Security Now 1025 transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show
0:00:00 - Leo Laporte
It's time for security now. Steve Gibson is here. We've got a lot of security news. The state of Virginia passes an age restriction law that Steve says has no chance of surviving a First Amendment challenge. There is a nasty PiPi package that has survived for three years and 11,000 downloads. Isn't anybody paying attention? And then Steve has a solution for government agencies that want to use signal without letting the whole world know what they're talking about. All that more coming up. Next on security now podcasts you love from people you trust. This is TWIT. This is Security Now with Steve Gibson, episode 1025, recorded Tuesday May 13th 2025. Secure conversation records retention. It's time for Security Now the show. We cover your security, your privacy, your safety online with a guy in charge at GRCcom, mr Steve Gibson. Hello.
0:01:09 - Steve Gibson
Steve, I have never been accused of talking quietly. Leo, there's never been anything that has happened. My wife has extremely sensitive ears and she talks to the other room and assumes I can hear her. She can hear me. So it's not reciprocal, but you know this is a.
0:01:29 - Leo Laporte
You know, this is a generally a couple problem. Lisa will talk to me from two floors away. I'm glad it's not just me and I and I can hear it's like what something?
0:01:43 - Steve Gibson
there's a conversation being had and she doesn't talk to herself.
0:01:45 - Leo Laporte
so I know it's aimed, but I wear hearing aids and it still doesn't help, so I don't know what the answer is. Oh, but you have such an excuse.
0:01:53 - Steve Gibson
That's great, you know. It's like they were off, or they.
0:01:57 - Leo Laporte
I need a trumpet, I need one of those old-timey, eh. So what's? Coming up this week on Security Now.
0:02:03 - Steve Gibson
We are here for episode the big episode. The first episode Past the two to the 10, episode 1025 for the 13th of May.
I got to today's topic through a rather circuitous route because it was originally titled what is end-to-End Encryption? Because I was thinking, I was noticing that it's become a buzzword, it's become like, oh, it's what you're supposed to have, or oh, it's this, oh, don't worry about it, it's end-to-end encrypted, even when you know like it may not be. And of course, this harkens back to the telemessage mess that we talked about and them insecurely archiving signal chat messages, signal protocol conversations. As I looked further and I thought about this problem, I ended up sort of the podcast morphed into today's topic, which is secure conversation records retention and the question and and the question is is is true, end-to-end encryption possible when records are being retained?
0:03:31 - Leo Laporte
yeah, because records have to be kept in the clear right, or at least well records.
0:03:36 - Steve Gibson
I guess not have to be accessible if you are subpoenaed right or and like I remember being appalled when my little, when I heard like my little company that's sort of doing nothing big over in the corner, you know it's corporate, you know records, responsibility and there's all kinds of like record keeping acts. Now, and in fact since I sent this email, the email of this show with the show notes to I think it was now we're up to 17,363 of our listeners. Several people wrote back and said that their enterprises, their companies, were telemessage customers and that they're now needing to find an alternative solution, because this actually is a problem. There is a need that companies have for their executives' dialogues and conversations and transactions to be retained for legal purposes.
Sure, yeah, there's regulations in almost all industries about that, so we're going to get around to that and, I think, have an interesting exploration of the issue and the problem. Exploration of the issue and the problem. And, believe it or not, leo, I have a solution, which I didn't have it when I started. It was as a consequence of sort of brainstorming during the podcast production and putting it all down, and I hope it happens. I imagine it will because you, you know, the podcast has some reach and if it hasn't occurred, maybe it's occurred to other people, but I've not seen it anywhere.
So I love this We'll talk about that First we're going to talk about the state of Virginia passing an age restriction law that, as I wrote, has no chance. It's like what are you, why are you even bothering to put you know? Waste the ink on this, you idiots. Uh, also, new zealand also tries something similar, citing the lead that they're taking from australia. Uh, we have a not a nasty python package. Uh, for that's actually is aimed at discord developers, which was only found after three years and more than 11,000 downloads, which tells us the story of well, we can't count on all the security firms always finding all the malicious you know a repository junk. That's out there, the malicious repository junk that's out there. Also, what's in WhatsApp Turns out that finding out was neither easy nor certain, and there's a story there. Also, the UK's Cyber Center says that AI promises to make things much worse.
Oh joy, we've got a bunch of great feedback from our listeners, which we're going to spend some time on and also use those as talking points. And then look at this question of what does it mean to need to retain records of what originally was a secure, end-to-end, encrypted conversation, and how could that be done? And, of course, the picture of the week also generated feedback from our listeners. Benito and I were talking about this beforehand as MacBreak Weekly was wrapping up. I learned something I didn't know, know which is interesting from our listeners and and which which benito also told me. Um, but the picture is interesting, so we'll have all right, I haven't looked at it.
0:07:33 - Leo Laporte
As always, I like to save it for the show. Uh security. Now it's underway, but before we get to going steve, let me stop you for a moment for a word from our sponsor and it's a sponsor I really like talking about, because they implement zero trust affordably easily and I'm a big believer in this. Zero trust is obviously the way to go in many circumstances. We're talking about ThreatLocker. I don't need to tell you, if you listen to the show, you know that ransomware is running rampant through businesses worldwide. They get in a variety of ways phishing emails, infected downloads, malicious websites, even rdp exploits but the key term there is they get in right. Somehow they get into your network and once they're in, they can do a lot of damage. Don Don't be the next victim. You need ThreatLocker's Zero Trust platform. It takes a proactive and this is the key deny by default approach. That's what Zero Trust means. It blocks every action unless it's explicitly authorized, and it's great because it protects you both from known and unknown threats. It can be a zero day. We're not actually looking at the threat to see what it is, we're just saying no, you can't do it, and that's why it's so important, especially for city governments, schools, infrastructure plays, jetblue big businesses like JetBlue. They use ThreatLocker to make sure that a bad guy, if they get in, still can't do any harm. Talk about infrastructure. The Port of Vancouver uses ThreatLocker. Threatlocker shields you from zero-day exploits and supply chain attacks and this is a really nice side effect provides complete auto trails for compliance. So it really is a handy tool. Threatlocker's innovative ring fencing technology that's what they call it isolates critical applications from weaponization. It means it stops ransomware cold and it also limits lateral movement within your network.
Threatlocker works in every industry. It supports Macintosh as well as Windows, so a heterogeneous network that's fine. Plus, you get 24-7 US-based support and you get comprehensive visibility and control. Let me give you an example Mark Tolson. He is the IT director for the city of Champaign Illinois. You know bad guys go after city governments like crazy because they figure, ah, they won't be well-defended. Plus, they probably have insurance. It's an easy buck. Well, don't go after Champaign Illinois. Mark says quote threat locker provides that extra key to block anomalies that nothing else can do.
If bad actors got in and tried to execute something, I take comfort in knowing threat locker will stop it. Stop worrying about cyber threats. Get unprecedented protection quickly, easily and cost-effectively with ThreatLocker. Visit ThreatLockercom slash twit to get a free 30-day trial and learn more about how ThreatLocker can help mitigate unknown threats and ensure compliance at the same time. That's ThreatLockercom slash twit. We thank him so much for supporting security now and the very important work steve does here. I'm ready to scroll up. I have been very good. You know it's hard for me. I have it right in front of me.
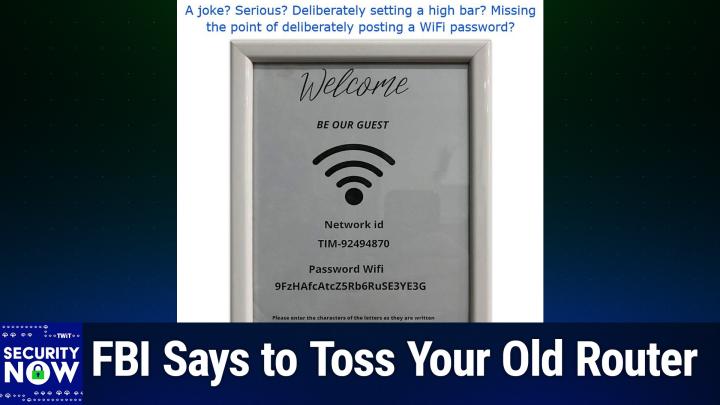
0:10:58 - Steve Gibson
We appreciate having your candid first look, as they they say. So I gave this picture, the caption, a joke, serious, deliberately setting a high bar, or maybe missing the point of deliberately posting a Wi-Fi password.
0:11:19 - Leo Laporte
That is the most annoying password I've ever seen. Okay, so for our listeners who are not seeing, not seeing this first.
0:11:25 - Steve Gibson
We have a guy who enjoyed, or a person, I don't know who. You know what their sex was, a person who had a lot of fun with fonts. This, this is a framed looks like eight and a half by eleven gray sheet. Uh, and actually it's a true photo. You can barely see the reflection of the person's smartphone, that that that bounced off the glass.
Who was taking a picture of this? Because they're like what the heck anyway? This says welcome in a nice big scrolly font. Then it says be our guest in, uh, sans serif ital font. Then they went to great trouble to find the very familiar Wi-Fi icon, you know the dot, with the three radiating semicircles coming off of it. So you know that this is about the Wi-Fi. And so they're saying you know, by all means connect. And so they're saying you know, by all means connect. Well, now then we hit the problem here. The network ID, for a reason that's not clear, is TIM T-I-M, in all caps, hyphen 924-94870. Instead of being, you know being, wait a minute.
0:12:45 - Leo Laporte
That must mean there are 92 million other Tims. Is that where we're you?
0:12:50 - Steve Gibson
know it could just be Barney or something. I mean, what is, it doesn't matter. 924-94870 following Tim. But that's not the worst, leo. No, it's worse, because the password is 9FZHAFCATTCZ5RB6RUSEE3YE3G. Nicely done, very nice. Capital R lowercase u. Capital S capital E three capital Y capital E three capital G Nicely done, Very nice.
And okay. So here's, of course, my point. It's like what Be our guest? First of all, there's no chance that you could type this into any kind of a touchscreen, you know in your phone. Now, the email that I received, as I mentioned, after people saw this. They said well, you know, steve, the nice thing about today's smartphones is you can just aim the camera at that. Oh, that's true.
0:13:59 - Leo Laporte
Take a picture of it. You know, you could even. I'll do you one better. I have a QR code on my wall, so visitors can they just scan the qr code and it joins the wi-fi. You don't have to type anything in at all again. So okay now so here's my question this is a joke, especially because at the bottom it says please enter the characters of the letters as they are written. That's a joke.
0:14:22 - Steve Gibson
Maybe they're just very uh he's he's OCD, I don't know teasing people I think, and so that's my question, exactly so maybe, and so you know, welcome be our guest here's your typing test yeah that's crazy.
Anyway, I don't enjoy the picture and you know, looking at this, I don't have it in front of me, but I found the most perfect perspective correction app for Windows. The photo that was sent to me was taken way off in both directions, so it was a skewed trapezoid from hell. And I found this app some time ago which works exactly the way you would want it to, but nobody else seems to figure this out. It gives you a four-point rubber-banded rectangle where you simply drag the four corners of the rectangle to four corners which should be rectangular on the image, and then it fixes it, and so what we're looking at in this perfectly looks like it's exactly square on image was originally really skewed. Anyway, I'll get the name of it for next week because it's just the best thing and it seems to be. You know, apple has all this weird like. You know, you swing it up and down and back and forth and try to negotiate with it, but when you know that what you want is something square, just drag a square over it. Anyway, I don't know why nobody else has done that. I've never found it on a Windows app and of course, now 25 of our listeners will say Steve, here's the one that I use. It's like okay, thank you. Okay, so my title for this first piece of news was Virginia's Folly and I wasn't sure whether to file this under things that will never happen or good luck with that, because the event was so obviously fraught. Because the event was so obviously fraught and there was a ton of coverage about it Because I mean, like when I did a little bit of Googling it was widely covered, probably because everyone recognizes this is really an issue and we've talked about this a lot found a very clear and concise blog posting, among all the other newsy stuff, from a law firm Hunton Andrews Kurth who specialize in privacy and cybersecurity law. So they're watching these sorts of things happen from their perspective as a group of attorneys. The headline title of their posting was Virginia Governor Signs into Law Bill Restricting Minors' Use of Social Media. And then they explain On May 2nd 2025, virginia Governor Glenn Youngkin signed into law a bill that amends the Virginia Consumer Data Protection Act, the VCDPA, to impose significant and oh restrictions on minors' use of social media.
The bill comes on the heels of recent children's privacy amendments to the VCDPA that took effect on January 1st 2025, so beginning of this year on January 1st 2025. So beginning of this year they wrote the bill amends the VCDPA to require social media platform operators to first, use commercially reasonable methods such as a neutral age screen to determine whether a user is a minor under the age of 16,. To determine whether a user is a minor under the age of 16, and, second, limit a minor's use of the social media platform to one hour per day, unless a parent consents to increase the daily limit. The bill prohibits social media platform operators from using the information collected to determine a user's age for any other purpose or signals that the user is or shall be treated as a minor. Unquote, including through quote a browser plug-in or privacy setting, device setting or other mechanism unquote. The bill also prohibits social media platforms from altering the quality or price of any social media service due to the law's time use restrictions.
The bill defines social media platform as a public or semi-public internet-based service or application with users in Virginia that connects users in order to allow users to interact socially with each other within such service or application and allows users to do all of the following, and there's three Construct a public or semi-public profile for purposes of signing into and using such service or application. Second, populate a public list of other users with whom such user shares a social connection within such service or application. And finally, create or post content viewable by other users, including content on message boards, in chat rooms or through a landing page or main feed that presents the user with content generated by other users. The bill exempts from the definition of social media platform a service or application that, first, exclusively provides email or direct messaging services, or, two, consists primarily of news, sports, entertainment, e-commerce or content preselected by the provider and not generated by users, and for which any chat, comments or interactive functionality is incidental to, directly related to or dependent on the provision of such content. The Virginia legislature declined to adopt recommendations by the governor that would have strengthened the bill's children's privacy protections. That would have strengthened the bill's children's privacy protections. These amendments to the VCDPA take effect on January 1st of next year, 2026. So the last changes to the VCDPA took effect on January 1st this year. This is setting things up for the beginning of next year. This is setting things up for the beginning of next year.
Now, this legislation won't get off the ground before it is enjoined by multiple lawsuits arguing with some strong rationale and probably merit, that the imposition of these restrictions flies directly in the face of the freedom of speech rights enshrined by the First Amendment to the US Constitution. I mean, these things are always immediately sued and then they go into the courts, and it was for that reason that I recently mentioned that I was hoping that the nine justices on our Supreme Court enjoy working the. What we're seeing is the upper echelons of the US legal system are being put to much more use than they've seen in quite a while. You know how many times have we recently heard quote this will eventually need to be decided by the Supreme Court, unquote. You know we're no longer talking about whether party A defrauded party B. Those are easy things to decide relatively. Now we're asking where exactly the line can be drawn when a state wishes to restrict what can reasonably be described as the free speech rights of a group of individuals. Consequently, many fundamental questions surrounding proposed laws and their precise relationship to the US Constitution are now being asked, and they will eventually be tried. So wow, I mean the system is being stressed, but we need to see what the answers are that come out the other end. So, anyway, one more point on this.
In New Zealand, the New Zealand press writes the National Party wants to ban 16-year-olds. Now, I think that Virginia said under 16. So now New Zealand has 16 and under. So, again, this is why my, in my opinion, apple trying to create zones of age I don't know why to maybe make it less obvious when someone's birthday is, you know, okay, but the problem is there's no alignment of any of these laws, not even among states, let alone among nations. So you know, I just think you know, giving the phone an API that lets the app say, you know, is the person above or below a given age, is what we're going to end up with. Anyway, the National Party wants to ban 16-year-olds from accessing social media, apparently all by forcing companies to use age verification measures. So this is the country of New Zealand.
National MP Catherine Wedd, with the backing of leader Christopher Luxon, has put forward a members bill which would follow Australia's lead on cracking down on social media giants. The prime minister said he wanted to explore, picking it up as a quote broader government bill, which is actually a term that means something within their legal framework, which would mean it could become law more quickly. Right now, the legislation does not have government endorsement, which means it would be debated only if it was drawn from the ballot at random, which seems bizarre, but okay. Catherine Wedd said the bill would put the onus on social media companies to verify someone is over the age of 16, over the age of 16, before they access social media platforms, and is modeled off Australian legislation. Wedd said quote currently there are no legally enforceable age verification measures for social media platforms in New Zealand. She said she'd heard from parents, teachers and principals that there wasn't enough protections in place. I'm sorry there wasn't enough protection in place. Quote my social media age appropriate users bill is about protecting young people from bullying, inappropriate content and social media addiction by restricting access for under 16. Now she says under 16 year old. So okay, but before it was over the age of 16. So even they're not sure. The bill would require social media platforms to take quote all reasonable steps to prevent under-16s from creating accounts. It would also introduce penalties for noncompliance, including financial ones.
So here's another piece. You know, this bit of news now from New Zealand reminds us that Australia has recently been exploring similar legislation. So, stepping back from this, I would say that it should be very clear to anyone that you know who's watching everything that's going on that sooner or later, and apparently sooner, we're going to be seeing age-based restrictions on access to social media which have until now been completely uncontrolled media which have until now been completely uncontrolled. So you know, and we know that, that the likes of Meta don't want it to be their responsibility. They're saying it should be the vendor, the platform producers responsibility. So it's a mess and you know, we're seeing legislation being put in place. It's being it's being fought back against by those who don't want it to be done that way. We have seen Apple make some steps forward, we've seen Google make some steps forward. So we need.
0:27:18 - Leo Laporte
I think you made an excellent point, though. Apple could solve this right away just by putting that feature in that you suggested, which is yeah, you know, the parent says this kid is such and such age and uh, and those.
0:27:33 - Steve Gibson
That would be the best way to do it make it the parent's choice right, and apple just needs to give, and google need to give them, that facility, that capability yeah, all you have to do is surface an api and then and that would mean that the worldwide web consortium would define a a little, a new javascript verb which allowed the browser to query the platform for its user's age.
0:27:57 - Leo Laporte
You also legislators, also have to realize you can't keep kids away from all well, that's the other, that's the other.
0:28:07 - Steve Gibson
Point is like nice to have a law right, but there's good, you know neighbors.
0:28:13 - Leo Laporte
Hey, I used to go down the local drug store and read the playboys on the shelf. I mean, there's no way you can keep them safe with a law. Yeah.
0:28:23 - Steve Gibson
Yeah, yeah, I'm continually seeing reports of malicious supply chain attacks where this security company discovers 52 malicious Python libraries, or that security company finds 46 malicious JavaScript libraries and I mean I don't talk about them every week because I see them every week and it's like okay, okay, you know, I mean, so I, I feel like I, I share them enough with our listeners to keep them on, to keep everybody you know aware of the issue, to keep it in mind, to to always bring some caution to going into a repository and saying, oh look, this is just the thing, that this is just the library that I was looking for. I'm so glad someone created this because, you know, the bad guys have figured out that that's what people do and they figured out that they can use the inherent openness of this ecosystem that we've created to hurt people, to get into people's computers, to infect somebody who's in an enterprise, then pivot from their PC, when it's connected to the enterprise network, into the enterprise's network and before you know it they're listed in that ransomware listing site and there's trouble. So again, I guess I want to make it clear that it's not like that only happens when I mention it. It's very much like the ransomware attacks. I see 12 of them every single week. This company, that company, it's like okay, well, that's just boring now because it's in the background, it's constant noise happening. So is all of the repository infection.
And the security companies, bless their hearts that are taking their time. You know, it must just be PR for them, right? They're like well, we found 52 malicious Python libraries. Woohoo, bro, pay attention to us. Are for them, right? They're like well, we found 52 malicious Python libraries. Woo-hoo, bro, pay attention to us. Oh, but our customers weren't affected because our scanners nipped those in the bud. So it's a way of saying and if you were one of our customers, you'd have our scanner in your PC too, and those 52 nasties would have never had a chance to get going.
But the troubling question is do they find them all? And what would not finding? Some look like very malicious and sophisticated Python Trojan, which had remained unfound, hidden for more than three years, was troubling. Their research posting was titled Malicious PyPy Package. Targets Discord Developers with a Remote Access Trojan, and their subtitle was with a remote access Trojan and their subtitle was the Socket Research Team Investigates a Malicious Python Package Disguised as a Discord Error Logger that Executes Remote Commands and Exfiltrates Data via a Covert Command and Control Channel. So I'll just share the start of their long report. They wrote On March 21st 2022, thus the more than three years ago, part March 21st 2022, a Python package, discord, pydebug all one word, discord P-Y-D-E-B-U-G was uploaded to the Python package index PyPy under the name discordpy P-Y error logger.
At first glance, it appeared to be a simple utility aimed at developers working on Discord bots using the discordpy library. However, the package concealed a fully functional remote access Trojan, an RAT. Over time, the package received over 11,000 downloads, placing thousands of developer systems at risk. The package targeted developers who build or maintain Discord bots, typically indie developers, automation engineers or small teams who might install such tools without extensive scrutiny. Since PyPy doesn't enforce deep security audits of uploaded packages, attackers often take advantage of this by using misleading descriptions, legitimate sounding names or even copying code from popular projects to appear trustworthy. In this case, the goal was to lure unsuspecting developers into installing a backdoor disguised as a debugging aid.
Discord's developer ecosystem is both massive and tightly knit, with over 200 million monthly active users, more than 25% of whom interact with third-party apps. Discord has rapidly evolved into a platform where developers not only build, but also live, test, share and iterate on new ideas directly with their users. Public and private servers dedicated to development topics foster an informal, highly social culture where tips, tools and code snippets are shared freely and often used with little scrutiny. Freely and often used with little scrutiny. It's within these trusted peer-to-peer spaces that threat actors can exploit social engineering tactics, positioning themselves as helpful community members and promoting tools like Discord, pi Debug under the guise of debugging utilities that they're familiar with. The fact that this package was downloaded over 11,000 times, despite having no readme or documentation, highlights how quickly trust can be weaponized in these environments.
Whether spread via casual recommendation, targeted DMs or Discord server threads, such packages can gain traction before ever being formally vetted. So the link to the rest of their extensive research is in the show notes for anyone who's interested. They talk about it at great length, but my intent here was to just you know, without wanting to shut down the value that can be obtained, to really put a point on the fact that you know, as they say, there's no such thing as a free lunch. You know, I mean this. This ecosystem that has been created is is so neat. I mean it's so cool to be able to, to have access to other people's freely shared work like this.
But unfortunately, there are other people we don't know and they can be other people who are trying to hurt us, trying to, you know again, typically not us as individuals, but we're the. Now you know, discord developers may well be working with an enterprise and using Discord in an enterprise environment. The bad guys want to get in there and so, you know, end users are no longer the targets that we once were. As soon as cryptocurrency happened and the concept of ransomware happened and encrypting servers and exfiltrating proprietary data and threatening in return for money happened, suddenly all the attention went to how do we get in? And that's through phishing, and that's through contaminating repositories and using those as the back doors into more valuable networks. So it is really happening and this thing sat there for three years without being found do they know how many people have downloaded?
it more than 11 000.
0:37:12 - Leo Laporte
Wow, that's terrible yeah it's funny, because they weren't. I mean, I guess it was indirectly targeting discord because they were going after the developers, right, but I? But I guess once you compromise a developer, you can then compromise their code.
0:37:27 - Steve Gibson
Well, yes, yes, it's the developer. The profile of a developer is one who is looking in the Python libraries for things that will help their work, and so a Discord debugger would be something that a Discord bot developer would say hey, that's great, I want help debugging my Discord app. And so it's on a developer machine who then, you know, works for an enterprise, or maybe he's doing that on his own in the evening on his laptop, and then, you know, brings it into the office, plugs it into the network, and then brings it into the office, plugs it into the network, and now this thing is able to move laterally into their employer's network, which is what they really want. And what you know, leo, what our listeners really want?
0:38:15 - Leo Laporte
No, they don't, but I'm going to do it anyway, I think.
What I really want is a little bit of coffee, A little caffeine While I talk about our sponsor for this section on Security Now, and that, of course, is US Cloud, the number one. Microsoft Unified Support replacement We've been talking about US Cloud for some months now. Microsoft Unified Support Replacement We've been talking about US Cloud for some months now. They are the global leader in third-party Microsoft support for enterprises, now supporting 50 of the Fortune 500. There's a reason 50 big companies switched to US Cloud.
Us Cloud could save your business 30% to 50% over Microsoft Unified and Premier support, but it wouldn't be any good if we're just less expensive. It has to be better, right? Yes, it's better, it's faster, for one thing, twice as fast in its average time to resolution versus microsoft. Uh, that's, that's a good improvement, plus the smartest engineers in the business. So you're getting people really know what they're talking about, and I think US Cloud is willing to tell you stuff that Microsoft's not. For instance, US Cloud now offers an Azure cost optimization service.
Microsoft may not want you to optimize your Azure costs, but really seriously, what was the last time you evaluated your Azure usage? I think everybody understands. You know we probably are spending more on Azure than we really need to. Everybody has a little Azure sprawl if you will spend creep. That's going on. But, good news, you don't have to be in the dark about it. Saving on Azure is easier than you think with US Cloud. They offer an eight-week Azure engagement. It's powered by VBox. It will identify key opportunities to reduce costs across your entire Azure environment. And you're not doing it on your own. You're getting expert guidance from US Cloud's senior engineers. These are the best in the business. An average of over 16 years with Microsoft products. At the end of the eight-week engagement, your interactive dashboard will identify, rebuild and downscale opportunities, unused resources, allowing you to reallocate those precious IT dollars towards needed resources. Or I got a thought keep the savings going by investing your Azure savings in US Cloud's Microsoft support. That's what a few other US Cloud customers have done, but completely eliminate your unified spend. Now that's a real savings.
Ask Sam. He's the technical operations manager at a company called Bede Gaming, B-E-D-E Gaming. He gave US Cloud five stars. His review said, quote we found some things that had been running for three years. Ours. His review said, quote we found some things that had been running for three years which no one was checking. These VMs were, I don't know, 10 grand a month. Not a massive chunk in the grand scheme of how much we spent on Azure, but you know, once you get to 40,000 or $50,000 a month, it really starts to add up. Uh-huh. It's simple Stop overpaying for Azure. Identify and eliminate Azure creep and boost your performance, and do it all in eight weeks with US Cloud. Visit uscloudcom and book a call today. Find out how much your team can save less uscloudcom. Thank you so much for supporting Steve Gibson and Security. Now you support us. If they ask you when you get to US Cloud, you say yes, Steve told me all about it. What is that little thing you got there? That is cool. That's like an e-ink.
0:41:54 - Steve Gibson
I found out it was on some podcast of twits and it's called terminal, one of your oh yeah one of your hosts mentioned it.
0:42:03 - Leo Laporte
Yes, um so you have your google analytics for your website on there.
0:42:08 - Steve Gibson
Yeah, that's so cool yeah, and you can see on april. What is that? 28th? I think Somebody mentioned Validrive and so we had a traffic spike then. But it is, it's battery powered. It runs for three months because it uses e-ink and it updates occasionally. They have a whole bunch of little widgets that you're able to drag Super cool.
So you can compose the screen that you want and it sits running on batteries, as I said, about three or four months, and it updates occasionally. And there's also the reason I was interested is that they have a developer kit that allows you to basically have it display a webpage and so at some point I'm going to have it monitoring, you know.
0:42:56 - Leo Laporte
Yeah, you know, internal uh, server stuff well, as long as we're celebrating, I might as well show you that you were a tiktok star last week. What you did? You talked about microsoft's bold passkey move, you know, getting rid of passwords and uh must have made it to the for you page on TikTok, cause you see here 193,000 views, 2,864 likes, 322 comments. That is very. Uh, those are good numbers, those for TikTok. That's incredible.
0:43:31 - Steve Gibson
Interesting.
0:43:32 - Leo Laporte
Yeah, so congratulations for reposting that you can now say uh yeah, I'm a TikTok star along with everything else. You tell your neighbors.
0:43:43 - Steve Gibson
Yeah, that's me. Yeah, I don't tell them that they look at me and go what. My neighbors have no idea what either Lori or I do. They just know we're nice people. But Lori starts talking about neurofeedback and modifying brain waves and they're like what?
0:44:00 - Leo Laporte
Oh, that's all the rage. Nowadays, though, that's a hot topic. All right, my mouse is stuck. Oh, there we go. I finally got rid of the screen Go ahead my friend Go ahead.
0:44:12 - Steve Gibson
So once upon a time it may have been difficult to toss a perfectly good consumer router into the trash bin. Bureau of Investigation, our FBI posted one of their PSAs, a public service announcement which was titled Cyber Criminal Proxy Services Exploiting End-of-Life Routers. Here's what the FBI wrote. They said the Federal Bureau of Investigation FBI, yes is issuing this announcement to inform individuals and businesses about proxy services taking advantage of end-of-life routers that are susceptible to vulnerabilities. And then they explain when a hardware device is end-of-life, the manufacturer no longer sells the product and is not actively supporting the hardware, which also means they're no longer releasing software updates or security patches for the device. Routers dated 2010 or earlier likely no longer receive software updates issued by the manufacturer and could be compromised by cyber actors exploiting known vulnerabilities. Exploiting known vulnerabilities End-of-life routers were breached by cyber actors using variants of the moon malware botnet. Recently, some routers at end-of-life with remote administration turned on were identified as compromised by a new variant of the moon malware.
This malware allows cyber actors to install proxies on unsuspecting victim routers and conduct cyber crimes anonymously. A proxy server is a system or router that provides a gateway between users and the internet. It is an intermediary between end users and the web pages they visit online. A proxy is a service that relays users' internet traffic while hiding the link between users and their activity. Cyber actors use proxy services to hide their identities and location. When actors use a proxy service to visit a website to conduct criminal activity like stealing cryptocurrency or contracting illegal services, the website does not register their real IP address and instead registers the proxy IP.
The Moon malware was first discovered on compromised routers in 2014 and has since gone through several campaigns. The Moon does not require a password to infect routers. It scans for open ports and sends a command to a vulnerable script. The malware contacts the command and control server and the C2 server responds with instructions, which may include instructing the infected machine to scan for other vulnerable routers to spread the infection and expand the network. Tips to protect yourself, they wrote. Commonly identified signs of malware infections on routers include overheated devices yeah, like when it's mining cryptocurrency with abandon. Problems with connectivity Same. Yeah, like when it's mining cryptocurrency, with abandon. Problems with connectivity same. And changes to settings the administrator does not recognize.
The FBI recommends individuals and companies take the following precautions. They list five If the router is at end of life, replace the device with an updated model, if possible, the device with an updated model, if possible. Second, immediately apply any available security patches and or firmware updates for your devices. Third, log in online to the router settings and disable remote management remote administration, save the change and reboot the router. Fourth, use strong passwords that are unique and random and contain at least 16, but no more than 64, characters. Avoid reusing passwords and disable password hints. And finally, if you believe there's suspicious activity on any device, apply any necessary security and firmware updates, change your password and reboot the router. So you know, this is good, but not surprising, advice for anyone listening to this podcast. Still, it's not anything that most non-cybersecurity-aware users would ever think to consider, so it's a good thing that these sorts of reminders and advisory public service announcements are being made by an entity that the public would trust, like the FBI. So that's good.
Three UK researchers, three from King's College and the third from Royal Holloway University of London third from Royal Holloway University of London decided to tear WhatsApp apart to figure out how it solves the challenges of multi-device group messaging and to see whether they may have left any rough edges in there. Here's how they described their work in their resulting papers abstract, which was short. The abstract was short, the paper was not. They wrote WhatsApp provides end-to-end encrypted messaging to over 2 billion users. However, due to a lack of public documentation and source code, the specific security guarantees it provides are unclear. Reverse engineering its implementation to provide a formal description of the subset of WhatsApp that provides multi-device group messaging. We utilize this description to state and prove the security guarantees that this subset of WhatsApp provides. Our analysis is performed within a variant of the device-oriented group messaging model, which we extend to support device revocation. We discuss how to interpret these results, including the security WhatsApp provides, as well as its limitations. Okay, now, that was their abstract.
What followed was a quite daunting 115-page paper and remember, you know we typically encounter page, you know papers like this that are 16 to 29 or 30 pages. This is a monster. And they start off by explaining group messaging in WhatsApp is based on the signal two-party protocol and the sender keys multi-party extension. For answering the question of how these building blocks are composed precisely is established by the WhatsApp security white paper or unofficial third-party protocol implementations. Now, I'm not going to go into 115 pages because I mean this is really hair-curling stuff, really hair curling stuff, and but it put me in mind of how spoiled I guess I am I know, leo, you are and many of our listeners are by Unix and Linux and signal and other open source security systems and operating systems.
The idea that these researchers were forced to reverse, engineer and divine the operating protocol of a critical encrypted communications applications such as WhatsApp, which is in use, as they said, by more than 2 billion people, seems really wrong. You know, it's true that my own Squirrel client for Windows was not open source, but every single detail about the protocols it implemented and how it did them was scrupulously detailed for the specific purpose of facilitating independent implementations. And all I was doing was creating an implementation of Squirrel's specification that was in the public domain from the first moment I disclosed its operation here on the podcast, and we know that the specification was correct because a number of other people created their own fully working squirrel implementations and everything interoperated perfectly. That's the way these sorts of things should be done. Now, the details of the security protocols that, in the case of WhatsApp, as I said, billions of people depend upon that should not be considered proprietary.
It just that's old thinking. It's like outlawing the export of ciphers using more than 40 bits. You know it's not the crypto way. While I was following the references in this paper, I got a kick out of noticing that they were sorted alphabetically, which brought all of the people's names together, and at the M's we have reference number 50,.
0:54:13 - Leo Laporte
Marlon Spike M.
0:54:16 - Steve Gibson
Private group messaging dated May 2014 and a link.
0:54:21 - Leo Laporte
That's the signal protocol Yep.
0:54:23 - Steve Gibson
Message 51, marlin Spike M the double ratchet algorithm Yep November 2016, and a link to the full specification revision one. And a link to the full specification revision one. Reference 52, marlin Spike M the X3DH key agreement protocol November 2016,. And a link to the full specification revision one. And reference 53, marlin Spike M the Sesame algorithm session management for asynchronous message encryption April of 2017, and a link to the full specification reference revision two.
Our listeners who've been with us from the early days may recognize every one of those specifications and protocols and I heard you recognizing them, leo, oh yeah. And protocols and I heard you recognizing them, leo, oh yeah Because we have examined each of them over the years as we followed Moxie Marlinspike's work from the start, and this is the point I wanted to make. The fact that Moxie and Signal have been sharing all of the details of their work all along demonstrates a fully mature understanding of security. That's the only way they can know what they have done is secure is by publishing it for other academic researchers to examine. By comparison, the fact that Meta's WhatsApp has taken advantage of all the good parts of that work for free, while refusing to disclose the very important workings of their own proprietary, and I have that in quotes. Extensions of that work is what I have a difficult time excusing. Is what I have a difficult time excusing After slogging through the 115 pages of the researchers' work and remember that's their output that they had to do the work in order to produce 115 pages of detailed results.
They summarized their findings mostly by explaining that they were unable to find anything big that seemed to be amiss, but since they didn't have access to any source code or even to complete algorithm descriptions, we couldn't find. Anything is not the same, as we looked at everything that matters and it all looks fine. You know, there were a number of edge cases that they were unable to explore due to lack of information, and some others that they found that were not hugely concerning, but okay. Like revoking the keys from a device when it's coming out of a group chat is a problem, and it's not exactly clear that WhatsApp has done that in a very solid fashion. So these intrepid academics, you know, did achieve something for their efforts, though what is so annoying is their tasks could and should have been so much easier, and nothing is gained by meta hiding what they've done and considering it. Oh, these are, you know secret sauce? No, it's. You know two billion people are depending upon it, not you not having made a mistake. And what we know is mistakes happen and you know they need to be aired in order to get fixed.
Center, the NCSC, which is roughly their equivalent of our CISA, just issued a report looking at the probable effect AI is expected to have upon cybersecurity over the next two years, from now until 2027. Now I have to say I was somewhat relieved to see that that was their time frame, to see that they clipped this to a relatively short-term window, since AI, arguably, is advancing so rapidly that any attempt to say anything meaningful about, for example, the next 10 years would be little more than a flight of fancy. Years would be little more than a flight of fancy. No one has any remote clue what the AI of 2037 is going to look like, or 2035 for that matter. Okay, so they opened this report by explaining who they are and what they used as the source of their various assessments, and they capitalized the A of assessment. So they said NCSC.
Assessment, which they abbreviate NCSC-A, is the authoritative voice on the cyber threat to the UK. We combine source information from classified intelligence, industry knowledge, academic material and open source to provide independent key judgments that inform policy decision-making and improve UK cybersecurity. We work closely with government, industry and international partners for expert input into our assessments. Ncsa is part of the Professional Heads of Intelligence Assessment. We have another acronym, that's the PHIA, the Professional Heads of Intelligence assessment. Phia leads the development of the profession through analytical tradecraft, professional standards and building and sustaining a cross-government community. This report uses formal this is the part I love formal probabilistic language. Then they say see the yardstick from NCSCA product to inform readers about the near-term impact on the cyber threat from AI. To find out more about NCSCA, please contact the NCSC directly.
Okay, now the probabilistic language is. What's so wonderful here? We have a chart. I've got it in the show notes for anyone who is curious. The chart is labeled likelihood of events or developments occurring, and so this is a spectrum, and on the far left we have 0% likelihood of events or developments occurring, all the way to the far right where we have 100% chance. But we need to apparently precisely define our probabilistic language. So they then ask themselves the question language. So they then ask themselves the question how likely is a realistic possibility? What does that mean?
1:01:45 - Leo Laporte
and and they wasted a lot of time on this.
1:01:48 - Steve Gibson
I can imagine the debates back and forth and we got shades of blue and so you know oh yeah at first, this whole effort appears to go right off the rails since, as I said, they present their so-called yardstick which firmly establishes the meaning of, with specific percentage ranges of probability of the various terms their report will use, if they ever actually get to reporting.
1:02:20 - Leo Laporte
It's like debating the shape of the table at the conferences. That's right.
1:02:26 - Steve Gibson
And wait a minute. Who gets to sit where? While I'm certainly no lover of bureaucracy and my first instinct was to balk at this entire thing as make work, I can see the need to define what almost certain means yeah, I mean that could have saved some time just by putting a percentage in the actual they really could have.
Prediction. What fun would that be? Leo, right, you know so. You know. How almost certain are they? And what about highly likely? How likely would that really be, and what's a realistic possibility? Those questions are, all you know, nearly answered using the handy yardstick that they provide, which shows essentially, as I said, a spectrum of likelihoods ranging from remote to almost certain, except it's probably a meter stick, not a yardstick, but other than that.
Oh, that's a good point, although they actually did use the term yardstick, so maybe they westernized it or angloized it, or something. Anyway. So they have remote, highly unlikely, unlikely, realistic possibility, likely or probably highly likely and almost certain. Now, that's the range right.
1:03:46 - Leo Laporte
Somebody's saying in the Discord they're missing the snowball's chance in hell section. Where does that fit in?
1:03:55 - Steve Gibson
So now that we have those, we'll all know what they're talking about when they make the following judgments based upon all of that data that they've gathered from all of their many primary sources. So here they are. We've got six judgments. Judgments Artificial intelligence AI will almost certainly continue to make elements of cyber intrusion operations more effective and efficient, leading to an increase in frequency and intensity of cyber threats.
1:04:31 - Leo Laporte
By the way, since four out of six of their conclusions are almost certainly. They wasted a lot of time on those other colors.
1:04:39 - Steve Gibson
Yeah, but, leo, you have to know where you're coming from. Oh, my God you have to know your roots or you wouldn't know how almost certain they were between systems keeping pace with AI-enabled threats and a large proportion that are more vulnerable, making cybersecurity a scale increasingly important to 2027 and beyond. I'm sorry cybersecurity at scale meaning let's get serious folks.
1:05:11 - Leo Laporte
This contains no information. This sentence no, no. Yes, there will be some systems that are vulnerable and there will be some that aren't, so we better pay attention.
1:05:21 - Steve Gibson
That's right, right, but now number three, assuming a lag.
1:05:26 - Leo Laporte
How much do they get paid for this?
1:05:29 - Steve Gibson
Yes by the word, apparently Assuming a lag or no change to cybersecurity mitigations. There is a realistic possibility thanks to our chart.
1:05:41 - Leo Laporte
I gotta check the chart where is that?
1:05:43 - Steve Gibson
where does that fall exactly? That's kind of in the middle.
1:05:46 - Leo Laporte
Okay, that's 40 to 50 percent now, leo, should, I should?
1:05:49 - Steve Gibson
I note that the chart uh has weird gaps, that is yeah what is this? Notice there's nothing between 35% and 40%.
1:05:57 - Leo Laporte
Yeah, nothing is 37% likely.
1:06:00 - Steve Gibson
Yeah. So in between it being unlikely and a realistic possibility, what happens if something falls in there? I guess that's called falling through the crack. It's literally a crack in the chart.
1:06:15 - Leo Laporte
That's called putting too many numbers after the decimal point is what that is. This is the. You cannot measure this that accurately, but okay.
1:06:22 - Steve Gibson
Yes, precision versus resolution, the two are not the same. No Assuming a lag, they wrote, or no change to cybersecurity mitigations. There is a realistic possibility of critical systems becoming more vulnerable to advanced threat actors by just two years from now, 2027,. Keeping pace with frontier AI. Oh and, by the way, leo, I left off the glossary at the end, where they clearly define what do we mean when we say frontier AI. We're exactly on the frontier with that fall. Anyway, keeping pace with frontier AI capabilities will almost certainly be critical to cyber resilience for the decade to come, even though they're only looking two years ahead.
1:07:10 - Leo Laporte
There's a realistic possibility. That's right.
1:07:13 - Steve Gibson
Oh no, that's been defined, leo, as a realistic possibility.
1:07:16 - Leo Laporte
I'm sorry, sorry, I have to check the averages again.
1:07:19 - Steve Gibson
My uh, what is that? That's sort of a oh. That's still in the middle.
1:07:23 - Leo Laporte
That's only 40 to 50 of a green green yeah, yeah, I'd say it's a higher than realistic possibility. I would, I, I would say it's almost.
1:07:32 - Steve Gibson
I would I would agree, that is a debatable point they should go back to their primary sources, yeah, and see if they don't think that maybe they've low barred.
1:07:39 - Leo Laporte
This Will critical systems become more vulnerable to advanced threat to actors in two years, yeah, uh-huh.
1:07:47 - Steve Gibson
Okay, so there it is, in other words, in the estimation of the United Kingdom's National Cybersecurity Center that apparently has, like maybe, some excess time on their hands.
It appears to be highly likely that the bad guys are going to be quicker to exploit the many possible nefarious benefits offered by AI than the good guys are going to be able to use that same AI, probably hampered by all of the restrictions we're going to put on Cyber Threat, published in January 2024. It highlights the assessment of the most significant impacts on cyber threat from AI developments between now and 2027. It focuses on the use of AI in cyber intrusion. It does not cover wider threat enabled by AI, such as influence operations. Ai and its application to cyber operations is changing fast. Technical surprise is likely Technically and, of course, technical surprise from one's adversaries is never what we want.
So overall, it appears almost certain that it would be a good idea to buckle up folks oh interesting times ahead for the industry and we'll be right here taking a look at everything every week on this podcast, as it happens.
1:09:38 - Leo Laporte
Yes, almost certainly, but not definitely Almost. It's a high reliability.
1:09:43 - Steve Gibson
Yes, because, after all, we have never missed a week, so it's a realistic possibility.
1:09:51 - Leo Laporte
I think what we should do, leo, before we start in our listener feedback yes is remind our listeners um I think there's a high likelihood that there's an ad coming up.
1:10:03 - Steve Gibson
Is that what you're saying it would be?
1:10:04 - Leo Laporte
there's a reasonable certainty oh, you know, sometimes government's just good for one thing. A comedy relief. Our show today, brought to you by Hawks Hunt. Oh, actually, this is great. If you are at all concerned, perhaps, that you will be attacked in the near future by a spear phishing attack, you need to know about Hawks Hunt. If you're a security leader, you get paid to protect your company against cyber attacks right, but it's getting harder, and I don't need any UK chart to tell me that.
More cyber attacks than ever, phishing emails generated with AI. No longer can you just say well, the grammar is bad on that one, it must be a fake. I mean, these things are indistinguishable, almost indistinguishable, from the real thing. So you've got to train your employees. But legacy, one-size-fits-all awareness programs they really don't stand a chance against today's new attacks. They send at most four very generic trainings a year. Most employees ignore them. In fact I I'll go a step further find them annoying, not helpful. And then, when somebody actually clicks right, they're forced into embarrassing, tedious training programs that feel more like punishment than information.
Well, there is a better way. More and more organizations are trying hox hunt. This is a brilliant solution out of finland. This is a great company. Hoxhunt goes beyond security awareness. They gamify it. Basically, they change your employees' behaviors by rewarding good clicks and coaching away the bad. So you get an email, your employees look at the email. Whenever they suspect an email might be a scam, they just look at Hoxhunt will tell them instantly, saying yeah, you're right, providing a dopamine rush that gets your people to click, learn and protect your company. It's a proven fact. Gamifying stuff makes it better, makes it a better learning environment. Right, it's more fun and you learn better.
Now, as an admin. For you, Hawks Hunt makes it easy to automatically deliver phishing simulations across any platform. You use email Slack Teams. For you, hawks Hunt makes it easy to automatically deliver phishing simulations across any platform. You use Email Slack Teams whatever you're using. And, by the way, you're also using AI to mimic the latest real-world attacks. So don't worry, you don't have to do a lot of creative thinking. Your phishing attacks will look real because they're using the same tools. This is great too.
Simulations are personalized to each employee based on department location and more. They're not generic, they are targeted, you know, and instant micro trainings solidify understanding. Micro training means you don't spend hours sitting and watching a flash slideshow. No, they're quick, they're enjoyable and they solidify understanding and they drive they truly do drive lasting, safe behaviors. You can trigger gamified security awareness training that awards employees with stars and badges, boosting completion rates, ensuring compliance. You get a huge library of customizable training packages and you get tools that make it easy to generate your own with AI.
Hoxhunt has everything you need to run effective security training in one platform, meaning it's easy to measurably reduce your human cyber risk at scale. But you don't have to take my word for it. There are over 3,000 user reviews on G2. They make Hoxhunt H-O-X-H-U-N-T, by the way Hoxhunt the top-rated security training platform for enterprise. They got easiest to use. They got best results. It's also recognized as a customer's choice by Gartner. Thousands of companies use it, including names you know, like Qualcomm, aes and Nokia.
Hoxhunt is being used to train millions of employees all over the globe, and I talked to the Hawks Hunt folks and I'll tell you one other thing that I thought was great. Your employees will actually ask for more fake phishing emails they like it's so much fun, it's so gratifying, the rewards are so great. They'll say that's I want more. Keep them coming. It's fun and you know what what? When something is fun, it works. Visit hoxhuntcom security now, today, to learn why modern, secure companies are making the switch to hoxhunt. That's hoxhuntcom security now h-o-x-h-u-n-tcom security. Now, you know, when you make it fun to learn, people really learn, and you make it unpleasant and hard to learn, it ain't gonna work. You need hawks hunt. Hawks hunt dot com slash security now. If you want, steve I, I can have them send you some fishing emails for just they. It lights up and it's so cool it. It's really, really cool. Anyway, you would probably catch them all, I'm sure you would Okay.
1:15:02 - Steve Gibson
Jim Reed said Dear Steve, in SN 1024, you quoted an email from Alex regarding speed test providers online and he quotes me. There are dozens and dozens of them. And he quotes me there are dozens and dozens of them. Even white label versions of the most infamous, the Ookla speed test, is that I've never really trusted the results because most of these are all about ads and the like.
Jim says as a former ISP executive, I spent a good deal of my time in speed test discussion, so he's an ISP executive on the other side of all this. He said until 2023, the OOCLA service was operated on behalf of the Measuring Broadband America program of the FCC. Using these servers would help provide some accountability back to the ISP. He says my ISP maintained a relationship to see aggregated data to help understand how we were doing so that's kind of cool. They were looking at what their own users were seeing out at the subscriber end in order to get that feedback. He said here's a big secret you should know More times than not.
It's not the ISP that has the network problem causing slowdowns. It's not the ISP that has the network problem causing slowdowns, it's people with a TV on the patio on the edge of their Wi-Fi coverage going. Why can't we see the game? It's someone speed testing a gigabit connection with 100 base T Ethernet on their machine. It's an eight-year-old iPad that has old generations of Wi-Fi. I could go on. But you understand the issue.
I'm not exempting the ISP from the discussion because things happen on networks. It only takes a few people to decide they need to download all 700 plus episodes of the Simpsons now to cause in-network impacts. The ISP needs to manage for those potentials and sometimes they just can't see things coming. Everyone starting to work from home during COVID is an example. If I had to give advice on speed testing, here's what I would suggest. If you're concerned you're getting what you're paying for, test from a wired connection on your best device. If that doesn't meet expectations, talk to your ISP support team. He said Steve, I've been out of the ISP game for five years now, but I always feel like going back to the basics is a good way to start troubleshooting. Since my retirement I get the latest episode of Security Now every Wednesday morning and start listening on my walk. Thanks for continuing my computing education far past retirement. Best, Jim Reed. And then he says PS 73 to W6TWT from N4BFR.
1:17:46 - Leo Laporte
That's me, W6TWT.
1:17:48 - Steve Gibson
I knew the twit, the TWT, that's great.
1:17:51 - Leo Laporte
And a 73 back to you, Jim.
1:17:53 - Steve Gibson
Yeah, jim's experience and his observations matches my own. I've always found that any interruption in my cable modem's connection is due to something on my end rather than something at Cox's end. I'm sure they occasionally need to rearrange things at their end and when nothing seems to have changed on my end, it would seem obvious that the other guy must be to blame. But almost invariably when I mess with connections, even those that have been problem-free for years, or I reboot something that appears to be running just fine, the problem will be resolved and it's always a big relief for me since I have far more control over my end than I have over Cox's end. So you know, I'm happy if it's my end because I can fix my end and my understanding of IT in general. I control a bunch of different web servers on AWS, alicloud and others. So I was interested in your discussion of changing the SSH port, which I have done on one server. On AWS and AliCloud. You can configure the ports you can use to connect to the server or disable them entirely. What are your thoughts on disabling them completely, then logging in to AWS to re-enable them before you SSH in or use AWS built-in console? He says I don't actively monitor SSH connection attempts, mostly because I know it would be a bit scary, but your comment on reducing traffic to the site really would be an advantage for almost all web servers. Cheers Simon, and I think Simon's approach makes a lot of sense. You know, what we're hoping to eliminate by moving a port out of the main traffic pattern is its overall exposure. So if the option exists to only enable remote access during those times it's needed, by all means take that option. A closed port is even better than an open port that's been relocated to some backwater location. John Borgan wrote hey, steve, I just got done hearing you talk about CloudFlare speed test, and wow, it sure is good. Just got done hearing you talk about Cloudflare Speedtest, and wow, it sure is good.
I want to share my favorite utility though, because it's unique in a few ways. It's testmynet. So T-E-S-T-M-Y dot N-E-T. He said what it does that I haven't seen anyone else do is actually upload and download chunks of random data, giving you a much more accurate view of your bandwidth instead of just a theoretical throughput. You can also schedule a speed test to happen every 15 minutes or hourly if you leave the tab open, so you can get a better understanding of your bandwidth throughout the day and it runs natively in any browser, including phones and pads. Anyway, I just wanted to share it because it's my favorite. Thanks for all you and Leo do. Okay, so I just went over to TestMynet and I saw that you had Leo also and yes, it looks nice. You know, it's certainly a consumer friendly site with some pretty graphics, and the domain testmynet is convenient and easy to remember.
The only thing I'll mention is that what all of these bandwidth testing sites are doing is uploading and downloading chunks of data. They don't have any choice. That's the way they work. I can't say for certain whether that data is random and in truth, whether the bits are all zeros or all ones, or alternating ones and zeros or random, makes absolutely no difference to the outcome. Just for the sake of argument and illustration, if some form of on-the-fly compression and decompression existed in generic internet connections, then the content of the data that was being sent and received would matter, since, as we know, anything encrypted is, by definition, absolutely uncompressible. Anything encrypted is, by definition, absolutely uncompressible, but typical data, you know, is not being compressed end to end. We don't have compression on by default on internet links. So anyway, I'm happy to put testmynet on everyone's radar. It looks like another useful speed test.
Steve Main said Hi, steve, I wanted to share with you just how wrong ChatGPT can be using the paid version of ChatGPT 4.0. It is such a great tool and it's still useful, but you have to be very careful, as it can be so confident in its answer, even if asked. Are you sure it took me proving it with a screenshot before it would admit it was 100% wrong and never once double-checked its own work, while it told me to double-check my work. I wanted to share this as I really think that this is an important point to drive home to people to be very careful using LLMs, he said. This is why I do not think they will be replacing anything anytime soon and they're just next generation search engines. I use it for coding PHP and JavaScript and it is amazing how much it fails so many times. It's great for generating code fast, but it's so buggy and it just hallucinates functions that don't exist. Again, still faster, but I've now had about 50 screw-ups with it over two months with it on a coding project. So anyway, I know that Steve Main's experiences, findings and what he's related echoes many others and mine as well.
I thought it was notable that he referred to using AI as a next generation internet search engine, since, as I mentioned several months ago, that's how I've sort of found myself using it and I know I've just heard you, leo, and Alex talking about that on MacBreak Weekly that you know it arguably has impacted some of Google's direct use, because you can you know you can get good search answers out of ChatGPT, which is now able to also look at the web, where I guess initially it wasn't so. Anyway, just another bit of feedback on yes, it's not like we like. We yet have the perfect Oracle that's going to give us, you know, perfect code every time. I still hold that if anyone actually has an interest in creating a perfect coding AI and I think there's big bucks in doing that it really ought to be possible and it's probably not going to be a generalist that you can also ask it how to tie your shoes. Lou Wolfgang wrote.
Hi Steve, in regard to your recent explanation of SSD data retention issues, the thought occurred that it would be nice if just reading from all cells would refresh their charges. I'm reminded of reading from core memory, where the cores have to be flipped to read their polarity, if I remember correctly, and he says, yes, I've used core RAM. And well, lou, I don't know if you know, you probably do know that I've used it too. I recall that we talked about-.
1:25:46 - Leo Laporte
You've seen it. You've actually used it. That's amazing. I've seen it.
1:25:51 - Steve Gibson
I've used it, I've held it in my hands and, in fact, I forgot this was going to happen. I could hold up a. I have it, I own core.
1:26:01 - Leo Laporte
Oh yeah, I have some in my. I have some too. I have some framed core memory.
1:26:04 - Steve Gibson
Yep yeah, but I never. I can't claim never having used it.
1:26:07 - Leo Laporte
When did you use it? Um, didn't they have solid state by the time you were no?
1:26:14 - Steve Gibson
no, no, those PDP-8E were. And, leo, they had 4K, of course. I mean 4K words, 4,096 12-bit words, because those are 12-bit mini computers. And that was where I learned my first assembly language was programming the PDP-8E. When I was I think I was a sophomore in high school and then afterwards, after Berkeley, I worked for a company called Mini Computer Technology. We had Nova and Data General machines and those were all Core. So I mean Core was around through the 70s and early 80s Because while there were semiconductor memories, they were still 4,096 bits and they were like $1,000. Yeah, so you needed a bunch of those to create words or bytes and it was just so expensive back then and the density was still so low You'd think Core would be more expensive.
1:27:23 - Leo Laporte
Somebody had to wire all that stuff. Yeah, okay.
1:27:27 - Steve Gibson
Yeah, wow. So Lou is correct. Core memory used a technology known as destructive read, because the process of reading a memory location inherently destroyed what was originally stored there. The way it worked was that. The reason it was called core memory is that these little, as they called them, cores, were circular ferromagnetic rings that have wires threaded through them and, being a closed ring, the ring could be magnetized in either a clockwise or counterclockwise direction and a sense wire, as it was called, would run through the center of the ring. It was able to sense, as a beautiful picture, when a ring switched its direction of magnetization, since this switching event would induce a pulse in this so-called sense wire running through the ring and that pulse would be picked up by a sense amp running through the ring and that pulse would be picked up by a sense amp. So the process of reading out a location of data from core memory required all of the rings representing the bits of that memory location be written in the zero direction, that is, be pulsed. So they all switched to the zero direction. Now, when that happened, only those rings that were originally set in the one direction would be reversed to the zero direction and that reversal event would produce a pulse on their respective bit sense lines. Respective bit sense lines. This allowed the computer to determine what had been stored in that location.
Now and Leo, so what?
1:29:30 - Leo Laporte
you're seeing is that red wire, that red wire which loops back and forth over and over.
1:29:32 - Steve Gibson
Yeah, yeah, that is the sense line for that little chunk of memory, and you can see that there's it. It's actually a continuous loop. Two wires come out from the left and then that wire, you know, zips back and forth, passing through each ring exactly once, and then goes back out to the left so that, by the way, they never were able to manufacture these with machines.
No, people actually threaded them hand, hand threaded them those cores and boy, they got very, very tiny over time. Yeah, because you know again, density always wants to go up this is a 128 byte core memory.
1:30:20 - Leo Laporte
This is from wikipedia. Very, very cool, yeah, yeah.
1:30:26 - Steve Gibson
So anyway, in order to determine what was in there, you had to write. You wrote all the cores of one location to zero. So any of the cores that had been set to a one direction were forced to reverse direction, and there was that direction reversal that induced a pulse in the sense line that then was able to be picked up. So now you know what was stored in the memory, but unfortunately you've just erased it. You've just set it to all zeros in the process. So if the instruction you were executing was, for example, a load loading what's in memory into a register, then you would need to immediately rewrite what was read from it back into it, and so it would be a read-write cycle. It would be a read-write cycle, but what was really cool is what if we wished to increment a binary value stored in a memory location like that, you know, to add one to it. So the clever computer designers of the era realized that this could be accomplished at the same time as that necessary rewrite of the original data for that location. It was known as a read-modify-write cycle, where, after reading a value from core memory, the value that had just been read would be passed through an adder to add or maybe subtract a one from it if you wanted to decrement the value in memory, and that modified value would be what was rewritten into the core memory instead of replacing the location's original value. So a core memory's cycle time, which was the time it took to read and rewrite, or read, modify and write, that was it turned out.
That was the slow part of computers of that era, the electronical part. They could do really fast compared to the actual physics of ramping up the current, giving the core time to switch its field, and then ramping the current back down, capturing those pulses, seeing whether they exceeded a minimum peak value, deciding that it was a one. All of that took time. So it was the memory cycle time that determined the rate at which instructions could be executed.
So anyway, lou's point was a good one. If reading from SSDs could refresh the charges stored in their cells, then a simple read pass could be used to keep the bits firmly written, could be used to keep the bits firmly written. Unfortunately, as we know, that's not the way today's NAND-style flash memories operate and, frankly, given that memory is in general read much more frequently than it's written, if we had to choose which process reading or writing would cause cell fatigue. It's way better the way it is, where the least frequently performed operation, which is to say writing, is the one that takes a lot more time and then also produces the wear on the cells.
1:34:06 - Leo Laporte
I wonder what the proportion of reading to writing is. On average it's probably 10 to 1 at least.
1:34:12 - Steve Gibson
Oh, I would guess it's more like 100 to 1. I think it's very high.
1:34:16 - Leo Laporte
You don't change data that often.
1:34:18 - Steve Gibson
Nope, nope and that's why we see it slowing down is that the cells are almost never being rewritten, unless there's some reason to do that, right? Chris said hey, I was just listening to this episode and the listener story about Verizon oh no, it was about horizon. Yes, about horizon was interesting. He said about six months ago I wanted to try their wireless gateway. I went to a local store and they would not sell me anything until I unfroze my credit and let them run a credit check. That's normal. Yeah, exactly. He said.
I'm not sure if that listener had done that or somehow the bad guy weaseled around it, but I tell anyone who will listen that they're crazy not to freeze their credit, given the protections it gives you in the real world too. Enjoy the show, chris. So I figured I'd just share Chris's experience for the sake of another viewpoint, given that the criminal purchaser presumably walked out of the store with a brand new multi-thousand dollar smartphone and that their credit worthiness would seem to be a huge factor in that. Uh, it is indeed puzzling how this happened to the person who wrote to me before. You know, perhaps it was just vendor error at the horizon store.
1:35:47 - Leo Laporte
Yeah, or you know, remember customer service reps try to be friendly and nice. Yeah, if you can persuade them to bypass their normal protections. You know, and a lot of Packers.
1:35:58 - Steve Gibson
And they probably get. I'm sure they get credit for selling an expensive phone. Yeah, that's true too. I wonder if they get dinged when it doesn't get paid for. Get paid for.
Lee McKinnell said I decided to pull the plug on my Microsoft password and I already had pass keys. Oh, as I already had pass keys set up, he said Microsoft makes you jump through some bizarre hoops. First, install the Microsoft Authenticator T-O-T-P. You know authenticator, time-based authenticator app on my device. He said it lets you use other password apps for T-O-T-P code verification. So I set it up in Bitwarden. But you need their app to turn off passwords. He said we'll get to that soon.
App to turn off passwords he said we'll get to that soon. Second, verify you have the TOTP app installed by providing a generated code as verification. Turn on passwordless login from Microsoftcom. And then, fourth you are then prompted to open Microsoft's Authenticator app to verify you want to disable passwords on your account. Then he said yay, I am now passwordless. He says now logging in passwordless. First, enter your email address. Second, you're prompted to verify login with the Microsoft Authenticator app, asked to select the matching two-digit code in the app. That was interesting. I don't know what that meant. I'm just reading what he shared.
He said at this point I selected other ways to sign in because I have pass keys. And he says shouldn't this be the default? And he says shouldn't this be the default? Then, three, the first option is now use your face fingerprint pin or security key. And then, fourth, the passkey process is then started so I can log in. And then he said he finished.
At this point I'm unable to remove the TOTP login option from my account or set passkeys as my default login option, so it sounds a little screwy to me. I haven't tried doing any of this myself yet, so I'm now as confused as Lee sounds. I don't dare mess up my original Microsoft account, since it's tied to my access to developer tools and downloads. So what I may do is just create a new account, a separate account, for testing, but I have not done so yet. I imagine I'll hear from other listeners who will help us figure out what's going on. Assuming that Lee is correct, it's annoying that Microsoft appears to force the use of their own authenticator app, though I'm not that surprised, since all time, as we know, all time-based one-time password apps should be equal and, in fact, allowing the user to use the one they prefer to use makes the most sense. You know. It makes much more sense than forcing them to use, you know, a specific app that's certainly not in keeping with the way we would expect it to work.
1:39:16 - Leo Laporte
I think it's what it's doing is different from, uh, the. I don't want to show this. It's an eight digit number. I took off I just I did disable my password in microsoft. I did not find it difficult, but I also use. I don also use it. I don't use the Microsoft Authenticator for anything but Microsoft.
1:39:34 - Steve Gibson
Right.
1:39:34 - Leo Laporte
But I've been using that for a long time to log into my Microsoft account. You know, it says on your computer a two-digit number and then you have to confirm the two-digit number in the Authenticator. You've done that right. I've not used Microsoft's Authenticator Well, you've done that right. I've not used microsoft's oh authenticator. Well, I'm not surprised that it. I mean, I had, I. But since I use it, it was a very simple thing to disable a password. I had, okay, I had some. You know, I was a little nervous about it, but you told me it's better not to have any, it is better not to.
1:40:04 - Steve Gibson
So you were able to delete your password yeah in fact it says right now.
1:40:09 - Leo Laporte
I don't want again, I don't want to to show you, but it says this account does not have a password. Nice, you can use this device to sign in instead.
1:40:17 - Steve Gibson
Nice, okay, so this is not just a TOTP, then it is a passkey kind of a situation. It is a passkey authenticator A single sign-on. Okay, yeah, so it's not a six-digit TOTP that actually.
1:40:33 - Leo Laporte
That resolves our confusion, yeah yeah, but it works great. I'm very happy with it, nice.
1:40:38 - Steve Gibson
Yeah, yeah, bienvenido del Rosario, said he said, dear Steve, I'm a longtime listener and Club Twit member from the Dominican Republic. Yay.
1:40:54 - Leo Laporte
I wanted to share my?
1:40:55 - Steve Gibson
yes, I wanted to share my experience with an open SSH port on my home server After hearing your recount of the many authentication attempts Galen was receiving on the Security Now podcast, episode 1023. Galen was receiving on the Security Now podcast, episode 1023. I was using public private keys Good, best way for my own login Get this, leo but I had between 70,000 and 80,000, 8,000, 80,000 daily failed authentication attempts.
1:41:31 - Leo Laporte
That's somebody hammering you, wow, yeah.
1:41:34 - Steve Gibson
After installing and configuring, failed to ban. The attempts went down to around 20,000 per day. Even though it was a big reduction in failed attempts, I still was feeling very concerned. I started reading posts about how to mitigate even more of the failed attempts and landed on a very simple solution Change the SSH port from the default of 22 to any other number in the user port range from 1024 to 49151. And voila to 49151. And voila All failed attempts ceased right away. Since then, I resorted to just closing the open custom port and I used Tailscale to access my home lab and I've been very happy ever since. I hope you find this information helpful. Best regards, bienvenido del rosario.
1:42:31 - Leo Laporte
So so I stayed corrected. I'm going to change the port.
1:42:34 - Steve Gibson
Yep makes sense to get it out of the main trajectory.
All the incoming missiles are aimed at port 22. Scott shable said hi. The recent discussions about the use of non-standard ports for services that don't need discovery validates my use of the practice for years, so thanks. The latest SecurityNow discussion got me wondering what about a non-standard port on an IPv6 address. I can't imagine how it would be easy to scan and find it Again, not for security, but for why not? He said. I still have IPv6 turned off on my network, but I'm wondering if I should start working to turn it on. Thanks, scott.
So it's true that moving to IPv6 would dramatically increase the address space the bad guys would need to scan. Although only a fraction of the total 128-bit IPv6 space has been allocated to the world's ISPs, it's still true that the world's ISPs now have vast IP space for their customers and, like Scott, I had also been routinely disabling IPv6 on my networks since being old school. I saw no need for it, but my work on the IPv6 capable DNS benchmark code required that I have IPv6 IPs and IPv6 protocol up and running, and it's been working without any trouble, both here on my Win7 box and on my Win10 box in my other location. That said, among those who have been testing the early pre-release benchmark code. There are many whose ISPs are not offering IPv6 and appear to have no plans to do so, so I've needed to have the benchmark accommodate its users who do not have access to IPv6. They'll still have IPv4, dns over TLS and DNS over HTTPS, just not IPv6.
And after the benchmark verifies that they need to skip IPv6, it won't bother them about it. But until they do, it says, hey, you don't have IPv6 working. Do you know that? Do you want to? Should you Anyway? So, yes, you could certainly play with IPv6. It works, and I've got a great note from a contributor and friend online named Greg Bellio. Let's take a break, and then I'm going to share what someone who calls themselves Fer uh, in our groups uh, has to share.
1:45:31 - Leo Laporte
I think I'm familiar with ferrix. This episode of security now is brought to you by thinks canary. I want to show you something.
I don't know if you're familiar with this, this little device looks like that is a usb, external usb drive, except, you might notice, there's an ethernet connection on there that, my friends, is my thinks canary honeypot it. It might if you, if you were no snooping around my network looked like a synology nas to you or a windows server or linux box, might even look like a skater device, because this little box is a honeypot, a thinksary, a honeypot that is easy to deploy, easy to configure. And if someone, a bad guy, who's penetrated my network, tries to access that little device there or the lure files I've created with that device, little phony Excel spreadsheets that say employee identities or I, actually you can put them on google drive too. I have one on google drive. I know it works because I, a couple of months ago I was testing and I made a, a fake pdf that said something like employee information, and put it on my google drive and russell, our it guy, said somebody just accessed that file. I said yeah, me, it's, it's the real thing, it works, it's so cool.
You will get if you somebody tries to access your fake synology nas or your ssh server or your scatter device or those lure files, you will get an alert immediately from your things to canary and you'll get it any way. You want email texts, sms, uh, slack, syslog. Of course there's an API. You could write your own code. It supports webhooks and on and on and on. Basically any way, you want to get alerted, or all of them. Thing is, you're not going to get alerts. There's no false alerts, unless there's somebody in your network attacking your ThinkScanary or those lure files. Choose a profile for your ThinkScanary device. You register with a hosted console. You Choose a profile for your ThinkScanary device. You register with a hosted console, you get monitoring, you get notifications and then you know, you just sit back. Attackers who breach your network, or malicious insiders and other adversaries. They can't help but make themselves known because they look at that ThinkScanary and they don't think it's a honeypot, they think it's something juicy and delicious and they can't wait to get their hands on it. And then you will know they're in your network. Visit canarytoolstwit.
I'll give you an example. You know how many you have really depends on the size of your network, how many different nodes you have and things like that. But let's say you're a small business. You want five Thinks to Canaries, $7,500 a year. You get your own hosted console, you get upgrades, you get support, you get maintenance. Oh, and if you use the code TWIT in the how did you hear about us box, you'll get 10% off the price for life not just for the first year for as long as you have your Thinks Canaries.
Now if that weren't enough, I'm going to give you one more thing that's very important. This is a no-risk offer because you can always return your Thinks Canaries with their two-month money-back guarantee, and you get a 100% full refund. I should mention that in all the years we've been doing these ads I think eight of them now that refund has never been claimed. That refund has never been claimed. Once you get a Thinks Canary or two in your network, you'll say how did I live without it? Visit canarytools. Slash twit. Enter the code twit in the how did you hear about us box C-A-N-A-R-Y dot tools. Slash twit the Thinks Canary. This is genius and it really works. And it's so cute. The thinkst canary. Give it a try today. We thank him so much for supporting steve. They really understand how important the work is here that steve's doing, so we appreciate that support. All right back to security now.
1:49:26 - Steve Gibson
So greg said hi, steve greg Ferex, here under a different email due to the mailing list. Regarding Windows 11 vertical taskbar, I thought you might enjoy knowing there's a bit of a story on this one, matching your intuition. There are some tools that give you back the Windows 10 taskbar or something like it on Windows 11. The Windows 10 taskbar or something like it on Windows 11. Some work by turning back on code that MS has disabled and may at a time delete, or by being shell replacements Stardock and start all back are examples. He said I wasn't satisfied with that because I'm accustomed to my taskbar behaving precisely how I want it to. Since Windows 7 through 10, I've run the famously useful 7 Plus Taskbar Tweaker utility. He said it improves all kinds of dumb behavior and limitations in the Windows taskbar management experience without replacing the taskbar or explorer.
Over a year ago, when I determined that MS would not support the only sensible vertical taskbar in Windows 11, I looked to Michael, the author of the above taskbar tweaker tool. He's been improving my taskbar experience ever since Windows 7. Could he revert, oh could he vertify the Windows 11 taskbar? I learned that Michael now makes a generalized system called Windhawk W-I-N-D-H-A-W-K to inject various user-selected changes into the Windows UI experience, instead of a monolith with a million checkbox features like the old tool. This is more of a framework that runs only the plugins, aka mods, that each user wants. It doesn't replace Explorer or any other process, but instead just inserts clever little hooks here and there to make Windows do its bidding.
Michael looked into the vertical taskbar issue and despaired. Windows 11 taskbar is an almost complete rewrite. Turning on verticality in the new bar cannot simply be done, since it was never implemented by MS in the first place. It would take at least weeks, if not a couple months, of development to build such a feature into the Windhawk system, if it was even possible at all, and more time than Michael could afford to spend on such a hobby project. So that's where he left it. But my company small development staff, including mostly me, rely on a vertical taskbar and it would be a massive efficiency hit to lose it. So we contracted with Michael to build the feature for us and although we paid for the initial development, we don't own it. He says it also provides feedback to make it better over time, a concept I know you're well familiar with with your own product development strategy.
In any case, I present Vertical Taskbar for Windows 11. And I've got a link in the show notes and he said, and a somewhat dated Reddit thread about it and I have a link there too. There too he said I don't get anything. Yes, leo, look at that. He said I don't get anything for touting this tool, and I know the idea of running such an extension may not be universally appealing, but I thought at least you'd find it an interesting tale. I think you, michael, and I share a certain perspective. We don't write operating systems or build the SSDs. Windows didn't plan on WinHawk being there. Active Directory didn't understand Yuba keys on its own, which, by the way, is what Greg added. Hard drives aren't built to expect spin right or read speed coming along. But with a little leverage in the right place, we can make other people's systems work better than their original design parameters. I'm sorry.
1:53:52 - Leo Laporte
Go ahead. I didn't mean to interrupt and he said and there's no feeling quite like it.
1:53:56 - Steve Gibson
This is an amazing tool. It is Leo Holy come all and it's free. Yes, it is an amazing piece of work. So I perked up when I saw email from Greg in the first place. I know him quite well from his many years of involvement and contributions to GRC's various online forums, and this Windhawk system which he brings to our attention is truly amazing. So go to Windhawk W-I-N-D-H-A-W-K dot net windhawknet. Then, at the top of the page, click Browse for Mods, which is what Leo did or go to windhawknet slash mods. By default, the page is sorted from the most popular, most installed to least, with the most having nearly 143 000 users and the least having two. And oh my god I have no idea this is how many mods there are overall.
But the mod list page scrolls and scrolls and scrolls nearly without end.
It's got to be hundreds and hundreds and they are very specific mod tweaks it's not just taskbar, it's everything and I mean wow yep so for so, for example, I'll uh reading from the most popular windows 11 start menu styler is a mod Customize the start menu with themes contributed by others or create your own. Then we have the Windows 11 Taskbar Styler Customize the taskbar with themes contributed by others or create your own. The Taskbar Height and Icon Size Control the taskbar height and icon size. Improve icon quality for Windows 11 only. Or, by the way, all this is Windows 10, unless it's Windows 11. Windows 11, oh, and probably Windows 7 too. Windows 11 notification center styler Customize the notification center with themes contributed by others or create your own Taskbar volume control. Control the system volume by scrolling over. Create your own Taskbar volume control. Control the system volume by scrolling over the taskbar.
Better file sizes in Explorer details Optional improvements Show folder sizes. Use MB and GB for large files rather than always being stuck on KB, rather than always being stuck on KB. And also, if you want, use the IEC terms. You know K, lowercase, I, uppercase B instead of KB. We have taskbar clock customization Customize the taskbar clock. Define a custom date time format. Add a news feed. Customize fonts and colors and more Slick window arrangement. Make window arrangement more slick and pleasant with a sliding, animation and snapping Taskbar labels for Windows 11. Customized text labels Well, I could go on and on, because there's literally hundreds of these little tiny mods. How does it do this?
1:57:05 - Leo Laporte
And Leo did I fail to?
1:57:07 - Steve Gibson
mention that all of the source code is provided. If you click on the details for any mod, the tabs are details, source code and changelog. So, as Greg said, these are all going to compile down to very tiny modules because you can click on source code and look at the source code of these modules to see how they work.
1:57:34 - Leo Laporte
It's like they're written in C.
1:57:36 - Steve Gibson
That's interesting. The mods page can be sorted many ways and it has an incredibly fast and responsive incremental search. Since I was curious about the vertical taskbar, greg's company commissioned, I entered V-E-R-T and was looking at vertical taskbar for Windows 11, which describes itself as, finally, the missing vertical taskbar option for Windows 11. And I put a picture of it in the show notes. I mean, it looks like exactly what you want, yep, there it is. So this, you, you want?
1:58:10 - Leo Laporte
yep, there it is. So this you used to be able to drag the taskbar around. They turned that off for windows 11 you never had that in windows 11 from it was.
1:58:19 - Steve Gibson
It's always been in in all previous windows and windows 11. They just unilaterally decided nope, you're gonna, this, we're going to, and what you can do now is at least you can have it float over to the left, so that so left alignment they have they've condescended to, but no, but not verticality. There's none of that.
1:58:41 - Leo Laporte
Wow, so now we have it and you still use windows, huh.
1:58:48 - Steve Gibson
Leo, that's where everybody is.
1:58:50 - Leo Laporte
I know you have to.
1:58:51 - Steve Gibson
I write apps for the majority desktop, and it's all Windows, yeah, wow.
1:58:58 - Leo Laporte
It's really interesting that you can write code that will modify the operating system this dramatically. I find that fascinating. Yeah, modify the.
1:59:09 - Steve Gibson
UI.
1:59:10 - Leo Laporte
Yeah, yeah, yeah.
1:59:13 - Steve Gibson
Well good. Thank you very much and I have no doubt that windhawknet is going to get some traffic from people saying, oh, I want to see what I can do and then doing it there's a lot of stuff and doing a really nice job of it. I love the idea of it being just a little framework and then you just you know little individual modules that do the things you want them to.
1:59:36 - Leo Laporte
Hey, before we talk about secure conversation records, retention and your invention, which I'm very excited to talk about, steve has solved the problem and he will tell you his solution.
1:59:48 - Steve Gibson
So everybody listen. I think I probably do have it and I'm hoping that it gets me now. I know from our listeners that a bunch of people want this too, and it's not a hard. It's not a hard solution, so I hope people get on it awesome, uh.
2:00:04 - Leo Laporte
Before we do that, I do want to give a little plug, uh, and a thank you to our Club Twit members, because they make such a difference to all of us here. Yes, we have ads. Ads support about 75% of the network. The other 25% comes from listeners. Truthfully, if it were up to me, I'd make it 100%, but we're not quite there yet. Maybe if you join Club Twit, we can get a little bit closer to that goal. It's only seven bucks a month. You get ad-free versions of all of the shows, because I'm not one of those people who wants to show you ads and charge you money. I think it's one or the other. I like having ads, in the sense that it means Twit will always be free. By the way, this is one of the things you get as a benefit when you join the club. You get access to the Club Twit Discord, which is a lovely social network, a great hang, and there are people in there who do some wild things. Pretty Fly, for Sisky has made an AI-generated picture of you. Should have gone. You went the wrong way, though. You made me look older, not younger. Looking at the. Oh, it is an old playboy in a liquor store. That is AI, my friends. But this is the kind of thing that you get to participate in. The club to a discord is a wonderful place to talk about the shows while they're on, but even when they're not on there's stuff to talk about. Tomorrow, micah's crafting Corner at 6 o'clock. It's a cozy time when you can craft along with Micah, whatever your craft might be. We've got Stacy's Book Club coming up.
Next week. This show is going to be a little later, steve, than maybe an hour later than normal, because we will be covering Google IO at 10 am on Tuesday, may 20th, and they say it's a two-hour keynote. So MacBreak Weekly will start at noon. I'm going to make a short MacBreak Weekly so we can get you in here by two o'clock. I think we can do that. Cool, yeah, but just a word of warning.
The other, more important warning is because we have received takedown notices, for what we like to do is do the keynotes and, at the same time as we're doing the keynotes, comment on it. But we've been getting takedowns from Apple, particularly on YouTube and Twitch, and we can't afford to be taken off YouTube. So we have decided that unfortunately, we won't do these keynote streams in public. We'll do them in the club. Only that way we don't have to worry about Apple, but you do have to be a member if you want to watch our coverage. It's going to start Monday of next week with Microsoft's Build Conference, the IO keynote Tuesday. On Friday, by the way, dick DiBartolo and I are going to do a Memory Lane episode, which should be a lot of fun, and then WWDC is coming up on the 20, no, I'm sorry, the 9th of June. There's other things going on the AI user group, which is now every first Friday of the month where we show you how we use AI. Last week, last time was Anthony Nielsen Amazing, amazing AI genius.
There's a lot. In other words, it's a club that you want to be in talking about the stuff you care about. So you get ad-free versions of the show. You get the club twit discord, a whole social network just for geeks like us. You get special shows and events that occur only in the club. You don't have to be there live. By the way, we do put them in the special feed. There's a TwitPlus feed just for club members.
I can go on, but the most important benefit really is that you are supporting us and you're keeping us going in the face of tough economic times. I know it's tough for you, so if you can't afford it, that's fine. We still offer the ad-free versions of almost everything we do. But if you can, I'd love to get you in the club. Twittv slash club twit. Uh, we should also mention once you join the club, sign up for the newsletter it's not automatic twittv slash newsletter. The newsletter is free and it will keep you up to date on club events so you don't have to be in the discord to see what's going on. Um, the newsletter is a great way to follow what's happening with twit twit club twit. To join the club twittv slash newsletter. To subscribe to our club twit newsletter. And thank you everybody. Thank you for being such great supporters of this week in tech 20 years we've been doing this.
all right, steve, I am just dying to hear your solution to all of this, okay.
2:04:30 - Steve Gibson
So what is end-to-end encryption and what does it mean in environments with requirements for the long-term retention of records? As civil disputes have arisen in an information age, attorneys have sought to obtain records of prior events that may not have been retained. The result of this has been a growing requirement for records retention, articulated by laws such as the Federal Records Act, the Freedom of Information Act, the US Presidential Records Act and the Federal Rules of Civil Procedure, and we've encountered many instances where private companies are required by law to retain their own records in the event of litigation. The recent events surrounding Signal and TeleMessage and members of the US government's use of end-to-end encryption, with TeleMessage's mission to archive conversations, raises many questions about the intersection of secure communications and the need for long-term records retention. Okay, but I'm getting a little bit ahead of myself. I settled upon this topic, as I said at the top of the show during this week's podcast, only after catching up with the news of an event that was the topic of last week's podcast, because it was not my original intention to give this whole telemessage signal gate story much more air. I originally had this as a news item near the top of the podcast, but we've learned some more in the past week and the news legitimately and ultimately led me to pose the question that became today's topic. So let's all catch up on what transpired over the past week.
Under the summary line three US departments ban telemessage. The Risky Business Security newsletter wrote According to Bloomberg, three US government departments have told employees to stop using the telemessage service. The service allows companies to log and archive conversations taking place in secure messengers such as Signal, whatsapp and others. Two separate hackers, two breached telemessages back end last week after it was revealed that White House officials used the service. Now Wired had the headline Customs and Border Protection Confirms Its Use of Hacked Signal Clone Telemessage With the subhead. Cbp says it has disabled its use of telemessage following reports that the app, which has not cleared US government's risk assessment program, was hacked. Rather than share the entire article, which is padded with a bunch of stuff that we already know, I'll extract things we didn't already have on the record. One the United States Customs and Border Protection Agency so this is Wired reporting confirmed on Wednesday that it uses at least one communication app made by the service, telemessage, which creates clones of popular apps like Signal and WhatsApp, with the addition of an archiving mechanism for compliance with records retention rules. The CBP spokesperson, rhonda Lawson, told Wired. Quote following the detection of a cyber incident, cbp immediately disabled telemessage as a precautionary measure. The investigation into the scope of the breach is ongoing. Unquote. Okay, so we have confirmation of the belief, which arose from the hacked data that was anonymously shared, which we talked about last week with 404 Media, that the CBP was indeed using the telemessage app. Also, says Wired.
In the days since the photo was published, telemessage has reportedly suffered a series of breaches that illustrate concerning security flaws. Analysis of the app's Android source code also appears to indicate fundamental flaws in the service's security scheme. As these findings emerged, telemessage, an Israeli company that completed an acquisition investigating a potential security incident. Upon detection, we acted quickly to contain it and engaged an external cyber. How can you have a potential incident which you contained, anyway engaged an external cybersecurity firm to support our investigation. Out of an abundance of caution, all telemessage services have been temporarily suspended. All other SMASH products and services remain fully operational. Unquote and quote. There is still no complete public accounting of US government officials and agencies that have used the software, so we're flying a little bit blind on that side. Jumping to the bottom of other reporting by NBC News, we find quote but archives of sensitive information inherently make targets for hackers inherently make targets for hackers.
On Sunday evening, a hacker credibly claimed to NBC News to have broken into a centralized telemessage server and downloaded a large cache of files. As evidence, the hacker provided a screenshot of telemessages contact list of employees at the cryptocurrency broker, coinbase, which uses TeleMessage. A Coinbase spokesperson confirmed to NBC News that the screen grab was authentic, but stressed that Coinbase had not been hacked and that none of its customers' data had been affected. The Coinbase spokesperson said quote at this time there's no evidence any sensitive Coinbase customer information was accessed or that any customer accounts are at risk, since Coinbase does not use this tool to share passwords, seed phrases or other data needed to access accounts. Unquote. The hacker told NBC News they've not fully sifted through the hacked files yet and it is unclear if they include sensitive conversations from the US government. Several government agencies, including the Department of Homeland Security, the Department of Health and Human Services, the Treasury Department and the US International Development Finance Corp, appear to have active contracts with TeleMessage or other companies to use TeleMessage's services, according to government records reviewed by NBC News. Separately, a different hacker told the tech news publication 404 Media that they also hacked telemessage and provided significant evidence. Nbc News has not interacted with that hacker of more apparent departments inside the US government using telemessage and lots of hacking of telemessage multiple confirmations from different sources and directions.
Last week, security researcher Micah Lee blogged under the headline despite misleading marketing Israeli company telemessage used by Trump officials can access plain text chat logs. Micah wrote in this post. I will give a high level overview of how the telemessage fake signal app and I would use the word clone, but he's using some strong language here signal app called TM Signal, because I mean it's not fake, no one believes it's signal. It calls itself TM Signal, right, sgnl. How it works and why it's so insecure. Then I give a thorough analysis of the source code for TM Signal's Android app and what led me to conclude that telemessage can access plain text chat logs. Finally, I back up my analysis with as yet unpublished details about the hack of telemessage.
The hack of telemessage. Okay. So, among other things, mica created a clear and simple diagram that depicts the flow of information for anyone using telemessage's modified signal app. The modified app does what it claims to do, but since the archived messages are themselves stored and forwarded in the clear. That does also serve to verify that telemessage themselves would indeed be privy to the content of the message flow of any of their customers. That's pretty much sure to be a permanent deal breaker for many of the more security-sensitive users of this system.
2:14:14 - Leo Laporte
Isn't TeleMessage an Israeli company? Yes, okay, just checking. Yep.
2:14:20 - Steve Gibson
So good.
2:14:20 - Leo Laporte
Our US government is basically passing all of their messages to the Israeli government. That's correct, or the Israeli company anyway.
2:14:29 - Steve Gibson
That's correct, and they are users of telemessage. But wait, leo, it gets worse. Oh good, there's something I haven't read or seen anywhere. This would be totally obvious to anyone with any operational cybersecurity understanding at all. So let me repeat this the telemessage system is depositing the full plain text transcripts of all conversations conducted with the signal protocol whenever using this app. My point is the entire design of this system is so transparently insecure that any claim to security would be utterly laughable, misleading marketing. It's sending everything you sent and received to Microsoft Outlook or any SMTP email account in the clear. That's what it does. It's emailing it. Yes, in the clear. Yes, it uses email, so there's nothing about this. That is secure.
2:15:52 - Leo Laporte
Why bother using Signal if you're going to use this?
2:15:56 - Steve Gibson
Yeah, there's nothing about this that's secure for the content of these messages, nothing. One of our listeners responding to my reporting of this last week, apparently feeling the need to defend the current administration, claimed that telemessages use had been approved by the Biden administration. At the time I knew nothing either way. Now I do. I presume this listener picked up this politically partisan fiction somewhere and wanted to believe it, but it was never true and these sorts of statements expressed as fact tend to spread and they're not helpful.
The Biden administration may have well done stupid things, but this was not among them. Telemessage's federal use has never been approved for use by anyone within the federal government. Part of the reporting about this in the past week noted that, while the telemessage company is itself a federal contractor, the consumer apps it offers are not approved for use under the US government's Federal Risk and Authorization Management Program known as FedRAMP. That's the approval that would be required and that's actually a relief. That is that it has never been approved, because telemessages apps which send, as I said, apps which send, as I said, conversation, plain text to any email servers specified by their users could never have possibly been considered safe or secure to use. This would have to be so blatantly obvious to anyone with even the slightest cybersecurity training that I would be quite worried if these apps could have ever been approved for use under the FedRAMP program. So the use of these communications applications by federal government officials was entirely illicit, so we can put that one to rest.
Micah's blog posting digs deeply into the entrails of TeleMessage's Android app, which is open source. I scanned through Micah's detailed posting and his reverse engineering and did not find anything that merited further deep discussion, but I've included its link in the show notes for anyone who might be interested in looking for more. It's all there and it's long and detailed. There's really nothing anyone with any training needs to know. Once it's understood that tele on, it's simply game over, and it must have made those within the NSA and CIA and other security aware agencies who know how much our adversaries would love to get their hands on these conversations just green, well guess what.
They already do. Yeah, this brings us to the first part of the meat of today's topic. When we use the term secure conversation and where telemessage quite clearly failed. What really is end-to-end encryption? And by that I mean what do we mean? When we say that something is end-to-end encrypted? How is that some sort of special type of encryption or a special type of encrypted system? And the bigger point is, how is that term increasingly being used, misused and, in some cases, abused? The difficulty and we should say that TeleMessage absolutely touted their technology as end-to-end encrypted. That's what they said in all of their marketing and apparently no one looked any further. Nobody who was going to use it thought to ask somebody with any cybersecurity awareness would this be safe for me to use? Because any of our listeners would go oh my God, no, okay. So the difficulty is that the term's common use appears to be diverging from its original technical meaning and has become a buzzword term, like everybody wants to have, oh, full end-to-end encryption. So it's being tossed around now by the marketing types because it feels good and fancy to say it. Okay. So let's first turn to the internet's encyclopedia to see what those who have spent time working to craft a clear and concise definition of the term have come up with.
Craft a clear and concise definition of the term have come up with Of end-to-end encryption. Wikipedia writes end-to-end encryption E2EE is a method of implementing a secure communication system where only communicating users can participate. No one else, including the system provider, telecom providers, internet providers or malicious actors, can access the cryptographic keys needed to read or send messages. End-to-end encryption prevents data from being read or secretly modified except by the true sender and intended recipients. Frequently, the messages are relayed from the sender to the recipients by a service provider. However, messages are encrypted by the sender and no third party, including the service provider, has the means to decrypt them. The recipients retrieve the encrypted messages and decrypt them independently, since third parties cannot decrypt the data being communicated or stored. Services that provide end-to-end encryption are better at protecting user data when they are affected by data breaches. Such services are also unable to share user data with government authorities, domestic or international. Okay, so I'd say that's a beautifully crafted definition of what is currently meant by the proper use of the term, and obviously telemessage completely fails in that regard. So, by way of comparison to non-end-to-end encrypted systems, the Wikipedia article actually says in many non-end-to-end encrypted messaging systems, including email and many chat networks.
Messages pass through intermediaries and are stored by a third-party service provider from which they're retrieved by the recipient. Even if the message are encrypted, they're only encrypted in transit and are thus accessible by the service provider. Server-side disk encryption is also distinct from end-to-end encryption because it does not prevent the service provider from viewing the information, as they have the encryption keys and can simply decrypt it. The lack of end-to-end encryption can allow service providers to easily provide search and other features or to scan for illegal or unacceptable content. However, it also means that content can be read by anyone who has access to the data stored by the service provider, by design or via a backdoor. This can be a concern in many systems where privacy is important, such as in governmental and military communications, financial transactions, and when sensitive information such as health and biometric data are sent. If this content were shared without end-to-end encryption, a malicious actor or adversarial government could obtain it through unauthorized access or subpoenas targeted at the service provider. Finally, end-to-end encryption alone does not guarantee privacy or security. For example, data may be held unencrypted on the user's own device or be accessible via their own app if their login is compromised.
Okay, so one of this podcast's early terms and acronyms was TNO, which stood for Trust no One. We used it when talking about storing our data in the cloud. Well before anything was being called the cloud was that client-side encryption and decryption would be employed on the user's PC, so that the only thing we were asking remote services to store was big blobs of data that were indistinguishable to them from completely pseudo-random data, which is exactly what good encryption produces pseudo-random data. Later, the term was used interchangeably with PI, p-i-e, which is another term we use, which stood for pre-internet encryption. So what emerges here is a very clear understanding of what the proper use of the term would be. In practical terms, it means that the providers of the service and any intermediaries that they may engage never, under any circumstances, have any access to the unencrypted content of the messages or data or whatever it is they're conveying or storing on behalf of their users. For this assertion to hold, any of the user data that a provider of end-to-end encrypted services ever comes into contact with must be encrypted, and the provider must never, at any time, have access to the cryptographic keys that would be capable of decrypting that data. By that definition and the set of requirements that flow from it.
It's clear that the messaging archiving services telemessage was offering could never, literally, by definition, have ever been considered to be end-to-end encrypted. That term could never be accurately applied. By comparison, we've previously explored at length the protocols that the likes of Apple and Signal have gone to in order to truly meet and live up to the definition of end-to-end encrypted communications and storage. This entire battle that Apple is presently engaged in with the UK over the provisioning of their advanced data protection amounts to exactly this. The switch on the user's UI on the phone is labeled enable advanced data protection, but it could just as accurately be labeled enable end-to-end encryption.
It might next be instructive to ask is there any hope for telemessage? Is there any way for a potentially system such as Signal, WhatsApp or Telegram remain end-to-end encrypted? And the answer to that is yes. There's definitely a way to do this securely, but TeleMessage never bothered to. Never bothered to. They opted for the user convenience of forwarding the user's plain text conversation logs to email, and in doing so they probably put themselves out of business forever. I doubt anyone would ever consider trusting telemessage again. So when someone does produce a true end-to-end encrypted messaging system with end-to-end encrypted long-term archiving. It won't be these guys, okay.
So how could what telemessage wanted to do be accomplished securely? The most obvious solution is to simply modify a cloned Signal app for long-term local archival storage so it would offer local storage, search and retrieval on the client-side device itself. After all, the plain text data is already there. It's been shown to its user right there on the screen. So the app simply feature from the app and replace it with long-term archival storage of everything that app sends and receives.
And to be a responsible archiving signal clone, any such clone which has been configured for long-term message archiving should periodically inject a notice to all other members of any archiving conversation that its user, member X, is permanently archiving their conversation. That might be expected to alter the behavior of the people in the group, causing it to be a little bit less boisterous and flippant. But that would probably be a good thing too. And if nothing else, these periodically injected archiving reminders would cause its recipients to ask the archivist why they were keeping the conversation if that had not been disclosed. But now we have a new problem.
The problem is that a high-level government or other individuals who are using an archiving system, an archiving secure messaging clone, whose entire messaging history exists inside that device, wind up carrying around something in their pocket that might well be worth a great deal to the right parties. No one in their right mind would want to have it known that they're walking around town, riding in cabs and dining in restaurants with months or years of top-secret records retained in their smartphones. So that's not a practical solution either, and even if walking around with this conversation archive was not a bit problematic in itself, the presumption is that, aside from having the convenience of searching for and retrieving past conversation details of searching for and retrieving past conversation details there is also some significant need for government records to be retained or other executive compliance requirements in the corporate world to be met. If a device were to be lost or stolen, and even if it could not be unlocked and used, the loss of those records could be a huge problem. This brings us to the inescapable conclusion that the app's local conversation memory should be kept short and non-archival, and that some secure means of removing the data from the device while retaining it permanently should be found.
The solution I've come up with that completely solves all of these various problems, providing truly secure records, retention for users of Signal and using only the official, unadulterated signal app to deliver full, true, end-to-end encrypted conversation. Security would be for these individuals to add a secure government signal bot to their conversations government signal bot to their conversations. This signal bot would be running deep inside a secure NSA facility. It would auto-accept all conversation invitations from known government staffers and it would passively receive and permanently archive all dialogue from everyone else who was participating in the conversations. It would function as a silent observer and would appear as a participant named something like Federal Records Retention in the list of conversation members, in the list of conversation members, so that everyone participating would be informed and reminded that their conversation was subject to legally required retention, while at the same time being assured that their conversation was being retained and that they were thereby abiding by their oaths of office and the law while participating in these conversations. Being a signal bot, all of the standard end-to-end encryption guarantees offered by the signal protocol would apply.
The only possible points of vulnerability would be at the individual device endpoints, but that's inherently an issue that's inherent in the use of any messaging application. Since Signal is open source and desktop clients already exist, the creation of various secure message archiving bots would be a simple matter for the likes of the NSA, cia, cisa or whomever. Or, better yet, perhaps a successor company to telemessage will arise from the ashes of telemessage's clearly useful and important concept to create a commercial implementation of this solution. For those who need signal message archiving, I would imagine that many enterprises would welcome the ability to automatically have their executives and other important individuals secure signal conversations securely archived on-premises without creating the sort of serious security weakness we've all just witnessed from telemessage. In retrospect, this seems like such an obvious solution for the secure archiving of secure messaging that I'm surprised such a service doesn't already exist. Let's hope someone creates such a system soon. It should not take that much effort or time and it should definitely remain open source, since it's all about first understanding and then trusting the implementation.
2:35:55 - Leo Laporte
Well, actually. So there is a protocol for this in the federal government. When you're doing classified communications, you're supposed to do it in a SCIF, and the SCIF has logging and recording and it stays in the SCIF. It stays in a secure environment. So it's very similar to what you just described. Um, and you're not and you're not supposed to do classified conversations outside a skiff at all. So, yeah, but yeah, I think what you propose makes sense, or even maybe that if you're going to do this, you're actually logged into a server inside the Pentagon and interacting only within that server, right, and then it's preserved there. The National Records Act does require clear text versions of the records. Obviously, they won't let you store it encrypted clear text versions of the records you.
2:36:51 - Steve Gibson
Obviously they won't let you store it encrypted, but what we've seen is that many agencies in the US government were telemessage clients, Right but that was illegal. And it is, but they were nonetheless yeah, and I've heard from many of our listeners whose corporations were telemessage clients and are now looking for an alternative Learning their lesson.
2:37:12 - Leo Laporte
Obviously, they didn't do their vetting they should have done. Of that, I mean that diagram is clear.
2:37:17 - Steve Gibson
So it's certainly not illegal to use Signal, yet it would be very convenient to be able to have a secure archive of Signal conversations.
2:37:29 - Leo Laporte
I think the thing is that the federal government does have a protocol for this and the protocol wasn't followed. And really this is the real issue in general is humans that the breaches often occur because humans don't follow correct procedure right?
2:37:47 - Steve Gibson
Well, and this came to light because a very insecure system was in use, and the good news is we have listeners whose companies did not were you know, were not sufficiently aware that, just saying, oh, sprinkle some end-to-end encryption dust on it yeah, tell a message.
2:38:07 - Leo Laporte
It was invented by the israeli defense force. What could possibly go wrong?
2:38:12 - Steve Gibson
it's just amazing actually the founder was x israeli defense. Yeah, I know?
2:38:18 - Leo Laporte
uh, it's my guess that this was always a honeypot from the israelis well, it uh, the, the.
2:38:26 - Steve Gibson
The really cool solution is just to create signal bots and have a secure signal bot. They're in the conversation.
2:38:34 - Leo Laporte
They're inside the Pentagon, they're in a secure environment, they record it and then it's done, job done. Instead, they sent it to the Atlantic Magazine editor, jeffrey Goldberg. He was their signal bot. You know it's funny he was more careful with the information than they were. That was the irony of the whole thing. Yeah, I think I like your idea. I think that's a great idea, for all we know, they are implementing something similar. I mean, I would expect that.
2:39:04 - Steve Gibson
It's open source and there are desktop versions. You can take the desktop version and turn it into an archiver. Yeah, I looked around and I didn't find anything. Maybe our listeners will find such a program or service.
2:39:18 - Leo Laporte
The NSA probably has and offers something like that, or the GSA or somebody offers that, but you have to get people to use it. That's the part of the problem.
2:39:28 - Steve Gibson
Well, and it still doesn't dispel the problem of having that kind of a conversation on consumer smartphones, because we do know that other aspects of Israeli services that we've talked about in the past are prying into consumer smartphones.
2:39:50 - Leo Laporte
Steve, as always, great stuff and I love your clear thinking. You always come up with great solutions. They seem obvious after you say them. If you enjoy this show, I do hope you will come back next week. We do Security Now every Tuesday, right after MacBreak Weekly. We're getting pretty close now to 1 30 pm. Pacific 4, 30 eastern, 2030, utc. We stream it on eight different channels because you know what? We're not trying to keep it a secret, by the way. Uh, so don't you? You tell your friends if you're in the club. It's on discord. Otherwise, youtube, twitch, tiktok, xcom, linkedin, facebook and Kik Watch where you want. Chat with us wherever you want. I see all the chats in my display here.
After the fact, on-demand versions of the show available at Steve's site. He actually has completely unique versions of the show, so we have it and he has it. If you want a 16 kilobit version, 16 kilobit audio or a 64 kilobit audio version, he's got those. He also has the show notes. He also has human written transcription really good transcriptions from elaine ferris available at his site, grccom. While you're there, I'll give you a little extra to do some extra credit. Uh, of course, pick up a copy of spin right steve's bread and butter and the world's best mass storage, maintenance, recovery and performance. Utility. 6.1 is the current version. If you don't have that yet but you already bought spin right, get your upgrade for free. If not, buy it today, because it is a must-have for anybody with mass storage.
You should also go to grccom slash email and register your email with steve. He doesn't do anything with it except whitelist it so that you can email him after that and that way, if you have a suggestion, a picture of the week you want to send him criticism, ding, what do they call them? Brick pats or bouquets you send it to Steve directly, but only once you've registered your email at security sorry, grccom slash email At the bottom. When you're doing that you'll see two unchecked checkboxes, but you can check them if you want and sign up for Steve's weekly Security Now show notes newsletter. He sends that out before the show, sometimes a day before the show every week, so you can comment on that. And also, very rarely he'll send out an email about a new product or something he wants you to know about. Grccom slash email.
We have his show at our website. Our unique versions are, for reasons that are too complicated to explain on this show 128-kilobit audio version. Yes, it's mono, I don't know why. Well, I do know why, but I'm not gonna tell you why it's 128. Kilobit has to do with apple. It's a complicated thing. Uh, we also have video which steve refuses, after all these years, to post on his site because he says no one needs video.
2:42:43 - Steve Gibson
But if you want it.
2:42:44 - Leo Laporte
You can get it twittv slash sn where you're there. You'll see a link to the youtube channel another way to get the video or share clips. I know a lot of people like to say, oh gosh, I got to send this thing to my boss. You can do that. It's a great way to spread the word about security now. You can also, of course, subscribe in your favorite podcast player. If you do that, please leave us a good review, leave us a five-star rating wherever the highest number of stars is. Help spread the word about security now because, frankly, I think everybody in and out of government should be listening to this show every week. Absolutely, subscribe to our newsletter if you don't already get it.
Steve's got a newsletter. We do too. It's free, it's weekly. It's twittv slash newsletter. That two it's free, it's weekly. It's twittv slash newsletter. That'll keep you up to date on what's coming up, uh, on future shows, especially for the club members, because if you're not in the discord it's, you may not know about special events we've got planned. Those are all in the newsletter. Steve, have a great week.
2:43:42 - Steve Gibson
Enjoy the remodel and we'll do and I'll see you and, uh, it will try be starting around two o'clock, you think, next week.
2:43:51 - Leo Laporte
A little later. Yeah, let's remind everybody, because of the Google IO keynote, which should go 10 to noon, we're going to make MacBreak Weekly two hours, so we should be getting to Security Now around 2 pm. That's my goal.
2:44:04 - Steve Gibson
Thank, you, Steve, Sounds good. See you next week. Buddy Bye.