Security Now 1023 transcript
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show
0:00:00 - Leo Laporte
It's time for security now. Steve Gibson is here. Some wacky stories today, including the explanation behind the mysterious appearance of the iNet pub directory on your Windows machine. It's on purpose and don't delete it. We have new information about data loss in SSD mass storage. If you leave it lying around, you might lose some data Loss in SSD mass storage. If you leave it lying around, you might lose some data. Plus, malware has found a new place to hide inside Windows. All that and more coming up on Security Now Podcasts you love.
From people you trust. This is Twit. This is Security Now with steve gibson, episode 1023, recorded tuesday, april 29th 2025, preventing windows sandbox abuse. It's time for security now, the show that I think many of us wait for all week long. If it's tuesday, it must be time for this guy right here, steve Gibson.
0:01:09 - Steve Gibson
I know that I wait for it all week long because it's a major event in my weekly cycle. It's a lot of work. I'm sure it's a lot of work. I start Sunday around noon after Laura and I have caught up with the Sunday morning shows, and I work all day Sunday and then all day Monday, so it's basically two days out of the week.
0:01:29 - Leo Laporte
But and it's funny. Steve, you have our eternal gratitude, thank you.
0:01:33 - Steve Gibson
It's funny because Lori says why can't you just cut and paste more? And I go well, because I like talking and you know I want to put myself into that, not just you know echo, echo, echo, other people. So I end up like really having a good time, and that's the problem is, yes, it's a big commitment, but I really do enjoy it.
0:01:55 - Leo Laporte
So you know well, we enjoy you and we thank you, unable to do anything halfway, as you know.
0:02:00 - Steve Gibson
so I, I, so I end up going all the way. So we are at the monumental episode 1023, which will be a significant number to all those who've ever studied computers on the binary side, especially because that would be one, one, one, one, one, one, one, one, one. That's nine ones, folks. And when we get one more one, then we wrap around two to the power of 10. And 1024, that is one binary K, and we will be there next week.
0:02:42 - Leo Laporte
When I first moved to San Francisco, the first place I rented the address was 1024 Page Street and I thought no one else appreciated it. But I thought this is cool. I'm on the 1K page, so yeah, those numbers are important and it's one of those things you know you glance at the digital clock and it says 512, or it says 1024, or it says 256 or 1128.
0:03:18 - Steve Gibson
So, yeah, I do live in that world. The fact that this really well-designed piece of work was sitting in Windows 10 and 11, largely underutilized, sometimes completely unknown, because who would know? I mean, unless you had some reason to go looking for something and someone like this capability and someone said, hey, just try the Windows Sandbox, it's built in. Anyway, now everybody knows. As I also mentioned in passing last week, the thing that reminded me of its existence is that malware, of course, has figured out how to crawl in there and use the sandbox behind people's backs without them knowing it's even there. So all of that cool separation that you get, which Windows Sandbox legitimate users take advantage of, malware has figured out a way to do too. There are a couple solutions for preventing its abuse, which we're going to talk about after we finish talking about the nature of the abuse. But first we've got this bizarre appearance of directory I'm very familiar with. Inetpub is the directory that's always created when Internet Information Services IIS server is instantiated into typically a server, but also workstations. I've long had it on all of my machines because I've always been using Microsoft's web services to deliver websites. Well, it mysteriously appeared unbidden. So everyone believed, after April's Patch Tuesday and there's a big story there that we're going to get to. Um, we also have a our, our friend who tweets as gossy the dog. Kevin beaumont has found a way to crash windows update using this mysterious directory, which I'm sure microsoft did not intend.
This whole thing has just been a big cluster. You know what a mess. Uh, we also have north korea now creating fake us companies, although they they they have like the one division that's that is spoofing fake employees. They said, well, let's go there, let's get on the other side, let's create fake us companies. See how that goes. Um, we have a new attack on gpt-style conversational AIs, known as the Inception attack, which subverts them. Also, a bunch of people sent me questions about this, so I figured, since everybody is concerned about mass storage, we've got some really interesting new information about the data loss. Well, here's the thing is it's about.
0:06:28 - Leo Laporte
Sorry.
0:06:29 - Steve Gibson
Continue on Some new information about data loss occurring in unpowered SSD drives. Also lots of terrific feedback from our listeners from recent episodes. And then we're going to get to how malware has taken to hiding inside the windows sandbox and what we can do to stop it. And, of course, we've got another picture of the week, which is one of the high points for the this weekly podcast. This one is it's a goodie, and, and actually the first couple that are that are coming. So I think, leo, for a change, we may actually have a goodie and, uh, and actually the first couple that are that are coming.
0:07:10 - Leo Laporte
So I think, leo, for a change, we may actually have a good podcast for a change. Yeah, it'll be unheard of. We may have stumbled on the right formula. 1022 episodes no, every episode is fantastic and I can't wait to get into it. But first we do have a sponsor, if you don't mind, and I'd like to mention them. Actually it's a very topical sponsor legato security.
Legato security. I had a great call. Do you spread it on your? No, not, not topical like ointment, oh, topical like timely. How about that? Ah, no, I'll give you an example. I had a great conversation with them last week, actually maybe a couple weeks ago now and uh, and they I brought up this kind of uh analogy when you wouldn't put in a burglar alarm system, uh, that didn't have monitoring.
Right, because burglars break into the house when you're not around most of the time and you're not there to say, oh, the alarm's going off. I mean, maybe you count on your neighbors, but really a burglar alarm system needs monitoring. Well, it's the same thing for your security. No business should be their own burglar alarm. And it's same thing applies to cybersecurity. Legato security it's perfect for small and medium businesses. You know, big business probably has a security operations center that is monitoring 24 seven. You know, if you're, you know a fortune 500 company, you probably have all that, but there are a lot of businesses that don't have it and need it. But there are a lot of businesses that don't have it and need it, unless you want your security team to live at the office. Legato Security provides the same standard of security controls that these large enterprises depend on, without the cost of building an internal security operations center. They're a recognized leader by CRN MSSP Alert in 2024.
Legato Security transforms how businesses approach cybersecurity. They're technology agnostic, so they will use what you're already using. They're also not there to replace you. They're there to give you some time off that you probably deserve. Their technology agnostic MSSP platform provides your business with a custom suite of security solutions tailored to your needs. Legato Security integrates seamlessly with all the tools you're using, so we're not talking a costly infrastructure overhaul.
This slides right in. It's a proprietary security operations platform. They call it ensemble, but what it does? It takes all the signals from the stuff you're using and delivers consolidated, prioritized and actionable alerts in real time via a comprehensive single pane. So everything you need to know is right there, right in front of you, no matter how many different tools you're using to protect yourself. See, here's the point.
Hackers don't take holidays. They don't stop working when you clock off. In fact, that's exactly when they start working. They say oh, they're leaving the house, now's the time to get in. Legato Security's 100% US-based team provides proactive threat detection triage. They even do remediation 24-7, 365 days days a year. They're there even when you aren't, and they use this purpose-built security operations center, this sock, so your team can focus elsewhere when it's time to clock out.
Finally, a weekend off right from entrepreneurs to we talk. We were talking about this uh year, or actually it was early this year that a bunch of browser extensions were hacked on Christmas Eve because they knew, oh, that's going to give us at least a couple of days to exploit people before anybody gets around to fixing it right. Not if you use Legato Security. From entrepreneurs to Fortune 100 companies, legato Security creates custom MDR solutions that protect businesses so business leaders can focus on growth. Here's a great testimonial from a recent customer Quote Legato Security is the only supplier that has delivered everything they said they would, and we didn't have to drive them. They just get it done. I love this too.
If you've got a problem, legato security is not going to call and say, hey, you got a problem. They're going to call and say, hey, we saw the problem and we fixed it and you're safe. That's what you want. That's what you want right it? And security professionals. Legato Securities MSSP is here to augment your security team, not replace them, not replace you. They're the professionals you want on your team to back up your cybersecurity forces, to fortify your proactive defenses, 24-7, 365 days a year.
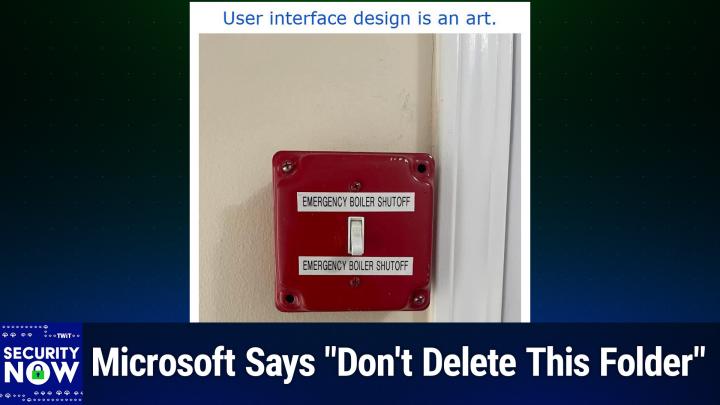
Security tools alone are not enough. You need the expertise to back it up. Oh, and here's a great tool you can go right now to legatosecuritycom and see if your defenses are as strong as you think. They've got a free risk assessment on the website. It's worth taking it just to see where the holes are. Visit legatosecuritycom to discover how they can help you regain control. And, you know, enjoy your weekends like you used to help you regain control and, you know, enjoy your weekends like you used to. That's legatosecuritycom L-E-G-A-T-O securitycom. It makes perfect sense. This is something you need. It's affordable, it's effective. Legatosecuritycom, check them out. All right, steve, I'm ready for the world famous picture of the week. So I gave this one the caption user interface design is an art. Okay, you want to describe this so funny, this so funny.
0:13:08 - Steve Gibson
This is obviously extremely critical. We have a red, bright red fire engine, red painted switch box with a toggle switch on it and it is labeled above the switch emergency boiler shutoff. And it is labeled below the switch emergency boiler shutoff.
0:13:35 - Leo Laporte
So so which way do you switch it?
0:13:38 - Steve Gibson
Yeah, I mean, it's not like it's some fancy industrial switch, it's a light switch, you know. And right now the toggle is pointing down and so it says, like in the old days, it says you know OFF. You can see it just below the little paddle down in relief, but you know. So if the boiler is in trouble do you turn it on.
0:14:05 - Leo Laporte
Yeah, turn on the shutoff.
0:14:07 - Steve Gibson
Do you turn on the shutoff or shut?
0:14:08 - Leo Laporte
off the turn on.
0:14:09 - Steve Gibson
Anyway.
0:14:12 - Leo Laporte
You know, I think that I understand the logic here. Somebody isn't telling you what to do. They're just labeling this box and they want to do it twice so you wouldn't miss it. This is the emergency boiler shutoff. There is no advice here about which way to switch it should say good luck to you maybe the presumption is well, whatever position it's in now, if you're having trouble you should just flip the switch if the boiler is not currently shut off then then toggle it.
0:14:43 - Steve Gibson
Yes, that's the silliest we have some some uh add, uh listeners who received the show notes from me last night and they said you know, I understand the point you're trying to make here, steve, but the biggest distraction for me is that there are two screws missing from the cover. Okay, okay, you're right it's a little sloppy. I did notice that also, but I you know it didn't distract me from the bigger problem, which is what the hell, what anyway?
0:15:13 - Leo Laporte
yes, user interface design.
0:15:15 - Steve Gibson
Leo is an art and not everybody is an artist. No turns out. No, this guy. Very funny, okay, so Very funny, okay.
So I first noticed a mention of this in passing, like a week or two ago, but it wasn't until I focused upon catching up with all the recent is that, you know, I'm so familiar with this iNetPub directory, but what's weird is that today, even now, we don't all know what this is actually all about. So you know, as I mentioned at the top of the show, I've been hosting websites based on Microsoft's IIS from the start. Um, I, you know I have some, some. I guess it was when I was running GitLab. I was running non yes, it was running on on FreeBSD, unix. So I had a web server running Apache, I think, or Nginx actually I think is what it was. But largely I'm an IIS guy. You know, when people go to Shields Up, they do the DNS spoofability test, the perfect pay-for-passwords, all of the technology that runs GRC's various services is written in assembly code running on a Windows server that has Microsoft IIS in front of it. So INetPub is the directory that you always see as part of that. So I didn't think much about it when I saw this mention a couple weeks ago.
But whatever's going on has confused many people who wondered why this mysterious and completely empty iNet pub directory suddenly appeared on their windows 11 machines after this month's April's patch Tuesday and bizarrely, microsoft says, nope, it's not a mistake, and what? The empty directory must not be deleted. Oh, come on, but they won't explain why. They still won't explain why. Now, because I was curious about this. I tried to fire up a Win11 instance yesterday and it got tangled up somehow. So this morning I created a brand new VM, installed Windows 11 24H2, and it's now running on the screen next to me. And I can understand why. Anyone who sort of like has a sense that maybe they're still in control. I would argue that that's an illusion in the case of windows these days. But you know we like to think. You know like once upon a time we actually knew what the files were on our computers, but that's. We lost that battle a long time ago.
But there's not many directories on the root of a contemporary Windows machine. I've got there's perf logs, which is there. If you click on it you get scolded oh, you're not allowed to look in there. But then there's just program files, program files, x86, users and windows. Those are the. There's like four directories. So when we're no explanation and new directory called INET pub appears and notice that, you know we're up, we're rebooting and installing updates, from time to time it's not even clear. It would not be clear to someone who happened to look at their directory tree at some point exactly when this appeared. Right, I mean you don't immediately inspect your computer for what happened after installing patches, because who knows what happened. But so I can get the angst where. I mean I would feel it if I some, you know, at some point a day or two or three after doing the patch, tuesday. There it is, leo, that's exactly right. So you are seeing this, exactly the same set of folders I'm seeing there on a fresh install of Windows 11.
0:19:50 - Leo Laporte
Let me just see if there's. Oh, this folder's empty. Nothing in there.
0:19:53 - Steve Gibson
It's empty and if you right click on it and go to properties and then go to advanced, you'll see or security, then advanced, you'll see that it's owned by the system. So, the system is the owner. So go security and then then hit advanced down below there on the right, there it is, and then you can see that the the owner of that directory is the system. Um, okay, so. So anyway, I can get why why somebody would be very worried.
I mean, you know, like the kind of listeners we have to the podcast if, if you just notice that for that there's a new directory on your computer, I would suspect malware. I mean, I would think, wait what?
0:20:38 - Leo Laporte
that's exactly the kind of thing malware does, yes, yes, and you might be tempted to delete it well, and many people did oh, uh-huh, uh, so there's and that's not, you know. If you hadn't told me, I would have deleted it yes, it's an empty folder.
0:20:54 - Steve Gibson
Don't believe it or not, it is your the, the. The patch for a bad privilege, escalation or elevation bug is the. The patch is dependent upon the, the current existence of that directory on the root of your system drive. Interesting, this whole thing is so half baked. It's a kludge. What it's a kludge? Thank you, that's the word. Yeah, okay, so there's been a lot of coverage of this in the tech press, but I'm going to share a lightly edited version of what Forbes Davey Winder wrote about this recent mystery, because he did a good job of summarizing it and kind of pulling these things together.
0:21:35 - Leo Laporte
It would have been easy for them to click the hidden box.
0:21:38 - Steve Gibson
Yes, and we don't know whether that would, whether it has to be visible. So I mean and that's part of the problem, leo, microsoft isn't saying even now they're just not telling us. So Davey Winder's-.
0:21:57 - Leo Laporte
There, I hit it, we'll see what happens. Okay, oh boy, good luck.
0:22:01 - Steve Gibson
Under the headline Microsoft's New Windows Update 1 Billion Users Warn, warned, do not delete. Now I'll note they weren't warned initially and was only in a later update. So, davey wrote the latest and somewhat confusing situation of Microsoft's making has come about, as Windows users noticed a mysterious new folder after the most recent security update, a folder with no explanation and one which Microsoft has now warned a billion Windows users they must not delete. I know this is such a kludge. He writes. As part of the April 8th Patch Tuesday security updates, microsoft included a fix for CVE-2025-21204. Remember that number 21204. We'll be hearing that a little bit later.
Windows update stack, which is responsible for the management of Windows updates, no less, could lead to an attacker to elevate privileges locally, something that the security experts at securityvulnerabilityio described as posing quote a significant risk to organizations, as the compromised systems could allow attackers to execute unauthorized actions, potentially undermining the integrity and security of sensitive information and systems operations. Unquote Davey says I won't bore you with the technicalities of link resolution process manipulation that could enable hackers to access files and execute commands. Just know it's pretty darn serious. Securityvulnerabilityio wrote the ability to conduct unauthorized actions can severely impact the integrity of the affected systems, resulting in potential disruptions of operations, implementation of malicious software or further vulnerabilities being introduced into the network, which is why Microsoft fixed it, and that's a good thing. The way that Microsoft fixed it, however, is not so good. He writes a lack of transparency is a particular bugbear of mine when it comes to anything security related, and this vulnerability patch is no exception. The problem is that Microsoft created a new and empty folder with the security update, the appearance of which led to a totally understandable debate in tech forums and on Reddit as well as other social media platforms.
What was this iNetPub folder? How did it get there? Is it dangerous? Is Microsoft using it to collect data, and should I delete it? According to a new Microsoft Security Advisory update Security Advisory Update the answer to the last of these questions is a resounding no. Microsoft warned that Windows users must not delete the iNetPub folder. Doing so would remove the vital security protections it provides and the reason for it being created. By this update, in the security updates table for your operating system, a new system drive backslash iNet pub folder will be created on your device. Microsoft went on to say now this again. This is two days after the updates and all of this furor had already resulted.
Microsoft went on to say that the folder installation was quote part of changes that increase protection. Unquote, he writes, but failed to explain precisely how. Precisely how he says. What I do know is that the iNetPub folder itself usually comes as part of the Internet Information Services web server platform, enabled using Windows features, but this update has created it, whether the user has IIS installed or not. Okay, now I'll just stop here to insert that anyone who already did have IIS installed on their machine will definitely have that directory and would be expecting to have it. If you have the IIS service installed in your machine, you cannot not have that directory. It's part of IIS.
So Davey continues more transparency is required, me thinks, although not at the expense of tipping off potential attackers, as to how the mitigation works, of course, which we know is ridiculous, because any hackers know anything that Microsoft knows. So it's not like they're keeping this a secret, it's like offering us some protection and we know how everybody feels about security through obscurity, so, he says. I contacted Microsoft for a statement, but a spokesperson informed me that there was nothing else to add other than the information contained within the security advisory at this time. What I can say, however, is that as a security wonk. I strongly urge all Windows users to follow Microsoft's advice. This folder should not be deleted, regardless of whether Internet Information Services, iis, is active on the target device, all of which is OK. But what if you have already deleted the iNetPub folder from your Windows installation or hidden it?
0:28:16 - Leo Laporte
Uh-huh, maybe yeah.
0:28:18 - Steve Gibson
I mean, he says, given the nature of the update and the social media conspiracy theories that surrounded it, I wouldn't be surprised if that were indeed the case for many users. He says I have already had a number of readers contact me to say they did just that and ask what they should do now. The answer is simple Restore it, even though we don't know why. He says the methodology required to do that is, thankfully, also pretty simple, as long as you complete these six steps as follows Head for the Windows control panel, click on programs in the programs and features section, choose the turn Windows features On and Off option. And now our listeners know, because we went there last week for Windows Sandbox. You could also just go to the Start menu and type T-U-R-N space and that would immediately highlight Turn Windows Features On and Off.
That brings you that menu that we saw last week that has Windows Sandbox on it. It also has Internet Information Services. So what's so galling, leo, is that the resolutionNet pub folder. You should install IIS on your workstation, on your Windows machine. It's like what? That's the fix. Yes, and what do home users do? I don't think home users get IIS.
I don't think you have that. No. So he says, tick the checkbox for Internet Information Services, Click OK, he says. Windows will then whir and grind its cogs until the INETPUB folder has been restored once more and you can check your system drive to ensure that it is. To ensure that it is, he says. By enabling IIS. In this way, the same folder is recreated as if Microsoft had dropped it there in a security update, and it will provide the same protections from Windows threats as well. Now I looked elsewhere for additional clarification, but everyone in the tech press is telling the same story. The Windows latest site wrote once IIS is installed, you don't need to make additional changes to Windows 11. Installing IIS will restore the folder, Microsoft told me.
0:31:02 - Leo Laporte
And a bunch of other stuff.
0:31:04 - Steve Gibson
Well, that's just it. It is a heavyweight web server. I mean it's, it's ridiculous. So the real question then is if you then uninstall iis, go back there and turn it off, does it leave inet pub behind and I did not have time to perform that experiment for our listeners, but my guess is it probably leaves it, in which case you can get rid of IIS after you've installed it Now. So here, okay, I'm getting ahead of myself. So Windows Latest wrote. Microsoft told Windows Latest that users need to follow the IIS installation steps. Microsoft is saying install IIS. Wow, this is so half-baked. If they accidentally deleted the folder right accidentally, this empty folder must remain present on Windows 11 system partition, on system drive backslash, inetpub, for the security patch to function correctly, which is itself a crock. The folder provides quote increased protection. Unquote.
0:32:19 - Leo Laporte
According to my God yeah.
0:32:22 - Steve Gibson
Let's add some more we need as much as we can get, give me more. What about backslash kitchen sink? Will that help?
0:32:30 - Leo Laporte
I'm restoring autoexecbat.
0:32:32 - Steve Gibson
There you go. According to Microsoft, turning on IIS creates the same folder with the same protection and your PC will not be vulnerable. Right to that today, and then in a later update to this article Windows Windows latest added update Microsoft will not explain why the empty folder is required to apply the security fixes. Okay, now I'm annoyed by what strikes me as, first of all, very lazy advice from Mike. I'm annoyed by many things, but one of them is very lazy advice from Microsoft. Installing IIS onto a system, as we have noted, is not a small thing, so it's ridiculous overkill to tell people to install the Microsoft Web Services as a means to create a single empty directory. That's crazy. Presumably, you know, the directory named iNetPub requires specific user account privileges to be set on it.
Apparently it needs to have system be its owner, whereas if the user did make dir to create a directory there new directory they would be the owner, so you'd have to change the ownership to system. But you could do that. Given the power of Windows PowerShell today, I am sure that a simple PowerShell script could do exactly the same thing. So asking people to install a full web server just to create a directory is nuts. But that said, randomly deleting directories that don't apparently serve any purpose is probably not a good idea either. You know power users who would tend to notice such things, like to imagine, as I said earlier, that they're still in charge of their Windows installation and environment. Here's another example of why that is not the case. You know it becomes less true with each iteration of Windows.
What I'm wondering, as I said, is whether uninstalling IIS once it's been installed leaves that INET pub directory behind. If so, the second half of the lazy advice should also be to then remove IIS after rebooting the system to first complete its installation and verify the existence of the inet pub directory. And what's infuriating is that microsoft won't tell us anything about why any of this is necessary. And, leo, to your point, does hiding it still work? Since we don't know why it's there, we're not able to evaluate whether hiding it wouldn't have been like something microsoft should have done. Maybe it still works if it's hidden, in which case they could create it, give it system privileges, give it the hidden um attribute, and nobody you know. No, it would have been been the wiser. It would have been created, but it wouldn't have been in everyone's face and basically that matter.
0:35:43 - Leo Laporte
They could release a powershell script that would create it with the proper permissions, yes, and tell people to do that, right, I mean?
0:35:50 - Steve Gibson
or leo. Why not just put a file in that directory with the name don't directly created by windows update, or that would do not delete this directory.
0:36:04 - Leo Laporte
What's your hypothesis for why this is necessary?
0:36:08 - Steve Gibson
I don't have one. I you know. There's no doubt that I don't need to spend my time, because the industry will tell us. The security industry is going to figure out what is going on. Industry is going to figure out what is going on. Now there's more, because kevin beaumont has figured out how to completely shut down windows update using this directory. What let's tell our listeners? Who's paying for this? Omg? Yes, there's a big crock here.
0:36:46 - Leo Laporte
Also, you know, my kind of naive theory would be maybe this malware looks for the presence of iNetPub and then doesn't activate if it sees it. I don't know, that's dopey, and is that the way to stop malware?
0:37:05 - Steve Gibson
well, and how is windows update and some process activation privilege of elevation tied to the presence of the iis root folder? Well, like I mean, it just seems so literally, maybe backslash kitchen, kitchen sink, and we'd get a more reliable windows. I just it's crazy.
0:37:32 - Leo Laporte
Yeah, yeah, but a prolific security researcher did you say you want me to do an ad now, let's let's do it, we're half an hour in.
0:37:42 - Steve Gibson
Okay, I'll do it now we're gonna tell, we're gonna tell everybody how they can shut down Windows Update so that it no longer functions at all.
0:37:49 - Leo Laporte
Well, that doesn't seem like a good solution either. No, I unhid my iNet pub, by the way, I didn't want to take a chance. I mean, it's a virtual machine. I guess what I could do is delete it and then reinstall IIS, or install IIS, uninstall it and see if it's still there.
0:38:07 - Steve Gibson
Oh do that.
0:38:08 - Leo Laporte
Should I do that, okay, after this word from our sponsor.
0:38:12 - Steve Gibson
I could do that too.
0:38:13 - Leo Laporte
We're all going to do that.
You know what would be a really good way to protect yourself from stuff like this? Threat locker? A good zero trust solution would solve so many zero-day problems. Ransomware is killing us, right. It's harming businesses worldwide. It works through phishing emails or infected downloads, uh, malicious websites, rdp exploits I mean on and on and An iNet pub folder. Don't be the next victim.
Threat Locker's zero-trust platform this is so good takes a proactive and here's the key words you want deny-by-default approach. It just doesn't assume that you have access to everything. It blocks every unauthorized action, protecting you from both known and unknown threats. It's so cool. It's trusted by you know, infrastructure people like jet blue airlines, right people who can't afford to go down the port of vancouver. You know they just can't afford to be hit by ransomware. They use threat locker. It shields them from zero-day exploits, from supply chain attacks, and this is great for compliance. Provides complete audit trails, know exactly who accessed what when. It's fantastic.
Threatlocker's innovative ring fencing technology. Basically, it isolates those critical applications so they can't be weaponized. It stops ransomware cold. It also limits lateral movement, right. That's one of the big problems. Like we talked about those guys who put their ransomware on a camera that was running Linux in its firmware because the company had some pretty good protections. But the thing is that lateral movement's the thing you've got to stop. The ability to browse around and find vulnerable spots can kill you. Well, threatlocker limits lateral movement. It doesn't say hey, you're inside, go anywhere you want, do anything you want. It stops bad guys cold.
And ThreatLocker works in every industry. By the way, supports Mac environments. So if you have a heterogeneous network environment, you're golden. They've got great 24-7 support based in the United States. With ThreatLocker you get comprehensive visibility and total control. Here's a quote, speaking of infrastructure, from another vital service, the city of Champaign, illinois. Their IT director, mark Tolson, gave us this quote. He said quote ThreatLocker provides that extra key to block anomalies that nothing else can do. If bad actors got in and tried to execute something, I take comfort in knowing ThreatLocker will stop it. This is the gold standard in security. Stop worrying about cyber threats. Get unprecedented protection quickly, easily and, by the way, the price is right, very cost, effectively with ThreatLocker. Visit ThreatLockercom slash twit to get a free 30-day trial and to learn more about how ThreatLocker can help mitigate unknown threats and ensure compliance. That's ThreatLockercom slash twit. We thank them so much for their support. Of security now, all right. How do I turn off all updates forever and ever?
0:41:30 - Steve Gibson
okay, I just confirmed that. Um installing iis and removing iis, oh, you did that inet, yes, while during an ad wow, yep, yep, uh leaves the uh inet pub directory subdirectory in place.
0:41:46 - Leo Laporte
And with the proper permissions and all that, so you're protected.
0:41:49 - Steve Gibson
Yeah, good, yeah, so anybody who did delete it, who was wondering what the heck this is about I'm just checking that with advanced and yep system is the owner, and there's actually a history subdirectory under it. If you install I iis but then it tells me I don't have permission to look at it, so it doesn't matter anyway, so that that will do the job, it turns out you don't even have to reboot, yeah, you, so you're able to install it. By the time it finishes making the changes, it has created that directory with all the proper permissions and then right. Then you are then able to uncheck the you know, go back in to turn Windows features on and off, uncheck the IIS feature, it does it again and then it tells you that you need to reboot now or later. But even when you come back from that boot, it's only one boot to the whole thing and iNetPub is still there. So again, it's annoying that. We don't know why. But get this. There's more.
Our prolific researcher who we frequently reference, kevin Beaumont, who once tweeted as Gossy the dog he's been active for years has posted into his blog on Medium under the headline Microsoft's patch for and here's the famous now CVE 2025-21204, simlink vulnerability introduces another SimLink vulnerability. Kevin explains Microsoft recently patched CVE 2025-21204, a vulnerability which allows users to abuse symlinks you know symbolic links to elevate privileges using the Windows servicing stack and the C colon backslash INet pub folder. To fix this, microsoft pre-creates the C colon backslash inet pub folder on all Windows systems from April 2025's Windows OS updates onward. Now what occurs to me is that it may be the pre-creation of it and assigning it to the system as the owner that subsequently prevents its abuse, which suggests to me that hiding it would be fine and Microsoft probably should have. But this whole thing, as I said, is about as half-baked as anything I've ever seen. Okay, I've ever seen Okay, so he said. However, kevin writes I've discovered this fix introduces a denial of service vulnerability in the windows servicing stack that allows non admin users to stop all future windows security updates. Whoopsie, non-admin and admin users can create junction points in the C root and in the show notes and in Kevin's blog he gives the make link command. I have it here in the show notes. He says so. A non-admin user can just do a windows plus R you know command. Just get a command line and then run and it's make link forward slash J for a junction and then C colon backslash INET pub space. C colon backslash windows backslash, system 32 backslash C colon backslash Windows backslash System32 backslash. And then he used the ever popular and benign notepadexe, which he's created the symlink for. He says this creates a symlink, a symbolic link between C colon backslash iNetPub and notepad.
After that point, april 2025, windows OS update and future updates unless Microsoft fixes it, fail to ever install. They error out and or roll back, forcing the system to MSRC about two weeks ago and finally received a response. So it took Microsoft security research a couple of weeks. They got back to Kevin writing Hello, kevin, thank you again for submitting this issue to Microsoft. Msrc prioritizes vulnerabilities that are assessed as important or critical severities for immediate servicing.
After careful investigation, this case is currently rated as a moderate severity issue. It does not meet MSRC's current bar for immediate servicing as the update fails to apply only if the iNetPub folder is a junction to a file and succeeds upon deleting the iNetPub sim link and retrying. In other words, you can undo this and then everything is fine, can undo this and then everything is fine. They said. However, we've shared your report with the team responsible for maintaining the product or service and they will consider a potential future fix. Taking the appropriate action is needed to help keep customers protected. At this time, we will not be providing ongoing updates of the status of the fix for this issue and we have closed the case.
Updates of the status of the fix for this issue. And we have closed the case. So Kevin finishes saying my feeling is the endpoint detection and response providers, including Microsoft, probably want to add detection for junction points being created from iNetPub on boot drives, as it looks like this issue isn't going to get patched anytime soon and it's a 100% reliable way to stop future security patching in Windows. Jeez Louise. So whatever underlying problem Microsoft originally had with this CVE, it certainly feels as though somebody cooked up, as I said, a half-baked solution that wasn't very well thought out system, which is normally only needed when a system is running their web server and which is naturally then open to public abuse, of the sort that Kevin stumbled upon, seems really very sad and half-baked.
0:48:38 - Leo Laporte
Wow Just amazing.
0:48:40 - Steve Gibson
Yeah, wow, okay. So this one you're not going to believe, leo. We've talked extensively extensively, worse than what we just talked about. We've talked extensively about the challenge presented by employers who are attempting to do the right thing by not hiring spoofed employees from hostile foreign powers. Security researchers at the firm Silent Push just reported on their discovery of a new bizarre twist. Their headline was Companies to Deliver a Trio of Malware Beaver Tail, invisible Ferret and Otter Cookie. These are the three pieces of malware. Well, you know, because all the good names are taken, they don't sound that scary, to be honest. No, they don't. But get this. The headline doesn't do the story justice. To give everyone a sense for what they discovered, they start with four key findings. And boy, they really are burying the lead here. Okay, key findings. And boy they really are burying the lead here.
Okay, silent push threat analysts have uncovered three cryptocurrency companies that are actually fronts for the north korean advanced persistent threat group. Contagious interview is the name of the group, the group, the group is called Contagious Interview, block Novus LLC and Angeloper Agency and Softglide LLC. So Block Novus, angeloper Agency and Softglide LLC. Three strains beaver tail, invisible ferret and otter cookie are being used to spread malware via interview. Malware lures to unsuspected cryptocurrency job applicants generated images to create profiles of employees in air quotes for the three front crypto companies employing remaker ai. That's remakerai for some of the ai generated images as part of the crypto attacks. The threat actors are heavily using github, job and freelancer websites. Okay, but that still fails to convey what's going on. It took some digging, but it turns out that North Korean hackers created and used US front companies, and I found two of them. I wasn't able to confirm separately Angeloper Agency, but definitely Block Novus LLC and Softglide LLC are corporations registered in the states of New Mexico and New York respectively, so they faked being US companies, then solicited US-based employees into interviews that infected those interviewees with malware that was carried back to their prospective employees' current employers as a means of infecting their organizations, and it worked. So not only now do employers need to be very much on the lookout for spoofed fake employee applicants, but anyone interviewing for a job change needs to now be equally cautious and careful about the legitimacy of the company that says they might be interested in hiring them for a fake enterprise and ends up asking you to do something that will infect your machine and when you go back to your current employer's network, infect your current employer. The world we live in today, my friends, wow, wow, incredible, okay.
On the ai front, uh-oh, carnegie mellon, unary, uh-huh, carnegie mellon university's cert coordination center posted the news of a new widespread vulnerability. What's really weird about this is it works across the ais. That is a single script a new widespread vulnerability that affects pretty much all of the various gpt ai models. The title of their vulnerability report was quote various gpt services are vulnerable to inception jailbreak allows for bypass of safety guardrails. So here's what they explained Two systemic jailbreaks and they call it systemic because it's again AI, you know pan AI Two systemic jailbreaks affecting several generative AI services have been discovered.
These jailbreaks, when performed against AI services with the exact same syntax, result in a bypass of safety guardrails on affected systems and indicating a systemic weakness within many popular AI systems. The first jailbreak facilitated and I just love these crazy jailbreaks facilitated through prompting the AI to imagine a fictitious scenario, can then be adapted to a second scenario within the first one. Continued prompting to the AI within the second scenario's context can result in a bypass of safety guardrails and allow the generation of malicious content. This jailbreak, named Inception by the reporter affects ChatGPT from OpenAI, claude, from Anthropic Copilot from Microsoft of course, deepseek, google's Gemini, twitter's Grok, facebook's MetaAI and Mistral AI. This single approach works across them all.
The second jail break is facilitated through prompting the ai to answer a question with how it should not reply within a certain context. I mean, we're literally right. We're like confusing the AIs. Answer a question with how it should not reply, instead of actually asking it to reply, which it won't because it shouldn't. So no, no, no, no, no. That's not what I want you to do. I want you to tell me how you shouldn't reply within a certain context. The AI can then be further prompted with requests to respond as normal, and the attacker can then pivot back and forth between illicit questions that bypass safety guardrails and normal prompts. That second jailbreak affects chat, gpt, claude, co-pilot, deep seek, gemini, grok and Mistral AI, allowing an attacker to abuse them for instructions to create content on various illicit topics, such as controlled substances, weapons, phishing emails and malware code generation.
A motivated threat actor could exploit this jailbreak to achieve a variety of malicious actions. The systemic nature of these jailbreaks heightens the risk of such an attack. Additionally, the usage of legitimate services such as those affected by this jailbreak can function as a proxy hiding a threat actors, malicious activity, in other words, instead of like using some dark underworld. You know dark web AI. We know dark web AI. We're using chat GPT, and it told us how to mix up that chemical explosive.
You know, and I don't even know how to respond to this, leo, other than to just shake my head and understand just what a new Wild West we have entered into here.
One of the key coding lessons of my own past 50 years of programming computers and I guess it's actually more like 52 now has taught me is that if I'm not 100%, completely certain how my code operates, it's, it's unlikely to be correct, because there are so many more ways for it to be wrong than for it to be right.
Then I read about the bizarre ways it's possible to have conversations with these conversational AIs in ways that lead them to ignore the imperatives of their programming, and I also understand that no one is really completely certain how all of this works in the first place. And then I think of my own far simpler coding experiences and it becomes very clear that this incredibly fuzzy world of AI which we're stepping into almost certainly has a far longer way to go before we're able to get a grip on it and, I think, far further than most people probably expect. I don't even think we're close to actually having control of this and, of course, a lot of people who actually are spend a lot more time thinking about this than than I have are very worried about what can happen, right, yeah?
0:59:28 - Leo Laporte
yeah, although I'm kind of a mixed feelings about ai safety, I think, as we've learned, it's kind of maybe a mistake to even try Right, right, right, and I don't think the companies are trying that hard. Obviously, if this thing works, they're not trying that hard.
0:59:46 - Steve Gibson
It's like I'm not asking you to tell me something that I shouldn't, but if I were asking you to tell me something that I shouldn't, but if I were asking you to tell me something that I shouldn't, what would you say? And then it's like well, well, in that case, if you're not actually asking, you're just asking me. If you were asking what I would say?
1:00:03 - Leo Laporte
Purely hypothetically. That's right, shouldn't you tell me?
1:00:06 - Steve Gibson
Yeah, now, I know you can't tell me how to make this explosive, but you know, if you could tell me how to make it, what would that be like? Yeah, oh yeah, I mean yeah, like you know, no street smarts in these things, yet no and no they're little children.
Yeah, yeah, okay. So one thing we all have in common yeah, yeah, my life's work, with the first half of my life invested in preparing for the second half, where I've been able to do something about it and have created solutions to help recover data lost or seriously endangered for arguably hundreds of thousands of PC users during the last 35 years. Nearly two weeks ago, the popular and respected Tom's Hardware website posted a piece under the heading Unpowered SSD Endurance Investigation Finds Severe Data Loss and Performance Issues. The start of that piece said you may not know it, but SSDs will lose data after a period of time if they are simply left unplugged, which can be a serious threat to your data if you store backups or precious files on unplugged SSDs. Not surprisingly, many of our listeners who are owners of Spinrite sent email wondering what I thought of the research Tom's hardware shared. Before I share the rest of that piece, which I later released as freeware, as a platform for verifying the operation of Spinrite's new low-level device drivers, the ReadSpeed benchmark takes an accurate measurement of a mass storage drive's performance at five locations across the drive at 0%, 25%, 50%, 75% and 100%.
We all knew that spinning drives would perform much more slowly as we gradually move toward their end, since track circumferences would be shortening, thus reducing their data transfer rate by as much as half. And that's what we now know. Today's super high density spinners have half the performance at the end of the drive because, in order to get this like to squeeze every literally squeeze every last bit of data into the drive, they've had to push the tracks further toward the hub of the drive. But being entirely solid state, none of us expected to find what we did. We didn't expect to see any speed variance in SSD performance, but, as we all know, that's not what we found. Many of us discovered that the SSDs our PCs were using were much slower to read near their beginnings of the drive than anywhere else. What we discovered was that those regions which were only ever read and rarely or never written, had become far slower to read over time, Since the front of these drives is where the operating system is written when it's first installed. We finally knew why, for years, pc users with solid-state MASH storage have been reporting that their systems seem to have slowed down over time and be running more slowly than when they were new. It turned out that it wasn't their imagination. Systems really do slow down because the reading performance of their solid-state mass storage really is slowing down. And we also know that, you know, not just thanks to synthetic benchmarks like read speed or what's built into Spinrite, but because once Spinrite 6.1 allowed people to easily rewrite their SSDs, they reported that they could clearly feel the difference. Their machines were once again booting in seconds, where they'd slow down to, in some cases, minutes, and the various annoying lags in its use they reported as completely disappeared.
There have been a great many theories voiced to explain this. People get themselves, I believe, all tangled up in the complexities of translation layers, wear leveling, block erasures, trimming and all the many various technologies that have been layered on top of basic NAND storage cells in an effort to overcome those cells' inherent physical limitations. To my mind you know donning my physicist's cap for a moment there's really no mystery about why this is happening. As I've described a couple of times in the past, flash NAND memory bits are just incredibly tiny electrostatic charge storage cells. They consist of a tiny bit of metal which gives electrons a place to sit, surrounded by insulation which keeps those electrons from wandering off when we wish to change what's stored in that bit cell.
We first create a high voltage Remember that voltage is electrostatic, pressure is electrostatic pressure. So we create a high pressure that's able to break down the cell's insulation, to inject some electrons across that insulation into that cell. The electrons that were injected under high pressure then remained there, trapped behind the cell's insulation. There, trapped behind the cell's insulation. At that point the magic of what's known as field effect transistors allows the effect of the resulting electrostatic field created by the charge which has been trapped in that cell to be sensed, so we're able to later read out what was previously stored there. So that's the whole magic of flash memory. That's how it works and overall this is an astonishingly effective technology. But it has one fundamental problem deliberately abusing a cell's dielectric insulation. Whenever we use the brute force of high voltage to break it down and force electrons across the barrier it was designed to present to their flow, it's trying to be insulation. We're breaking down that insulation. You know we want a perfect insulator, except when we don't want it to be perfect and over time, with repeated breakdown of its like forcible breakdown of its insulation, its insulating properties begin to falter and weaken with the barrier become slightly more porous to unintended electron migration.
Okay so with this background, let's look at what Tom's Hardware wrote. Their piece said. You may not know it, but SSDs will lose data after a period of time if they're simply left unplugged, which can be a serious threat to your data if you store backups or precious files on unplugged SSDs. A year two update on the how long can SSDs store data unpowered video series is another reminder about the importance of regularly refreshing your backups with a bit of juice. The tests consist of storing data on an SSD and then leaving it unplugged for years to see the impact on the stored data. An SSD's endurance rating is calculated based on how long it can store data if left unplugged after a certain amount of data has been written. Hence the importance of this testing.
Techtuber HT Wingnut is back with a report on his modest experiment involving a quartet of SATA SSDs. The key finding was that the two-year-old, well-worn drive exhibited noticeable performance degradation and was affected by a handful of corrupted files. These are signs that this particular SSD was on its way to silicon heaven. That's not true, but that's what people think. But it's something I'll explain. Anyway, they write. Ht Wingnuts video is an update on an episode from a year earlier and further updates are promised. They said the four tested Levin JS600 branded SSDs are basically bog, standard no-name units. Ht Wingnut says they're all TLC SSDs with 128 gig capacity and rated to withstand 6D60 terabytes of written data. 6d60 terabytes of written data. Every drive has 100 gigabytes of files containing random data, with hash values for all the content provided for later verification.
Now I'll just interrupt again to note that this is not how I would conduct such a test, since the file system's metadata that's being relied upon to access these files is sharing the same medium as the files it's managing, and you really don't want a file system involved at all. What you care about is the underlying medium underlying medium. The right way to do this would be to use a pseudo random function to generate a stream of pseudo random data that would then be written to the raw media. Then, years later, a year and two, and three and four and so forth use the same pseudoom function to recreate the original data stream for a bit-by-bit comparison with what is later read back. You know, but who am I to talk? I didn't do any of that, and this HT Wingnut guy at least did what he did, so what we have from him is better than nothing.
The article continues better than nothing. The article continues the two fresh sample drives have barely been used. Perhaps only the 100 gig of data was written there and verified, and that's it. Meanwhile, the two worn drives had been subjected and this is before the testing began they were subjected to 280 terabytes of written data churn, much more than their rated 60 terabytes endurance rating. So this guy deliberately you know, really you know overwrote them in order to fatigue them. Before beginning this experiment, they said if you watch the previous year one video, you'll have seen there were no issues with either worn or fresh drives.
He says. However, time has now taken its toll. He says let's take a look at the year, two samples in turn. He said, for the fresh SSD tests. The data on this SSD, which hadn't been used or powered up for two years, was 100% good on initial inspection, all the data hashes verified, but it was noted that the verification time took longer than two years previously. Hd Sentinel tests also showed good, consistent performance for a SATA SSD.
Digging deeper, all is not well, though, although, firing up crystal crystal disk info, ht wingnut noted that this SSD had a hardware ECC recovered value of over 400. In other words, the disks. Error correction had to step in to fix hundreds of data based parity bits, of data-based parity bits. In other words, even this was the fresh SSDs not well-worn, just having not been used for two years and hardware ECC is being required in order to recover the data and it's slowing down. Okay, according to HT Wingnut. They write seeing these error means the SSD is on its way out Again. No, everybody gets this wrong, but I understand the way it looks. It's just the data has been leaking.
1:14:14 - Leo Laporte
It's just leakage which you know, as you get older it can become a problem. Yes, it's not hardware failure, it's just the data needs to be refreshed. That makes sense, Exactly, yeah.
1:14:25 - Steve Gibson
So they said. Indeed, if there is anything iffy about your data storage integrity, it is at least a warning. Data storage integrity, it is at least a warning. However, the errors could also have something to do with the drive being left unpowered for two years. Again, I don't think so. That could even be a problem, because if it were powered up it would be hotter, and heat is something nobody remembers to think about. Anyway, I have a chart in the show notes for anyone who's interested. Who shows and the chart shows what the various testing times were and how. It was indeed way worse on the Warn drive that had a lot of data written to it. Because all of that excessive data, again, it rewrote the entire drive. It was a 128 gig drive and they wrote 280 terabytes. So it really worked the drive well past its endurance rating, they wrote.
As the worn SSD's data was being verified, there were already signs of performance degradation. The hashing audit eventually revealed that four files were corrupt. Hash did not match, took over four times longer up to 10 minutes and three seconds to 42 minutes and 43 seconds Again, not surprising to anyone who has seen this happen. You know for themselves. Further investigations in HD Sentinel showed that three out of 10,000 sectors were bad and performance was spiky. Returning to CrystalDiskInfo, things look even worse. Ht Wingnut notes that the unrecoverable sectors count went from 0 to745 before to 201,273 after tests. That one day, so more than 200,000 ECC recoveries. So they said in summary, the year one fresh and well-worn drives had no issues. However, the year two heavily worn SSD had file corruption and performance was poor. The so-called fresh drive was still good, but ECC figures still raised concern. Come back in late 2025, they wrote, for the next update from HT Wingnut and they finish.
We also want to say that this is a very small test sample, highlighted out of our interest in the topic rather than for its hard empirical data. He said I've also experienced SSD data loss after leaving a mini PC unpowered for just six months or so at my Pita Terre in Taiwan. On return, windows refused to boot or be repaired, but a reformat and reinstall seemed to return everything to normal right, because there was nothing actually wrong with the drive. So I have a link in the show notes to HT Wingnut's YouTube video for anyone who is interested. Everything that we just saw, everything he found, perfectly matches the model I've developed and shared about what's going on with our SSDs.
The reason we see the performance drop when attempting to read data that was written long ago is that those microscopic, tiny electrostatic charges stored in the SSD's NAND bit cells have partially leaked away. Bit cells have partially leaked away. This very slightly changes the voltages stored in the cells and forces the flash controller to work much harder to recover and reread the original data. We sense this by seeing the SSD's performance drop. If you ever notice a drop in SSD performance, that's the time to rewrite its data. You'll want to do so before that data becomes completely unreadable. And the reason the problem was demonstrably worse on well-worn SSDs is that all of that prior writing further weakened the insulating dielectric which was keeping the electrons in their place. So the leakage rate was significantly higher on those well-worn SSDs, which were tending to lose their data faster.
And, as I mentioned, one thing that has not been mentioned, which we know from physics, is that temperature is crucially important.
Several years ago we covered a piece of news here that noted that offline SSDs stored in hot data centers tended to lose their data more quickly than those same SSDs stored in a cool environment.
Heat inherently agitates electrons and increases the probability that one will make it across the cell's insulating barrier. It's known as tunneling. So if you do have any offline SSDs or thumb drives where you have important data stored, I'd give them a full data rewrite pass. You know Spinrite's able to do that using level three then put them in a Ziploc bag, in you guessed it a refrigerator, or at least store them somewhere which is guaranteed to stay mostly cool. The reason why rewriting an SSD's existing data for example with Spinrite's Level 3, restores its factory-fresh performance is that the act of rewriting an SSD literally restores the strength of its bits, which we now have additional and rather absolute proof decay over time. Rewriting an SSD's data eliminates the uncertainty in the state of individual bits that can and does creep into our mass storage over time. Therefore, the speed with which an SSD's data can be read forms a highly visible and valuable proxy for the integrity with which the SSD's data is currently stored and is readable and recoverable.
1:21:24 - Leo Laporte
This sounds like somewhat similar to spinning storage, right, the same kinds of things happen. I mean, it's not physically the same process, but but yeah yeah, my, yeah.
1:21:36 - Steve Gibson
My feeling is that that what goes bad with spinning storage is is like lubrication of the drive. It's not a weakening of the magnetic signal yeah, uh, that that tends to really hold very well. You can get stiction where? The head ends up being welded to the surface, so there are other problems.
1:22:05 - Leo Laporte
But the data on a spinning drive is not going to slowly decay over time in the same way.
1:22:12 - Steve Gibson
I think that's all of the support mechanisms that are required, that the physical do do have a problem. Yeah, so again, your, your 3-2-1 backup strategy. Is you know what you really want? You want to have a hierarchy of of backup, but I'm, you know, I, I I wanted to take this opportunity just because this was perfect evidence of the fact that that what we've, what we discovered to our surprise when we began playing uh with the development of 6-1, was that the front of ssds had slowed down right and it was like what the heck why? And now we know, and happily it's only temporary. Those drives that are having all those problems they're not bad, said to me. Ssds never rewrite their own data. That's not something they do. So having the drive powered up arguably keeps it warmer and I think it causes it to lose data more quickly.
1:23:30 - Leo Laporte
Ah, interesting.
1:23:31 - Steve Gibson
So I'm not convinced that this is a matter of them being unpowered. They just haven't been touched in so long, right, I know how that feels.
1:23:41 - Leo Laporte
No, I'm just kidding. Actually, Alan sent me an email just this week for you, Both of us actually. Yeah, so you got it. Yes, oh, good Okay.
1:23:51 - Steve Gibson
Yeah, he has some neat points to make. Yeah, he's a sharp fella and you have a neat point I do.
1:23:58 - Leo Laporte
I'm so glad you asked, mr Gibson, I've been just champing at the bit Waiting to tell you about OutSystems, our sponsor for this segment of Security. Now OutSystems the leading AI-powered application and agent development platform. They've been doing it for more than 20 years. The mission of OutSystems is to give every company the power to innovate through software. You know, typically we talk about this all the time.
It teams have two choices to make. We call it the build versus buy conundrum right to make. We call it the build versus buy conundrum right. Do you buy off-the-shelf SaaS products for speed but then lose flexibility and differentiation? Or do you build your own custom software, but at a cost of time and resources? Well, there's now a third choice between build and buy.
Ai forges the way for another path. It's the fusion of AI, low-code and DevSecOps automation into a single development platform. That's OutSystems. Your teams will build custom applications with AI agents as easy as buying generic off-the-shelf. Sameware and flexibility, security and scalability come standard with OutSystems. With AI-powered low-code, teams can build custom, future-proof applications just as fast as they would buying it and with features that you really will appreciate fully automated architecture, security, the integrations are there, the data flows, all the permissions. That's all handled by out systems. Out systems is the last platform you need to buy, because you can use it to build anything and customize and extend your core systems. It's time to build your future without systems. Visit out systemscom. Slash twit to learn more. That's out systemscom. Slash twit to learn more. That's outsystemscom slash twit. We thank him so much for supporting Steve Gibson and Security Now, and now it's back to Steve for some listener feedback.
1:26:05 - Steve Gibson
Yeah, got a bunch of good stuff to share. John Canfield said hi, steve, like you, I had heard about this Windows Sandbox feature long ago. John Canfield said XML configuration with map folders to my PC memory and CPU configs, and it sits on my PC to this day, ready to use when the need arises. When you were describing the significant architectural capabilities and efficiencies that went into this feature, I can't help but think that this would be exactly what was needed for Windows 10X. And he said see Paul Theriot's article, particularly the last sentence, which he quotes. Quote worse, microsoft hasn't addressed the single most important 10X feature its planned ability to run Win32 apps in a container. Is that key work? Continuing Unquote. He quotes Paul. So he says could Windows Sandbox have been developed for Win10x or maybe the reverse? This feature existed before and someone said hey, let's use that for 10x 32-bit apps, let's use that for 10X 32-bit apps. Windows 11 came out in 2021, and Windows Sandbox was developed in 2018,.
According to your post, those years line up pretty well for one or the other to have happened. All the usual praises, listening and watching back to the tech TV days. Proud Spinrite, owner, a joy to watch you and Leo every week. Best regards, john. That's great. So I chose John's question because it serves to highlight one of the reasons why Microsoft's implementation of Windows Sandbox is so economical. The long ago abandoned Windows 10X effort was Microsoft's ill-fated plan but I understand it to wash away Windows' long legacy of backward compatibility. At one point they were planning to have a dual-screen Surface tablet PC.
1:28:28 - Leo Laporte
The Courier oh, we wanted that so badly.
1:28:32 - Steve Gibson
And they wanted to move toward more of a lean, mean OS, sort of like iPad OS. That meant essentially starting over from scratch with a new implementation of Windows, and, among other things, that version of Windows would be dropping support for 32-bit Win32 apps. Now, philosophically, I love the idea of a complete reboot of Windows. One of the mixed blessings of today's Windows OS is that it still runs Win32 apps and it probably always will, because they cannot take that away. Too much legacy code depends on it. Just look at how difficult it was for them to kill off Internet Explorer 6. Ie6 refused to die because too many enterprise users had written code that would run nowhere else. And if you imagine that was true for IE6, just imagine trying to take away Win32's API. Remember that Windows 7 included an XP mode. Xp mode was a full virtual machine that would allow Windows 7 users to still run an instance of Windows XP. Why was Microsoft forced to include that? Specifically for backward compatibility, which serves as another example of the powerful drag created by Windows legacy code. And in addition to the Win32 API, windows legacy code and in addition to the Win32 API, windows also runs all of the other APIs that Microsoft keeps coming up with. I've lost track and count of the number of ways it's possible to author applications for Windows. And now they've added the Linux subsystem support.
One of Microsoft's biggest problems with Windows is that they're unable to stop screwing around with it. They can't keep their hands off it. They're continually adding more stuff, but the critical need for backward compatibility means they're never able to eliminate anything that came before. They were finally able to drop support for 16-bit code when they moved to their 64-bit OSs, but even that was painful, and they were only able to do so because Windows hadn't really gotten fully up to speed before everything switched to 32 bits, so there wasn't all that much 16-bit code legacy. So, as I said, philosophically I love the idea of a massively simplified single API rewrite of Windows to create something truly lean and mean. But that's just a pipe dream. It's never going to happen, because what would? What would remain, would not be useful to anyone. And once smart people at Microsoft realized that the windows 10 X project was dropped. So John asked whether the windows sandbox might have in some way been part of the win 10X project. But I can't see how.
What makes the Windows Sandbox so special is that it manages to surface an exact, duplicate instance of the underlying OS in a sandboxed environment. It refuses I mean sorry, it reuses the hosting OS's read-only files and even the underlying host OS's code which is loaded into RAM, and that's the entire key behind Windows Sandbox. So if anything like the Sandbox were to run on top of Win 10x, it could only be an exact clone of the OS it's running on, so it would be unable to, for example, support legacy APIs that had been removed through a host OS rewrite and again through a host OS rewrite. And again, I think Microsoft has probably given up the idea of ever getting rid of their legacy APIs. You know, hopefully they just leave them alone and they don't, you know, wreck them because there's just too much old code there that depends upon the older support Antoine Chopin said. Hello Steve, thank you for security.
Now I had a question about Windows Sandbox you presented last week you mentioned. It uses a clever mechanism, using links to static files to reduce the image size, which seems clever indeed, but made me wonder what would happen if the host OS had been compromised and some files, supposedly read-only, had been modified somehow. In that case I guess the sandbox would be compromised the same way, which means it's not as isolated as one could think. Curious to hear your thoughts on this. Thanks again for the great podcast, antoine. And I would say that Antoine is completely correct. And it would likely go even further, since we know that the Windows sandbox also conserves its usage of RAM by mapping the underlying host OS memory footprint into its own memory space. Any malware that operated by hooking kernel API functions in RAM which we know is something malware commonly does, like rootkits would inherently duplicate those hooks as well, and the same OS compromise would appear inside the sandboxed OS. So Antoine's point is a good one and it's an important distinction between a sandbox and a full virtual machine. As, leo, you noted last week, the sandbox solution is closely aligned with the concept of containers, which share many of the same properties. Neither the sandbox nor containers contain an entire isolated instance of an operating system. They use Hyper-V virtualization to create and enforce containment of the code they host, but they're running on top of their containing host. So neither Windows containers nor the Windows sandbox are isolated from underlying host problems. Only a full standalone virtual machine would provide that. But that level of isolation code comes at the cost of significant host platform resource consumption with a full virtual drive and much more RAM consumption. All these various technologies are interesting and powerful and each one has its place.
Brian asked Hi, steve, love the show and a proud owner of Spinrite. I know this may be a bleak question, but would you consider open sourcing Spinrite upon your eventual, but hopefully distant, passing? He says it's an excellent product and I just don't have faith that people will put this kind of effort into something like this again. I'd love to see Spinrite live on and continue to keep up with hard drive technology into the future. Thanks, brian. And he says you can use my first name if you ever mention this on the air. Okay, so let me just state for the record I don't consider this to be a bleak question at all. I consider it to be practical and flattering. Our listeners here would have no way of knowing that I have formally stated several times in GRC's public newsgroup forums that it is my intention to release all of my work, the source code for everything I've ever written, into the public domain once my own commercial interests are no longer connected to it. Good on you.
1:37:05 - Leo Laporte
Mr Gibson, I did not know that. That's great, I'm going to do that.
1:37:08 - Steve Gibson
Yay. Now, ideally this would occur at some point when I still have some cognitive faculties available, so that I could shepherd the code into the world and be available to answer any questions that would doubtless arise. So I very much look forward to that day, since I think it would be a lot of fun. But the bottom line is that, yes, once I hang up my spurs or am struck by lightning, everything I've created will be released to the public, and I would be honored if there was interest in keeping it alive and growing into the future in whatever form might make sense. So it will not all be lost. Galen wrote. Hello, steve, in episode 1019, you're talking about the constant internet spam and brute forcing going on. It is so much worse than you stated. He said I have SSH open on my home lab so that I can manage it remotely with fail to ban configured, fail to ban monitors, auth logs, and can do automated actions based on successive failures. I have fail to ban set up to ban the IP of anyone who has two failed login attempts for three hours, then ban anyone with two bans in the same day for a year, as this lab is only used by a close friend and myself and we both use keys to authenticate, it's unlikely for us to ever have a failed login attempt. I set it up with a Discord bot to automatically notify me of bans and send me daily reports on ban counts and it is crazy to watch. Yeah, I bet I've seen days with up to 5,000 unique IPs banned. Yeah, I bet Not all of them end up banned because some of the bots spaced their logins out a lot. I have banned around 26,000 unique IPs and at any moment have around 4,000 banned. I highly recommend that anyone hosting publicly accessible SSH install fail to ban, even with just the default settings SSH.
Thanks for the podcast, galen. Now, this was a great data point and not only supports what we were talking about four weeks ago during podcast 1019, but also more recently when I was talking about the fact that typical network monitoring is only looking at what gets inside the network. While certainly that certainly inside the network is of the most concern, there's still the fact that we don't know what we don't know. We don't know what we don't know. The fact that Galen has witnessed this firsthand has doubtless altered his behavior in a healthy direction. It will serve to inform him about just what a jungle it is out there and the degree to which he can really never afford to take his own security for granted Say, for example, that he was still relying upon username and password for protection. If he didn't already know better and he does but if he didn't, seeing the truth about how much attention his own SSH server is drawing would doubtless motivate him to take the time to be as secure as he could possibly be.
Like Galen, I've looked at my own external bandwidth logs and what's going on out there, as he said, 24-7, 365, it is truly harrowing. I mean, it's insane. We talked a few podcasts ago about the abuse of login attempts to Microsoft Outlook and how wrong it feels that Microsoft are not providing better abuse protection, are not providing better abuse protection. Everyone knows that credential stuffing attacks have grown to become one of the major threats on the internet, yet Microsoft only offers geofencing for their enterprise users. A few podcasts ago, I took the opportunity to rave about my absolute favorite SSH client and SSH server Bitvice for Windows. Many of our listeners wrote to let me know that Windows already has SSH client and server solutions built in, and that's absolutely true. Windows now offers the industry standard setting OpenSSH server. So thanks to our listeners for notifying me of that, but Windows doesn't have Bitvice built in.
In addition to having an extremely pleasant zero learning curve graphical user interface, I have my Bitvice server instances configured to only consider everice. Client is 100% reliable. A single failure to authenticate from within the US permanently blacklists that IP and just so that I'm not locked out in the event that I fumble finger the connection at that client end, I have permanent whitelist IP overrides for the two IPs I would probably always be connecting from. As I've mentioned previously, my two cable modem IPs are extremely static. And all of that is after configuring the server to only accept authentication via a public-private key exchange challenge. Finally, all of that was done with a few clicks of a mouse while browsing the Bitvice user interface.
So much as I strongly prefer living off the land solutions using what's already present in this case, I'm not giving up Bitvice for anything. It remains my highest possible recommendation for anyone who wants to run an SSH server on Windows. It is trivial to implement that level of, you know, multi-layered security, and I mean it is. I cannot imagine, like Galen, running an SSH server where you don't at least I mean like at least geofencing. Why would.
If I am always in the US and I virtually always am why would I ever entertain having my SSH server accept a connection from India? And that's, as it happens, where they're like the majority of them are coming from. That's just. You know, no, and it's easy to just click a button and say US only. Thank you very much. And speaking of the utter mess that the internet is outside of our walls, we have a note from matt davis. But before this, leo, since we're at an hour and a half, in sure, let's take a break and then we're going to continue with some great feedback from our listeners you're going to like this next sponsor, brand new sponsor on the show.
1:45:29 - Leo Laporte
Yay, uh, and they do. Uh, a very clever way to train your employees not to click on a phishing email. Very good, they gamify it, so it's fun. I'm talking about hoxhunt h-o-x-h-u-n-tcom. As a security leader, I'm talking to you.
You get paid to protect your company against cyber attacks, right, but it's getting harder and harder. More cyber attacks than ever. And of course, I think the majority of them come through phishing emails and nowadays generated with ai. So you can't look for grammatical errors anymore. Like, they're well written, they're very convincing. So you need an awareness program, right, you need to teach your employees what not to do. But legacy, one size fits all. Awareness programs don't stand a chance against modern phishing attacks. At most they'll send, you know, four generic trainings a year. Employees ignore them. You actually have to crack the whip to get them to take these trainings and then, when somebody actually clicks, you know like in and on the, on the, on the test, phishing email. Right, then they're, they're forced into embarrassing training programs that feel more like punishment than anything else.
There is a better way. More and more organizations are trying hox hunt and I gotta tell you. It is, it's fun. Hox Hunt goes beyond security and awareness and changes behavior by rewarding good clicks and coaching away the bad. Whenever an employee suspects an email might be a scam and some of them are legitimate scams some of them are from Hox Hunt Hox Hunt will tell them instantly. Some of them are from hawks hunt. Hawks hunt will tell them instantly and in a you know like. You get a gold star, providing that, like dopamine rush, that gets people involved. They want to click, they want to learn, they want to protect your company. They want the gold star as an admin for you.
Hawks hunt makes it easy to automatically deliver phishing simulations. It's not just email. You can do it in slack, you can do it in teams, you can use ai to mimic the latest real world attacks. I mean, they are up to the minute. The simulations, even better, are personalized to each employee, based on department location and more so. They're really effective.
And while instant micro trainings solidify understanding and drive lasting, safe behaviors, you can even trigger gamified security awareness training that rewards employees with stars, with badges, boosting completion rates, ensuring compliance. You actually get it. In fact, the fire hawks hunt people told me this. The employees say give me more, give me, give me more, I'm. This is great. It's like duck hunting right, you're going? Oh, I got one, I got one. Choose from a huge library for you customizable training packages. You can even generate your own with AI.
Hoxha has everything you need to run effective security training in one platform, meaning it's easy to measurably reduce your human cyber risk at scale. You need this, but you don't have to take my word for it. There are over 3 000 user reviews on g2, making hawks hunt the top rated security training platform for enterprise, including uh easiest to use, best results. It's also recognized as a customer's choice by gartner and thousands of companies like Qualcomm, aes, nokia, use it to train millions of employees all over the globe. This is so much fun. You actually can go to the website and get a simulation. You could see how this makes it fun for your employees to be smart, to learn, to protect you. Visit hawkshuntcom slash security now, today, to learn why modern secure companies are making the switch to Hoxhunt. Hoxhuntcom slash security now it really works and it's so much fun. Hoxhuntcom slash security now Fun and effective. That's kind of a good combination. Okay, steve, on we go. And a great advertiser for the podcast, isn't it? It's perfect, right? It's exactly what everybody needs, yeah.
1:49:40 - Steve Gibson
Okay. So this is a great, great piece from a listener of ours, matt Davis, who said Hi, steve, I wanted to share a bit of unexpected side effect that I experienced a few months ago when let's Encrypt stepped up from single perspective issuance and started requiring a second perspective gateway protocol hacking. The CA browser forum had decided that certificate authorities would need to be verifying internet domain control from multiple viewpoints on the internet. So, he said, I run a small web hosting business on the side for a few clients, and one client called me one morning to report that her website was showing the big, scary red certificate warning page in Chrome. I took a look and, sure enough, her let's Encrypt certificate had expired the evening before. As you know, all let's Encrypt certificates should be renewing automatically through the ACME protocol and, of course, just pause here for a second. This is the big nightmare, right With short lifetime automated delivery of certs is what happens if anything ever happens to interfere with that process. Suddenly, all the websites that are needing to be renewed can't be, so let's hope that doesn't happen. Anyway, it happened to a client of his right. So what happened, he says? After troubleshooting this problem for over an hour, I eventually realized what was going on.
This client runs a small local photography business in the US. In working to secure her WordPress site, we made a quick and easy decision. She did not need any web traffic from China, russia or any other country banging at her digital door banging at her digital door. If the person trying to access the site wasn't in her local area, or even in the USA, they simply had no business being there. So we set up Cloudflare to block all traffic from all 194 other countries. It was of no use to her and it eliminated massive amounts of bot traffic, image theft, hotlinking, ai scraping, wordpress login attempts and other shenanigans. After implementing that rule, requests to her site again a local photography business dropped over 95% and bandwidth was reduced by even more than that. However, now with Acme challenges coming from random countries around the globe, I've had to take steps to whitelist those let's Encrypt challenges, no matter where they come from. Multiperspective issuance has reduced this site's security, as our web application firewall is now forced to allow certain traffic from any country at any time. This may be an unusual example, but when a website really doesn't need to be global, you can easily reduce your tax surface through GOIP firewall rules and other limitations, or at least you used to be able to Thanks, matt. So, wow, what a great real-life example of the mixed blessing consequences of increasing security.
Whenever we tighten anything down to prevent its abuse, we run the risk of triggering false positive blocks. You know, in my own example of super tightly locking down my own access to my Bitvice SSH server instances, I was acutely aware that, yes, there would be some risk that I might lock myself out of my own server, but that was a balance that I judged to be easily worth the risk In the multi-instance or in the instance of multi-persistence issuance corroboration, which was the title of our podcast a few weeks back. We've only heard from one of our listeners just now, matt, and thanks for sharing that, matt. What a great story. But it's not difficult at all to imagine that there were probably many thousands of other ACME-based certificates that were also probably recently similarly impacted. And Matt's right that by needing to allow a subset of queries from anywhere through to his client server so that it's able to authenticate its control of the domain, he has been forced to reduce that website's overall security. And if Matt were to tighten down on the class of foreign queries that were allowed to reach the server so that only those qualifying were allowed, that is, if he were to be really specific about what his server accepted about what his server accepted then any change that let's Encrypt might make to their own query protocol could again cause a breakage. We're living in a world of trade-offs.
One thought I had and I imagine this probably occurred to Matt he didn't say was that let's Encrypt queries over port 80 using HTTP or what are generated. That is to say, it makes sense, right, since port 443 is what you're trying to provide a certificate for. Let's encrypt. Acme protocol works over port 80, which is not encrypted. It itself does not require encryption in order to do its job, so it uses port 80 because it needs to be sure to be able to make a connection even when there's no certificate present, because it's about issuing certificates. So let's encrypt queries over port 80 using HTTP.
The good news is that pretty much nothing else uses port 80 anymore. We were recently talking about Cloudflare dropping all API support over port 80 because they just don't need it. I haven't looked at Cloudflare's country-based filtering closely, but if it were possible to block all port 443 access from everywhere other than the US, that ought to restore much of the benefit of a full, blanket block, in other words, block all 443 from everywhere but the US, but not Port 80, which could be coming in from ACME verification. So that would mean that only traffic coming to Port 80 would be allowed from anywhere. Otherwise 443, which is really all you need now for a website, could be restricted to the US, which, as Matt saw, was a huge win.
Then, since let's Encrypt's ACME protocol always and only looks for its domain control authentication token in the ACME-challenge subdirectory of the well-known root directory, that is to say there's one specific directory where the ACME protocol looks in, it would probably be possible to set up a htaccess or a webconfig rule to only allow queries over port 80 to that one directory, which would be absolutely uninteresting to anybody but Acme protocol. That ought to allow let's Encrypt to obtain what it needs over port 80 incoming from anywhere in the world, while not giving any of the rest of the non-US world anything that it might find interesting no login attempts, for example, or you know any of the other shenanigans that matt talks about. And boy, what a lesson that is to just to geofence a site that does not need international presence in order to dramatically reduce all of the crap that, uh, you know the internet otherwise is and it's not. You know her site's not like some big deal, right, it's a local special interest photography site, for you know her region, yet look what it's subjected to. Wow.
Daryl in Kansas says Steve, I'm a Spinrite site licensed guy. Much appreciated Daryl. I listen to Security Now every episode guy. Much appreciated daryl. I listen to security now every episode. Um, how safe is the trust, this computer option for websites when you're at home on your own network? He says I use a chrome box for extra security. Do you click yes or let sleeping dogs lie? Thanks for security now. And hi to Leo.
1:59:54 - Leo Laporte
Hi, Leo, depends how much you trust your spouse, or evil maid, I guess?
1:59:58 - Steve Gibson
Right? Well, and the sense is, I wanted to explain to Daryl what was going on. So what's going on beneath the surface is not at all obvious from the question itself. Right? Do you trust this computer Like what it's my computer? Why would I not trust it?
So, as we know, each of our web browsers which makes queries to remote websites, each of those queries stand alone. That means that unless something explicit is done, there's no way for a remote website to know who any given query is coming from. That something explicit that is now always done is that any time a web browser query is made which does not include a browser cookie, one is sent back to the browser. A unique cookie is sent back to the browser with its reply, so that all subsequent queries which issue from that browser will automatically be tagged with that new unique cookie, since that browser cookie will always be returned. So the first thing to appreciate is that all of the web browsers that are querying remote web servers, if they don't already have one, are each given a unique cookie so that the remote site has some means of telling them all apart. The next important point is that if a specific user identifies themselves to that remote website by logging into it using some credentials. It's the ongoing presence of this cookie that serves to keep them logged in. Their logged in-ness is thanks to that cookie. Thanks to that cookie. Okay next, it's probably always possible to deliberately and explicitly log out of any website. There's always going to be some log out option, generally, you know, by growing convention, in the upper right-hand corner of the website's pages. But the question is what happens if you do not remember to log out? Many websites don't care at all how long you've been gone, how long you've been away. When you return you'll still be logged into that site, and the only reason you'll still be logged into that site is that your web browser has remembered and still has the cookie it received the last time you were logged in.
Grc uses the Zenforo software for its various web forums and I cannot recall the last time I was asked to log into my own forums. You know, for me that's a convenience and I'm sure it is for all of the people who hang out there. You know, since in my case I'm the only one using any of the computers where I'm logged into our forums. So I'm able just to go to forumsgrccom and pick right up where I left off. The same thing is true for xcom. Actually, there was an instance where, about a couple of months ago, I got logged out and I had a hard time getting logged back in because I mean, I'd been logged in for years and something happened where I lost my, my, my browser cookies and so I had to, like you know, do it again. So you know, everybody's used to. Now, these days you just sort of you stay logged in.
But what if multiple people use the same computer? Or what if you're logging in an Internet cafe or in a public library? In that case you would not want your login to be so persistent. And that's what this trust, this computer checkbox which often accompanies a log on page, is all about. Cookies all come with an optional expiration date. If that date is ever reached, the web browser will no longer honor the cookie. Instead it simply deletes it. But I mentioned that the expiration date is optional.
If a cookie is given to a web browser without any expiration date, then that cookie is deliberately never written in any way to any form of persistent physical storage. It is only deliberately and explicitly ever retained in RAM. That means that once the web browser application is closed, the values of any of the non-expiration dated cookies it may have received while it was running will be lost forever. And that's the beauty of not having the trust this computer checkbox checked when you log into a website. When logging in with that checkbox unchecked, any log on authentication cookie your browser receives will have no expiration date set. So it will be ephemeral and your logged in identity will be deliberately lost when you close the web browser application.
So, daryl in Texas I mean in Kansas you asked how safe is the trust this computer option for websites when you're at home on your own network and only you can really answer that.
But now you probably can, since you should have a good understanding of exactly what that means. It boils down to whether anyone else might have physical access to any computer where your prior logons would be persistent because you had enabled the trust this computer option which will have created persistent logon sessions. Which will have created persistent logon sessions. If you're the only person who has access to any computers where you might have left a site logged on, then remaining logged on is likely a convenience. That would have no downsides. But if others might use a computer where you were left logged on to a site which you would prefer, they not gain access under your account and since you might easily forget to explicitly log out after using that site, then logging in in the first place with trust. This computer disabled would mean that you'll be automatically logged out when the browser is closed or the computer is turned off.
2:06:30 - Leo Laporte
So that's the whole tune up on what's going on with that checkbox it just means it used to be that sometimes they'd say are you on a public computer, remember that, and that may be a little easier to understand. Uh, for people like yeah, I mean it's.
2:06:45 - Steve Gibson
It's like my own computer. Why would I not trust right, because it has an inet pub folder on it yes that's a good reason, but I mean.
2:06:53 - Leo Laporte
So I think that that's probably a more accurate way to ask the question. Obviously, some lawyers are, you know, seriously.
2:07:03 - Steve Gibson
Trust this computer, I guess because if you were at a computer in an internet cafe or in a library, Then you would certainly not right.
2:07:15 - Leo Laporte
Yeah, you would say I don't trust this computer, I don't know who's going to look at it next right. So I think the public computer made more sense to people. But I guess, yeah, do you trust this computer?
2:07:26 - Steve Gibson
yeah, and you can't ask. Would you like your log on session to be forgotten? Yeah, that's even shut the browser down. I was like what?
2:07:35 - Leo Laporte
actually that is the right question, that actually is the right question. That is the right question yes, maybe they should ask that okay, and one last piece of feedback from angus mckinnon.
2:07:46 - Steve Gibson
He said, after reading the following what would you recommend? He said I am a backblaze customer. Now okay. Angus's note included a link to a document from the website of morpheus research. I have the link in the show notes for anybody who might also be a a backblaze customer before you get too far into this, though, I do want to issue.
2:08:12 - Leo Laporte
I've been looking at this and I'm trying to figure out whether we should talk about it okay backblaze denies it. They say, these morpheus guys don't know what they're talking about.
2:08:22 - Steve Gibson
So okay, so for what it's worth, I I was very careful, uh, to say that, you know, based on this, so, who knows this could?
2:08:33 - Leo Laporte
this was basically came from somebody who is shorting backblaze, so although from it doesn't sound like there's much left to short.
2:08:44 - Steve Gibson
Well, if you believe this.
That's the point. So let's, so, let's, so, let's do this. Um, because they've been around forever. They've been around for 18 years. You know the name is very familiar. Uh, they were founded in 2007 and they went public four years ago, in 2021. Nobody disputes any of those facts. Apparently, their stock is not worth what it once was, and so Angus saw the same research that you and I, leo, have both seen, and he's freaked out by it. I ended up noting that this research said that Backblaze had lost many of their customers to wasabi, and all I know about wasabi is that they used to be a sponsor of the network.
2:09:34 - Leo Laporte
I know the guy who created wasabi and he's a good guy.
2:09:38 - Steve Gibson
Yes, so I like wasabi so what we'll say to angus and any of our listeners who may also be back blaze customers is I have a link to uncorroborated that's what it is basically report, yeah, which would, if you like, were really dependent on your backed up data, worry you whether you would be right to be worried. I don't know.
2:10:06 - Leo Laporte
A lot of people in our community use Backblaze, so it just makes me very nervous. I really went back and forth about whether I would want to report this story or not.
2:10:20 - Steve Gibson
So it's there and I think we've said enough.
2:10:24 - Leo Laporte
Yeah, I don't know how to corrupt it. It came from a short seller, so that means somebody who has shorted their stock who wants to benefit from further driving it down?
he wants their stock to go down so he can make money. So that's the only reason I that was a alarm bell and plus that and back place is a great company. They have been for a long time. They do that hard drive report, which is extremely useful. I know many people have been for a long time. They do that hard drive report, which is extremely useful. I know many people who use Backblaze, including many of our hosts.
2:10:58 - Steve Gibson
So I'm very reluctant to. So I would say I don't care about Backblaze's status because I haven't ever used them and I don't use them Right. There are many allegations here that could be checked. You know there are some that can't be right, like the value of their share price. That's a matter of public record.
2:11:20 - Leo Laporte
Right. So Backplace says the report is inaccurate and misleading, based largely on litigation of the same nature and a clear attempt by short sellers to manipulate our stock price for financial gain. They claim that independent third party reviews have found there has been no wrongdoing or issues with Backblaze's public financial results.
2:11:43 - Steve Gibson
There are allegations of multiple lawsuits against them, so that would be something that is also in the public record.
2:11:49 - Leo Laporte
That's true, those are true, those are real. Yeah, it's. Yeah. I mean it's important to know that. Just my, my journalistic nose went up a little bit and I thought they're also in my hometown, which made me a sad. Irvine.
2:12:04 - Steve Gibson
Well, that means they're good, no, they're in San Mateo.
2:12:06 - Leo Laporte
Oh, your hometown. Hometown, yeah, where you grew up. That's where I grew up in San Mateo. Yeah, you know we'll. We'll keep digging on this and we'll absolutely report on it if we can get any corroboration of these allegations.
2:12:18 - Steve Gibson
Yeah, and mostly I just wanted to bring it to our listeners' attention because this, you know, angus was worried because he's a Backblazed customer and he said what do you think about this? And again, the way I phrased this I said, you know, I said this report clearly unnerved our listener, angus, who wonders what I would recommend.
2:12:38 - Leo Laporte
The lawsuits came from two former employees, one of whom was their head of finance for four years and the other as a VP of investor relations. So the lawsuits and they're real lawsuits, but they haven't been adjudicated yet either. So I just I don't know.
2:12:57 - Steve Gibson
Yeah, and, and, and, and. The report out uh alleges that since the IPO, the share price has dropped by 71%.
2:13:04 - Leo Laporte
Right.
2:13:05 - Steve Gibson
Again you could, that you could look that up. That's percent right. Again you could, that you could look that up. That's, that would be a matter of public record. Yeah, they apparently raised a hundred million dollars when they went public and yeah, and I, I mean I've never heard anything negative about backblaze. So you know, and who's to say, leo, that if the company's in trouble, they they're a public company, they've got customers and assets and revenue. They might be purchased by a big fish, right? So it's not to say that they're not a going concern and would not remain viable.
2:13:41 - Leo Laporte
Yeah, their quarterly results come out May 7th. Maybe we'll learn more then.
2:13:49 - Steve Gibson
Cool and I'm glad you gave us a yeah. Well, I've been going back.
2:13:54 - Leo Laporte
Since this story broke, I've been going back and forth about how we wanted to report it, and so I'm glad you brought it up.
2:14:00 - Steve Gibson
Yeah, in case a listener needs to know. Our listeners are intelligent. I'm glad they know. Yeah, they can do with it. Even it's glad they know.
2:14:05 - Leo Laporte
Yeah, they can do with it.
2:14:06 - Steve Gibson
Even though we're not able to make any kind of representation Right, what we can represent is why it would be good to be in the club.
2:14:14 - Leo Laporte
I would love everybody to join our club. And here's something I can tell you Even if we were to go under, it's only seven bucks a month. Come on guys. Oh look, we're in little round portholes. Hi everybody, can I come over to yours? Yeah, come on over, steve. What is the club?
Well, four years ago we created Club Twit. It was right in the middle of COVID and advertising was starting to disappear and we thought you know, all along, from day one and I know you remember this, steve the whole idea was we want to be supported by our audience. Our community is the best. That's what makes Twit hum. We realized early on that to grow in the way we wanted to, we were going to have to take advertising. In fact, your show was the first to have an ad. But I still have that kind of dream of being supported by the people who listen to us.
What we decided was we could kind of split it down the middle For seven bucks a month, which is as low as you can go. I mean, you know this is a heck of a deal. You get ad-free versions of this show and all of our shows. You get access to our Club Twit Discord, a great community where you can hang out with like-minded smart people. And it goes all around the clock, not just when the shows are on. There's also events going on. We're going to do all the keynotes in there. For instance, from from now on, microsoft's build, google, io, apple's wwdc because we keep getting takedown threats from apple. So we just thought, well, we'll do it in the discord for club members only. So we're going to do that.
We also have things like Micah's Crafting Corner. The Giz Whiz is coming up with a special 2000th episode reunion. We're doing the photo Chris Marquardt, our photo guy this Friday. Anyway, I can go on Stacy's Book Club. These are all things that we don't do in public. We do in the club as a benefit to club members. In return for you supporting us, we like to give you a little extra value, but the real value is knowing that you're supporting the work steve does and everybody in this network does to keep producing content that we hope you love. It's a way of voting twittv slash club twit. If you're not a member, I hope you'll consider joining. We'd love to have you twittv slash club twit. If you're not a member, I hope you'll consider joining. We'd love to have you. Twittv slash club twit. All right, steve. I'm dying to hear more about this sandbox escape, or whatever you call it. Well, what do you call it? Is it escape?
2:16:42 - Steve Gibson
Is it? No, it is Malware has figured out. Hey, there's this cool thing called Windows Sandbox, let's hide in there. So last week's Windows Sandbox podcast reminded us that you know, everybody with Windows 10 or 11, with the exception of Home Edition users has access to a very nifty Windows execution environment specifically designed to allow users to safely experiment with throwaway programs, installations, files and anything else, without having any impact on their primary Windows OS installation. And, moreover, I was very impressed with Microsoft's surprisingly efficient and economical implementation, which got so many things right.
One interesting feature of Windows Sandbox, which I believe I mentioned in passing last week, is that Windows Defender and this is certainly salient here is disabled by default within the Sandbox and it cannot be enabled via either the GUI or PowerShell commands. So isn't that a nice little place for malware to hide somewhere where there is no AV? Now, this decision was presumably made because running Defender inside the sandbox would slow everything down, because users might specifically wish to run things that would cause defender to freak out, you know, to quarantine and delete their files, and because the entire point of the sandbox is that it's a safe place where terror may reign, with confinement, and nothing can get out you. You got full confinement there. So, unfortunately, it would probably come as no surprise to anyone who's been following this podcast for long to learn that the bad guys have figured out how to take up residence in Windows Sandbox as a means of obtaining secret persistence within Windows systems, while still being hidden from Windows Defender and any other AV scanning, which you know might be patrolling the grounds outside the sandbox but be unable to see inside. So let's take a closer look at how Windows Sandbox is being abused and what that means, and then we're going to examine what can be done to prevent its abuse, whether a user wishes to use Windows Sandbox or not for themselves.
So I'm going to start by sharing a piece of an overview of the problem which appeared in the Risky Business newsletter. That newsletter was headlined Chinese APT. So yes, we have Chinese advanced persistent threat actors. Chinese APT abuses Windows Sandbox to go invisible on infected hosts. Catalin, writing on the newsletter, wrote A Chinese cyber espionage group named Mirror Face, also known as Earth Kasha and APT10, is abusing the Windows Sandbox virtual environment to hide the execution of its malware on infected systems. Attacks incorporating Windows Sandbox have been taking place since 2023 and represent the first known case of Windows Sandbox abuse since its release in December of 2018.
As the name hints, the feature allows Windows users to start an isolated sandbox where they can temporarily install and test apps and then shut down the virtual environment without impacting the main OS and their data. It functions as a virtual machine, but it doesn't have all the bulky features of a VM. It's light, super fast, easy to start and use. It's light, super fast, easy to start and use. Abuse of this feature sounds implausible because Windows Sandbox support is disabled by default and when a sandbox is started it runs in a window in the user's foreground. But according to reports from the Japanese government and ESET, mirrorface has found a way around these limitations. The group gains an initial foothold on compromised networks, enables Windows Sandbox restarts systems, then silently launches Windows Sandbox instances that do not appear on the screen. This is accomplished by launching the sandbox via task scheduler under a different account from the user's current one, so the sandbox UI never appears on the logged on user.
The mirror face operators drop malware in a folder on the infected systems, then use Windows sandbox dot WSB configuration files to share access to that folder to the sandbox, grant the sandbox network access, then configure one of the malicious files to automatically run. I'm sorry, to automatically run when the sandbox is executed, since Windows Sandbox environments cannot run Defender. Nothing happens inside and is either logged or detected. This allows the attacker to install malware and open a hidden backdoor inside that system and a victim company's network. Japanese security firm ITOCHU explains how blind companies can become against Windows Sandbox-based attacks. They wrote since the malware in Windows Sandbox operates according to the WSB files configuration, it can access files on the host machine. However, because the files are accessed from the sandbox, activity is never logged by monitoring tools running on the host system monitoring tools running on the host system.
The technique used by MirrorFace seems to be an evolved version of a technique first documented by security researcher Lloyd Davies back in 2020. Ito CHU researchers say the abuse can go a few steps further, since new features are constantly being added to Windows Sandbox. For example, the Windows Sandbox can now share clipboard audio and video input with the base OS. The Windows Sandbox can now also be started via command line arguments using the new wsbexe command WSBexe command, which removes the need for WSB configuration files, which are artifacts security firms could use to detect possible abuse. The technique is incredibly simple to automate, even for low to mid-tier skilled malware developers.
Once detailed in these reports, it is likely to spread to other groups. The first to jump on and abuse this technique are likely ransomware gangs. Some groups are already using something similar. At least half a dozen ransomware groups have been spotted installing bulky VM software you know, full virtual machine suitesites on infected hosts, just to start the VM and send victim files to be encrypted inside. Where security tools don't have access to spot the ongoing encryption built in and present on all Windows 10 and Windows 11 systems, and the app's file is signed by Microsoft itself, abusing it is likely easier and safer. Ito CHU has published some monitoring and infection remediation advice to detect this technique, but the cat is out of the bag now and further and broader abuse is now expected to start taking place.
Okay, so one thing that's very interesting is the observation that the Windows Sandbox is able to launch and run under a different user's account, so that the foreground user never sees any indication that it's happening in the background. And here the inherent efficiency of Windows Sandbox, which so impressed me last week, actually works against the user, since its lightweight nature means a user would be much less likely to wonder where all their free RAM went because it wouldn't be going anywhere. It wouldn't be consuming very much, just like an app. Also, the default enabled clipboard sharing is a bit chilling, since it would be a bit like having a malicious instance of Windows Recall running unseen in the background, capturing anything the foreground user might temporarily place onto their clipboard, such as a cryptocurrency wallet address. I was curious to see what this researcher, lloyd Davies, came up with five years ago in 2020. Whatever it was, microsoft apparently blew it off without a second thought. Since we're now five years downstream of that and Windows Sandbox is still here and completely abuse prone.
Five years ago, under his headline weaponizing windows sandbox to bypass, defender lloyd davies wrote this short blog post may be useful for a red team living off the land for the execution of payloads on a machine where Windows Sandbox can be enabled. Windows Sandbox is designed to work this way. No exploitation of anything is covered in this post. With this technique, in terms of executing within a VM, we don't need to load an external ISO onto the machine, as all of this is handled by the sandbox. In my research, the sandboxwsb configuration file was not inspected or blacklisted on any major EDR or AV At the tail end of last year, microsoft introduced a new feature named Windows Sandbox WSB for short, windows Sandbox allows you to quickly, within 15 seconds, create a disposable Hyper-V based virtual machine with all the qualities a familiar VM would have, such as clipboard sharing, mapping, directories, et cetera.
The sandbox is also the underlay for Microsoft Defender Application Guard for dynamic analysis on Hyper-V enabled hosts, and can be enabled on any Windows 10 Pro Enterprise or education machine, making this perfect as a living off the land technique. Perfect as a living off the land technique. So you know he's couching this all as red team, not you know like how, like a, a, a red team who is are good guys acting to see, like to do um, uh uh, exploit, testing, uh uh, against someone who has hired them to check their defenses could use in order to obtain an undetected presence on computers. So he says the TLDR of this technique is to craft the WSB that can be executed on an endpoint which mounts the user's file system, allowing us to execute the implant inside a hidden VM and bypass any AVE DR that's on the host. The WSB configuration also seems to be bypassing Windows Defender on the host where it's executed. It's not incredibly complicated but could prove useful in an engagement.
Lloyd then proceeds to talk about a document the various ways very powerful wsb files can be created to give a malicious sandbox all the power it might need on the user's system, all while always remaining completely hidden and undetectable. He concludes his observations by writing A similar technique has been used by the infamous Maze and Ragnar Locker threat actors in recent times. However, they've installed third-party virtualization suites such as VMware and VBox. Using Windows Sandbox bypasses the requirement for this software to be installed. To complement this technique, he says I created a simple Go program to find drives automatically and mount network shares that include them as mapped folders, and then generates a WSB based on this. To an English language translation of the talk that was given last January in Japanese by the ITOCHU researchers. Among the many other things they've noted is that with the introduction of Windows 11, microsoft has enhanced the sandbox's features in ways that allow for additional abuses, they wrote.
The changes to Windows Sandbox after the Windows 11 update are as follows Addition of the wsbexe command enabling sandbox execution via the command line, background execution of the sandbox and the ability to modify certain settings via the GUI. These recent feature updates may make it more difficult to detect attacks leveraging Windows Sandbox. The key reasons for this are as follows, and they list three Background execution of Windows Sandbox. Previously in Windows 10 and early versions of Windows 11, windows Sandbox always ran as a foreground GUI application. However, with the new wsbexe start command, it can now run in the background. As a result, the sandbox can be launched without user awareness and its window remains hidden until the wsBexe connect command is executed.
Second, sandbox execution without a WSB file. The updated WSBexe command allows sandbox configurations to be set entirely via command line arguments. Previously, wsb files were an important forensic artifact during investigations, but this change increases the risk of leaving no trace of sandbox usage. And third, persistent data inside the sandbox. In earlier versions, closing the Windows sandbox window would terminate the process and delete all data within the environment. However, after the update, closing the window does not stop the sandbox and its data remains intact. To delete data, the sandbox must be explicitly stopped using the WSBXE stop command or terminated by shutting down the host machine. This change significantly increases the potential for long-term attacker operations within the sandbox. Given these updates, security researchers must carefully verify whether such feature changes improve convenience for attackers and implement appropriate countermeasures when new functionalities are introduced.
Having now explored the dark side of this otherwise truly useful and nifty Windows Sandbox feature, if it's not something that its user will be actively using, it might be worth considering taking some measures to neuter it so that it cannot be abused behind its user's back. Neuter it so that it cannot be abused behind its user's back. My number one favorite way to do this would be to disable a system's virtual machine extension's capabilities at the pre-boot firmware level. I recently learned that the BIOS settings backup battery on the aging gigabyte motherboard of my older Win 7 machine had died. My neighborhood had a planned day-long power outage while our local power company's equipment was replaced. When I fired my machine back up after having it shut down for the day, I quickly saw that it had lost its time of day and date clock. That's probably something that's familiar to us oldsters back in the days when you know the CMOS battery dies and the.
CMOS battery died.
2:34:19 - Leo Laporte
Exactly.
2:34:21 - Steve Gibson
So I rebooted and went into the BIOS and set that the time and date correctly. Some time later, when I attempted to launch a VirtualBox virtual machine, I received an error that VBox was unable to operate without the Intel virtualization technology, which is abbreviated VT-X, enabled in the system's BIOS. I mentioned last week that the same is true for Windows Sandbox. The Microsoft Hyper-V virtualization technology the Sandbox depends upon is in turn dependent upon having Intel's virtualization technology enabled technology enabled. So the absolute best protection for anyone who does not routinely use either the Windows Sandbox nor any of the many other various virtualization systems since all of those are now known to be prone to abuse as well, and especially Windows Sandbox, and especially Windows Sandbox would be to simply run without the Intel VT-X extensions enabled. No VT-X means no virtualization funny business period. Doing this will have zero impact upon Windows operation and it will completely shut down any chance of abuse. Now, if you do need to run virtual machines other than Windows Sandbox, you'll need to have the Intel VTX extensions enabled in your machine's firmware. Enabling Windows Sandbox requires admin privileges, but we know that doesn't present much of a barrier to malware, since pretty much everything bad that malware does requires admin privileges anyway so they're able to get it, and we know that elevation or privilege exploits are constantly being uncovered. The solution for anyone who wishes to prevent any behind-their-back exploitation of Windows Sandbox and for whom disabling all use of virtual machine technology via the VTX extension is not an option, Windows AppLocker is probably the next best solution. Applocker can either be configured in a managed enterprise setting through group policies or on a local machine using the local security policy snap-in. The use of AppLocker is straightforward and many how-tos exist on the internet for anyone who wants to take that approach. Under Windows 10 or 11, you'll want to block the execution of the WindowsSandboxexe executable program, which lives in the System32 directory it's System32 backslash, windowssandboxexe and additionally, under Windows 11, you would also want to prevent the Wbexe command from being used.
Once any of those have been foreclosed, anything that tries to crawl into your machine and set up shop behind your back using the windows sandbox will be out of luck, and I'm not.
I'm not suggesting that this is, like you know, the sky is falling and some, you know, major security problem to worry about. Remember that something bad has to get into your machine first before it's able even to have the opportunity to enable and use the Windows sandbox behind your back. So it's not like having the sandbox there is, you know, sending out a call for malware to come crawling in your machine. All of your existing defenses, windows Defender and AV tools and everything else that's already there is still functioning. It's just that if something gets in, everybody now knows there is a new place for it to hide. Everybody now knows there is a new place for it to hide, and hopefully Microsoft will take some action and do something to minimize, you know, the potential for this behind our back abuse. Because this is if you know, if bad guys are bothering to install VMware and virtual box on people's machines, they're sure going to be trying the Windows Sandbox first.
2:38:52 - Leo Laporte
Do they do that? They install virtual machines?
2:38:54 - Steve Gibson
Yes, they bring the whole VMware or VirtualBox system in Wow, it's crazy. And actually run a VMware or a VirtualBox VM in the background.
2:39:08 - Leo Laporte
Now you don't have to, because you can just use windows sandbox. That's right 15 seconds.
2:39:13 - Steve Gibson
You're ready to go, you bad malware you.
2:39:19 - Leo Laporte
Uh, great, great stuff, as always, steve. Thank you so much. I appreciate this. Thank Lori, for she gives you up a couple of days a week for this and I appreciate it and I I looked, it was actually a conversation she was having with someone else that included me ah, you were cc'd in, I know yes, it was somebody else who was sending her messages.
2:39:40 - Steve Gibson
That went to me too, so no, I saw your puzzled look.
2:39:44 - Leo Laporte
I was like why am I seeing this? That's all right. Lisa's texting me. She's at the big rsa conference in san francisco right now and a lot of our favorite people are there, including a hawks hunt and uh the threat locker guys, uh, haroon from uh, uh the thinks canary, and she's hobnobbing. She's having a great time. It's so much fun. I, she says next time you gotta go, you would really love rsa. Have you ever you've been to rsa, haven't you? That's where I found yubico. Right, that's right, that's right. A couple of years ago it was actually january 2020, come to think of it we had a party along with rsa, and we found out later that a number of people at RSA had COVID. It was one of the first appearances of COVID on our shores. Whoops, whoops. I didn't get it then. I've had it since, but I think next year we'd love to do something with RSA, because it's a great conference every year in.
San Francisco. All the security folks come by and it's a chance to see all the different tools and it's really it's a fun community and you make it fun because you are the king of security. Steve does security now with us every Tuesday. I hope you'll tune in and watch 130 Pacific 430 Eastern, 2030 UTC. We stream it on eight different platforms. Members, of course, can watch in the discord, kind of behind the velvet rope, but we also are on YouTube, twitch, tiktok we're back on TikTok. We are on kick, linkedin, facebook and xcom, so there's pretty much anywhere you go. You're going to see oh look, security now is on. You can watch along if you're. You're going to see. Oh look, security Now is on. You can watch along. If you're watching, you can chat on any of those platforms and I'll see it over here in my master chat screen. After the fact, you could download copies of the show.
Steve has some unique copies on his website, grccom. He has a tiny little 16 kilobit version for the bandwidth impaired. He has the 64 kilobit, which sounds exactly the same as ours, but it's half as big. It's kind of a miracle. It's a complicated, long story. We make 128 kilobit audio for reasons. He also has the show notes there, transcripts written by an actual human being, not an ai, elaine ferris, who is smarter than any ai. And, of course, once you're there, there's a lot of other things. The, the grc site is great. Uh, for instance, you can pick up a copy of spin right, the world's best mass storage, maintenance, recovery and performance enhancing tool 6.1, the current version right there on the website. If you don't already have a copy and if you bought a copy in the past, the upgrade is available to everybody for free, right, you upgrade everybody.
2:42:38 - Steve Gibson
Yeah, that's really nice of you, every single person.
2:42:41 - Leo Laporte
I was looking at my license. I think I bought it 20 years ago, yeah, but I got 6.1. Steve's a very generous fella. If you want, you can sign up for his newsletters there, including the weekly mailing of the show notes the day before, but also a very infrequent newsletter which might announce new products, like I don't know, a DNS benchmark pro kind of a thing at some point. That is grccom slash email and actually the other reason to go there is to validate your email to show Steve you're not a spammer. So that way, if you want to email him, as Alan Malventano did, you can email him and he will see it. Otherwise he ain't going to see it. Grccom slash email.
We have the 128 kilobit audio version on our website, as well as video at twittv. Slash SN there is. You'll see a link right there to a YouTube channel. That's a good place to know about. That's the video, but it also is an easy, simple way to share little bits of the show. If you want to clip something and say, hey, I got to send this to my friend, do it there on the YouTube site. Everybody's got YouTube. It's easy. Everybody will understand how to use it. It's a great way to promote the show and we thank you for doing that.
Of course, the best way to get the show for yourself is subscribe. That way, you don't have to think about it. You'll get it the minute it's available. Any podcaster should have a copy of Security. Now, oh and when you do that, please leave us a five-star review. Share the wealth. Let other people know how useful this show is. Don't keep it to yourself. That wouldn't be right. It won't dilute it any, I promise. No, as a matter of fact, it doesn't. It just strengthens the solution. Next week, episode 1024. Yay, we hit 1K. Nice, steve, have a great week and we will see you next time on.
2:44:32 - Steve Gibson
Security Now. Oh, and it'll be May. We're going to see you in May, yay.
2:44:37 - Leo Laporte
May Bye.
2:44:37 - Steve Gibson
Bye.