it will give you the driver's license of your member of parliament to use for a fake ID. It's just that's what happens, though. When you create these surveillance societies, you teach people how to get around them, yeah, so let's hope we can get around it, right, yeah?
1:48:08 - Steve Gibson
Okay, we have some listener feedback after we take a break, so I can recaffeinate download your encryption tools today.
1:48:14 - Leo Laporte
Boys and girls, you never know when they're an outlaw. Our show today, brought to you by us cloud love these guys. The number one microsoft unified support replacement, and we've been talking for a long time. One Microsoft Unified Support Replacement, and we've been talking for a long time at least you know, I think six months now about US Cloud. They are the global leader in third-party Microsoft support for enterprises, now supporting 50 of the 5-0 of the Fortune 500. And there's a good reason.
Switching to US Cloud can save your business 30 to 50% over microsoft unified and premier support, but it wouldn't be any good if it were 30 to 50 percent cheaper. It's better, a lot better. Uh, it's faster twice as fast in average time to resolution versus microsoft, and you know when your hair's on fire, the network network's down. The boss is calling. Speed is pretty important. They're also better. I'll explain. And the other thing they could do that I don't think Microsoft will ever do is save you money on Azure. That's not in Microsoft's interest, is it?
Now US Cloud is excited to tell you about a new offering Azure Cost Optimization Services. So let's be honest when was the last time you evaluated your Azure usage Like any other cloud service. If it's been a while, you probably have some Azure sprawl right, a little spend creep going on. Well, there's some good news. Saving on Azure is easier than ever with US Cloud. Us Cloud offers an eight-week Azure engagement. Powered by VBox, it identifies key opportunities to reduce costs across your entire Azure environment and you're going to get and this is the other way US Cloud's great expert guidance, access to US Cloud senior engineers with an average of over 16 years in Microsoft products. And these are the pros right. So at the end of the eight weeks, you're going to get an interactive dashboard. It's going to have very clearly rebuild and downscale opportunities, unused resources, allowing you to reallocate precious IT dollars towards things you really need.
Or and I like this idea. Keep the savings going. Invest your Azure savings in US Cloud's Microsoft support. That's what a few other US Cloud customers do. Completely eliminate your unified spend and the savings just keep on going. Sam is the technical operations manager at Bede Gaming B-E-D-E. He gave US Cloud five stars the highest rating saying we found some things that had been running for three years which no one was checking. These VMs were, I don't know, 10 grand a month not a massive chunk in the grand scheme of how much we spend on Azure, but once you get to 40 or $50,000 a month, it really starts to add up. Yeah, it's simple. Stop overpaying for Azure. Identify and eliminate Azure creep and boost your performance all in eight weeks with US Cloud. It's true. Visit uscloudcom, book a call today to find out how much your team can save. That's uscloudcom to book a call today. Get faster, better Microsoft support for less, a lot less uscloudcom. We thank him so much for supporting security now and the good work Steve's doing here. All right.
1:51:44 - Steve Gibson
Listener feedback time Steve's doing here. All right, let's go back time. Yeah, mike Sanders said. Hello, steve, new subscriber, longtime listener. You've mentioned over the years how you're still using win seven and maybe win 10.
With when 10 soon to go out of support, I wonder if you might consider discussing how you would or would not use Win 10 after October. The tech press seems to view this as a hair on fire event. Perhaps I'm numb to the risks. I have never had any antivirus beyond Defender. To the best of my knowledge, I've never had a virus. I use Firefox pretty much exclusively.
I really do not want to move to Win 11 for a variety of reasons I'm sure I do not need to enumerate. Your views on this topic might be of interest to others who listen. Regards Mike. So Windows 11, I've had some updated experience with it recently is extremely pretty. I set up several dedicated Windows 11 machines at both of my development locations because I expected that I was going to need to spend some time with Windows 11 before I'd be able to final operation was going to drive the benchmark crazy, but to my surprise, the new DNS benchmark code all worked perfectly under Windows 11. In any event, windows 11 was so pretty that for a while, I was a bit seduced by it, but that wore off. I was a bit seduced by it, but that wore off. I've seen too many postings by people asking how they can go back to Windows 10 after making what they come to feel was the mistake of moving to 11. So, since I use Windows as my daily work platform, if I'm able to avoid losing any performance to, you know, rounded corner, animated, zooming and fading windows lovely as they may be, you know and all the other stuff they've added, that really doesn't matter to me. That's what I'm going to do. So I'll be sticking with Windows 10 for the foreseeable future.
And given that I'm still using Windows 7, whose support support ended more than 10 years ago, on January 13th 2015, and that Windows 10 has an even stronger following today than Windows 7 did back then, and that so many machines are compatibility disabled to make the move to Windows 11, I suspect that Windows 10 will refuse to die. I really stubbornly refuse. Having ridden the Windows 7 train, I've seen that at some point in the probably distant future. But eventually the browsers will start refusing to upgrade themselves any longer. Right now, chrome won't and Firefox won't, and I'm using a back version, the last version, of Brave that would agree to run on Windows 7. So, as I've said, browsers are the main attack surface for PCs today, so that'll eventually become a problem.
My Windows 10 machines operate behind two layers of NAT routing and a PFSense firewall. They're all on their own isolated LAN segment, separate from IoT devices which are roaming around, and, like you, mike, I've never had a virus or a malware problem. It may be that my surfing is tame and also that I never failed to treat the external internet as a hostile foreign power. I'm never in too big a hurry to put something through VirusTotal that I download and I'm not sure about before I open it or run it, and I do as much security checking as I can. Sometimes I'll actually launch something in a VM if I'm not sure. So, yeah, I'm taking a lot of responsibility for my security.
Given the maturity of Windows 10, which is significantly more now than Windows 7, I can't see any reason to feel pressured to move to Windows 11 only for the sake of an ongoing flow of security updates to repair the things that they will be breaking in Windows 11. Having played with it for a while, I understand its appeal Windows 11. It is truly lovely, but I don't plan to move. So I will be glad that Microsoft will finally stop, or has stopped, messing with Windows 10. They're going to leave it alone. So it will have another six months of updates after October. Now we know that we're able to make it to April of 2026 before this really becomes a problem, and at that point I think that if anyone was concerned, then the zero patch people will. As long as Microsoft continues to offer any updates, the zero patch guys will be reverse engineering those updates and offering them. So I think Windows 10 is going to continue for a long time into the future.
Dennis Borentrager asked does Spinrite 6.1 work on drives bigger than two terabytes? I can't get it to do it. I'll just quickly say yes, it operates actually on drives up to 144,000 terabytes. As it happens, that's 48 bits of sector addressing. The two terabyte limit comes about because of 32 bits of sector addressing and the use of older machine BIOSes. So I'm sure, dennis, that you're attempting to connect a larger drive through USB on a machine with an older BIOS. Move to a machine with a newer BIOS, as many of our testers did during the development of 6.1, it'll run on a drive of any size up to 144,000 terabytes, which probably ought to hold everybody for the foreseeable future.
Rick LaBlanca said in your second zero trust example, I thought all you need to do is oh, and he's talking about the one where we had the two customers of the one supplier and the four boxes for whether they'd been allowed to purchase 100, 200, 300, or 400 of the items. He said I thought all you needed to do is hash the quantity sold and give it to each other is hash the quantity sold and give it to each other. A match means the same amount sold, but the amount is not revealed. Okay, that's technically true, but Rick's question is a great example of why these zero-knowledge proofs can be so tricky. The problem with his suggestion is that both parties could hash the various purchase quantities themselves to obtain the direct hash equivalents of those quantities. Then, if either party were to reveal the hash of their quantity, the other party would see which of the hashes had been provided and they would immediately know the other's quantity. So in this case the hashes are just unique versions of the quantities. The reason we needed to jump through all of those hoops with the locked boxes and the paper slips dropped through the slots was to concoct an algorithm that would deliberately blind both parties to any knowledge other than whether or not they had purchased the same quantity. If not, they would still learn nothing of what quantity the other party had purchased, only that it wasn't the same as theirs. So interesting, tricky problems.
Lee McKinnell said hi, steve, on your comment about needing cheap biometrics for age verification, he said my smartphone in Australia cost me $100 Australian dollars. It's a Samsung Galaxy A15. It's a current model, released on 16th of December 2023. It has a fingerprint sensor that I use with Bitwarden and Passkeys. A flagship phone is not required. I bought this phone because it was affordable. Lee from Brisbane, australia. Okay now, I appreciate Lee's note and I'm glad to know that low-end biometric-enabled smartphones are available. And, leo, when you were talking about people spoofing their age authentication with a photo of somebody else or something, this is why, every time I've talked about age verification, I've talked about age verification, I've included the phrase unspoofable biometric age verification. Clearly, there has to be a biometric binding between a person's actual age and their ability to to.
2:01:49 - Leo Laporte
To verify that on the fly um I checked with the internet and it turns out that best best buy these days.
2:01:52 - Steve Gibson
best buy was willing to offer me a uh oh, now it's taking dictation whoops. Was willing to offer me a brand new Samsung A15 for $39.
Nice With next day free delivery, look at that I was astonished, got a side-mounted biometric fingerprint sensor, multiple cameras, a nice high-res AMOLED screen, connectivity via Wi-Fi, bluetooth, nfc, of course, android. That means that it could almost certainly serve as a full-featured authenticator and a price of $40 would be hard to beat. I mean, I was astonished by the fact that a state-of-the-art Samsung Android smartphone could be had for $40. As I said, one of the biggest problems with age verification is that it's difficult to see how it can be done without biometrics. You know, verifying someone's age only makes sense at all if that verification can somehow be locked to their physical body. Any privacy requires that both the biometric lock and the real-time age verification with a remote site all be performed locally. That is, if you're going to prove that you are the age you claim you are to an adult-only access site. You can't use a third-party site, otherwise you lose privacy. So it's got to be an assertion that your device is able to make of your age, in very much the same way that PassKeys is able to make an assertion that you own the private key that is in your PassKey. That's why I referred to FIDO the other day. This is very much a FIDO-esque problem and that's why I talked about Stena and authentication. There's a lot of overlap here between passkey style prove that I own the private key style. Prove that I own the private key directly in a two-party conversation. So what we need is we need a third party one time to create that identity assertion. You go to the post office, you go to the DMV, you go to a notary and show you know, improve who you are, show them a government ID, prove your age. They then allow you to create a binding with your device and then there's some hope that this could happen. But anyway, I don't see any way that age verification can possibly be made available for no cost because of the need for some sort of biometric attestation, a facial recognition, fingerprint or whatever. So I don't know how we get there and it's going to be interesting to see. And to your point, and I have a feeling we're going to have lots of false starts before we finally solve this problem, unfortunately. One last piece of feedback from a listener that just came in this morning so I updated the original show notes to version 1.1 so that I could include this from Sable Cantus, who wrote regarding Project Hail Mary. He said Hi, steve, longtime listener, spinrite owner and SoCal native here. He said I was listening to the show when you were thinking about the movie adaptation. I just wanted to share that I think we'll be in good hands with this movie.
Last Saturday I attended San Diego's Comic-Con and went to the panel for Project Hail. Mary Andy was there, andy Weir, of course. The author Andy was there with the directors. Of course the author Andy was there with the directors and Ryan Gosling and the same screenwriter who wrote the Martian adaptation, drew, who we talked about before. They spoke about the production and the storytelling. We watched a few clips and the first five minutes of the movie. Andy Weir said that Ryan brought more depth to Dr Grace than was written in the book and he stated that every number you see on screen, every formula, even if it's blurred, was Andy's work by hand. Wow, he made it clear that he spent hours verifying the science behind everything in the movie. Sable said I don't expect them to capture the entire journey of a huge book. I am impressed with what I saw at the panel. I don't think they're skimping out in any way. They did show the set for the tube and that alone showed me they are not cutting corners. Keep up the good work, steve. Live long and live well and prosper Sable. So I am hopeful, leo, that, uh, that we might get a great movie.
Um, uh, lori finished reading Artemis. Um, she was. She said she was a little put off by the science because apparently it is deep in science. Like I mean, I'm in love with it. I'm just I'm just starting. What we like, yes, and the idea that aluminum smelting, which is going on on the moon, produces a huge excess of O2 and silicon, I think is very cool. And the fact that glass is made of silicon and O2, and so there's a glass factory, I mean that's like okay, that's hard science fiction. I mean that's as hard as it gets and I love it.
2:08:19 - Leo Laporte
Yeah, and he spent a lot of time thinking about what a moon colony would require, how you could make a sustainable moon colony. It is wonderful, yeah, so you like you're reading the book now, or not? Oh yeah, I am into Artemis now. Okay, and you liked it.
2:08:32 - Steve Gibson
Just the beginning I'm. I have a hard time making time because I there's so much other stuff I'm trying to get done. Tell me about it. Yeah, but I am absolutely 100%. I mean mostly the guy is a writer. He's a very good writer and Laurie is very choosy and she said, as she put the book down, finishing it last night, she said this guy is as good a writer as Michael Crichton. That's good, you know.
2:08:59 - Leo Laporte
The thing. I'm glad to hear that Laurie liked it, because the protagonist is a woman and a lot of times women say men can't write women. But I think he did a good job and I'm glad to hear Laurie liked it. That's good, that's good, yeah, good. Well, read it everybody. I guess the movie version of that did not happen, or maybe it's still in the cooker, I don't know, but I look, look forward to.
2:09:22 - Steve Gibson
Andy is working on another book oh god, he's got one on the topic of ai. And, of course, he does his style, his, his humor. Of course he does his science. Uh, it's, and it's supposed to. Apparently he's been a little stalled because he's very involved in the movie production of Hail Mary, so that has slowed down his work on this next book. But it was expected in the spring of this year, so that means it's like you know we're going to have another book from Andy.
Probably you know I would imagine late. I'm just making this up Late summer, early autumn, maybe early fall. From from andy probably you know I would imagine late.
2:10:01 - Leo Laporte
I'm just making this up late summer, early autumn, maybe, uh, early fall good, well, I'll interview him when he, uh, when it comes out, if we, if he'll have us, uh, I have kind of a tradition. I've interviewed him for every book so far. I bet he will. Which makes me think where's daniel suarez? What's his latest book, I feel like, because he did write a book about ai, I think.
Yeah, in fact, all his books have a certain amount of ai in them oh my god, yeah, yeah, yeah, the very first one yeah, we had the motorcycles and the drones and yeah, um, I guess I'll call daniel and I'll call uh, uh, uh, andy, and we'll see if we can get a little. That'd be fun to have both of them on. If I can get them both, or even if I just get Andy, I would love to have you on with us. That'd be fun. Yeah, you got me. Yeah, good Deal. Let's pause because you're going to talk about the SharePoint extravaganza, or should I say fiasco.
But first a word about our club. This is something so important to me Should be important to you too, steve, because the club pays your salary. The club pays more than that. It is 25% of our operating expenses now and I'm really thrilled. We created this club almost five years ago At least it was Lisa's idea.
At the time we were in the height of the pandemic and advertising was dwindling and we thought you know, maybe it's time to have the listeners support the network. You know, my dream from day one was to have Twit be entirely listener supported. I think we were smart to do advertising, because it's made it possible for us to grow and do a lot of stuff. But you don't want to be entirely reliant on advertising. I'd like, if you like what we do, I'd like your support, and the best way to do it is to join Club Twit. Now here's the deal with Club Twit it is 10 bucks a month. That's what a year.
There are several other versions. There's a enterprise, you know, a company plan. Uh, there's also a family plan. There's even two-week trials. So if you're not convinced, you could do the two-week trial.
What do you get? You get a lot of, I think, great benefits, of course, primarily ad-free versions of all the shows we do, which is nice. It saves you time. For sure you wouldn't even hear this plug. You also get access to the Club Twit Discord, which is a fabulous place to hang out with some of the smartest, geekiest people in the world, not just during the shows, but you can also join us in the club for special events. People chat all the time about the club or in the club about all kinds of topics 3d printing, gaming. We have a pretty active advent of code group every december. That's a lot of fun. There's also special events that go on in the club. The AI user group is coming up on Friday. In fact, if we do an interview with Andy Weir, it would almost certainly be a club event. That's one of the ways we make the club more interesting. Is these extra things Hands on tech, hands on Apple, hands on Windows. You can get the audio of those. They're open to the public, but the club members get video as well.
Stacey's Book Club is coming up. We're going to do a really great sci-fi. It's a sci-fi book club and a really great one called this Is how you Lose the Time War. Not too late to read it because it's a fairly short, almost a novella length. That's August 8th, a week from friday following the same day, following the book club, we're going to do the photo segment with chris marquardt. We do this every month. The photo assignment is the word classic, so it's not too late to take pictures. The club is fun. There's stuff going on. We're going to do the google uh pixel keynote august 20th.
Mic Micah's Crafting Corner I will be doing a sewing project, oh, ah, ah. And Micah is doing a D&D one-shot adventure and he's trying to figure out what the best way to do it would be. So he's got a poll that you can vote in about how would you like it to be just twit hosts, or would you like to be able to participate, or would you like a mix? These are the look. This is what makes the club so much fun, so interesting.
Uh, it is a place for you to hang with other like-minded smart people and enjoy the benefits of being a geek. So if you're not a member, can I encourage you to go to twittv slash club twit, join the club. At least do the free trial, because we would love to have you in the Discord part of the club and we sure appreciate the support we get from our great club members. Thank you, club members. We really, really really appreciate it. Now on we go with Security. Now. One of the main reasons to be in the club is this great show and the information you get from Steve Gibson. Let's talk about SharePoint.
2:15:12 - Steve Gibson
Okay. So today's title, to remind people, is Inside the SharePoint zero-day RCE RCE, of course, the abbreviation we all know remote code execution. The title leaves little room for misunderstanding A remotely exploitable code execution vulnerability exists in all unpatched, widely and long-used on-premises instances of Microsoft SharePoint server, and it is known that more than 400 organizations have been attacked and hacked as a result of this flaw. Among the growing number of victims are several US federal and state agencies, universities and hospital chains. Because a trio of Chinese APT groups appear to be behind the attacks, we would perhaps not be surprised to learn that the US federal victims include the US Department of Homeland Security get this the US National Nuclear Security Administration. Not good.
2:16:25 - Leo Laporte
Not good.
2:16:26 - Steve Gibson
And the NIH, the US National Institutes of Health. For those who are not tied into the enterprise world and may not be intimately familiar with Microsoft SharePoint Microsoft says that SharePoint enjoys 200 million users. That's not servers, that's people using it. But here's how Wikipedia describes it in two lines. They said SharePoint is a web application by Microsoft that's primarily used for building an intranet and managing and sharing files. Launched in 2001, the year of the Space Odyssey, it was initially bundled with Windows Server as Windows SharePoint Server, then renamed to Microsoft Office SharePoint Server and then finally renamed just SharePoint server and then finally renamed just SharePoint. It could be used on-premises or as a Microsoft 365 hosted service, you know, in the cloud.
So this news was breaking while we were recording last week's podcast. I don't know why that's happening now, leo, but, like, for this is the second time, second week in a row it was while. You know, like last last week, while we were recording the podcast, cloud strikes outage was. You know, I mean cloud flare, sorry, cloud flares big DNS outage was happening for an hour. So today's news while we were. While we were, we were recording last week's podcast. Anyway, enough time has now taken for the story to have taken shape. So I'm going to share first what Wired wrote, since it nicely places the story into context and provides some background, and after that we'll examine what the security firms who dug into this more deeply found. So, wired said hundreds of organizations around the world suffered data breaches as an array of hackers rushed to exploit a recently discovered vulnerability in older versions of the Microsoft file sharing tool known as SharePoint. The string of breaches adds to an already urgent and complex. Dynamic Institutions that are longtime SharePoint users can face increased risk by continuing to use the service, just as Microsoft is winding down support for this platform in favor of newer cloud offerings. In other words, as I've said before, microsoft is like saying sorry, no, we're no longer going to support the things you bought from us in the past. Now you're going to have to subscribe to the same thing in the cloud, they wrote.
Microsoft said last Tuesday that, in addition to other actors, it has seen multiple China-linked hacking groups exploiting the flaw, which is this is Microsoft acknowledging this, which is specifically present in older versions of SharePoint that are self-hosted by organizations, in other words, using SharePoint server 2016 and 2019, or maybe even older ones? It does not impact the newer, cloud-based version of SharePoint that Microsoft has been encouraging customers to adopt for many years. Bloomberg first reported on Wednesday that's last Wednesday that one of the victims is the United States National Nuclear Security Administration, which oversees and maintains US's nuclear weapons. On-premises or self-managed SharePoint servers are a popular target for hackers because organizations often set them up such that they're exposed to the open internet and then forget about them or don't want to allocate budget to replace them. That sound familiar. Oh, even if fixes are available, the owner may neglect to apply them.
This is Wired Magazine, right? This is not this podcast. We say that all the time. Wired said. That's not the case, though, with the get this, with the bug that sparked this week's wave of attacks. While it relates to a previous SharePoint vulnerability discovered at the Pwn2Own hacking competition in Berlin in May, the patch that Microsoft released earlier this month was itself flawed, meaning even organizations that did their security diligence were caught out. Microsoft scrambled this week to release a fix for the fix, or what the company called more robust protections in its security alert. Now I'll just pause to say this really shouldn't surprise us. We've covered in the past how Microsoft's current incarnation of security updates appears to focus upon implementing a quick fix for the symptoms rather than addressing underlying systemic weaknesses. I don't know that's what happened in this instance, but if it quacks like a duck in this instance, but if it quacks like a duck, wired continued writing.
A Microsoft spokesperson wrote in an emailed statement quote at Microsoft our commitment, anchored in the secure future initiative, is to meet customers where they are. That means supporting organizations across the full spectrum of cloud adoption, including those managing on-premises systems. Wow, okay, talk about a statement that says nothing. Anyway, wired continues. Microsoft still supports SharePoint Server versions 2016 and 2019, with security updates and other fixes, with security updates and other fixes, but both will reach what Microsoft calls end of support on July 14th, 2026. Well, okay, this is the 29th, so that happened. Sharepoint server 2026. So next year? What am I saying? This is 2025. So July 14th, 2026. So, just short of one year from now, support for 2016 and 2019 SharePoint servers will end, have already reached end of life and receive only the most critical security updates through a paid service called SharePoint Server Subscription Edition. Right, so you could subscribe to, as now Microsoft is doing, to receive extended support? Wired wrote. As a result, all SharePoint server versions are increasingly part of a digital backwater, where the convenience of continuing to run the software comes with significant risk and potential exposure for users, particularly when SharePoint servers sit exposed on the internet.
Jake Williams, a longtime incident responder who's vice president of research and development and hunter strategy, said quote years ago, microsoft positioned SharePoint as a more secure replacement for old school Windows file sharing tools. So that's why organizations like government agencies, maybe the CIA invested in setting up those servers, and now they run at no additional cost compared to Microsoft 365 subscription in the cloud that requires continuous payment. Okay, this is not me saying this again, this is somebody else, so no surprise. He says so. Microsoft tries to nudge the holdouts by charging for extended support, but if you're exposing a SharePoint server to the internet, he said, I would emphasize that you also have to budget for incident response because that server will eventually get popped. Unquote, wired says the United States Cybersecurity and Infrastructure Security Agency said in guidance about the vulnerability Tuesday that quote CISA recommends disconnecting public facing versions of SharePoint server that have reached their end-of-life or end-of-service.
For example, sharepoint Server 2013 and earlier versions are end-of-life and should be discontinued if still in use. Now the problem is it's working and it's been paid for. Been paid for. So when budgets are tight and when are they not going through all the hassle of switching to a paid Microsoft cloud-based service and then needing to continue paying for it can be a difficult sell to upper management, as I've observed here recently. The entire model that's evolved across our industry of selling online software systems that are later found to have critical vulnerabilities and expecting their users to suddenly take proactive responsibility or even be aware that there's a problem that needs their attention is inherently impractical and is badly broken in practice.
Wired's author of this article apparently agrees. Writing. The ubiquity of Microsoft's Windows operating system around the world has led to other situations in which a long goodbye as the way he put it, a long goodbye has created security issues for holdout users and other organizations or individuals with connections to a vulnerable entity. Microsoft struggled to deal with the long tail of users on extremely popular Windows editions, including Windows XP and Windows 7. And, of course, I would expect this whole drama to repeat itself with Windows 10, starting soon, wired wrote.
But legacy software is a challenge for any software or digital infrastructure provider. Earlier this year, for example, oracle reportedly notified some customers about a breach after attackers compromised a legacy environment that had been largely retired in 2017, yet people were still using them. The challenge with a service like SharePoint is that it often acts as an ancillary tool without ever being the center of attention, meaning it's just kind of there in the proverbial back closet somewhere working and forgotten. Bob Huber, chief security officer at the cybersecurity company Tenable, says quote for on-premises software like SharePoint, which is deeply integrated into the Microsoft identity stack, there are multiple points of exposure that need to be continuously monitored in order to know, expose and close critical gaps. Unquote.
When asked about the alleged breach at the National Nuclear Security Administration, the Department of Energy emphasized that the incident did not impact sensitive data or classified data. A DOE spokesperson told Wired in a statement. Quote on Friday, july 18th, the exploitation of a Microsoft SharePoint zero-day vulnerability began affecting the Department of Energy, including the NNSA. The department was minimally impacted due to its widespread use of the Microsoft 365 cloud and very capable cybersecurity systems, so a bunch of them had migrated to the cloud, but not all, he said. A very small number of systems were impacted and NSA is taking the appropriate action to mitigate risk and transition to other offerings as appropriate. So maybe this you know this incident has spurred people to move to the cloud. Microsoft Wired finishes saying Microsoft did not immediately return Wired's request for comment about the process of sunsetting SharePoint server. The company wrote in a blog post on Tuesday that customers should keep supported versions of SharePoint server updated with the latest patches although that didn't help in this case and turn on Microsoft's anti-malware scan interface as well as Microsoft Defender antivirus. Unfortunately, as we saw, we're going to get some more information on this now.
Microsoft fumbled and botched the security patch during May's Pwn2Own competition, which we covered at the time, since it was the first time Pwn2Own had been held in Berlin, having moved from Toronto with the cybersecurity arm of Vittel, a telecom firm run by Vietnam's military, identified a SharePoint bug dubbed Tool Shell and demonstrated a way to exploit it. That discovery won the researcher an award of $100,000. But here's where the plot thickens. Exploits discovered by security researchers remain explicitly secret. We only learn that there is a flaw and of its general nature and nothing more. As part of the researcher's agreement, they confidentially provide all required information to Trend Micro's zero-day initiative team, which then in turn forwards that information to the affected software vendor with a 90-day time expiration on that zero-day flaw being patched. The publication on that zero-day flaw being patched. The publication we all know.
The register theorizes that the exploit may have leaked from Microsoft. I don't buy into it completely, but here's what the register said Less than two months later, on July 8th, microsoft disclosed the two CVEs 49704, which allows unauthorized remote code execution, and 49706, a spoofing bug, and released software updates intended to patch the flaw. So July 8th was patch Tuesday. Earlier this month the register wrote but mass exploitation had already started the day before, on July 7th. Now that's not true. Some exploitation had started, not the mass exploitation. Dustin Childs quotes the register. Head of threat awareness at trend micro, zero day initiative said quote 60 days to fix isn't a bad timeline for a bug happened, which may have been true. Again, no proof of it.
Patch Tuesday happens the second Tuesday of every month, writes the register. In July that was the 8th, but two weeks before then. Microsoft provides early access to some security vendors via the Microsoft Active Protections Program, mapp. These vendors are required to sign a nondisclosure agreement about the soon-to-be-disclosed bugs and Microsoft gives them early access to the vulnerability information so that they can provide updated protections to customers faster, childs said.
Childs with Trend Micro said the first MAPP drop occurs at what we call R-14, meaning 14 days before release, release minus 14. In this case that was June 24th. Then on July 7th, which was one day before the patch Tuesday, he said, we started to see attacks, again not apparently mass and widespread. July 8th the patches were out and were almost immediately bypassed. Well, they were almost immediately bypassed for another reason.
Zdi writes the register, along with other security providers, poked holes in the initial patches, true and determined that the authentication bypass piece was too narrow and attackers could easily bypass this fix. In fact, writes the register. Anyone who received the early MAPP information about the CVEs and software updates would be able to tell that this is an easy way to get past it. I want to make sure I don't forget to mention that once the patch Tuesday patches came out, they were immediately diffed. You know differences made and the patches were reversed, engineered from the diffs, not from any MAPP or not necessarily using any MAPP advanced information. So you know a lot is still unknown. The register finishes saying on July 18th, I security first sounded the alarm.
So it was on the 18th of July, 10 days later, 10 days after patch Tuesday, that the actual large scale exploitation of a new SharePoint remote code execution vulnerability chain in the wild was seen, and one day later, that's when Microsoft warned SharePoint server users that three on-prem versions of the product, including a zero-day flaw, was under attack and that its own failure to completely patch the holes was to blame. Okay, but there's more in use by auditors, banks, healthcare companies, major industrial firms and US state, federal and international government bodies. Are in use 8,000. In other words, it's a mess. The 8,000 figure might be conservative because the Shadow Server Foundation, which continuously scans the Internet for potential digital vulnerabilities, put the number at a little more than 9000, cautioning that that figure is a minimum. That is a minimum of more than 9000 instances of SharePoint, of vulnerable SharePoint on the internet, meaning that they were able to confirm that 9,000 figure and there's likely more. The Shadow Server Foundation said most of those affected were in the United States and Germany.
The last thing I want to share is some of the very interesting reporting by the researchers at iSecurity. Those were the first people to report this and to report that, basically, the attacks went viral, and the last thing you want is just to hear that a zero-day remote code execution vulnerability attack has gone viral. Remember that the first known instance of exploitation occurred on the day before the July 8th Patch Tuesday, which was exactly three weeks ago today. As we're recording today's podcast, the iSecurity researchers wrote on the evening of July 18th iSecurity was the first to identify large-scale exploitation of a new SharePoint remote code execution vulnerability chain in the wild, demonstrated just days before on X, which is what used to be called Twitter the X platform. On X, which is what used to be called Twitter the X platform. This exploit is being used to compromise on-premise SharePoint servers across the world. The new chain we uncover in this blog was later named and then they updated CVEs. Microsoft had the first round of CVEs. Then, when they fixed the fix, they gave them CVEs 53,770 and 53,771. They wrote before this vulnerability was widely known.
Last Friday our team scanned over get this 23,000 SharePoint servers worldwide In total at that time. That is again before this vulnerability was widely known. Last Friday they discovered more than 400 systems actively compromised during four confirmed waves of attack. So there was four confirmed waves of attack. They enumerate them the initial attack wave, 17th of July at 1251 UTC, coming from IP 96.9-125-147. They think that was a testing wave to verify their exploit. Then there was attack wave, one the next day on the 18th of July, at 1806 UTC, coming from a different IP 107, 191, 58, 76, and that one was widely successful. The third wave, the second big attack wave the following day, the 19th of July, at 728 UTC, originating from IP 104, 238, 159, 149. And then multiple smaller waves on and after the 21st of July, after a public proof of concept exploit script was released on GitHub. So basically the world knew about it at that point and remember, all of those attacks were effective against both unpatched that is never before patched and then fully patched post patch Tuesday SharePoint servers. So there was a 10 day window from July 8th through July 18th when these attacks were effective and even after the 19th before the updated update got out to everybody. Update got out to everybody.
So in this instance it was Microsoft's significant fumble of the initial patches that were readily bypassed because they were merely cosmetic symptom covering patches of the sort that we've seen before. There are postings on the net by people saying that they diffed Microsoft's Patch Tuesday patches, patch Tuesday updates. Found out what the differences were, that affected SharePoint server and then reverse engineered the patches and wrote code to sidestep the imperfect fixes that Microsoft had attempted to implement in patch Tuesday. So basically, microsoft made things much worse by poorly patching SharePoint server on Patch Tuesday, because then everybody else in the world was able to see what they changed. Take a close look at it and see that Microsoft had not actually fixed the problem. Microsoft's updated patches, which do now the updated patches do now actively, you know actually resolve the problem. Those only cover SharePoint server 2016 and 2019, sharepoint server 2010 and 2013, which are on the internet, remain vulnerable and no patch for those, as expected. So they must either be isolated from the public Internet or shut down. Okay, so what exactly and this is really cool because it's a sort of a here's how, like exactly what happened here's what the eye security guys saw that led to this whole thing. They wrote they wrote.
Early in the evening, our 24-7 detection team received an alert from one of our CrowdStrike Falcon EDR deployments at a specific customer chain on a legacy SharePoint on-prem server tied to a recently uploaded maliciousaspx file. At first glance it looked familiar a classic web shell, obfuscated code in a custom path designed to allow remote command execution via HTTP. We've seen many of these before. What made this one stand out, however, is how it got there. Our first hypothesis was mundane but plausible a brute force or credential stuffing attack on a federated active directory identity, followed by an authenticated upload or remote code attempt using valid credentials. The affected SharePoint server was exposed to the internet and tied to Azure Active Directory using a hybrid ADFS. That stack, when misconfigured or outdated, can be a dangerous combination. It all seemed to confirm the theory credentials compromised, shell dropped, persistence achieved.
But examining the IIS logs, the web server? Examining the IIS logs more closely, we noticed that the referrer was set to slash underscore layouts forward, you know, forward, slash, sign out, dot ASPX. That's odd, they wrote. How can that be an authenticated request just after the user has logged out? Something didn't add up. We found no successful authentications in ADFS logs, or the logging was at least insufficient. Malicious IIS logs did not contain a value in the username column. A post request to the underscore layouts slash 15, slash tool pane, dot ASPX seemed rather specific. Referrer set to underscore layouts forward slash, sign out, dot ASPX. Cannot be authenticated. Right.
We began to develop a feeling that credentials were never used. So how could the attacker write files to the server without ever authenticating at all? That's when we realized we were no longer dealing with a simple credential-based intrusion. This wasn't a brute force or phishing scenario. This was zero-day territory. After some digging we learned that three days earlier, the offensive security team from CodeWhite GmbH demonstrated they could reproduce an unauthenticated RCE exploit chain in SharePoint, a combination of two bugs originally presented at Pwn2Own Berlin earlier this year in May. Those bugs were still present in the patched SharePoint server. They dubbed the chain ToolShell. What we discovered on the 18th was not a credential issue. We had stumbled upon a weaponized pwn-to-own exploit already being used in the wild.
When our team began reviewing the impacted systems, we expected to find the usual suspects standard web shells designed for command execution, file uploads or lateral movement. Instead, what we discovered was more subtle and arguably more dangerous a stealthy spinstall0.aspx file whose sole purpose was to extract and leak cryptographic secrets from the SharePoint server using a simple GET request. This wasn't your typical web shell. There were no interactive commands, reverse shells or command and control logic. Instead, the page invoked internal NET methods to read the SharePoint server's machine key configuration, including its validation key. These keys are essential for generating valid view state payloads, and gaining access to them effectively turns any authenticated SharePoint request into a remote code execution opportunity. Then it all clicked Once the machine key configuration, including the validation key, had been obtained. Future payloads can embed any malicious commands and would be accepted by the server as trusted input, completing the RCE chain without requiring any credentialing. Exploited four years ago in 2021, but it's now been packaged into a modern zero-day chain with automatic shell drop and full persistence with zero authentication.
More than 24 hours after we published our initial findings and reached out to affected vendors, including Microsoft, and reached out to affected vendors, including Microsoft, the Microsoft Security Response Center issued an official advisory and assigned vulnerability identifiers On their page. Microsoft confirmed active exploitation in the wild and acknowledged the severity of the issue. They make one final crucial point Due to the fact that this is a machine key exfiltration attack. They said the attack we've observed specifically targets the exfiltration of SharePoint server ASPNET machine keys. These keys can be used to facilitate further attacks even at a later date.
It is critical that affected servers rotate SharePoint server ASPNET machine keys and restart IIS on all SharePoint servers. Patching alone is not enough. If you are not targeted or you are unsure, we also advise teams to rotate their machine keys just to be sure it has no system impact, only that IIS is offline for some seconds while restarting services. So we don't know how many systems, enterprises, organizations and networks have been compromised as a result of Microsoft's botched patches for the original Pwn2Own zero day, but that number lies somewhere between the 400 that have been confirmed and the 9000 that were known to be vulnerable by the Shadow Server Foundation, and the attackers were aggressive and automated. This is a great deal of damage, and the ransomware demands have already begun. As an industry, we need to do better, we need to change the model and, of course, this has been an important, high-profile incident, that individual, so much so that individual reports have now been published by Broadcom's, symantec, cisa, cisco, talos, census Checkpoint, crowdstrike, isecurity, logpoint, microsoft Orange, palo Alto Networks, qualys, sentinelone, tenable, trend Micro and Varonis.
2:50:51 - Leo Laporte
Some or all of whom are sponsors of this show Pretty much everyone.
2:50:54 - Steve Gibson
I'll make it easy Pretty much everyone.
2:50:58 - Leo Laporte
You know, one sysadmin or security researcher said uh, you should just assume that you, if you are running on-prem sharepoint, that you are compromised. You should not assume that you're not.
2:51:11 - Steve Gibson
Yes, unplug, repatch, update, patches, rotate your keys and then, of course, you need to worry about if something crawled in. Where might they else? What? Where else?
2:51:22 - Leo Laporte
yeah, they may have already breached the rest of your network. Yeah, that's why I set up my my things. Canary, our sponsor thinks canary's honeypot, to be sure. Point 10, just you know just to see that's one of those things.
Nobody the outside is going to get into it. But but if, if somebody is in our network, that's the first thing they'd go. Outside is going to get into it, but but if, if somebody is in our network, that's the first thing they'd go to go. I know how to hack that, because that was unpatched anyway. What fun.
Not for the poor 9 000 people who run on-prem sharepoint so I imagine you know that this will push some people into the cloud um uh, yeah, but if you're the, you know, if you're in charge of the nuclear weapons, you probably don't want to run in the cloud, right, you probably want on prim, but maybe you should.
2:52:14 - Steve Gibson
Cloud's got its own problems. I mean, it was all of the people who had their email in the cloud that had Shiner reading their email.
2:52:22 - Leo Laporte
Right, oh Lord. Dale Poco in our YouTube chat says Pondone was in Vancouver, not Toronto. I don't know, maybe he's Canadian and he cares, I don't know, but it was in Vancouver.
2:52:37 - Steve Gibson
Oh, yeah, yeah, yeah, yeah, thank you for the credit. Yeah, I know what you meant. You meant Canada, I meant Canada, and of course, I have such fond memories, leo, of you and me.
2:52:46 - Leo Laporte
In Toronto and Vancouver. When you first proposed that we do this podcast, we started this show in Toronto 20 years ago, but you must have come to the lab in Vancouver. You were bored, leo, and you are no longer bored, I don't have enough to do steve.
2:53:03 - Steve Gibson
I merely have five days a week, a month. And you had, yeah, and he had the weekend show, the weekend radio show, and you were just at loose ends, you know, the other day, and you said, let's do a podcast what do you think?
2:53:13 - Leo Laporte
and you said what's a podcast? I did well not many, I know now was way back then now yeah, yeah, we all know now, uh, 20 years in your, your 20th anniversary is coming up this month, next month, yep, yep, wow, wow, wow. So it was 2005, yeah, the fall of two or summer of 2005. I said hey, steve, let's do a show unbelievable. Well, oh, dale poco lives in a suburb of vancouver.
2:53:49 - Steve Gibson
That's why he cares now remember that the the the first few I would bring. Uh, I would bring the microphones uh to to to toronto and we sat in your hotel room. That's right, and once we did it on the roof, didn't we?
2:54:05 - Leo Laporte
of the of the uh drake in uh in toronto, I think? So, yeah, yeah, I remember we. I had a really cool thing you could plug in multiple microphones too. Yeah, of course you did of course you had whatever gadget was a good excuse to buy that crap.
Yeah an sd card and or a uh the the square thingy, uh oh, compact, compact flash compact flash card yeah, you know, we had all of that stuff until we closed the studio down. At that point we had to sell or give away most of it. I think a lot of it went to schools and other people could use it. Thank you, grayson, for $5. He has just donated in our YouTube chat, in our Super Chat. Thank you, grayson. Grayson's always in here listening. He's a regular. So, steve, I hope you're all regulars. You should come back every week.
We do this show Tuesdays right after MacBreak Weekly. That's about 1.30 Pacific, 4 eastern, 2030 utc. You can watch live, as I mentioned, on youtube and twitch and tiktok and facebook and linkedin xcom kick, or in our club to a discord if you're fortunate enough to be a club member, or, I should say, generous enough to be a club member. After the fact, we put it up on the website twittv slash sn. Actually we have two versions 128 kilobit audio, mp3, and we have video so you can see steve's mustache at work.
But steve has his own unique versions on his website, grc. He's got 16 kilobit audio which, to be frank, isn't the highest fidelity, but it's a small download, so you take your choice. He also has a perfectly good quality 68, I'm sorry, 64 kilobit version MP3. He also has the show notes there, fantastic human written transcriptions from Elaine Ferris, so you can read along or search. He also has other things there. You know, you've heard perhaps and mentioned a little thing called spin right. Version 6.1 of the world's best mass storage, maintenance, recovery and performance enhancing utility is available at grccom, and that is steve's bread and butter. So if you don't have a copy and if you have mass storage which I think you do, and who doesn't, yeah, it's been right work.
We found out last week it works on a kindle for crying out loud. Amazing. Um, there's lots of other stuff there's. Grccom is a treasure trove. Uh, it's more like steve's attic with all sorts of stuff, little nooks and crannies, and you could just spend days there. So check it out If you want to send Steve an email. That is not so easy. Steve doesn't like spam, so what?
2:56:51 - Steve Gibson
you have to do is go to grccom slash email.
2:56:52 - Leo Laporte
Enter your email address there. Steve will validate it. Now you're whitelisted and you can send him email. You can also. It's not done by default, so look below that and you'll see two check boxes one for the Security. Now show notes. You can get those emailed to you a couple of days ahead of time. Prepare for the show, if you will. There's also a much less frequent newsletter that he sends out whenever he's got something new.
Thank you, ixion. Another contribution of I don't know why, $4.20. What is 4.20? It's an interesting amount. We know what you're up to, ixion. Or is it 9-eon? I'm not sure if those are Roman numerals. Anyway, thank you. The Super Chat donations are great, although the best way to support us, as I mentioned, join the club, uh. That way you get, you know, automatic uh memberships plus you get lots of additional benefits. But if you just want to donate in the super chat or subscribe by the way, if you go to the club tweet page, twitchtv slash club to it you can just subscribe to security. Now I think that's is that four or five dollars a month, it's. It's less expensive, so you can. If that's the only show you listen to, you can absolutely do that uh, steve will be back next week, as will I in august. The guns of august, yes, see you then, steve. Bye, security now.