Security Now 1030 transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show
0:00:00 - Leo Laporte
It's time for security now. Steve Gibson is here, apple denies it, but there's clearly an exploited iOS message vulnerability, a good reason not to use Telegram ever, ever, ever, and Steve's evolving opinion of Microsoft security. I think you can guess which direction it's headed. All that and more coming up next on Security Now Podcasts you love. From people, you trust.
This is Twit. This is Security Now with Steve Gibson, episode 1030. Recorded Tuesday, june 17th 2025. Internet foreground radiation. It's time for Security Now. I know you wait all week for Tuesday to come around. Steve Gibson is here. The man in charge of security, now our expert. I shall give you the Klingon salute. Oh, that's good.
Yesterday I went to our wonderful little coffee shop in town, which has really become a community center. Good friend of mine runs it. Uh, has a game night on monday nights and I brought my chess set down. I thought, oh, this will be fun, I'll, maybe I'll, somebody will play chess with me. I set it all up with the clock there nobody was playing. But there was a guy across from me setting up his star trek 3d holo chess that plugs in and the things light up and stuff, and I said I came over. I said, hey, I gotta play some. He said, well, I don't know the rules and I and I seem to have lost the booklet. So, uh, I asked ChatGPT. Chatgpt knew the rules. Fortunately, the proprietor had also saved the booklet. What ChatGPT said is, since there are no canonical Star Trek rules for holochess, people have made them up over time.
0:01:59 - Steve Gibson
I was going to ask whether you know did I miss that episode? Because you know they always were moving them around.
0:02:04 - Leo Laporte
Yeah, you knew they were playing. Yeah, but here is uh, here's the photo of uh, of chris and peggy and me playing oh good, star trek hollow chess and it had, uh, it has, um, it has sound effects, and then the pieces light up and stuff, and the rules are so complicated that you get a card that you hold. So you know, there's a piece called the I guess that's how you pronounce G-H-H-H-K. Anyway, it was a lot of fun. We played to a draw.
0:02:43 - Steve Gibson
I think Klingon was actually a fully realized language wasn't.
0:02:46 - Leo Laporte
I think there's some klingon uh names in this you can actually speak klingon. Oh yeah, there's people yeah, apparently shakespeare has been translated, realized language, so yeah, yes, because before computers we didn't have enough to keep us busy. Uh anyway it was. It was a lot of fun. Um, we and there's a name for it too, uh, which I can't remember.
0:03:12 - Steve Gibson
It's not, no, it's something almost equally silly, like gajit or something, but uh, anyway, and as a an accomplished chess player, leo, was it actually a useful game or just no?
0:03:28 - Leo Laporte
no, chess is so much better. If I could have just gotten anybody to play chess with me, I would have been uh, it's called dejaric, it's not.
0:03:37 - Steve Gibson
Did I say star trek, it's star wars oh, this is not oh, and that does look like the, I would say yes this is the one they were playing on the Millennium Falcon.
0:03:46 - Leo Laporte
I apologize. Yeah, okay, I get them confused. No, no, you don't, I do, and that's not good.
0:03:53 - Steve Gibson
No, you don't. You can't do podcasts. If you confuse Star Trek and Star Wars, I'm going to take away my geek credentials.
0:04:00 - Leo Laporte
I'm sorry, that's not okay. What's coming up on security now?
0:04:10 - Steve Gibson
So we're going to talk about I had fun with the title because I've for 20 years I've been talking about a term that I coined internet background radiation. Yes, Today's podcast is titled Internet Foreground Radiation what? And we're going to find out what that's all about. Ground radiation what? And we're going to find out what that's all about. Uh, but we're also going to look at an exploited ios I message vulnerability, which apple is denying. Do we trust them? Are they saving face? We don't know. Uh, the npm repository is under siege with no apparent end in sight.
Two pieces of news there Not good Were Comcast and Digital Realty compromised. Don't ask them. They say no, not here, but evidence and even some serious agencies suggest otherwise. Matthew Green has agreed that XChat does not offer true security. We touched on that last week. I said I might dig deeper into it. I don't have to because Matthew did for us. We may know how Russia is convicting users of Telegram, and it's not by decrypting their messages. Interestingly enough, Microsoft finally decides to block two insane Outlook file types and I'm going to deliberately control my language because we have young listeners of this podcast Good.
Boy Wow I know you want to. It turns out just as we were doing the podcast. Last week, leo, you ran across the news that 40,000 video cameras were online on the Internet. I've got the details to follow that up and, interestingly enough, where they are and who owns them. Also, there was a question about running Spinrite on encrypted drives that I'm going to cover briefly. Dumping all of Elaine's transcripts into an LLM and then asking it how my opinion of Microsoft security has evolved over time. Oh boy, and what do we know about the bots that are scanning the internet to create internet foreground radiation? Internet to create internet foreground radiation. So and oh, a picture of the week. That is I. I sent the show notes out. Show notes out about 24 hours ago. Uh, yesterday afternoon this one generated more lols than is common. Um, I am going to have to describe, before we explain this, what it means to refactor uh code, because I know that well I know, you do and I, I also uh have had to do so from time to time.
0:07:14 - Leo Laporte
Yes, um, but anyway we have a great picture of the week. Can't wait, I have not looked at it. We will see it together in just a minute or two on this episode of security. Now can't wait. I always look forward to this. Go ahead, have a little sip of java. There's a lot of work ahead of you. Steve, while I. Now our sponsor for this segment is delete me.
And if ever you thought you needed to delete your data from data brokers, there is a real reason to do it now. I know people have been watching the news about what happened in minnesota. They recovered, uh, the suspect's notebooks and he had a list in the notebooks of all the places you can go online to get personal information about people, including their home addresses, from those data brokers. You, if you've ever gone online and done a search for your name, you know you see these people. They call them people searches, but they're data brokers. They're people, online sites, companies that collect your personal information and then sell it to anybody who comes along your name, your contact info. I was stunned to know it's legal to sell my social security number and your home address, even information about your family members, all being compiled completely legally. There's no law against it. There really needs to be by data brokers and sold online. Anyone on the web can buy your private details. This can lead to identity theft, phishing attempts, doxing, harassment and now we know much worse. But now you can protect your privacy with delete me. Look I, I live in the public. I uh, I share my opinions online. Uh, I make people mad because I confuse star wars and star trek. Obviously, obviously, I'm in trouble, right? Uh? It's really important to everybody, though, to keep your personal information private. That's why we use uh at twit for our management, our, our, our managers, and we recommend Delete Me. We did it when Lisa started getting. There were phishing texts being sent to our employees, to Lisa's direct reports, impersonating Lisa, and how did they know what her phone number was and who her direct reports were? Those darn data brokers? We immediately went to Delete Me.
It's a subscription service that removes your personal info from data brokers hundreds of them. You sign up, you give Deleteme the details about what information you want deleted, because you fully control that, and their experts take it from there. Now here's the neat thing. Just the other day, lisa got an email from Deleteme about what the status is, about, where her name is showing up and what they've done to delete it. Deleteme will continually do this. They'll send you regular personalized privacy reports showing what info they found, where they found it and what they removed. It's not just a one-time service. It's always working for you, constantly monitoring and removing the personal information you don't want on the internet. You know you need this, we all do. It's sad, but until there's a law against it, thank goodness there's Deleteme.
Deleteme does all the hard work of wiping you, your family, your company, your employees' personal information from data broker websites. They've got plans for businesses, families, individuals. Take control of your data. Keep your private life private by signing up for Delete Me. We've got a special discount for individuals today 20% off your Delete Me plan when you go to joindeletemecom slash twit and you use the promo code twit at checkout. But the only way to get 20% off is to go to joindeletemecom slash twit and enter the code twit at checkout joindeletemecom slash twit. Offer code twit at checkout. Join delete me dot com slash twit. Offer code twit at checkout. I hate to bring you know these terrible stories in but honestly, if ever there were a need for delete me, it's now join delete me dot com slash twit. Use the offer code uh twit, uh. Sometimes the world intrudes on our nice little space here. All right, I'm ready for the.
0:11:31 - Steve Gibson
Uh, the picture of the week set me up you, you, okay, if you're willing to wait for our listeners. I I was gonna say you, you could go, you could jump ahead if you didn't read it out loud. Okay, so I'll wait okay. So what I need to explain for those who are not coders is what the process of refactoring a code base is and it really comes from. It came from math where, for example, if you have the number 30, there are a bunch of factors of 30. You know two?
0:12:06 - Leo Laporte
five, 10, 15, 30.
0:12:09 - Steve Gibson
So so they're different. The point is there are different ways to break that 30 down into its factors. One of the things that happens with code is you start off with kind of an idea of what you're going to do and you, you, you say okay, this, okay, I'm going to put these things in this file and the things for the user interface they're going to go over here and things for the database go in the database file and everything sort of starts off right. And then reality hits. It's time for version 1.5. And some guy says, well, but AI, now we need an AI. It's like ooh crap, where do I put that? So you kind of stick it in somewhere just to get it working, because the boss says you got to ship this yesterday. What's taking you so long?
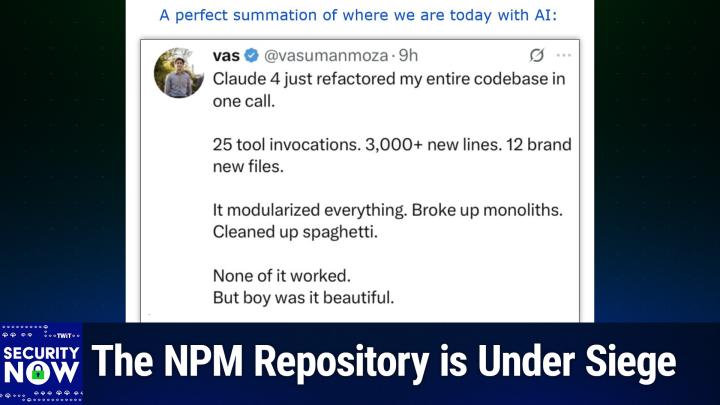
And a few years go by and the point is that code notoriously does not evolve well. It just kind of it gets stuff hung on it like barnacles and strange fungus and you know it. Just it's not good. And so it gets to a point, typically, where you say okay. At some point you say, okay, wait, we're having a hard time maintaining this because it just doesn't make any sense anymore and so we need to refactor it. It basically means sort of just saying, ok, hold on, this thing over here should really go over there, and this one function ended up with so many arguments that nobody knows what it does anymore. So let's break this up into multiple smaller pieces, each which has a clearer task. I mean, it's like a rethinking of something big and complex. Okay, so with that background, the title I gave this perfect snippet from Twitter or X was a perfect summation of where we are today with AI.
0:14:14 - Leo Laporte
All right Now, I have not seen this. I'm going to scroll up here and you should read it to yourself. Claude, just refactored my entire code base in one call 25 tool invocations, 3,000 plus new lines, 12 brand new files. It modularized everything, broke up monoliths, cleaned up spaghetti. None of it worked, but boy, was it beautiful.
0:14:37 - Steve Gibson
Yeah, yeah, I've seen that happen actually, oh yeah, this is just great, so, anyway. So this guy Vaz is his handle on Twitter or his name, his actual handle is a lot longer he dumped some massive code base into Cloud 4 and said fix this. And oh, it was so impressive. Of course it broke his code completely. Yes, he said. But oh, it was so impressive, Of course it broke his code completely. He said. But, oh, my God, it's just so pretty.
Now, yeah, doesn't work, doesn't work, but wow, if it did, that would be great. Anyway, yes, where we are today with our AI. Okay, so the mobile threat hunting security firm, iverify posted the news of their discovery under their headline Iverify uncovers evidence of zero-click, which is the worst kind mobile exploitation in the US, and at that point it's like, ok, that seems kind of generic, it could be whatever. Then we find out they wrote throughout late 2024. So, quite recently and early 2025, I verify detected anomalous activity on iPhones belonging to individuals affiliated with political campaigns, media organizations, ai companies and governments operating in the United States and the European Union. Specifically, we detected exceedingly rare crashes, typically associated with sophisticated zero-click attacks via iMessage, an exploitation technique previously unobserved in any systematic way in the United States. Subsequent forensic examination of several of these devices ultimately revealed a previously unknown vulnerability in the imagent I-M-A-G-E-N-T, the imagent process you know image agent, so they crunched it together process which, owing to its relative position in the operating system and its functionality, would provide attackers a primitive for further exploitation. This vulnerability was patched by Apple in iOS 18.3. We've dubbed this vulnerability nickname because it's taking advantage of an apparent flaw in iMessage's nickname functionality. They said.
In the course of our investigation, we discovered evidence suggesting, but not definitively proving, this vulnerability was exploited in targeted attacks as recently as March of this year. Specifically, we learned that Apple sent threat notifications to at least one device belonging to a senior government official in the EU on which we saw the highly anomalous crashes. So some correlation there. We don't know about causation associated with successful exploitation, specifically the creation and deletion of iMessage attachments in bulk within a matter of seconds on several occasions after an anomalous crash. Again, that's not normal. We only observed these crashes on devices belonging to extremely high-value targets and these crashes constituted only 0.0001% of the crash log telemetry taken from a sample across 50,000 iPhones.
They said, while this evidence does not definitively prove exploitation, it is nonetheless difficult to ignore and merits a public discussion, particularly in light of signal gate. Our findings suggest it doesn't matter what channel is being used to communicate. If the device itself is compromised and of course, that's what we've been saying all along. Right, you know, do you may have a even with with signal, if, if you've got a compromise in the device, it's before it's encrypted and after it's decrypted on the device. Our findings suggest it doesn't matter what channel is being used to communicate it. The device itself is compromised. Attackers have access to all conversations, regardless of whether those happen over signal, gmail or any secure application, excuse me. This is why it's crucial that organizations on the front lines of digital conflict, including the US government, adapt their mobile security models to face modern threats.
Our findings have been vetted by multiple independent third parties, including iOS security experts such as Patrick Wardle from the Objective by the Sea Foundation, who have confidence in our conclusion that mobile compromise is real, not academic or hypothetical, and that it's happening here in the United States. So what exactly are those findings? So far, we've observed six devices total that we believe were targeted for exploitation by this threat actor, four of which demonstrated clear signatures associated with nickname and two which demonstrated clear signs of successful exploitation. Interestingly, all of the victims had either previously been targeted by the Chinese Communist Party, the CCP, meaning they were confirmed to have also been targeted by Salt Typhoon meaning they were confirmed to have also been targeted by Salt Typhoon. They were engaging in business pursuits counter to or of particular interest to the CCP, or they had engaged in some sort of activism against the CCP. We don't have enough evidence, they wrote, to make clear attribution or a full view of an exploit chain, but the circumstantial evidence could indicate the CCP. So how does it work? Iphones allow you to set a nickname or avatar for numbers in your contact list.
The vulnerability is likely triggered by sending repeated, rapid-fire nickname updates to iMessage, which results in a use-after-free memory corruption. And of course, we, just in the last few months, we've extensively looked at the idea of well, of what is use-after-free and how a race condition could cause something that has been freed to get used before the access to it has completely disappeared. They wrote, this makes nickname a good candidate for a primitive to pivot off of as part of a longer exploit chain. We believe this vulnerability correlates with successful iPhone exploitation due to four concurrent factors. First, the extreme rarity of these specific crash patterns less than 0.001% of all crash logs. Second, their exclusive appearance on devices belonging to high-value targets appearance on devices belonging to high-value targets. Third, similarity to crash patterns seen in previously known spyware attacks. And finally, evidence of successful exploitation, including the receipt of at least one Apple threat notification proximal to the observed behavior and evidence of cleaning behavior. So is it still active? Differential analysis reveals the vulnerability was patched in the iOS 18.3.1 release. However, nickname could be one link in a larger exploit chain. It's possible that there are other elements of the exploit chain that are still active, which is why we're only speaking about the link in the chain that has definitively been patched. We provide a full technical analysis and look forward to sharing any additional material findings when our investigation concludes.
I've got a link in the show notes to their full technical report, which is extremely thorough, and it's important to disclose that Apple is actively contesting this, although boy I mean, the evidence surely does point at this. Axios reported Apple has fixed the flaw which was present in iOS versions through 8.1.1, but disputes that it was ever used to hack devices. Ivan Krstic, head of Apple security, engineering and architecture, said in a statement we've thoroughly analyzed the information provided by iVerify and strongly disagree with the claims of a targeted attack against our users. Kerstic added Apple confirmed the underlying nickname bug but said its own field data from iPhones points to it being a quote conventional software bug that we identified and fixed in iOS 18.3. He said iVerify has not responded with meaningful technical evidence supporting their claims and we are not currently aware of any credible indication that the bug points to an exploitation attempt or active attack. We are constantly working to stay ahead of new and emerging threats and will continue to work tirelessly to protect our users.
Okay, so the results are, at best, ambiguous On the Iverify side. You know, if it walks like a duck and quacks like a duck, you know which this flaw certainly did then it really would be reasonable to conclude that it's probably a duck. But, as we have observed and talked about long ago, back when Kaspersky discovered some of their iPhones containing very similar malware, the very fact that iPhones have been so tightly locked down actively thwarts the type of post-exploitation forensic analysis that would allow third parties like iVerify to be able to dig more deeply and to help put pressure on and and you know, kind of keep Apple honest, if indeed they were not already being. You know I mean Apple certainly doesn't want this to be true, boy, but the the circumstantial evidence, which you know is circumstantial because it's the only evidence you can get because these iPhones are so well protected. The trouble is that the stakes in all this, as we know, have been raised to such a high level.
Iverify referred to Signalgate in their posting, reminding us of the threat that high-level classified military operations planning was now known to have been conducted on non-secured civilian smartphone hardware. They didn't identify who these people were that were attacked, but they were explicit about saying individuals in the US, very high value targets in the United States. They ended their disclosure with an important reminder. Iverify did. They wrote iVerify recommends that high risk users keep their phones updated and turn on Apple's lockdown mode, which is designed to guard against spyware.
I verify COO Rocky Cole said that it's likely that lockdown mode would have prevented these potential infections, and so that's just a reminder about that, given that all the evidence continues to show you know just consider last month's pwn to own competition against fully patched systems that we do not still do not currently have the technology or capability to perfectly secure our devices, you know so having a bifurcated feature set where fewer features can be offered optionally to obtain greater security makes all kinds of sense after observing that 80% of their Chromium-based browser's security problems were being discovered in the just-in-time compiler, and with computers having become so fast today that the just-in-time compiler optimization is way less necessary than it once was. So, as we recall, they did some experiments where they experimentally turned it off in Edge and nobody noticed, and so they thought well, let's just leave it off, because we have a much more secure browser with it that way. So, anyway, no one's ever going to know.
There was some reporting I think it was last week or the week before where somebody that I was referring to had made the comment that, while we don't get details from Apple, they do keep fixing things and rebooting our phones. And oh, it was about the, the whole jailbreak, the, the evolution in jailbreaking and how it was now much less feasible to like certainly not as a hobby, you know offering jailbreaking services. Those days are gone, um, but the point being, you know apple is still releasing super critical, important updates. Uh, they don't tell us why or how or what, but they're happening.
0:29:27 - Leo Laporte
So it feels like also, if you really are a high risk subject, you shouldn't be using a consumer grade smartphone to begin with right.
0:29:35 - Steve Gibson
Yes, yeah, yeah, as we covered at the time it was I think it was Obama who was very upset that they took away his Blackberry. They took his Blackberry away. He's like hey.
0:29:50 - Leo Laporte
But that's what our security agencies do. Is they create hardened devices for this purpose?
0:29:56 - Steve Gibson
Yeah, and they're much less fun to use.
0:29:59 - Leo Laporte
Yeah, I'm sure. Yeah, of course they are.
0:30:01 - Steve Gibson
Yeah, it's just they don't have all the bells and whistles and goodies, because every extra goodie is one more opportunity for exploitation, as we well know. Okay, so I've got two quick bits that should serve to remind us and that's just why I'm doing this that the open source library system is more or less under constant attack, which is, you know, leo, where we say why we can't have nice things, because really, you know, gosh. Okay, so the node JavaScript package manager, npm, the, the, the, the facility. Its facility description reads, just to remind everybody relied upon by more than 17 million developers worldwide, npm is committed to making JavaScript, of JavaScript, code sharing and, with more than 2 million packages, the largest software registry in the world. Our other tools and services take the registry and the work you do around it to the next level. Great.
0:31:21 - Leo Laporte
And, of course, claude Code is installed installed, as are many tools, through NPM, Right. So if you're doing vibe coding, you're probably using NPM.
0:31:32 - Steve Gibson
And I mean the concept of a huge repository of useful libraries where you can say, oh, I need a regex parser, grab it from here. Oh, I need a background log writer, oh, grab it from there. And you piece together a package using the well-intentioned and hopefully proven work of many other authors in order to glue together solutions much more easily. Unfortunately, its openness is also its challenge. The first piece of news that caused me to pause here was 84 malicious NPM packages were discovered and taken down last week. The advisory said check out the GitHub Security Advisory Portal for more details.
This also includes two packages spotted by Socket that would wipe production systems Almost as well as an AI can Nasty yeah, Almost as bad as asking AI to refactor our code, please. It used to work. I hope there's an undo on this. The second piece of news was a threat actor has compromised 16 NPM libraries from the GlueStack UI framework. The attacker compromised a GlueStack admin's account, adding a remote access trojan to the libraries, and pushed updates on friday. The affected packages are extremely popular and have almost one get this leo 1 million weekly downloads. Akito security says the attacker is the same threat actor behind another supply chain attack on the rAND user agent package last month.
0:33:29 - Leo Laporte
Oh we talked about that, yeah.
0:33:30 - Steve Gibson
Yeah, and I have a snippet from KetoSecurity's posting. In the show notes they note active NPM supply chain attack one million weekly downloads. Supply chain attack 1 million weekly downloads. They wrote today we uncovered a rapidly evolving supply chain attack targeting glue stack packages on NPM. More than 15 packages compromised so far, nearly again 1 million weekly downloads.
Malware includes a full-featured remote access. Remote access trojan lovely abbreviation is rat. Of course. The latest package was compromised just one hour ago before their one hour previous uh, you know, before their posting. Wow, the same threat actor behind the rand user agent attack is now targeting UI-focused packages like at react-native-area-button and at gluestack-ui-utils and more.
The malware gives attackers the ability to run shell commands, upload files, persist across even after update. I'm sorry. Persist access even after update, I'm sorry. Persist access even after updates. This could have a massive impact, particularly for mobile developers using React Native. So developers, check your dependencies now. Security teams review access logs for anything suspicious. They said they finished. We're tracking this live so we will give updates. So you know this is another PSA. In this case it's a programmer service announcement reminding and cautioning all of our listeners who may have be availing themselves of the true value I mean this is the problem is this stuff is really valuable, so there's a strong interest in going there and using it this true value of shared, open libraries. To nonetheless always remain vigilant and aware that not everyone who places code there is motivated by altruism.
0:35:44 - Leo Laporte
Are there there silly question as libraries like this for assembly language, any assembly language package repositories?
0:35:53 - Steve Gibson
in the old. It's funny because there's never been a market, believe it or not, there there were. In the early days there were a couple assembly language libraries like macro libraries or something.
Yeah, and the floppy disk and later a CD bound into the back cover, and it was like some well-meaning programmer sat down and wrote a toolkit. Here's a bunch of things to put text on the screen. Here's a bunch of sorting routines here on the screen. Here's a bunch of sorting routines. Here's a you know this, this and that. Just sort of a hodgepodge. But after selling two copies that the publisher decided not the gibson by them both.
0:36:37 - Leo Laporte
Okay, you know, that's one of the reasons I like common lisp. There's nobody messing with a lot with the common list package libraries. Uh, there's a good one called quick lisp, there's a new one called ultra lisp, but I don't think attack it's not a target.
0:36:52 - Steve Gibson
Rich environment, shall we say no, it's why I kept my realtor on windows 98 for so long yeah because she was worried about viruses. And I said judy, you know you're, you have different dna in your computer. Viruses don't know they look at that go.
0:37:08 - Leo Laporte
Where am I? They don't care. It's like I don't want this person um time for a break.
0:37:17 - Steve Gibson
I'm gonna wet my whistle and then we're gonna look at what happened with comcast and digital realty. I didn't, I didn't know about Digital Realty. They're a massive data center provider. Like it turns out that AWS and Google and those guys, they subcontract their space.
0:37:38 - Leo Laporte
That's a good business If you think about it. Yeah, you want to make money. Don't be a gold miner. Be the guys who make the picks and shovels. Yeah, we'll get to that in just a second.
But first a word from Bitwarden. You know I love talking about Bitwarden, the trusted leader in password management. Yes, but of course we got to include passkeys. Now All my passkeys are in Bitwarden. I am so thrilled More and more sites are using Passkeys. It makes me so happy.
They're also good for secrets management. If you're a developer, you know you have a lot of API keys and secrets and stuff. And Gosh, how close have you come to committing it in public to GitHub? Right, I know you have, because so many people do and you've stopped. But if you store them in Bitwarden, you don't have to worry about it. Ssh keys too. Bitwarden is consistently ranked number one in user satisfaction by G2 and software reviews more than 10 million users across 180 countries and this is something maybe you didn't know. Of course, we know Bitwarden is great for individuals 50,000 businesses too. It's great in business.
Oh, and if you're traveling, bitwarden password manager can make your travels safer and easier. Do what I do Add your passport to your vault for easy access to I don't know tax-free shopping. Secretly share your hotel or locker code with your travel partner. There's a lot of stuff. As you're traveling around, you'd want to keep on your phone. You want to keep with you, but you don't want just anybody to see it. I got my driver's license, my social security, my passport it's all in Bitwarden.
Let's say you're at an airport or hotel and you want to use the wi-fi. Take proactive steps to secure your data. Encrypt it right with bitwarden. Protect against cyber threats and, by the way, only connect to the official airport high wi-fi network, okay, uh, and if you're using bitwarden, turn on autofill for credentials, because then you don't have to worry about automatically filling a phishing site with your password. That's a very nice feature. Prevent your device from automatically reconnecting to public Wi-Fi but forgetting the network in your device's settings. This is just good advice after use. Avoid downloading files or clicking unfamiliar links or accessing sensitive personal or work accounts while connected to public Wi-Fi. It has nothing to do with Bitwarden, but you know what they care about you. They want to keep you safe.
Students are now mostly online, right, they spend learning and homework, but also socializing and gaming. I think kids nowadays. 90% of their time is online. And with all this comes, of course, many accounts, many passwords, and you know you may have a smart student in your family or in your friend group, even if the student knows the security risks. A lot of times convenience takes precedent. Kids, you know. They feel invulnerable.
Make sure the young people in your life have a password manager like Bitwarden. It generates unique, strong passwords that are only used once on every site. Students can use them, access them from any device. And, by the way, bitwarden is free for individuals because it's open source. Now Steve and I, I think, pay the $10 a year for the supporter badge, but it's free forever for individuals. Unlimited passwords, pass keys, hardware keys, all of the features I just talked about. And, by the way, tell the kids this is going to help your job prospects when you get out of school.
Cybersecurity skills are in high demand. Potential employers will appreciate employees with a solid understanding of password management. You know, if I were an employer, I'd put that on the interview. Do you use a password manager? I would certainly want to know that before I hired anybody. And good news, in business and anywhere. Bitwarden setup only takes a few minutes. You can import from most password management solutions automatically and, as I always hammer in in, I think anytime you use cryptography it should be open source.
Bitwarden is fully open source. Gpl licensed the codes on github. Anyone can look at it and, of course, they always every year bring in third-party experts to to assure you that it's exactly as safe as they can make it. They meet sock to type 2, g 2, gdpr, hipaa, ccpa compliance, iso 27001-2002 certs. Get started today with Bitwarden's free trial of a team or enterprise planner. Get started for free, across all devices and individual user. Get those students, the young people in your life, an account. Do them a favor, tell them it'll help you get hired bitwardencom slash twit in your business. If somebody, if an employee, future employee, prospective employee says I use bitwarden, you know they're good bitwardencom slash twit. We thank them so much for their support of the good works that steve here at Security Now.
0:42:40 - Steve Gibson
Okay. So I was scanning reports of a possible undisclosed breach of Comcast and the major data center enterprise digital realty when I encountered this comment, quote inside two major US telecomcom operators incident response staff leo, are you sitting down? Incident response staff have been instructed by outside counsel not to look for signs of salt typhoon as a comcast user.
0:43:17 - Leo Laporte
We're using it right now.
0:43:19 - Steve Gibson
I'm a little disturbed perturbed Inside two major US telecom operators. Incident response staff have been instructed by outside counsel not to look for signs of salt typhoon, said one of the people declining to name the firms because the matter is sensitive, because he wouldn't want to find it. Gee, you think so that's what has evolved from the intersection of big business, cyber security and legal accountability. Uh, the reporting is from next gov's cyber security reporter. Cybersecurity reporter. The headline of the story was US agencies assessed Chinese telecom hackers likely hit data center and residential internet providers. Now this headline teases us with the phrase US agencies, which begs the question which US agencies made this assessment? To that end, the reporting says two US security agencies listed mass media provider Comcast and data center giant Digital Realty among companies likely ensnared by a Chinese hacking group previously found inside major US and global telecom operators, according to three people familiar with the matter. So triple sourced reporting. And guess who those two US security agencies are? The National Security Agency yes, our NSA, they wrote, made the determination that Comcast had likely been impacted by the group known as Salt Typhoon. According to two of the three people, the Cybersecurity and Infrastructure Security Agency, our illustrious CISA, cataloged digital realty as being potentially compromised. The third person said the people spoke on the condition of anonymity to discuss the matter's sensitivity.
Salt Typhoon breached major telecom carriers in a global multi-year espionage campaign uncovered last year. Over time, news trickled out about the scope and scale of the incident, which was first reported by the Wall Street Journal. The hacking unit is part of a broader syndicate of state-backed groups tied to different military and intelligence arms of China's central government. The typhoon moniker comes from a Microsoft naming convention for Beijing-linked cyber actors. Such intrusions, especially into a data center environment, could give the hackers a potentially far deeper foothold into infrastructure supporting the world's information service providers than previously known. This is what was really creepy about this. I hadn't really considered that data centers offer a different view than telecom providers. They wrote. The agency's assessments have not been previously reported.
There's uncertainty among officials about who was impacted by salt typhoon. Various agencies across the US government are in possession of lists of confirmed or potential victims, but it's not clear if the tallies are consistent with each other, adding to confusion about who may have been accessed, targeted or marked for investigation. Cisa, for instance, is in possession of a list of both telecom and information technology companies, but an FBI tabulation shows different entities. And here it comes, they wrote. Making investigations into the breach more complicated is that multiple telecom providers have invoked legal strategies to protect themselves from disclosing compromise by the hackers, and this is what I quoted that just brought me up short. Inside two major US telecom operators, incident response staff have been instructed by outside counsel not to look for signs of salt typhoon, said one of the people declining to name the firms because the matter is sensitive.
0:47:58 - Leo Laporte
Yeah.
0:47:58 - Steve Gibson
I bet it's so. Yes, now we have deliberate and internally formalized heads buried in the sand strategies in place, because employees, after all, may be deposed under oath. Be deposed under oath. I hope that any cross-examining council has the presence of mind to ask whether they were ever instructed by anyone to avoid looking for signs of external intrusion.
Not just are they aware of any signs of external intrusion. The article continues One of the sources said that, having been assessed as likely victims oh, and I should just mention it might be that the external counsel knows that that counsel, the cross examining counsel, might ask them just that, were you ever instructed not to look? And that when you think about it, saying yes, I was instructed not to look is probably less damaging than looking and finding. That is it's like better to say, yeah, my boss has told me don't look, so, oops, I don't know. It's probably better not to know. I mean even to admit that you were told not to look than it is to be able to. You know, then, if you did look and then had to say, yeah, and I did find evidence that we were compromised, that, think about it that's probably more damaging. So what a world. One of the sources they wrote said that, having been assessed as likely victims, cisa representatives should have contacted Digital Realty and Comcast multiple times since December. It's not clear whether consistent back and forth communications were established. Cisa tends to initiate outreach to potential victims when it's believed their networks are compromised. According to another person familiar with the Cyber Defense Agency's notification process.
Now, of course, a new concern this year is that CISA has recently suffered a significant and controversial reduction in personnel as a result of the job cuts enacted by Doge. In the same way that it's impossible to prove a negative, it could be challenging to justify the presence of staff whose job is to prevent trouble. Right, it's like? Well, they're here to prevent trouble. Of course, this is the problem. This is a familiar problem. It's one that corporate CISOs also face, but on a government agency scale. In the case of CISA, someone challenges what are all those people doing over there? And to which the reply is well, they're keeping an eye on things, which is then followed by the difficult to defend challenge. So why do we need so many of them? Right, you know, I don't know. So, as all of our listeners will appreciate, sisa, as we've often said on this podcast, has been doing a surprisingly tremendous job since it really got rolling a few years ago. I've often commented that I've been surprised by how proactive and effective it has been, especially considering that it's a government agency. So I hope, I sincerely hope, these cutbacks will not compromise that. It's probably impossible to accurately gauge, since we cannot know how things would have been with a significantly smaller CISA. We'll just need to watch and see. The reporting continues. Writing.
A Comcast spokesperson told NextGov, quote We've worked with law enforcement and government agencies and have closely monitored our network. So this is Comcast speaking. We have found no evidence that Salt Typhoon has impacted our enterprise network. Unquote. An intrusion into either provider could carry significant national security risks. Comcast, they write, facilitates internet access for millions of users and businesses, while Digital Realty hosts troves of physical infrastructure used by telecom operators, cloud providers and governments to route global web traffic. A CISA spokesperson said as a policy, we do not comment on individual entities. The NSA, for their part, declined to comment and the FBI did not respond to a request for comment. Digital Realty did not return multiple requests for comment.
Nextgov reported in December that hundreds of organizations were notified. Hundreds of organizations were notified of potential salt typhoon compromise were notified of potential salt typhoon compromise. Last month, cyberscoop reported that CISA and the FBI devised a coordinated notification campaign to alert affected companies and help them deter the hacks, sometimes providing new data to them on an hourly basis. The FBI concurred with other agency assessments that the salt typhoon attacks, broadly speaking, are the most egregious national security breach in US history bya nation-state hacking group. Mark Rogers, a seasoned telecommunications cybersecurity expert, said quote a breach of Comcast and digital realty would confirm what many of us in the cybersecurity industry already suspected that the SALT campaign was broader than just telcos, and we have low confidence. The attackers have been evicted.
Nextgov obtained an internal CISA list of communications sector hardware and software products found to have been exploited by the China-linked hacking groups. Of several listed, one of those vulnerabilities first discovered in 2018, was found in microtik routers, and some of the software flaws exploited by Salt Typhoon were first disclosed in 2018, same year as the microtik router flaws. Mark Rogers said, something that isn't being talked about enough is that the initial way in which these attackers used were simple flaws, like eight-year-old vulnerabilities and credential theft. Instead of talking about ripping and replacing, we should be looking at why we aren't simply patching and maintaining our existing critical infrastructure. Eric Hanselman, the chief technology, media and telecommunications research analyst at S&P Global Market Intelligence, explained that, quote Chinese access into data center and co-location firms would provide the hackers with a different target set compared to messaging services operated by traditional carriers. Set compared to messaging services operated by traditional carriers. This is him speaking. The additional risk created would be their gaining the ability to monitor intra-service and intra-application communications traffic that does not normally traverse the internet backbone normally traverse the internet backbone. That could include storage traffic moving from co-location environments into cloud or traffic moving from hosted environments into on-premises infrastructure. That traffic might have less robust protections as it's not traversing the open internet. In other words, it might all be behind firewalls, so where we trust everybody inside behind the firewall.
Digital Realty, writes NextGov, has over 300 data centers. This was a surprise to me. Digital Realty has over 300 data centers across 25 countries and 50 metropolitan areas, including to a company marketing webpage. They list Amazon Web Services, google Cloud, ibm, microsoft and NVIDIA among their clients. The company is considered one of the largest data center co-location providers in the world, housing the physical systems where cloud and telecom networks exchange data, and they're believed to have been compromised. Eric Hanselman said we can reasonably assume that these attackers already have sufficient access into Internet infrastructure and are looking to expand the depth with which they can monitor other activities that are taking place within data center environments. Comcast's broadband and data and cable customer base is around 51 million, while its total wireless customer count totals around 8.1 million according to recent earnings data.
It's widely believed that Salt Typhoon has still not been excised from telecom systems, despite public statements from companies saying otherwise. On the other hand, they've been told not to look too closely. On Thursday, they write. Well-known Republican Senator Josh Hawley said in a Senate Homeland Security Committee hearing that the hackers are still inside. He said quote if a foreign actor chose to concentrate on any member of the audience here. We were told behind closed doors, of course, but what we were told is that foreign actors basically have unlimited access to our voice messages and our telephone calls. President Donald Trump, vice President JD Vance and a range of US officials had their calls and texts directly targeted by Salt Typhoon hacks. The cyber spies accessed providers' lawful intercept systems used to comply with government orders requiring access to communications metadata for law enforcement investigations. Wow and remember that, as we previously saw, salt typhoon's apparent way into these major telecom backbone providers was not rocket science nor advanced pwned-to-own-style elite hacking. It was simply that someone somewhere within telecoms sprawling and largely out-of-control infrastructure, somewhere somewhere there were older unpatched systems still online with known vulnerabilities, the reporting says.
A spokesperson for the House China Select Committee said in an email. If these reports are accurate, they point to yet another serious and deeply concerning example of the Chinese Communist Party targeting America's digital infrastructure, and noted that quote. The panel has repeatedly warned about the CCP's efforts to exploit access points into our communications networks and this apparent breach reinforces the urgent need to harden our defenses. In March, the House's Homeland Security Committee chair, republican Representative Mark Green of Tennessee, sent a request to DHS asking the agency to transmit internal documents about Salt Typhoon and another Chinese hacking unit, volt Typhoon, green said in a statement to NextGov. Quote every new detail that emerges surrounding the Salt Typhoon intrusions teaches us the lengths Chinese-backed hackers will go to undermine the integrity of our critical infrastructure, our US sovereignty and the privacy of Americans. Green said this is in reference to recent testimony from DHS Secretary Kristi Noem saying CISA is lacking detailed information about the telecom hacks.
Okay, it's difficult not to wonder whether some additional manpower at CISA might help. Green added my colleagues and I on the committee share this concern, which is why we sent a letter in March to examine the previous administration's response to the Volt and Salt Typhoon intrusions. Now I was about to comment on that, that is, that they were sending a letter about the previous administration's responses. When I saw that NextGov's reporting had already done so, they wrote. The Cyber Safety Review Board, a DHS body that was dismissed at the start of the Trump administration, was in the middle of investigating the Chinese telecom hacks.
Lawmakers have called for it to be reinstated. Cisa has also been mired in budget plans to slash significant parts of its workforce and operations, so I hope that CISA will be able to recover and rebuild whatever effectiveness it may have lost. It seems pretty clear that, unfortunately, private industry is unwilling to expend the cost and effort required to fully secure its own business operations. You know they'd rather have their attorneys say oh don't. You know, don't tell anybody, but we'd like you not to look too closely because you could be put under oath and cross-examined, and we would. That apparently needs to be imposed by the government, so let's hope we get that.
Matthew Green, our illustrious scriptographer, says well rewritten in Rust, end-to-end encrypted XChat DM, you know, direct message facility and had decided that it was no better than the old one. He shared Elon's declaration about how it was written in Rust and unfortunately it turns out it's still written in C and C++. Since then, matthew Garrett's posting came to the attention of another Matthew. This Matthew was none other than the renowned Johns Hopkins University cryptographer, matthew Green. This Matthew is well known to this podcast, so this Matthew's posting last week, titled a bit more on Twitter slash X's new encrypted messaging is of interest. Matthew's post is longer than we need and I've included a link to the entire thing in the show notes, so I'm just going to share his relatively short bullet pointed introduction and summary. It'll really tell us as much as we need. So he wrote. Matthew Green posted Matthew Garrett has a nice post about Twitter X's new end-to-end encryption messaging protocol, which is now called XChat.
The TLDR of Matthew's post is that from a cryptographic perspective, xchat is not great. The details are all contained within Matthew's post. Matthew Green writes but here's a quick TLDR from Matthew Green. But here's a quick TLDR from Matthew Green. First, there's no forward secrecy. Unlike Signal Protocol, which uses a double ratchet to continuously update the user's secret keys, the XChat cryptography just encrypts each message under a recipient's long-term public key. The actual encryption mechanism is based on an encryption scheme from Libsodium.
Second, user private keys are stored at X. Xchat stores user private keys at its own servers. To obtain your private keys, you first log into X's key storage system using a password such as a PIN. This is needed to support stateless clients like web browsers and, in fairness, he writes, it's not dissimilar to what Meta has done with its encryption for Facebook, messenger and Instagram. Of course, those services use hardware security modules. And third, he says X's key storage is based on juice box. To implement their secret storage system, xchat uses a protocol called juice box. Juice box shards your key material across three servers so that, in principle, the loss or compromise of any one server won't hurt you. Okay so, and we've talked about key sharing schemes in the past, where a key is broken up into pieces so that no one person has the entire key and you see, you need some some number of individuals to all come together in order to reassemble the original key. This sounds like what juice box is doing. So our Matthew Green writes.
Matthew's post correctly identifies that the major vulnerability in X's system is this key storage approach. If decryption keys live in three non-HSM servers that are all under X's control, then X could probably obtain anyone's key and decrypt their messages. X could do this for their own internal purposes, for example, because, he writes, their famously chill owner got angry at some user. Their famously chill owner got angry at some user, or they could do it because a warrant or subpoena compels them to. If we judge XChat as an end-to-end encryption scheme, this seems like a pretty game-over type of vulnerability, and he says so in a sense. Everything comes down to the security of juice box and the specific deployment choices that X made Since Matthew wrote his post, writes Matthew Green.
I've learned a bit more about both of these In this post. I'd like to go on a slightly deeper dive into the juice box portion of X's system. Deeper dive into the juice box portion of X's system. This will hopefully shed some light on what X is up to and why you should not use XChat. So the bottom line is that Matthew Green concurs with Matthew Garrett, which is to say that no one should consider any encrypted messaging system to be securely end-to-end encrypted when such a system externally stores, on its users' behalf, their private keys.
Now, a perfect example is Apple's currently controversial advanced data protection. What it explicitly does is give its users discretionary control over whether or not a copy of their private key is also retained by Apple. Allowing that enables additional features, but it also enables Apple to similarly respond to court-ordered subpoenas in the United Kingdom and all of your devices are running Apple OSs that support ADP. You know iOS or iPad OS 16.2 or later in the case of iPhone and iPad then you can turn that on and a new private key Apple has never seen will be created and shared only among your iDevices. So no one should confuse Apple's state-of-the-art encryption technology and, for that matter, signals with what Elon is peddling. I'm not suggesting that anyone necessarily needs end-to-end encrypted DMs on X, but everyone should be aware that they're not really available there to the same degree they are elsewhere. Nor, for that matter, are they available on Facebook Messenger or Instagram, which, as Matthew Green notes, similarly stores its users' private keys in their own data centers in order to enable the features that are necessary.
Leo, we're at an hour in. I want to talk about what we learned about Telegram. Let's take our third break.
1:11:35 - Leo Laporte
Indeed, we shall Thank you, steve. Indeed, we shall thank you, steve. Uh, this is a good time to mention that this portion of security now is brought to you by material, because you know what, when it comes to security, you need security in your email, don't you? Material is the multi-layered detection and response toolkit for email. Nowadays, we all have a cloud office right. We use Google Workspace, maybe use Microsoft's 365. It's the heart of your business. But the problem is traditional security tools don't really know about that. They treat email and documents as kind of afterthoughts, which means your most critical assets are exposed.
Material transforms cloud workspace protection with a revolutionary approach. It goes beyond traditional security paradigms. Dedicated security for modern workspaces ensures purpose-built protection specifically designed for Google Workspace and Microsoft 365. You get complete protection across the entire security lifecycle. That means defending your organization before, during and even after potential incidents, not just attempting to block them or prevent them. Material allows you to scale security without scaling your team, because your team is now using intelligent automation to multiply their impact. It's a force multiplier. They provide security that respects how people work, eliminates the impossible choice between robust protection and productivity, and it's all very cleverly done, turns out.
Google Workspace and Microsoft 365 have very robust APIs that allow material to protect you without having you send your data. Through material, material delivers comprehensive threat defense through four critical capabilities Phishing protection they have AI, power detection that identifies sophisticated attacks again API-based. They also help you with data loss prevention. They have intelligent you with data loss prevention. They have intelligent content protection and sensitive data management. They will help you with your posture management, identifying misconfigurations and risky user behaviors and, of course, identity protection. Comprehensive control we were just talking about it over access and verification.
You know who uses Material Figma. I love this. The head of security at Figma. They're a design firm, right, he said, quote it's rare to find modern security tools with a pleasant, usable UI. Being at Figma, we're obviously attracted to well-designed interfaces and Material's interface was just so smooth and so slick, and that's because of their secret sauce this API-based protection. From automatic threat investigation to custom detection workflows. Material converts manual security tasks into streamlined, intelligent processes. It provides visibility across your entire digital workspace, which means your security team can focus on strategic initiatives instead of endless, pointless, sometimes alert triage. Protect your digital workspace, empower your team, secure your future with material. Go to materialsecurity. You can learn more and book a demo. That's materialsecurity. This is a modern way to protect yourself and very, very effective in this modern time where we're all kind of living in the cloud Materialsecurity.
1:15:05 - Steve Gibson
Thank you, material for supporting Steve Gibson back to the show I'm so jealous of that top level domain. But isn't that great dot security? It's how much insanely expensive. Yeah, of course, I think it's like 25 000 a year I mean, that's nothing dude crazy isn't that, what would you? Do grcsecurity? I don't know I'm no, I don't really want it. I love grccom.
1:15:28 - Leo Laporte
It's pretty darn good yeah, you know, those three-letter tlds are are even more expensive.
1:15:33 - Steve Gibson
Yeah oh, I get offers all the time. Sure, yeah, okay. So I also recently mentioned the telegrams. Encrypted privacy had recently been called into some question when russian citizens when Russian citizens who were supporting Ukraine, naughty Russians were being arrested and convicted by Russia's FSB. It turns out that the culprit might not be any weakness in Telegram's it's a little questionable encryption, but it's probably good enough. It could instead be a compromise of its network infrastructure. In other words, there may be some leakage of messaging metadata, and we've talked about metadata a lot. We know that it can be notoriously difficult to prevent metadata leakage. You know it's why we've gone to all the lengths of creating the Tor network. And when it turns out, you couple that with the fact that Telegram's network infrastructure appears to be directly under Russia's control. That's a problem for privacy. So this could explain how people are getting in trouble for who they contact without needing to see inside their messages.
I'm not going to spend any more time on this, because this brings us to another of those. You know I wouldn't use Telegram in any event if you really care about privacy, but apparently it is worth noting that Telegram's networking infrastructure is entirely under the control of at least Russia sympathizers. I've got a link to extremely detailed coverage of this in the show notes for anyone who wants more. The report is titled Telegram, the FSB and the man in the middle. The FSB and the man in the middle. The technical infrastructure that underpins Telegram is controlled by a man whose companies have collaborated with Russian intelligence services. So, again, who you connect with can be just as damning as what you say during that connection, be just as damning as what you say during that connection, especially if you're in Russia and you're connecting to a telegram contact that supports the Ukraine, apparently. So don't do that. Okay, Leo, here's where I need to control my language Bleeping computer.
1:18:11 - Leo Laporte
I want to hear what this AI figured out about your opinion about Microsoft. Oh yeah, we're going to get there in a second.
1:18:26 - Steve Gibson
Bleeping Computer brings us the news that starting in July, so next month, starting next month, sometime next month Microsoft Outlook will be blocking two additional file types, bleeping Computer reported. Microsoft announced it will expand the list of blocked attachments in Outlook Web and the new Outlook for Windows starting next month. The company said in a Microsoft 365 Message Center update that Outlook will block library-ms and search-ms file types beginning in July. Microsoft said quote as part of our ongoing efforts to enhance security in Outlook Web and the new Outlook for Windows, we're updating the default to the blocked file types list. Windows library files library-ms, which define virtual collections of folders and files in the Windows file system, were used earlier this year in phishing attacks targeting government entities and private companies to exploit a Windows vulnerability. Cve-2025-24054,. That exposes NT land manager hashes. It exposes NT land manager hashes.
Okay, now let me just pause here for a moment to say that if I didn't know that we have many young people listening to this podcast with their parents while they're on their way to school in the morning, as well as many other settings, and that those parents have grown to trust me to keep the colorfulness of my language under control for those young ears, at this point, I would loudly expand upon the well-known abbreviation WTF. Why in the world Microsoft would have ever, by default, ever by default, ever considered allowing any email client which inherently think about it, inherently presents as large an attack surface as any web browser and which is being constantly instantly bombarded with unwanted and potentially malicious content, to handle dot library hyphen, ms files, which we are now told define virtual collections of folders and files? You know, I've been in this business, as have you, leo, since long before it was a business, as have you, leo, since long before it was a business and I've never seen a library-ms file. How is it that this is a file type that all Outlook users' clients should have ever been able to open, and how can that possibly be addressing the need that anyone has in email?
It's just utterly unbelievable to me, as it should be equally unbelievable to anyone trained in the practice of cybersecurity. How many times have we talked about the security benefit that flows from first blocking everything by default and then only allowing selected, known, safe and needed content through any security perimeter? Email is a security perimeter. This is unbelievable. I'm so surprised by this because any rational, security-aware design would never be permitting the reception and handling of, by default, any wacky file type somebody at Microsoft might come up with in the future, which is apparently what happened here, because that file type didn't exist in the past.
1:22:56 - Leo Laporte
Ah, that's why they didn't block it Okay.
1:22:58 - Steve Gibson
But they shouldn't be. They shouldn't be. Unless we know it's bad, we're going to let it through.
1:23:04 - Leo Laporte
You're saying it should be a whitelist, not a blacklist.
1:23:07 - Steve Gibson
Yes, yeah, it's a security perimeter. Email is getting bombarded with all kinds of crap. Okay, Take a deep breath, Steve. So what about this other file type? Uri protocol handler has also been exploited in phishing and malware attacks. Get this since at least June of 2022.
Oh, that's a long time, that's three years, yes, when Hacker House co-founder and security researcher, matthew Hickey, found that it could be used to automatically launch Windows search windows on recipients devices to trick them into launching malware when chained with a Windows support diagnostic tool. That's MSDT remote code execution vulnerability, cve 2022 3190. Well, isn't that just beachy. What year, what year was that? Oh yeah, 2022. So it only took microsoft what three years to finally announce that next month, not not not this month. Next month they plan to start blocking this other unneeded and clearly abuse prone file extension. Bleeping Computer reports that in Microsoft's announcement. Microsoft wrote, quote the newly blocked file types are rarely used, except by hackers and malware and bad guys who just love using them. So most organizations, they say, will not be affected by the change. However, if your users are sending and receiving affected attachments yeah, like, when did anyone ever get a search-ms attachment in email? They will report that they're no longer able to open or download them in Outlook Web or the new Outlook for Windows Apparently, the old Outlook for Windows is screwed.
You're still going to get those. No action is required if your organization does not rely on these file types. If your organization does rely on these file types, you've got a different set of problems. The update will automatically apply to all OWA mailbox policies in your organization. If your organization needs to allow these files, you can add them back to the allowed file types property of your users.
Owa mailbox policy objects. Before the rollout why not just have that always been that way? If your organization needs one of these wacky no one has ever heard of them file types, then turn them on for your people and good luck to you, rather than exposing the rest of the world to this nonsense. Bleeping computer that explains you can find the complete list of blocked Outlook attachments it's apparently very short list. On Microsoft's documentation website, enterprise users with a Microsoft Exchange server account can ask Exchange server administrators to adjust security settings for their mailboxes to accept attachments blocked by Outlook if they can't be shared as an archive using a different extension or using OneDrive or SharePoint. Broader effort, apparently, which Microsoft has just initiated, to remove or secure and turn off Office and Windows features that have been abused and exploited to infect Microsoft customers with malware. Wow, what a concept.
I'm shocked yeah we'll see what AI thinks about this rant. What AI thinks about this rant? It started in 2018 when Microsoft expanded support for its anti-malware scan interface, amc, to Office 365 client apps. Apparently, they haven't had anybody looking at this ever since 2018. Somebody woke up and said, oh look, let's add some more stuff to the AMSI to block access using Office WBA macros. Since then, the company began blocking VBA Office macros by default.
Another great jump a leap for security Disabled XL 4.0, xlm macros. I remember covering that Yay, introduced XLM macros. I remember covering that Yay, introduced XLM macro protection. We even gave it a nice name and started blocking untrusted XLL add-ins by default. Because what could an untrusted LLM do? Wow, microsoft also announced in May 2024 that it would. So. A year ago, it would kill off VB script and disabled all active x controls and windows versions.
Boy, you know, I don't know. Oh, again, it is truly I mean inexplicable that Microsoft has been so utterly lame about the security of their email clients on the desktop and in the cloud. The only rational explanation is this was all originally put in place by engineers who had zero training in security. Hubris is the only explanation for a policy of allow everything to run by default. It is the exact equivalent of having an allow-all firewall policy and believing that it could ever be secure to only block the dangerous ports. Nobody does that, haven't for a long time. Microsoft's just beginning to wake up to this and say oh look, three years ago people began exploiting the search-ms extension, which nobody has ever needed or uses, but which Microsoft says oh look, let's open that. My God, okay, as we were Take a deep breath.
1:29:56 - Leo Laporte
I mean, yeah, I can't think of any reason. I mean one thing would be that engineers say, well, you should just be able to send anything you want. Why wouldn't? Yeah, what?
1:30:01 - Steve Gibson
could possibly go wrong. All of our code is perfect. We never have any flaws.
1:30:07 - Leo Laporte
Just ignore those 125 critical updates that we had last month, every month, and the next 150 that we've got planned for this coming month.
1:30:17 - Steve Gibson
Really, those are just exceptions. Besides, none of those were dot search hyphen, ms. So you don't. You know, wouldn't have been, this wouldn't have helped anyway. It's unbelievable. I again that all should be turned off. And if, by some bizarre, for some bizarre reason, some enterprise has to send I don't even virtual folders and directories through email, what?
1:30:42 - Leo Laporte
Not through email, never.
1:30:43 - Steve Gibson
No, I mean, that's what this does. Yeah, Whatever that was, it's unbelievable. That was, it's. It's unbelievable. I'm just. I'm looking forward, leo, to october, when they stop messing with windows 10 and just will leave it alone, and then it can. It'll have a chance to settle down and then we can just keep using that. That'll'll be good. Okay, I don't need any more coffee, that's for sure.
As we were recording last week's podcast, Leo, you encountered the news of 40,000 cameras having been found online. Now, this raised a bunch of questions online. Now, this raised a bunch of questions, the first of which was probably what sort of exploit might have been needed to hack into and compromise such a huge inventory of internet connected cameras? And the answer, it turns out, is none. All 40,000 of these video cameras are simply online and wide open, viewable by anyone, anywhere, anytime. The news of this came from BitSight, an internet scanning company that offers to keep an eye on the IPs and ports of its own clients to let them know when anything like this might be happening to them. In BitSight's report, they wrote Welcome to 2025, where thousands of internet-connected cameras meant to protect us are actually putting us at risk. In our latest research at BitSight Trace, we found over 40,000 exposed cameras streaming live on the internet. No passwords, no protections just out there. We first raised the alarm in 2023, and, based on this latest study, the situation has not gotten any better. These cameras intended for security or convenience these cameras intended for security or convenience have inadvertently become public windows into sensitive spaces, often without their owner's knowledge. Anyone can buy one, plug it in and start streaming with minimal setup is likely why this is still an ongoing threat, and it doesn't take elite hacking to access these cameras. In most cases, a regular web browser and a curious mind are all it takes, meaning that 40,000 figure is probably just the tip of the iceberg. Okay for their key takeaways, they wrote. Bitsight Trace has found more than 40,000 security cameras openly accessible on the internet, allowing anyone to view their live footage.
The United States and Japan rank first and second for camera exposure. Most times, all that an attacker needs to spy on homes or even large organizations is just a web browser and the right IP address. We detected conversations on the dark web where bad actors are discussing exposed cameras. We scanned the entire internet for exposed HTTP-based and RTSP-based cameras. The United States leads the charge with roughly 14,000 exposed online cameras, followed by Japan, Austria, Czechia and South Korea. Given the high prevalence of exposed cameras in the United States, we also analyzed their distribution across each state. I grabbed the heat map both of the world and of the US, and what's curious is that the US map is not at all uniform. It shows that a huge preponderance of open cameras are located in California and in Texas, like way more than any other two states. It would be interesting actually to determine why. I have no idea. As I said, the distribution is extremely non-uniform.
Bitsight noted that not all cameras are bad. Some people stream beaches or birdhouses on purpose. But here's where things get problematic, they said. Residential cameras watching front doors, backyards and living rooms, Office cameras disclosing whiteboards and screens full of confidential information, factory cameras showing manufacturing secrets, even public transportation cameras streaming passengers' movements. By leveraging the intelligence gathered by our awesome cyber threat intelligence colleagues, we dug into dark forums where people openly discuss tools and tactics to find and abuse the content being exposed by these cameras. Even are some, even some even sell access. They said this isn't hypothetical, it's happening right now.
Then they finished their synopsis with a section titled what should I do to protect myself or my company? Their advice is what any longtime listener of this podcast would echo. They wrote if you have a security camera at home or manage surveillance cameras for your company, then taking the right precautions can make the difference between keeping your footage private and unintentionally broadcasting it to the world. Here are some simple but essential guidelines to ensure your cameras are secured. First, check if your camera is accessible from the internet. Try accessing it from a device outside your home network. If you can reach it remotely without logging in through a secure app or VPN, it's exposed. Second, change default usernames and passwords. Many cameras come with weak or publicly known default credentials. Set a strong, unique password. Third, disable remote access if you do not need it. If you only use your camera on your home network, there's no reason to allow outside connections. Fourth, keep its firmware up to date. Manufacturers often release security updates that fix known vulnerabilities. Regularly check for updates and install them. Additionally, they wrote if you manage security cameras in your organization, restrict access with firewalls and VPNs. Ensure that only authorized personnel can access camera feeds using a VPN or firewall rules that block access from untrusted sources. And finally, monitor for unusual activity. Set up alerts for unexpected login attempts.
It really would be interesting, I think, to follow up and track down a large set of those cameras to determine whether they are likely being deliberately shared publicly or may be inadvertently exposing parts to the physical, you know, like views of the physical world to a global audience that should not have access to it. The idea, you know like, of a corporate camera aimed at a conference rooms whiteboard is terrifying, you know. I mean, maybe they just think it's a security camera and don't realize that some configuration misstep, you know, allowed this thing to go out over the internet, but clearly the consequences could be devastating. Leo, we're an hour and a half in, let's take a break, and then I'm going to talk briefly about using Spinrite on an encrypted drive, share some feedback and then we're going to start talking about internet foreground radiation, All right.
1:39:43 - Leo Laporte
I hope you're enjoying the show. So far I certainly am, and we thank Steve for doing such a good job putting this all together, and we thank our sponsors who make it all possible this episode of Security Now brought to you by Drada. If you're leading risk and compliance at your company, you have our deepest sympathy. But you're probably wearing 10 hats at once, right? You're managing security risks, compliance demands, budget constraints, and it's hard to say one's more important than the other, right? And you're then, all the while, trying not to be seen as the roadblock that slows the business down.
But GRC isn't just about checking boxes. It's a revenue driver that builds trust, accelerates deals and strengthens security. That's why modern GRC leaders turn to deals and strengthens security. That's why modern GRC leaders turn to Drata, a trust management platform that automates tedious tasks, so you can focus on reducing risk, proving compliance and scaling your program. With Drata, you can automate security questionnaires, automate evidence collection, automate compliance tracking. Itives you more time to do whatever you want. You could stay audit ready with real-time monitoring. I mean, this just takes a huge load off your shoulders. It also will help you simplify security reviews. Auditors love Drada's Trust Center and you'll get AI-powered questionnaire assistance that makes it a snap to fill those questionnaires out. Instead of spending hours proving trust, build it faster with Drata. Are you ready to modernize your GRC program? Visit dratacom slash security now to learn more. D-r-a-t-a, dratacom slash security now this is the premier name in automating compliance, and, man, you deserve it, that's all I could say. You deserve the help. Dradacom slash security.
Now thank them for supporting security now when you talk to them. All right, steve, on, we go.
1:41:44 - Steve Gibson
So my tech support guy, greg, forwarded an interesting question about Spinrite which bears sharing, because its answer is not always intuitive and sometimes results in some confusion, as it did when it was recently posted over in GRC's web forums. Lee Garrison sent the email through Greg. Hi, steve, I need to run Spinrite 6.1 ona three terabyte partition which is encrypted with VeriCrypt for the purpose of locating and fixing bad sectors on this encrypted partition. The drive is a Western Digital 4TB hard disk drive, meaning a spinner, which also has the rest of the drive space occupied with an unencrypted partition. My question is should I first decrypt this partition with VeriCrypt before running Spinrite on it, or should I leave it encrypted while running Spinrite on it? We've been discussing this problem over on your GRC forums under the running Spinrite topic, but with varying opinions persisting. Yes, leo, leo's raising his hand.
1:42:56 - Leo Laporte
Yes, I don't have your audio. I didn't turn on my microphone so you didn't hear my oh, oh, mr Gibson. Oh, it doesn't matter, am I right? It doesn't matter.
1:43:13 - Steve Gibson
Correct. All right, I went over to the forum to see what the dialogue had been over there since he referred to that, and it was as Lee had asked. The answer, as you said, leo, is that Spinrite has no problem running on drives that have been encrypted with VeriCrypt, truecrypt, bitlocker or any other form of encryption. Since Spinrite 6.1 is seeing the drive as nothing more than opaque blocks of data, it doesn't care whether the data might be encrypted or not. Now what's interesting is that Spinrite has this real-time monitor screen, which presents a cool window that allows its user to see the data that's passing by as Spinrite is working on it. And one of the cool things that Spinrite users notice is that they often see their own recognizable data flashing past that window while SpinRite is running on their drive. But that's an example of what encryption would change. When SpinRite is running on an encrypted drive or partition, that real-time monitor window will never reveal any of its users recognizable data. Everything will just look like monitor, static. It will be digital noise because, as we know, the result of high quality encryption is data that is indistinguishable from completely random noise. So by all means, lee, run Spinrite over that encrypted partition and any damaged sectors that Spinrite is able to recover will result in recovered files once that encrypted partition is remounted and viewed through its decryption. Okay, some other feedback. Okay, some other feedback.
Jason egan wrote steve, I wanted to send along my thanks to you for reminding me of the tower of hanoi puzzle. I had forgotten how much I'd enjoyed it as a child. I picked one up for my children, who are eight and ten, for father's day and le Leo is showing it to us on camera and they are hooked. It's so great. He said it makes me proud. He said thanks for not only bringing us timely and informative security news, but also for interesting and fun things like this. I appreciate what you do every week, jason.
1:45:46 - Leo Laporte
I did the same thing because, I told you, I grew up with one of these and I just couldn't resist going out and buying one. They're expensive and they're a lot of fun.
1:45:54 - Steve Gibson
Yeah, and that's a nice one. Different colored wood discs?
1:45:58 - Leo Laporte
Yeah, so you kind of know the even and odd. It makes it a little easier to spot it and it all folds up and goes into this. Yeah, very cool, so you can put it away.
1:46:08 - Steve Gibson
I was wondering if the pegs like are, are like attached to the lid enough so that you're able to move the discs around. Yeah, but they do come out. You have to really jam them in.
1:46:18 - Leo Laporte
so they don't but, they do come out so you can put it all in the box. Nice, yeah, I love this. It was nothing, it was on Amazon, it was nothing, and it's just a great memory for me as.
1:46:27 - Steve Gibson
I said last week, there are pages of them. Oh yeah, and many of them are those really nice-looking blue ones with their own little box. So, jason, thank you for your note. I very much appreciate it and all the feedback our listeners take the time to send every week, and it's interesting. A surprising number of our listeners mention that the podcast also makes them laugh. I assume that's mostly thanks to the picture of the week, not makes them laugh.
1:46:51 - Leo Laporte
I assume that's mostly thanks to the picture of the week and not our silliness.
1:46:59 - Steve Gibson
Yeah, we do encounter things in the security space that are so absurd as to be ridiculous and funny. So, anyway, when it is occasionally impossible to both inform and entertain, well, that's a win. Brian Tillman wrote. Well, that's a win. Brian Tillman wrote. What I'm curious about is how a newspaper can claim that it's LLM's users. Oh, he's referring to an article we talked about last week how a newspaper can claim I think it was New York Times that was leading a group of newspapers that were suing I don't remember who it was that an LLMs users are reading data. That's supposed to be behind a paywall?
If there's a paywall in place, how are the LLMs gaining access to that material? Same way. It doesn't seem like a very good paywall to me. No, it's not, and I think that's a really good point.
1:47:50 - Leo Laporte
You just turn off JavaScript, yeah.
1:47:53 - Steve Gibson
Many sites like coding forums will have huge historical depth of code that could be plumbed once. So once an LLM got in there and sucked out all of its content, it's game over for that site. The information has escaped, but the point of a news site is that it's news. So to Brian's point, although it may not have been clear several years ago, today's LLMs have learned that they must legally abide by robots exclusion rules and not traverse into any sites that have explicitly banned their entry or put up a paywall.
1:48:37 - Leo Laporte
that's key I want and I would be pretty sure that's no longer happening yeah, well, it depends on the llm.
1:48:45 - Steve Gibson
Some some of them are very aggressive and and I did just see something I haven't had a chance to follow up. I mean, it was like, literally during one of our commercial breaks, someone sent something about how LLMs are getting clever about like being LLMs are being used't. Adhere to robotstxt.
1:49:11 - Leo Laporte
But I think more and more that's going to make them liable in courts. That's going to be the real problem, right.
1:49:19 - Steve Gibson
If you put up a clear specification saying you know LLAI not welcome here, right, and then there is evidence that AI got trained here, that's trouble. You got a good case. Yeah, yeah, okay. So Z? Zv said hi steve and leo, my name is zv. Yeah z e postrophe ev so I'll go leave, actually I think. You think it's what ziv yeah, okay well unless he's hawaiian.
Oh, that's where he's from, and I'm a long-time listener of the security Now podcast. Your show is fantastic and I'm glad to hear that there's no definitive end date in sight. Yay, he said recently. Like many others, I've become interested in AI as part of a hackathon. At work, I explored the Lama Index Python library, which can be used, among other things, to easily create a retrieval augmented generation, which he calls a RAG system. That immediately made me think of the incredible podcast transcripts that Elaine Ferris has created for your show. I realized it might be an interesting opportunity to use AI to gain insights from this amazing trove of data. I ended up writing a simple Python program around 130 lines of code that lets you run a query or prompt to get an answer based on the transcripts. After some experimentation I found that indexing and querying the transcripts by year yields the best results. He said below are a few examples of prompts I tried and the responses I got from the LLM. He also said the code is available on GitHub here and he gives us a link. I've got it in the show notes for anyone who wants to go there GitHubcom.
Slash Z-E-E-V, hyphen B slash S-N. And he said thank you for all the work you put into the podcast. It's been an invaluable source of knowledge and entertainment over the years. Best regards Zev. This is cool. Now you could do this also with a notebook LLM.
1:51:35 - Leo Laporte
If you have all the transcripts downloaded, just give them to Google's notebook LLM and do the same thing. In fact, I did it with just a handful of them, a few months worth, and made a little show and it sounds just like our show, except it's two very nice ai voices so, uh, zeve shared his query and the llm's reply about our most recommended science fiction reading material and our most recommended television shows.
1:52:03 - Steve Gibson
But his third query, as I mentioned at the top, I can't wait and the llm's response was the most interesting to me and I figured would be the most interesting to our listeners. What Zeev asked his transcript trained LLM's reply was Steve's opinion of Microsoft security has evolved significantly over the years, reflecting a complex interplay of recognition of improvements, growing skepticism and critical concerns about the company's practices. In the early years, particularly around 2015, Steve acknowledged Microsoft's efforts in managing security, noting that the company had developed defenses against constant attacks and was not frequently in the news for major breaches. He appreciated the improvements in security, but remained cautious about privacy implications, especially with Windows 10's design. By 2016, his perspective began to shift toward a more critical stance, particularly regarding Microsoft's handling of updates and the promotion of Windows 10. He expressed concerns about the alignment of Microsoft's interests with those of its users and highlighted issues such as the lack of transparency in updates and potential security risks associated with third-party antivirus software. In subsequent years, Steve recognized improvements in built-in security measures, particularly with Windows Defender, but he also emphasized the ongoing challenges in cybersecurity landscape. By 2018, he began to advocate for the use of built-in security solutions over third-party options, acknowledging the complexities of maintaining security in a rapidly evolving environment.
However, as time progressed, his concerns deepened by 2019 and into 2020. He expressed frustration with Microsoft's inconsistent handling of vulnerabilities and updates, particularly regarding support for older operating systems. He highlighted the need for users to be proactive about security and criticized Microsoft's approach to updates, which he felt often led to significant vulnerabilities. By 2021 and 2022, Steve's skepticism intensified as he noted a perceived negligence on Microsoft's part in addressing known security issues promptly. He pointed out that the company seemed to prioritize other aspects over security, leading to a growing concern about the effectiveness of their measures.
In 2023, his criticism became more pronounced, focusing on Microsoft's reliance on updates and their prevalence of known vulnerabilities in their products. He expressed frustration with the company's failure to address these issues proactively and questioned the ethics of their approach to forcing upgrades. By 2024, Steve's opinion had crystallized into a broader skepticism about Microsoft's commitment to security, particularly in light of high-profile security failures and a corporate culture that seemed to deprioritize security investments. He criticized the company's reactive approach to vulnerabilities and argued for the inclusion of essential security features in base products rather than as a paid add-on. As of 2025, Steve's view reflects a recognition of the inherent complexities in securing Microsoft systems, acknowledging that, while improvements have been made, the legacy nature of their software creates ongoing vulnerabilities, he advocates for additional protective measures when using their products, emphasizing the need for caution and accountability in Microsoft security practices. Overall, Steve's evolving opinion illustrates a journey from cautious optimism to critical skepticism, highlighting the need for significant changes in how Microsoft approaches security to better protect its users.
1:56:42 - Leo Laporte
I think, that was fairly accurate, do you think?
1:56:45 - Steve Gibson
Yes, I mean you know it has that kind of vanilla feel yeah, that AI.
1:56:50 - Leo Laporte
thing.
1:56:50 - Steve Gibson
That AI gives things, but you cannot argue that to give something just a bunch of text.
1:57:32 - Leo Laporte
Astonishing revolution where we're witnessing the emergence of a technology that's able to take transcripts of 20 years of my rambling and turn them into that which, while, yeah, a little pablum ish, still you know it's. It's amazing that it even is able to say this. I'm astonished, yeah. Yeah, it is amazing. Notebook LM would do the same thing. In fact, we're going to talk to the folks from Notebook LM on IM Tomorrow.
1:57:46 - Steve Gibson
Yeah, oh, you know more than I do, cool.
1:57:49 - Leo Laporte
Yeah, cool yeah.
1:57:50 - Steve Gibson
Okay, I do. Cool, yeah, cool, yeah, okay. Uh, just for the sake of not breaking up this final piece, okay, foreground radiation let's take our last break, and then we're going to look at what is going on with proactive bot scanning in the foreground across the internet and and it is very rare that we encounter something fundamental that we have never talked about in 20 years of this podcast well, I am in the neil sadaka camp on this one.
1:58:24 - Leo Laporte
uh, breaking up is hard to do, so let's get the ad out of the way. And then internet foreground radiation with Mr Steven Tiberius Gibson, who apparently knows the difference between Star Trek hollow chess and Star Wars hollow chess, even though, as far as I could tell, they do look the same. Am I wrong? I think they do look the same.
1:58:47 - Steve Gibson
Star Trek's. They had three dimensional.
1:58:50 - Leo Laporte
Oh, that's right, it was three dimensional.
1:58:52 - Steve Gibson
And they had weird little three by three and four by four boards and spock would move things around and yeah no one ever explained it yeah, there is and there are.
1:59:01 - Leo Laporte
You can get those chess boards too and make up your own rules. All right, our show. The last uh advertiser for this particular episode of Security Now is Big ID. They're the next generation AI-powered data security and compliance solution. Big ID is the first and only leading data security and compliance solution to uncover dark data through AI classification, to identify and manage risk and to remediate the way you want. You can also use it to map and monitor access controls, scale your data security strategy, and it's got great unmatched coverage for cloud and on-prem data sources. In fact, they work with anything. Bigid also seamlessly integrates with your existing tech stack so you can coordinate security and remediation workflows, take action on data risks to protect against breaches, annotate, delete, quarantine and more based on the data, all while maintaining an audit trail, which is very handy. As I said, it works with everything you work with. Partners include ServiceNow, palo Alto Networks, microsoft, google, include ServiceNow, palo Alto Networks, microsoft, google, aws and more.
With BigID's advanced AI models, you can reduce risk, you can accelerate time to insight, you can gain visibility and control over all your data. If you think about it, if you're using AI, if you're doing what we just talked about with Steve RAG Retrieval, augmented generation. You want to make sure that you're not feeding AI proprietary, secret information, stuff you don't want to incorporate into the models. But to do that you need to be able to see and control your data. That's what BigID does. Intuit named it the number one platform for data classification, and that's in accuracy, speed and scalability. Who has the most dark data, do you think in the world? Bigid equipped the US Army yes, 250 years of dark data to illuminate the dark data, to accelerate this ongoing process of cloud migration, to minimize redundancy, to automate data retention. All of these are high priorities. And what a great quote BigID got from US Army Training and Doctrine Command. This is the quote.
The first wow moment with BigID came with being able to have that single interface that inventories a variety of data holdings, including structured and unstructured data, across emails, zip files, sharepoint databases and more, to see that mass and to be able to correlate across all of them completely novel. They go on to say I've never seen a capability that brings this together like big id does. That's the us army training and doctrine command, but that's that's not all. Cnbc recognized Big ID as one of the top 25 startups for the enterprise. They were named to the Inc 5000 and the Deloitte 500, not once, but for four years in a row. The publisher of Cyber Defense Magazine says quote Big ID embodies three major features we judges look for to become winners understanding tomorrow's threats today, providing a cost-effective solution and innovating in unexpected ways that can help mitigate cyber risk and get one step ahead of the next breach.
Start protecting your sensitive data wherever your data lives at bigidcom slash security now. Get a free demo to see how BigID can help your organization reduce data risk and accelerate the safe adoption of generative AI. Again, that's bigidcom slash security now. Oh, when you get there, there's a free white paper that provides valuable insights for a new framework. It's AI, trism, t-r-i-s-m, trust, risk and Security Management to help you harness the full potential of AI responsibly. You'll find that and everything else at bigidcom slash security now. B-i-g-i-dcom slash security. Now Big ID. We thank them so much. Two thumbs up for Big ID. We thank them so much for their support of security. Now, I can never get to do it when I want to, but it always does it when I don't want it to. All right, let's talk about foreground radiation. You're the guy, at least as far as I know, coined internet background radiation.
2:03:21 - Steve Gibson
That's my term, yep, Okay. So, as I mentioned at the top of the show, today's podcast title, Internet Foreground Radiation, is a play on the term internet background radiation, which I coined 26 years ago, back in 1999, while developing GRC's Shields Up facility which, by the way, Paul Therot was the first person to discover and write about.
2:03:49 - Leo Laporte
Really. Oh, that's awesome. That was small world noise that would occasionally flow into any internet IP address.
2:04:04 - Steve Gibson
Now Wikipedia reminds us that, quote cosmic background radiation is an electromagnetic radiation that fills all space. The origin of this radiation depends on the region of the spectrum that's observed. One component is the cosmic microwave background. This component is red-shifted photons that have freely streamed from an epoch when the universe became transparent for the first time to radiation. Its discovery and detailed observations of its properties are considered one of the major confirmations of the Big Bang.
Now, fortunately, unlike the cosmic background radiation, which will presumably never die, the original designers of the Internet had the foresight to place a time-to-live counter into every single packet that moves across the internet, and the very first thing that every internet router does when it receives an incoming packet is to decrement that packet's remaining time to live. If the packet's time to live was one and is decremented to zero packet's time to live was one and is decremented to zero, that signals that the packet has been alive long enough and that if it was ever going to reach its destination it should have by now, and that, for the sake of the greater good of the internet, it must now be put to rest. Sorry, packet. When this occurs, well-behaved internet routers will see where that packet came from, from its source IP address, and will send back an ICMP time exceeded message to inform its sender that the packet it sent to, whatever destination IP never, for whatever reason, reached its destination. My point here is that, unlike true cosmic background radiation, internet packets are strictly not allowed to wander around the internet forever aimlessly. And what this in turn means is that all internet background radiation has a deliberate source somewhere and that at any time a packet is received, someone somewhere deliberately formed it and dropped it onto the internet.
Now, that said that someone somewhere could be some cranky, old and forgotten NT server in a locked and forgotten closet that became infected with Code Red or Nymda worms back in 2001. Those were the good old days where Code Red, for example, was a flash worm that successfully infected more than 350,000 Microsoft IIS web servers within a few hours of its launch onto the Internet. So if any skeptics might be wondering whether things have actually gotten better through the intervening years, the answer is certainly yes. Yeah, we do seem to be well past the point of flash worms taking down the internet, thank god, yeah, jeez, I forgot all about that yeah, but the presence still the presence of any monoculture should always make a prudent person nervous, since mistakes can always happen.
My point is that even today, even though Internet packets will never persist on the Internet, true Internet background radiation being emitted from dusty servers in lonely locked closets may still exist. So the reason I named today's podcast Internet Foreground Radiation is that there's something else going on that an internet security firm has been observing. The distinction I wanted to make is that, whereas internet background radiation, much like the cosmic background radiation, lacks deliberate intention, there is now separate internet foreground radiation behind which a great deal of deliberate intention lies. So who's generating that radiation and why? Last week, the firm Human Security posted the results of their long running research under the heading Opportunity Makes the Thief how Web Scanner Bots Target New Websites for Cyber Attacks target new websites for cyber attacks, and I have in the show notes a link to their full research paper. Since what they found is not something that I think has ever been known before or appreciated before, I thought it would be worth sharing and taking a closer look at. They introduced the subject by writing.
When a new website goes live, it's not people who visit first, it's bots. Automated tools probe new domains within minutes, long before any customer or legitimate user arrives. These bots vary widely in intent. Some are benign search engine crawlers indexing your pages, or commercial security scanners checking for vulnerability with permission but many are malicious. Among the most pernicious are web scanner bots, which quickly examine websites for weaknesses and exploit them immediately, turning reconnaissance and attack into a single automated sequence carried out at scale. Human Security's Satori threat intelligence team monitors bot activity across our customer network and in dedicated research environments. One such environment is a honeypot, a web server we intentionally set up to attract only bot traffic. By observing the requests hitting this fresh, otherwise unpublicized website, we are able to gain insight into the types of bots that target a website from its inception onwards. One early finding in this experiment was that web scanners consistently dominate early traffic to new sites and continued to probe the sites day after day, long after other bot types began to appear. This persistence underscores why scanner activity is a security concern for the full lifespan of any web property. This blog post examines the threat of these web scanner bots and shares our recent research findings on several active scanner campaigns, including the Mozi A botnet, a Mirai variant called JAWS and the Romanian distillery scanner.
Web scanner bots are an escalating cyber threat. These bots are often the very first visitors to any new website, probing for security weaknesses, long before any human users arrive on a newly launched site. Observed by human security, scanners made up an average of 70 70 percent of all bot traffic in the first days, meaning web scanners scanning the entire site and on some days, 100% of detected bot visitors were from scanners. Bot-driven scanning operations are growing more complex. The Romanian distillery operation is a prime example. Once focused solely on harvesting SMTP credentials, it now probes for PHP services, env files and misconfigurations across a distributed slash 24 subnet. Its scan patterns follow doubling revisit intervals and reveal a coordinated infrastructure designed for scale.
In some cases, such scanners don't stop at discovery. They attempt SQL injection or deploy malware immediately after identifying a weakness. Traditional defenses struggle to catch web scanners. Many of these scanner bots evade simple security measures. Many of these scanner bots evade simple security measures. They may rotate through networks of infected devices, using other botnets to distribute their scans, hide their true identity by omitting or faking their user agent strings and rapidly change tactics to avoid signature-based detection. Legacy security tools that rely on known malicious IP lists or obvious signatures often miss these stealthy probes.
Web scanners, also known as website vulnerability scanners, are automated tools designed to identify security weaknesses in web applications, websites and APIs. They systematically probe and inspect websites for misconfigurations, exposed files, default credentials or known vulnerable software. If a new website is still being configured or lapsed, proper protections scanners will attempt to find and exploit any flaw they can before the site's owners have a chance to secure it. Okay, so the first and crucial takeaway would be to never assume that any security can be added after any portion of a new site goes live. Never assume that, since it hasn't been advertised or announced in any way publicly that it might be at all safe to place anything online that hasn't already been fully hardened. Essentially, the entire Internet has become a loaded and cocked mousetrap ready to spring and capture at the slightest provocation.
This is where my favorite of all tricks, ip-based filtering, can come in handy. It is so simple and is so absolutely robust as a security solution. If you wish to create some true external exposure, simply first block all access, then selectively allow the IPs through that you know you can trust, but never open the floodgates until you are fully prepared to be deeply attacked, because that will immediately happen, they wrote. Not all scanners are bad, though. There are good scanners run by security companies or researchers to help site owners by identifying vulnerabilities so they can be fixed before the bad scanners can get to them. But both good and bad scanners impose load on your site and the bad ones, if not blocked, will certainly attempt to leverage any weaknesses they find.
Scanners don't visit just once. They constantly and persistently re-scan sites over time since new vulnerabilities might appear with site updates or as new exploits are discovered. Okay, so it's always fun to run across, as I said, something we've never touched on or talked about on this podcast, given that this is our 1030th podcast. We've logged many thousands of hours discussing and covering pretty much anything and everything that's happened over the past 20 years, so it's not often that we encounter something we've never discussed before, but today is one such rare day, because the ubiquitous shift to TLS HTTPS website connections, which increasingly require the use of SNI, which we were just talking about server name indication, to be specified and provided by the connecting client in its first TLS handshake packet, means that knowing the IP address of a site or having a site's IP address simply by scanning them all, is no longer sufficient to successfully establish a completed handshake to a site's servers. That's new. We've never mentioned this before. Think about that for a second.
From the birth of the internet, it has been possible to simply scan the internet's 32-bit IPv4 space for web servers and to establish connections to them. But that all changed once the likes of Cloudflare and other CDNs came along, as a result of IPv4 space depletion and the economic fact that IP sharing is inherently far less expensive, since it also allows for infrastructure sharing. Today, more than 90 percent nine zero percent of today's websites are now sharing IP addresses, leaving fewer than 10 percent of all sites sitting on a single dedicated IP address. This means that more than 90% of the Internet's websites have migrated behind proxies that are only able to disambiguate website destinations by examining the incoming client's SNI extension field in the TLS handshake, the client hello packet. This even applies to a modest facility like mine. Grc's sc shortcut server, our mail dev get lab servers and others all share the same IP, so it's not possible to reach any of them simply by their IP, because we don't know where which server to send it to. It's necessary for anyone who wishes to connect to any server behind that IP to somehow also first know which domain name they expect to find at which IP address. So, as I said, that's not an observation that's ever come from this podcast before. The bad news is, I wish this presented a bigger problem for web scanners than it does. The guys at human security explain that scanners response to this has been to solve it. They wrote to ensure that their scanners manage to get first in line for any new website.
Threat actors take advantage of feeds and services that announce new websites or domains coming online. For example, threat actors monitor newly registered domain NRD feeds, which are lists of recently registered, updated or dropped domains, such as whois databases and domain drop lists. Such NRD feeds are repurposed from policy feeds intended to increase corporate security to threat intelligence and monitoring feeds against the websites themselves. Threat actors also monitor certificate transparency logs, such as CertStream, which publicly log new TLS certificates. For scanners, a new domain registration or certificate issuance indicates a new website that could be scanned. Once the large scale SEO crawlers index the new website, scanners may also monitor the search engine's new listings and the scale of scanners will increase even further. Scanners will increase even further One thing that hadn't occurred to me until just now, as I was as I was reading this and paying attention to it is that wildcard certs are an interesting hack here.
If a wildcard cert is issued that just says, for example, stargrccom is issued, that just says, for example, stargrccom. That doesn't indicate what the site's host names are and there's no indication of that from a wildcard certificate. So there's a little bit of obscurity there. I wouldn't rely on it, but still it's there. So for the purposes of this research, these guys are interested in identifying and, where possible, disambiguating and classifying the range of bots that are probing their honeypots. We know this doesn't matter for the sake of security, since for security it's necessary to simply be equally secure for anyone who might come knocking. But what these guys found was intriguing and revealing. Under the heading of identifying web scanner bot traffic, they wrote some scanners openly identify themselves in the user agent string which okay, that's interesting in the user agent string which okay, that's interesting which is the part of an HTTP request that might say, for example, mozilla slash 5.0, parens compatible semicolon scanner XYZ forward slash 1.0, and then it goes on. So this is identifying itself as a scanner and they say security teams can easily filter or block those known scanners.
But many malicious scanners naturally deliberately mask their identity for use misleading user agents, I'm sorry. Or use misleading user agents to obfuscate their true nature. Misleading user agents to obfuscate their true nature. In these cases, identifying them requires analyzing their behavior and deploying anti-bot mechanisms to intercept their activity. You know, like maybe a ridiculous number of page requests per second. You could say wait a minute, this is not a person. On the other hand, you wouldn't want to block a search engine and this thing might be declaring itself to be Google, a Google spider. So there you'd have to know if it corresponded, if the source IP corresponded, with a legitimate, known Google IP address. Anyway, they wrote.
Some user agents we observed suggest the presence of outdated or anachronistic systems, including the BOS legacy, linux kernels and even Windows 3.1 Internet Explorer versions. Obviously, no real users are surfing the web on Windows 3.1 today, so this was a dead giveaway of automated activity and not very smart activity. These impossibly old user agents likely came from a public user agent database that the attackers grabbed for obfuscation purposes. For obfuscation purposes, a fun and benign find that should never hit any of your web servers if you have a decent bot mitigation solution deployed and, leo, you put that on the screen a second ago and they show some of these ridiculous user agent strings slash 1.1, compatible msie 5.01, palm os 3.0 I remember that. Udora web 2.1 yes, palm os 3.0 now my refrigerator could use that, but nothing else and then udora web 2.1, wow, anyway. So I would be inclined to agree with their assumption about the likely source of those bogus bot user agent strings. Uh, you know where else you're going to get them from some old historical list somewhere under the heading of reconnaissance and probing the target.
They explain what these scanners tend to do. Once they locate a new candidate target, they write. Before scanners are even deployed, operators conduct manual reconnaissance to identify likely entry points, directories, configuration files, endpoints and services that may exist at newly launched sites. They then craft scanners so they're talking about the operators who design what the behavior of the bots will be. So they design this behavior. Then they turn the bots loose, so they said. They then craft scanners with predefined paths and exploitation logic tuned to probe and attack if those elements are present and identified.
Once launched against a site, the scanner rapidly tests for these known targets. It attempts to enumerate directories, pages, api endpoints and exposed resources, executing preset payloads or exploits, where applicable. One of the most common methods to launch scanners is using DERBUST, a dictionary-based attack against web servers that automates the process of discovering hidden files and directories on a website. This tool scans through predefined lists of potential directory and file names. You know, slash admin, slash configphp, slash backupzip, etc. In hopes of getting lucky in finding unprotected sensitive files or admin interfaces.
Now here again. Having been a website admin myself for the past 25 years, it can sometimes be tempting to imagine that it might be possible to just briefly do something that's not entirely secure, under the assumption that you know just for a few minutes nobody will notice. All I can say is that on today's internet, doing anything like that is risky at best. I've always had better things to do than wonder and worry about what percentage of GRC's inbound connection traffic has malicious intent. But, for example, I have seen ample evidence of tools like that, durbust. They mention in the logs that I sometimes briefly enable when I'm trying to track down some specific behavior. The only way to be safe is to assume that everything is malicious and be prepared for that. Grc's servers do not log website activity specifically because the signal-to-noise ratio is so low that there's virtually no signal among all of the noise. That's the reality of today's web. For sites that have been around for the last 25 years, it really has become a nasty jungle out there. It's sad it's happened, but it has. They wrote.
Using the scanner traffic from our research, we mapped the most targeted path types targeted by scanners. This mapping shows that scanners have particular favorites when it comes to these initial probes. The two most targeted types of files by far were environmentconfigurationenv files and repositories for code secrets. In fact, about one-third of all scanning attempts in our study were after env files and another one-third were looking for Git repository data, such as git folders or leftover export files. They wrote this is no surprise. Environmentenv files often contain API keys, database passwords and other secrets. That would be a jackpot for an attacker, and Git-related files might expose source code or credentials that enable a deeper compromise.
The potential exploitation from each of these path types is listed in the table below, and the most targeted paths are shown in the chart, and I've a big pie chart here. It is rather astonishing, mostly to see how, again, non-uniform this stuff is. So I mean, here's a hint If you wanted to immediately increase the security of and you don't use env files or git secret files, simply set up a trap so that any query to those file extensions on your site blacklists that source IP for some length of time. I mean again, no legitimate user who is clicking on a URL to access a page on your site for a site that doesn't use those file types is going to query that. So you're Um so, astonishingly, fully 33.6% of web server file type requests which they observed were for dot ENV files. 33.6%, wow. The effectively equal 33.5% were for Git secrets. So these are clearly malicious spiders.
2:31:52 - Leo Laporte
Yes, there's no other reason.
2:31:54 - Steve Gibson
No other reason for anything to probe that period. So there's two-thirds of the probes right off the bat you're able to identify as malicious intent. Next up at 23.4% were common PHP files. So collectively, just those three account for a whopping 90.5% of all website probes. This leaves 4.3% for unprotected config files, 2.9% for YML files and 1.1% for Python mail sender files. They offered a table that explained why different file types were being searched for.
As I mentioned, the env files typically store API secrets, tokens and other sensitive information that can be used by attackers to pivot and attack. The git secrets are used to gain access to victims' repositories, leading to cross-organization compromise. Access to victims repositories leading to cross organization compromise. But, of course, common php, if you, if you left your php config out, that might allow them to do recon, identify versions of php and other installed frameworks, um, even wordpress, popular php, cms, uh files. You, as we know, wordpress has a long history of vulnerabilities. Attackers try to find fresh versions that are still using default credentials or endpoints that provide additional fingerprinting, such as plugin versions. So these can be further than scanned for vulnerabilities and exploited if they're found lacking the latest security patches. So you know a wealth of information just from you know scouring and looking for things, and we know we know how many unintentionally exposed files exist on the internet that make this sort of scanning worth doing. I mean, unfortunately there is a payoff. You just don't want it to pay off on your site.
They wrap up the topic of reconnaissance and probing by adding beyond those, scanners also commonly seek out various configuration and backup files, for example yml or yaml configs, old back or zip backups of the site, or files like configphp that might reveal database connection information. Ooh, that's true. They probe for known software-specific files. Known software-specific files. For instance, requesting a URL ending in wp-configphp could indicate the site uses WordPress and reveals its config if it's not secured. Or hitting slash server hyphen status on a web server could reveal internal information if that page is not locked down. Scanners will even check for well-known vulnerable services. One example is scanning for Outlook web access and exchange server paths on sites. Since unpatched exchange servers are high-value targets that could lead to a broader organizational breach. Lead to a broader organizational breach. Essentially, during the probing phase, scanner bots test the site against a predefined list of files, directories and endpoints that should never be exposed. Every directory listing config file or version disclosure it finds constitutes loot that can be used in the next phase of the attack. This process is highly automated and aggressive. The scanner might attempt hundreds of different URLs on your site in rapid succession, far more exhaustive and faster than any human could manage. That behavior pattern is often a telltale sign that the traffic is a scanner bot.
So when you stop to think about it, there's only one reason any of this exists and any of this is worth the time and contains a very long legacy of being insecure by default. That's what this is about. Right, you have to be proactive, you have to take measures not to expose these things. I mean, it is really a sad state of affairs that we have developed a world in a world which is insecure by default.
You know, although this characteristic is beginning to disappear, historically it has been entirely possible, and was even once acceptable, to choose not to use any password at all when setting up a new operating system or a device. Unix and Linux once allowed the root user's password to be null. You know, today we all recognize this as beyond bad, but we all probably also remember a time when perhaps we did that ourselves. In the future, the option to skip a password won't exist, no one will believe it was even ever possible, and they'll understand that doing so in the future would be insane. So once upon a time, though, though, it was not so insane, but that, you know, that has been. That approach of having no or low security has been now entirely upended, thanks to the internet's steadily growing foreground radiation.
2:38:00 - Leo Laporte
I remember a time when no one locked their doors and children would play out in the street with absolutely no fear at all. Times have changed, Steve.
2:38:10 - Steve Gibson
Used to be a friendly neighborhood.
2:38:12 - Leo Laporte
Used to be a nice place back here. Nope, yeah, got to have a password for your root user. Got to Just seems sensible. Also, you got to listen to this show every Tuesday. My God, you miss an episode. You miss a mountain of information that is, I'm sure, useful to you and your work and at home and keeping things secure. This is the show. We do this every Tuesday right after MacBreak Weekly, so that's about 1.30 Pacific, 4.30 Eastern, 20.30 UTC. You can watch us during the show recording if you want to get the freshest version. Fresh usually means there's some unbaked parts, but most of the time it's pretty good. If you are watching live, you can chat with us. So that's the advantage.
Club members get behind the velvet rope access in our Club Twit, discord. Love to see you there. If you're not yet a club member, please join it. We'd love to have you Ad-free versions of all the shows and a lot of special programming just for the club, including, by the way, all those keynotes we did last week and the week before from Apple and Microsoft and Google and all that stuff. That's all club only. Now. The live streams for everything we do not only are in Discord, but open to the public at youtubecom, twitch, tiktokxcom, facebook, linkedin and Kik. Pick one of those. You can watch live chat with us live After the fact. Of course, you can download a copy. Now.
Steve has some unique versions of the show. In fact, every version Steve has is unique, different. There's a 16-kilobit audio version for the bandwidth impaired. It's a little scratchy but it is small. It has that virtue. He has a normal 64-kilobit audio version. We don't make those anymore, so that's the place to get that. He also has those great transcripts that Lane Ferris does. It takes a couple of days to get those out, so come back, maybe in Friday or Saturday and you should be there.
What else? He's got the show notes there and if you want to get those ahead of time, you can subscribe to the show notes newsletter. In fact, the best thing to do if you want to correspond with Steve in any way is to go to grccom slash email and sign up to get whitelisted. Basically, you'll vet your address to make sure that it's OK, you're not a spammer. You can send them emails Great way to submit pictures of the week or comments, that kind of thing. It's also great great forums there, which may be even a better place to do the comments. Anyway, when you're going there GRC dot com slash email you'll see two checkboxes unchecked by default one for the weekly show notes and one for a much less common uh email.
When steve has something to announce, like the forthcoming version of his dns benchmark pro um and there's lots of other great stuff that's free forever, like his famous shields up where this whole background radiation thing started. Uh, he's got all sorts of information about vitamin D and just a variety of stuff. Grccom Now, our unique versions are a 128 kilobit audio version. Don't know why, but that's what we do. I'm told it has something to do with the way Apple re-encodes his stuff, that if you don't have a higher bit rate, apple munches it up anyway. That's what you can get in audio. We also have a video version if you want to see steve's mustache at work. It's basically got a life of its own.
Uh, that's all at twittv slash s and I'm teasing s only in my imagination, twittv slash s and there's a youtube channel dedicated to securing now that I recommend if you want to share clips. I know often when you're listening you go oh, my boss has got to hear this, or my co-worker, my friend, my, my, uh, my spouse whatever. Go to the website grccom slash sn. There's a link there to the dedicated youtube channel with all the videos makes it very easy to clip it. Best thing to do, if you ask me, is subscribe, because it's a podcast. I know it's old fashioned, but we still make these as RSS feeds, so you can subscribe and you'll get a notification the minute a new one comes out. You can even set your podcatcher to automatically download it, so it's there, ready and waiting for you to watch or listen whenever you're in the mood.
If you do that, though, many of these uh apps have directories and have a review capability. Leave us a good review, would you, because it really helps build the audience when shows get uh long in the tooth like this one. Um, we don't get much on the charts because there's not a whole bunch of new subscribers at any given time, it's just a steady hum uh. So the reviews are really what makes the difference. Leave us five stars, if you would. We'd appreciate that. If you're not a member of the club twittv slash club, twit 10 bucks a month and you get all those great benefits. I think that does it for me, steve. We'll be back here next Tuesday for 1031.
2:42:59 - Steve Gibson
Yes, we will See you then, my friend, bye. Yes, we will see you then, my friend, bye, bye. Nice noise, yes, nice, nice noise. So I heard you say before, uh, that you become a fan of gl1, glp1 agonists.
2:43:19 - Leo Laporte
Oh, zempic, oh. I asked my doctor for truzepatide, which is um, the dual glp-1 and gip agonist, and he said I can give it to you. It's more expensive. I have to. We have to jump through some hoops, send you an endocrinologist. But I've been on a zympic for three weeks. I love it. My, my a1c well, I don't know my a1c yet, but my blood sugar is down. It was, it was averaging 154 when I started.
2:43:42 - Steve Gibson
It's now down 125 average well, and, and you said, you're really seeing a change in appetite uh, like, yeah, I'm not interested in it.
2:43:51 - Leo Laporte
I don't have those and, by the way, I don't want to do an ad for this. I'm not. I'm not recommending this for anybody I know I waited.
I wanted to wait till we were off the podcast we're not on the podcast, we're still streaming, so if you're, if you're hearing this yeah, I'm not hiding it because I think it's really interesting For me. No side effects. A lot of my friends have a lot of nausea and stuff, but I haven't and I'm on the lowest dose, which means it's amazing that it's even working at all. I mean the doctor said don't expect much in the first month. It's working at all. I mean the doctor said don't expect much in the first month it's working.
It's amazing, lost five pounds already I mean, I just said you went from your typical four slices of pizza to yes. So if there's a pizza sitting on the counter it's really hard for me to have one. I didn't even finish a piece. Yeah, it was fine, I was happy. It probably takes a little of the edge off, you know like, oh, this tastes so good.
2:44:46 - Steve Gibson
That's all right. It's worth it. I'm sure it does.
2:44:50 - Leo Laporte
Yeah.
2:44:50 - Steve Gibson
I'm, you know. But if so, if you're a foodie, then you know you have to give that up a little bit, but for longevity worth it. Yeah, it's worth it?
2:44:58 - Leo Laporte
I was. I scared myself, my blood sugar was just getting too high. So, um, yeah, this has been, this has been great, what it really just. I mean you feel full most of the time. You always have a full feeling because you're still not thinking about food. That's the main thing I don't have these like, oh god, I can't wait to eat something. I fast until uh, one o'clock every I don't eat. I eat it last meals, like six or seven, and then I don't eat again until after about one o'clock. Good, that's fine.
2:45:26 - Steve Gibson
Yeah.
2:45:28 - Leo Laporte
So I only have two meals a day. I don't eat all those snacks I would eat in the evening. It's a big difference. Nice, I feel good too. I feel much healthier. Yeah, yay, thank you, thank you. Okay, buddy. Yeah, have a good one, mr Gibson. See you next week. Give my love to Lori. We'll see you next week. Will do Bye, bye.
2:45:51 - Steve Gibson
Oh Zampy.
2:45:55 - Leo Laporte
I don't want to be an ad for that drug I don't but I have to say it's kind of amazing.
2:46:03 - Steve Gibson
You need to learn the disclosure spiel at the end of it.
2:46:06 - Leo Laporte
You may cause sausage fingers and weird hallucinations. You may not be able to poop for a week, but you'll lose weight.
2:46:15 - Steve Gibson
Side effects include instant death, instant death.
2:46:19 - Leo Laporte
I haven't had any side effects, which is great, because Will Harris said he would get terribly nauseousous. I know a number of people would just say I get so sick every time I have my dose. But it's worth.
2:46:29 - Steve Gibson
It is what they all say all drugs are like that. Right, it's very specific to the person.
2:46:33 - Leo Laporte
I you know, I never have a reaction to vaccines, to medicines of any kind. I'm I'm pretty insensitive, I guess would be the word oh, and I do my Tai Chi like crazy. I love my Tai Chi. I am now up to so there's 108 poses in the Yang that we do, the Yang style that we do. I'm now up to 38. I could do about a third of the total, but I have to say I love Tai Chi. Sometime I'll do you a little Tai chi demo. It's so much fun and I do it as slow as I can. So I had class yesterday and I love it. Lisa and I are both doing it. It's really good.
We have a nice um sensei. He is a uh, he is a black belt in kempo. He's like a super black belt. He's like a he's very high level kempo master but he all he knows every many other disciplines but studied tai chi for many decades. He's about my age, uh, since since his 20s, so 40 or 50 years, since his 20s, so 40 or 50 years. But he has his own flavor. You know, I look at the videos on YouTube and stuff and I'm doing a little. It's a little different but it's so, so good. I really love it and I exercise every day. I usually row for half an hour every morning and then I now am in the habit of taking a couple mile walk after dinner every night, because that helps also with the blood sugar. So I'm getting good habits. Yeah, I feel, and I have been feeling much better. Thank you for asking, except you didn't. But there you go, you're going to hear it anyway. Anyone.